Updated: August 3, 2025
Credential theft, AI-powered phishing, and Ransomware-as-a-Service are redefining risk in the most targeted sectors from manufacturing to healthcare and finance.
Mohammed Khalil

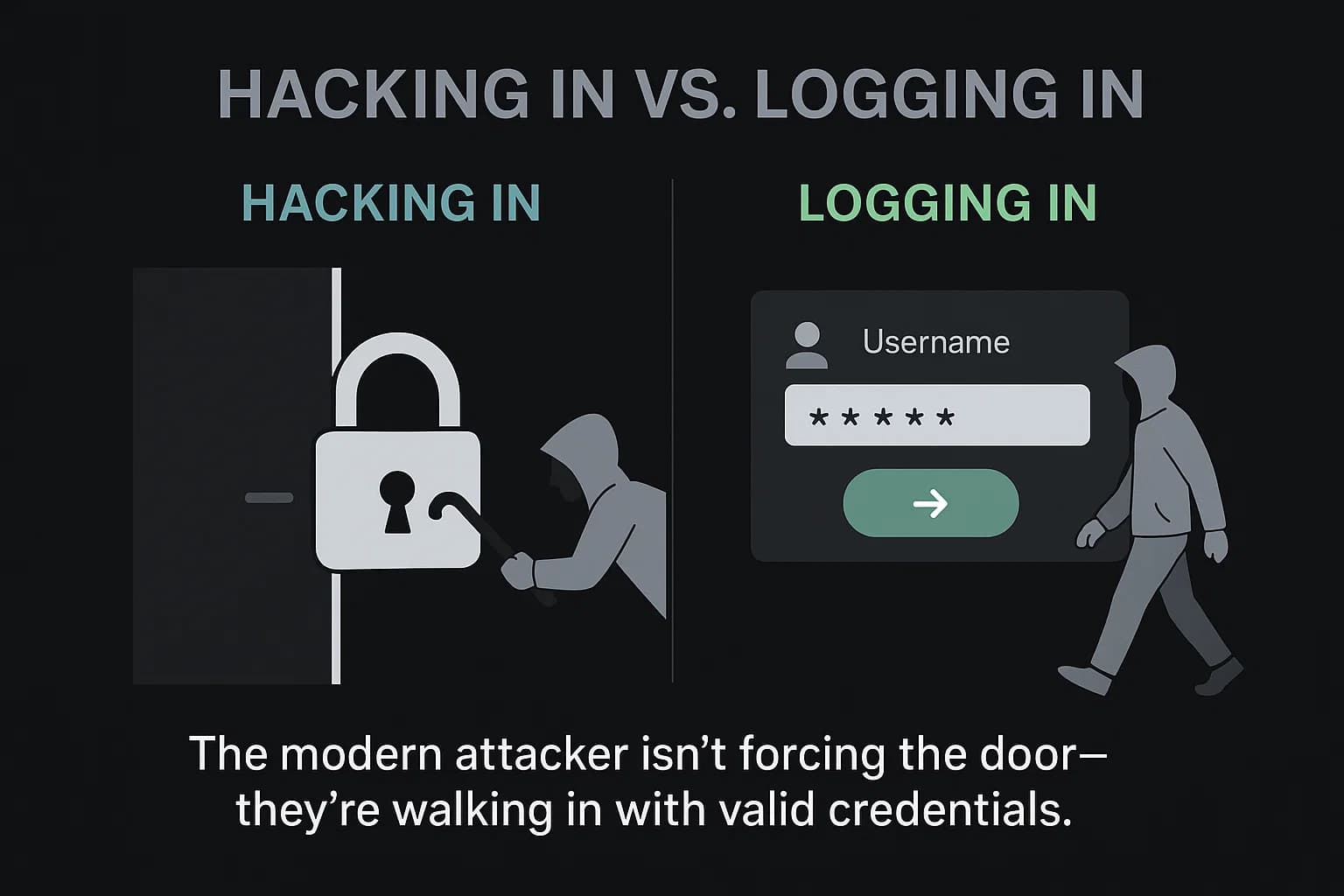
In 2025, understanding the top industries targeted by hackers requires looking beyond the headlines. The central truth of the modern cyber threat landscape is a quiet but profound shift in attacker methodology. The era of noisy, brute force network breaches is being eclipsed by a far more insidious approach: attackers are no longer just hacking in; they are simply logging in.
