June 3, 2025
Updated: June 3, 2025
How healthcare organizations validate real-world security and meet HIPAA Security Rule requirements
Mohammed Khalil

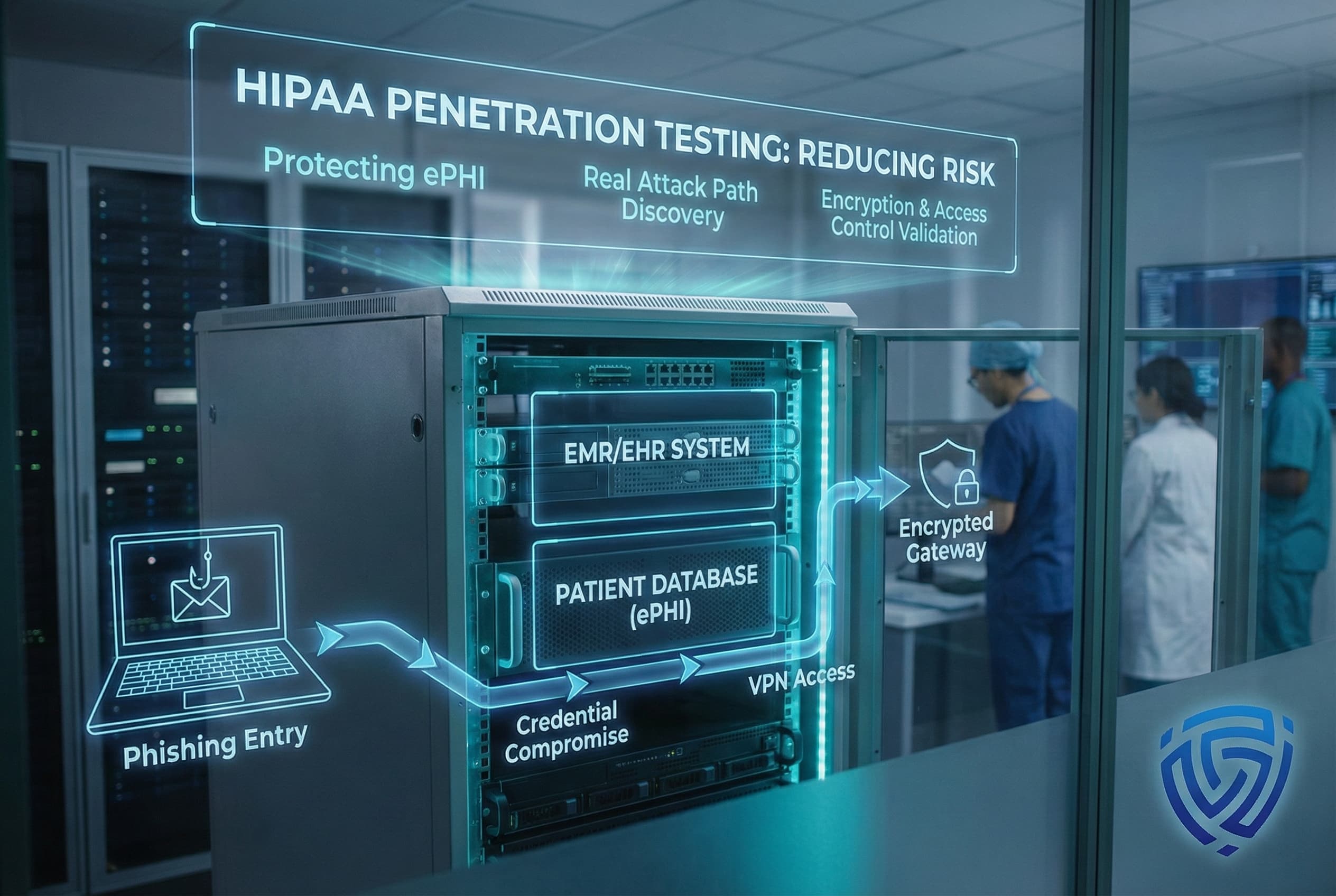
HIPAA penetration testing is a specialized security assessment that simulates cyberattacks against your healthcare systems to identify weaknesses before real attackers do. Covered entities like hospitals, clinics, health plans and their business associates are expected to perform these tests regularly as part of HIPAA’s required risk management. In 2025, this practice has taken on new urgency ransomware and PHI breaches are surging, and regulators are tightening rules to enforce proactive security measures. A HIPAA focused penetration test provides peace of mind that your electronic Protected Health Information ePHI is locked down against current threats and meets evolving compliance standards. It’s not a check the box exercise it actively proves that your safeguards encryption, access controls, etc. work under real attack conditions.

