April 29, 2025
Updated: April 29, 2025
The definitive 2025 phishing report attack volume, costs, AI-powered threats, and proven defenses.
Mohammed Khalil

Phishing remains the dominant initial access vector for cyberattacks in 2025, with the average phishing related data breach now costing organizations a staggering $4.88 million. The most devastating variant, Business Email Compromise (BEC), caused over $2.7 billion in reported losses in the U.S. alone in 2024, according to FBI releases annual internet crime. The game has fundamentally changed with the weaponization of Artificial Intelligence, which has driven a surge in attack sophistication and volume, with some metrics showing a 1,265% increase in phishing emails since the launch of generative AI tools. Defenses are struggling to keep pace, as attackers increasingly bypass traditional MFA and exploit the human element, which is involved in over 60% of all breaches.

For years, the term "phishing" conjured images of poorly worded emails from a foreign prince promising riches. That perception is now dangerously outdated. In 2025, phishing is no longer a nuisance; it is the sharp end of the spear for sophisticated, corporate level cyber threats. It stands as the world's number one cybercrime, with an estimated 3.4 billion malicious emails flooding inboxes every single day.
The latest data confirms its central role in the threat landscape. Phishing is the primary entry point for 36% of all data breaches, making it the most reliable method for attackers to gain an initial foothold in a target network. At its core, the enduring success of phishing lies in its exploitation of the most unpredictable element in any security system: people. The 2025(https://www.verizon.com/business/resources/reports/dbir/) underscores this reality, finding that the human element, a mistaken click, a moment of lapsed judgment is a factor in approximately 60% of all confirmed breaches.
This report provides a definitive look at the phishing landscape in 2025, drawing on data from leading authorities like IBM, Verizon, the FBI, and the Anti Phishing Working Group (APWG). We will dissect the staggering financial costs, explore the revolutionary impact of AI on attack methods, analyze the most targeted industries, and break down what modern defenses actually work. The data paints a clear picture: phishing has evolved into a corporate level existential risk, serving as the launchpad for the most destructive attacks, from nation state espionage to crippling ransomware. For a broader view, see these Cybersecurity Statistics 2025 Threats, Trends & Challenges.
The financial fallout from phishing is no longer a hypothetical risk; it's a quantifiable, multi million dollar reality. The costs extend far beyond a single compromised account, creating a ripple effect of operational disruption, regulatory fines, and long term reputational damage.
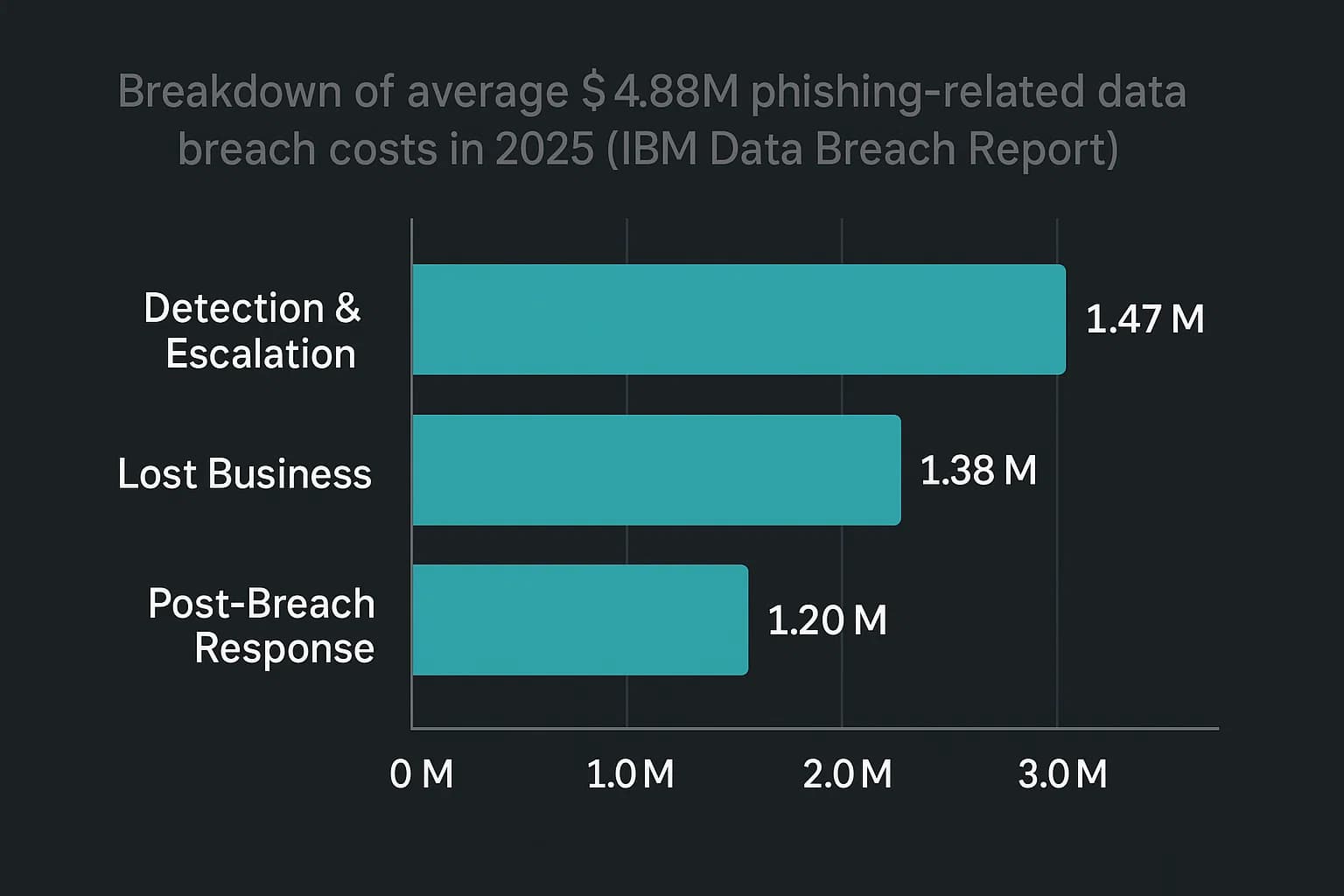
When a phishing email successfully hooks an employee, it triggers a costly chain of events. According to 2025 ibm data breach, the average cost of a data breach that originated from phishing has climbed to $4.88 million. This figure represents a significant jump from previous years, highlighting the escalating financial stakes. For organizations in the United States, the situation is even more dire, with the average breach cost reaching a record breaking $10.22 million.
