November 7, 2025
Updated: November 6, 2025
Discover the key differences between internal and external penetration testing methods, tools, compliance, and why both are essential in 2025.
Mohammed Khalil

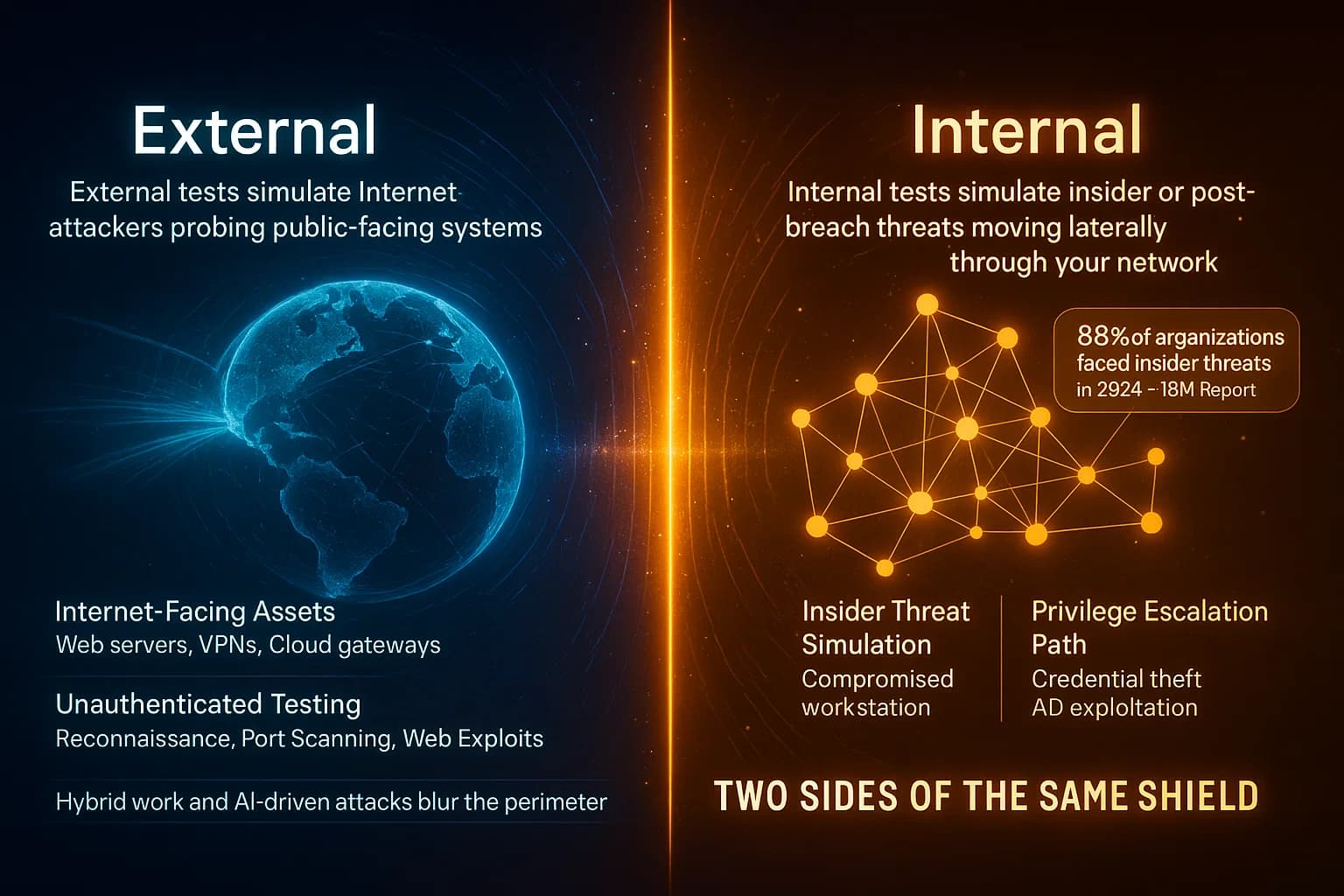
Penetration testing comes in two flavors, external and internal. An external penetration test acts like an attacker on the Internet with no inside knowledge, probing your firewalls and public IPs. By contrast, an internal penetration test simulates a threat behind the firewall, say a malicious insider or malware that has already breached the perimeter. Both perspectives are crucial. In today’s landscape hybrid work, cloud apps, AI driven attacks, organizations can no longer assume the network perimeter is impregnable. For example, IBM reports that in 2024 about 83% of organizations experienced at least one insider attack. That underlines why we can’t rely solely on external testing.
In the first 100 words: External tests probe internet facing systems, websites, VPNs, etc., while internal tests probe the LAN from a user’s viewpoint. This matters in 2025 because sophisticated threats and remote endpoints have blurred old perimeters. As one security blog puts it, external pentests simulate internet based attacks on public facing assets like servers or VPNs, whereas internal pentests simulate insider threats or a device that’s already inside to find privilege or lateral movement risks. In this article, we define each type, compare their goals and methods, and explain when and how to use both.
