July 31, 2025
Updated: July 31, 2025
A detailed breakdown of how penetration testing helps meet requirements across PCI DSS, HIPAA, SOC 2, ISO 27001, GDPR, and more.
Mohammed Khalil

Penetration testing for compliance is the practice of simulating a cyberattack against your systems to verify that your security controls meet the specific, and often rigorous, requirements of regulatory and industry standards. The era of "checkbox compliance" is over. Today,
auditors, regulators, and even your customers demand tangible proof that your security is effective, not just a collection of policies sitting on a shelf.
The stakes have never been higher. The average cost of a data breach in the U.S. has skyrocketed to a record $10.22 million, according to the 2025 IBM Cost of a Data Breach Report. This staggering figure, driven in part by steeper regulatory fines, frames the conversation not just around penalties, but around catastrophic financial risk.
This shift isn't happening in a vacuum. It's a direct response to how attackers are breaking in. The 2025 Verizon DBIR reveals that vulnerability exploitation has surged by 34%, now accounting for 20% of all breaches and nearly catching up to the use of stolen credentials as a primary entry point. Breaches like the one at Equifax, caused by a failure to patch a known
zero day exploit, show the devastating consequences of not acting on identified weaknesses.
As a result, compliance frameworks are evolving to mirror the threat landscape. Regulators are no longer satisfied with simple vulnerability management; they are increasingly mandating or strongly recommending exploitation testing a compliance pentest to ensure security gaps are not just found, but proven to be fixed. This means your compliance strategy and your security strategy must now be one and the same. Viewing penetration testing services as a mere compliance checkbox is a fast track to becoming another statistic.
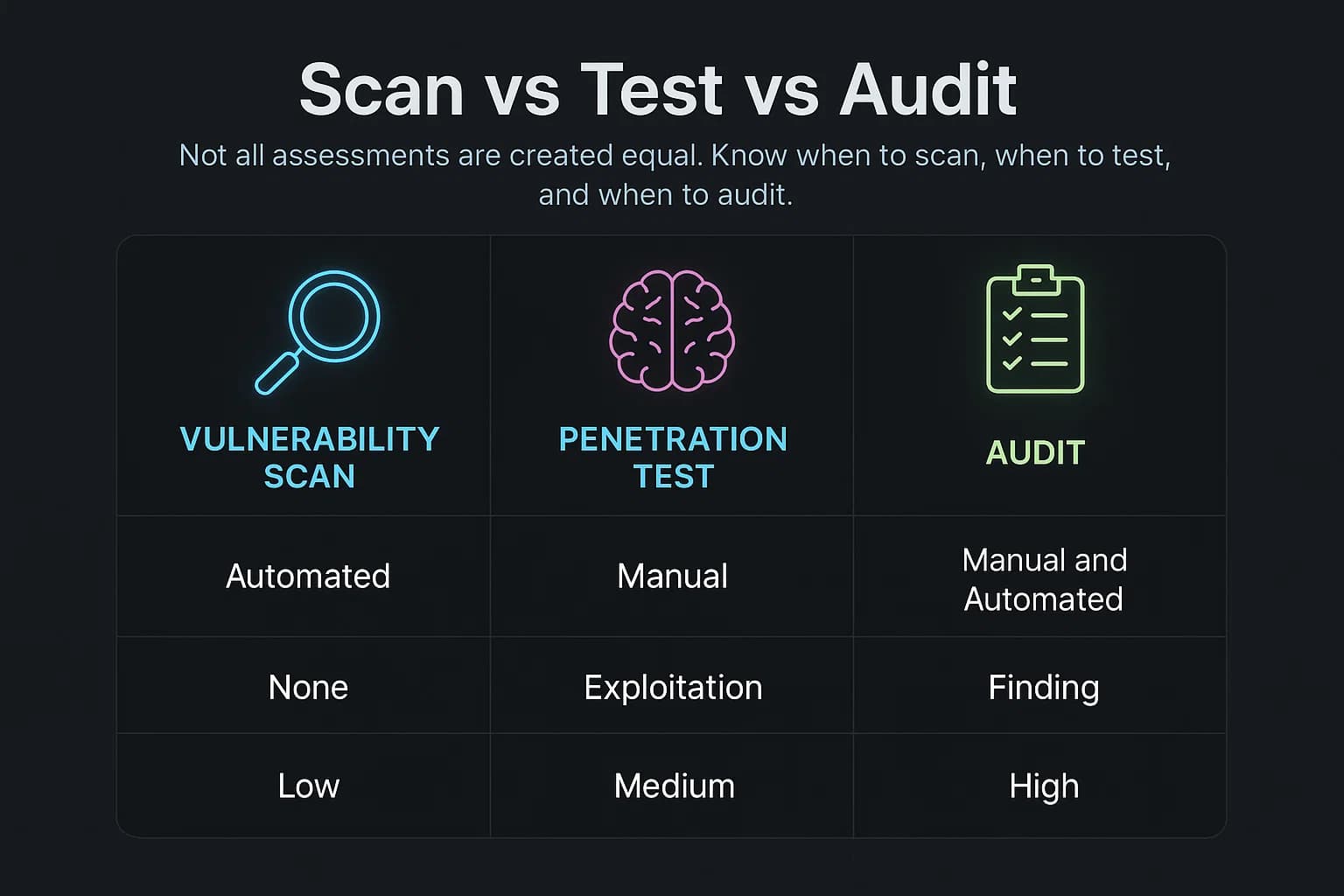
