September 6, 2025
Updated: September 6, 2025
Fresh data on who’s exploiting zero-days, which vendors are hit, and how to respond in 72 hours.
Mohammed Khalil


What are the latest zero-day exploit statistics, and why should they command your immediate attention? The data is in, and it paints a stark picture of a threat landscape that has fundamentally shifted. While the total number of detected zero-day exploits fluctuates year to year, the overall volume of attacks has stabilized at a new, elevated baseline, far exceeding levels seen before 2021.
Here’s the deal: According to Google's Threat Intelligence Group (GTIG), 75 zero-days were actively exploited in the wild in 2024. But the real story isn't just the number, it's the target. We're witnessing a dramatic and calculated pivot by adversaries. Attacks targeting enterprise specific technologies skyrocketed, accounting for 44% of all zero-day exploits, with a laser focus on security and networking products like VPNs and firewalls (Google Threat Intelligence Group, 2025).
This trend is powerfully corroborated by Mandiant's M Trends 2025 report, which confirms that for the fifth consecutive year, exploits are the number one initial infection vector, responsible for 33% of all breaches investigated. Zero-days are no longer a niche threat reserved for high stakes espionage; they are now the primary tool of choice for breaking into corporate networks. Understanding these cybersecurity vulnerability statistics is critical for shaping a defense that can withstand the realities of 2025.
To effectively defend against this threat, it’s crucial to speak the same language. The term " zero-day" is often used loosely, but in cybersecurity, precision is everything. The threat is composed of three distinct stages: the vulnerability, the exploit, and the attack.
Distinguishing between these terms is vital. A vulnerability is a static condition; an attack is an active, malicious event.
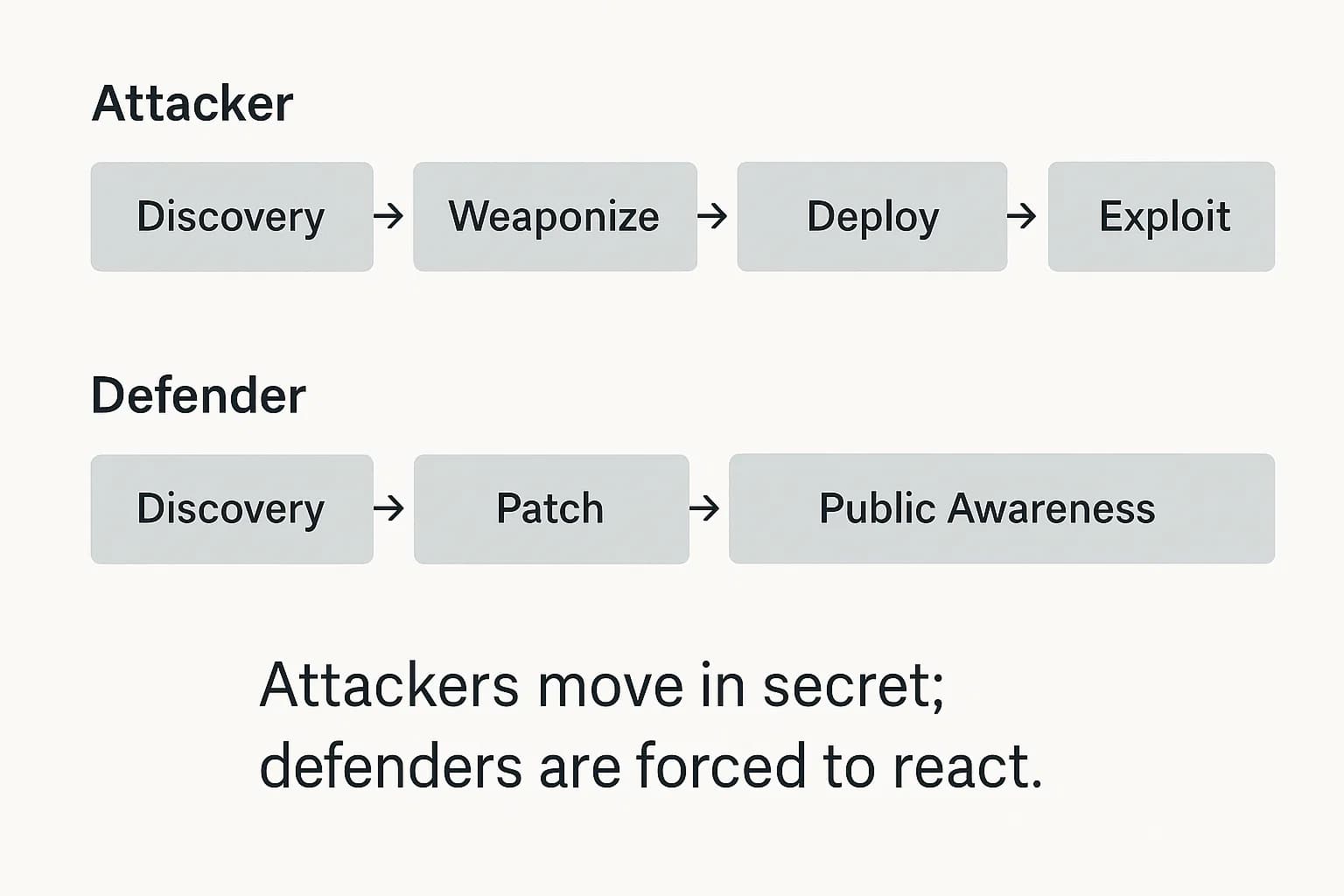
The core strategic challenge of defending against zero-days lies in the profound asymmetry between the attacker's and the defender's operational cycles. Attackers operate in secret, while defenders are forced to react to public information, creating a significant time gap advantage for the adversary. For a deeper dive, explore the complete zero-day exploit lifecycle and prevention process.
