July 29, 2025
Updated: July 29, 2025
A side-by-side breakdown of penetration testing and bug bounty programs costs, goals, scope, and when to use each for maximum impact.
Mohammed Khalil

A penetration test is a structured, time boxed security assessment performed by a dedicated team, ideal for compliance audits and pre launch validation. A bug bounty program is a continuous, crowdsourced security effort where a global community of researchers tests live applications on a pay for results basis.
Penetration testing establishes a critical security baseline and satisfies formal requirements for frameworks like soc 2 penetration testing and pci dss penetration testing. Bug bounty programs provide ongoing vigilance against new threats and code changes, directly addressing the rapid exploitation of vulnerabilities highlighted in the 2024 Verizon DBIR.
They are not competitors; they are complementary. The most resilient security posture in 2025 uses periodic, in depth pentests to build a strong foundation and an "always on" bug bounty program to continuously test it.
Deciding between penetration testing vs bug bounty isn't about which is "better" , it's about which is right for your specific goal, right now. A pentest is like a scheduled, deep dive inspection of your building's foundation and structure. A bug bounty is like having thousands of security experts continuously checking every door, window, and access point, 24/7. Think of a pentest as a spotlight intensely focused but limited in coverage and a bug bounty as floodlights, illuminating a wide area continuously. Each reveals different blind spots.
This distinction matters more in 2025 than ever before. The game has changed. The 2024 Verizon Data Breach Investigations Report (DBIR) reveals a staggering 180% increase in breaches originating from exploited vulnerabilities. This isn't a slow moving threat; it's a high speed race. Attackers are weaponizing flaws faster than ever, making point in time security checks, while essential, insufficient on their own.
The real enemy isn't just the vulnerability itself; it's the "vulnerability window" the critical time gap between when a flaw is introduced in code and when it's discovered. With attackers moving this fast, shrinking that window is the primary challenge for security leaders.