Understanding the difference between these three terms is critical. Choosing the wrong one can waste time, blow your budget, and leave you exposed during an audit. They are not interchangeable, and each serves a distinct purpose.
A vulnerability assessment is an automated, high level test that uses a scanner to check for known vulnerabilities based on a signature database. Think of it as an automated checklist. It's great at finding low hanging fruit like missing patches, outdated software, and common misconfigurations.
However, its limitations are significant. Scans are notorious for producing false positives, cannot find business logic flaws, and can't chain multiple low severity issues into a critical attack path. A vulnerability scan answers the question, "What might be wrong?" but offers no proof of actual risk.
A penetration test is a hands on, goal oriented assessment where an ethical hacker manually mimics a real attacker to exploit vulnerabilities. It goes beyond a simple list of potential flaws to prove whether a weakness is truly exploitable and what the business impact would be for example, gaining access to sensitive data or achieving a full account takeover.
This process combines automated tools with human creativity to uncover complex issues that scanners miss such as a dangerous real world SSRF attack scenario or a subtle JWT based cross subdomain account takeover. A pentest answers the critical question: “What can an attacker actually do?”
A security audit vs pen testing is a formal, systematic review of your organization's security policies, procedures, and controls against a specific framework like SOC 2 or ISO 27001. An audit is about governance and documentation. It asks: Do you have a policy for vulnerability management? Are you following it? Can you provide records to prove it?.
An auditor might verify that your policy requires an annual penetration test, but the pentest itself is the technical evidence that proves the controls mentioned in your policies are actually working.
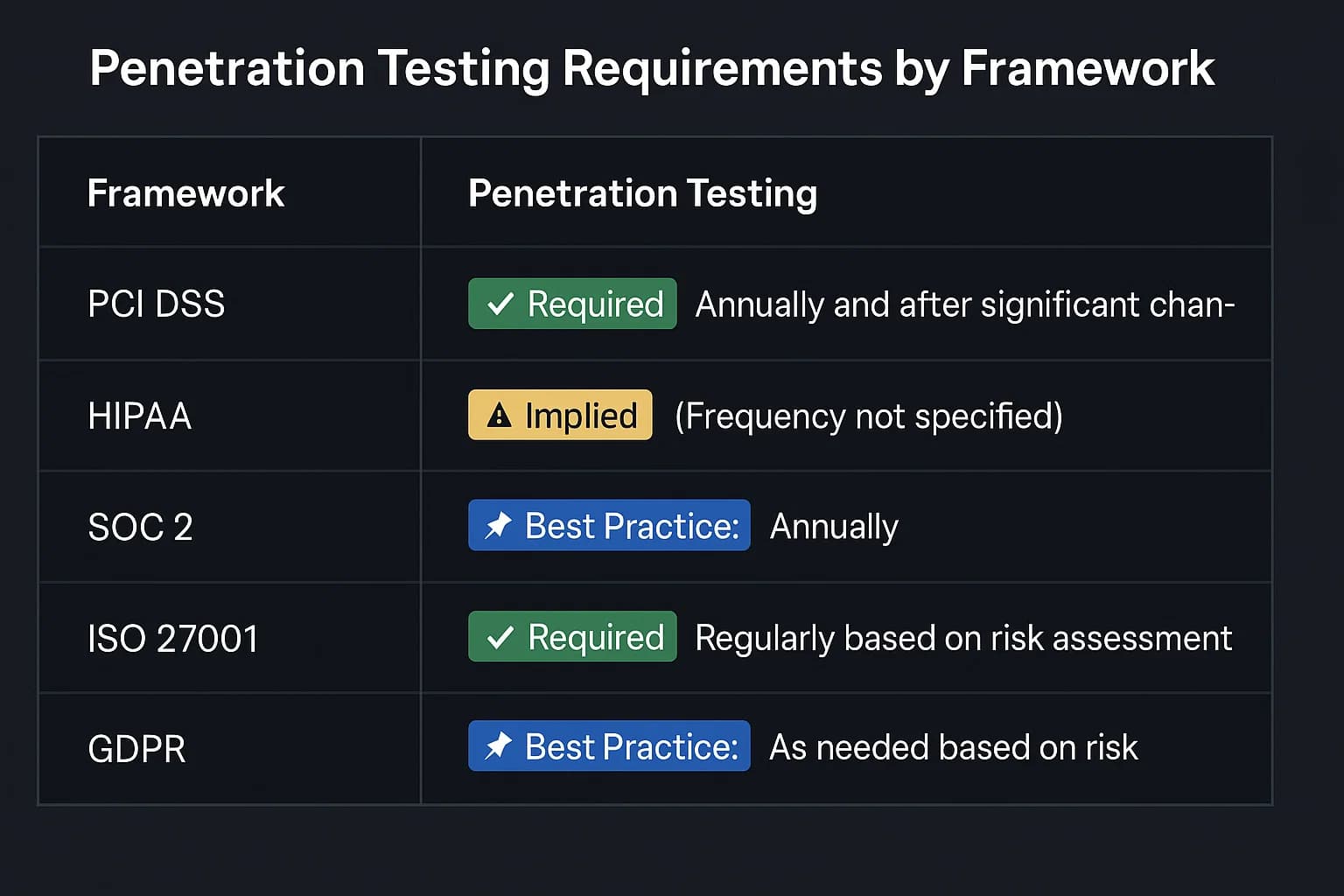
