October 14, 2025
Updated: July 28, 2025
Discover how black box, white box, and grey box testing differ strengths, limitations, real-world use cases, and best practices for secure software development.
Mohammed Khalil

In today’s complex software landscape microservices, cloud, remote work, relying on one testing approach is risky. Security teams and QA engineers must understand the black box vs white box difference to choose the right method.
This is crucial for effective penetration testing and compliance with standards e.g. NIST, SOC 2, ISO 27001. We’ll define each approach, compare them side by side with a handy table, discuss advantages/disadvantages, and provide real world guidance on when and how to use each technique.
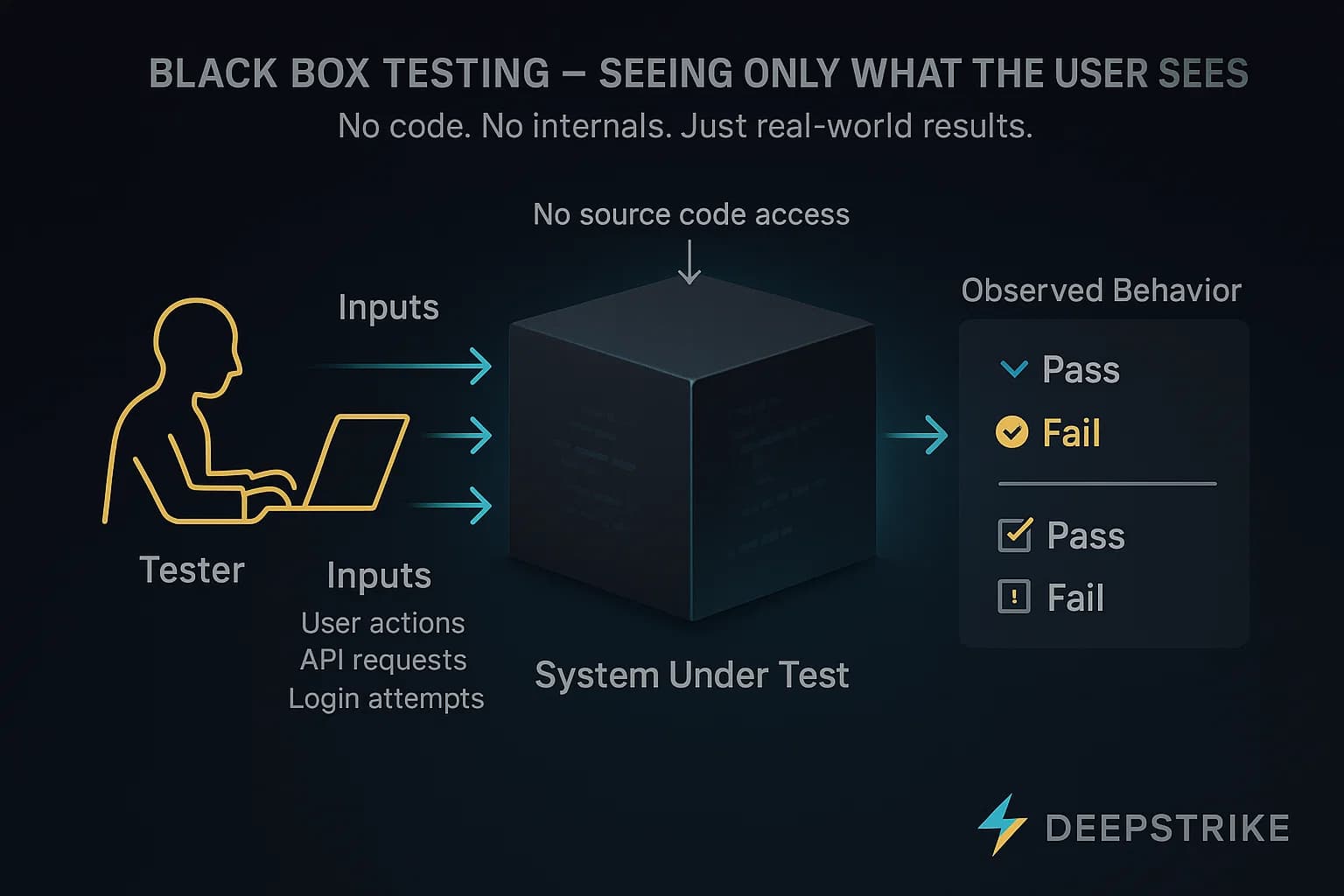
Black box testing treats the system as a black box: the tester has no knowledge of the internal code or structure and evaluates functionality purely based on inputs and expected outputs. Test cases come from requirements, user stories or specifications.
