July 29, 2025
Updated: July 29, 2025
A complete guide to ethical hacking services, types of tests, compliance benefits, and how to choose the right provider.
Mohammed Khalil

Penetration testing services, often called "pen testing" or "ethical hacking," are a professional security assessment where cybersecurity experts simulate a real world attack on your organization's digital assets. The goal is to proactively find and exploit vulnerabilities in your computer systems, networks, and applications to see how your defenses hold up.
Think of it like a bank hiring a professional to try and break into their vault. If the "burglar" succeeds, the bank gains invaluable, firsthand knowledge on how to tighten its security before a real criminal tries the same thing. A pen test answers one critical question: "If a skilled attacker targeted us, could they get in, and how bad would the damage be?"
In 2025, this proactive approach is more critical than ever. The threat landscape is relentless, and the financial stakes are staggering. According to IBM's latest research, the average cost of a data breach has climbed to a record $4.88 million. The 2025 Verizon Data Breach Investigations Report (DBIR) further highlights the urgency, revealing that
stolen credentials (22%) and the exploitation of known vulnerabilities (20%) remain two of the primary ways attackers get in exactly the gaps a pen test is designed to uncover.
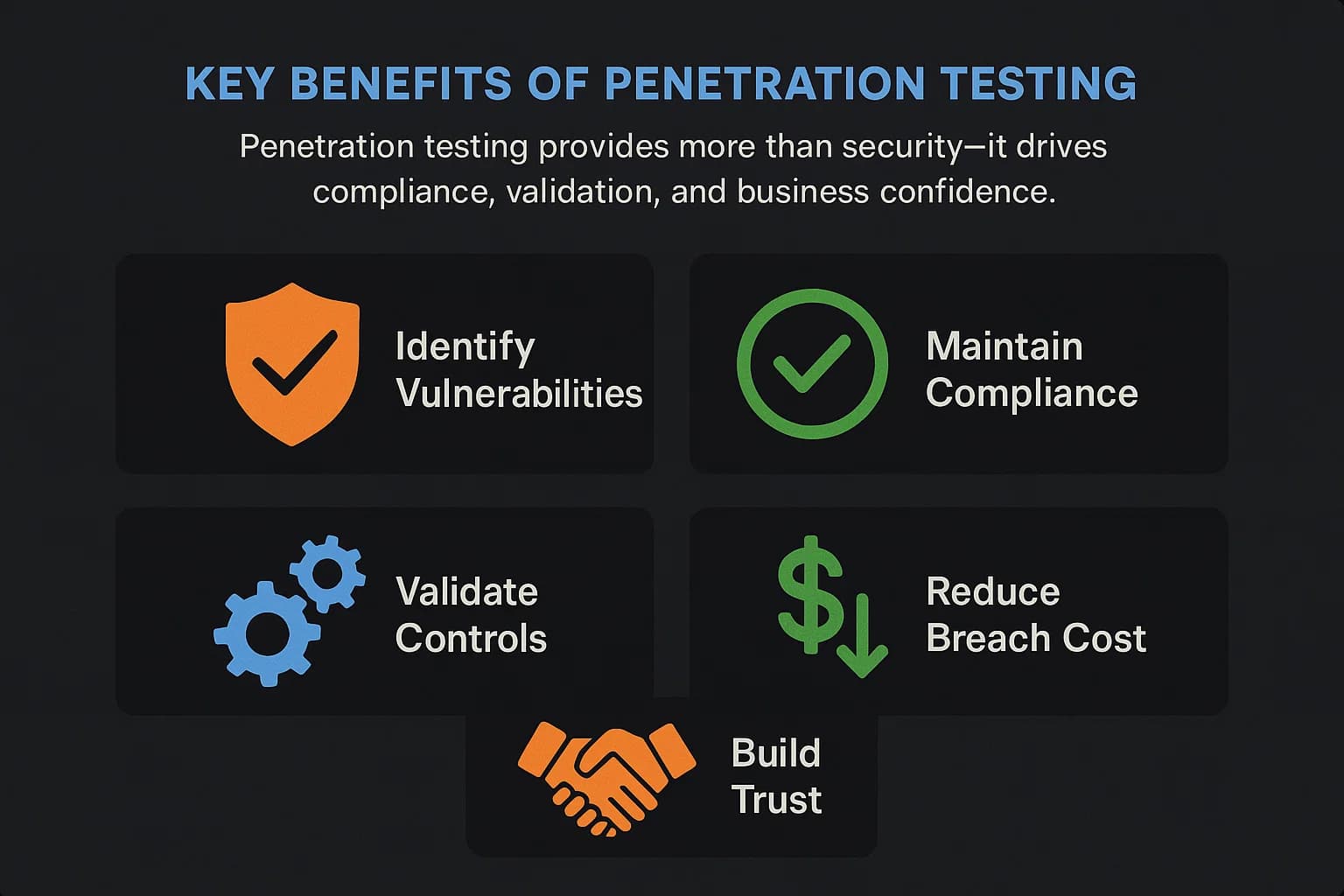
Beyond just finding flaws, penetration testing delivers tangible business value by turning abstract risks into a clear case for action. It's a crucial practice for any organization serious about security.
