June 17, 2025
Updated: June 17, 2025
Why penetration testing is now a non-negotiable for cyber insurance coverage, lower premiums, and airtight claims.
Mohammed Khalil

Penetration testing reduces cyber insurance premiums, improves insurability, and prevents policy denial by proving due diligence, validating risk controls, and aligning with underwriter expectations.
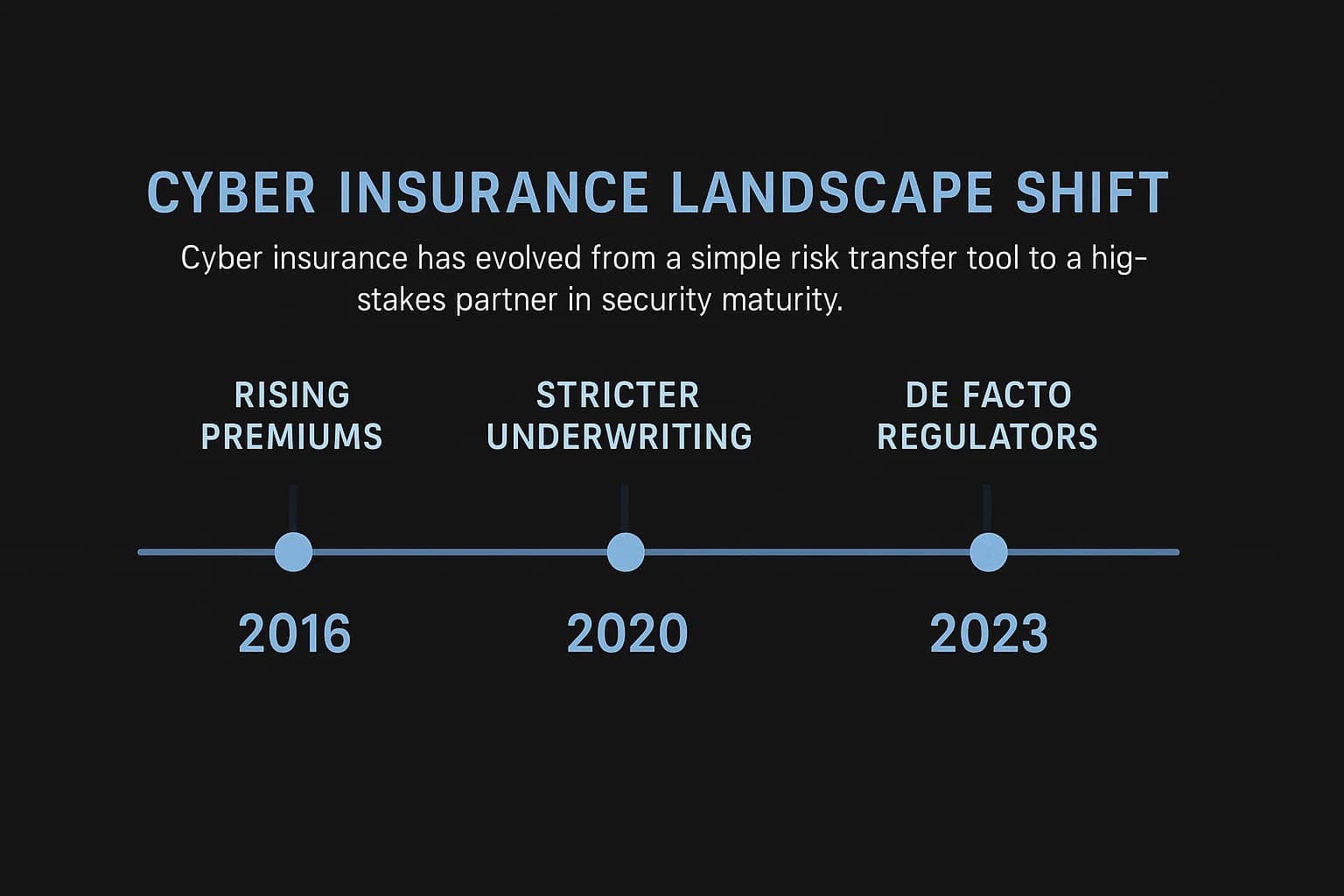
The cyber insurance market is currently experiencing a "hardening" phase, characterized by rising premiums, stricter underwriting criteria, and reduced coverage capacity. This shift is a direct response to the escalating frequency and cost of cyber incidents. The average cost of a data breach has climbed to USD 4.35 million, and organizations are facing a relentless barrage of attacks, with 83% reporting more than one breach. This has fueled a surge in cyber insurance claims, which grew by 39% over a recent two year period. Ransomware, a particularly costly threat, saw average payment demands jump 60% in a single quarter, reaching $178,254 per incident.
