August 18, 2023
Updated: January 26, 2025
This article unveils an email-based vulnerability across digital platforms, demonstrating how it enables unauthorized access to company resources and suggests potential remedies for such security risks.
Mohammed Khalil

The platform (redacted.com), offers a diverse range of accounting services. A particular feature that stood out was the ability to add expenses through email. To utilize this function, users are required to forward their email receipts to receipts@redacted.com. However, before doing so, one needs to set a source email address with redacted.com to ensure that the emails are recognized and accepted.
For illustration, if I receive an invoice at user@deepstrike.io and need to upload it to the accounting website, I first need to set user@deepstrike.io on redacted.com as the source email to store the received mails from. Subsequently, I forward the invoice from user@deepstrike.io to receipts@redacted.com. The platform then processes this email, converting its HTML content into a PDF, which gets stored in the user's portal.
To leverage this vulnerability and infiltrate the company's workspace, our approach was to register on GitHub as example using the receipts@redacted.com email. Here's a step-by-step breakdown of our exploitation process:
receipts@redacted.com. It's essential to note that GitHub dispatches these confirmation emails from the address noreply@github.com.noreply@github.com, we modified the source email setting in our portal to noreply@github.com. This meant any correspondence from noreply@github.com directed to receipts@redacted.com would be rerouted and stored in our account on the portal.receipts@redacted.com. As anticipated, GitHub's confirmation email (originating from noreply@github.com) was dispatched to receipts@redacted.com.noreply@github.com as our source, the PDF containing the confirmation code was deposited into our portal account.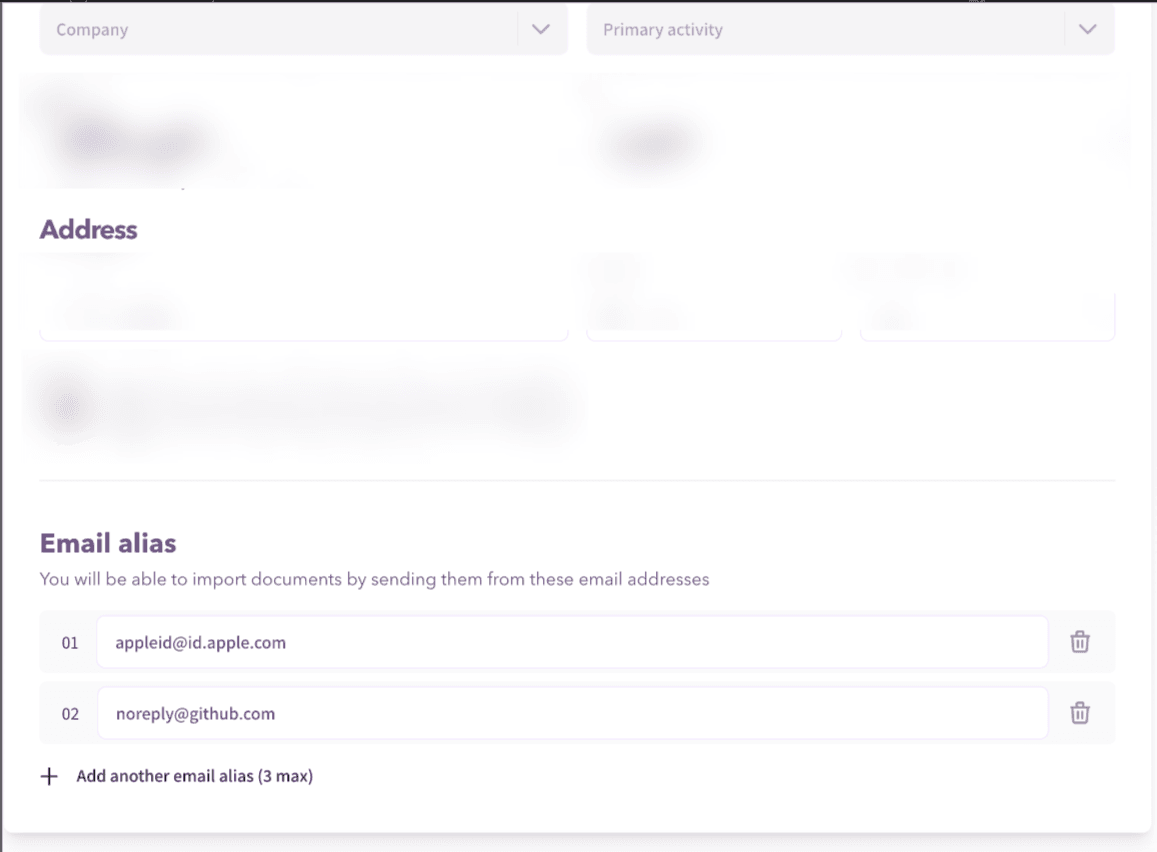
While exploiting GitHub was relatively straightforward given their consistent use of the static noreply@github.com address, other platforms presented challenges. For instance, Slack employs dynamic emails in the form of no-reply-{{Random-Token}}@slack.com, making it nearly impossible to predict the exact source email for our portal.
