October 29, 2025
Updated: October 29, 2025
ISO 27001 doesn’t explicitly require penetration testing but in 2025, it’s the strongest proof that your controls truly work. Learn how to align pen tests with Annex A and your ISMS.
Mohammed Khalil


Penetration testing is the practice of simulating cyberattacks to find and fix security gaps. In the context of ISO/IEC 27001, it means aligning those tests with the standard’s requirements. While ISO 27001 never says you must do a pen test, best practice and auditors expect organizations to verify controls under attack scenarios. In 2025’s threat landscape with more cloud apps, remote work, and automated hacking pen tests for ISO 27001 compliance are more important than ever. They turn theoretical risk assessments into concrete findings and proof of control effectiveness.
If you’re wondering what does a penetration test have to do with ISO 27001?, the short answer is: everything. Pen testing feeds evidence into the ISMS Information Security Management System. Test results identify the precise threats that matter, so your risk treatment plans can focus on real weaknesses. In practice, firms rely on specialized penetration testing services or Penetration Testing as a Service PTaaS to run these in depth assessments. The result is stronger controls and an audit trail showing you’re on top of vulnerabilities.

ISO 27001 is an international standard for managing information security risk. It requires organizations to assess risks to their data and implement controls in Annex A to mitigate them. Penetration testing is a hands-on way to verify those controls. In simple terms, a pen test tries to break into your systems networks, servers, applications the way a real attacker would. It uses tools and creative hacking techniques under safe conditions.
Unlike a purely automated vulnerability scan, a penetration test involves skilled testers exploring every angle. They might brute force passwords, exploit software bugs, try SQL injection on web apps, or trick users with phishing. A well run pentest goes beyond the checklists of scanners and uncovers hidden flaws. In ISO 27001 terms, penetration testing helps organizations identify vulnerabilities and assess the effectiveness of their security controls. For example, Annex A.12.6.1 Technical Vulnerability Management says you must obtain information about technical vulnerabilities, evaluate exposure, and take measures to address risk. A pentest directly supports this, it simulates attacks to find unpatched software, misconfigurations, or coding errors before cybercriminals do.
In short, ISO 27001 pen testing means planning and executing security tests specifically designed around your ISMS scope. You typically define the scope based on critical assets, internet facing apps, internal networks, cloud infrastructure, etc., then choose a testing approach black box, gray box, or white box. The findings are documented in a report that ties back to ISO 27001 controls and your risk registry. All of this becomes part of the ISMS documentation, demonstrating compliance and driving improvements.

Today’s cyber threat climate makes pen testing more than a nice to have. Ransomware, data theft, and supply chain attacks have skyrocketed. Breaches cost companies millions and wreck reputations. Regulators and customers demand proof that you’re on the ball. Penetration testing provides that proof. According to NIST guidance, an effective security program should include both frequent vulnerability scans and periodic penetration tests. Pen tests are high impact: they use real exploits and expose the level of damage attackers could do.
In 2025, ISO 27001 auditors and cyber insurers expect organizations to do robust testing. For example, technical compliance reviews Control A.18.2.3 imply that systems must be regularly evaluated against policy. Demonstrating that you run annual or more frequent pen tests shows auditors that you take vulnerabilities seriously. It is often listed explicitly in cyber insurance questionnaires and questionnaires against frameworks like SOC 2 or PCI DSS. DeepStrike’s experience shows that engaging in pen testing builds trust: executives see that security isn’t theoretical, but actively tested. It also often reveals high priority fixes that risk assessments alone might miss.
Real world example: A finance firm needed ISO 27001 certification. They added regular penetration testing into their ISMS schedule. Each test uncovered issues old server patches, weak passwords in development tools. Remediating those not only improved security but satisfied the auditor’s requirements for risk treatment evidence. The testers’ reports showed exactly which Annex A controls were impacted by each vulnerability e.g. A.12.6.1 for an SQL injection bug in a web app. This mapping made it clear that pen testing isn’t extra fluff, it's concrete risk management.
Penetration testing is an essential component of any ISO 27001 ISMS, from initial development through to ongoing maintenance and continual improvement, notes an industry guide. In practice, that means running tests at key points after major system changes, before certification audits, and regularly in between. The data from pen tests is fed back into the ISMS’s risk assessment process: vulnerabilities form a key input to your risk assessment, updating likelihood and impact estimates. As ISO 27001 itself emphasizes, this closes the loop: new flaws get fixed and controls are refined, driving continual improvement.