The attacker centric lifecycle is entirely covert and designed to maximize the exploit's operational lifespan:
The defender centric lifecycle, in stark contrast, is inherently reactive and only begins once the vulnerability becomes known:
The entire attacker lifecycle can be completed before the defender's response even begins. This fundamental imbalance means a security model based solely on preventative patching is mathematically certain to fail against a determined adversary.
When viewed together, the data from leading threat intelligence organizations like Google, Mandiant, and CISA paints a clear and alarming picture of the current threat landscape. These are not isolated data points; they are interconnected pieces of a single narrative that every security leader needs to understand.
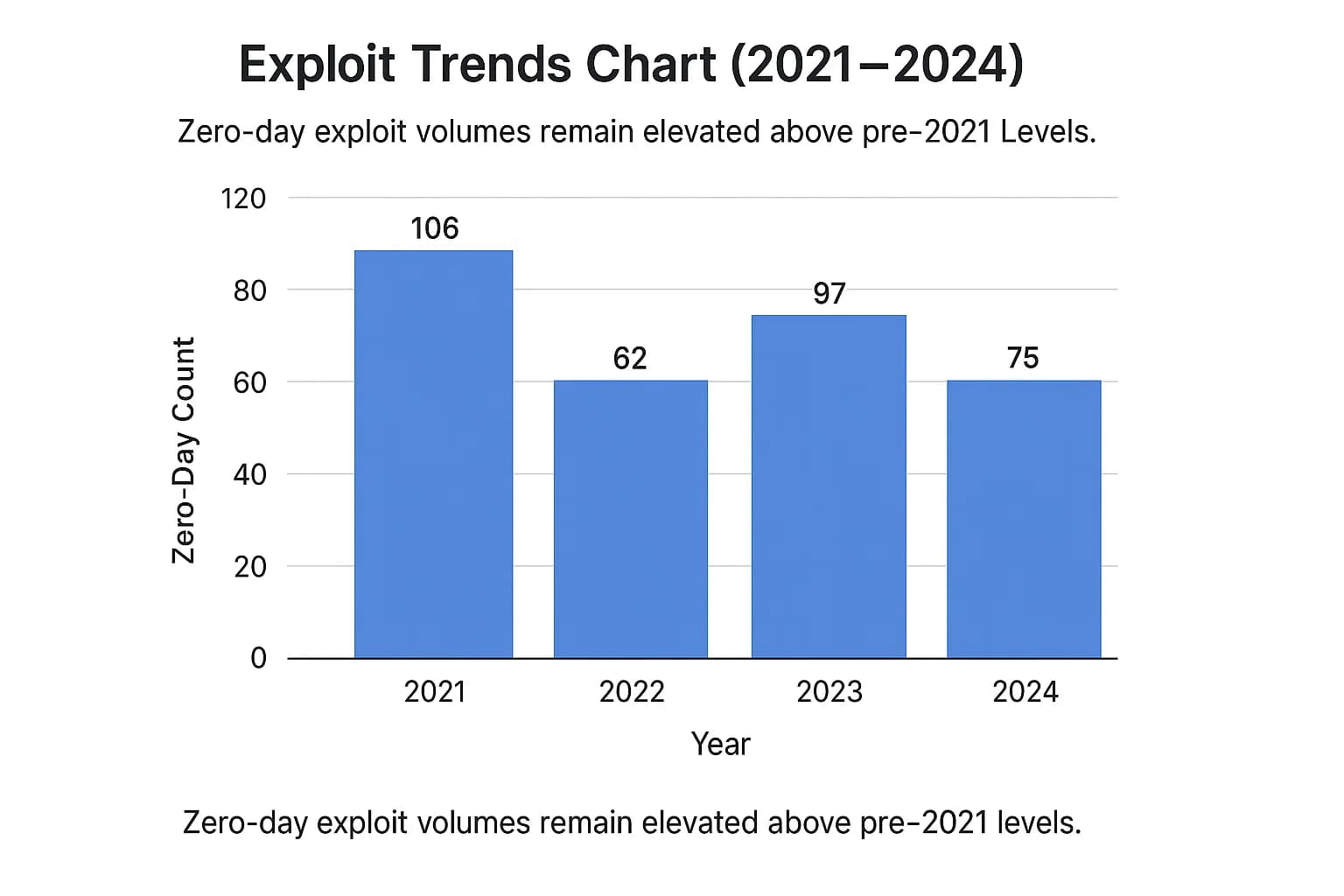
The top line numbers show that while the volume of zero-day exploitation fluctuates, it has settled into a new, higher tier of activity.