In practice, a QA engineer or pentester runs the application or API with various inputs and checks the results against expected behavior. For example, testers might input valid/invalid login credentials to verify the authentication workflow, without seeing the source code. Common techniques include functional testing, regression testing, and usability testing.
This approach simulates a real user or external attacker who only sees the public interfaces of an application. It is widely used in system and acceptance testing, as well as automated UI and API tests. Penetration testers performing a black box pentest try to breach the system with no insider information.
Because testers don’t need programming knowledge, a broader range of people can perform black box tests. However, black box testing only covers what the system does, not how it does it. Hidden bugs, untested branches, or security flaws in the code can go undetected.
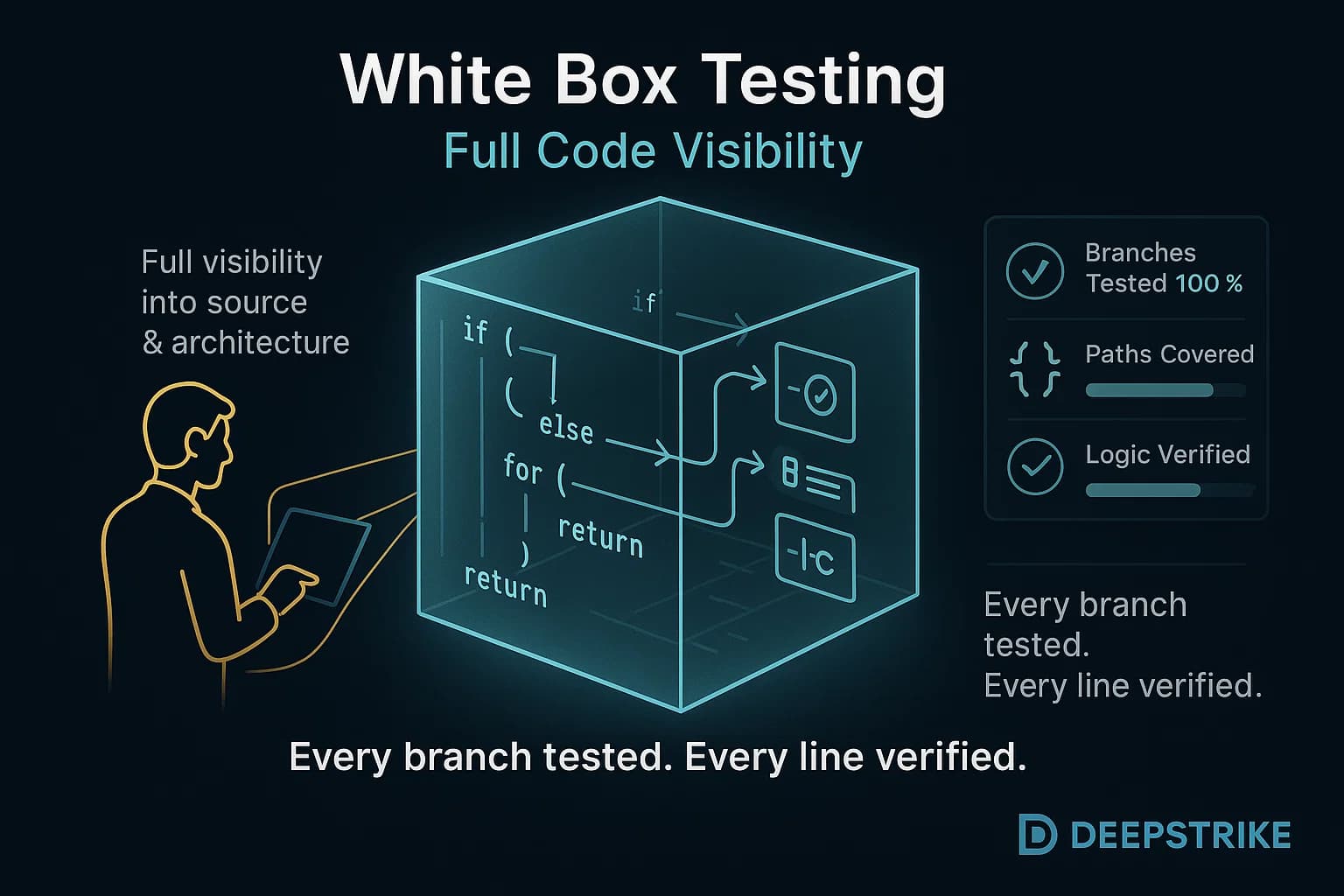
White box testing also called clear/transparent box testing assumes full access to the internal code and architecture. Testers often developers or specialized QA engineers design tests based on the source code, control flow, and data paths.
