July 6, 2025
Updated: July 6, 2025
A catastrophic password leak exposed billions of login credentials worldwide. Here’s how it happened and how to protect your accounts now.
Mohammed Khalil

Let's be direct: if you're online, there's a high probability your login credentials were part of the colossal 16 billion record password leak that came to light in June 2025. That number, roughly double the Earth's population, signals widespread exposure and likely means multiple accounts per person have been compromised.
But this isn't your typical data breach story. This leak wasn't caused by hackers breaking into Google or Apple's servers. Instead, it’s a massive "collection of collections" , largely fueled by a stealthy threat called infostealer malware that steals passwords directly from your personal computer or phone.
This isn't just security blog chatter. The incident prompted an official advisory from India's Computer Emergency Response Team (CERT In), which issued advisory CTAD 2025 0024 warning millions of users about the exposure and its severe risks. The core danger lies in a single, pervasive habit: password reuse. Because so many people use the same password everywhere, this 16 billion record database has become a goldmine for cybercriminals launching automated credential stuffing attacks to hijack your accounts. The latest password statistics for 2025 confirm this habit isn't improving, making the fallout from this leak far more severe.
The story of this leak unfolded over several months. Security researchers at outlets like Cybernews began tracking disparate sets of exposed credentials in early 2025, culminating in the discovery of the full $ 16 billion record trove between June 18-19, 2025.
It's crucial to understand that this wasn't a single database hack. The data was spread across approximately 30 different datasets found on dark web forums and in misconfigured, publicly accessible cloud storage buckets. As infostealers have become more common, threat actors now often release these massive compilations for free on platforms like Telegram to build their reputation in criminal circles. While credentials for major services like Apple, Google, Facebook, Telegram, and even government portals were included, those companies themselves were not directly breached. The data was stolen at the user level, from individual devices.