In response to these trends, more organizations are seeking financial protection, with the percentage of companies purchasing cyber insurance rising from 26% in 2016 to 47% in 2020. However, insurers, facing unsustainable losses, have been forced to fundamentally alter their business model. The era of passive risk transfer, where a policy was granted based on a simple questionnaire, is over. Today, insurers are active participants in their clients' risk management programs. The underwriting process has evolved from a brief form filling exercise into a rigorous evaluation involving detailed, 30 plus page documents and even on site audits. This new model is predicated on risk mitigation; insurers will only cover organizations that can prove they have a robust security posture designed to prevent claims in the first place.
This dynamic has given rise to a new, powerful force in the cybersecurity landscape: the insurer as a de facto regulator. While government bodies like those enforcing the Health Insurance Portability and Accountability Act (HIPAA) or the General Data Protection Regulation (GDPR) impose penalties after an incident, insurers exert financial pressure before one occurs. The penalty for non compliance with an underwriter's standards is not a potential future fine but an immediate and certain financial impact in the form of prohibitively high premiums or an outright denial of coverage. Insurers, armed with vast amounts of claims data, mandate specific, pragmatic controls they know are effective at preventing losses, such as multi factor authentication (MFA), endpoint detection and response (EDR), and, critically, regular penetration testing. In doing so, they are establishing a "common law" of effective security, compelling a level of cybersecurity maturity that often exceeds the letter of traditional regulations. For a Chief Information Security Officer (CISO), the primary compliance audience is now twofold: the government regulator and the insurance underwriter, whose requirements carry direct and immediate consequences for the organization's financial health and operational viability.
In the rigorous new world of cyber insurance underwriting, demonstrating "due care" or "reasonable security" is paramount. Insurers no longer accept an organization's claims about its security at face value; they demand evidence. The gold standard for providing this evidence is the penetration test. Insurers explicitly require regular penetration testing because it demonstrates that an organization is proactively identifying, assessing, and mitigating its security risks. The inability to produce a recent, comprehensive penetration test report is a major red flag and a common reason for coverage denial.
A penetration test, also known as a pentest or ethical hacking, is a simulated cyberattack authorized by an organization to evaluate the security of its systems. Unlike automated scans that simply list potential vulnerabilities, a pentest involves skilled security professionals who mimic the tactics, techniques, and procedures of real world attackers to actively exploit weaknesses. This process provides an independent, third party validation of a security program's true effectiveness. It serves as tangible proof that the organization has exercised due diligence in protecting its assets.
For an underwriter, a pentest report answers the most critical question: Does this organization take security seriously?. It moves the assessment from the theoretical to the practical. For example, a claims adjusting organization used a penetration test not only to fulfill a compliance requirement but also to gauge its resilience to realistic attack scenarios. The test uncovered critical vulnerabilities related to social engineering that would have been missed by other assessment methods, demonstrating the unique and irreplaceable value of simulating a real world attack. By providing this level of validated insight, the penetration test has become an indispensable tool for any organization seeking to prove its insurability.
The decision to invest in penetration testing has a direct and measurable impact on an organization's finances, influencing not only the cost of insurance premiums but also the quality of the coverage obtained. A robust security posture, proven by a history of regular and thorough penetration testing, can lead to significantly lower premiums. Insurers are fundamentally in the business of pricing risk. An organization that can present a documented history of proactively finding and fixing security flaws is, by definition, a lower risk client and will be rewarded with more favorable terms.
Conversely, the absence of such proactive measures signals a higher risk of a claim, leading to higher premiums. The cost of a comprehensive penetration test should therefore be viewed as a strategic investment rather than a mere operational expense. The return on this investment is realized through direct premium savings and, more critically, by securing adequate coverage limits and avoiding policy exclusions that could render the insurance useless when it is needed most.
One of the most dangerous exclusions in a modern cyber insurance policy is for incidents arising from a known but unpatched vulnerability. If an organization is breached through a vulnerability that was publicly disclosed months prior and could have been identified by a standard pentest, the insurer may have grounds to deny the claim, arguing that the organization failed to exercise reasonable care. A regular pentesting program identifies these very issues, and the subsequent remediation efforts create a documented record of proactive risk management that can be indispensable during a claims dispute. Other common exclusions, such as those for acts of war or certain insider threats, also underscore the need for a clear understanding of what a policy does and does not cover, a process that is informed by the risk insights gained from penetration testing.
Understanding the reasons why cyber insurance claims are denied is essential for building a security program that meets underwriting standards. The most common reasons for denial are "policy exclusions" and "poor prevention practices". An insurer can and will reject a claim if the organization failed to implement the core security controls attested to in their application, such as MFA, network segmentation, or having a tested incident response plan. A critical and increasingly frequent point of failure is the inability to provide documentation of these preventative measures. The penetration test report is the primary form of this documentation.