Here are the key benefits of conducting regular pen tests:
Identify and Fix Vulnerabilities Proactively: The primary goal is to find weaknesses before malicious actors do. A pen test goes beyond automated scans to uncover complex logic flaws, misconfigurations, and chained exploits that could lead to a major breach.
Meet and Maintain Compliance: Many regulatory frameworks mandate penetration testing. Standards like PCI DSS (for payment card data), HIPAA (for healthcare), SOC 2, and FedRAMP all require regular, independent security testing to ensure sensitive data is protected. For a full breakdown of how each compliance framework addresses penetration testing including PCI DSS, HIPAA, SOC 2, and ISO 27001 our comprehensive guide to penetration testing for compliance. A pen test provides the necessary evidence that you're meeting these obligations.
Validate Your Security Investments: You've invested in firewalls, endpoint detection, and other security tools. But are they configured correctly? A pen test is one of the few ways to empirically validate that your security controls are working as intended. It answers the CISO's crucial question: "Are we getting a return on our security spending?"
Reduce the Financial Risk of Breaches: By proactively identifying and remediating vulnerabilities, you significantly lower the likelihood of a successful attack, helping you avoid the catastrophic costs associated with data recovery, regulatory fines, legal fees, and reputational damage.
In modern DevOps environments, security can no longer be an afterthought. As code moves quickly from development to production, vulnerabilities can slip through undetected unless security is embedded directly into the CI/CD pipeline. That’s where DevSecOps pentesting comes in. Learn how to embed pentests into your software delivery lifecycle in our guide to penetration testing for DevOps, which maps modern testing workflows to OWASP and NIST 800-204D standards.
In fact, many insurers now require proof of regular pen testing to issue or renew cyber insurance policies. See how penetration testing strengthens your eligibility and lowers cyber insurance premiums.
Build Trust with Customers and Investors: A clean penetration test report is a powerful trust signal. It demonstrates to clients, partners, and investors that you take cybersecurity seriously and have taken proactive steps to protect their data, which is especially critical for startups and small businesses.