HIPAA penetration testing is a hands-on evaluation of your organization’s security defenses, tailored specifically for healthcare environments. In a HIPAA pen test, experienced ethical hackers attempt to breach the safeguards around your ePHI targeting everything from web applications patient portals, EHR web interfaces and APIs to internal networks, medical devices, and cloud storage where PHI resides. The aim is simple: find any pathway that could lead to unauthorized access or exposure of patient data, so you can fix it.
How is this different from a vulnerability scan? A vulnerability scan is an automated sweep that flags known issues like missing patches or open ports, but it doesn’t tell you if those weaknesses are truly exploitable or dangerous. Penetration testing goes further by actively exploiting vulnerabilities to prove the real world impact. For example, a scanner might report an outdated system, whereas a penetration tester will try to actually break into that system to see if they can extract PHI. This approach provides concrete evidence of which flaws are critical. It’s the difference between checking for unlocked doors versus actually pushing them open.
There’s a common misconception that HIPAA security testing is just a checklist or that a one time compliance scan is enough. In reality, effective HIPAA penetration testing is an ongoing process of rigorous evaluation. It validates that your technical safeguards encryption, access controls, audit logs, etc. work as intended. By simulating how an attacker would navigate your environment, the test can reveal complex logic flaws or misconfigurations that basic audits miss. In short, it’s not about simply having security policies on paper it’s about proving those defenses can withstand an attack.
Pen tests can be performed with varying levels of knowledge about the target black box with no internal info, gray box with limited access, or white box with full knowledge. In healthcare scenarios, a gray box approach is often ideal testers might be given a standard user account or minimal insider knowledge to simulate an insider threat or a compromised employee credential. This way, the testing covers both external attacks and malicious insiders, aligning with real world risks in hospitals and clinics.

Healthcare breaches are increasingly common because patient data is both sensitive and valuable. Cybercriminals know that hospitals and clinics can’t afford downtime, and stolen medical records fetch high prices on the black market. This puts every HIPAA regulated organization in the crosshairs. Below are some of the most pressing threat scenarios facing healthcare today each often tied to gaps in required safeguards:
Each of these threat scenarios maps to one or more HIPAA Security Rule failures whether it’s lack of encryption, poor access control, insufficient audit logs, or lax vendor oversight. Penetration testing directly addresses these issues by actively probing your defenses against such attacks. By understanding how an attacker would target your organization, you can strengthen weak points before a breach happens.

Penetration testing isn’t just about security it’s about compliance. The HIPAA Security Rule’s Administrative Safeguards require ongoing risk analysis and risk management 45 CFR 164.308a1, as well as periodic technical evaluations of security controls. In simple terms, you must regularly assess whether your protections are working. A penetration test provides hard evidence for that assessment. Think of it as the active component of your HIPAA risk analysis: instead of just reviewing policies, you’re actually attacking your own systems in a controlled way to find and fix weaknesses. This is how you satisfy the mandate for an accurate and thorough security evaluation by moving beyond paperwork into real world validation.
The Technical Safeguards 45 CFR 164.312 covering things like access controls, audit logs, integrity checks, and transmission security are also directly supported by penetration testing. For example, HIPAA requires you to implement unique user IDs and emergency access procedures; a pen test will try to bypass those access controls. HIPAA says you should encrypt data; a pen tester might attempt to read or tamper with PHI if they steal some encrypted files or sniff network traffic, checking if your encryption is properly implemented. By testing these controls, you’re effectively doing a quality assurance check on your HIPAA implementations. It’s far better to find out in a controlled test that an admin account has a default password or a database isn’t encrypted than to have an OCR auditor or hacker discover it.