These staggering figures are not abstract numbers; they are composed of tangible business expenses. The largest components of this cost include :
For a deeper dive into financial impacts, explore Cyber Insurance Claims Statistics
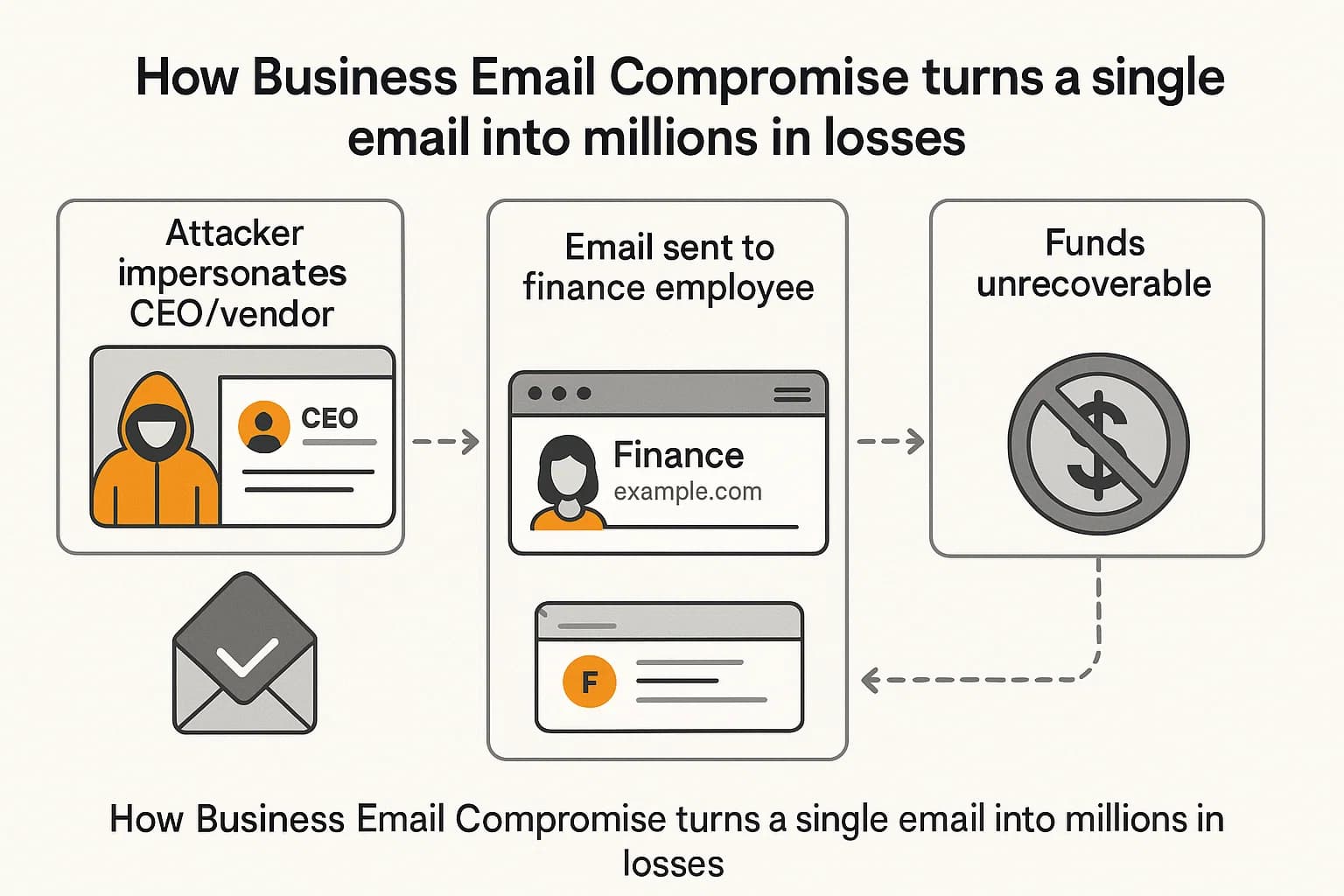
While general phishing casts a wide net, Business Email Compromise (BEC) is a precision guided munition aimed directly at an organization's bank account. In a BEC attack, threat actors use social engineering, often by impersonating a CEO or a trusted vendor, to trick employees into making fraudulent wire transfers. The financial damage is immense and immediate.
The FBI's Internet Crime Complaint Center (IC3) reported a staggering $2.77 billion in losses due to BEC in 2024 alone. Other data cited in the 2025 Verizon DBIR puts the figure even higher, at $6.3 billion in total reported losses. This makes BEC one of the most financially destructive forms of cybercrime. Incident response data confirms its prevalence, with BEC accounting for 27% of all engagements, second only to ransomware.
The amounts stolen in individual BEC attacks vary but are consistently high. The APWG trends reports reported the average requested wire transfer in Q4 2024 was $128,980, while other analyses from early 2025 show average requests around $39,315. These attacks represent direct, often unrecoverable, theft from a company's treasury, all initiated by a cleverly crafted email. To understand more about how these attacks fit into the broader landscape.
Thinking about the cost of phishing in terms of just credential theft or direct fraud is a dangerously incomplete picture. Phishing is the primary delivery mechanism for ransomware, the digital plague that has crippled businesses, hospitals, and governments worldwide. The connection is direct and statistically undeniable: 54% of all ransomware infections begin with a phishing email.
The 2025 Verizon DBIR found that ransomware was a component in 44% of all confirmed breaches, a sharp increase from 32% the previous year. While there is some good news, the median ransom payment has fallen to $115,000 as more organizations (64%) refuse to pay. The fact remains that the initial access enabling these devastating attacks is most often gained through phishing.
This causal link means that a significant portion of the multi billion dollar ransomware economy is directly subsidized by successful phishing campaigns. When calculating the risk and potential cost of a single phishing click, organizations must factor in the potential for a full scale ransomware event. This reframes the entire business case for investing in robust email security and employee training, moving it from an IT line item to a critical component of business continuity. For more on this threat, see our complete report on ransomware statistics and trends for 2025.
Studies show 82.6% of phishing emails include AI-generated content. Meanwhile, attackers increasingly target countries, industries, and organizations based on shifting global threat patterns. For geopolitical patterns, see:
Top 10 Countries Most Targeted by Cyber Attacks in 2025.
For years, a key tell tale sign of a phishing email was poor grammar or awkward phrasing. AI has eliminated that indicator entirely. Attackers are now leveraging large language models (LLMs) to generate flawless, contextually aware, and highly persuasive phishing emails that are virtually indistinguishable from legitimate communications.