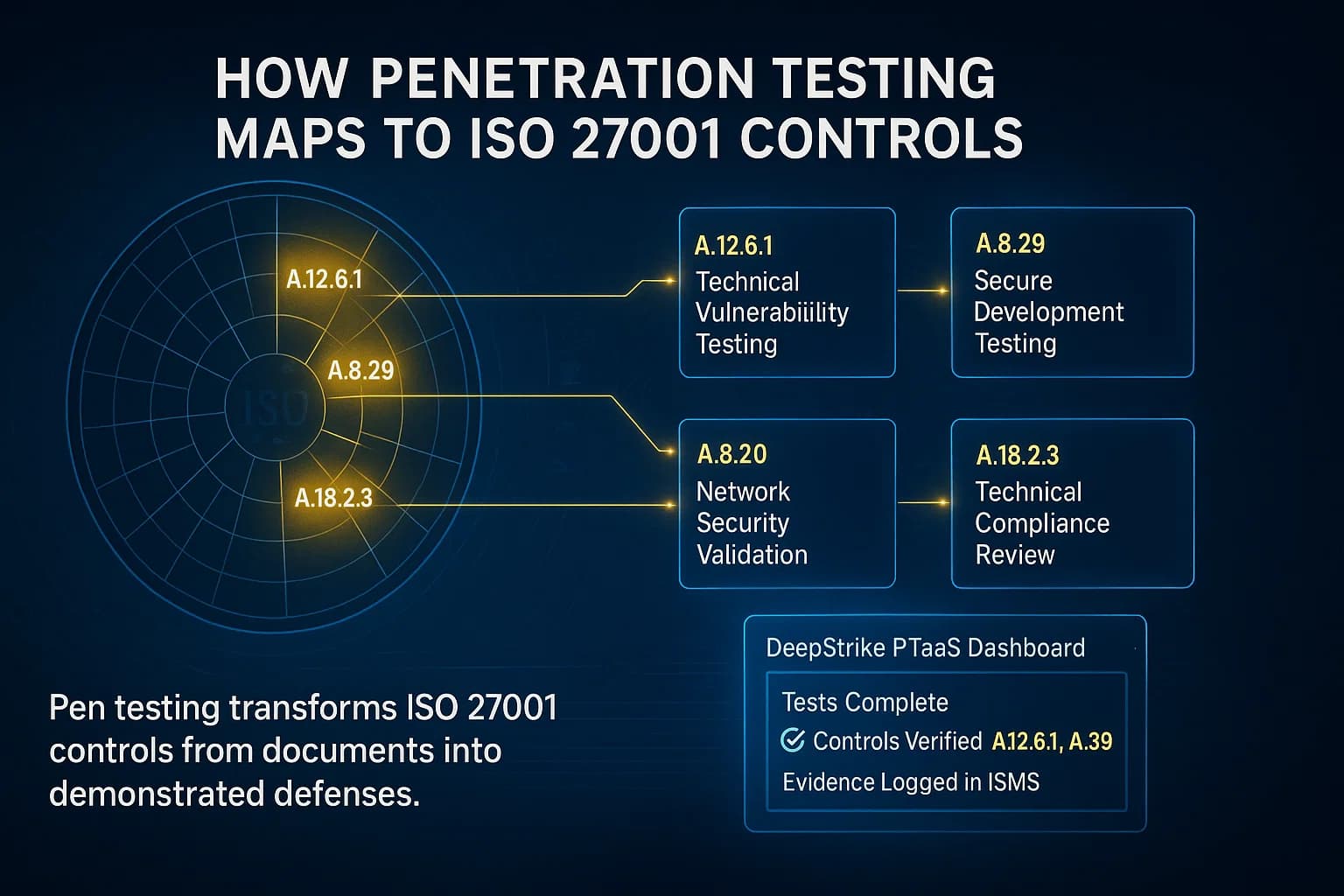
Several specific ISO 27001 controls implicitly call for or benefit from pen testing. Here are a few highlights:
By aligning your testing program to these controls, you cover audit expectations. In fact, industry experts note that a properly scoped pentest satisfies both A.12.6.1 and A.8.29, providing a way to demonstrate adherence to compliance with technical vulnerability management. In other words, you’re not just finding bugs you’re generating the evidence ISO auditors want to see.