Examining real world denial scenarios illustrates the importance of this process:
These scenarios reveal a crucial evolution in the role of the penetration test report. It has transcended its technical origins to become a quasi legal and financial artifact. An insurance policy is a contract, and the application forms the basis of that contract. Any misrepresentation on the application can render the contract void. The pentest report is the primary evidence that substantiates the security attestations made on that application. In the event of a claim, this report will be scrutinized by forensic investigators, auditors, and lawyers to determine if the organization met its contractual obligation to maintain a reasonable standard of care. Therefore, the report is no longer just a technical to do list for developers. It is a critical piece of evidence in a high stakes financial negotiation (underwriting) and potential future litigation (claims). This reality elevates the entire penetration testing process, making the careful selection of a vendor, meticulous definition of scope, and the clarity of the final report as important as the technical findings themselves.
Not all penetration tests are created equal. To satisfy the rigorous scrutiny of a cyber insurance underwriter, a pentest must be comprehensive, methodical, and focused on demonstrating real world risk. Merely checking a box is insufficient; the test itself must be defensible and its results must provide a clear, accurate picture of the organization's security posture. Understanding the key components of an insurance grade penetration test is the first step toward building a testing program that delivers both security and financial value.
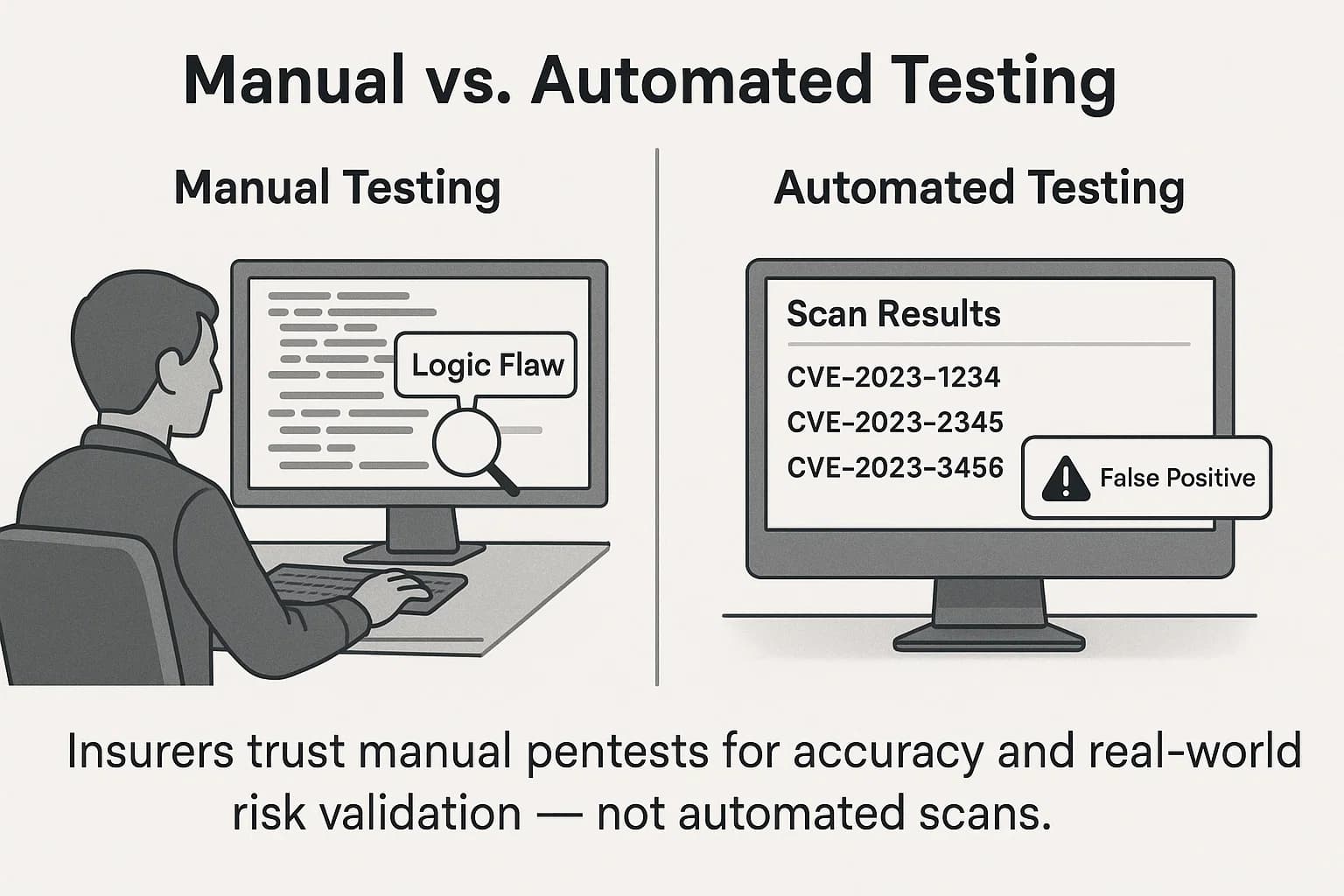
The most fundamental distinction in the world of security testing is between automated and manual approaches. While both have a role, underwriters place significantly more value on manual testing for its depth and accuracy.