The efficiency gains for attackers are astronomical. In a landmark experiment by IBM security researchers, an AI was able to construct a sophisticated phishing campaign in just 5 minutes using 5 prompts. The same task took a team of human experts 16 hours to complete. This explosive productivity allows attackers to create and launch polymorphic campaigns where each email is slightly different to evade filters at a scale previously unimaginable. According to a KnowBe4 report, AI generated content is now used in an astonishing 82.6% of phishing emails.
One of the most widely cited statistics is the 1,265% surge in phishing attacks linked to the rise of generative AI tools like ChatGPT. This number reflects the massive increase in the volume of malicious email creation. However, a more nuanced picture emerges when looking at what actually bypasses security filters and lands in user inboxes.
A detailed analysis by Hoxhunt of 386,000 malicious emails that successfully evaded enterprise email defenses found that only 0.7% to 4.7% were definitively written by AI. This suggests a critical distinction: while AI is being used to generate an unprecedented volume of attacks, today's advanced email filters are still catching the majority of low effort, generic AI generated spam.
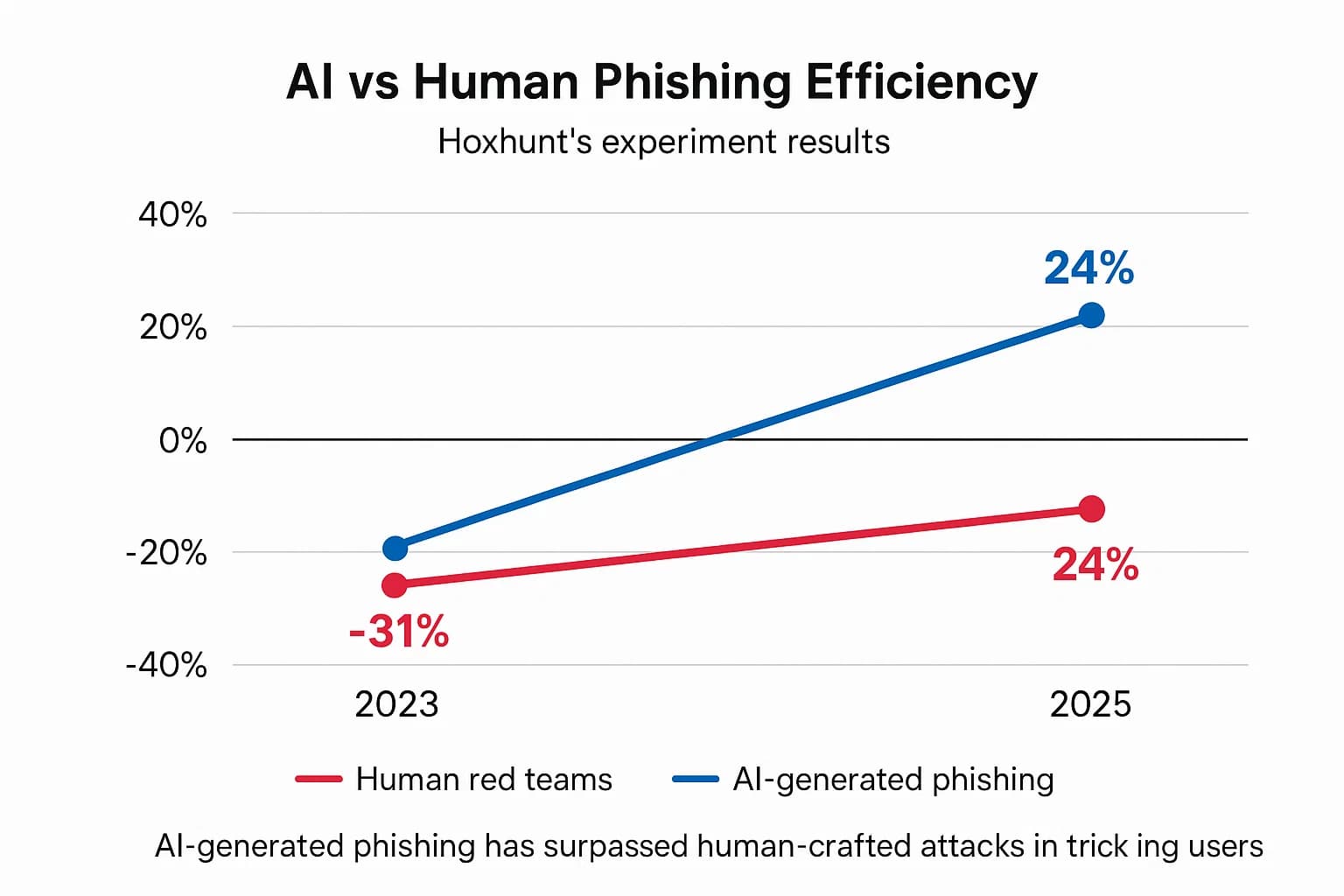
The real threat, however, lies in the attacker's learning curve. The velocity of improvement is what should concern every security leader. An ongoing experiment by Hoxhunt that pits an AI spear phishing agent against their elite human red team tells the story. In 2023, AI was 31% less effective than humans. By March 2025, the tables had completely turned: the AI agent was 24% more effective at tricking users than the human experts. This demonstrates an exponential improvement in AI's ability to craft sophisticated, targeted attacks. The implication is stark: today's defenses are being trained on yesterday's AI attacks, while tomorrow's threats will be orders of magnitude more advanced. To understand the human side of this equation, see this red team vs blue team explained article.