zero-day Exploits Detected In the Wild (2021 2024)
While the 75 in the wild zero-days tracked by Google in 2024 represent a decrease from 97 in 2023, it's still significantly higher than the 62 observed in 2022 (Google Threat Intelligence Group, 2025). This data shows that the massive spike in 2021 was not an anomaly but the start of a "new normal" where 60 100 exploited zero-days per year is the expected baseline.
Perhaps more alarming is the collapsing "Time to Exploit" , the window between a vulnerability's public disclosure and its active use in attacks. In 2024, this window shrank to an average of just five days, down from 32 days in previous years (CyberMindr, 2025). This acceleration, likely driven by automated exploit development pipelines, renders traditional monthly patch management cycles dangerously obsolete.
Mandiant's M Trends 2025 report provides the crucial "how" behind modern breaches. For the fifth year running, exploits were the most common initial infection vector, accounting for 33% of all intrusions Mandiant investigated (Mandiant M Trends 2025). This finding solidifies exploits as the primary method attackers use to gain their initial foothold.
Key findings from the report include:
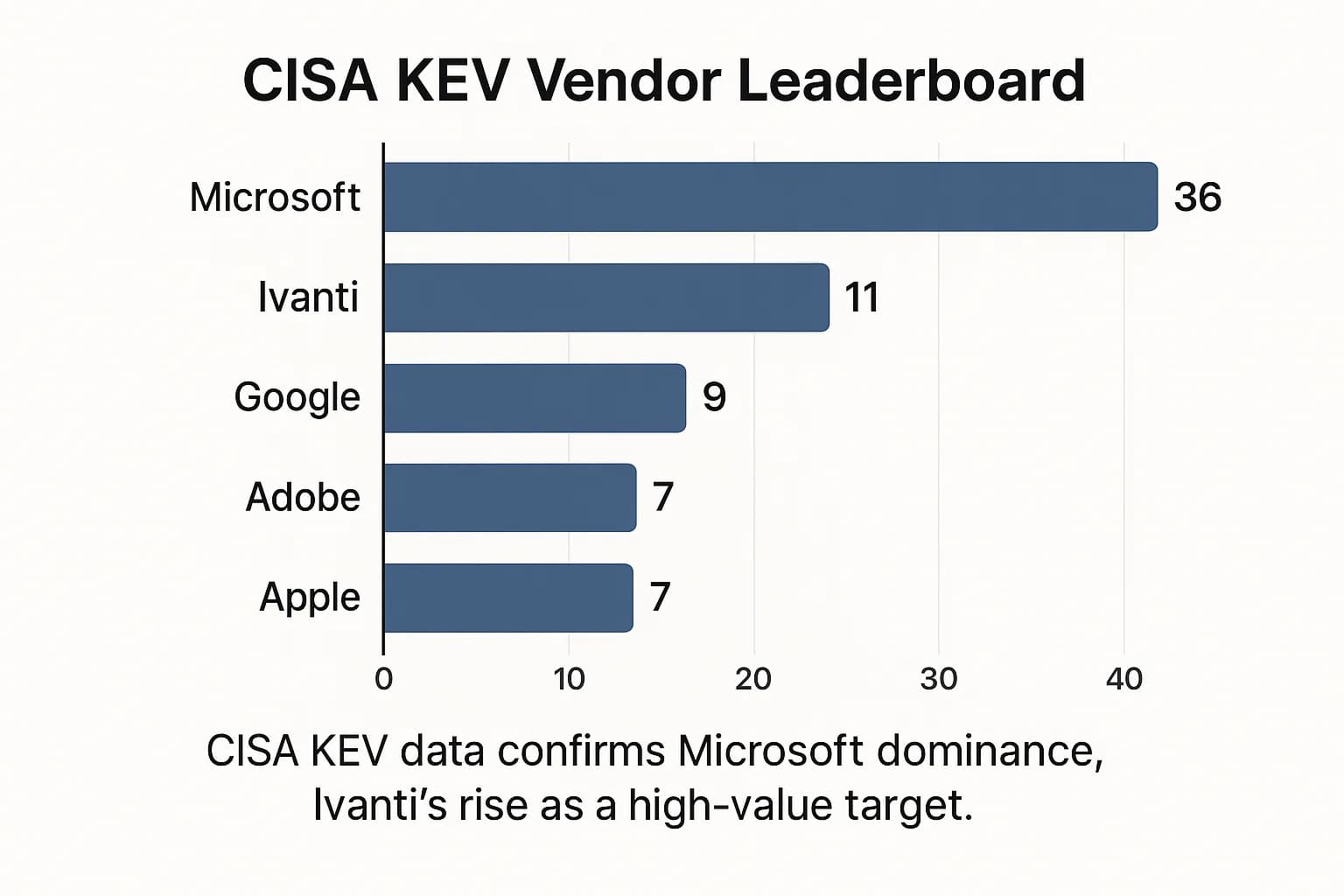
The CISA Known Exploited Vulnerabilities (KEV) catalog
provides ground truth data on which specific products and flaw types are under active attack. In 2024, CISA added 186 new vulnerabilities to the KEV list, requiring federal agencies to patch them on an accelerated timeline.
Top Targeted Vendors in CISA KEV Catalog (2024 Additions)