You might have heard of past mega breaches like "RockYou2021" or the "Compilation of Many Breaches" (COMB). While massive, those were primarily collections of old data from previous, known breaches. The June 2025 leak is far more dangerous for one key reason: it contains a significant volume of fresh data harvested within the last year by infostealer malware. This means many of the passwords are still active and in use. Furthermore, many records included not just usernames and passwords, but also active session cookies and authentication tokens, making them "dangerously usable" for immediate exploitation and account takeover.
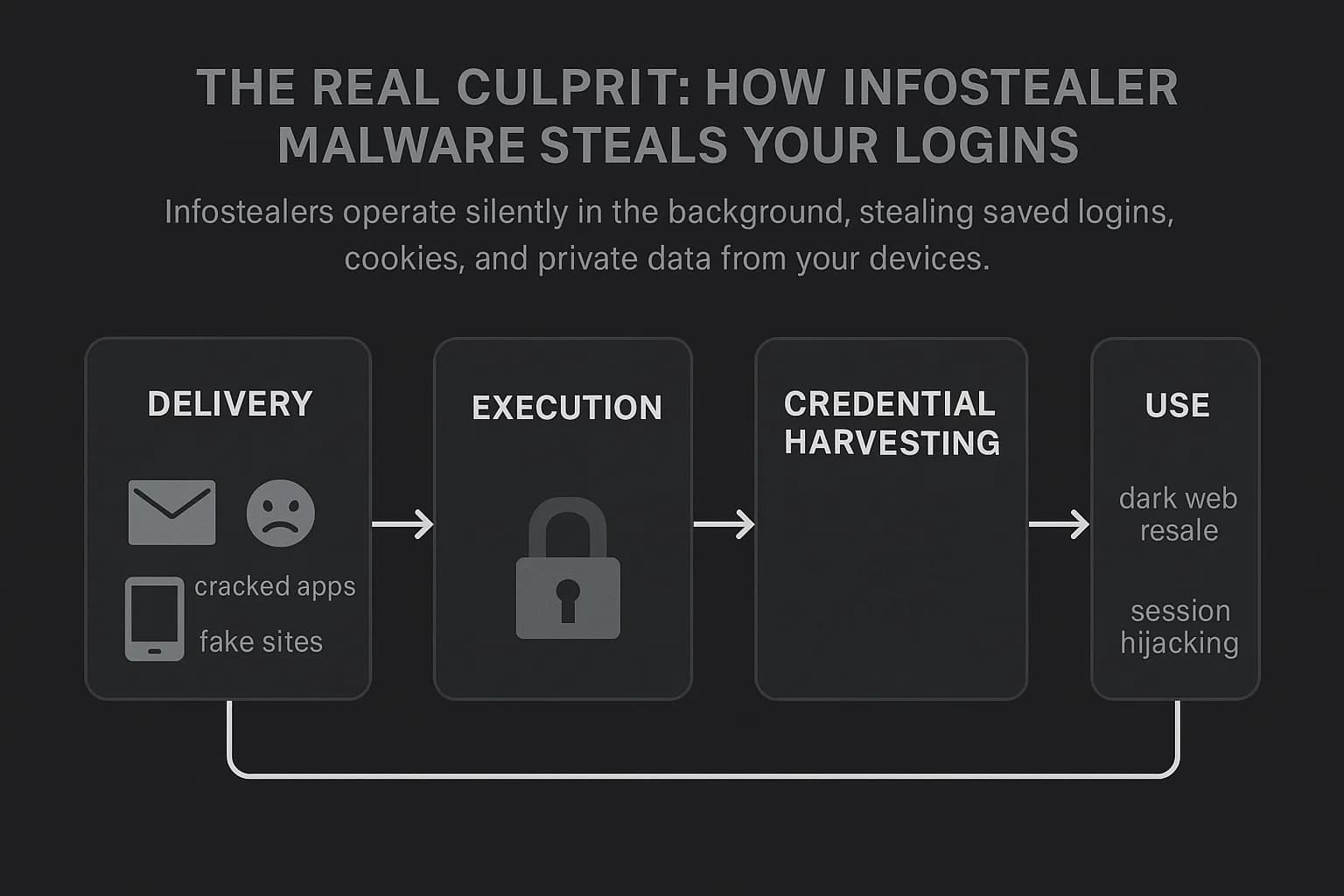
The engine driving this massive credential exposure is infostealer malware. Understanding how it works is the first step to protecting yourself.
Infostealers are a type of malicious software designed specifically to harvest sensitive information from a compromised computer, operating silently in the background. Unlike ransomware that noisily encrypts your files for a ransom, infostealers are spies. They are programmed to find and exfiltrate high value data, including:
Popular variants like RedLine, Raccoon Stealer, and LummaC2 are often sold on the dark web as Malware as a Service (MaaS). This business model allows even low skilled criminals to rent the malware and its infrastructure, launching sophisticated data theft campaigns with minimal effort and contributing to the massive scale of the credential leak. It's one of the most common forms of malware we've seen in 2025.
Infostealers don't typically exploit complex software vulnerabilities. Instead, they rely on social engineering to trick you into running them. Here are the most common ways they infect a device:
A single leaked password might not seem catastrophic, but it's the first domino to fall in a chain reaction that can lead to devastating consequences.
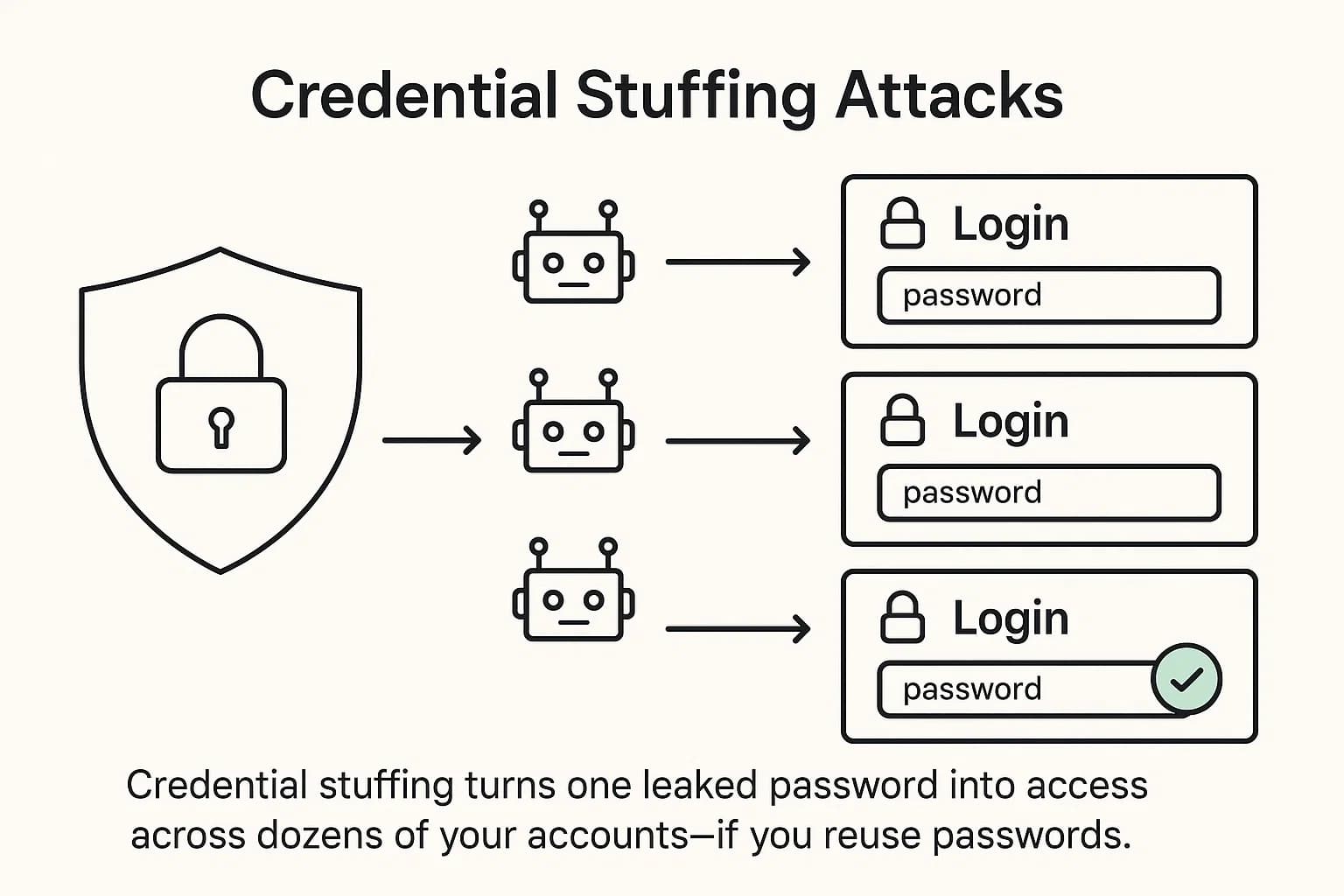