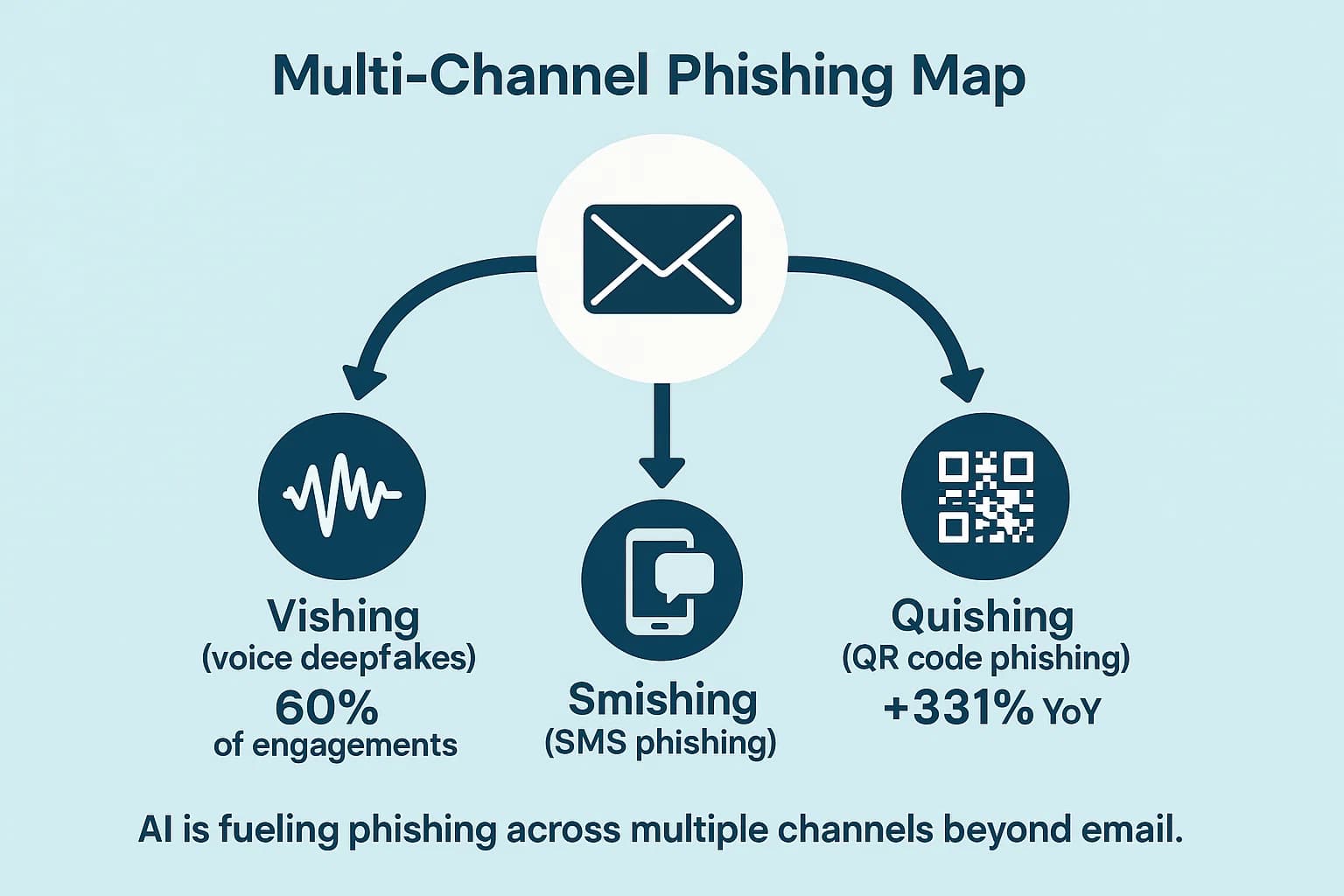
The phishing threat has broken free from the confines of the email inbox. Multi channel attacks are now the standard, with around 40% of phishing campaigns extending to other platforms like Slack, Microsoft Teams, and social media. AI is accelerating this trend across multiple vectors:
These multi channel attacks often lead to credential theft and full account takeover, as detailed in this real world case study.
Credential harvesting accounts for roughly 80% of phishing campaigns. Attackers heavily target Microsoft 365 and Google Workspace accounts.
For organizations comparing their regional security posture or evaluating vendors, explore:
Brand impersonation is widespread, with Microsoft, DocuSign, Facebook, and Amazon among the top abused brands.
Industries most targeted include:
Healthcare remains the most vulnerable.
The vast majority of phishing attacks an estimated 80% of all campaigns are designed to steal user credentials. The primary targets are cloud based services, with attackers relentlessly going after logins for Microsoft 365 and Google Workspace. These platforms are the nerve centers of modern business, and a single compromised account can provide an attacker with a treasure trove of sensitive data and further access. Protecting them requires robust web application penetration testing services and the use of the best CSPM tools for cloud security.
The 2025 Verizon DBIR confirms that this strategy is highly effective, with the use of stolen credentials identified as the initial access vector in 22% of all breaches. Once attackers have valid credentials, they can often bypass perimeter defenses and operate undetected for long periods, making credential abuse one of the most common network vulnerabilities in 2025. For more on this, see our report on password security statistics 2025.
To trick users into giving up their credentials, attackers rely on the power of brand impersonation. By creating convincing fake login pages and emails that mimic trusted companies, they lower their victims' guards. The most frequently impersonated brands include a who's who of the tech and e commerce world :
Social media platforms are a particularly fertile ground for phishing, accounting for approximately 22.5% of all phishing attacks observed by the APWG in late 2024. Attackers also frequently impersonate government agencies like the IRS, a tactic that has seen a 35% increase as they prey on taxpayers' fears of legal and financial penalties.