Data from the IBM X Force Threat Intelligence Index 2025 reveals that abusing valid accounts is now the preferred entry point for cybercriminals, accounting for 30% of all incidents. This strategic pivot is driven by simple logic: it’s stealthier, more effective, and bypasses many traditional defenses. By using legitimate credentials, attackers blend in with normal network traffic, making their malicious activities incredibly difficult to detect.
This new reality, which defines the primary cyber threats 2025 will bring, is shaped by three powerful forces:
Understanding these macro trends is the first step to building a defense that can withstand the attacks of today and tomorrow.
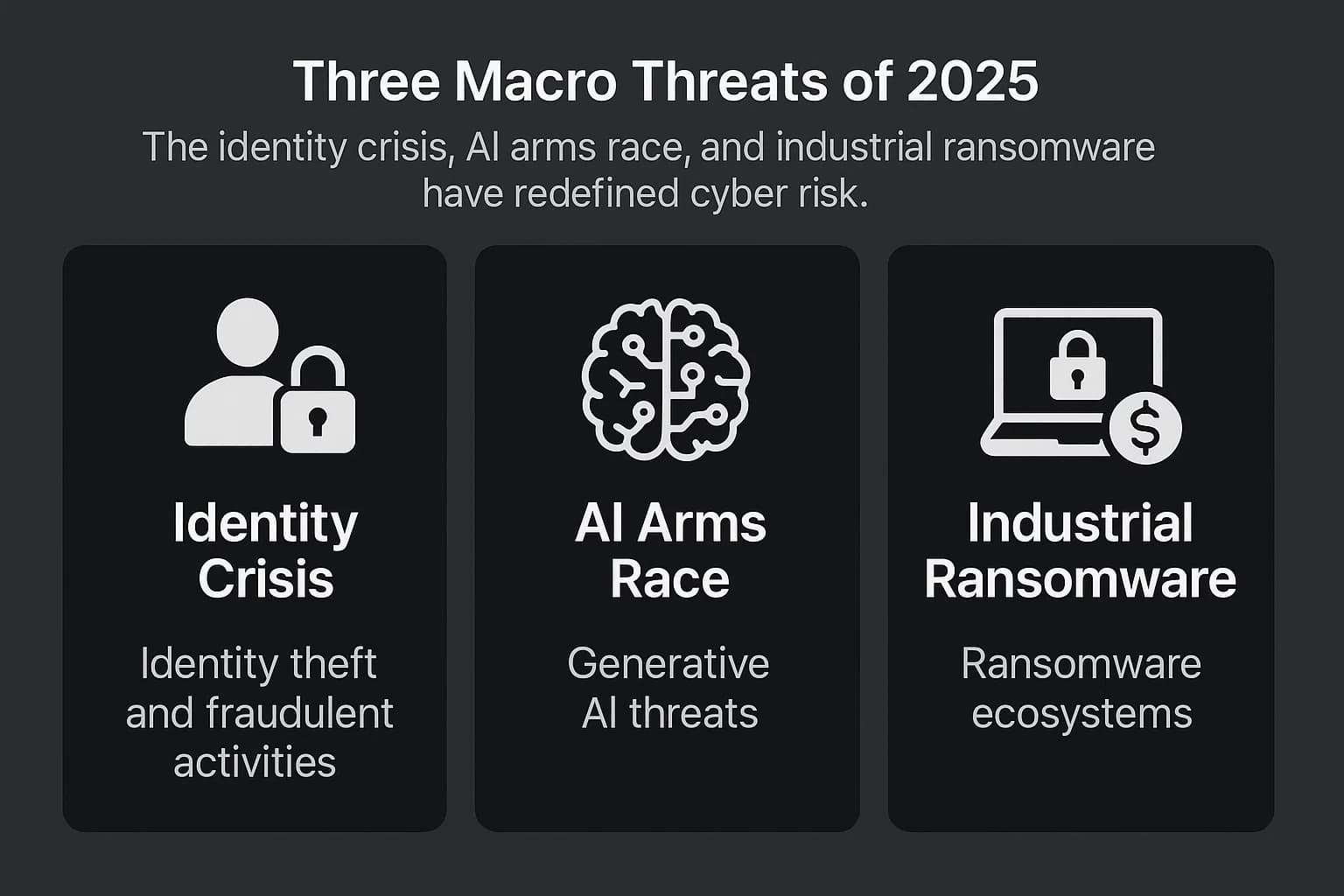
Before diving into specific sectors, it's crucial to analyze the overarching threats that impact every organization. These trends form the foundation of the modern cybercrime economy.