Not all compliance frameworks treat penetration testing the same way. They exist on a spectrum from highly prescriptive (telling you exactly what to do and when) to descriptive (telling you the goal and letting you decide how to achieve it). Understanding where each framework falls on this spectrum is key to building a smart, cost effective testing strategy.

The Payment Card Industry Data Security Standard (PCI DSS) is the most prescriptive of the major frameworks. If you handle cardholder data, the rules are crystal clear.
For a full breakdown, check out our complete guide to pci dss penetration testing.
The Health Insurance Portability and Accountability Act (HIPAA) has historically been more descriptive, but that's changing fast.
Dive deeper into the requirements with our dedicated guide on HIPAA penetration testing.
For a SOC 2 audit, a penetration test isn't technically mandatory, but it's practically required. Failing to provide one to an auditor is a major red flag.
Learn more about how to prepare with our SOC 2 penetration testing guide.
Like SOC 2, ISO 27001 is more descriptive, but penetration testing is essential for demonstrating compliance with several key Annex A controls.
The General Data Protection Regulation (GDPR) focuses on outcomes, and penetration testing is a key way to prove your security measures are effective.

Once you know you need a pentest, the next question is what kind. The choice between black, white, and grey box testing depends on your specific compliance goals and what you want to simulate.
In a black box the tester is given zero prior knowledge of your environment. They start with just a company name or an IP address, just like a real external attacker.
Here, the tester is given full access to source code, architecture diagrams, and admin credentials. This simulates a worst case scenario: a malicious insider or an attacker who has already achieved a deep compromise.
This is the most common and often most practical approach. The tester is given limited knowledge, such as a standard user's login credentials.