For managers evaluating the cost, the justification for the higher price of a manual test lies in the quality and relevance of its findings to an insurer. An underwriter is less concerned with a long list of theoretical CVEs from an automated scanner and more interested in a validated, evidence backed report that shows which vulnerabilities truly pose a threat of financial loss.
1. Goal
Why it matters: Insurers aren’t just looking for a long list of theoretical issues they want to understand your true breach risk. Manual testing provides that assurance.
2. Accuracy
For underwriters: False positives waste your remediation budget and skew your actual risk profile something insurers use to determine your premiums and claim eligibility.
3. Depth of Analysis
Why underwriters care: The biggest breaches (and payouts) often stem from logic flaws in transactions, APIs, or access control not just outdated software.
4. Cost
Insurer perspective: Higher testing costs often signal stronger risk maturity and can translate to lower premiums or fewer exclusions.
5. Compliance & Insurability
Insurers and regulators both require human led testing for critical coverage thresholds.
Final Thought:
Automated scans are a helpful baseline, but they won’t get you far with underwriters. If you're serious about cyber insurance eligibility, lower premiums, and airtight claim coverage, manual penetration testing is the standard insurers actually trust.
A comprehensive testing strategy must evaluate security from two distinct perspectives: that of an outside attacker and that of an insider threat.
Insurers require visibility into both. A strong perimeter is essential, but it is no longer considered sufficient. The increasing sophistication of phishing and social engineering attacks means that initial access is often inevitable. The most damaging and costly claims, particularly from ransomware, arise from what happens after the initial breach. This reality has led to a significant shift in the underwriting mindset toward an "assumed breach" model. Insurers no longer just ask, "Can an attacker get in?" They now ask, "When an attacker gets in, how much damage can they do?" Data supports this focus; one analysis found that internal networks have nearly three times more exploitable vulnerabilities than external ones. The internal penetration test is the only reliable method to assess an organization's ability to contain a breach through controls like network segmentation and least privilege access. It has therefore become a mandatory data point for any sophisticated underwriting process.
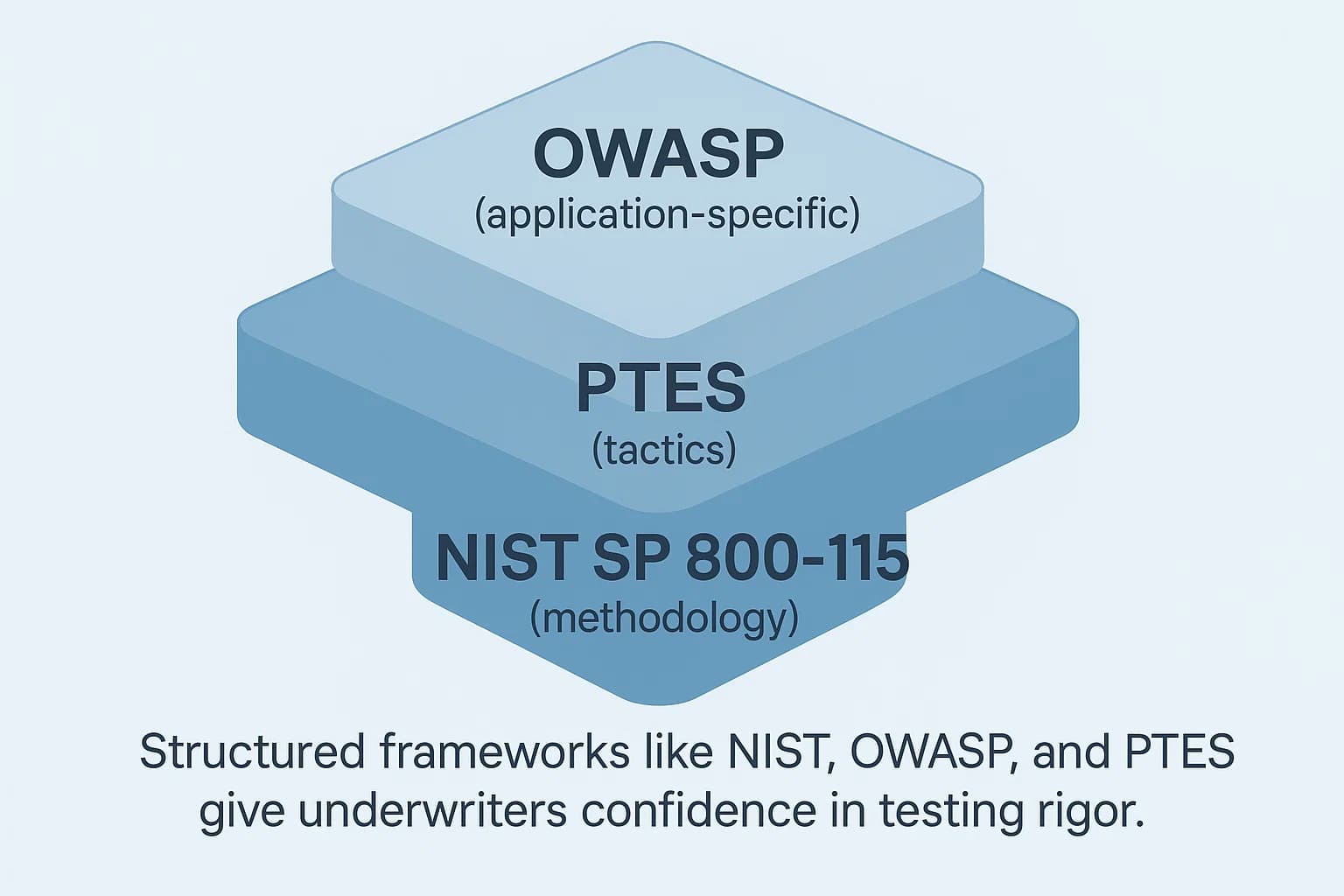
To ensure a penetration test is methodical, repeatable, and credible, it should adhere to an established industry framework. Referencing a recognized methodology in the test report signals to an underwriter that the assessment was a structured, professional engagement, not an ad hoc exercise. Key frameworks include:
The choice of framework may depend on the specific scope of the test, but the crucial point is that the test is grounded in a recognized, defensible methodology.
For the vast majority of modern businesses, web applications are a primary attack surface, used for everything from e-commerce to customer portals to internal operations. Consequently, the OWASP Top 10 has become a de facto benchmark for underwriters assessing application security risk.
The 2021 OWASP Top 10 includes critical risks such as:
From an underwriter's perspective, a penetration test report showing multiple, unmitigated OWASP Top 10 vulnerabilities in a critical application signals an unacceptably high level of risk. While tools like a Web Application Firewall (WAF) can help provide a first layer of defense against some of these threats, such as injection attacks , a manual penetration test is required to validate that these controls are working correctly and to identify flaws like insecure design or broken access control that automated tools and WAFs typically miss. Demonstrating that the organization has tested for and remediated the OWASP Top 10 is one of the most direct and effective ways to prove a mature application security program and improve insurability.
A significant, though often overlooked, benefit of a comprehensive penetration testing program is its ability to generate evidence that satisfies the requirements of multiple business functions simultaneously. A single, well scoped penetration test can provide the necessary documentation for cyber insurance underwriting, regulatory compliance audits, and customer due diligence requests. This creates a powerful return on investment, transforming a security expenditure into a strategic enabler that supports legal, compliance, and sales objectives.
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment.
The Health Insurance Portability and Accountability Act (HIPAA) Security Rule establishes national standards to protect individuals' electronic personal health information (ePHI) that is created, received, used, or maintained by a covered entity.
The General Data Protection Regulation (GDPR) is a landmark data privacy law from the European Union that governs the processing of personal data of EU residents.
A System and Organization Controls (SOC) 2 report is an audit of a service organization's systems and is based on the Trust Services Criteria (TSC) developed by the American Institute of Certified Public Accountants (AICPA). It is a key tool for B2B companies to demonstrate their security posture to customers.
By strategically planning a penetration testing program, a CISO can address these disparate requirements with a unified effort. The following table illustrates how different pentesting activities map to the requirements of various stakeholders, providing a powerful tool for building a comprehensive business case.