The most significant change in the threat landscape is the move away from complex exploits toward the simple, effective use of stolen credentials. We are facing an identity crisis fueled by a booming dark web economy where credentials are the most valuable commodity.
The scale of this problem is staggering. The first half of 2025 saw an 800% increase in credentials stolen by infostealer malware, with 1.8 billion credentials harvested from 5.8 million infected devices. This firehose of stolen data feeds massive credential dumps, like one incident in 2025 that exposed 16 billion passwords online, providing attackers with the keys to countless corporate and personal accounts. The primary delivery mechanism for this malware remains phishing attacks, with IBM observing an 84% weekly increase in phishing emails designed to deliver infostealers.
This trend has effectively dissolved the traditional network perimeter. The Verizon 2025 Data Breach Investigations Report found that 46% of systems compromised by infostealers were non managed personal devices used for both work and personal activities. An employee's laptop, infected at home, becomes a direct gateway into the corporate network. This reality makes a perimeter based defense model obsolete and underscores the urgent need for a security posture built on Zero Trust principles.
Generative AI is no longer a future threat; it is a powerful weapon in the hands of attackers today, dramatically lowering the skill, cost, and time required to launch highly sophisticated campaigns.
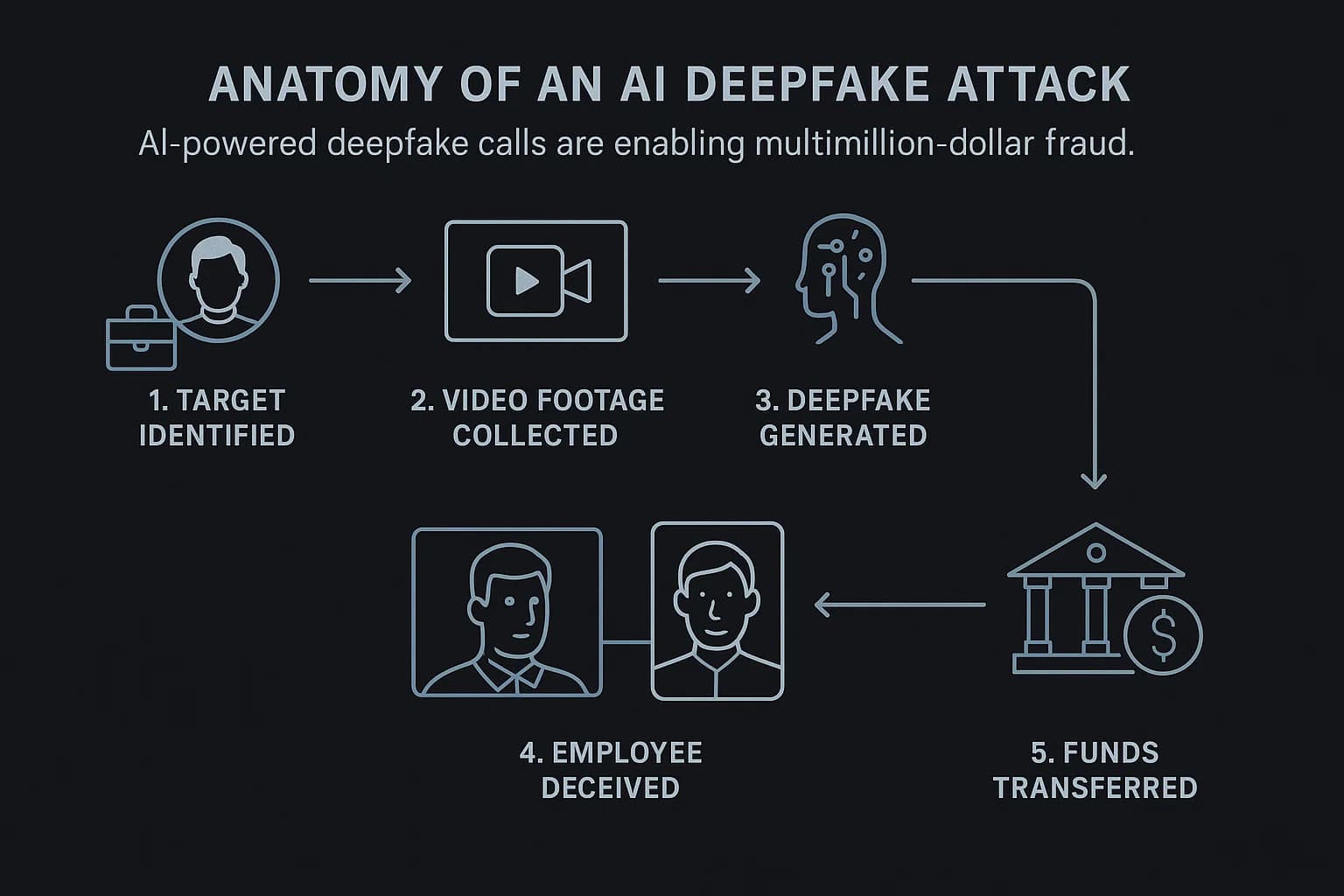
What is an AI Driven Deepfake Attack? A deepfake attack uses artificial intelligence to create highly realistic but fake video or audio. Criminals use this to impersonate executives or trusted figures in live video calls or voice messages to trick employees into making fraudulent payments or revealing sensitive data.
AI is supercharging social engineering. Attackers now use AI to craft hyper personalized, context aware, and grammatically perfect phishing emails at an industrial scale, leading to a reported 1,265% increase in AI driven phishing campaigns. The threat extends beyond text. In a widely reported 2024 incident, a finance worker at multinational firm Arup was tricked into paying out $25 million after attending a video call with deepfake versions of his CFO and other colleagues.
Compounding the risk is the rise of "Shadow AI" , the unauthorized use of AI tools by employees. According to IBM's 2025 Cost of a Data Breach Report, one in five organizations experienced a data breach stemming from shadow AI, adding an average of $670,000 to the total cost of the breach.
