June 23, 2025
Updated: June 23, 2025
How AI driven zero day attacks in demand advanced behavioral detection, proactive threat hunting, and Zero Trust security strategies.
Mohammed Khalil

A zero day exploit is the cybersecurity equivalent of a secret weapon. It’s an attack that uses a security flaw that no one, not even the software developer, knows exists. The name comes from a simple, urgent reality: the vendor has had
zero days to fix the problem before it's used to cause damage.
In 2025, understanding zero day security exploits isn't just for security analysts; it's a critical business imperative. The threat landscape is evolving at an unprecedented pace, as detailed in the latest cybersecurity statistics for 2025. Attackers, supercharged by AI, are weaponizing vulnerabilities faster than ever, and the financial stakes are staggering. The global cost of cybercrime is projected to hit a mind boggling $10.5 trillion this year.
This isn't about theoretical risks. These are real world attacks happening now, targeting everything from your web browser to the critical infrastructure that powers our daily lives. This guide will break down what a zero day exploit is, why it matters in 2025, and provide an actionable playbook for detection, prevention, and response, backed by insights from leading authorities like NIST, CISA, and IBM.
The terms surrounding zero days can be confusing, but they break down into a simple cause and effect chain. Getting this right is the first step to building a solid defense.
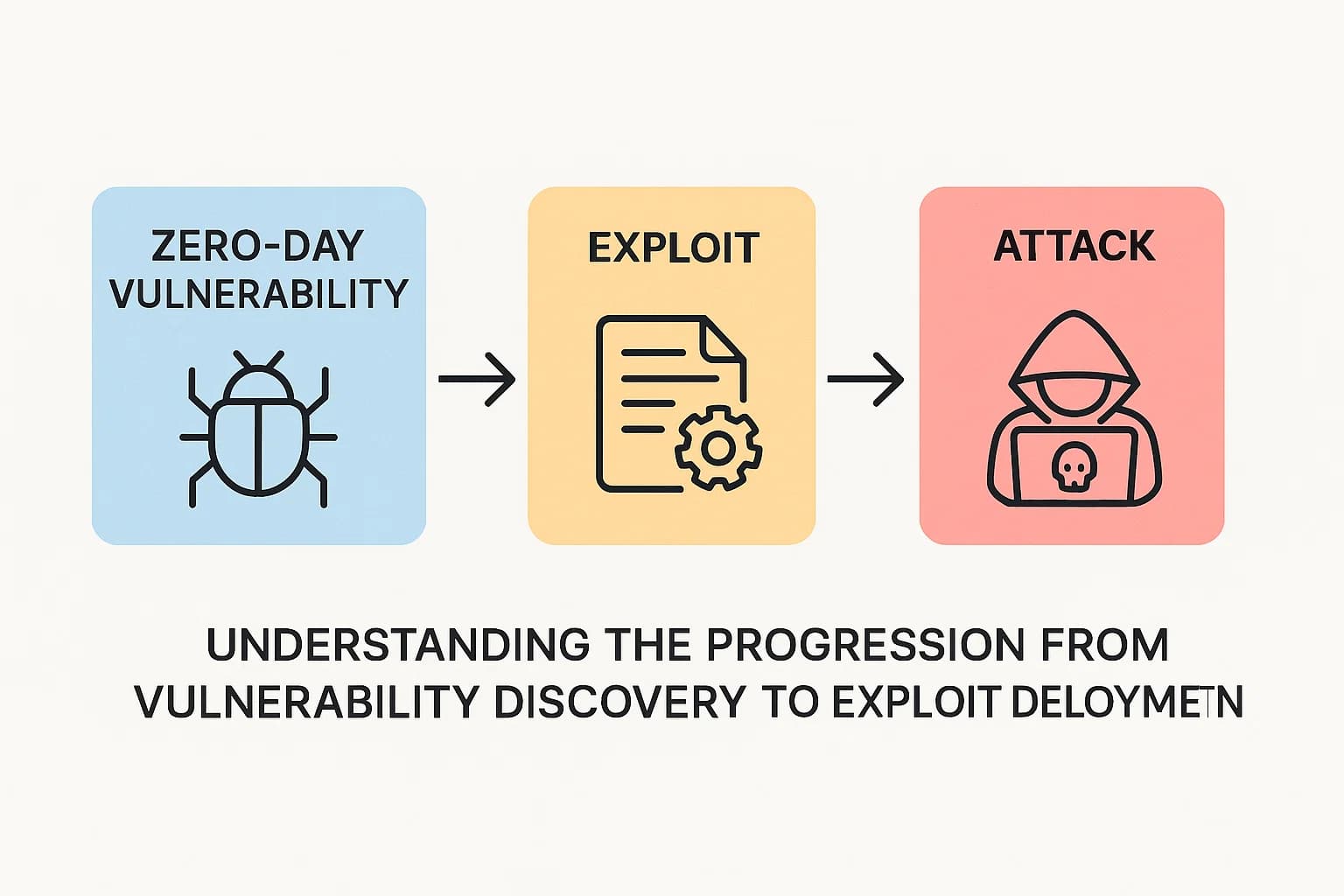
Here’s how the concepts connect:
The key difference between a zero day and a known vulnerability is the element of surprise. For a known vulnerability (one with a Common Vulnerabilities and Exposures, or CVE, ID), a patch is usually available from the vendor. For a zero day, there is no patch, making traditional defenses like signature based antivirus almost useless. This is why they are considered such a severe threat. Once a patch is released for a zero day, it becomes a known, "n day," or "one day" vulnerability. However, attackers continue to exploit it against organizations that are slow to apply the update, a common problem highlighted in numerous data breach statistics.