One point of confusion in compliance is the addressable vs required label on certain safeguards. Some organizations mistakenly think addressable means optional it does not. In HIPAA, addressable means you must implement the control or a suitable alternative if it’s reasonable and appropriate to do so. In practice, given today’s threats, there is no alternative that provides the same assurance as a penetration test for evaluating technical defenses. Regulators have made it clear that simply saying we decided not to do it doesn’t fly. In fact, recent HIPAA compliance updates are eliminating the addressable category altogether, effectively making robust security testing a standard requirement. The latest HHS proposal explicitly calls for vulnerability scanning every 6 months and penetration testing at least every 12 months for all covered entities and BAs. While that rule is still pending, it underscores that proactive testing is becoming non negotiable.
Failing to comply has serious consequences. If a breach occurs and investigators find you never tested your systems, you could be cited for neglecting Security Rule safeguards. OCR penalties for willful neglect conscious disregard of compliance obligations can reach into the millions of dollars, not to mention the costs of breach notification and remediation. Even absent fines, a breach means costly downtime, emergency IT repairs, legal liability lawsuits from patients or states, and reputation damage that erodes patient trust. In short, investing in proper security testing now is far cheaper than the fallout from a major security incident or compliance violation later.

We assess the security of all web facing applications that handle PHI from patient portals and electronic health record EHR web apps to telehealth platforms. Using OWASP Top 10 methodologies, our team checks for issues like SQL injection, cross site scripting XSS, CSRF, and authentication flaws. We pay special attention to healthcare specific access controls; for instance, ensuring one patient cannot see another’s records by modifying a URL or ID preventing insecure direct object references. Our approach includes thorough web application security testing for login and session flows to verify that user authentication, session management, and data validation are airtight. The result is a detailed understanding of any web application weaknesses that could expose patient data or allow unauthorized access.
Modern healthcare systems rely on APIs for data exchange whether it’s patient data via FHIR APIs, mobile health app backends, or integrations with third party services pharmacies, labs, billing. We rigorously test these APIs for vulnerabilities such as broken user authentication/authorization, input injection, and excessive data exposure. This means checking that each API request properly enforces permissions so a mobile app user can only access their own records, for example and that sensitive data isn’t leaking through error messages or unsecured endpoints. We also examine the security of integration points and data feeds between your organization and external partners, making sure that API keys, tokens, and data transfer mechanisms are secured and cannot be abused. By hardening your APIs, we help ensure that inter system connectivity doesn’t become an attack pathway.
Our network penetration testing covers both external network entry and internal lateral movement. Externally, we identify open ports and services on your perimeter firewalls, VPNs, remote desktop gateways, etc. and attempt to exploit any weaknesses for example, weak credentials on a VPN, an outdated SSL VPN appliance, or misconfigured cloud firewall rules. Internally, assuming an attacker breaches the perimeter or an insider is present, we simulate how they could move through your network. This involves network scanning and mapping, cracking weak password hashes, attempting Active Directory attacks, and pivoting between hosts and VLANs. We specifically test whether sensitive segments like your EHR servers, research databases, or medical device networks are isolated. If we can jump from a compromised office PC to the clinical network, we’ll document that path. This testing shows exactly how an adversary might traverse your environment and gives you a roadmap to strengthen network segmentation and internal controls.
If your ePHI lives in the cloud whether in AWS/Azure infrastructure or SaaS applications we examine those cloud configurations for security gaps. Our cloud penetration testing checks for things like misconfigured storage buckets e.g., AWS S3 buckets inadvertently left public, improper access control settings, and overly permissive user roles or firewall rules. We also perform cloud security testing focused on identity and access paths, reviewing IAM roles and policies to ensure the principle of least privilege is in effect for instance, that a compromised cloud user account can’t escalate into full admin access. Additionally, we verify that all cloud databases, containers, and backups containing PHI are encrypted and not exposed to the internet. For SaaS platforms such as cloud EHR systems or patient engagement tools, we assess any available security settings and perform tests with permission to validate that data exchanges with these platforms are secure. This component of testing ensures your cloud adoption doesn’t introduce unnoticed risks to patient information.