However, where there's a will, there's a way. We found an ingenious workaround by leveraging the trust relationships between third-party authentication providers and platforms:
appleid@id.apple.com as our source email.
receipts@redacted.com.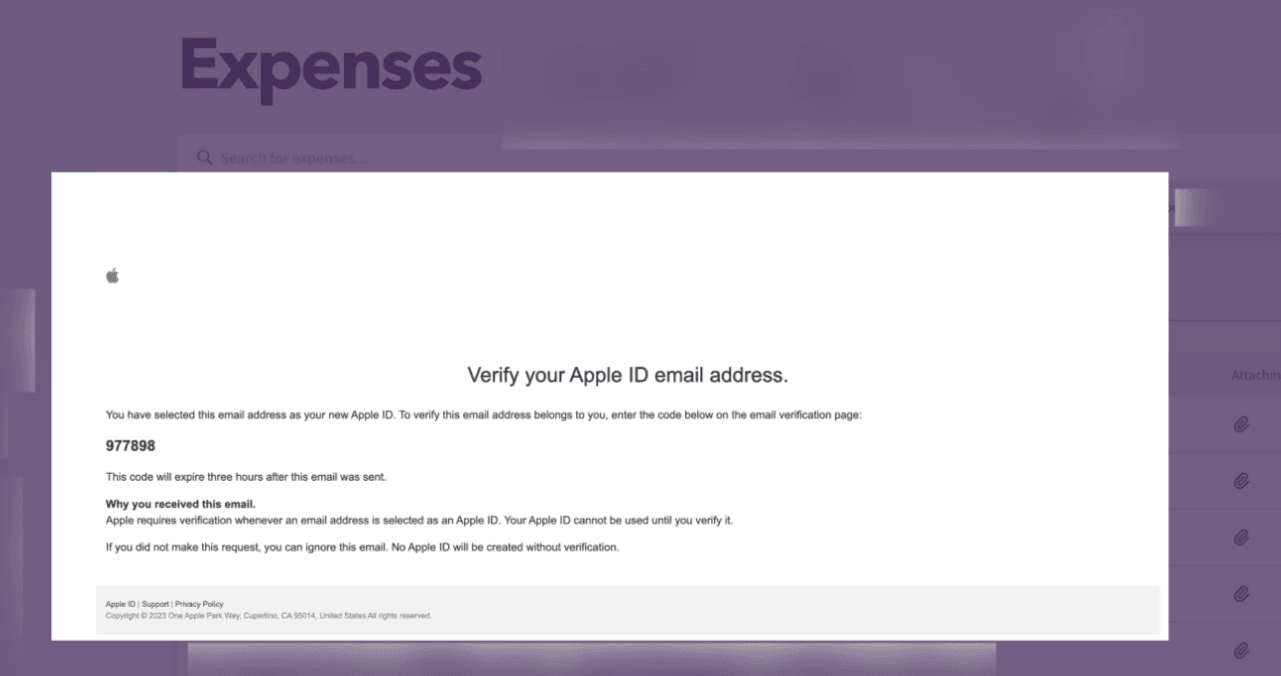
receipts@redacted.com was not only an active email on the target domain but also linked to a new Apple account.receipts@redacted.com) was authenticated, Slack trusted this authentication and allowed us to proceed, giving us access to the company’s workspace without the traditional confirmation step.In essence, we managed to circumvent the dynamic email hurdle by harnessing the implicit trust platforms place in third-party authentication providers, exemplifying the potential risks inherent in such trust relationships.
Certain accounting platforms require the use of a single source email, specifically the one utilized during sign up. For instance, if you register with user@deepstrike.io, only the emails forwarded from user@deepstrike.io to receipts@redacted.com will appear in your account. This implies you'd need to register with noreply@github.com (in the context of GitHub) to successfully exploit the system. The trick lies in the fact that some applications mandate email confirmation, while others do not. We successfully circumvented the email confirmation in certain targets because some platforms underestimate the security implications of such a requirement.
The most effective method to rectify this problem is to offer users a completely distinct email domain. For instance, if your employees are using redacted.com, establish a new domain for user emails like redacted.co, or create a new subdomain, such as mail.redacted.com. Consequently, the receipts email would change to receipts@redacted.co or receipts@mail.redacted.com. This strategy effectively compartmentalizes different email functions, significantly reducing the risk of such vulnerabilities.
We initiated our search by looking for recurring patterns in email addresses and keywords that might indicate similar functionalities, such as "receipts@" and "expenses@" To aid in our search, we employed search dorks to comb through networks for comparable features, using search terms like "“receipt@" and "Forward" We then applied these discovered patterns to identify new potential targets. One notable example was within lifestyle and time management applications, where users are often required to forward specific emails to addresses like save@lifestyle.tld We frequently found mentions of these functionalities in community forums, support sections, or official documentation, either as user queries or as described features.
Throughout our exhaustive research, we scrutinized over 75 platforms that employed similar email-based functionalities. The security landscape of these platforms is as follows:
receipts@users.target.com or receipts@target.me, further compartmentalizing their email roles and reducing risk.
Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us