October 12, 2025
Updated: October 12, 2025
SOC 2 doesn’t explicitly require penetration testing but in 2025, auditors and clients expect it. Learn how to scope, execute, and document a SOC 2 pentest that validates CC4.1 & CC7.1 controls.
Mohammed Khalil

Penetration testing bridges the validation gap left by automated tools. It’s like asking an ethical hacker, Can you break in?and then fixing what they find. In short, SOC 2 penetration testing is a proactive way to demonstrate that your security controls really work under attack, earning trust and audit confidence.

SOC 2 penetration testing is just regular ethical hacking done with SOC 2 compliance in mind. It simulates real attack scenarios against your in scope systems networks, apps, cloud environments, etc. to uncover vulnerabilities an attacker could exploit. Think of it as a focused red team style audit to verify your SOC 2 security controls.
SOC 2 is a compliance framework focused on Trust Services Criteria like Security, Availability, and Confidentiality. It requires organizations to assess their risks and ensure controls are working effectively. Importantly, SOC 2 does not explicitly say you must do a pentest. Instead, the AICPA guidance calls for ongoing risk assessment and control evaluations, which can include vulnerability scans, audits, and yes penetration tests. In practice, auditors and customers expect a high quality pentest as evidence that your Security CC4.1 and Vulnerability Management CC7.1 controls are effective. In other words, a SOC 2 report is stronger when backed by a recent pentest report.
doing a pentest isn’t technically a checkbox in SOC 2, but skipping it can raise eyebrows. Customers and prospects often expect it as a best practice. Likewise, auditors will ask how you’ve separately evaluated your controls and a pentest is a common answer. So even if SOC 2 doesn’t force a pentest, tradition and good sense usually do.

By 2025, cyber threats have only grown more sophisticated. SOC 2 pentesting gives you a reality check: it finds flaws that code scans and checklists miss. A good pentest simulates chained exploits and business logic attacks that automated tools can’t detect. For example, automated scanners might flag a potential SQL injection, but only a manual test can prove the full impact e.g. extracting customer data. As one expert puts it, a scan gives a list of possibilities, whereas a pentest gives a list of certainties.
In today’s fast moving IT world, relying on a once a year checklist is dangerous. New features or misconfigurations can introduce critical bugs overnight. That’s why many teams are adopting continuous security practices like CI/CD integrated pentesting to catch issues in real time. Still, at a minimum, an annual SOC 2 pentest is expected. In short, regular pentesting is one of the most effective ways to stay ahead of evolving threats and prove your security controls work under pressure.

SOC 2 requires you to assess risks and implement controls that reduce those risks to acceptable levels. As part of this, you must evaluate that your controls are working. Penetration testing is one proven way to do this, especially for technical controls like firewalls, authentication, and network defenses.
In practice, SOC 2 pentest usually means a standard business as usual pentest, but scoped to your SOC 2 environment and timing usually within 12 months of the audit date. Discuss scope early with your audit team to ensure they see all relevant controls covered.