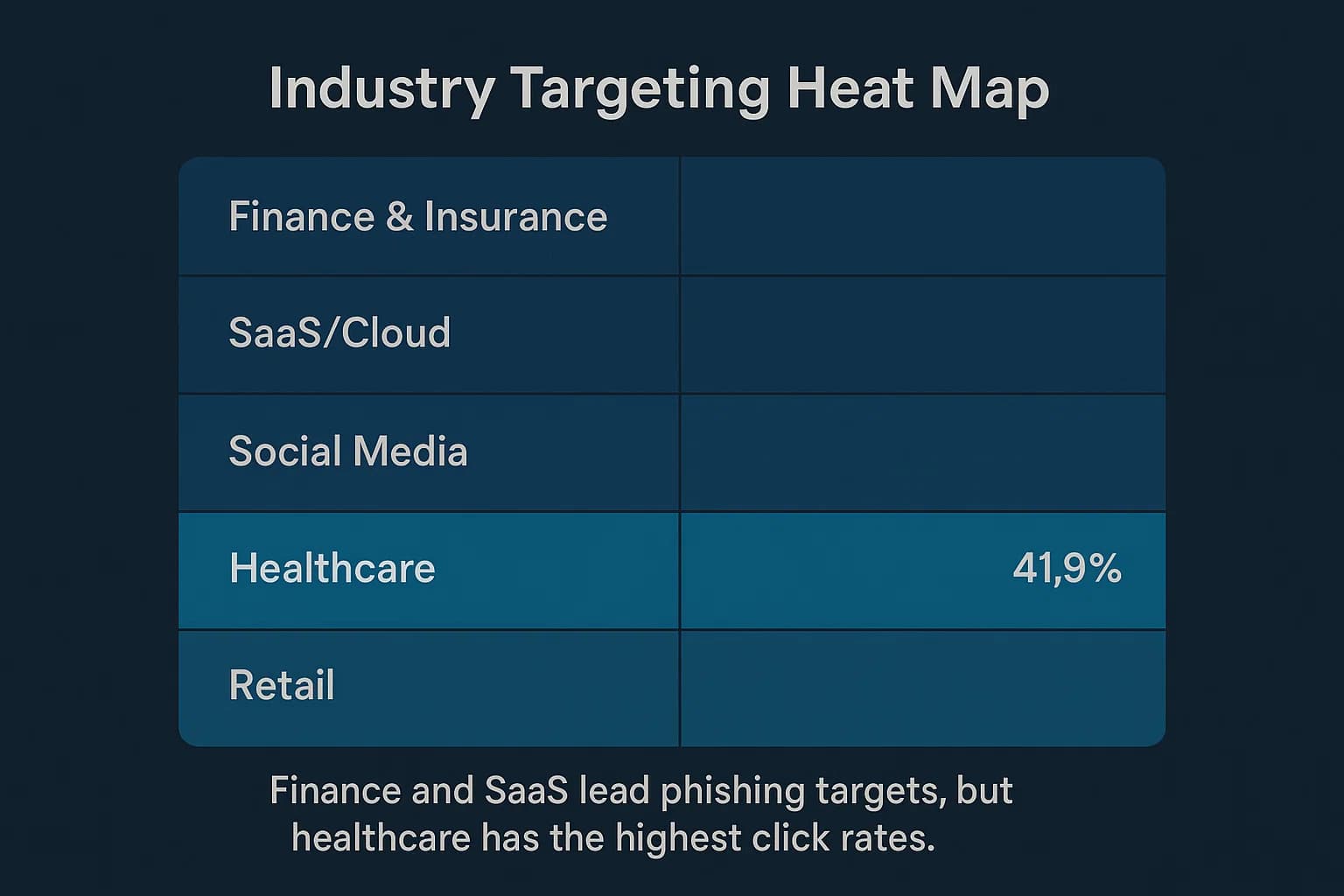
While no industry is immune, phishing attacks are not distributed evenly. Threat actors focus their efforts on sectors that are data rich, time sensitive, or have historically weaker security postures. Based on data from the APWG and security vendors like Cofense, the industries most targeted by hackers in 2025 are :
The Education sector, while not always the most targeted, has one of the highest phishing email click rates, making its users particularly vulnerable to compromise. However, it is the Healthcare industry that stands out for its susceptibility. With a baseline Phish prone Percentage (PPP) of 41.9%, healthcare employees are the most likely of any sector to click on a malicious link, a vulnerability that had devastating consequences in the Change Healthcare breach. This is why understanding Healthcare data breach statistics and trends 2025 is so critical.
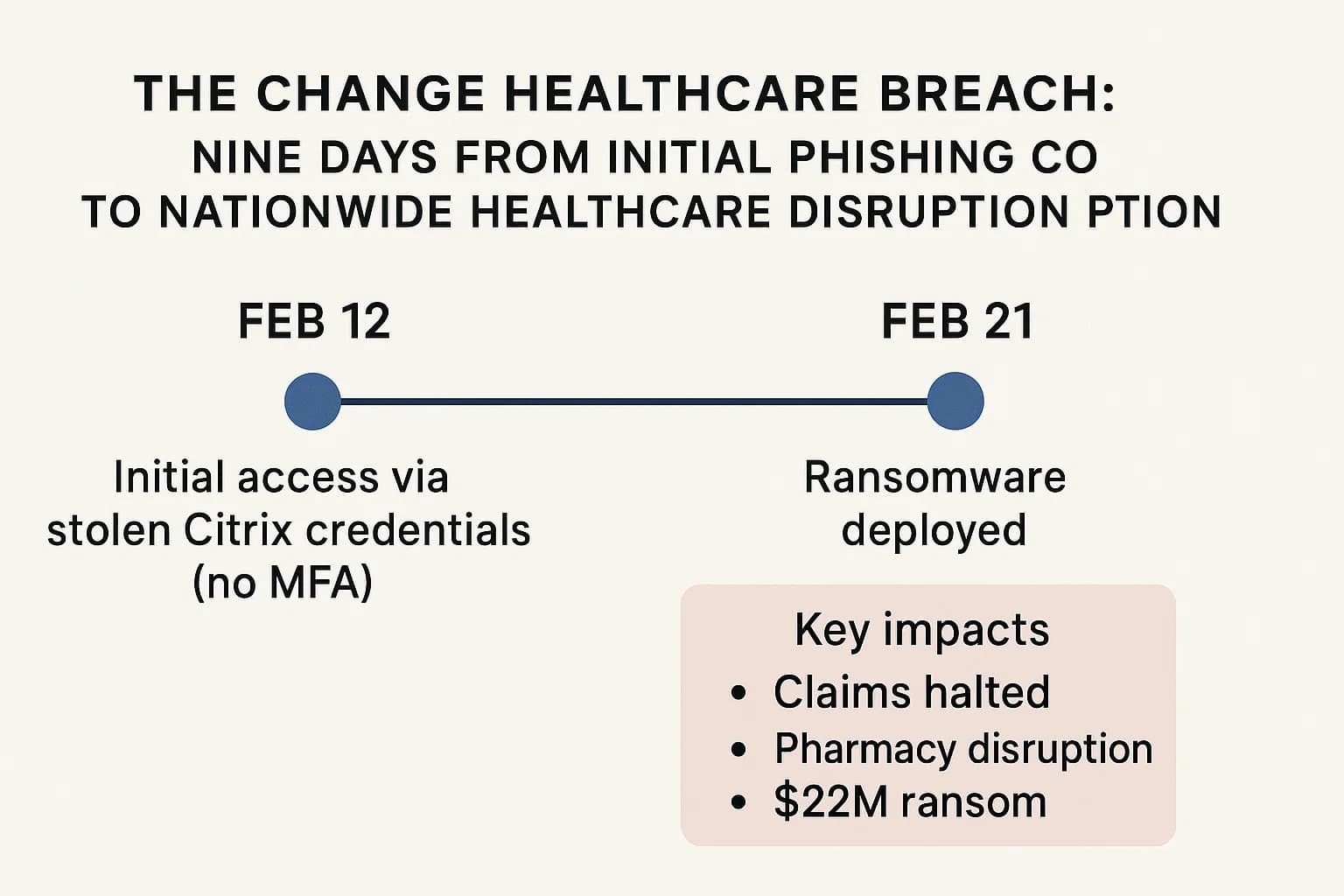
The February 2024 cyberattack on Change Healthcare, a subsidiary of UnitedHealth Group (UHG), serves as a masterclass in the catastrophic potential of a single phishing related failure. This was not an attack that relied on a sophisticated zero day exploit; it was a textbook case of attackers walking through an unlocked door, leading to a systemic breakdown of the U.S. healthcare system.