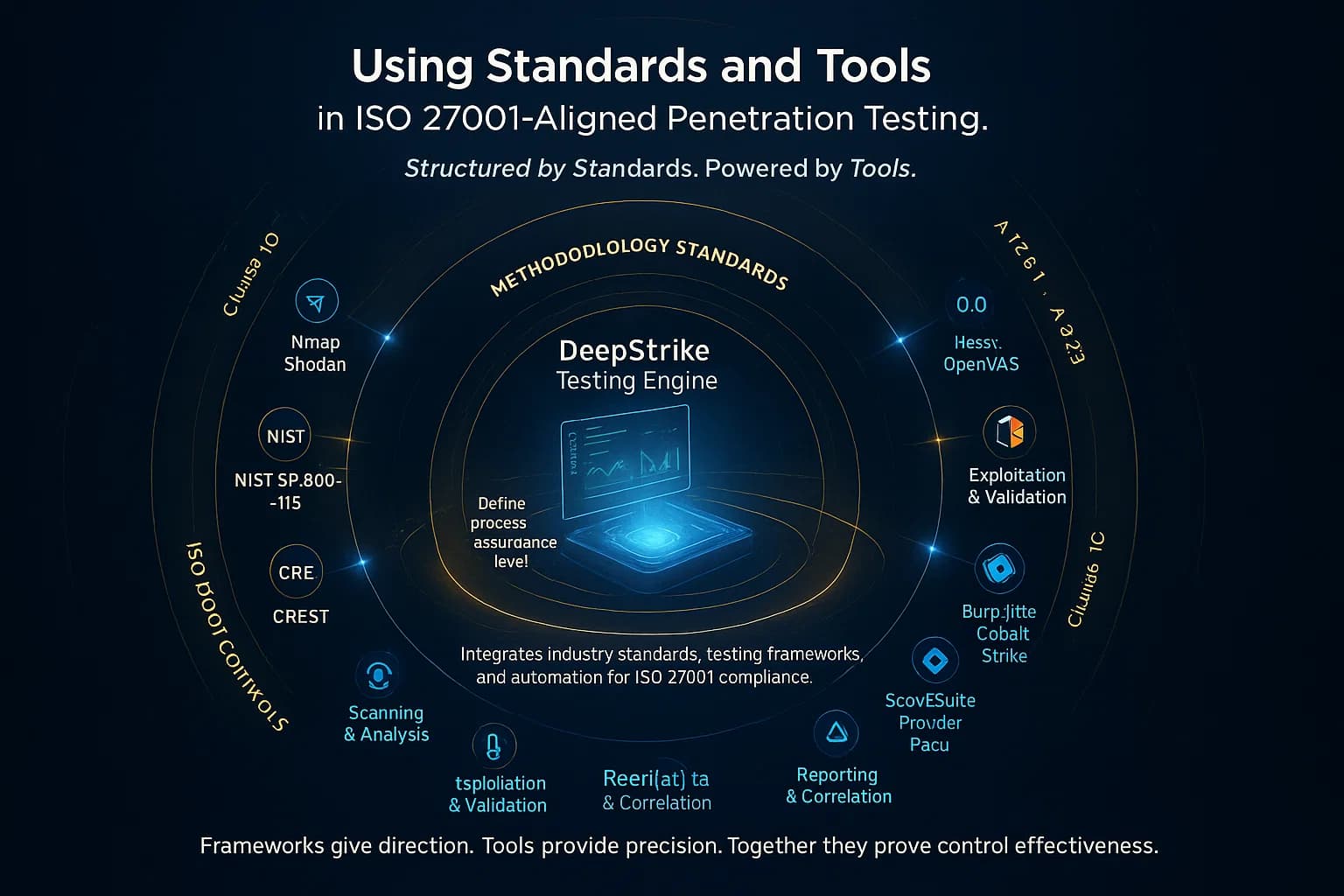
A structured methodology keeps ISO 27001 style pen testing organized and repeatable. Here’s a typical approach:
Scope defined, rules of engagement set, assets listed, methods black/gray/white chosen, schedule and backup plan agreed. Test external, internal, apps, etc. Document all findings with ISO references. Assign fixes, retest, and update ISMS documentation.