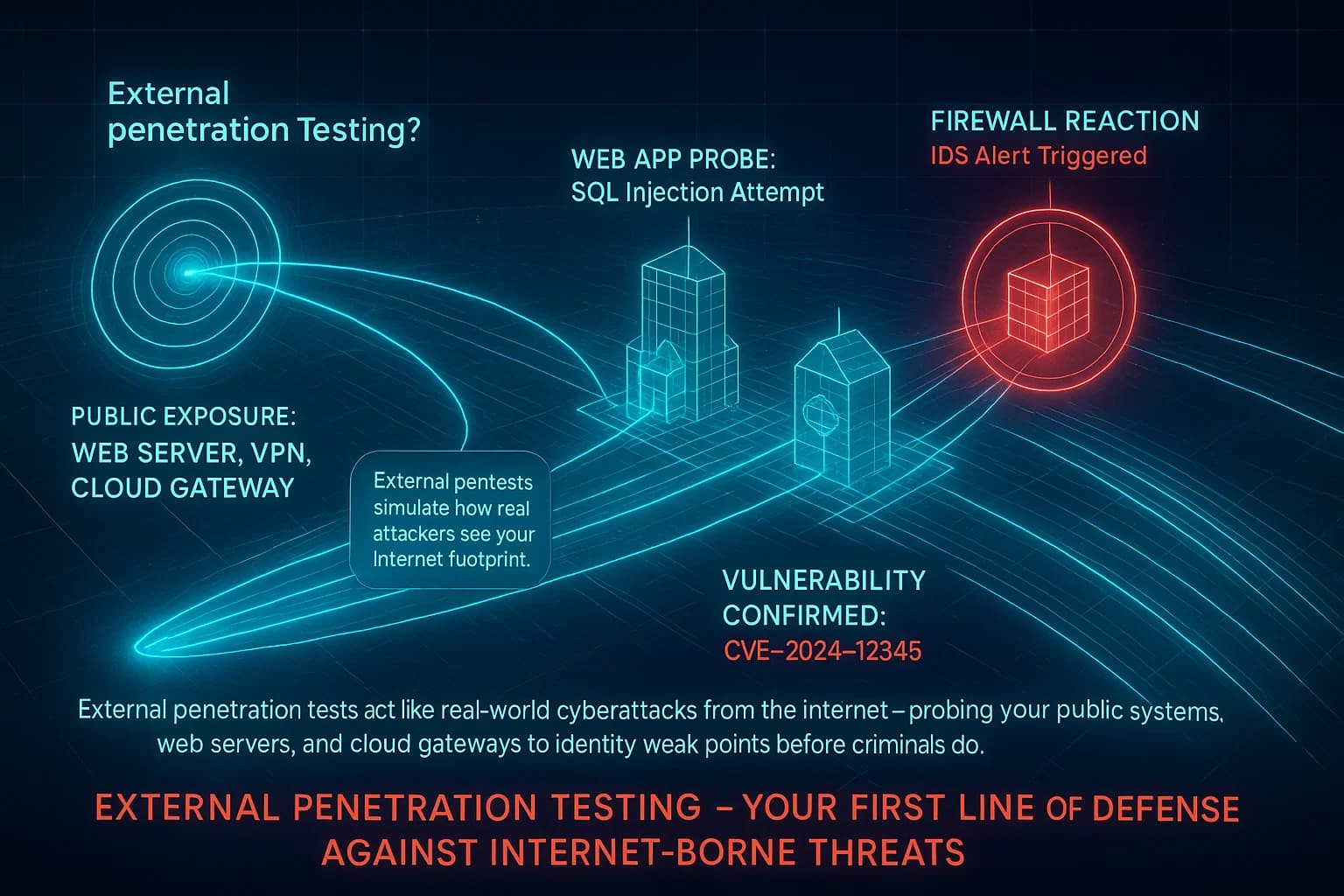
An external penetration test focuses on perimeter security. The testers have no credentials and treat your defenses as if they were strangers on the Internet. They use only publicly available information IP addresses, domain names, WHOIS data and try to find exposed entry points. The goal is to see if an outsider could penetrate your network from the outside. External pentesters will scan open ports on firewalls and routers, probe web applications looking for SQL injection, XSS, etc., test VPN or RDP gateways, and check for weak authentication on internet facing services.
Key points for external testing, testers are outside your firewall with zero prior access. They use techniques like open source reconnaissance, port scanning e.g. Nmap, vulnerability scanning Nessus, OpenVAS, and web application testing Burp Suite, OWASP ZAP. Since their traffic passes through your perimeter defenses, firewalls, IDS/IPS, they get a realistic view of what’s visible from the Internet. In short, external tests find holes that real world Internet attackers might exploit.