This guide provides a strategic framework to help you build a defense that is both deep and continuous. We'll move beyond generic definitions to provide a practitioner's view, backed by data from sources like NIST, IBM, HackerOne, and Bugcrowd. We'll cover the methodologies, compare them head to head, and give you a clear decision framework for allocating your security budget effectively.
A penetration test, or pentest, is a security assessment that mimics real world attacks to identify and exploit vulnerabilities. As defined by the National Institute of Standards and Technology (NIST) in SP 800 115, it involves "issuing real attacks on real systems and data, using the same tools and techniques used by actual attackers".
The primary goal is not just to find flaws, but to determine the degree of resistance a system has to a hostile cyber attack and to understand the potential business impact of a successful breach. This makes it fundamentally different from a simple vulnerability assessment vs penetration testing, which focuses on identifying potential weaknesses without necessarily exploiting them.
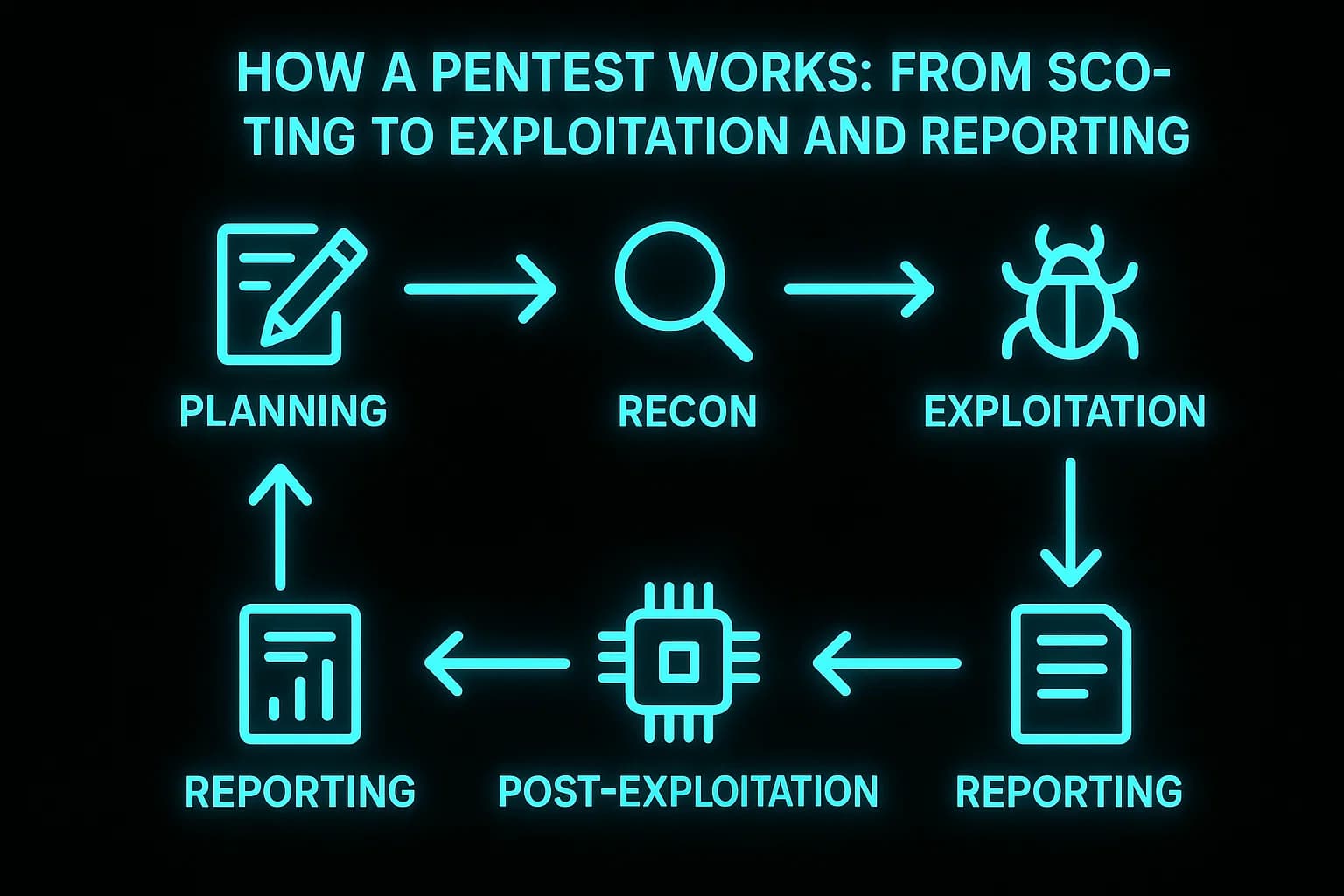
This isn't random hacking; it's a methodical process. Based on industry best practices from SANS and NIST, a typical engagement follows these phases :
The type of test depends on the objective and the threat you want to simulate. The most common distinctions are:
A bug bounty program is a deal offered by an organization that invites individuals often called ethical hackers or security researchers to find and report security vulnerabilities in exchange for recognition and monetary rewards.
It's a form of crowdsourced security, leveraging a global talent pool with diverse skills and perspectives to continuously scrutinize digital assets. Major platforms like
HackerOne, Bugcrowd, and Intigriti act as intermediaries, connecting companies with this community and managing the logistics of the program.

The process is fundamentally different from a contracted pentest, operating on a continuous, results driven model :

Shopify runs one of the most successful bug bounty programs, having paid out over $7.2 million in bounties to date. Their program is a masterclass in transparency, with a detailed public process for triage and a severity calculator that maps CVSS scores to specific reward amounts. They've shared case studies of critical bugs found through their program, including a Remote Code Execution (RCE) vulnerability in Shopify Scripts that resulted in a $20,000 bounty. This demonstrates the power of the crowdsourced model to uncover even the most severe and complex flaws in a live, enterprise scale environment.