Every zero day follows a predictable lifecycle. It begins with the Discovery, where a threat actor or researcher finds a previously unknown flaw. The attacker then moves to
Exploitation, weaponizing the vulnerability and delivering it through vectors like phishing. Eventually, the vendor learns of the issue through
Disclosure begins Patch Development, a process that can take an average of 22 days. Even after a patch is released, the threat continues with
Post Patch Exploitation, as attackers target organizations that are slow to apply the update. This entire period represents a critical "window of exposure" where systems are at risk.
Zero day exploits are high value commodities traded in a sophisticated market. This market includes a White Market for responsible disclosure (bug bounties), a lucrative Gray Market where brokers sell exploits to governments for millions, and a Black Market for cybercriminals. The skyrocketing prices, with some exploits fetching up to $7 million, reflect their power and mean that zero day attacks in 2025 are often highly targeted campaigns by well funded adversaries.
2025 Zero Day Exploit Pricing:
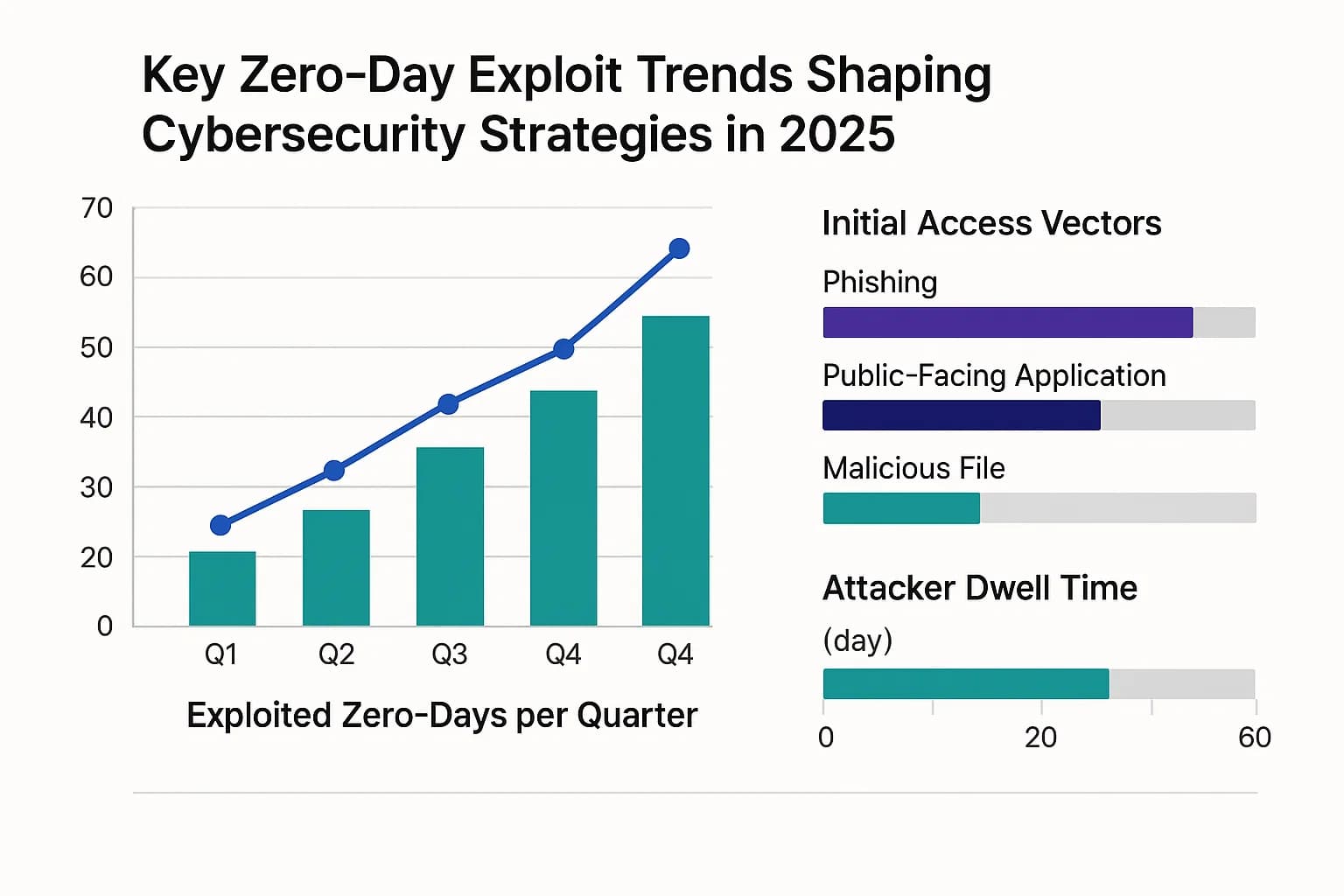
Intelligence from Google, Mandiant, and IBM reveals several critical trends defining the current landscape.
