April 17, 2025
Updated: March 2, 2026
How CPT compresses exposure windows, breach probability, and expected loss in high-velocity enterprises.
Mohammed Khalil

Continuous Penetration Testing (CPT) is a continuously operating adversarial control validation process that re-tests exploitable attack paths as systems, identities, and configurations change. It continuously verifies security controls and shrinks the time a vulnerability remains untested (the Exposure Window), thereby compressing breach probability and expected loss (EL = Probability (P) × Impact (I)). By shortening Exposure Windows, CPT directly lowers P and thus EL, providing near real time risk compression.
AI driven exploitation velocity has permanently altered breach economics. Adversaries no longer wait for annual control validation cycles; they weaponize configuration drift, identity sprawl, and cloud misalignment in near real time. Meanwhile, insurers are tightening underwriting scrutiny, regulators increasingly expect continuous monitoring evidence, and boards demand quantifiable cyber risk metrics tied to financial exposure.
In this environment, traditional penetration testing services are structurally misaligned with adversarial tempo. Continuous Penetration Testing must therefore be understood not as enhanced testing frequency, but as a probabilistic risk compression mechanism aligned to modern threat velocity.
Continuous testing drives Exposure Window (EW) reduction and thus risk compression. For example, an enterprise may observe vulnerability exposure percentiles such as: EW P50 = 14 days, P75 = 30 days, P95 = 90 days. CPT aims to compress these windows (e.g. shift P95 closer to P50).
Mathematically, reducing EW shortens the time attackers have to exploit a flaw, which lowers breach probability and expected loss. For a constant daily attack rate λ, the breach probability over EW days is (P = 1 - (1 - λ)^EW). Thus,
Enterprise example: Assume 1% daily exploit chance (λ≈0.01). Over a 5 year horizon, a 90 day window yields (P=1 (0.99)^{90}≈60%) chance of breach (for that vulnerability), whereas compressing EW to 30 days yields (P≈26%). If impact (I)=$5M, EL falls from ≈$3.0M to ≈$1.3M. CPT’s shrinking of EW from P95 to P50 dramatically cuts multi-year risk.
The chain of exposure compression is explicit: as EW decreases, the opportunity for attackers falls, so breach probability decreases, which in turn reduces expected loss (EL). This linkage makes shorter exposure windows a primary lever for risk reduction. (See IBM data: lifecycle <200d ⇒ $3.87M cost vs $5.01M for >200d.)
Consider a cloud native environment following a microservice deployment. A newly exposed authentication endpoint contains a logic validation flaw (Initial Access). An adversary exploits the flaw to obtain a low privilege token. That token is then reused to pivot into an internal API (Lateral Movement), where insufficient segmentation allows privilege escalation via misconfigured IAM roles as demonstrated in our AWS penetration testing guide. From there, sensitive data repositories become accessible and exfiltration occurs.
A periodic penetration test might identify the initial flaw. However, unless the exploit chain is continuously revalidated after each deployment or configuration change, downstream privilege boundaries may remain untested for months.
Continuous Penetration Testing interrupts this sequence at each boundary:
Chain logic is therefore treated as a living control surface, not a historical report artifact.
To illustrate multi year risk compression, use the formula for n year breach probability:
[ Pn-year = 1 - (1 - P1-year)^n ]
For 5 years: (P_{5y} = 1 (1 P)^5). Two scenarios show the effect of lowering P:
Despite only a 4× reduction in annual P (20% → 5%), the 5 year risk drops by more than half (67% → 23%). This nonlinear compression means CPT’s reductions in P yield outsized multi year benefits.
Worked example: If an enterprise cuts its annual breach likelihood from 10% to 5%, the 5 year breach chance falls from ~41% to ~23%. CFOs can translate this into lowered expected losses (EL = P×I) over the planning horizon.
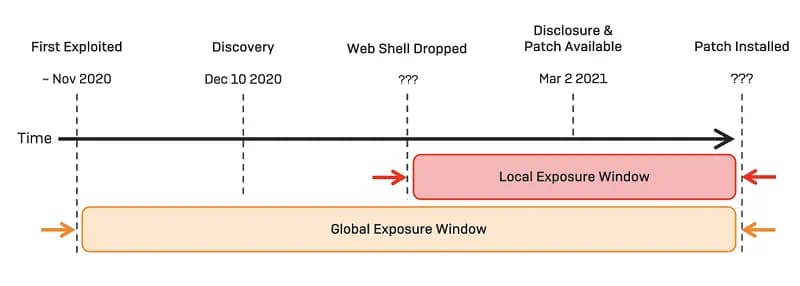
Exposure Window compression directly reduces breach probability and expected loss.
Decision Variables
Define five quantifiable drivers:
Decision Logic Model:
If:
Then: Periodic pentesting is structurally insufficient. Continuous Penetration Testing is economically justified.