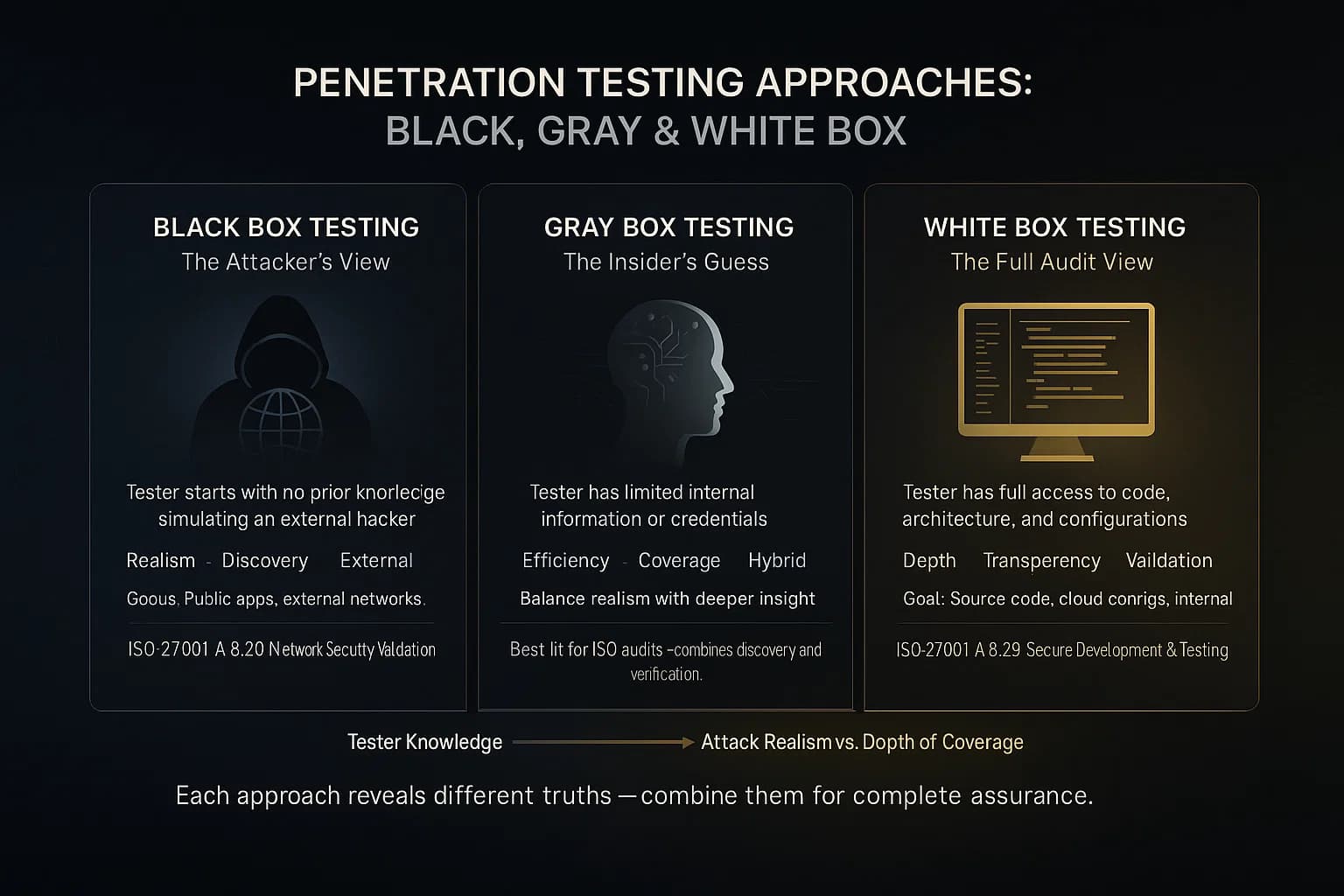
There are several testing styles, each providing a different view of your security:
For ISO 27001 compliance, Gray Box is frequently preferred. It effectively tests controls both from the outside and just inside the firewall. In our experience, clients get the best results when test teams know where to look e.g. which subnet or server to start with but still have to do significant digging.
In practice, you will do a mix: initial external black box, then interior gray/white, plus special checks e.g. source code review for A.8.29. The test report should clearly state the approach used so that management knows what was simulated.