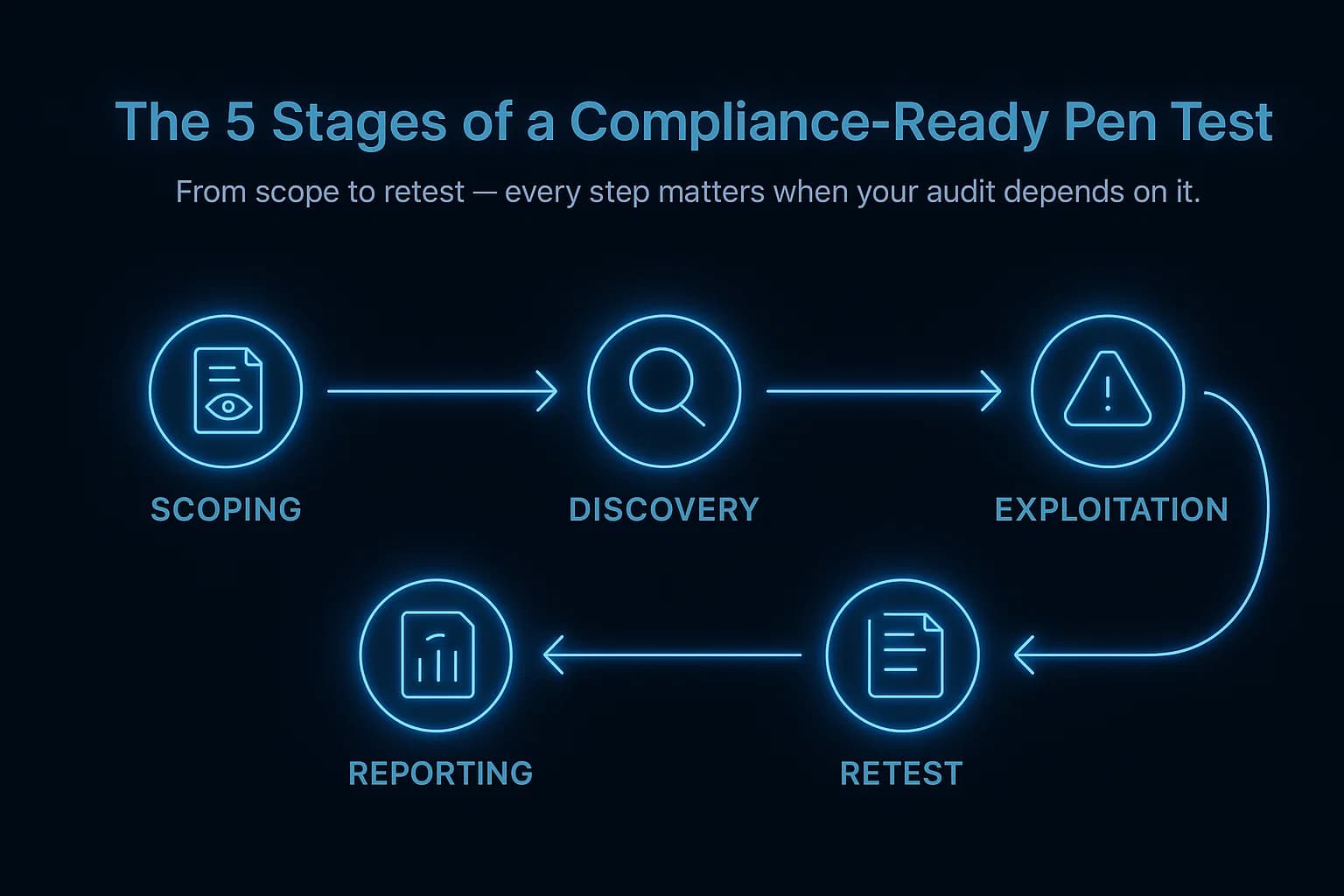
A successful compliance pentest is a structured project, not a chaotic free for all. Here’s a look at the process from start to finish.
This is the most important phase. A poorly defined scope leads to a useless report.
The tester begins with reconnaissance, mapping your attack surface and using automated scanners to find initial targets and known vulnerabilities. This phase looks a lot like a vulnerability scan, but it's just the starting point for the real work.