Else: Hybrid PTaaS or quarterly pentesting may be sufficient.
Definition: The Continuous Validation Efficiency Ratio (CVER) is a metric of CPT investment efficiency. It is defined as the amount of vulnerability exposure time eliminated per unit of testing spend. Formally:
[ \text{CVER} = \frac{\text{Exposure days eliminated}}{\text{Annual CPT cost (USD)}}. ]
This yields units of exposure days per dollar (or its inverse, cost per exposure day eliminated).
Formula and example: For instance, if an organization spends $100,000 on CPT annually and thereby reduces total annual exposure by 500 asset days, then CVER = 500 exposure days / $100,000 = 0.005 days per dollar. Equivalently, the cost per exposure day eliminated is $200.
Interpretation: Boards and CFOs can use CVER to benchmark CPT ROI. A higher CVER means each dollar of CPT drives significant risk reduction. For example, if each exposure day is valued at $5,000 in potential damage, then a CVER of 0.01 (1 day per $100) implies $5 of loss prevented per $100 spent (5% ROI just from reduced exposure time). Over time, this multiplier effect is used to justify CPT budgets.
Board usage: Presenting CVER in dashboards translates technical testing into financial terms (X exposure days prevented for $Y spent), enabling risk committees to compare CPT efficiency against other controls. High CVER scores (on a consistent scale) signal to leadership that CPT is delivering material risk reduction per dollar.
| Attribute | Annual Pentest | PTaaS | Continuous Penetration Testing |
|---|---|---|---|
| Cadence | 1–2 times/year | Monthly or quarterly cycles | Event-driven, continuous |
| Exposure Window | 90–365 days | 30–90 days | Hours to days |
| Financial Impact | Static snapshot | Reduced exposure gaps | Probability compression engine |
| Governance Alignment | Compliance-driven | Semi-operational alignment | Fully integrated with risk governance |
| Insurance Leverage | Limited underwriting impact | Moderate insurer confidence | Strong underwriting signal |
| Cost Structure | Fixed project-based fee | Subscription retainer model | Strategic risk allocation model |
| Strategic Fit | Compliance minimum requirement | Scaling / growing organizations | High-velocity, cloud-native enterprises |
| Board Concern | CPT Validation Metric | Financial Effect | Governance Signal / Framework |
|---|---|---|---|
| Unquantified cyber risk Lack of clear risk metrics (likelihood/impact) | Exposure Window & MTTI/MTTC Median/95th percentile time to remediate (EW) or prevent exploitation; reduction in attack chain exploitability count. | Tighter EW lowers expected breach losses (P×I), which compresses budget volatility and insurance exposure. | NIST CSF 2.0 Govern (GV) establishes risk mgmt strategy and risk quantification. Continuous monitoring per NIST SP 800 137. |
| Regulatory/compliance risk PCI, FedRAMP, GDPR concerns about undetected vulnerabilities | Penetration Test Coverage Frequency and scope of tests; percentage of CDE (Cardholder Data Environment) tested; time between critical fixes. | Reduces fines, breach remediation costs, and downtime. Demonstrates proactive controls to regulators/boards. | PCI DSS 4.0 (Req 11.x) requires regular pen tests; CPT supports or exceeds annual testing. Continuous monitoring mandates. |
| Insurance and audit pressure Demand proof of effective controls | Control Validation Logs & Trends Number of successful test iterations vs failures; trending risk score reductions. | Strong control evidence can lower premiums or expand coverage. Reduces potential claim payouts. | Insurance underwriting best practices (proof of controls); NIST/ISO risk management audits (supply chain, systemic risk). |
| Rapid change environment Cloud migrations, agile releases, supply chain changes | Change Rate vs Test Rate Velocity of code/infra change vs frequency of CPT validations; number of new findings per period. | Prevents compounding of unattended flaws; reduces large scale corrective costs (e.g. emergency patching, incident recovery). | NIST CSF Identify/Protect (change mgmt); Continuous monitoring doctrine (visibility on new vulnerabilities). |
| Strategic reporting Demand for metrics vs narrative | Risk Dashboards Reporting of quantitative P, I, EL metrics; validation pass/fail rates; governance scores. | Improves decision making on risk appetite and controls investment; connects cybersecurity to financial planning. | NIST CSF’s emphasis on communication and governance; Board Risk Committee charters; regulatory boards. |
| Aspect | Continuous Penetration Testing (CPT) | Traditional Pentesting |
|---|---|---|
| Timing | Testing runs 24/7 or on a very frequent schedule, immediately after changes. | Conducted annually or after major changes. |
| Validation Freshness | Control validations and findings are always up to date, reflecting current environment. | Findings are a historical snapshot; risk may re accumulate quickly. |
| Chain Logic Validation | Simulates and validates full adversary kill chains (e.g. via MITRE ATT&CK methodology) continuously, not just point in time. | Often focus on isolated vulnerabilities; complex chains may only be partially tested once a year. |