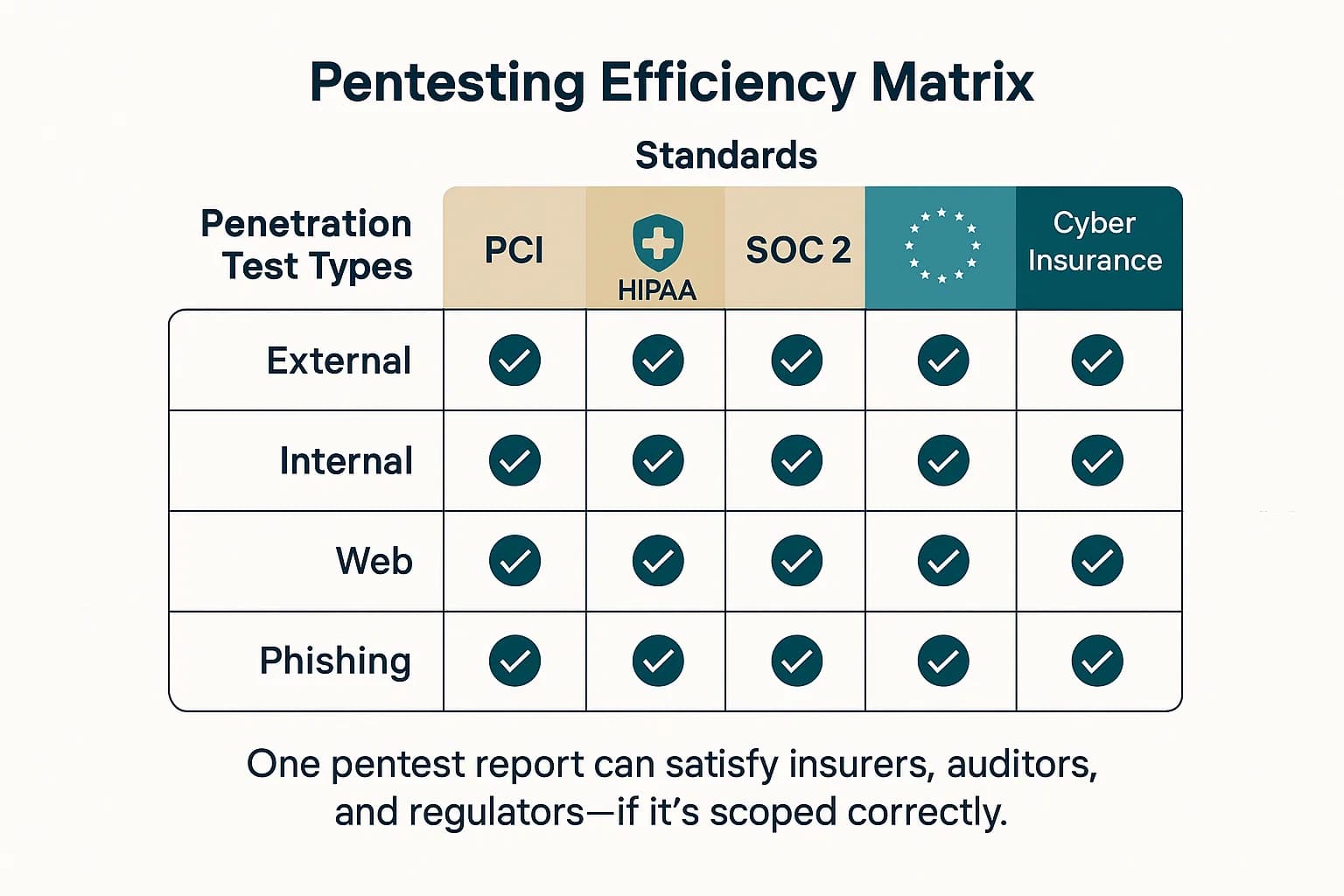
Which types of penetration tests satisfy both cyber insurance underwriters and regulatory compliance? Here's what you need to know organized by activity and mapped to PCI DSS, HIPAA, SOC 2, and GDPR.
External Network Penetration Test
Purpose:
Required for:
Internal Network Penetration Test (Segmentation)
Purpose:
Required for:
Purpose:
Required for:
Purpose:
Required for:
Final Note:
Cyber insurance underwriters now expect proof that your controls are working and regulators require specific types of testing to validate due diligence. Use this matrix as your checklist for both compliance and insurability.
Transitioning from understanding the "why" and "what" of insurance grade penetration testing to the "how" requires a structured, deliberate approach. Executing a successful pentest that meets the expectations of underwriters, auditors, and internal stakeholders is a multi phase process. This playbook provides a practical, step by step guide to navigating the engagement from initial planning to final reporting, ensuring the organization maximizes the value and impact of its investment.
The scoping phase is the most critical stage of a penetration test; it lays the foundation for the entire engagement. An improperly scoped test can result in wasted resources, missed vulnerabilities, and a final report that fails to satisfy the underwriter. The objective is to define clear boundaries, objectives, and rules of engagement that align the technical testing activities with the organization's business and insurance goals.
The organization must lead this process, providing the necessary context for the testing vendor. Key considerations during the scoping call should include:
The quality of a penetration test is directly dependent on the skill and professionalism of the vendor conducting it. A low cost provider that delivers a superficial report can be worse than no test at all, as it may provide a false sense of security and fail to meet insurer requirements. Vetting a potential vendor should be a rigorous process.
A comprehensive vendor questionnaire should include the following areas:
The final report is the primary deliverable of the penetration test and the main artifact that will be reviewed by third parties. A high quality report must be tailored to multiple audiences.