A bug bounty program is more than just a testing method; it's a catalyst for organizational change. A penetration test is a controlled, scheduled event. The security and development teams know it's coming and can prepare. The report is delivered, and remediation is planned in future sprints. In contrast, a bug bounty program is "always on" and unpredictable. The unpredictability of when a critical vulnerability might be reported demands immediate attention from development teams, which can disrupt planned sprints.
This unpredictability, while challenging, creates a powerful "forcing function." It compels an organization to move beyond scheduled, reactive security fixes and build a mature, rapid response incident management capability. To succeed with a bug bounty, you can't just have a good development team; you need a well oiled machine for triage, prioritization, patching, and re testing that operates continuously. Therefore, launching a bug bounty program forces the maturation of the entire security development lifecycle (DevSecOps), improving processes in a way that periodic pentesting alone cannot.
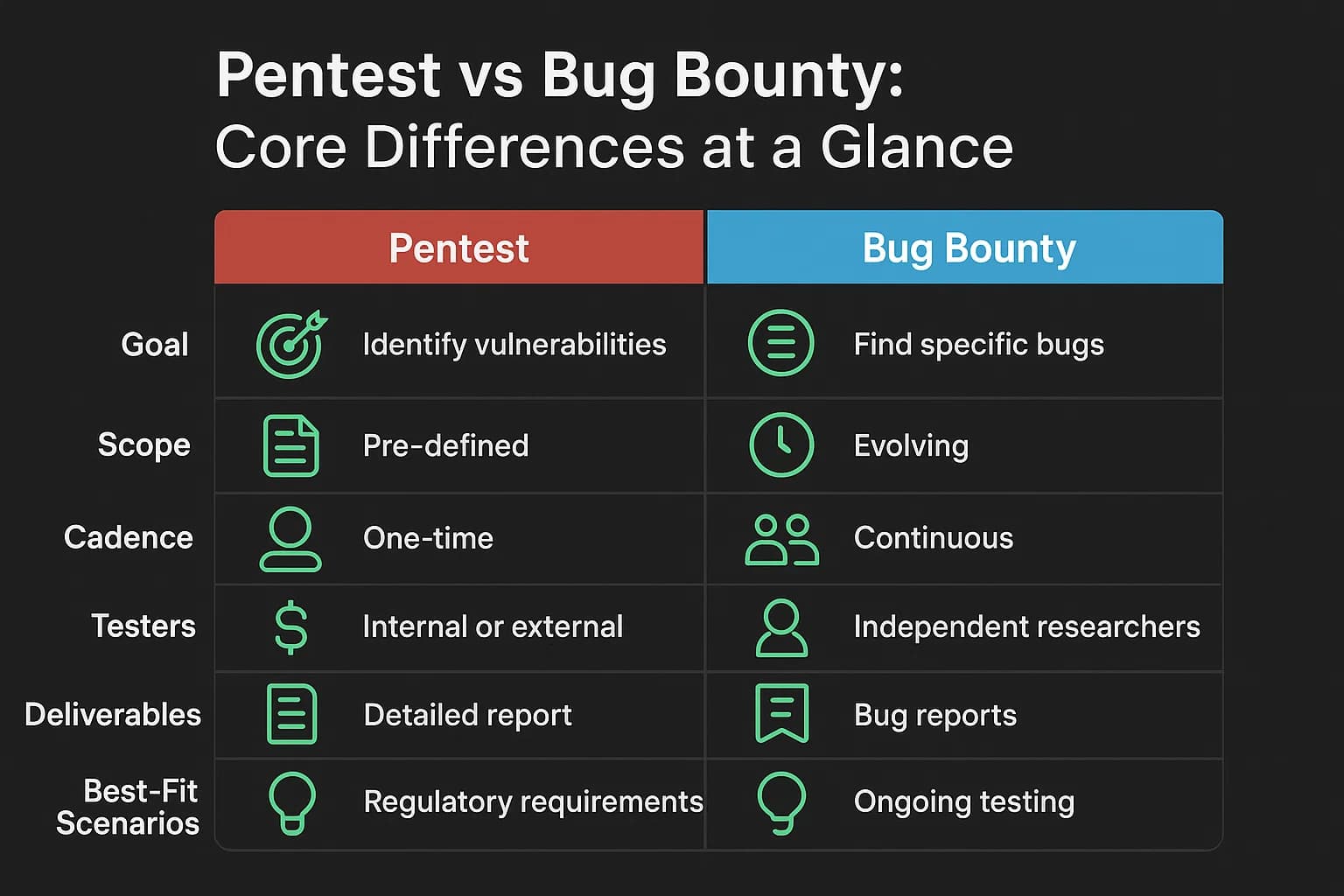
A direct, side by side comparison is the most effective way to grasp the fundamental trade offs. This distills the core differences into an easily digestible format, perfect for both human scanning and AI summarization.