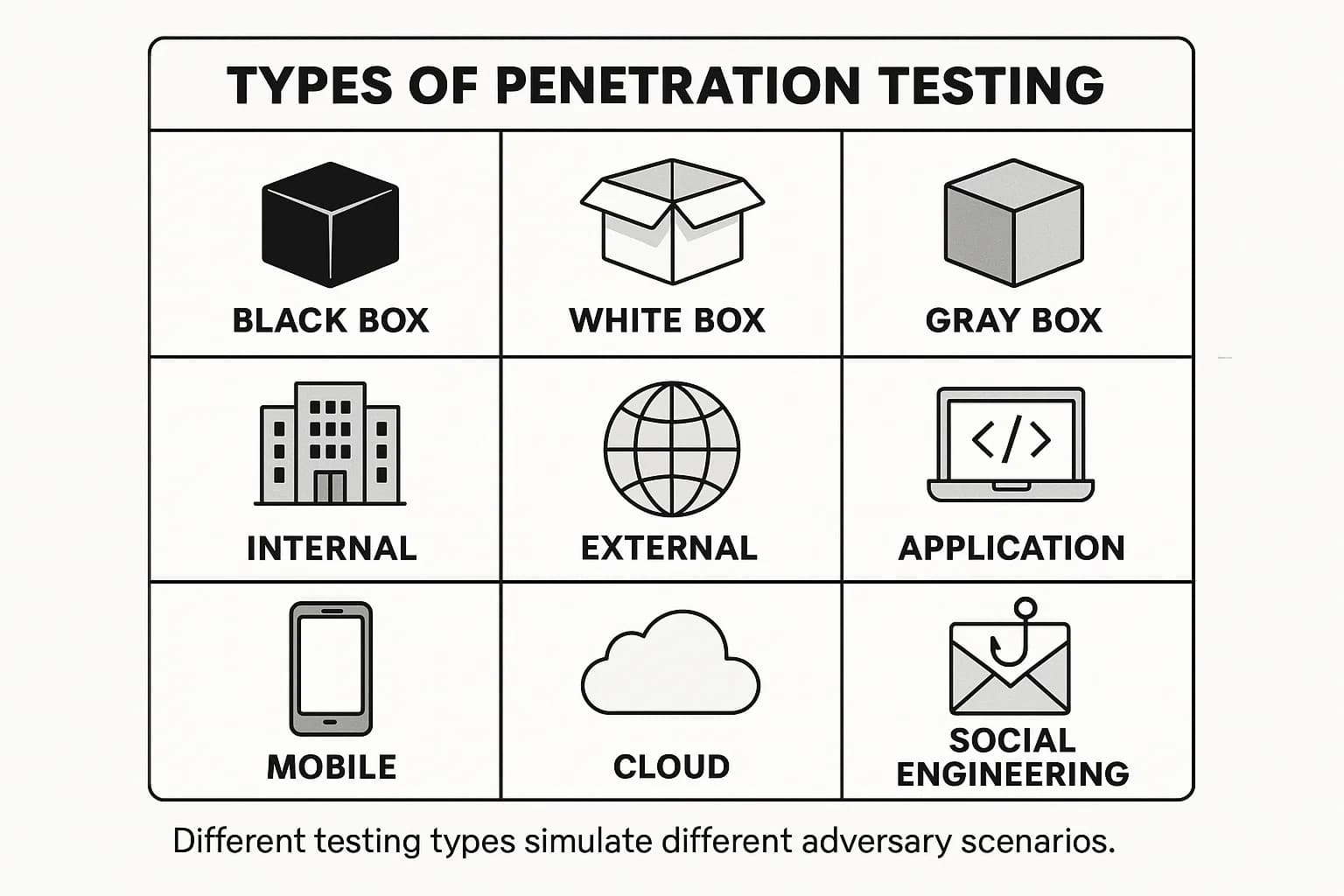
Penetration testing isn't a one size fits all service. The right type of test depends on your goals, the assets you need to protect, and the threat scenarios you're most concerned about.
This classification refers to how much information the ethical hacker is given before the test begins.
Black Box Testing: The tester is given almost no information, often just the company's name. This approach best simulates an attack from an external adversary with no prior knowledge of your systems and is excellent for testing your perimeter defenses.
White Box Testing: The tester is provided with full details about the target environment, including source code, network diagrams, and credentials. This "full knowledge" approach allows for a much deeper and more efficient audit, uncovering vulnerabilities that might be missed in other tests.
Gray Box Testing: A hybrid approach where the tester has limited knowledge, such as the login credentials for a standard user. This is perfect for simulating threats from an insider or an attacker who has already compromised a user account.
Want a deeper dive into how Black Box, White Box, and Gray Box testing compare in real world scenarios? Check out our full guide on Black Box vs White Box Testing to explore their pros, cons, and how to choose the right approach for your security goals.