A standard, comprehensive report should contain:
In addition to the full report, organizations should request a separate Attestation Letter (also called a Certification Letter) from the vendor. This is a concise, one page document on the vendor's letterhead that is specifically designed to be shared with external parties like insurers or customers. It typically includes:
This letter provides the necessary proof of testing to an underwriter without disclosing sensitive details about specific vulnerabilities, which should remain confidential.
The purpose of a penetration test is not merely to find vulnerabilities but to drive their remediation. A report filled with unaddressed critical findings is a liability, not an asset, when presented to an insurer. It demonstrates knowledge of a risk without the corresponding action to fix it.
The post testing phase is therefore just as important as the test itself. The process should follow a clear loop:
This closed loop process demonstrates a mature, functioning risk management program exactly the kind of proactive posture that underwriters are looking to insure.
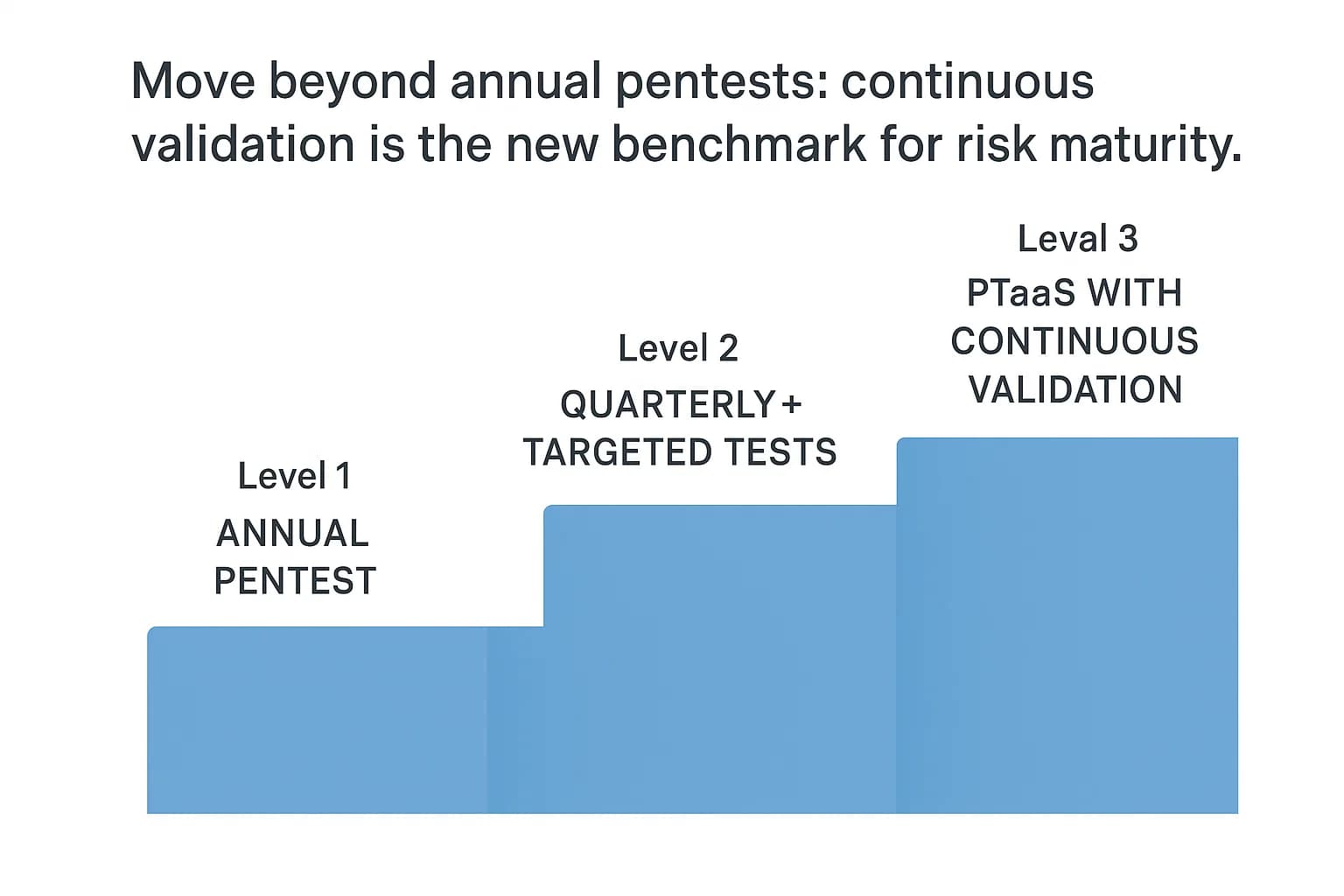
Successfully navigating the cyber insurance landscape requires more than just executing a single, point in time penetration test. It demands a strategic, forward looking approach to risk management. For senior leadership, the goal should be to embed security testing into the fabric of the organization's operations, transforming it from a reactive, compliance driven exercise into a continuous program that builds long term resilience and provides a durable competitive advantage.