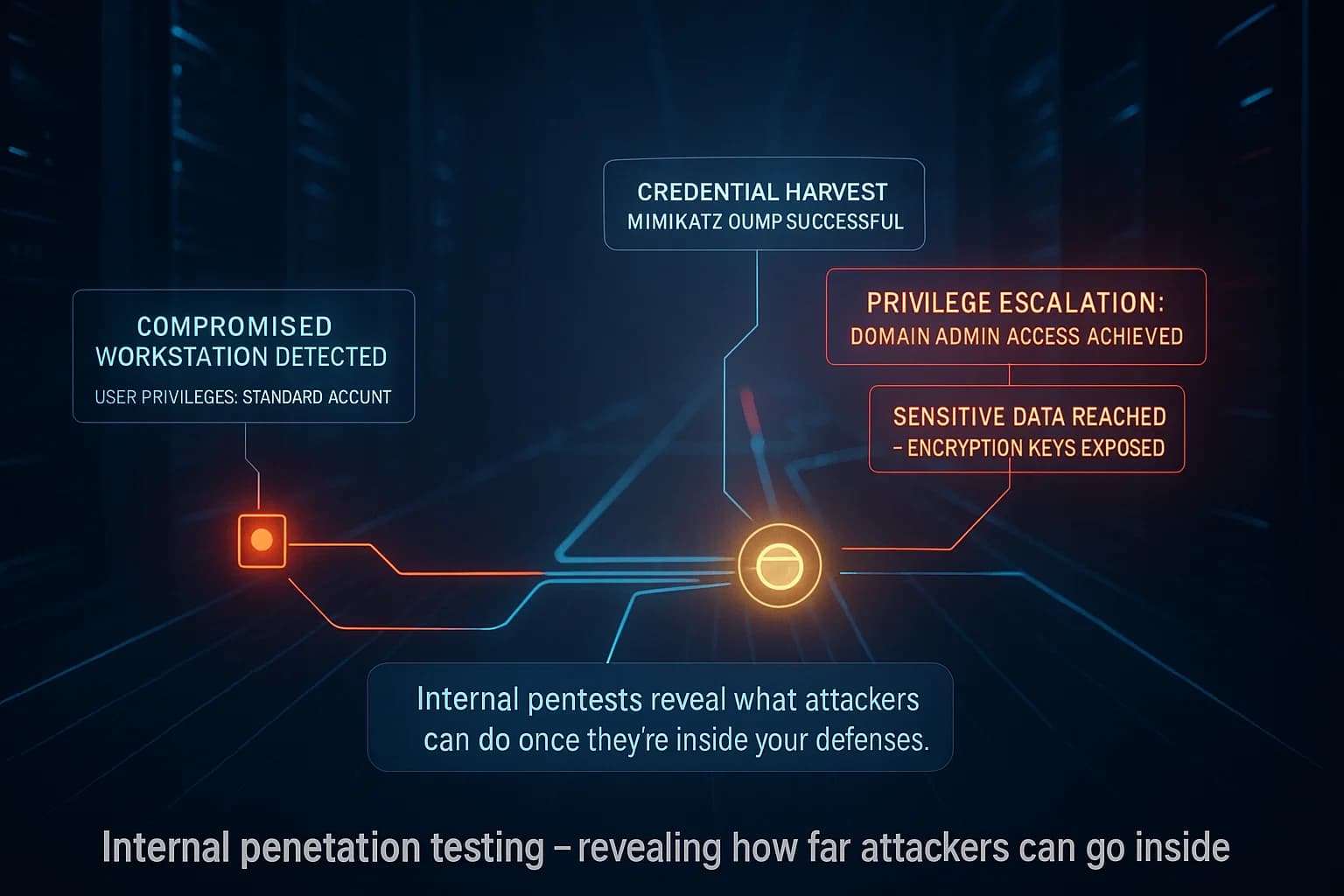
An internal penetration test starts from inside the network, assuming an attacker has managed to get in or is a malicious insider. Testers are given user level network access for example, a VPN or a compromised workstation account and they try to move laterally and escalate privileges. This simulates scenarios like a disgruntled employee, a compromised PC, or malware that has already breached the firewall. The focus shifts to internal systems: file servers, workstations, internal web apps, Active Directory domains, etc.
Internal pentesters will run LAN port scans, enumerate network shares and services, attempt password attacks using tools like Hashcat/John, and use Windows credential tools like Mimikatz or Responder to harvest credentials. They test for misconfigurations in AD group policies, lack of network segmentation, or vulnerable internal apps. The objectives are to see how far an attacker could go once inside: Can they reach the domain controller? Steal sensitive data? Take over admin accounts? As one source explains, internal tests aim to uncover issues like privilege escalation, lateral movement, and unauthorized access to sensitive data.
Importantly, internal pentests cover the internal perimeter for example, the Cardholder Data Environment in PCI DSS. PCI guidance clarifies that an internal test looks at the internal network of systems handling card data, not just front door systems. In practice, external pen testing checks how effectively your defenses can withstand real world attacks from external threats, while internal pen testing shows the damage an attacker could do if they bypassed those defenses.
| Aspect | External Penetration Test | Internal Penetration Test |
|---|---|---|
| Attacker Location | Outside your network, treating it as a black box. | Inside the network behind the firewall insider or assumed breach. |
| Initial Access | Unauthenticated; testers only know public IPs/domains. | User level credentials or VPN access provided simulating an employee. |
| Scope | Internet facing assets: web servers, VPN/RDP gateways, mail servers, etc. public attack surface. | Internal LAN: workstations, internal servers, databases, AD controllers, network devices inside the firewall. |
| Focus Areas | Perimeter security, firewall rules, IDS/IPS, network borders. | Lateral movement, privilege escalation, internal app bugs, segmentation flaws. |
| Common Tools | Nmap, Nessus/OpenVAS, Burp Suite, Metasploit, Hydra, etc. for external scanning and exploitation. | Nmap internal scans, Active Directory tools BloodHound, CrackMapExec, credential tools Mimikatz, Responder, Wireshark, Metasploit for internal exploits. |
| Examples of Tests | Exploiting a web app on your public site, guessing VPN passwords, testing open ports on routers. | Dumping domain creds with Mimikatz, exploiting trust relationships, cracking local passwords, testing network shares. |
| Typical Frequency | Required at least annually or after major changes e.g. per PCI DSS 11.3. | Also annual or after internal changes; used for insider threat assessment and compliance PCI requires both. |

Both test types share some tools, but emphasis differs. Both may use Nmap or Nessus for scanning. External tests rely heavily on web/vulnerability scanners Burp, Nikto, ZAP and brute force tools for login pages. Internal testers use internal focused tools: Mimikatz credential dumping, Responder LLMNR/NBT NS spoofing, BloodHound AD mapping, and password crackers Hashcat, John. For example, Mimikatz is famous for pulling Windows credentials during an internal pentest, while Burp Suite is a staple for attacking web apps externally.