Credential stuffing is the immediate and most widespread threat following a password leak. It’s an automated attack where bots take the massive list of leaked username/password pairs and "stuff" them into the login forms of thousands of other websites, your bank, your email, your social media, your e-commerce accounts. Attackers use specialized, readily available tools and configurations to automate these attacks at a massive scale, making them incredibly efficient.
Think of it like a thief finding a single key and then methodically trying it on every door in your neighborhood. Because of rampant password reuse, that one key often opens many doors. The scale of this threat is immense; Akamai reported observing 193 billion credential stuffing attacks in a single year back in 2020. With 16 billion fresh credentials now in circulation, that number will undoubtedly explode. According to the Verizon Data Breach Investigations Report, over 80% of web application breaches are caused by stolen credentials, making this the single biggest vector for a full account takeover.
Once an attacker successfully uses a leaked password to access a critical accountespecially your primary emailthe damage escalates quickly. From inside your email, they can search for messages from other services and initiate password resets for your bank, PayPal, investment accounts, and more.
Even worse, some of the leaked data includes session cookies. Here’s a real world scenario: an infostealer on your computer steals the active session cookie for your Google account. This cookie is what keeps you logged in without having to enter your password every time. The attacker can inject this cookie into their own browser and instantly gain access to your Gmail, Google Drive, and Photos, completely bypassing your password and even MFA.
This isn't a theoretical risk. The IBM X Force Threat Intelligence Index confirms that abusing valid accounts was the top initial access vector in 30% of the incidents their team responded to. It's the primary way major breaches and financial theft begin. The end goals are clear: drain bank accounts, commit fraud with stolen credit card details, and orchestrate full blown identity theft, a nightmare that can take years and significant resources to resolve.