One of the most significant trends is the shift in targets. While browsers and mobile operating systems are still in the crosshairs, attackers are increasingly focusing on enterprise specific technology. In 2024, 44% of all zero days targeted enterprise products, particularly security and networking appliances, firewalls, VPNs, and gateways from vendors like Ivanti, Cisco, and Fortinet.
This pivot is a direct response to improved defenses on traditional endpoints. Widespread Endpoint Detection and Response (EDR) has made attacking user workstations riskier. In response, adversaries have moved to the network edge, which often represents a blind spot for security teams as these devices typically lack EDR agents. This makes understanding and securing these network vulnerabilities in 2025 a top priority.
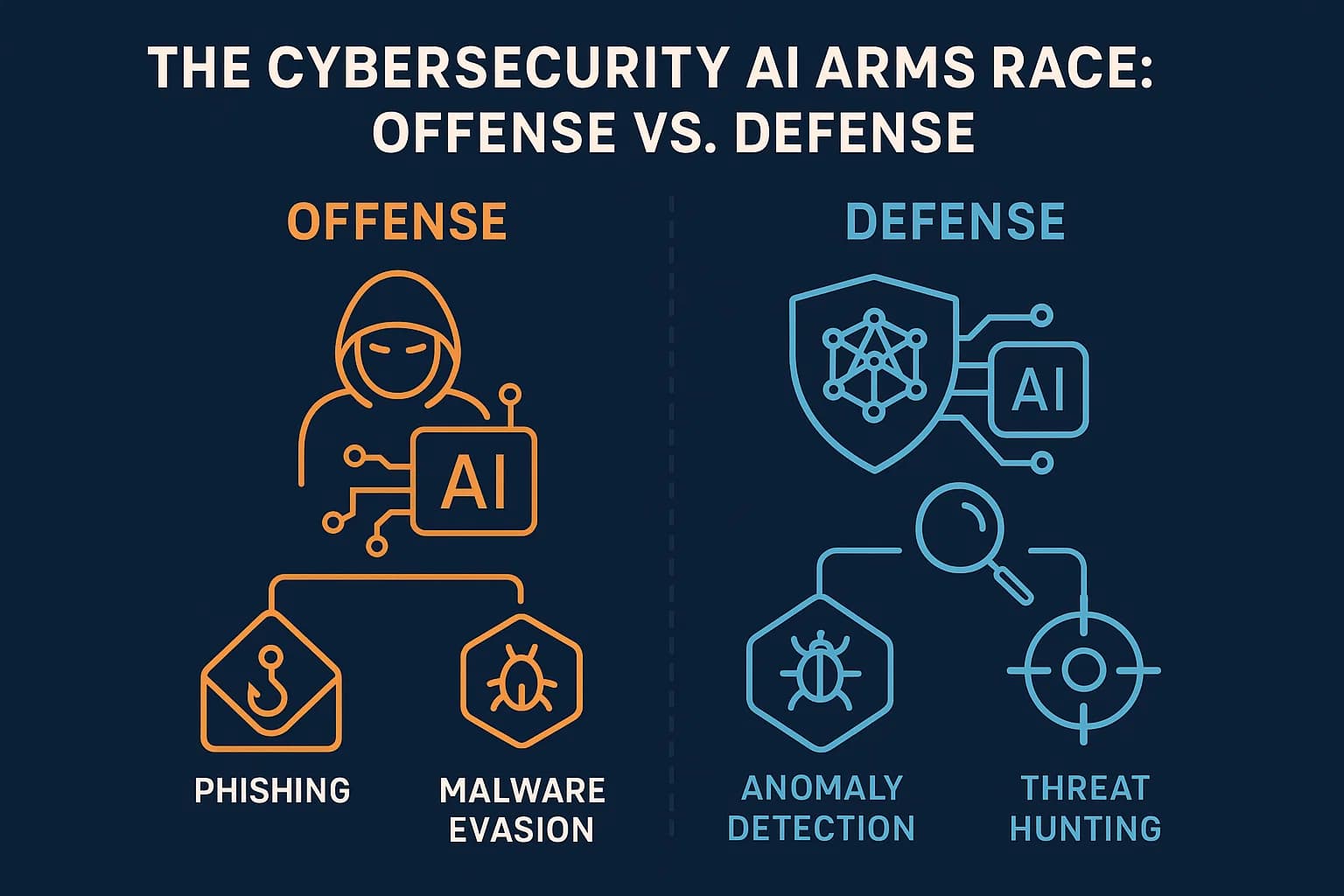
Artificial intelligence is a true double edged sword in the fight against zero days. Attackers use it for hyper realistic phishing, automated vulnerability discovery, and evasive malware. Defenders use AI for behavior based detection, threat hunting, and automated response (SOAR), which are essential for identifying the anomalous behavior of a zero day exploit without a pre existing signature.