A key part of our HIPAA aligned approach is testing what happens after an initial breach can a low level account or system compromise be escalated into a full scale takeover? We attempt to escalate privileges on systems we compromise, such as gaining administrator rights on a server or elevating from a local machine to domain admin in Active Directory, by exploiting any configuration mistakes or credential reuse we find. We also test horizontal access controls within applications: for example, ensuring that a receptionist’s login cannot access HR or billing records, and a physician’s account cannot perform admin level actions it shouldn’t. This validates that role based access and separation of duties are effectively enforced. If multi factor authentication MFA is required for certain sensitive actions, we’ll confirm it’s properly implemented and cannot be bypassed. By thoroughly vetting these privilege boundaries, we help you tighten any access loopholes before a malicious actor can discover them.
| Area Tested | What We Validate | Why It Matters for HIPAA |
|---|---|---|
| Web Applications & Portals | Input validation SQL injection, XSS, session management, access control enforcement. | Prevents PHI leaks via patient facing systems; fulfills HIPAA technical safeguard requirements for secure web access. |
| APIs & Integrations | API authentication/authorization, data exposure through APIs, proper rate limiting. | Secures data exchange channels mobile apps, third party integrations so PHI isn’t improperly exposed; supports compliance in inter system data sharing. |
| Network Internal & External | External attack surface open ports, unpatched systems and internal network segmentation. | Ensures perimeter defenses and internal separations protect ePHI repositories; aligns with HIPAA’s need to control system access and prevent common network based attacks. |
| Cloud & SaaS Systems | Cloud storage configurations e.g., S3 bucket access, encryption of data at rest, IAM role permissions. | Verifies cloud hosted PHI is properly safeguarded no public data leaks, strong encryption; addresses HIPAA security requirements as more ePHI moves to cloud services. |
| User Access & Privileges | Role based access controls, potential privilege escalation paths in applications and AD. | Confirms users can only access the minimum necessary PHI and cannot escalate privileges; critical for HIPAA’s access control and user accountability provisions. |

Most healthcare organizations now use a mix of on premises systems and cloud/SaaS services. Our penetration testing approach adapts to each environment’s nuances. Below is a quick comparison:
| Aspect | Cloud & SaaS Environments | On Premises Environments |
|---|---|---|
| Security responsibility | Shared model vendor secures the cloud infrastructure, you secure your data/configuration. Must ensure proper setup of IAM, encryption, monitoring, etc. | Full responsibility on the organization’s IT team to secure servers, networks, and physical access on site. |
| Common risks | Misconfigurations leading to exposed data e.g., public storage buckets, overly broad access roles; compromised API keys or cloud credentials. | Legacy systems and unpatched software; flat internal networks; physical device access or unsecured network ports within facilities. |
| Scaling & maintenance | Highly scalable; cloud provider handles infrastructure uptime and updates. However, configuration mistakes can scale quickly too. | Capacity is limited to in-house hardware; internal team manages all maintenance, upgrades, and patching which can lag if resources are tight. |
| Pen test focus | Emphasis on configuration review and identity checks validating cloud storage settings, API security, and identity/access management controls. Testing often requires coordination with cloud vendors’ policies. | Emphasis on network penetration finding open ports, weak protocols, and exploiting devices/software. Also checks segmentation of internal networks and the security of on site equipment servers, workstations, medical IoT devices. |

The HIPAA Security Rule doesn’t explicitly use the term penetration test, but it does require regular technical security evaluations and thorough risk analysis. In practice, it’s nearly impossible to meet those requirements without doing something like penetration testing. OCR expects covered entities to validate their controls, not just trust paperwork. In fact, proposed updates to HIPAA will mandate annual penetration testing for all covered entities and business associates. So while you won’t find the word pentest in the law today, it’s effectively required through the Security Rule’s evaluation standard and soon it will be required by name. In short, to be safe and compliant, you should be conducting penetration tests.
At least once per year for a full scope test is the widely accepted standard. The latest guidance from HHS via a 2025 NPRM is pushing for a minimum of every 12 months. Many healthcare organizations already test annually; some go further and do major tests twice a year or quarterly on different assets. You should also do an extra test after any big system upgrade or merger/acquisition, and consider smaller targeted tests if new vulnerabilities like a major software bug emerge. Remember, vulnerability scanning automated scans should be more frequent e.g., monthly or quarterly but a deep dive penetration test annually is a must to really probe your security. Always base the frequency on your risk profile: the more sensitive data and the more change in your environment, the more frequently you should test.