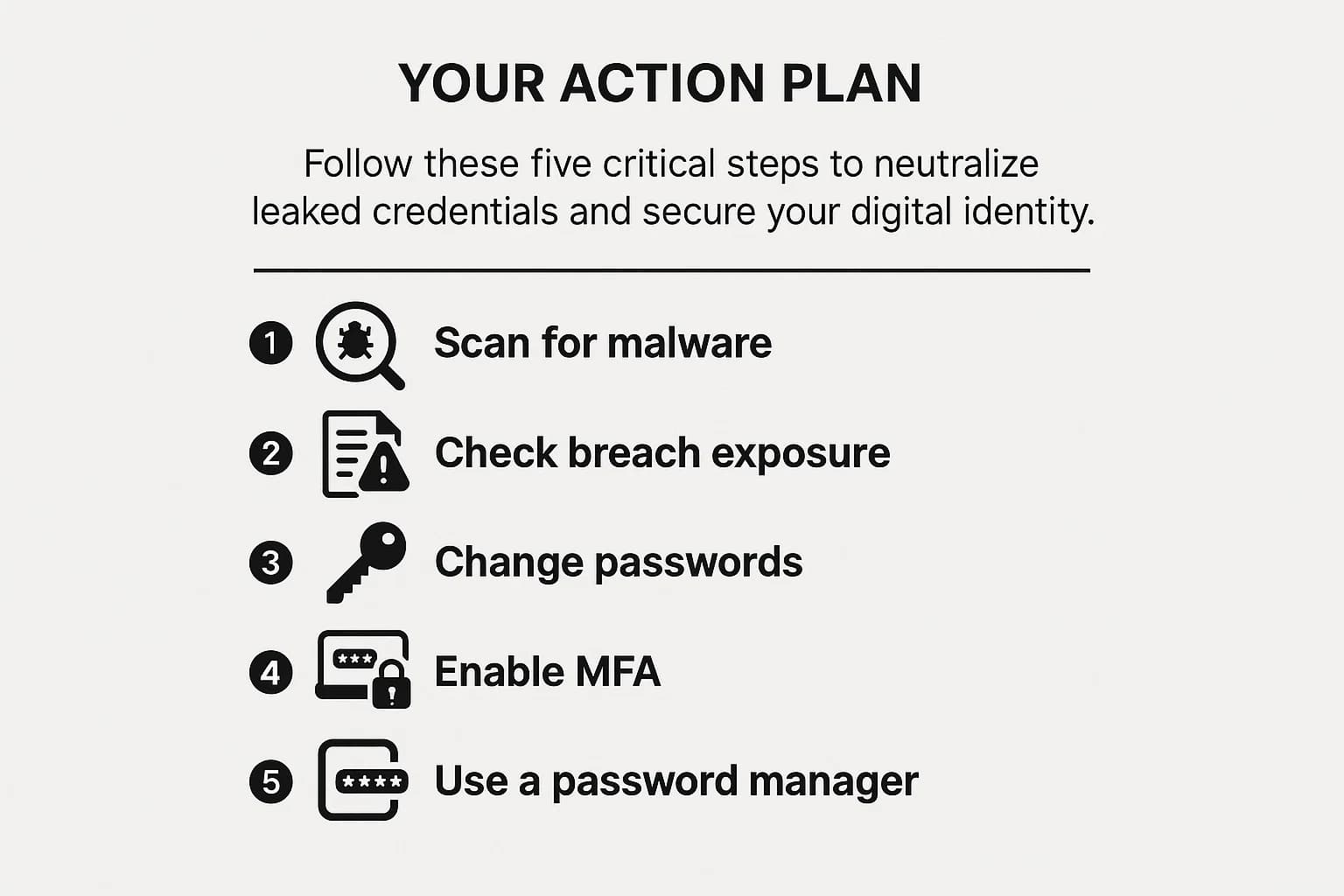
Feeling overwhelmed? Don't be. You have the power to make these stolen credentials worthless. Follow these steps methodically to reclaim your digital security.
This is the most critical first step. If an infostealer is still active on your device, changing your passwords is a wasted effort; you're just handing the new credentials directly to the attacker on a silver platter.
Action: Before you change a single password, run a full, deep scan with a reputable and up to date antivirus or anti malware program. Services like Malwarebytes, ESET, or Bitdefender are excellent choices. If possible, disconnect the infected device from the internet and use a separate, known clean device (like your phone or another computer) to perform the next steps. Do not skip this.
Once your devices are clean, it’s time to assess the damage.