This is where the magic happens. The ethical hacker manually attempts to exploit the vulnerabilities found in the previous phase. The goal is to gain access, escalate privileges, and move laterally through the network to demonstrate real-world impact. This could involve anything from an HTTP request smuggling attack to exploiting a misconfigured cloud service.
For compliance, the report is everything. It's the evidence you'll hand to your auditor. A good report must include:
The test isn't over when you get the report.
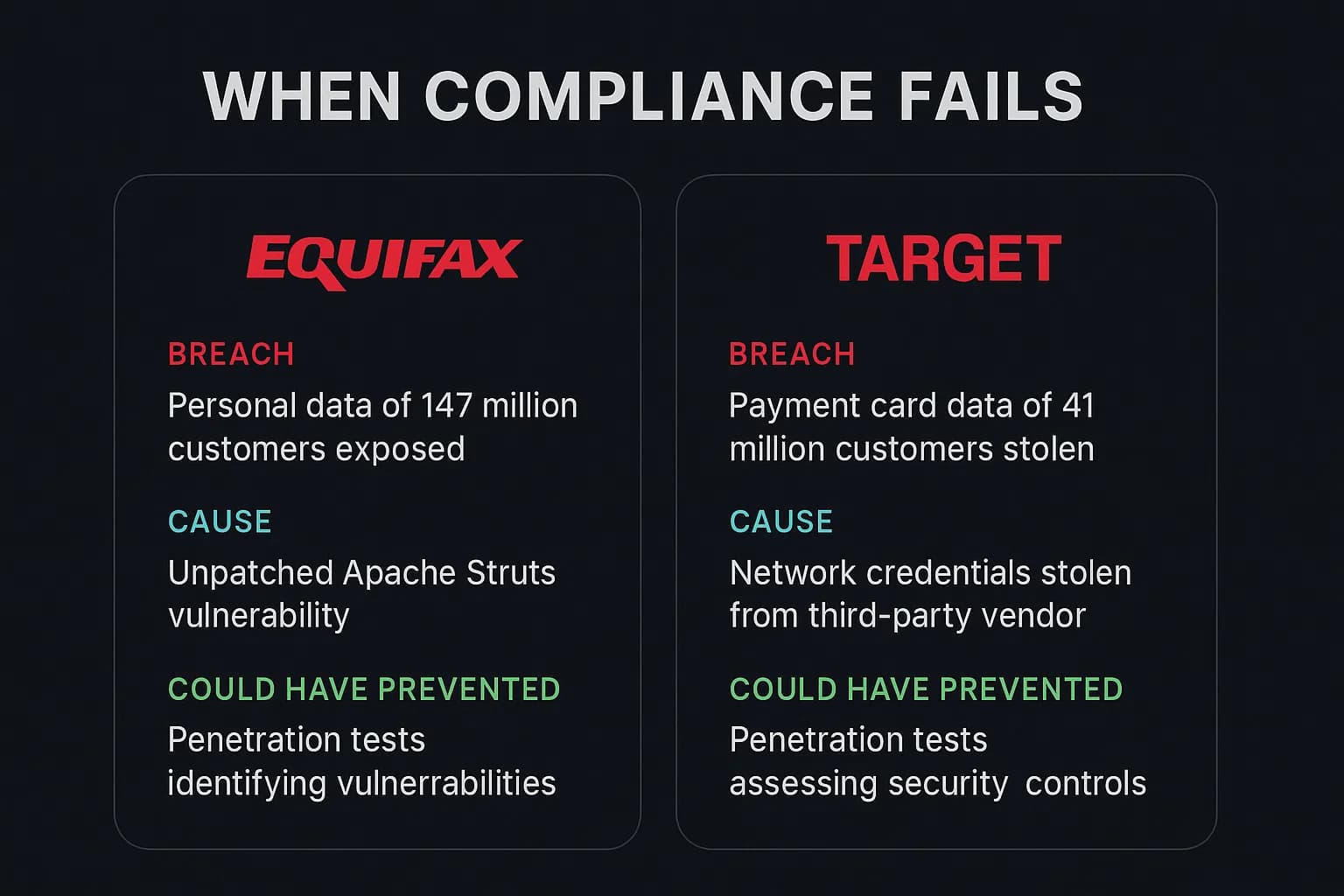
The consequences of inadequate testing aren't theoretical. They are written in the headlines and financial reports of some of the world's largest companies.