The goal is to exercise every branch, loop, and condition in the code. For instance, a white box test might ensure each if statement and every possible code path is executed at least once. Common activities include unit tests, integration tests, and static code analysis.
Since white box testers see the inner workings, they can find issues that would be invisible in black box tests for example, dead code, hidden logic bugs, or poor error handling. This leads to comprehensive coverage testers can write cases to trigger each statement and branch. In security, white box testing such as source code review or static analysis can uncover vulnerabilities like insecure input handling before the software even runs. On the downside, white box testing requires skilled engineers familiar with the codebase, and writing exhaustive tests is time consuming and costly.
Example of White Box Testing: Inspecting source code to design test cases. White box testing thoroughly examines internal logic credit: L. Gomes via Pexels.

The table below highlights the main contrasts between black box and white box testing:
| Aspect | Black Box | White Box |
|---|---|---|
| Tester’s Knowledge | No insight into code or internals. | Full access to source code and design. |
| Test Basis | Requirements/specifications external behavior. | Code and architecture internal behavior. |
| Focus | Functionality inputs-outputs. | Logic/structure flow paths, conditions. |
| Design Techniques | Specification based equivalence classes, boundary values. | Code based control flow, branch/statement coverage, data flow. |
| Testing Level | Higher levels: system, integration, UI, API acceptance. | Lower levels: unit, component testing. |
| Testers | QA testers, end users, possibly external auditors. | Developers, SDETs, security analysts. |