The incident began on February 12, 2024, when threat actors from the notorious ALPHV/BlackCat ransomware group gained initial access to Change Healthcare's network. They did so by using stolen credentials on a Citrix remote access portal. The critical failure, as later admitted by the UHG CEO in a congressional hearing, was that this customer-facing portal lacked multi factor authentication (MFA). From a security architect's perspective, this represents a fundamental and entirely preventable breakdown in basic cybersecurity hygiene. Leaving a remote access server exposed to the internet without MFA is akin to leaving the front door of a bank vault unlocked.
Once inside, the attackers spent nine days moving laterally throughout the network, exfiltrating an estimated 6 terabytes of sensitive data before deploying their ransomware payload on February 21. The impact was immediate and devastating. Change Healthcare is a critical node in the American healthcare infrastructure, processing 15 billion transactions annually and touching the records of roughly one in every three U.S. patients.
The attack crippled this vital system, causing a nationwide crisis:
In an attempt to prevent the public release of the stolen data, UHG confirmed it paid a $22 million ransom in Bitcoin. However, due to infighting within the ALPHV/BlackCat RaaS operation, the affiliate who conducted the attack claimed they never received their share. This led to the data not being returned and a second ransomware group, RansomHub, later claiming possession of the stolen files, illustrating the futility and risk of negotiating with criminals.
The Change Healthcare incident is the ultimate testament to the exponential consequences of foundational security failures in an interconnected ecosystem. The root cause was not a mystery; it was the absence of a basic, well established security control. This single point of failure within a critical third party vendor triggered a cascade of disruption across an entire national industry. For any CISO or business leader, this case proves that an organization's security posture is no longer defined by its own defenses, but by the security of its most critical and potentially least secure partners. It elevates third party risk management and the need for a HIPAA penetration testing checklist 2025 from a compliance checkbox to a top tier, strategic imperative.
The threat landscape is daunting, but the data also points toward a clear, multi layered strategy for building a resilient defense. It requires moving beyond legacy tools and embracing a modern approach that hardens technical controls while empowering the human element.
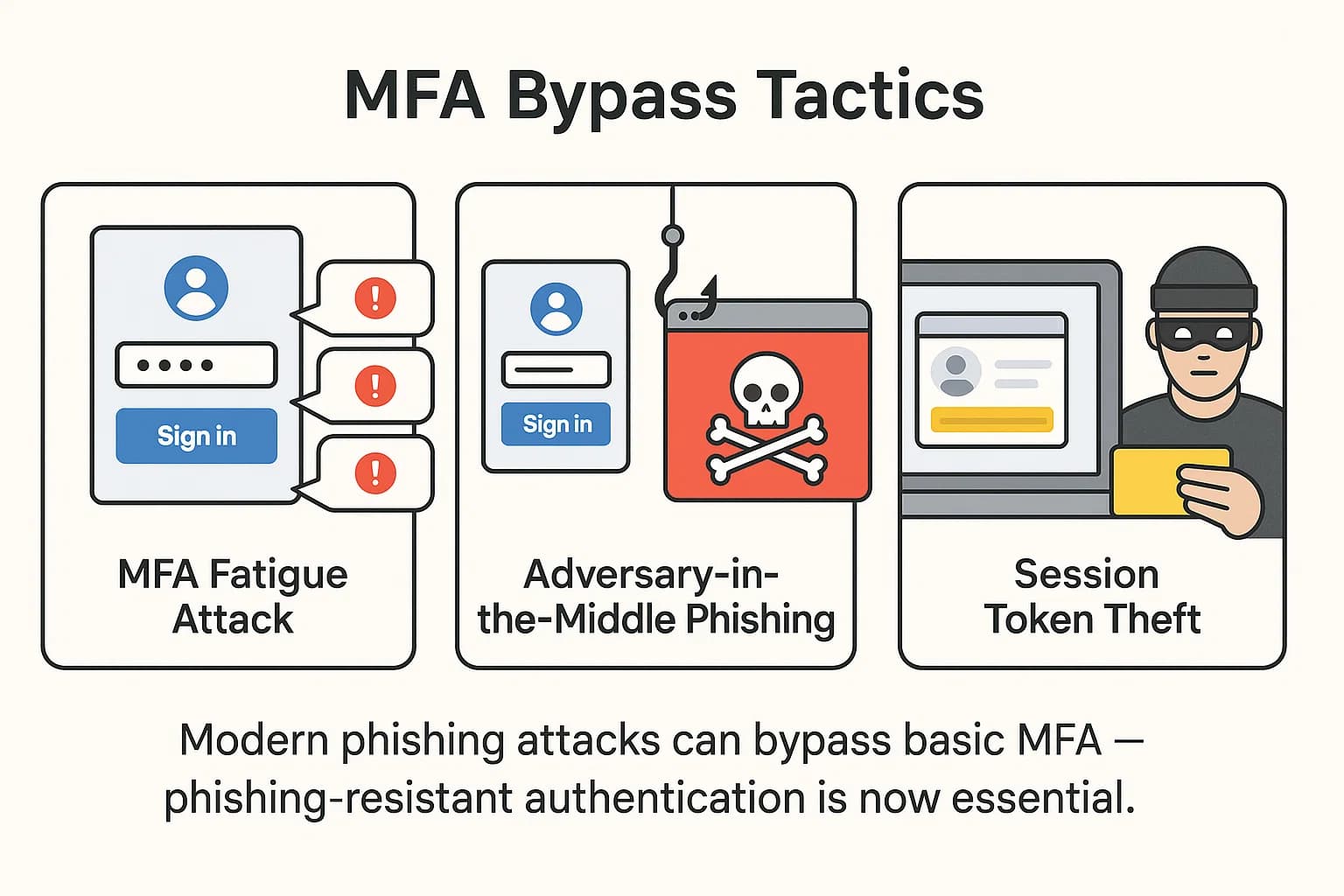
Multi factor authentication remains an essential security control, but not all MFA is created equal. Attackers are now routinely bypassing weaker forms of MFA using a variety of sophisticated techniques :
The only effective defense against these modern attacks is to adopt phishing resistant MFA. This category includes solutions like FIDO2/WebAuthn compliant hardware security keys (e.g., YubiKey) and device bound passkeys. These methods create a cryptographic bond between the user, their device, and the service, making them immune to interception and replay attacks. For more on implementing modern authentication, see this Auth0 security tips for developers.