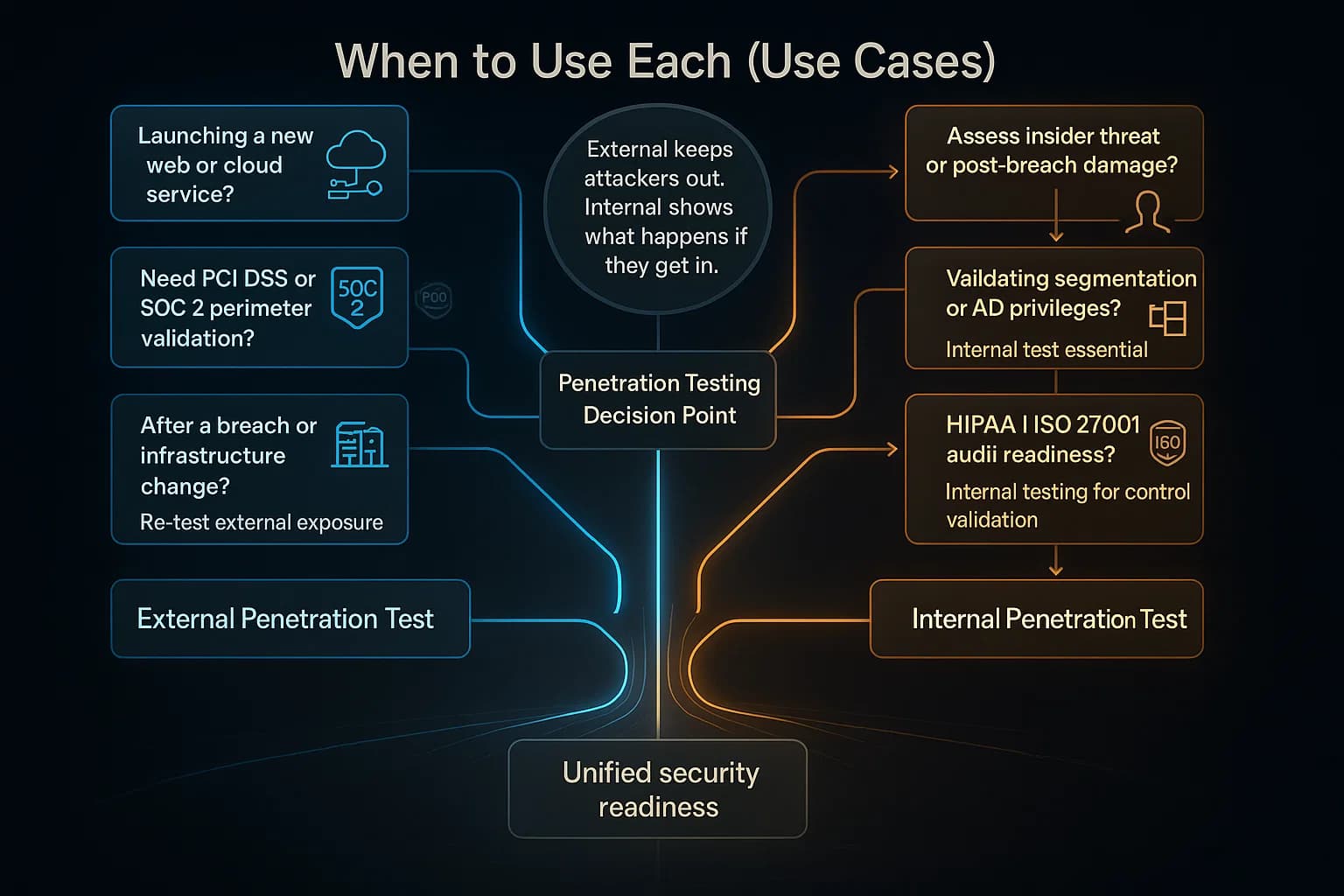
In practice, both types complement each other. External tests protect your perimeter; internal tests show the fallout if that perimeter is breached. Industry experts recommend running both. PCI DSS 11.3, for instance, explicitly covers the entire external and internal card data environment. Likewise, ISO 27001’s principles of risk management imply testing all parts of the network. New HIPAA rules proposed in late 2024 are moving toward mandating annual penetration tests of ePHI systems. Bottom line: a strong security program schedules both external and internal pentests at least annually and after big changes.