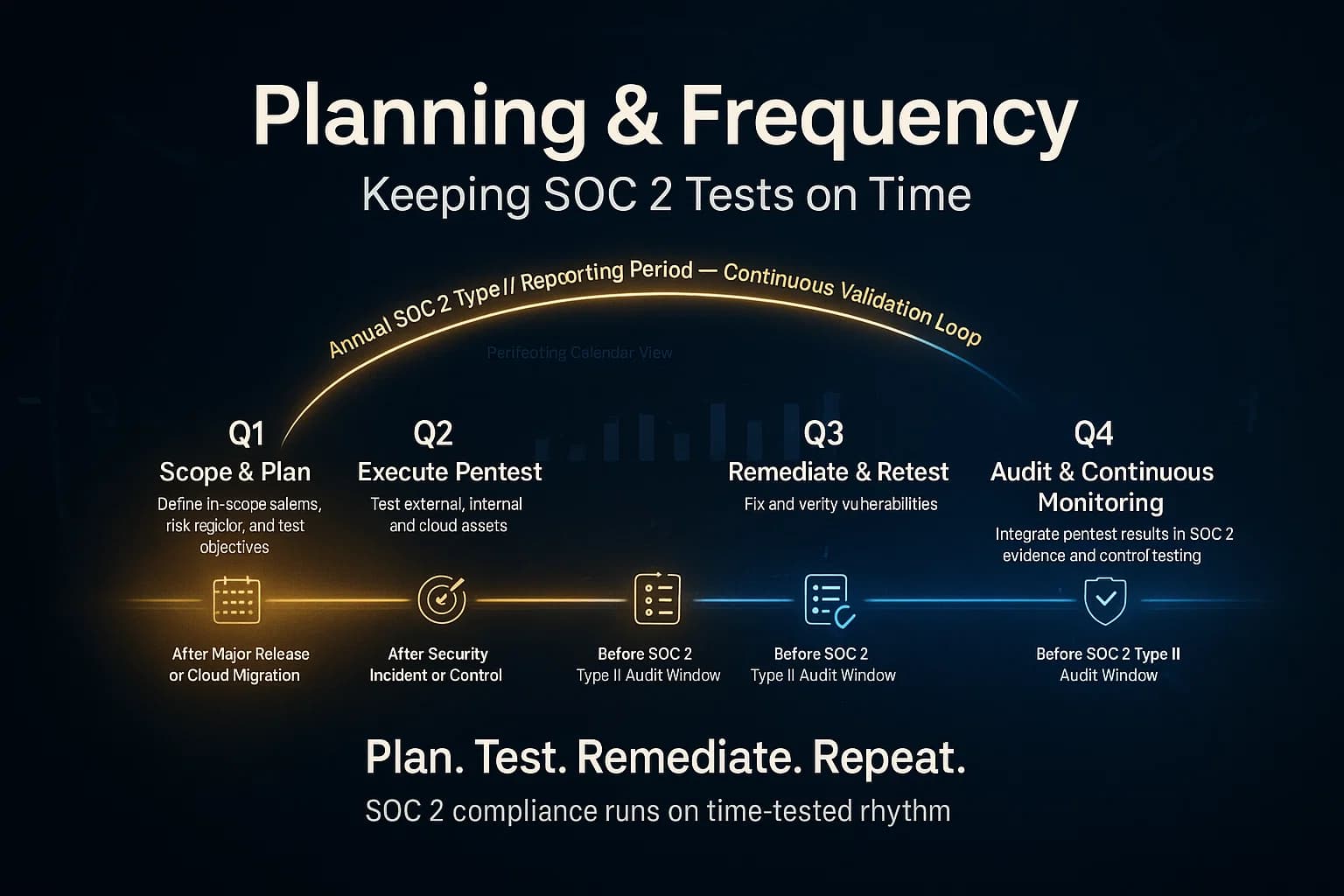
How often? SOC 2 itself doesn’t set a schedule, but best practice and other regulations like PCI DSS is at least annual testing, and always after major changes. Our recommended baseline: a full manual pentest once per year, more often if you have fast release cycles or higher risk. Automated vulnerability scanning should run continuously or weekly/monthly.