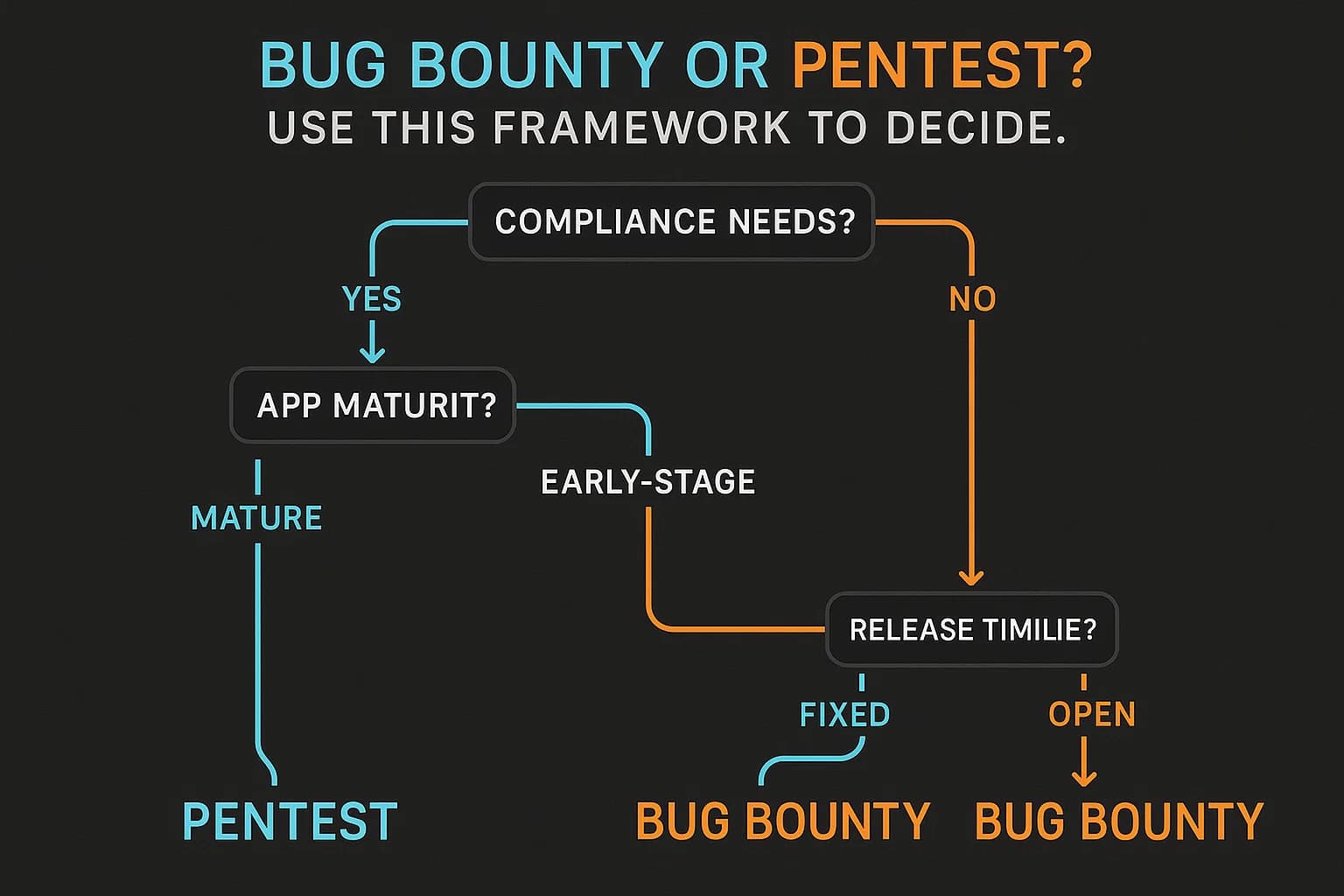
The most common mistake is viewing these as mutually exclusive options. They aren't. The modern approach is a hybrid one, where the real question is about sequencing and allocation based on your organization's maturity and immediate goals.