The data is revealing. Microsoft, with its massive install base, remains the top target. However, seeing Ivanti, an enterprise VPN provider, as the second most exploited vendor, ahead of giants like Google and Apple, is a powerful data point. It provides government validated proof that attackers are focusing their most potent weapons on the enterprise perimeter.
Furthermore, the most common weakness type added to the KEV catalog was OS Command Injection (CWE 78), a class of vulnerability that gives an attacker direct control over the compromised system. This shows a clear preference for flaws that provide immediate, high impact access.
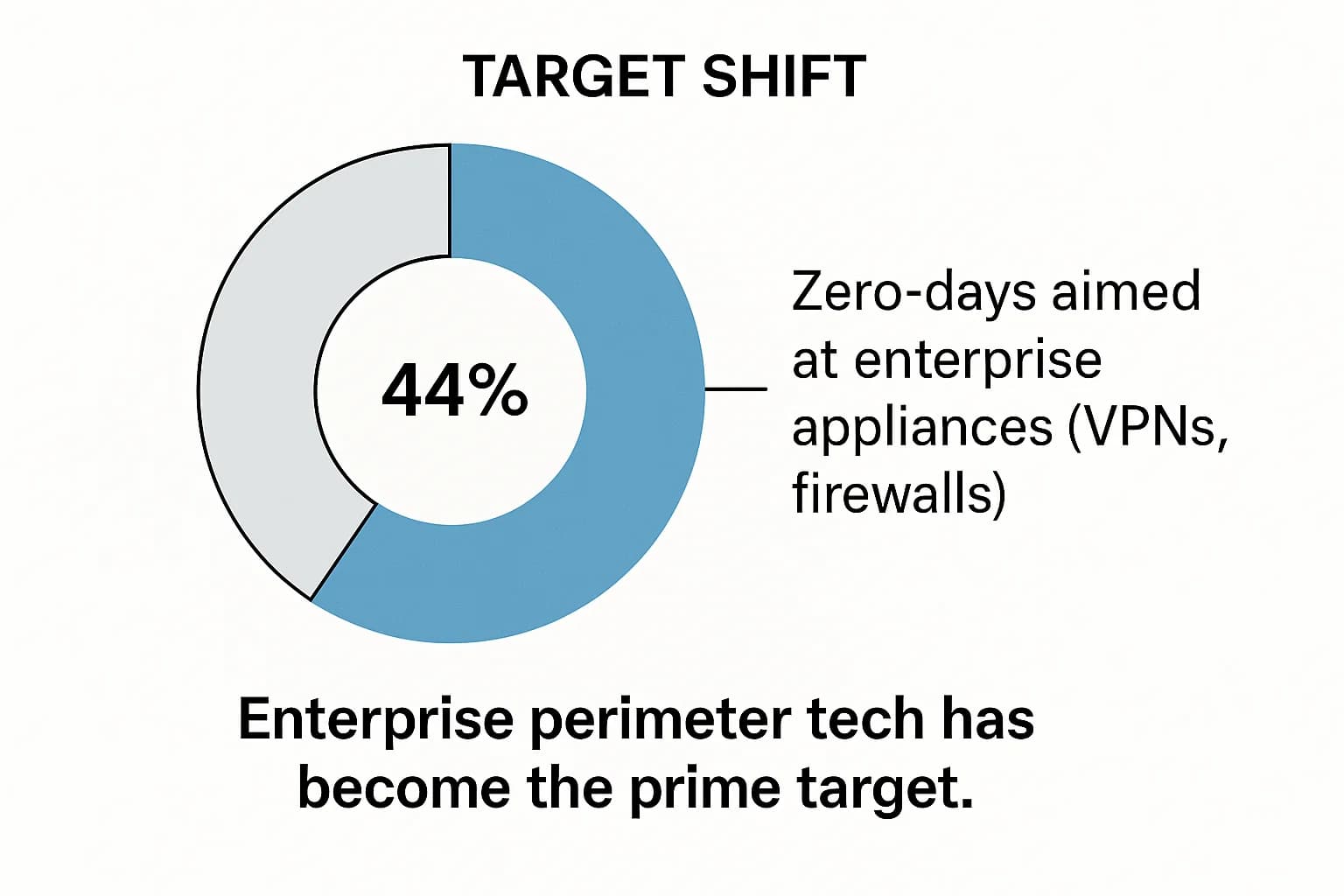
The statistics reveal a clear, deliberate shift in attacker strategy. The days of focusing primarily on end user devices like iPhones and laptops are waning. The new front line in the war against zero-days is your corporate network's edge.
This strategic pivot is not random; it's a direct response to successful defensive investments by major technology vendors. Over the past several years, companies like Google and Apple have poured immense resources into hardening their platforms.
Security features like Google Chrome's MiraclePtr, which eliminates entire classes of memory corruption bugs, and Apple's Lockdown Mode for iOS have significantly raised the bar for attackers. The results are measurable: in 2024, browser based zero-day exploits dropped by roughly a third, and mobile OS exploits were cut in half compared to 2023 levels (Google Threat Intelligence Group, 2025).