How to choose a vendor? Look for experienced, certified testers:
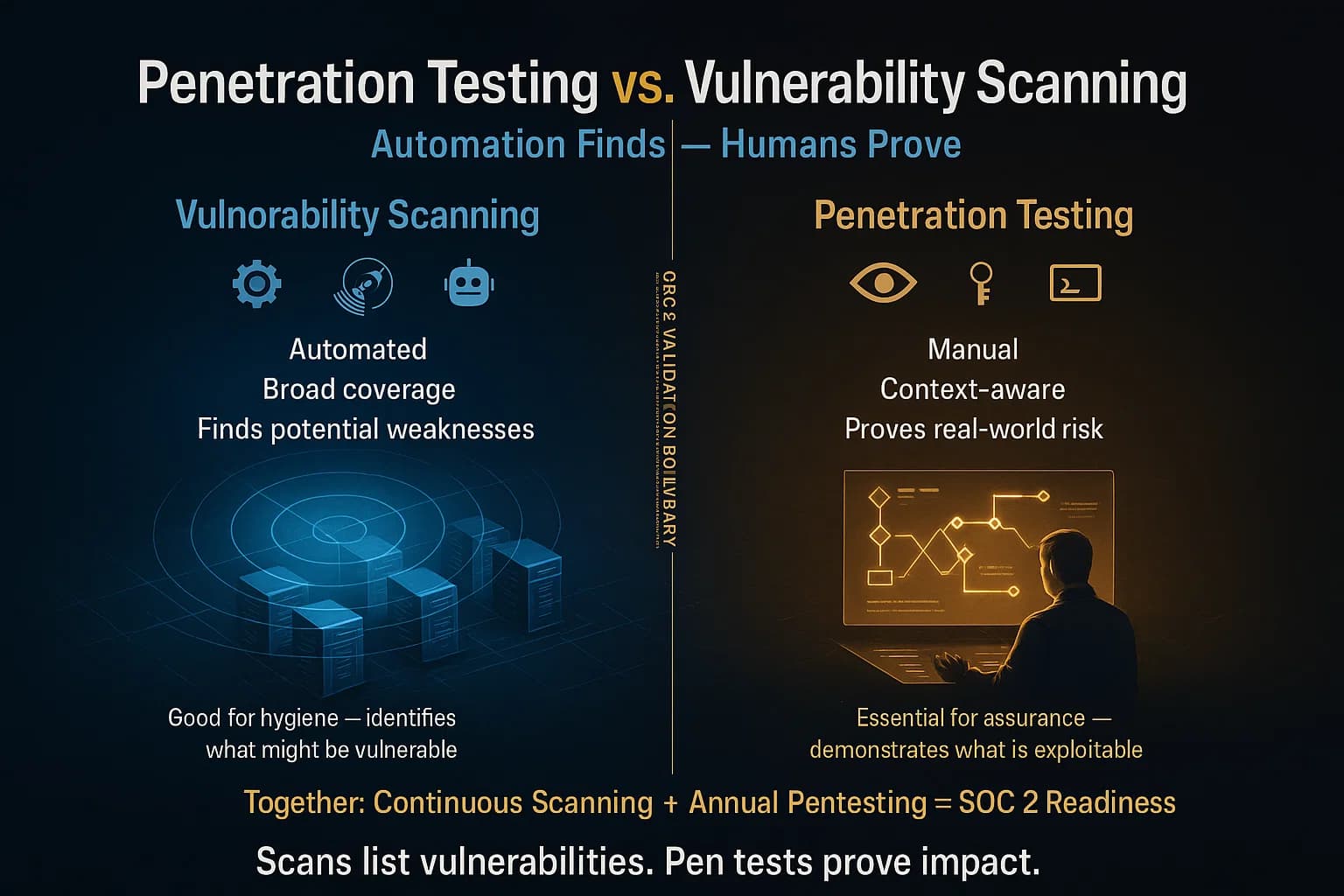
A common question: Can I just run vulnerability scans instead of a full pentest? The answer is no. They serve different purposes.
These are complementary, not interchangeable. For SOC 2, automated scans are great for ongoing hygiene, but auditors expect the proof of risk reduction via an actual exploit attempt. As DeepStrike’s experts put it: A scan gives you a list of possibilities; a pentest gives you a list of certainties.
Always include a vulnerability scan in your overall program auditors love seeing that as evidence of continuous monitoring but accompany it with a manual pentest for full validation.