This distinction is based on where the simulated attack originates.
External Penetration Testing: This test focuses on your internet facing assets like websites, firewalls, and servers to see if an attacker from the outside can breach your perimeter. It answers the question, "Is our front door locked?"
Internal Penetration Testing: This test assumes an attacker has already gained a foothold inside your network, perhaps via a phishing attack or as a malicious insider. The goal is to see how far they can move and what data they can access. It answers, "If someone gets past the front door, can we stop them?" For a deeper look, see our guide on internal vs external penetration testing.
As technology evolves, so do the types of tests needed to secure it.
Web Application & API Penetration Testing: This is one of the most common tests, focusing on vulnerabilities in web apps and APIs. Testers look for flaws outlined in the OWASP Top 10, such as Injection, Broken Access Control, and real life scenarios of SSRF attacks. With the rise of AI, forward thinking tests now also cover the
OWASP Top 10 for Large Language Models (LLMs), addressing new risks like Prompt Injection. Explore our dedicated web application pentest services for more.
Mobile Application Penetration Testing: This assesses the security of iOS and Android apps and their backend APIs, looking for issues like insecure data storage or flawed communication channels. Learn more about our mobile application pentest services.
Cloud Security Penetration Testing: With 82% of breaches now involving data stored in the cloud, testing these environments is critical. This test focuses on misconfigurations in AWS, Azure, and GCP, insecure APIs, and identity and access management flaws.
Social Engineering: This test targets your people. Testers use techniques like phishing and vishing (voice phishing) to assess how well employees resist manipulation and adhere to security policies.
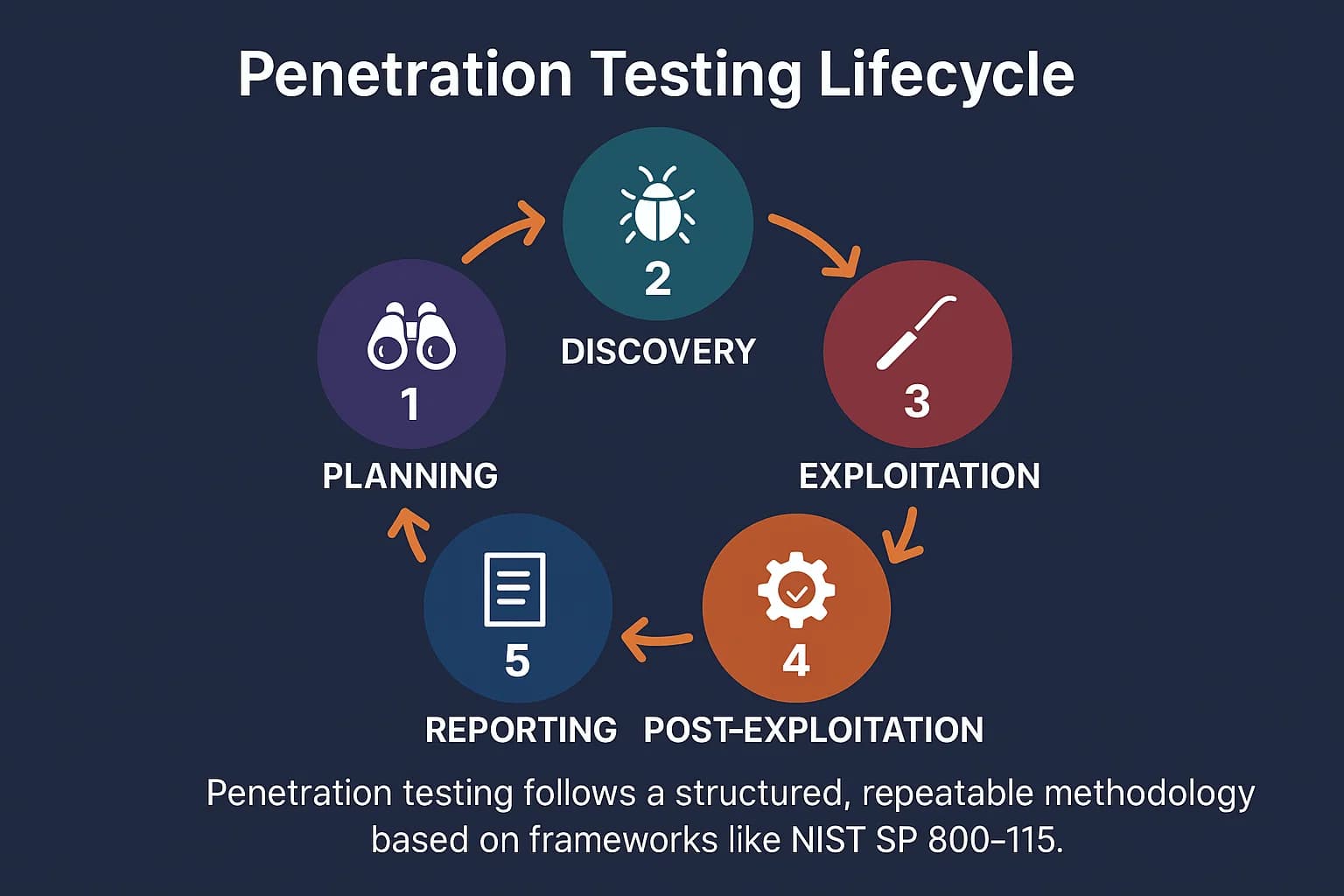