Action: Use Troy Hunt's HaveIBeenPwned.com, a trusted and free service that aggregates data from thousands of breaches. Go to the site and enter your primary and secondary email addresses. It will show you a list of the known data breaches your email address has appeared in. You can also use the "Pwned Passwords" feature to check if a specific password has been exposed, without the service ever seeing your password in plaintext.
Now it's time to replace the compromised locks.
Action: Prioritize your most critical accounts: your primary email, online banking, password manager master password, and major social media accounts. When creating new passwords, follow modern security standards championed by NIST and OWASP:
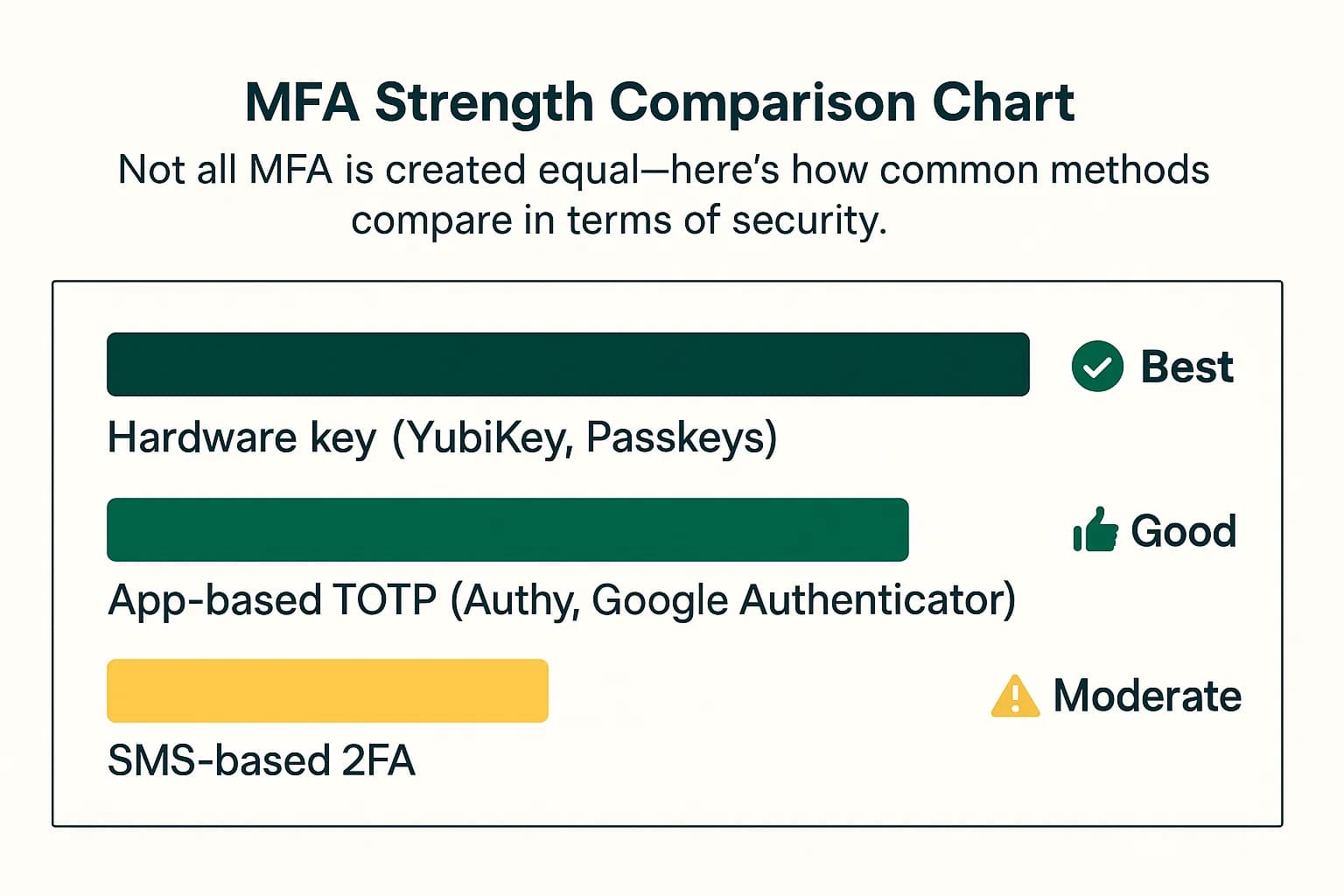
This is your single most powerful defense against credential stuffing. MFA is the digital equivalent of a deadbolt on your door; even if a thief has your key, they still can't get in.