1. How often is penetration testing required for compliance?
It varies by framework. PCI DSS and the proposed 2025 HIPAA rule mandate annual testing. PCI DSS also requires biannual tests for network segmentation. For descriptive frameworks like SOC 2 and ISO 27001, the frequency is risk based, but an annual test is the accepted industry standard.
2. What's the main difference between a vulnerability scan and a pen test for compliance?
A vulnerability scan is an automated tool that generates a list of potential issues. A penetration test is a manual, human led exercise that attempts to exploit those issues to prove real world risk. Auditors increasingly want to see the proof that a pentest provides, not just a list from a scanner.
3. Can my internal team perform a pen test for SOC 2 or PCI DSS?
Yes, but with a big caveat. The internal resource must be "organizationally independent" from the team that builds and maintains the systems being tested. They must also be demonstrably qualified, with relevant experience and certifications. Proving both independence and qualification to an auditor can be challenging, which is why many organizations opt for a qualified third party.
4. Is a penetration test mandatory for SOC 2 compliance?
No, the SOC 2 framework doesn't explicitly state "you must perform a penetration test." However, it is the most common and widely accepted method for fulfilling Common Criteria 4.1 (Monitoring Activities), and most auditors expect to see a recent pentest report as evidence that your controls are effective.
5. What makes a penetration test report "audit ready"?
An audit ready report is clear, actionable, and directly tied to compliance goals. It must include a non technical executive summary, detailed technical findings with risk scores (like CVSS), tangible evidence of exploitation (e.g., screenshots), and prioritized remediation recommendations that are mapped to the specific controls of the framework you're being audited against.
6. Does GDPR Article 32 require penetration testing?
Article 32 requires a "process for regularly testing, assessing and evaluating" the effectiveness of your security measures. While it doesn't use the specific term "penetration testing," a pentest is the industry standard method for fulfilling this requirement and demonstrating due diligence to regulators.
7. How does penetration testing help with cyber insurance?
Proving you conduct regular penetration tests has become a critical factor for cyber insurance underwriting. Insurers see it as a sign of a mature security program. Many now require a recent, clean pentest report as a prerequisite for obtaining coverage or will use the results to determine your premiums and coverage limits.
8. What about other regulations like CMMC, FINRA, or NYDFS?
Yes, many other federal, state, and industry specific regulations either mandate or strongly recommend penetration testing. For example, financial services regulations like FINRA and the SWIFT Customer Security Program (CSP) recommend pentesting as a best practice to manage risk. Federal frameworks like FISMA, the upcoming CMMC for defense contractors, and the requirements for Fedramp penetration testing also have stringent assessment requirements that are often met through penetration testing. State level rules, such as NYDFS 23 NYCRR 500 for financial and insurance companies in New York, also emphasize the need for robust testing programs. The key takeaway is that across nearly every regulated industry, the expectation is to move beyond automated scanning and validate security controls with adversarial testing.
Penetration testing has firmly evolved from a niche technical exercise into a core business process for managing risk and proving compliance. The trend across all major frameworks from the prescriptive rules of PCI DSS to the descriptive principles of SOC 2 and ISO 27001 is a clear convergence on the need for proactive, adversarial testing.
A clean, thorough penetration test report has become one of the most powerful pieces of evidence you can provide to an auditor, a major customer, or your insurance provider. It demonstrates that you've moved beyond theoretical security and have validated your defenses against the same tactics that attackers are using in the wild.
Ultimately, it's time to stop viewing compliance penetration testing as a cost center. It's an investment in resilience, one that pays dividends in audit success, customer trust, and the prevention of a multimillion dollar breach. As development cycles accelerate, many organizations are now moving beyond annual point in time tests toward continuous penetration testing and PTaaS (penetration testing services) models to ensure compliance and security are maintained year round.

For Cybersecurity Consulting Services
Need expert guidance? We’re here to help. Whether you’re planning a security strategy, facing compliance challenges, or just want an expert opinion, drop us a line. At DeepStrike, we don’t sell fluff, just clear, actionable advice from real world practitioners.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us