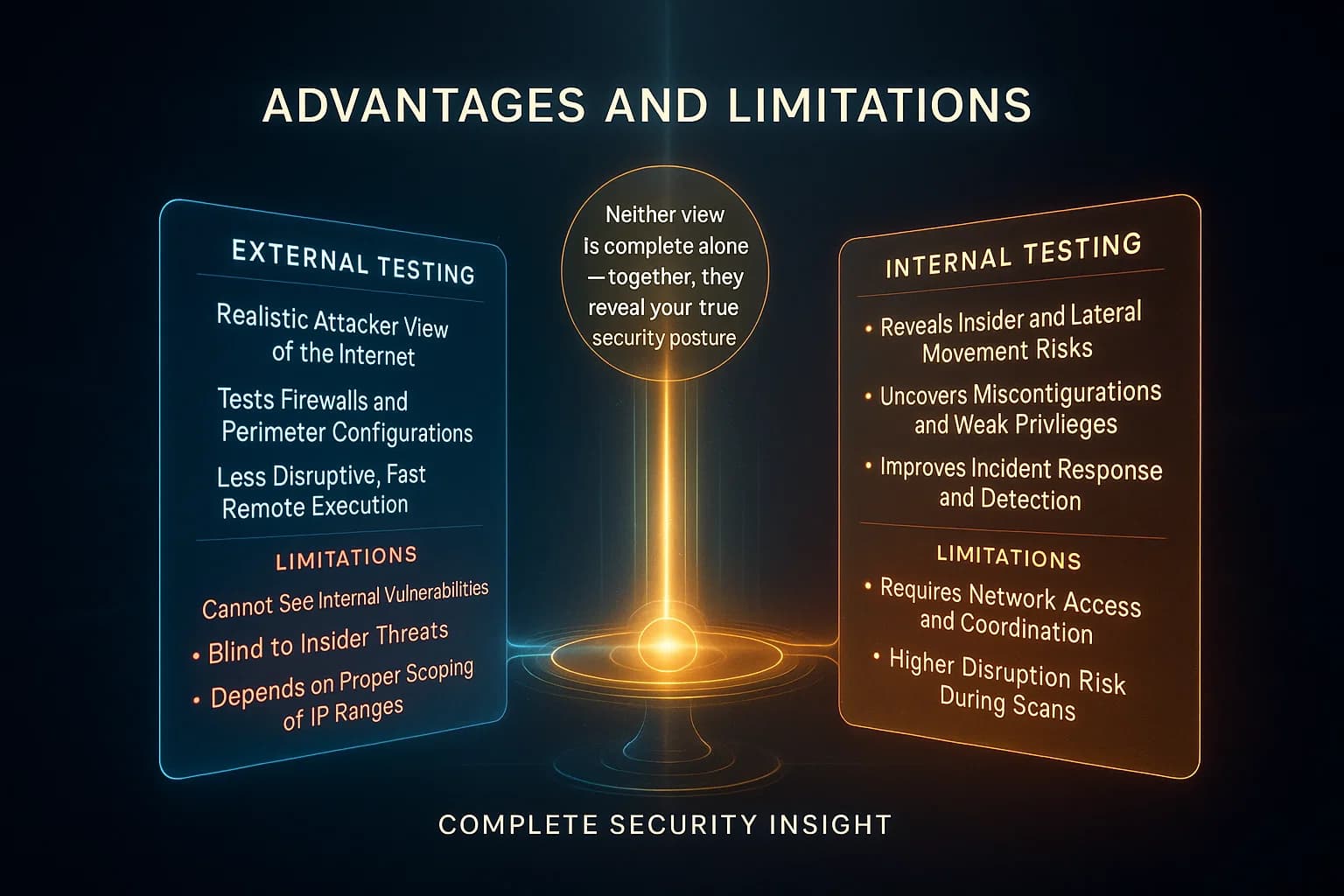
Neither type is a silver bullet alone. External tests keep the bad guys out; internal tests show what happens if they get in. Together, they provide a full picture of your risk profile.
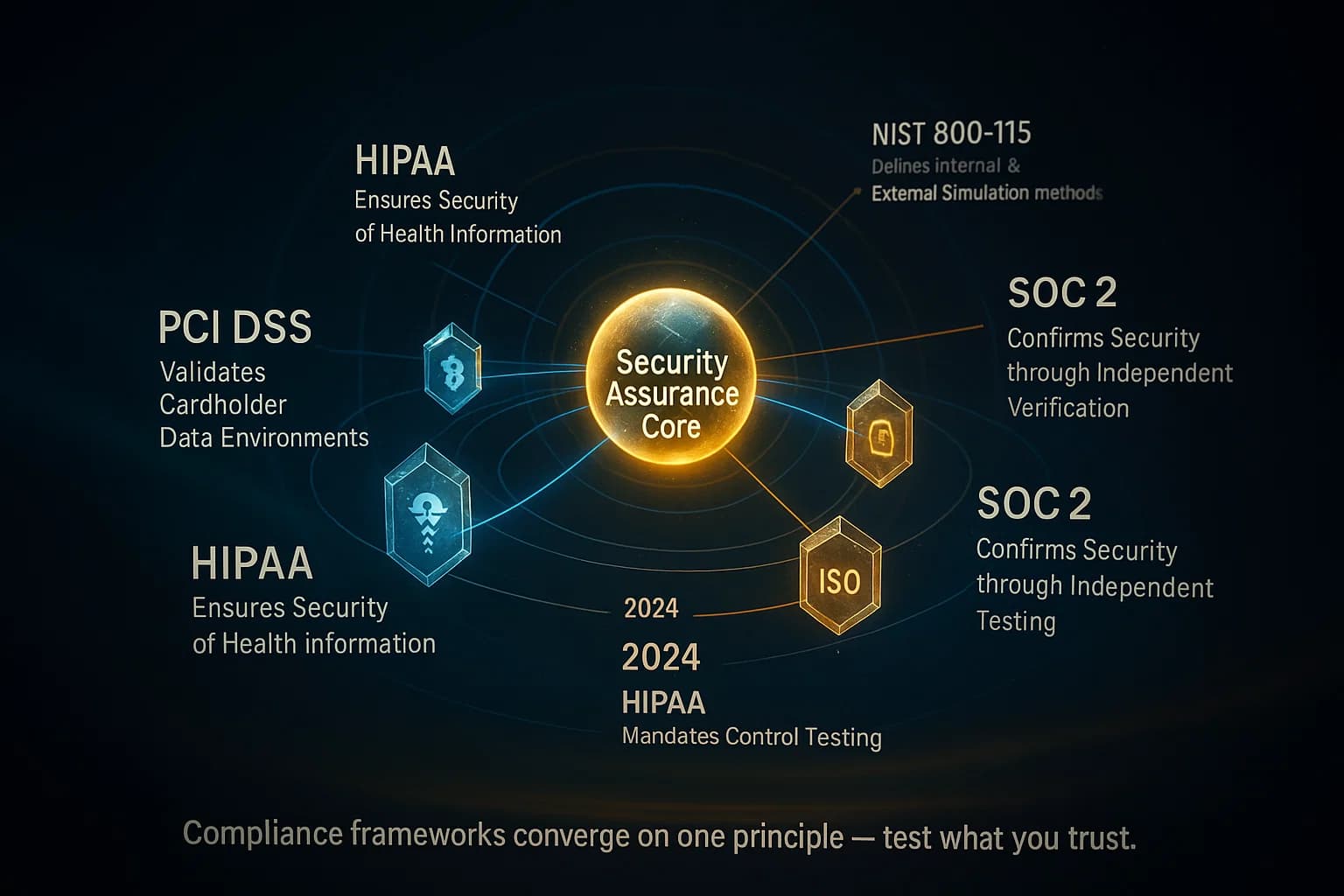
Most security frameworks expect both perspectives. The PCI DSS Payment Card Industry famously mandates both external and internal tests of your cardholder data environment CDE each year. The PCI Pen Test Guidance spells out that the scope of a penetration test… includes the entire CDE perimeter and any critical systems, covering both public facing external and internal segments. In practice, PCI audits demand that all Internet facing card systems and all in scope LAN systems be tested annually by qualified testers.
For HIPAA U.S. healthcare privacy law, penetration testing wasn’t always explicitly required, but that’s changing. The December 2024 NPRM from HHS would mandate annual pen testing of systems handling ePHI. Even today, best practices and OCR guidance encourage HIPAA regulated entities to include both external and internal pentests as part of risk assessments, since health data breaches can originate from either vector.
ISO/IEC 27001: The standard doesn’t name penetration testing, but it requires regular vulnerability assessments and technical testing of controls. Organizations typically interpret this to include both external and internal tests. Section A.12.6 of ISO 27001 Security of systems and applications implies that testing of internal and external systems should happen routinely.
Other frameworks SOC 2, NIST 800 115, GLBA, etc. all recommend or require testing your defenses. NIST SP 800 115 explicitly notes that a pentest scenario can simulate an inside attack, an outside attack, or both, and that both methods should be considered in planning. In short, compliance and best practice guidance almost universally assume a comprehensive approach: prove your perimeter security with external tests, and validate your internal controls with insider tests.