No a vulnerability scan alone is not enough. Vulnerability scanning running automated tools that flag known issues is an important practice in addition to penetration testing, not a replacement. HIPAA’s Security Rule requires that you evaluate your security, which implies more than just scanning. Scans might tell you what’s potentially weak; penetration tests show what an attacker can actually do with those weaknesses. OCR has penalized organizations that only did superficial assessments. In proposed rules, HHS calls for both: regular scanning e.g., every 6 months and annual penetration testing. The bottom line: use scans to maintain good cyber hygiene, but use penetration tests to truly validate and challenge your defenses. Both tools together keep you in the best compliance posture.
Everything that handles or protects ePHI. That means all your critical applications and databases that store patient data EHR systems, EMR databases, billing systems, patient portals, etc., as well as the supporting infrastructure. Networks, firewalls, and VPNs that transmit PHI should be tested for holes. Cloud services where you store backups or imaging data need testing for misconfigurations. Even user workstations or medical devices should be in scope if compromising them could lead to PHI exposure. Importantly, include third party systems that have integration with your data if you have a vendor providing a patient portal or a contractor with access to PHI, their systems should be assessed too often this is via contract requirements. Essentially, if a system is part of your ePHI ecosystem, it should be periodically tested. A good penetration test plan will map out all these components so nothing is overlooked.
It produces the evidence you need to show auditors or regulators that you’re on top of security. A penetration testing report, plus the documentation of how you fixed the findings, demonstrates compliance with the Security Rule’s mandate to identify and mitigate risks. During an OCR audit or investigation, you can present the reports as proof that you performed due diligence you didn’t just rely on policies, you actively checked your systems. This can be the difference between a finding of compliance versus non compliance. For example, if a breach occurs but you can show that you had recent pen test reports and remediation action plans, it indicates you were making reasonable and appropriate efforts, which may reduce regulatory penalties. In short, pen testing is like an internal audit of your technical controls; it prepares you for the real audit by finding issues first so you can address them.
It depends on the scope and complexity. For a mid sized healthcare organization, the average price of a penetration testing engagement might be in the range of $15,000–$30,000. Smaller engagements say, testing a specific web app or a small clinic’s network could be less, perhaps under $10k. Larger health systems or those needing a comprehensive, multi month assessment might invest $50k or more. Factors that influence cost include the number of IP addresses/apps in scope, whether both internal and external networks are tested, and if specialized areas like medical device/IoT testing are included. While this is not a trivial expense, consider the ROI: a single breach can cost millions in fines and response costs. Many organizations find that regular penetration testing pays for itself by preventing incidents. Also, having pen test results can sometimes favorably impact cyber insurance premiums or contracting it shows you take security seriously. Always obtain a tailored quote, but be wary of too cheap offers; quality testing by experienced professionals is worth the investment.
Look for a provider with healthcare security expertise and solid credentials. Key things to consider: First, they must sign a BAA any reputable vendor will do this to handle PHI during testing. Second, check their certifications and methodologies e.g., are their testers OSCP, CISSP, or have similar certifications? Do they follow NIST SP 800 115 or OWASP testing standards?. Third, ask for a sample report or report template. A quality penetration testing report should map findings to HIPAA or NIST controls, provide clear risk ratings, and include remediation guidance this shows the vendor understands compliance reporting. Also, consider their experience: vendors who can cite healthcare clients or case studies even anonymously are preferable, as they’ll know about things like medical device sensitivities or HL7/FHIR nuances. You might also inquire about any HIPAA specific training or certification their team has for instance, some may have HITRUST assessors or similar on staff. Lastly, evaluate communication and flexibility a good firm will work with you to define scope correctly and accommodate your operational needs like testing in off hours for patient safety. In summary, choose a firm that is technically strong and understands the regulatory context.

HIPAA penetration testing is no longer optional it’s a fundamental practice to ensure ePHI stays secure against aggressive cyber threats. By rigorously evaluating your systems through the eyes of an attacker, you gain invaluable insights into your true security posture and compliance readiness. The result is not just ticking a box for HIPAA, but actually reducing the risk of breaches and service outages in your healthcare organization. DeepStrike’s team of offensive security professionals stands ready to help you identify and remediate vulnerabilities before they can be exploited, fortifying both your HIPAA compliance and your patient trust.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike Specializing in advanced penetration testing and offensive security operations, he holds certifications including CISSP, OSCP, and OSWE. Mohammed has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us