Organizations sometimes wonder if an automated scan can replace a pentest. It cannot, but both have roles. Here’s a quick comparison:
| Aspect | Vulnerability Assessment | Penetration Testing |
|---|---|---|
| Purpose | Quickly identifies known vulnerabilities CVE based across many hosts. | Actively exploits vulnerabilities known and unknown to assess risk impact. |
| Method | Automated tools Nessus, Qualys, etc. that produce a list of issues. | Human driven plus tools; includes social and business logic exploits. |
| Depth | Surface level, may flag potential issues e.g. open port. | Deep dive, confirming true exploitability. Finds complex chains e.g. pivoting. |
| Output | Scanner report with severity. | Detailed attack narrative, evidence, and business impact. |
| ISO 27001 Context | Not mandated but recommended as ongoing maintenance supports A.12.6.1. | Highly recommended; directly aligns with ISO controls and audit evidence. |
| Frequency | Can be run weekly/monthly in live systems low risk. | Typically done annually or after major changes, higher impact. |
Vulnerability scanning is easier and cheaper, so organizations do it regularly. ISO 27001 doesn’t require it specifically just like pentesting, it’s a choice, but the standard’s spirit of risk management encourages using all tools. Often a scanning run happens monthly or quarterly to keep things tidy, while a penetration test is scheduled for when you need a thorough check e.g. before audits.
scanning tells you this port is open or this patch is missing, but it won’t prove an attacker can exploit those holes. Penetration testing takes the next step to exploit and validate the risk. Both together give you a strong defense: automatic tests catch drifting config issues, and periodic pen tests ensure nothing slips through unchecked.
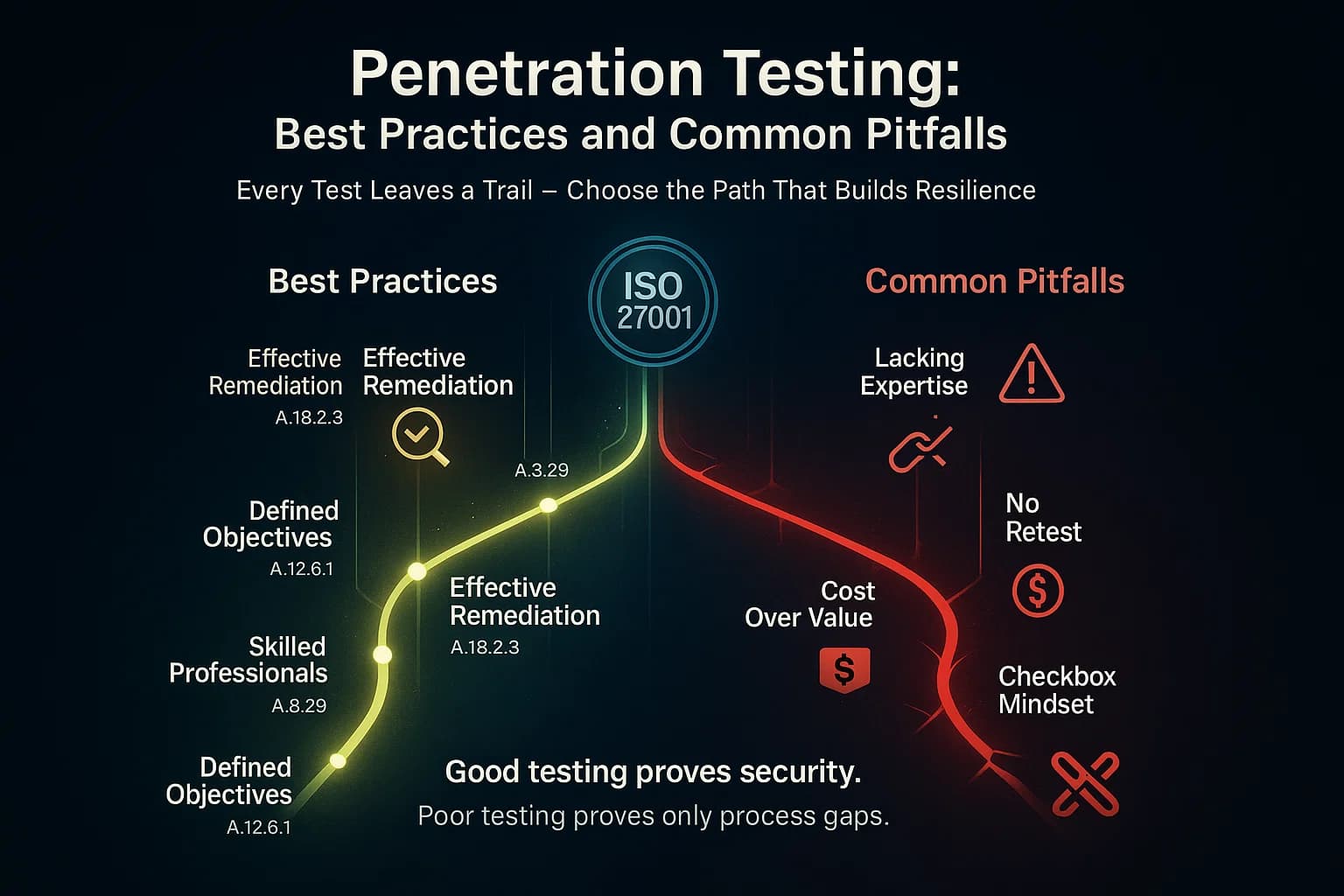
Common mistake: thinking that penetration testing alone is enough. It’s one part of the larger ISMS. Results must feed into your risk register, training programs e.g. if social engineering succeeds, and patch management.
To maximize effectiveness, follow industry best practices:
In 2025 and beyond, ISO 27001 compliance means proving your security works in practice not just on paper. Penetration testing is a vital way to validate controls, uncover hidden risks, and continuously improve your ISMS. While not a strict must have per the letter of ISO 27001, it’s widely seen as mandatory in spirit. A well run pentesting program ties directly into ISO risk management: testers reveal the real world threats that inform your risk register, and retesting ensures fixes actually hold.
Ready to Strengthen Your Defenses? The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.

Explore our penetration testing services to see how we can uncover vulnerabilities before attackers do. Drop us a line we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