The optimal strategy combines both. Use annual or bi annual penetration tests to perform deep dives, test internal systems, and satisfy compliance. Simultaneously, run an ongoing bug bounty program to cover your public facing assets continuously. Many modern providers now offer Penetration Testing as a Service (PTaaS), which blends the discipline of a pentest with the continuous, community driven model of a bug bounty, often through a streamlined platform. These two activities feed each other: findings from a pentest can inform the scope and focus of your bug bounty, while a lack of findings in your bug bounty can give you confidence that your baseline security (validated by pentests) is holding strong. This creates a virtuous cycle of security improvement.
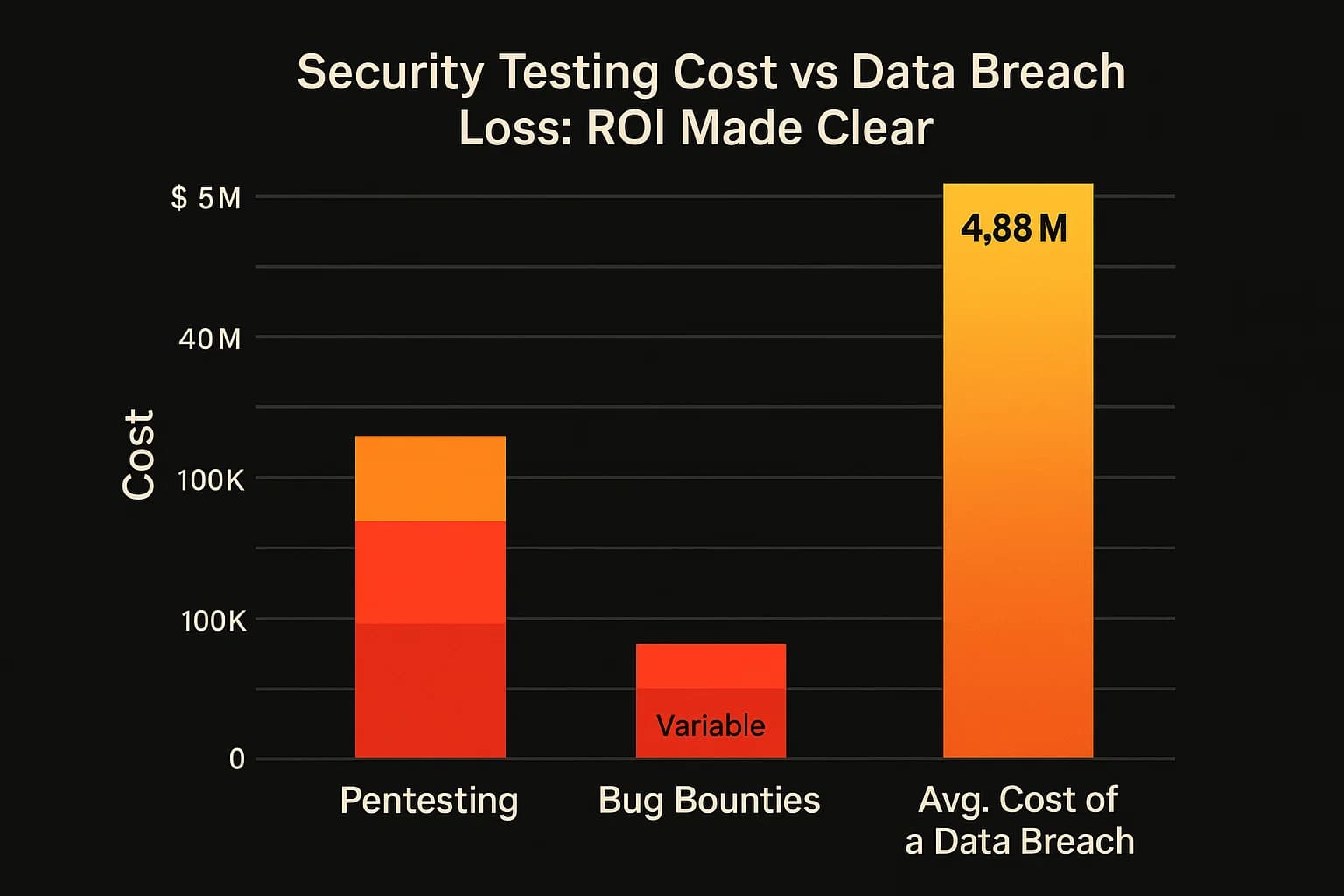
Viewing the cost of proactive testing in isolation is a mistake. It must be compared against the staggering cost of a potential breach.
According to IBM's 2024 Cost of a Data Breach Report, the global average cost of a data breach has hit a record $4.88 million. For the financial services industry, that number climbs to $6.08 million.
When framed this way, the ROI becomes crystal clear. Spending $50,000 on a pentest or $100,000 over a year on bug bounties to prevent a multi million dollar incident is an obvious win. The discussion shifts from "Can we afford to test?" to "Can we afford not to?" This proactive investment also helps reduce costs associated with cyber insurance, as insurers increasingly reward demonstrated security maturity.
Artificial Intelligence is not just a new tool; it's a new battleground. It is simultaneously enhancing both defensive and offensive capabilities while creating an entirely new attack surface that must be defended.