This success has displaced attackers, forcing them to find softer, higher value targets. They found them in enterprise infrastructure. The proportion of zero-days targeting enterprise specific products has steadily climbed, jumping from 37% in 2023 to 44% in 2024 (Google Threat Intelligence Group, 2025). Within that category, security and networking appliances, the very devices meant to protect the network, accounted for over 60% of the zero-days. These devices are ideal targets: they are internet facing by design, often run with high privileges, and a single compromise can provide a gateway to the entire internal network.
The sustained campaign against Ivanti Connect Secure VPNs is a perfect case study of this trend in action. A suspected China nexus espionage group, tracked as UNC5221, demonstrated high sophistication by chaining multiple zero-day vulnerabilities (CVE 2023 46805 and CVE 2024 21887) to achieve unauthenticated remote code execution on internet-facing VPN appliances.
Mandiant's investigation revealed that exploitation began as early as December 3, 2023, well over a month before Ivanti's public disclosure. Once inside, the attackers deployed a suite of custom webshells (with names like LIGHTWIRE, WIREFIRE, and BUSHWALK) to maintain persistence. They also stole device configuration data, harvested credentials, and even manipulated the built in Integrity Checker Tool to cover their tracks and evade detection. This campaign is a textbook example of nation state actors targeting critical edge infrastructure as a primary vector for espionage.