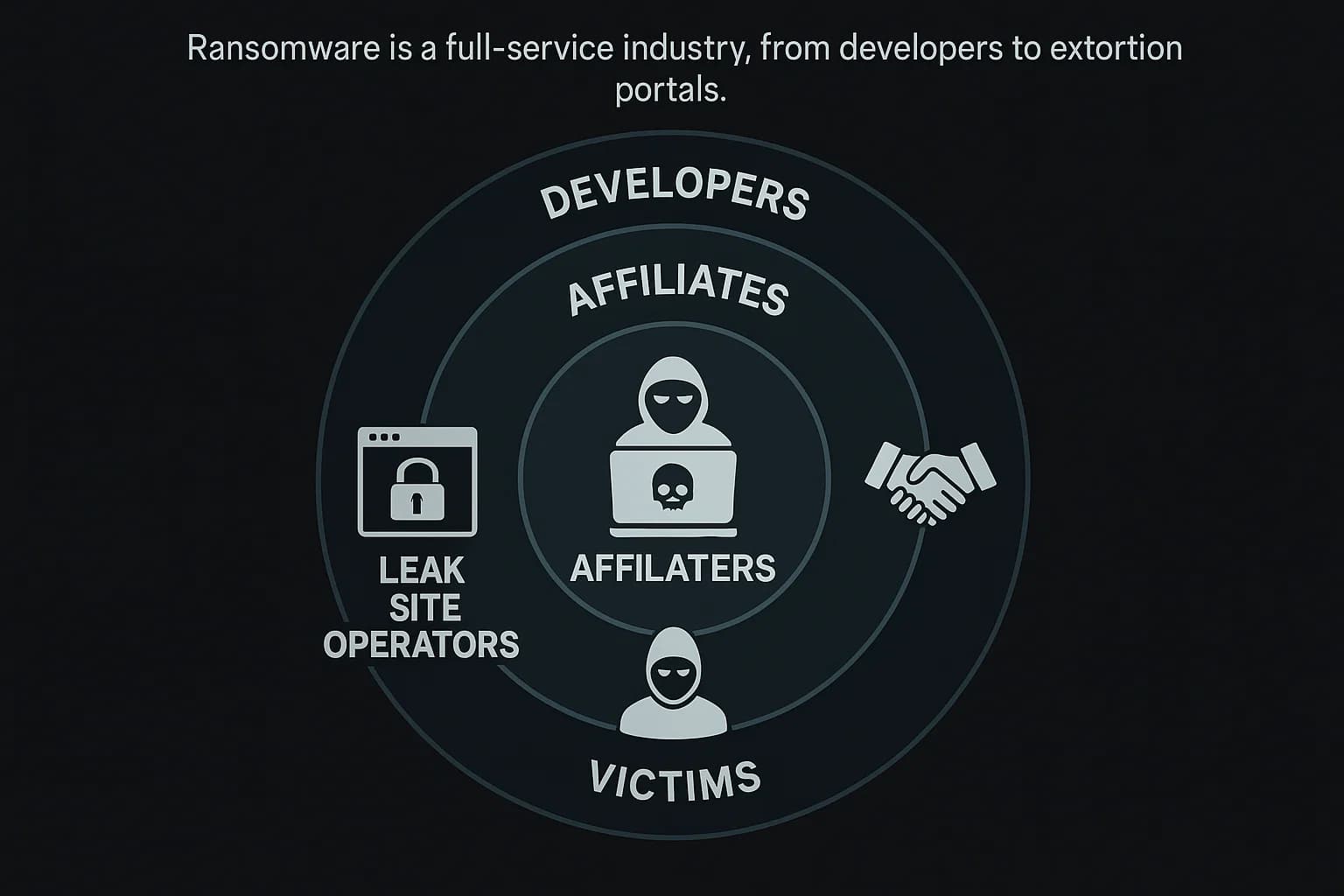
The Ransomware as a Service (RaaS) market has matured into a sophisticated, business-like ecosystem. The dominant model is now double extortion encrypting data and threatening to leak it with a growing trend toward pure data extortion without any encryption at all.
The market is incredibly volatile. The first quarter of 2025 saw a 213% increase in the number of victims listed on data leak sites compared to Q1 2024. Law enforcement actions have disrupted major players like LockBit, but new groups like Cl0p, RansomHub, and Akira have quickly risen to fill the void. These groups are behind some of the year's most significant attacks, including the massive MOVEit supply chain attack orchestrated by Cl0p, which exploited a zero day attack risk to steal data from hundreds of organizations globally.