AI is supercharging the traditional pentesting workflow. AI powered tools can accelerate reconnaissance by analyzing vast public datasets, automate vulnerability scanning with greater accuracy, and even suggest or generate exploit payloads for known vulnerabilities. This doesn't replace human pentesters. Instead, it frees them from repetitive, time consuming tasks, allowing them to focus on complex, creative problem solving and business logic exploitation areas where human ingenuity still reigns supreme. The future is one of human machine teaming.
For bug bounty hunters, AI is a powerful assistant for smarter recon and identifying subtle patterns in code that might indicate a flaw. More importantly, AI and Large Language Models (LLMs) are now a primary target themselves. The
HackerOne 2024 Hacker Powered Security Report notes a 171% increase in AI assets being added to the scope of bug bounty programs. This has introduced new, critical vulnerability classes like prompt injection, data poisoning, and model manipulation.
The future of offensive security is hybrid, a collaboration between creative human experts and powerful AI assistants. The most effective security programs will leverage both. The rise of "Agentic AI" will create autonomous threats that can plan and execute attacks, demanding equally adaptive AI driven defenses. The strategic focus is shifting from just testing applications to testing the AI models themselves, a trend highlighted by the World Economic Forum's Global Cybersecurity Outlook 2025.
The Reality: While the pay for results model sounds appealing, it's highly unpredictable. A very vulnerable application can quickly become a "bug bounty money pit," costing far more than a fixed fee pentest and completely overwhelming your development team.