| Exposure Governance | Monitors and reports ongoing exposure windows (time vulnerable) across assets; KPIs drive reduction. | Measures exposure only at test time; after report, actual EW may grow unchecked. |
| Primary Output | Quantitative risk metrics (likelihood, impact, EL) and dashboards for executives. | Detailed pentest reports (vulnerability lists) aimed at remediation; primarily technical deliverable. |
| Aspect | Continuous Penetration Testing (CPT) | PTaaS (Pentest as a Service) |
|---|---|---|
| Timing | Truly ongoing; often fully automated or hybrid (24/7). | Usually subscription based but periodic (e.g. monthly/quarterly engagements). |
| Validation Freshness | Near real time re testing after each change. | Freshness depends on testing cadence; may lag actual changes. |
| Chain Logic Validation | Validates complete attack chains on demand, leveraging frameworks (MITRE ATT&CK) to test end to end kill chains continuously. | Provides deep manual and automated tests, but typically on schedule; may not re validate chains until next cycle. |
| Exposure Governance | Actively shortens exposure windows and records metrics continuously. | Provides recurring risk assessments and reports but can leave longer static exposure between engagements. |
| Primary Output | Embedded risk dashboards with trend metrics (EW, P, EL) for governance. | Comprehensive pentest reports at each cycle; helps close gaps but less continuous risk data. |
CPT is an always on security testing practice that continually simulates real world cyberattacks against an organization’s systems and controls. Unlike a one time annual pentest (see black box vs white box penetration testing ), CPT automates regular red team style assessments (often using frameworks like MITRE ATT&CK) immediately after changes. It systematically re validates critical defenses and attack chains in near real time, producing evidence based risk metrics for executives. The goal is to eliminate vulnerability exposure quickly and maintain continuous assurance of control effectiveness.
By dramatically shrinking the vulnerability exposure window. CPT continuously finds and fixes weaknesses soon after they appear, so attackers have less time to exploit them. In risk terms, CPT lowers the breach probability P in the formula EL = P×I. For example, IBM data shows breaches contained in under 200 days cost roughly $3.87M vs $5.01M for longer breaches indicating that faster containment (smaller exposure) greatly reduces risk and cost. Over multi year periods, even modest reductions in P have large effects (5 year breach chance falls precipitously as P declines), so CPT’s continual testing yields outsized reductions in expected loss.
No. PCI DSS 4.0 does not explicitly mandate continuous pen testing. It requires at least annual penetration tests (Requirement 11.3) and tests after significant changes. CPT is not a stated PCI requirement, but it can help meet and exceed compliance. In fact, PCI’s new guidance (Req 6.4.2) hints that organizations should continuously assess changes. Implementing CPT can therefore streamline PCI compliance by effectively satisfying continuous monitoring expectations without waiting for annual tests.
Cost for continuous validation (CPT) services varies based on scope (number of assets, complexity, change rate) and vendor.. It is typically offered as a subscription or service fee. Smaller organizations might spend tens of thousands annually, while larger enterprises could invest hundreds of thousands per year. Costs are often framed relative to the value of reduced risk (see CVER). While CPT generally costs more than a single pentest, it replaces or augments periodic testing and eliminates costly breach scenarios. In practice, CPT budgets are often aligned to a fraction of expected breach savings for example, if $1 of CPT spend prevents $5 of breach losses (per CVER analysis), the investment is justified.
They are different models. PTaaS is a managed service offering periodic pentests on demand (e.g. quarterly or monthly) via a vendor platform. CPT extends that by making testing truly continuous. CPT often incorporates or builds on PTaaS capabilities (automation, reporting). In general, CPT provides more frequent validation and broader chain testing, delivering higher confidence and fresher security posture. PTaaS may suffice for organizations with slower change rates or limited budgets. Neither is strictly better universally; CPT represents a strategic shift for high risk or high velocity environments, whereas PTaaS can be an interim or complementary solution.
Transition to CPT when static testing is not keeping up with business velocity or risk exposure. Key triggers include:
Mid-Market Organizations Best suited for hybrid CPT-light models focused on internet-exposed assets and compliance alignment.
Enterprise (Multi-cloud / High Change Velocity) Full CPT implementation integrated into CI/CD, identity governance, and executive dashboards.
Regulated Industries (Finance, Healthcare, Critical Infrastructure) CPT aligned to regulatory continuous monitoring mandates, insurer reporting, and board-level risk tolerance thresholds.
CPT maturity should align with exposure complexity and financial materiality, not security marketing narratives.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us