A professional penetration test is not a chaotic free for all. It's a methodical process that follows a structured methodology to ensure comprehensive and repeatable results. Most professional firms follow structured frameworks like the NIST SP 800-115, ensuring tests are repeatable, evidence-based, and auditable. For a full breakdown of the industry’s most trusted approaches like PTES, NIST, OWASP WSTG, and more see our complete penetration testing methodology guide.
Step 1: Planning and Reconnaissance This foundational phase sets the rules for the engagement. The testing team works with you to define the scope (what's being tested), objectives, and communication protocols. Legal authorizations are signed, and testers begin passive reconnaissance, gathering publicly available information to understand your digital footprint without actively touching your systems.
Step 2: Discovery and Scanning Here, testers begin actively probing the target environment. They use tools like Nmap to discover live hosts and open ports and vulnerability scanners like Nessus to identify services and potential weaknesses. This phase maps out the theoretical attack surface based on known vulnerabilities.
Step 3: Exploitation (The Attack) This is where ethical hacking happens. Testers take the potential vulnerabilities from the discovery phase and manually attempt to exploit them to gain unauthorized access. This creative process relies on the tester's expertise, using frameworks like
Metasploit to launch exploits or tools like Burp Suite to manipulate web application requests and uncover flaws like broken access controls.
Step 4: Post Exploitation and Analysis Gaining initial access is just the start. Once inside, the tester attempts to determine the full potential impact of the breach. This involves escalating privileges (e.g., from a standard user to an administrator), moving laterally across the network, and identifying sensitive data to demonstrate tangible business risk.
Step 5: Reporting and Remediation The final and most important deliverable is the report. A good report is clear, concise, and actionable. It details every vulnerability found, provides step by step instructions to reproduce the exploit, and offers concrete, prioritized recommendations for remediation. This report becomes your blueprint for strengthening your defenses.