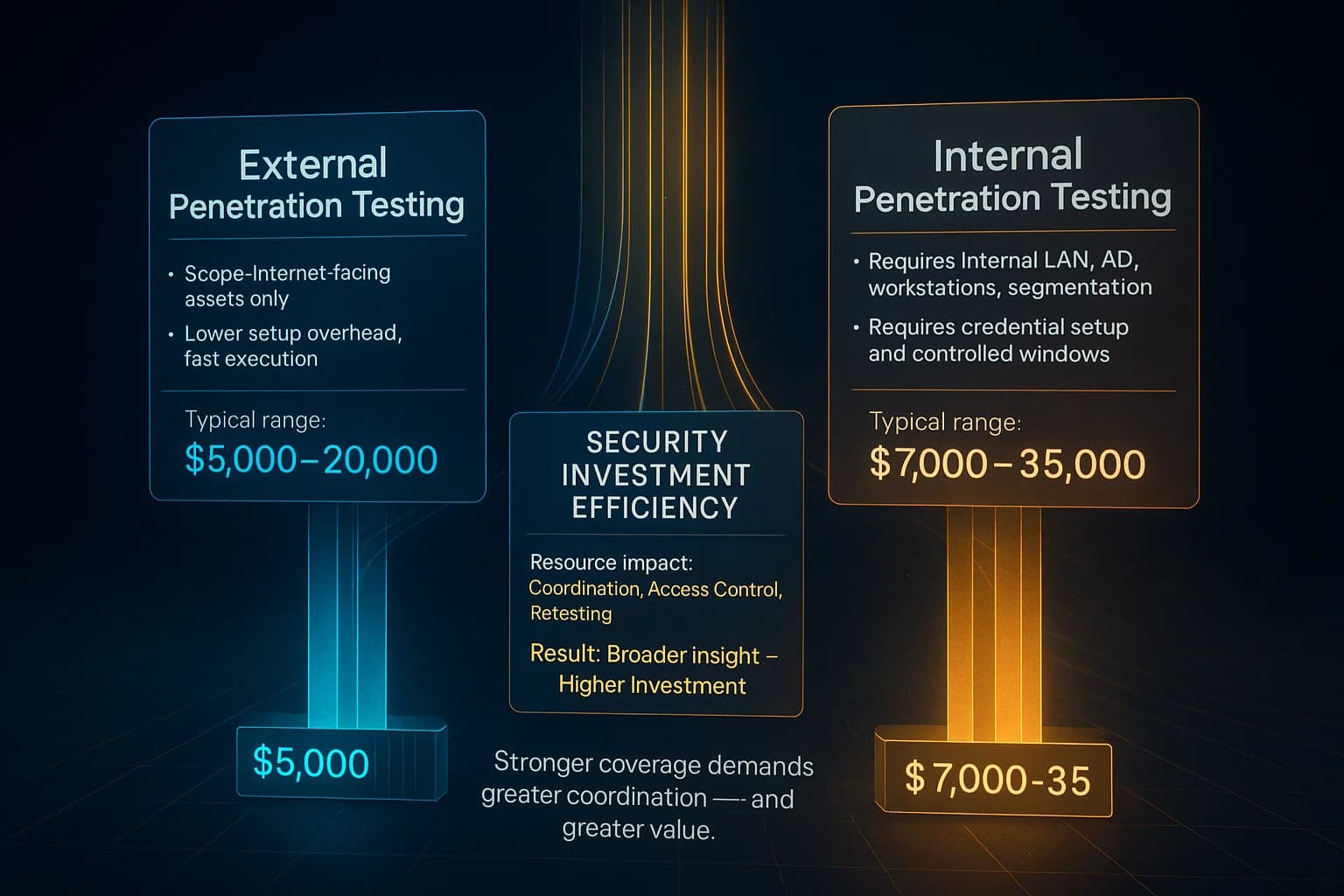
Budgeting also reflects the difference in scope. Generally, external tests are smaller and cheaper than full internal tests. External tests may involve scanning a handful of IP addresses or servers, whereas internal tests often cover dozens or hundreds of workstations and servers. According to industry data, external penetration tests typically range around $5,000- $20,000, while internal penetration tests are often in the $7,000- $35,000 range. Prices vary widely by scope: a simple website test on one server might be low end, while a large internal network test can climb much higher. So in practice, internal pentests often cost more due to the broader asset count and longer testing time.
Resource wise, external tests can usually be done remotely with minimal involvement from the client. Internal tests may require on site access or secure VPN setup and closer coordination with IT to provide test accounts, define safe scanning windows, etc.. Because internal testing is closer to production, it must be carefully planned to avoid disrupting business e.g. scheduling around sensitive hours.
In house teams sometimes handle internal pentesting using their own tools and knowledge of the network, while third party vendors typically perform external tests for an impartial view. However, many organizations hire external specialists for both types to ensure independence. In any case, remember that the testing cost is just one part of the budget you’ll also want to allocate resources for remediation. Internal scopes especially can generate many findings e.g. patching dozens of systems, so fix management and any retesting need planning too.
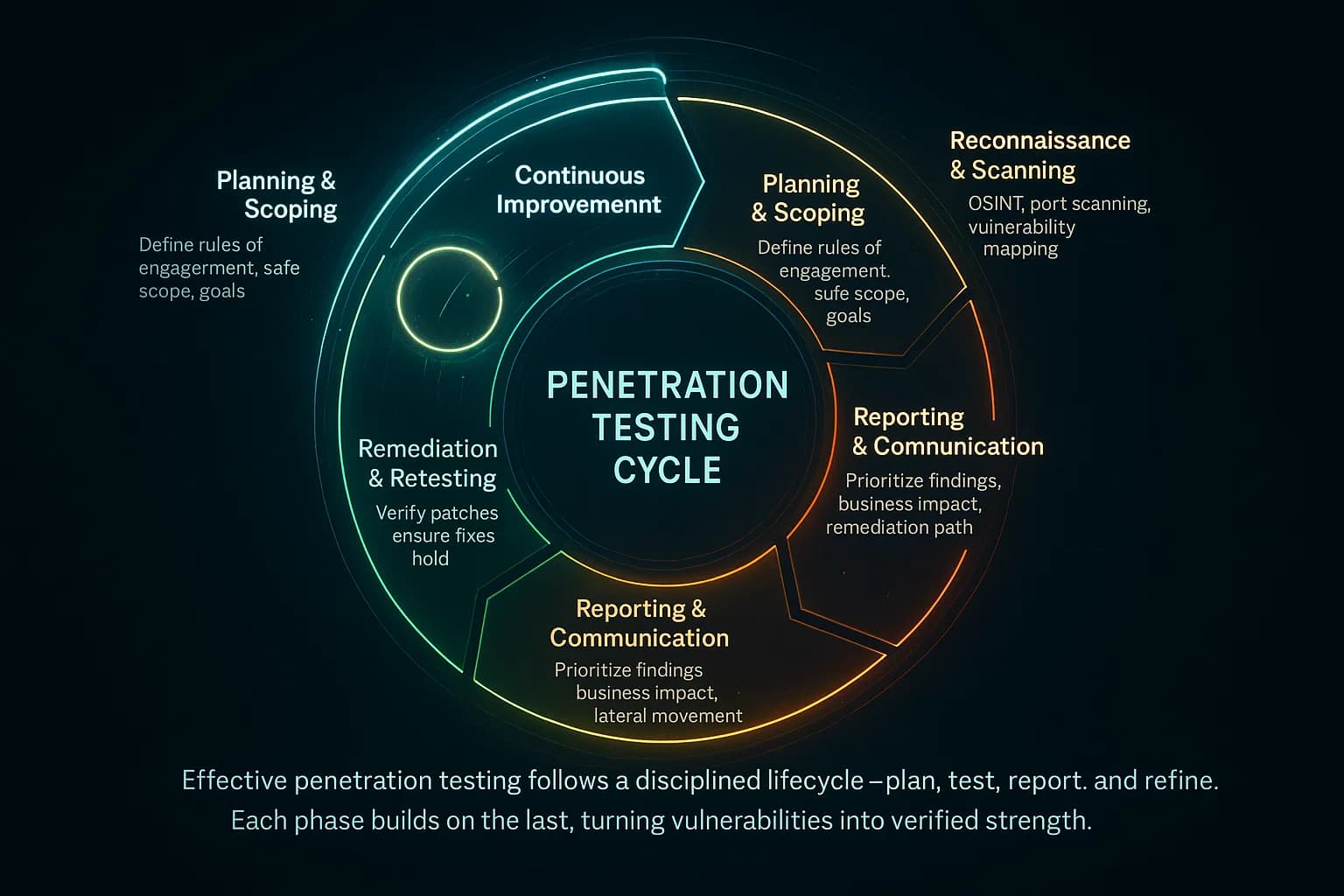
To maximize the value of both external and internal pentests, follow these best practices:
By scoping carefully, using skilled testers, and acting on the results, organizations turn pen testing into a cycle of continuous improvement. The goal isn’t a one time checkmark, but an ongoing arms race: find holes before attackers do.