Action: Enable Multi Factor Authentication (MFA) on every single account that offers it. MFA requires a second piece of proof to log in, typically something you have (like your phone) or something you are (like your fingerprint). However, not all MFA is created equal. Prioritize them in this order:
The Rise of Passkeys: A More Secure Future
You're hearing more about passkeys for a reason. They are the next evolution of authentication, designed to replace passwords entirely. A passkey is a cryptographic key stored securely on your device (phone, computer) and linked to your biometric data (fingerprint, face scan). When you log in, the website verifies your device's key instead of a password. This makes them inherently resistant to phishing and server side breaches, as there is no shared secret to steal. CERT In and other security bodies are now actively encouraging users to transition to passkeys wherever they are supported by services like Google, Apple, and others.
Trying to create and remember long, random, and unique passwords for dozens or hundreds of websites is humanly impossible. A password manager makes it not only possible but easy.
Action: Choose a reputable password manager to generate and securely store your credentials.
The 2025 password leak isn't just a consumer problem. When employees reuse passwords, a personal breach quickly becomes a corporate liability.
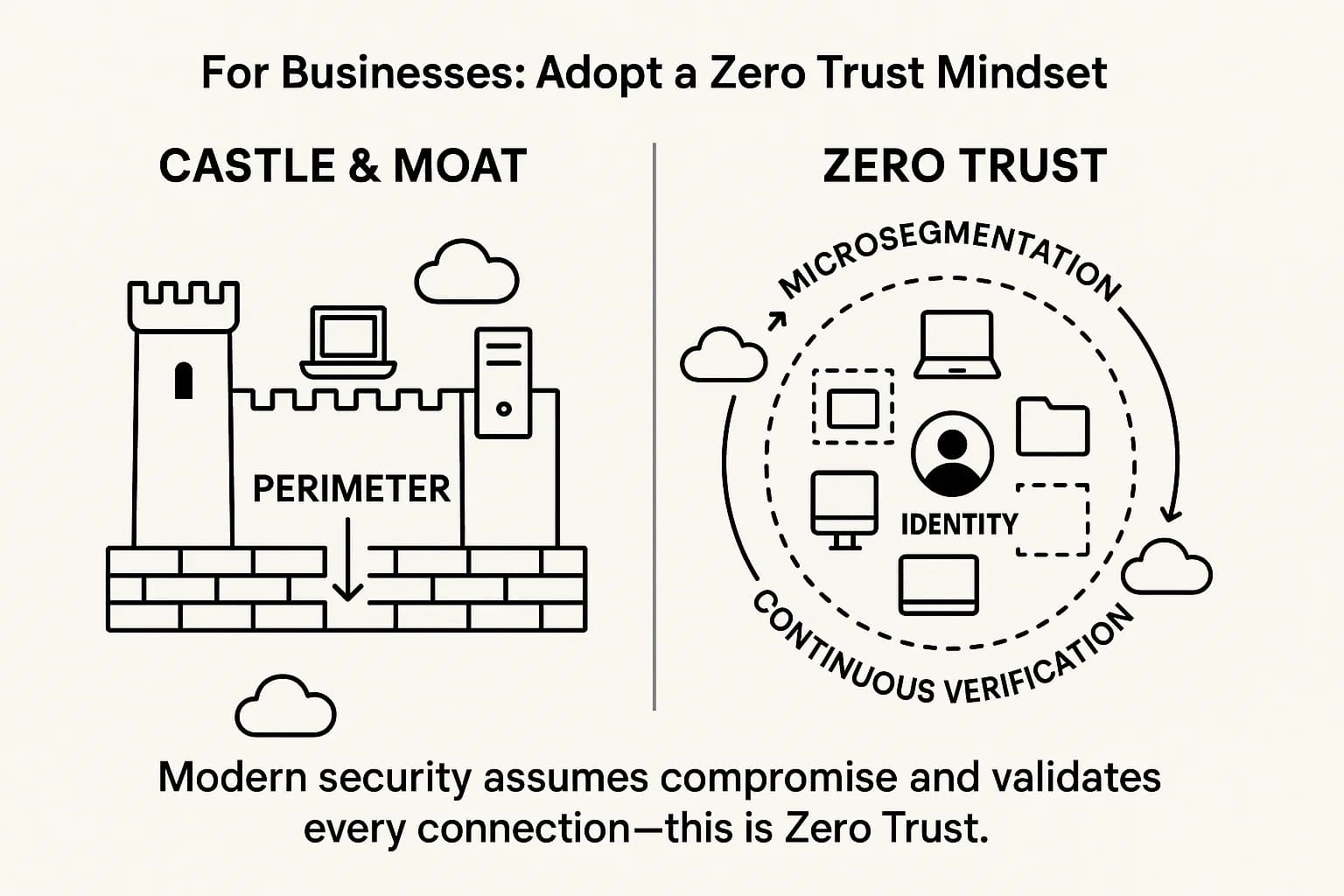
The traditional "castle and moat" security model is dead. The modern principle is Zero Trust: "Never trust, always verify". In the context of this leak, it means you must assume any employee credential could be compromised at any time. The perimeter is no longer your office firewall; it's the identity of every user, wherever they are.