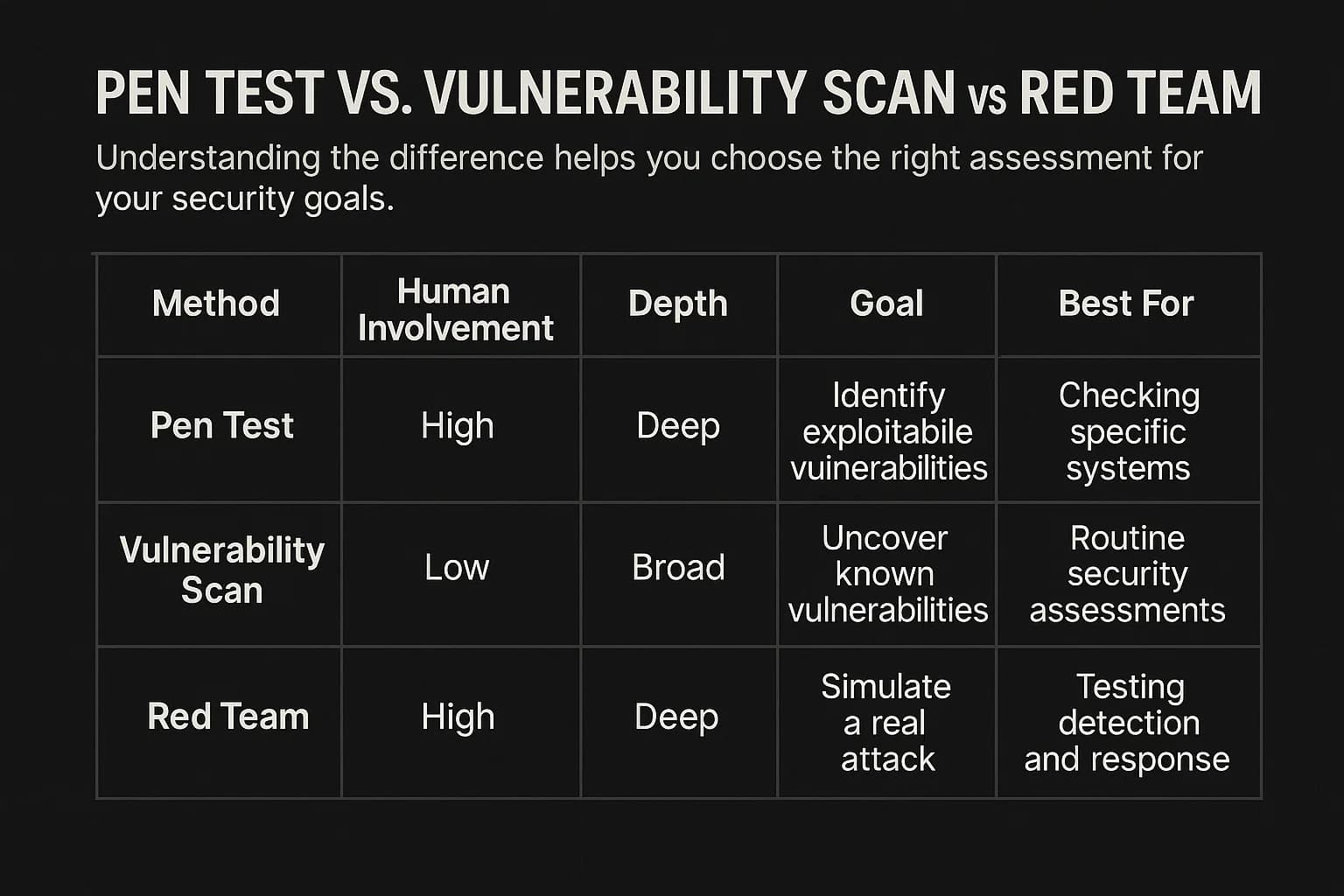
These terms are often used interchangeably, but they describe distinct services with different goals. Choosing the right one depends on your security maturity.
A vulnerability scan is an automated, high level test that checks systems against a database of known vulnerabilities. It's fast and great for regular health checks, but it's passive; it reports potential issues without confirming if they're exploitable, often leading to false positives. It answers:
What potential weaknesses might we have?
A penetration test is a manual, hands on examination by a human expert. The tester actively tries to exploit the vulnerabilities a scan might find. This human element is key, as it uncovers complex logic flaws and chained exploits that automated tools miss. It answers:
Can an attacker actually break in, and what could they do? For a deeper dive, read our analysis of vulnerability assessment vs penetration testing.

A penetration test is typically scope bound and aims to find as many vulnerabilities as possible within a specific area and timeframe. The defensive team (blue team) is usually aware of the test.