The threat landscape is not static; new vulnerabilities are discovered daily, and attackers are constantly refining their techniques. While an annual penetration test is the established baseline for insurance and compliance, it provides only a snapshot of an organization's security posture at a single moment in time. A company could receive a clean report in January and be vulnerable to a new exploit by March.
To address this gap, leading organizations are moving toward a model of continuous security validation. This can involve several approaches:
Adopting a more continuous testing model sends a powerful signal to insurers. It demonstrates an exceptional level of security maturity and a commitment to proactive risk management that goes beyond the minimum requirements. This can be a powerful negotiating tool, potentially unlocking the best possible premiums and the most favorable coverage terms.
The cyber insurance industry itself is rapidly evolving, driven by data analytics and automation. The future of underwriting will be even more data driven and less reliant on static questionnaires. Insurers are increasingly using their own automated tools to continuously scan the external attack surface of their applicants and clients. This practice, known as Attack Surface Management (ASM), gives them a real time view of an organization's exposed assets and potential vulnerabilities.
Furthermore, the rise of Artificial Intelligence (AI) will impact both attackers and defenders. Attackers will use AI to craft more sophisticated phishing campaigns and discover vulnerabilities faster. Defenders and insurers will use AI to analyze vast datasets to model risk and detect anomalies. The Cybersecurity and Infrastructure Security Agency (CISA) has already begun issuing guidance on securing the data used to train and operate AI systems, recognizing it as a new frontier of risk.
Organizations that proactively adopt these future facing technologies will be better positioned in the insurance marketplace. A company that already has its own robust ASM program and a continuous testing model will have a security posture that is always "underwriter ready." They will be able to identify and remediate exposures before an insurer's scanner does, maintaining a consistently strong and defensible risk profile.
For the CEO, CFO, Board of Directors, and other senior leaders, the complex world of cybersecurity insurance and penetration testing can be distilled into a clear set of strategic actions. This plan synthesizes the key takeaways of this report into a high level roadmap for success.
What role does penetration testing play in cyber insurance eligibility?
Penetration testing is a critical, and often mandatory, component of cyber insurance eligibility. Insurers require penetration tests to get a clear, evidence based assessment of an organization's security posture and overall risk profile. A formal pentest report demonstrates that a company is taking cybersecurity seriously and exercising "due care" to protect its systems. The findings help underwriters determine whether a business qualifies for coverage and on what terms.
How often should we conduct pentests to stay compliant with insurers?
The standard baseline required by most cyber insurance providers is an annual penetration test. However, best practice, and a requirement for some regulations like PCI DSS, is to also conduct a pentest after any significant changes to your IT environment. While an annual test is often the minimum, moving to a more frequent or continuous testing schedule can further improve your risk profile and potentially lead to better insurance terms.
What kind of penetration test do underwriters want?
Underwriters want to see a comprehensive, insurance grade penetration test, not just an automated vulnerability scan. This means a test that includes both external and internal assessments to evaluate perimeter security and insider threats. Insurers place a high value on manual testing performed by skilled ethical hackers who can identify complex business logic flaws and chained exploits that automated tools would miss. The test should be conducted using a recognized methodology, such as those from NIST or OWASP, to ensure a thorough and professional assessment.
Can a missing pentest void your insurance claim?
Yes, it is possible. If an organization states in its insurance application that it performs regular penetration tests but fails to do so, an insurer may deny a claim based on misrepresentation or a failure to maintain the required security controls. Insurers expect policyholders to demonstrate "due care" in protecting their assets, and not performing a promised pentest can be seen as a failure to meet this standard, potentially voiding the policy or leading to a claim denial. According to one report, 43% of companies could have their insurance coverage voided for having insufficient security controls in place.
What’s the difference between a vulnerability scan and an insurance grade pentest?
A vulnerability scan is an automated process that uses software to check for a list of known, potential vulnerabilities, but it is prone to false positives and cannot find complex or novel flaws. An insurance grade penetration test is a much more in depth, hands on assessment conducted by human security experts. These ethical hackers don't just find vulnerabilities; they actively attempt to exploit them to prove real world risk, identify business logic errors, and validate findings to eliminate false positives. Insurers value the deep, contextual analysis of a manual pentest far more than a high level automated scan.
Don't let a compliance gap or outdated scan void your cyber insurance claim. Book a Free Coverage Readiness Review with our pentesting experts.
About the Author
Mohammed Khalil, CISSP, OSCP, OSWE
Mohammed Khalil is a cybersecurity architect specializing in advanced penetration testing, offensive security operations, and secure DevSecOps pipeline integration. With over a decade of experience in cloud native security, vulnerability management, and audit driven assurance, he helps enterprises design and implement PTaaS solutions aligned with compliance frameworks like SOC 2, PCI DSS, HIPAA, and ISO 27001.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us