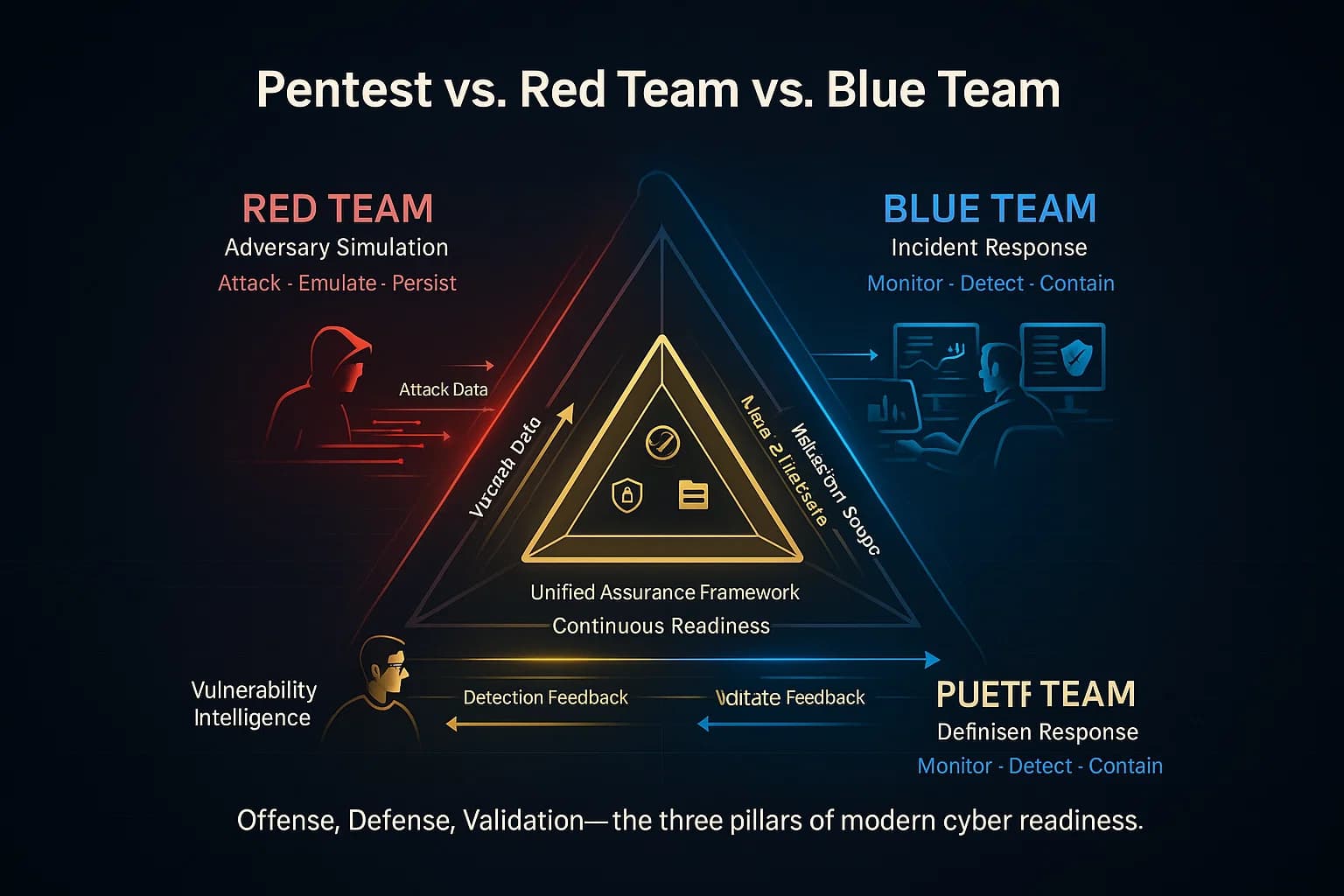
SOC 2 pentesting is usually white box or gray box testing with the goal of finding and fixing vulnerabilities. It does not fully replace a red team exercise, which goes beyond pentesting to test your people, processes, and detection capabilities.
For SOC 2, the focus is on the security controls themselves, not your incident response. In practice, a red team is usually overkill unless you have sophisticated requirements. Our recommendation: start with a solid pentest. If one day you want to test your SOC and IR team, consider a separate red team engagement.
Related reads: Vulnerability scanning vs penetration testing and Red team vs Blue team explained.