Historically the domain of nation state espionage, zero day exploits are now increasingly used as the entry point for high impact ransomware attacks. Threat actors use a zero day to gain initial access, move silently through the network, steal data, and then deploy ransomware. This "double extortion" tactic maximizes their leverage and poses a direct threat to business operations.
Case studies make the threat tangible. Analyzing past and present attacks shows how attacker TTPs (Tactics, Techniques, and Procedures) have evolved.
While you can't stop a zero day vulnerability from existing, you can build a resilient defense that detects and contains an attack before it causes catastrophic damage. A modern, multi layered strategy is essential.
By definition, you can't detect a zero day with a signature. You have to look for the behavior of an attack in progress.
Prevention focuses on reducing your attack surface and making it harder for an attacker to succeed.
When a zero day attack hits, a well rehearsed plan is the difference between controlled response and chaos.
Step by Step Zero Day Incident Response Checklist:

Misconceptions about zero days can lead to a false sense of security or a feeling of helplessness. Here are the facts.
The era of relying on firewalls and antivirus software is over. The 2025 threat landscape, defined by AI driven attacks and sophisticated adversaries, demands a fundamental shift in mindset from reactive compliance to proactive resilience.
Zero day exploits are a core component of the modern cybercrime ecosystem. Winning against this threat isn't about achieving perfect, impenetrable security. It's about building a system that can withstand an attack, detect it quickly, and respond effectively. It requires integrating advanced technology, adopting a modern architectural framework like Zero Trust, and hardening your human defenses.
The clock is always ticking. The question is no longer if a zero day will target your systems, but when. Your readiness will determine the outcome.
What is a simple definition of a zero day exploit?
A zero day exploit is a cyberattack that takes advantage of a security vulnerability that is unknown to the software developer or the public. Because the flaw is a secret, the developer has had "zero days" to create a patch to fix it, making initial attacks highly successful.
What is a real world example of a zero day attack?
A famous example is the Stuxnet worm (2010), which used four different zero day vulnerabilities in Windows to physically damage Iran's nuclear centrifuges. A more recent example is the
Log4Shell vulnerability (2021), a flaw in a popular Java library that allowed attackers to take remote control of millions of applications worldwide.
How are zero day exploits discovered?
Zero day exploits are discovered in several ways. Security researchers and threat actors can find them through methodical processes like fuzzing (bombarding a program with invalid data), reverse engineering software, or performing source code analysis. Sometimes, they are found by accident during a routine penetration test.
How do you protect against zero day attacks?
Protection requires a multi layered strategy. Key defenses include:
What is the difference between a zero day exploit and a known vulnerability?
A zero day exploit targets a vulnerability that is unknown to the vendor and has no patch available. A known vulnerability (often identified by a CVE number) has been publicly disclosed, and a patch or mitigation is typically available. Attackers exploit known vulnerabilities in unpatched systems, while zero days are used against fully patched systems because no fix exists yet.
Why are zero day attacks so dangerous?
They are dangerous because of the element of surprise (no pre existing defenses), their high success rate against initial targets, and the significant time gap (window of vulnerability) between the first exploit and when a patch is widely deployed.
How much is a zero day exploit worth?
The price varies dramatically based on the target. In 2025, a zero day exploit for an iPhone can sell for $5 -7 million, while one for Google Chrome can fetch $3 million. The high prices are primarily paid by government agencies and top tier criminal groups.
Got questions? Need expert insights on zero day defenses? Reach out, always happy to chat.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us