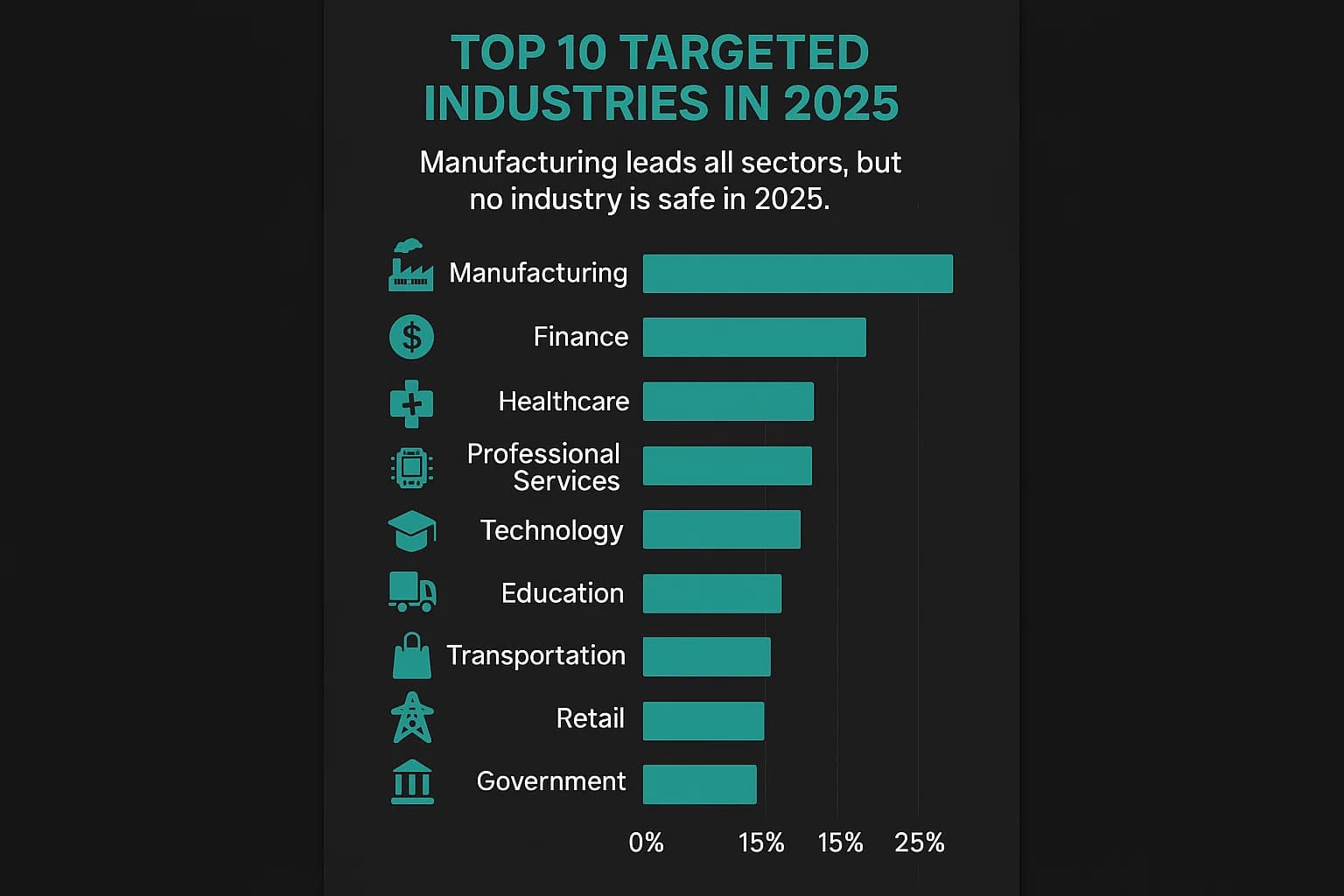
While the macro trends affect everyone, attackers prioritize their targets based on a cold calculation of leverage and profitability. Analysis of recent breach trends across industries and threat reports from sources like IBM, Dragos, and SOCRadar reveals a clear hierarchy of risk.