The list of most targeted vendors confirms this strategic shift:
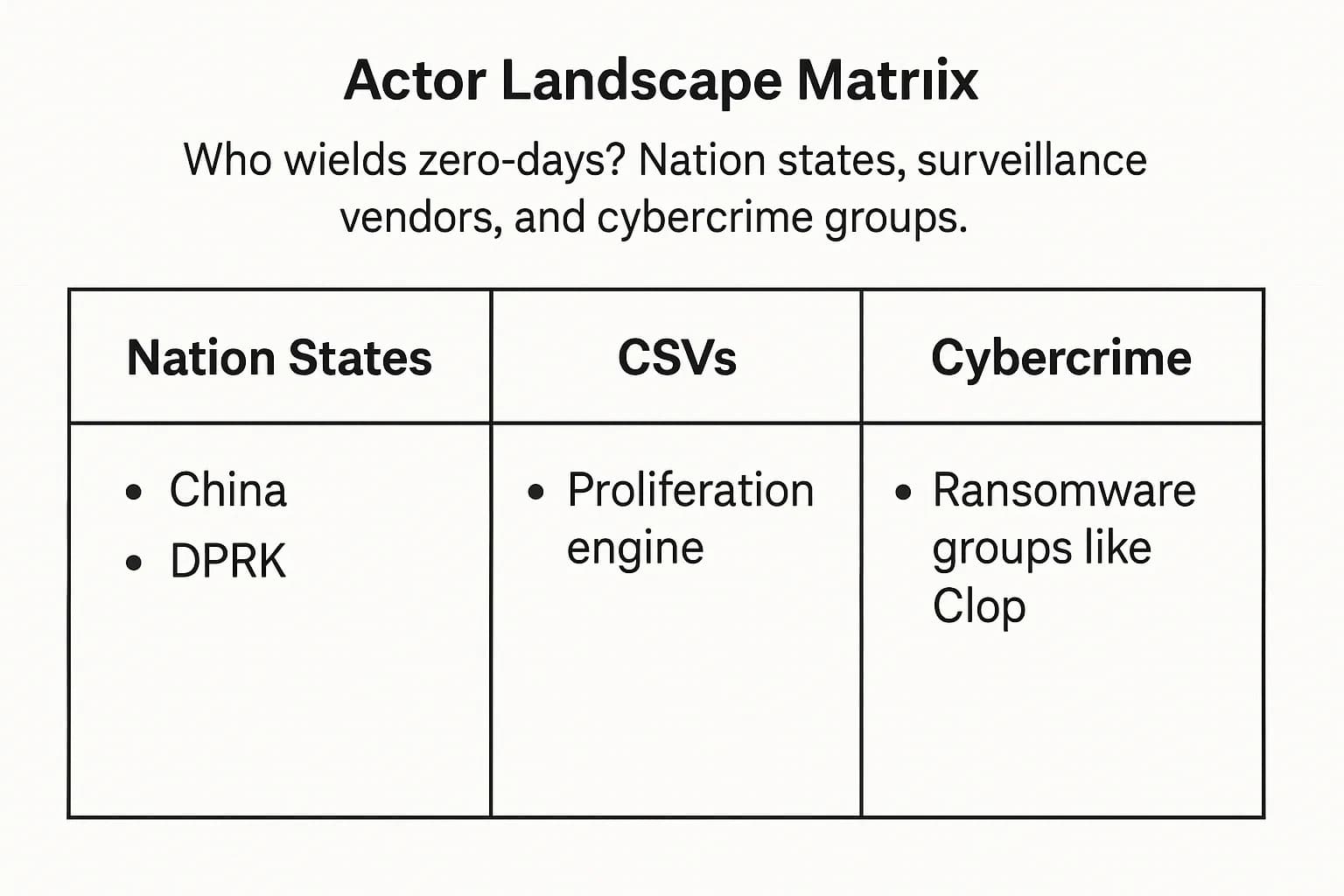
The ecosystem of threat actors developing and deploying zero-days is a complex mix of nation state intelligence services, a booming private sector of commercial surveillance vendors (CSVs), and the upper echelon of financially motivated cybercriminals.
Myth vs Fact Myth: zero-day attacks are only used by nation state spies. Fact: While nation states are major players, top tier cybercrime groups, especially ransomware gangs like Clop, now regularly use zero-days to execute large scale, financially motivated attacks.
Nation state sponsored groups remain the primary drivers of zero-day exploitation, using these capabilities for strategic intelligence gathering and geopolitical advantage.
A significant and growing portion of the zero-day market is occupied by Commercial Surveillance Vendors (CSVs). These private companies develop and sell sophisticated exploits and spyware, primarily to government customers who may lack their own internal development capabilities.
CSVs act as a proliferation engine, increasing global access to advanced offensive tools. In 2023, they were responsible for over 60% of all browser and mobile device zero-day exploits. In 2024, Google attributed eight of the 75 tracked zero-days to CSV customers. Their activity makes attribution more difficult and lowers the barrier to entry for a wider range of state actors to conduct surveillance operations.
The traditional distinction between sophisticated state sponsored espionage and financially motivated crime is eroding. This is best exemplified by the devastating MOVEit Transfer campaign. The Clop ransomware gang, a financially motivated cybercrime group, exploited a critical SQL injection zero-day (CVE 2023 34362) in the popular MOVEit managed file transfer (MFT) software.
This was a classic supply chain attack executed with nation state level capability. By targeting a single, widely used piece of enterprise software, Clop achieved a massive scale of compromise, exfiltrating huge volumes of sensitive data from thousands of downstream organizations for extortion. This campaign proved that top tier criminal organizations now possess and deploy zero-day capabilities, applying them to their brutally efficient business model of data theft and extortion. The implication for defenders is stark: you can no longer assume the motive of an attacker based on the sophistication of their tools.
The trade in zero-day vulnerabilities is a secretive, multi million dollar global market. Prices are dictated by the target's popularity, its security posture, and the exploit's reliability and impact. Understanding the penetration testing cost and Vulnerability Assessment Pricing models provides a baseline for how much organizations are willing to spend to find flaws before attackers do.