The Reality: A pentest is a snapshot in time. Your security posture can change the moment you deploy new code. A clean report is a good sign, but it doesn't grant you a year of immunity. This is the "vulnerability window" problem in action.
The Reality: This is a common and costly mistake for organizations with low security maturity. A bug bounty is not a replacement for fundamental security hygiene. You need a pentest to establish a solid baseline first. Otherwise, you'll pay a premium for researchers to find basic flaws that a structured pentest would have identified more cost effectively.
The Reality: This couldn't be further from the truth. While the idea of an unvetted crowd is a valid concern, reputable bug bounty platforms like HackerOne and Bugcrowd have sophisticated systems for vetting researchers to mitigate this risk. While public programs are open, many are private and invite only. The top researchers are elite specialists in niche areas like GraphQL penetration testing or exploiting complex OAuth security flows. It's a global community of experts, not a random crowd.
The Reality: While professional penetration tests are conducted in a controlled manner to minimize risk, they are still simulated attacks. If not executed correctly, there is a small but real possibility of adverse effects, such as system damage or server crashes. This is why scoping, planning, and using experienced, certified testers are critical to a successful and safe engagement.
1. Can a bug bounty program replace a penetration test for compliance?
Generally, no. Compliance frameworks like SOC 2 and PCI DSS require the structured methodology and formal report provided by a penetration test. A bug bounty program is seen as a sign of strong security maturity that complements compliance efforts but doesn't typically replace the core requirement.
2. What is the average cost of a penetration test in 2025?
Costs vary widely based on scope and complexity, but typical ranges are from $10,000 to $50,000 for a standard web application or network test. Large, complex enterprise wide tests can exceed $100,000.
3. How much do bug bounty programs pay for critical vulnerabilities?
Payouts vary by program, but top tier companies pay significant amounts. HackerOne's 2024 report shows the average for critical bugs is around $25,000, with the 95th percentile reaching into the hundreds of thousands, and crypto programs hitting $1 million. Shopify's top bounty is $200,000.
4. Which is better for a brand new application: a pentest or a bug bounty?
A penetration test is almost always the correct first step. It establishes a secure baseline in a controlled, cost effective manner before you open the floodgates to a public bug bounty program.
5. How do you measure the success of a bug bounty program?
Success isn't just about the number of bugs found. Key metrics include time to triage, time to remediation, the severity of bugs found over time (it should decrease), and researcher engagement. A successful program strengthens your security posture; it doesn't just generate reports.
6. What's the difference between a vulnerability assessment and a penetration test?
A vulnerability assessment is about identifying potential flaws, often with automated scanners. A penetration test goes a step further by actively exploiting those flaws to determine their real world impact.
7. How often should a company perform a penetration test?
At a minimum, annually. For compliance frameworks like PCI DSS, it can be required twice a year or after any significant system change. For high risk environments, quarterly testing is a best practice.
8. Do companies prefer penetration testing or bug bounty programs?
Companies don't see it as a preference but as a strategic choice based on their goals. They typically require penetration tests for compliance and structured, point in time assurance. Many mature organizations also run bug bounty programs for continuous, real world coverage of their live applications. The modern preference is not for one over the other, but for a hybrid approach that combines the strengths of both.
In the end, the debate of penetration testing vs bug bounty is a false choice. They are two essential, complementary tools in a modern security arsenal. Pentests provide deep, structured assurance and are critical for compliance. Bug bounties offer the continuous, creative vigilance needed to keep pace with modern threats and rapid development cycles.
In an era of record high data breach statistics and lightning fast exploitation, a static, point in time defense is no longer enough. A resilient security program is a layered one. It starts with a strong foundation built through rigorous penetration testing services and is then continuously hardened by the diverse, global expertise of the ethical hacking community. The right strategy isn't about choosing one; it's about knowing when and how to use both.
Security questions don’t wait. Neither should you. Whether you're evaluating PTaaS, need help with a red team vs blue team assessment, or just want to see what DeepStrike can uncover ,drop us a line. We’re always happy to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us