For the fourth consecutive year, manufacturing remains the most targeted industry, accounting for 26% of all attacks. The Dragos Q1 2025 Ransomware Report confirms this, showing manufacturing made up 68% of all industrial ransomware incidents.
The healthcare sector is a top target for its valuable patient data and the life or death pressure to maintain operations.
With direct access to financial assets, this sector remains a perennial top target. The average cost of a breach here is £4.54 million.
Government agencies are prime targets for nation state actors seeking to conduct espionage and exert geopolitical influence.
The potential for widespread societal disruption makes this sector a high value target for both nation states and sophisticated ransomware groups like Play and Babuk 2.
Tech companies are prized targets because compromising one can provide access to thousands of downstream customers.
This sector operates on tight schedules and complex digital systems, where any disruption triggers immediate and widespread financial losses.
Retailers are a magnet for financially motivated cybercriminals due to the enormous volumes of payment and personal data they process.
Educational institutions are attractive targets because they hold vast amounts of sensitive data but are often under-resourced in cybersecurity.
As the foundational infrastructure for all modern communication, the telecom industry is a primary target for sophisticated nation state espionage.
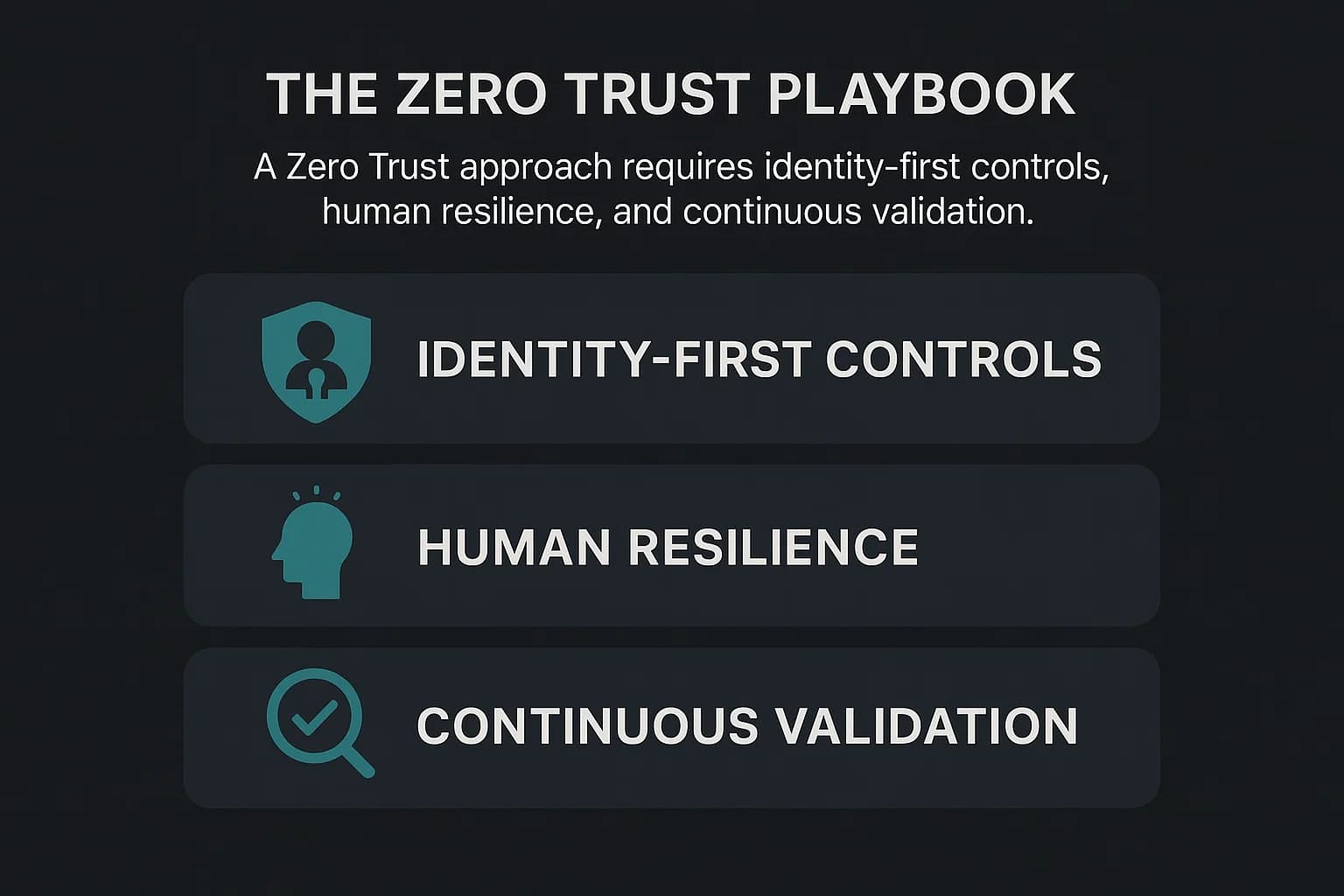
To defend against the modern adversary, organizations must adopt a proactive, resilient, and identity focused security strategy.
Security must be rebuilt around the principle of Zero Trust, which assumes no user or device is trusted by default and requires explicit verification for every access request. Key actions include implementing micro segmentation, enforcing strong authentication, and applying the principle of least privilege.
Your employees are your last line of defense. Training must evolve beyond spotting typos to include simulations of deepfake voice calls and highly personalized spear phishing emails. Foster a culture where it is normal to use a secondary channel to verify any urgent requests involving money or data.
A reactive "patch everything" strategy is impossible. A proactive, risk based approach is the only viable path forward. This includes prioritizing internet facing systems, using actionable threat intelligence, and embracing continuous security testing to ensure you meet standards for compliance driven security testing.