Internal and external penetration tests address different pieces of the same security puzzle. External tests harden your perimeter against outside threats, while internal tests reveal what an attacker could do once inside. In today’s world 2025 and beyond, you can’t afford to rely on one without the other. Combined, they validate your defenses both at the firewall and behind it. By understanding the differences, using the right tools, and following best practices, organizations stay one step ahead of attackers.
Ready to strengthen your defenses? The threats of 2025 demand more than awareness they require readiness. If you’re looking to validate your security posture, find hidden risks, or build a resilient defense strategy, DeepStrike is here to help.

Our expert penetration testing team delivers clear, actionable guidance to protect your business. Check out our penetration testing services to see how we can uncover vulnerabilities before attackers do. Drop us a line we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
External pentesting simulates attacks from outside your network, targeting public facing assets with no inside access a black box test. Internal pentesting simulates an attacker inside your LAN like a disgruntled employee or post breach malware and focuses on privilege escalation and lateral movement. The key difference is where the attacker starts: outside the firewall vs inside it.
Internal testing uncovers vulnerabilities that attackers could exploit once past the perimeter. With insider breaches becoming more common IBM reports 83% of orgs had insider attacks in 2024, it’s critical to know how far a threat can go inside your network. Internal tests can reveal weak credentials, poor segmentation, or overly permissive access that an external test alone would miss.
Most standards require both types at least annually. For example, PCI DSS 11.3 mandates yearly tests of both your external and internal cardholder data environments. It’s also wise to test after any major change, new systems, network redesign or breach. BrightDefense and NIST recommend doing external tests first and then internal tests as soon as possible afterward to complete the assessment.