A red team engagement is a broader, more adversarial simulation. The goal is to test an organization's detection and response capabilities against a persistent, stealthy attacker with a specific objective (e.g., "exfiltrate customer data"). It's a true test of your people, processes, and technology. It answers:
Can our security team detect and stop a sophisticated, real world attack? Learn more about this dynamic in our guide to red team vs blue team.
Still deciding whether a traditional penetration test or a bug bounty program is the right fit for your organization? Explore our detailed comparison of penetration testing vs bug bounty programs to evaluate the pros, cons, and use cases for each.

Selecting the right partner is critical to the success of your penetration test. Here’s what to look for:
Experience and Expertise: Does the team have a proven track record? Look for providers whose testers hold respected certifications like Offensive Security Certified Professional (OSCP), Certified Ethical Hacker (CEH), or GIAC Penetration Tester (GPEN).
Methodology: Do they follow a recognized methodology like NIST SP 800 115 or the Penetration Testing Execution Standard (PTES)? A structured approach ensures comprehensive and repeatable testing.
Manual vs Automated Testing: A quality pen test is not just an automated scan. Ensure the provider emphasizes manual testing, where human experts use their creativity to find flaws that tools can't. check out our in depth guide on manual vs automated penetration testing.
Clear Reporting: Ask for a sample report. The report should be easy for both executives and technical teams to understand, with clear risk ratings and actionable, prioritized remediation guidance.
Post Test Support: Does the provider offer support after the report is delivered? A good partner will be available to answer questions and often includes re testing to verify that your fixes were successful.
1. How much does penetration testing cost?
The cost of a penetration test typically ranges from $5,000 to over $40,000. The final price depends on the scope and complexity of the target, the methodology used, and the experience of the testing team. Be wary of any service priced below $4,000, as it may just be a repackaged vulnerability scan.
2. How often should you conduct a penetration test?
The industry standard is to conduct a pen test at least annually and after any significant changes to your environment, like a major application update or cloud migration. For a more modern approach, consider continuous penetration testing to provide ongoing assurance.
3. What's the difference between internal and external penetration testing?
An external test simulates an attack from the internet, targeting your public facing systems. An internal test simulates an attack from inside your network, assuming the attacker has already gained initial access. Both are crucial for a complete security assessment.
4. What tools do penetration testers use?
Testers use a wide array of tools, including Burp Suite for web application testing, the Metasploit Framework for exploitation, Nessus for vulnerability scanning, and Nmap for network discovery. However, the most important "tool" is the tester's own expertise and adversarial mindset.
5. How do I become a penetration tester?
Penetration testing is not an entry level role. It requires a strong foundation in IT, networking, and systems administration. Aspiring testers often start in roles like network engineering or software development before specializing in security and pursuing certifications like the CompTIA PenTest+ or the highly respected OSCP.
6. How much does penetration testing cost?
The cost of a penetration test typically ranges from $5,000 to over $40,000. The final price depends on the scope and complexity of the target, the methodology used, and the experience of the testing team. Be wary of any service priced below $4,000, as it may just be a repackaged vulnerability scan.
For a detailed breakdown of pricing models, influencing factors, and real-world benchmarks, check out our full guide on penetration testing cost.
In the complex cybersecurity landscape of 2025, hope is not a strategy. Penetration testing has proven itself to be an essential, human driven security practice that provides clarity in a world of ever evolving threats. It moves beyond the theoretical checklists of automated scanners to answer the most practical and pressing questions about your security: Are we vulnerable? How vulnerable? And what is the real world risk to our business?
By simulating the actions of a determined adversary, penetration testing validates your security controls, helps you achieve and maintain compliance, and provides a clear, actionable roadmap for hardening your defenses. In an era where a single breach can have devastating financial and reputational consequences, proactively identifying and fixing your weaknesses before an attacker does is one of the most valuable investments you can make.

Security questions don’t wait. Neither should you. Whether you're evaluating penetration testing services, need help with a red team assessment, or just want to see what DeepStrike can uncover, Reach out. We’re always happy to dive in.
About the Author
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us