Key actions to take include:
For a business, MFA cannot be optional. It must be a mandatory, enforced policy across all critical systems, especially for access to cloud services, VPNs, and internal applications. Pair this with strong password policies based on CISA and NIST guidelines: enforce minimum length, use blocklists to ban weak passwords, and provide employees with an enterprise grade password manager to eliminate excuses for poor hygiene.
Reactive measures aren't enough. Businesses must proactively hunt for exposed corporate credentials on the dark web and test their defenses to see how they could be exploited. This is where passive monitoring meets active validation.
Engaging in regular security assessments is crucial to identify and close these gaps before attackers find them. This includes services like penetration testing as a service ptaas for ongoing assessments and continuous penetration testing to ensure defenses remain effective over time. Understanding the difference between a vulnerability assessment vs. a penetration test and when to deploy red team vs. blue team exercises is fundamental to building a resilient security posture.
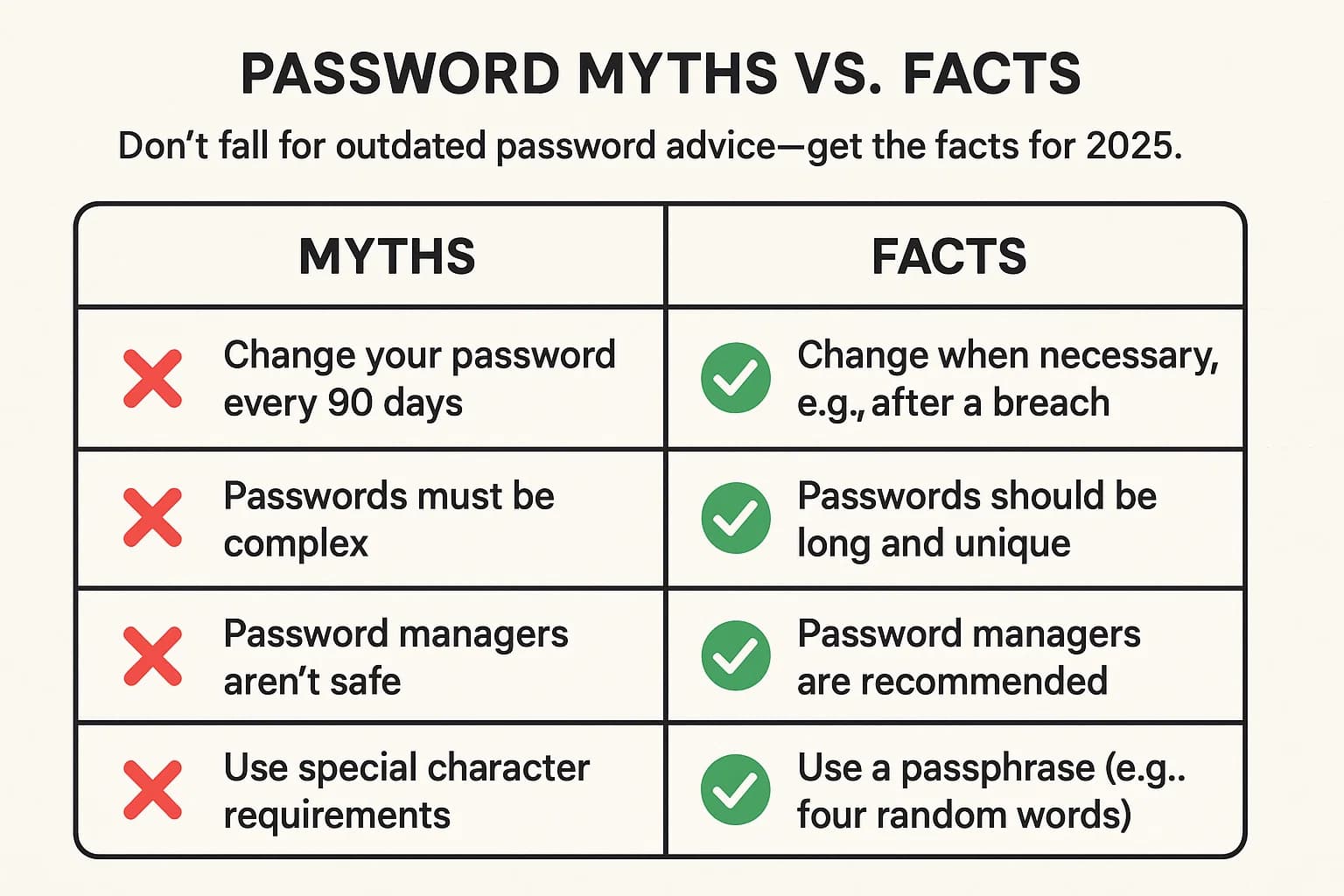
Misinformation about passwords is rampant. Let's clear up a few common myths.
The best way is to use the free, trusted service HaveIBeenPwned.com. Enter your email address to see if it has appeared in known data breaches. Many password managers like Bitwarden and 1Password also have built-in breach monitoring. It's also crucial to run a malware scan on your devices, as infostealers are a primary source of these leaks.
Follow these steps in order:
1) Scan your computer for malware.
2) Change the password for the affected account and any other account using the same or similar password, starting with email and financial accounts.
3) Enable multi factor authentication (MFA) everywhere. 4) Consider a temporary credit freeze if financial data was exposed.
Yes, reputable password managers are safe. They use a "zero knowledge" security model, meaning they never store your master password. Your data is encrypted using your master password. So, even if a hacker steals the encrypted vault (as in the LastPass breach), it's just a scrambled block of data without your unique master password. The risk of not using one (password reuse) is far greater.