Hackers target healthcare because it holds highly valuable Protected Health Information (PHI), operates under immense pressure where downtime can be life threatening, and often relies on outdated, vulnerable technology. This combination makes healthcare organizations prime targets for ransomware and data theft.
In 2025, the most vulnerable industries are Manufacturing, Healthcare, and Financial Services. These sectors are targeted for their valuable data, critical operations, and direct access to financial assets. Critical Infrastructure and Government also remain high on the list due to their societal importance.
The most common initial attack vector is the abuse of valid credentials, where attackers "log in" rather than "hack in." This is primarily fueled by large scale credential theft from infostealer malware and sophisticated phishing campaigns.
AI is industrializing cybercrime by enabling hyper personalized phishing emails, creating convincing voice and video deepfakes for social engineering, and helping attackers discover software vulnerabilities faster. This allows criminals to launch more sophisticated attacks at a massive scale.
The MOVEit attack was a massive supply chain data theft campaign executed by the Cl0p ransomware group. By exploiting a zero day vulnerability in the popular MOVEit file transfer software, the group stole sensitive data from hundreds of organizations worldwide, including government agencies, financial institutions, and healthcare providers, leading to one of the most widespread breaches of the last few years.
In 2025, the industries most under siege from cyber attackers from Manufacturing and Healthcare to Finance and Government are those with the richest data and the most to lose from operational disruption. The threat landscape is now defined by identity based attacks, AI driven social engineering, and an industrialized cybercrime economy.
Surviving and thriving in this environment requires a fundamental shift to a proactive, identity centric defense built on the principles of Zero Trust. Resilience is no longer about preventing every single attack, but about containing the blast radius and ensuring operational continuity when an intrusion inevitably occurs.
Ready to Strengthen Your Defenses?
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our Penetration Testing Services to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us