No ISO 27001 clause explicitly mandates a penetration test, but several controls imply it. For example, control A.12.6.1 requires identifying and fixing technical vulnerabilities in a timely way. In practice, auditors expect evidence of vulnerability testing. So while you could rely on code reviews and scans alone, most organizations choose penetration testing to meet those intent based requirements.
ISO 27001’s cycle and Annex A don’t prescribe exact frequency. However, best practice is at least annually, and whenever major changes occur. NIST suggests that annual pentests may suffice given their high cost and impact, but supplement that with regular vulnerability scans. If you add or upgrade systems, a targeted retest is wise. Common practice: do full internal+external tests yearly, plus smaller scans quarterly.
Scope is agreed case by case, but generally it covers in scope assets per your ISMS. For example, internet facing apps, key servers, and critical cloud services are always included. The goal is to hit everything that could affect the core of your ISMS. Scope should exclude out of bounds systems like partner networks you don’t own and consider environments testing on a staging copy vs live. Defining scope well ensures testing time is used where it matters most.
No, scanning does not replace pen testing. A scan automates checks and finds known issues, but a pen test actively exploits issues to show real risk. For ISO 27001 compliance, audits usually expect testing that proves controls are effective. Scanners help keep the ship tight, but pen tests validate it under attack. In our strategy, we use scans continuously and schedule pentests periodically to cover both needs.
Include the testing plan, rules of engagement, and the final report in your ISMS documents. The report should explicitly connect findings to ISO clauses or risk treatments. Auditors want to see that you planned the test, conducted it under controls, and acted on every finding. Checklists used, tester qualifications, and remediation records can all live in your compliance folder.
External tests simulate attacks from outside your network internet threats. They focus on firewalls, DMZ, web apps, remote access points. Internal tests simulate an attacker who has breached the perimeter or is an insider. These focus on LAN devices, internal apps, privilege escalation, and insider threats. Both types are important; ISO 27001’s risk assessment should guide where you need each. Internal tests, for example, can uncover exposure from things like employee workstation compromise.
Costs vary widely by scope. As a ballpark, a basic external network test might start around $6,000 for a few days of work, while a full multi vector test networks, web apps, etc. could reach $20,000 or more. Factors include asset count, test depth, and tester expertise. Importantly, very cheap offers few thousand dollars often only run automated scans, which we advise against. Consider it an investment: the cost of testing is typically far less than the cost of a breach it could prevent.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us