The market operates across three distinct tiers:
The value of a zero-day exploit is a direct reflection of the difficulty in achieving a compromise. Prices have been inflating at an estimated 44% annually, with mobile devices and encrypted messaging apps commanding the highest premiums.
The legitimate bug bounty market effectively sets the price floor for the illicit markets. To persuade a top researcher to take on the immense legal and ethical risks of selling on the gray market, brokers must offer payouts that are orders of magnitude higher than what a vendor like Apple or Google would pay. This creates an economic arms race for both vulnerabilities and the elite talent that discovers them.
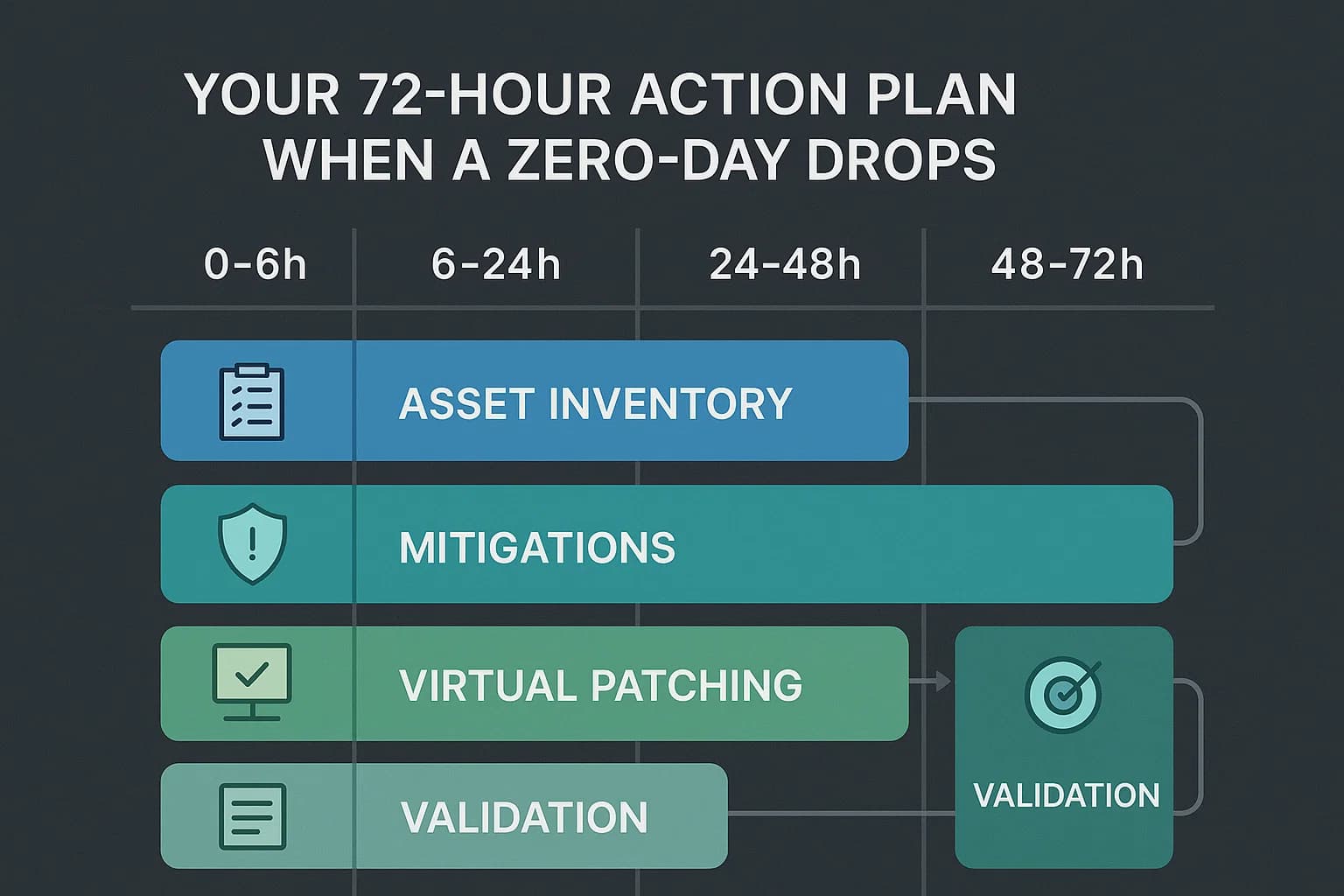
When a critical zero-day is disclosed, the clock starts ticking. The days of waiting for a patch are over. Your team needs a rapid response plan to contain risk before it spreads. This checklist, designed for the first 72 hours, helps you act decisively even when no patch is available.