| Tools | GUI/API testing tools Selenium, Postman, fuzzers, scanners. | Unit test frameworks JUnit, pytest, code coverage tools JaCoCo, static analyzers SonarQube. |
| Coverage | Covers visible behavior; may miss hidden paths or unimplemented features. | Aims for thorough path coverage; can miss un coded requirements. |
| Execution | Generally faster to run, no code review needed. | More time consuming detailed test creation. |
| Typical Use | Acceptance testing, regression testing, penetration tests from outsider view. | Unit/integration tests, code reviews, secure code analysis. |
In 2025 and beyond, software ecosystems are more complex and interconnected than ever. Cloud based microservices, remote work tools, and AI components mean security flaws can hide in code or emerge at interfaces. Using both black and white box testing strengthens your defense:
Combining both styles answers the key question: What could an attacker do, and does our code even have those flaws? Balancing external and internal views is essential for a resilient security posture.
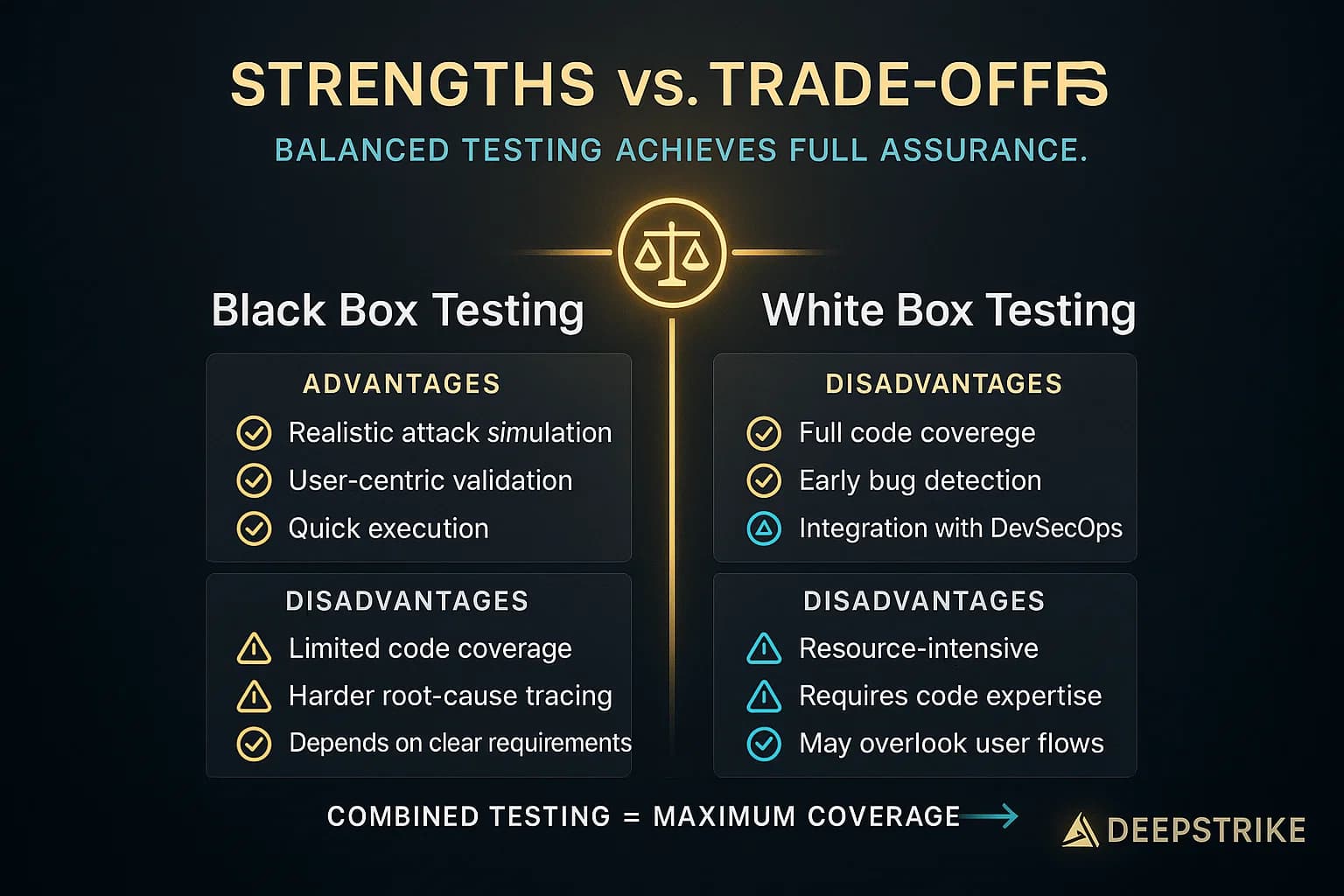
Both approaches have strengths and trade offs. Understanding them helps pick the right tool for each job:
In practice, mixing them mitigates weaknesses, for example, a security team may start with a white box code review static analysis to clear obvious issues, then perform a black box pentest to find any flaws remaining at the external interface.
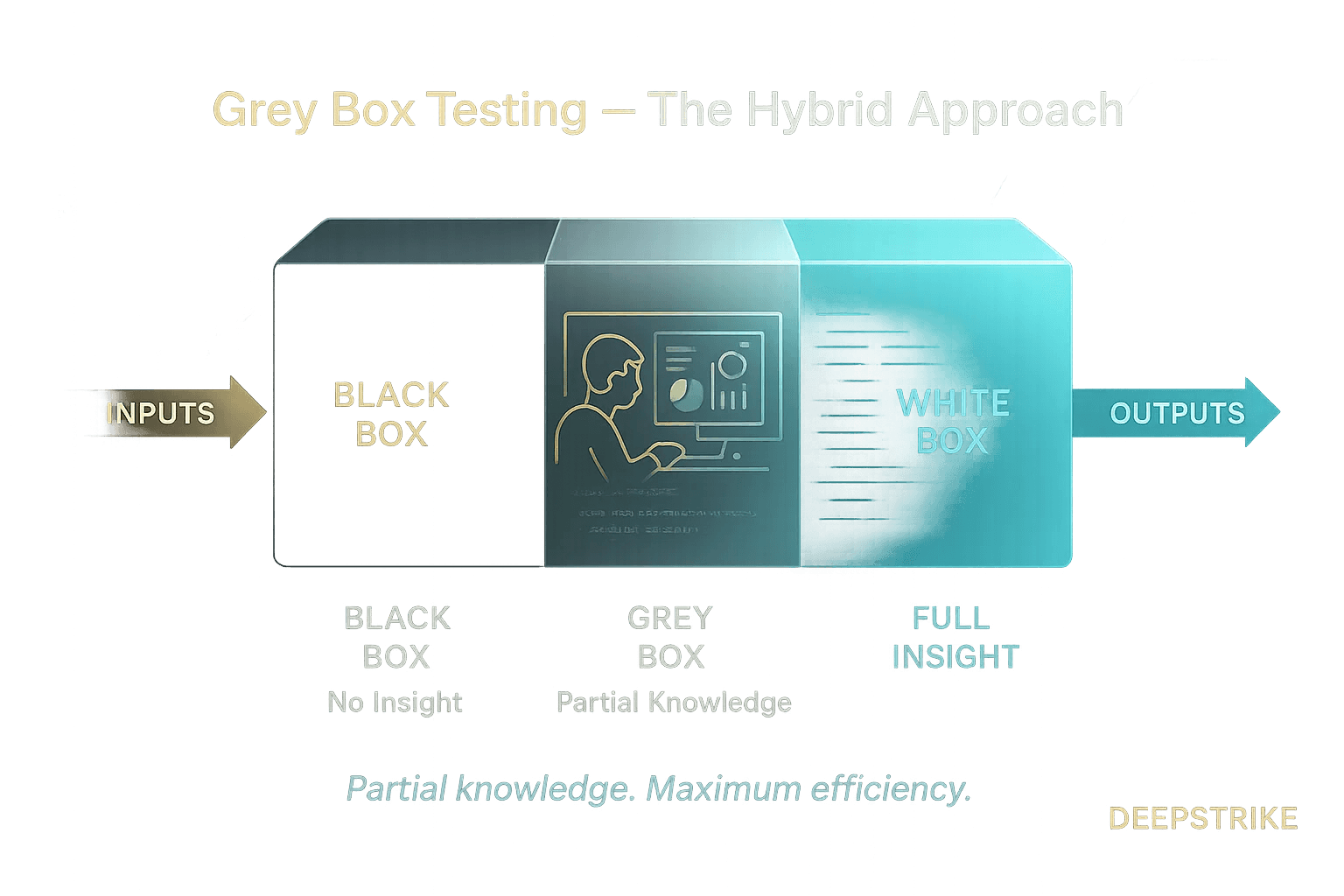
Grey box testing sits between black and white box. Testers receive partial knowledge e.g. architecture diagrams or user credentials to focus their efforts. For instance, providing login credentials lets testers bypass initial reconnaissance and concentrate on post login functionality. Grey box testing simulates a privileged user or insider scenario. It achieves a