Costs can vary widely by scope. A small web app test might be $5K- $10K, while a full enterprise network/cloud scope can run $30K or more. Here’s a rough idea:
| Provider | Specialties & Credentials | Pricing approx |
|---|---|---|
| DeepStrike | Offensive-security boutique specializing in manual web and cloud pentests (OWASP Top 10 + custom threat modeling). Testers hold OSCP, OSWE, and CRTP credentials. Delivers evidence-rich reports mapped to SOC 2 and MITRE ATT&CK. | Starts around $6K for web / API scope; enterprise packages from $18K + |
| Blaze InfoSec | SOC 2focused pentests web, APIs, cloud by OSCP/OSCE testers. Delivers SOC ready reports. | Starts $4,999 basic scope |
| TargetDefense | US based firm OSCP/CREST offering network, web, API pentests. Positions as SOC 2/PCI helper. | Starts $995 scans; manual tests from $5K+ |
| A LIGN | Compliance specialist SOC 2, ISO 27001 with certified pentesters. Full service pentest & SOC readiness. | Custom quotes many engagements done |
| Astro InfoSec | SOC 2 oriented testing: apps, APIs, cloud. Emphasizes covering all Trust Criteria. | Custom quotes contact for estimate |
| Astra Security | CREST accredited PTaaS 12,000+ tests done. Automated + manual, with retests. | Custom pricing by engagement size. |
Prices above are illustrative. Always ask for a custom quote. Beware extremely low prices <$4,000 for a pentest they often mean just a basic automated scan, which won’t meet auditor expectations. Investing in a thorough manual test even if pricier usually saves money by avoiding breaches and compliance roadblocks.

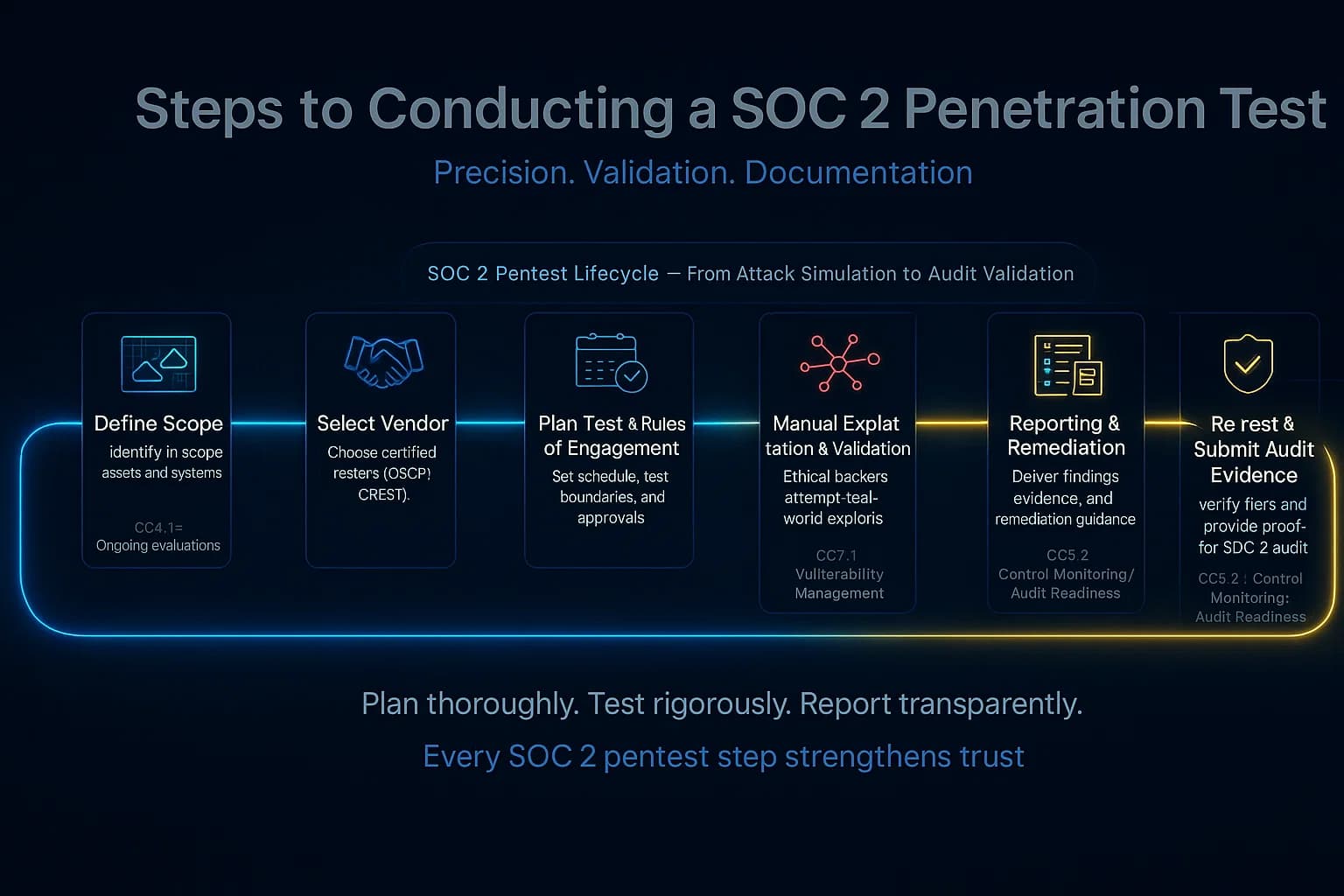
A SOC 2 friendly pentest report is a professional audit document. Key elements include:
In short, your pentest report should demonstrate that controls were tested and vulnerabilities closed. A clear, professional report plus evidence of fixes makes your SOC 2 audit much smoother.