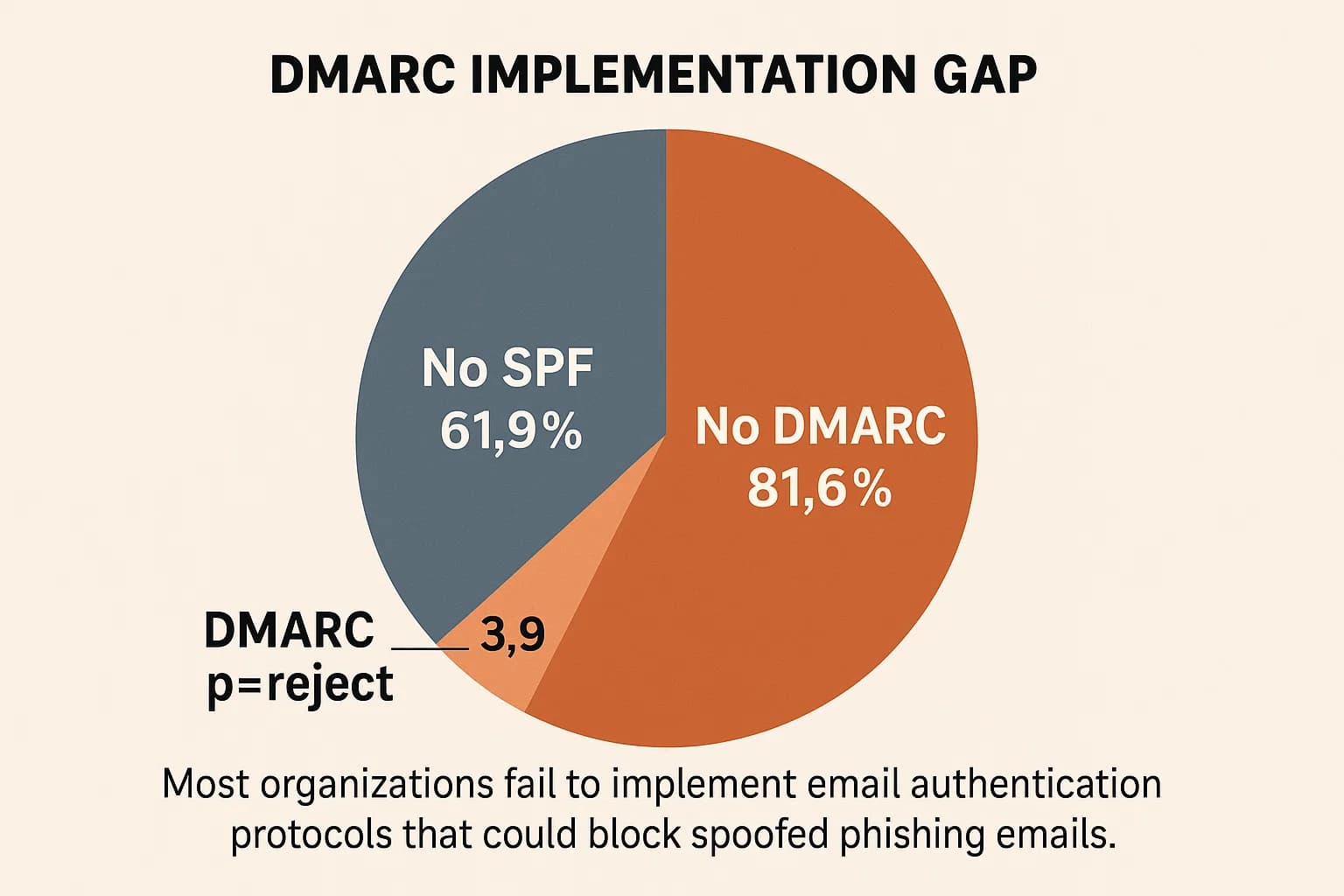
The email authentication protocols Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain based Message Authentication, Reporting, and Conformance (DMARC) are designed to prevent attackers from directly spoofing an organization's domain in phishing attacks. When properly implemented, they are highly effective.
The problem is that they are rarely implemented correctly. A recent analysis of 10 million of the internet's most popular domains revealed an alarming level of neglect :
Even among the small fraction of domains that have published a DMARC record, the vast majority use a p=none policy. This "monitoring mode" provides visibility into who is sending email on your domain's behalf but offers zero protection against spoofing. The same study found that only a minuscule 3.9% of domains enforce the most secure p=reject policy, which actively blocks unauthorized emails from being delivered.
This massive gap between best practice and common practice means that attackers often don't need to find a way to break DMARC; they can simply rely on the fact that most organizations haven't configured it to block them. For security teams, this presents a clear opportunity. Implementing a strict DMARC policy is a high impact project that directly closes a major attack vector that is being widely exploited.