compromise, more efficient than black box, less time guessing and more realistic than pure white box still tests real authentication/authorization flows. According to Redscan, grey box is often the preferred balance between efficiency and authenticity. Use grey box tests when you want both domain knowledge and realistic attack simulation.
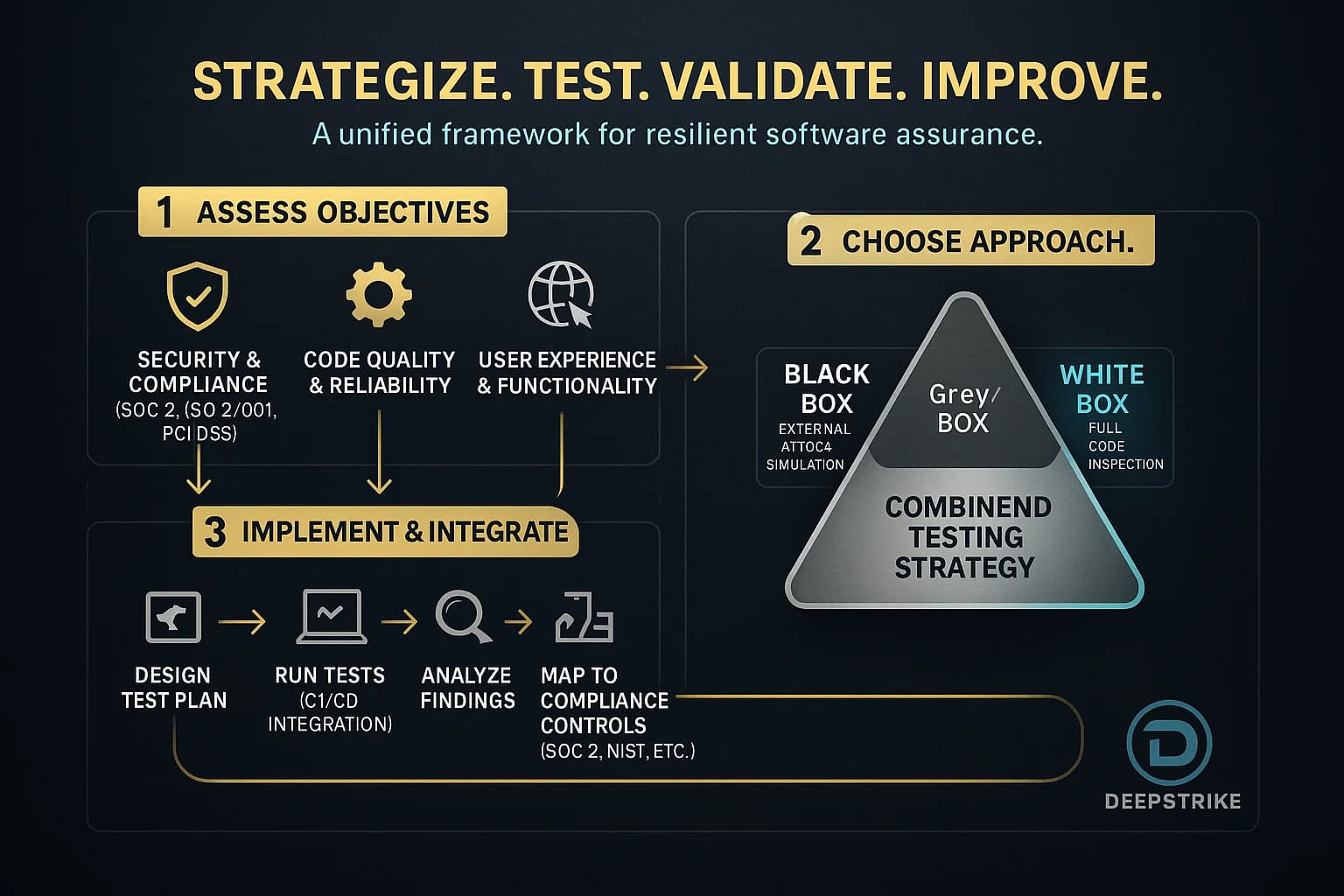
For each project, define scope UI, APIs, network, etc., choose testers QA vs developers, decide on approach black/white/grey, set tools pytest, Selenium, Burp, etc., and map tests to compliance requirements e.g. SOC 2 TSC CC4.1 for periodic testing.

For more on penetration testing strategies and costs, see our guides: What is Penetration Testing ?, penetration testing cost, and penetration testing for startups and SMBs. Also, learn how PTaaS and continuous testing platforms bring both worlds together in Penetration Testing as a Service PTaaS and continuous penetration testing platform offerings.
Black box and white box testing are two pillars of software quality and security. Black box testing ensures that the software does what it should from the user’s perspective, while white box testing ensures the software is built correctly under the hood.
In 2025’s threat landscape, relying on only one perspective is risky. A modern testing strategy uses both code level checks plus end to end tests.
Ready to strengthen your defenses? The threats of 2025 demand more than just awareness; they require readiness. If you’re looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of experts provides clear, actionable guidance to protect your business.
Explore our penetration testing services to see how we can uncover vulnerabilities before attackers do. Drop us a line we’re always ready to dive in.