Here’s a quick checklist for your SOC 2 penetration test:
Treat every vulnerability seriously, even if it’s just medium. SOC 2 auditors want confidence that you’re not leaving open doors. Respond promptly to all findings, and document the outcome.
Penetration testing is a critical piece of a strong SOC 2 security program. It’s how you turn theory into proof: testing your security in action under real world attack scenarios. While not required by name, a well executed pentest is often the most convincing way to satisfy SOC 2 trust criteria and earn your auditors’ trust.
Ready to strengthen your defenses? The threats of 2025 demand more than just checklists they require readiness. If you need to validate your security posture, find hidden risks, or build a resilient defense, DeepStrike can help. Our experienced team provides clear, actionable guidance and an audit ready pentest report to protect your business.

Explore our penetration testing services to see how we can uncover vulnerabilities before attackers do. Drop us a line via our Contact page we’re always ready to dive in.
About the AuthorMohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
SOC 2 itself doesn’t explicitly require a pentest. It requires you to assess risks and test controls, which can be done in many ways. However, pentesting is strongly expected by auditors and customers as proof that security controls actually work. In practice, virtually all SOC 2 reports include a pentest especially for Type II because it adds credibility to your Security controls CC4.1 and Vulnerability Management CC7.1 evidence.
At minimum, once per year. Many frameworks PCI, HIPAA mandate annual tests, and auditors expect a fresh test for each audit cycle. Also test after any major release, migration, or environment change. In short, annual testing plus triggered tests on change is best practice. Automated scans should fill in the gaps by running continuously or weekly/monthly.
It varies widely with scope. A simple web/app test might be $5K- $15K, while a large enterprise multiple networks, cloud, APIs, mobile can exceed $30K. Most projects fall in the $10K- $30K range. Price factors include the size of the attack surface, the depth of testing black box vs white box, and tester expertise. Beware ultra cheap quotes <$4K those are usually just automated scans and won’t satisfy auditors.
A SOC 2 pentest report looks like a professional security audit. It has an executive summary, scope & methodology, and a findings section listing each issue with description, risk rating, affected assets, proof of concept screenshots/logs, and remediation advice. Often it includes a summary matrix or chart of findings by severity. The report should also document any re-tests after fixes. The key is that it provides clear evidence of what was tested and that any critical flaws were addressed. Auditors will expect to see this report and proof that issues were fixed as part of your SOC 2 evidence.
No. Automated scans are useful for finding known issues quickly, but they only show potential problems. A human led pentest is needed to actually exploit vulnerabilities and prove how an attacker could break in. Think of a scan as an X ray and a pentest as surgery both are important. For SOC 2, auditors usually want the hands on test to be sure the risks are real and under control.
Start early. Review your system description and gather documentation network diagrams, code inventories, etc.. Make sure you can provide the testers with any required access e.g. VPN accounts, test credentials and point out any high sensitivity areas. Back up critical systems beforehand. Schedule the test at a safe time usually off hours, and notify all stakeholders. Communicate with your auditor so they know a test is happening. Fix simple known issues like expired certificates before the test to focus on unknowns. In short: clarify scope, ensure backups, gather info, and coordinate with all parties for a smooth test.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us