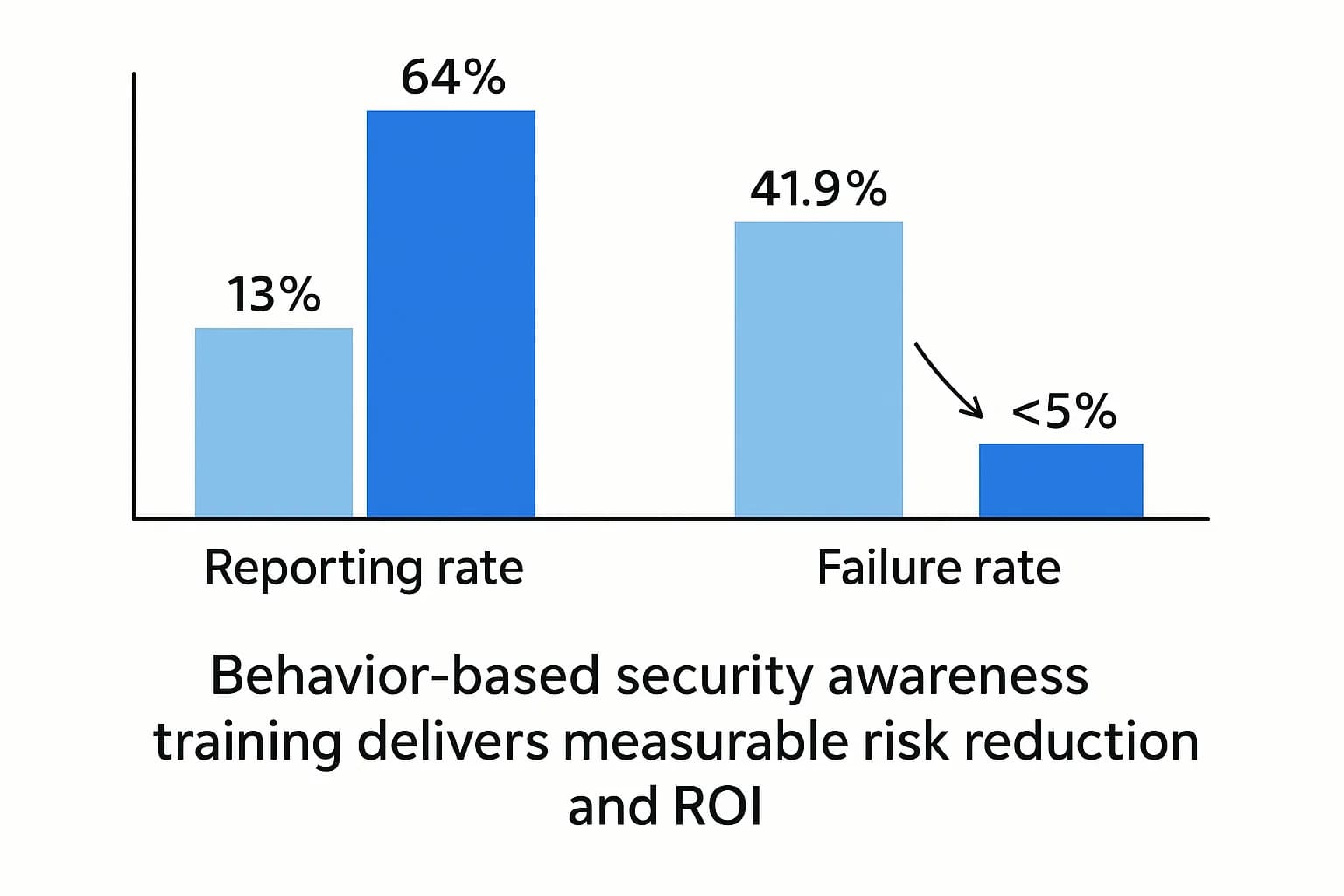
For decades, the human element was seen as the weakest link. A modern security strategy, however, treats employees as a critical layer of defense: a distributed threat detection network that can spot and report attacks that technology misses. The data proves that this approach works and delivers a significant return on investment.
Untrained users are a massive liability. The Verizon DBIR found that only 5% of users report a phishing attempt without any recent training. That figure jumps to 21% for users who have been trained within the last 30 days. This four fold increase in reporting demonstrates the immediate impact of education.
The results are even more dramatic with continuous, behavior based training programs. Data from Hoxhunt's platform, which uses millions of real and simulated phishing reports, shows that organizations can transform their workforce's security posture over time. Real threat reporting rates can soar from a baseline of 13% to an impressive 64% after 12 months of consistent training. This is the difference between having a few dozen eyes on the problem and having thousands.
The financial ROI is just as compelling. A study from the Ponemon Institute calculated a 50x ROI on security awareness training, while other reports show that effective programs can reduce the risk of a phishing related breach by up to 70%. These programs are a core component of a proactive security strategy, much like the practice of continuous penetration testing.
Phishing attacks are extremely common and represent the most prevalent cyber threat. An estimated 3.4 billion phishing emails are sent every day, and phishing is the initial attack vector in 36% of all data breaches. The APWG trends reports detected over 1 million unique phishing attack sites in the first quarter of 2025 alone, demonstrating a sustained high volume of activity.
The financial impact is severe. According to IBM data breach, the average breach originating from a phishing attack costs an organization $4.88 million. For the highly targeted variant known as Business Email Compromise (BEC), the losses are even more direct and staggering. The FBI releases annual internet crime reports that BEC schemes result in billions of dollars in losses annually, with the average fraudulent wire transfer request often exceeding $30,000.
Artificial Intelligence has fundamentally revolutionized phishing by automating the creation of highly convincing and personalized attacks at an unprecedented scale. This has led to a reported 1,265% increase in phishing email volume since the widespread availability of generative AI tools in 2022. Beyond just writing better emails, attackers are using AI to generate deepfake voices for vishing scams and to orchestrate sophisticated, multi-channel attacks across email, SMS, and collaboration platforms.
Data from authoritative sources like the APWG and Cofense shows that threat actors consistently target industries that are rich in data and financial assets. The most targeted sectors include Finance and Insurance, SaaS/Cloud services, Social Media platforms, Manufacturing, and Healthcare. The Healthcare industry is particularly vulnerable, with its employees showing the highest susceptibility to clicking on phishing links in simulations.
Employee failure rates vary significantly depending on the industry and the maturity of their security training program. The baseline Phish prone Percentage (PPP), which measures the likelihood of an untrained employee clicking a malicious link, can be as high as 41.9% in vulnerable sectors like Healthcare. However, organizations with consistent, behavior based security awareness training can dramatically reduce these failure rates, often to below 5%, while simultaneously increasing phishing report rates from under 10% to over 60%.
Yes, but with a critical distinction. Basic forms of multi factor authentication, such as SMS codes and simple push notifications, are no longer considered a sufficient defense. Attackers are actively bypassing these methods using techniques like MFA fatigue attacks and Adversary in the Middle (AiTM) phishing kits. To effectively defend against modern credential phishing, organizations must implement phishing resistant MFA, such as FIDO2 compliant hardware keys or device bound passkeys.
Microsoft consistently ranks as one of the most impersonated brands in phishing campaigns. Attackers leverage the widespread use of Microsoft 365 and Azure to trick users into providing their login credentials. Other frequently impersonated brands include major technology companies, financial institutions, and social media platforms like Docusign, Facebook (Meta), and Amazon.
The phishing statistics for 2025 paint a sobering picture. The threat is more dangerous, costly, and intelligent than ever before, fueled by the weaponization of AI and the persistent exploitation of human psychology. The data unequivocally shows that relying on single point solutions or outdated security models is a failed strategy. The sheer volume and sophistication of modern attacks will overwhelm any defense that isn't layered, adaptive, and proactive.
True readiness in this new era requires a fundamental shift in mindset. It means moving from simple awareness to a state of active defense. This involves building a resilient organization through a multi layered strategy that treats the human element as a powerful asset, not a liability. The evidence is clear: the most effective defenses combine hardened technical controls like phishing resistant MFA and properly enforced DMARC policies with AI driven threat detection and, most importantly, continuous, behavior based security training that transforms employees into a vigilant, distributed sensor network. The threats are evolving at an exponential rate; our defenses must do the same.
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us