About the AuthorMohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security. With certifications including CISSP, OSCP, and OSWE, he has led red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in finance, healthcare, and technology.
Black box testing examines software as an external user, without seeing the code; it focuses on inputs and expected outputs. White box testing reviews the internal code and logic, aiming to execute all paths and conditions. The key difference is knowledge of internals and test focus.
Use black box testing when validating functionality and user requirements system or acceptance tests. Use white box testing during development unit/integration tests or security code reviews to verify code quality and logic. Many teams use both: e.g. developers write white box unit tests, then QA or pentesters perform black box tests.
Grey box is not strictly better, but it provides a middle ground. It gives testers limited internal info like credentials to speed up targeted testing. It can be more efficient than pure black box and more realistic than full white box. Use grey box when you want to simulate insider threats or when partial system knowledge is available.
Yes. Black box tests are often automated via UI/API test suites, fuzzers, or scanners. White box tests are automated as unit tests and static analysis. Automation boosts speed, but human oversight is still needed to design meaningful tests and interpret results.
A penetration test can be conducted in a black box, white box, or grey box style. A black box pentest uses no insider info mirroring an external attacker. A white box pentest provides the tester with full system info like source code for an in depth review. Choosing the style affects scope, time, and cost. For details, see our vulnerability assessment vs penetration testing guide.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us