The two most effective defenses are using a unique, strong password for every single account (made easy with a password manager) and enabling multi factor authentication (MFA). If an attacker has your password for one site, it will be useless on others, and MFA will block them even if they have the correct password for the targeted site.
Infostealer malware is a type of spyware that secretly collects sensitive data from your device, including saved passwords, browser cookies, and credit card info. To remove it, you must run a full system scan with a reliable and updated anti malware program like Malwarebytes or another trusted EDR solution. After removal, you must change all your passwords.
Unfortunately, no. Once data is leaked and distributed on the dark web and other channels, it is impossible to completely remove it. The focus must shift from removal to mitigation: making the leaked data useless by changing your passwords and protecting your accounts with MFA.
A data breach is an incident where a specific company's security is compromised, and their user data is stolen from their servers. A password leak, like the June 2025 event, is often a broader exposure of credentials that may come from many different breaches and malware infections compiled into one large collection.
The 16 billion credential leak of 2025 is a definitive, global wake up call. It signals a fundamental shift in the threat landscape away from singular, centralized company breaches and toward decentralized attacks that originate from our own devices via infostealer malware.
The critical vulnerability exploited by this leak is the deeply ingrained human habit of password reuse. This single practice is the fuel that turns a minor credential exposure into a potential cascade of devastating account takeovers.
A modern, layered defense is no longer optional. It consists of three essential pillars:
1) Proactive Endpoint Security to stop malware before it can steal anything,
2) Perfect Password Hygiene (unique, strong passwords for everything, made manageable by a password manager), and
3) Robust Authentication (universal, phishing resistant MFA).
In today's landscape, your identity is your perimeter. Protecting it isn't a one time fix but a continuous practice of vigilance and good digital hygiene.
Security questions don’t wait. Neither should you. Whether you're evaluating penetration testing as a service ptaas , need help with a red team vs. blue team assessment, or just want to see what DeepStrike can uncover, drop us a line. We’re always happy to dive in.

Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us