Typically, an internal test costs more due to its broader scope. Industry surveys find external pentests often range around $5K- $20K, while internal tests are roughly $7K- $35K. Exact prices vary by asset count and depth. External tests have fewer targets public servers only, whereas internal tests might cover dozens of machines, hence higher cost and effort.
Many tools overlap, but focus differs. External testers use network scanners Nmap, vulnerability scanners Nessus/OpenVAS, web proxies Burp Suite, and brute force tools Hydra, Medusa against login pages. Internal testers use those plus specialized tools for internal networks: credential dumpers Mimikatz, AD analyzers BloodHound, CrackMapExec, name server poisoners Responder, and password crackers Hashcat on captured hashes. In both cases, exploit frameworks like Metasploit are handy. Essentially, external tests lean on web/app scanners, internal tests lean on Windows/LDAP and privilege escalation tools.
No. A vulnerability scan automated tool that finds known flaws is only one part of a pentest. Penetration testing goes further: it actively exploits vulnerabilities to demonstrate the actual impact. For example, a scan might flag a missing patch; a pentester will actually attack that vulnerability e.g. remote code exec to prove an entry into the system. In short, scanning shows what could be wrong; penetration testing shows how bad it can get and includes manual techniques, not just tools.
Look for experience and relevant certs. Common credentials include OSCP practical pentesting cert, CEH ethical hacking, CISSP security management, CREST or GIAC GPEN penetration testing. These indicate formal knowledge. The author Mohammed Khalil holds CISSP, OSCP, OSWE, reflecting expertise in network and application hacking. But also ask about hands-on experience: ideally the testers have real engagement experience similar to your environment.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us