Given the statistics, a security strategy based solely on preventing breaches is destined to fail. The strategic goal must shift from perfect prevention to organizational resilience operating under the assumption that a compromise will occur and focusing investments on minimizing its impact.
Myth: A rigorous patch management program is the best defense against exploits.
Fact: Patching is essential, but it's a reactive measure that is insufficient against modern threats.
The data is unequivocal. In 2023, nearly 70% of in the wild exploits were zero-days, meaning they were used before a patch was available. Furthermore, with the average time to exploit for n day vulnerabilities now at just five days, attackers can weaponize a publicly disclosed flaw faster than most organizations can test and deploy the corresponding patch.
The Microsoft Exchange ProxyLogon crisis of 2021 serves as a critical lesson in this "disclosure race". After Microsoft released emergency patches for four zero-days, a feeding frenzy ensued. More than a dozen threat groups began mass scanning the internet, compromising tens of thousands of servers that remained unpatched. For these organizations, the window between patch availability and widespread exploitation was measured in hours, not weeks.
A resilient defense strategy must be proactive and assume compromise. Aligning your efforts with established frameworks like the NIST Cybersecurity Framework (CSF) provides a structured path forward.
While you can't predict the next specific zero-day, you can proactively identify and remediate the classes of vulnerabilities that are most commonly exploited, such as SQL injection, command injection, and deserialization flaws. This is where offensive security testing becomes a critical component of a resilient defense.
Engaging in regular penetration testing services for businesses allows you to simulate the actions of a real world attacker. Experienced testers can identify weak points in your perimeter, find misconfigurations in your security appliances, and discover vulnerabilities in your web applications that could be exploited. Understanding the difference between internal and external penetration tests helps you assess threats from both outside and inside your network.
For organizations with mature security programs, a continuous penetration testing platform provides ongoing validation of your security posture. This approach moves beyond point in time assessments to offer persistent testing that can identify new risks as your environment changes. Ultimately, the goal of a vulnerability assessment vs penetration testing is not just to find flaws, but to test the effectiveness of your detection and response capabilities against the very TTPs used by groups like UNC5221 and Clop.
How many zero-days were exploited in 2024 vs 2023?
In 2024, 75 zero-days were exploited in the wild, which was a decrease from the 97 detected in 2023. However, this number is still significantly higher than the 62 from 2022, indicating that overall activity remains at an elevated new baseline (Google Threat Intelligence Group, 2025).
Why are VPNs and firewalls the new zero-day hot spot?
Attackers are pivoting to enterprise appliances because consumer platforms like iOS and Chrome have become much harder to exploit due to vendor security investments. VPNs and firewalls are ideal targets because they are internet facing, highly privileged, and a single compromise can provide a gateway into an entire corporate network.
How fast do attackers weaponize a vulnerability after it's disclosed?
The average "Time to Exploit" for a publicly disclosed vulnerability (an n day) has collapsed to just five days in 2024. This is a dramatic acceleration from previous years and means attackers can develop a working exploit and launch attacks before most organizations complete their monthly patch cycle.
What’s the difference between a zero-day vs N day exploit?
A zero-day exploit targets a vulnerability that is unknown to the vendor, meaning no patch exists. An N day exploit targets a known vulnerability after a patch has been released, preying on organizations that have not yet applied the security update.
What were the top vendors targeted by zero-days in 2024?
Microsoft (26 exploits) and Google (11 exploits) remained the most targeted due to their massive market share. However, the most significant trend was the targeting of 18 unique enterprise vendors, with Ivanti being a prominent example, highlighting a diversification of attacker focus (Google Threat Intelligence Group, 2025).
What is a real world example of a zero-day attack?
Famous examples include Stuxnet (2010), which used four Windows zero-days to damage Iran's nuclear program, and the MOVEit campaign (2023), where the Clop ransomware group exploited a zero-day to steal data from thousands of organizations.
Can you fully protect against zero-day attacks?
No, complete prevention is impossible because the vulnerability is unknown to defenders by definition. The goal is not perfect prevention but resilience, the ability to rapidly detect, contain, and recover from an attack to minimize business impact.
The statistics for 2024 and 2025 are not just numbers; they are a clear directive for security leaders. The sustained high volume of in the wild exploitation, the decisive pivot to enterprise infrastructure, and the convergence of nation state and criminal actor capabilities prove that the threat landscape has evolved. A defense strategy rooted in reacting to known threats is no longer viable. The modern imperative is to build a resilient security posture, one that assumes compromise, prioritizes visibility and containment, and continuously validates its defenses against the tactics being used by adversaries today.
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
About the Author
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us