July 7, 2025
Updated: July 7, 2025
Misconfigurations remain the #1 cause of cloud breaches. Discover how CSPM tools help secure AWS, Azure, and GCP by eliminating exploitable attack paths before it's too late.
Mohammed Khalil

In a dynamic multi cloud world, manually tracking every configuration, permission, and compliance rule across thousands of ephemeral resources is impossible. This visibility gap is where breaches are born. According to Gartner, by 2025, over 99% of cloud breaches will be the customer's fault, primarily due to these preventable configuration errors.
This is the exact problem Cloud Security Posture Management (CSPM) was built to solve. CSPM is an automated, continuous process of monitoring cloud infrastructure for risks, compliance violations, and most importantly security misconfigurations. It's the foundational layer of modern cloud security, designed to give you control over the chaos. This guide will break down exactly what CSPM tools are, why they are non negotiable in 2025, and how to implement them effectively.
The true danger of a misconfiguration lies in its role as a bridge in the attacker's kill chain. Recent data reveals a clear causal sequence: attackers abuse valid accounts as a top intrusion method , and they increasingly exploit public facing vulnerabilities. A stolen credential is only as dangerous as the permissions it holds, and a vulnerability is only as exploitable as the access it grants. A misconfiguration like an overly permissive IAM role or a public facing server is what connects a compromised identity or a software flaw to a catastrophic data breach. Therefore, CSPM's real value isn't just tweaking settings; it's about breaking the attack chain by removing the misconfigured pathways attackers rely on for lateral movement and privilege escalation.

CSPM is not a single feature but a collection of integrated capabilities that work in concert to secure the cloud control plane, the management layer where all resources are configured and controlled. Understanding its core functions reveals how it provides such comprehensive protection.
You can't protect what you can't see. This is the first principle of cybersecurity, and it's where CSPM begins. A CSPM tool connects to your cloud environments including AWS, Microsoft Azure, and Google Cloud Platform (GCP) via APIs in an agentless fashion. It then creates a comprehensive, real time inventory of every single resource you own. This includes virtual machines, containers, serverless functions, storage buckets, databases, and identity and access management (IAM) roles. This initial discovery phase is often eye opening, as it almost invariably uncovers "shadow IT" resources spun up by developers for temporary projects that were never decommissioned, creating unknown and unmonitored security risks.
Cloud environments are not static; they are in a constant state of flux. Developers deploy new code, automation scripts make changes, and resources scale up and down dynamically. A security snapshot taken on Monday could be dangerously out of date by Tuesday. CSPM addresses this with 24/7, uninterrupted monitoring to detect "configuration drift" any change that deviates from a secure baseline. The tool continuously assesses your assets against established security benchmarks like the Center for Internet Security (CIS) Benchmarks or frameworks from the National Institute of Standards and Technology (NIST).
This is the heart of CSPM. The platform automatically flags any configuration that violates a defined security policy, such as a storage bucket open to the public or a database without encryption. However, in a large environment, this could generate thousands of alerts. The real innovation in modern CSPM is contextual risk prioritization. Instead of just creating a long list of problems, it analyzes the context to answer the critical question: "Of these 1,000 alerts, which 5 actually create a viable attack path to my critical data?". It correlates misconfigurations with other risk factors like network exposure, identity permissions, and data sensitivity to surface the toxic combinations that represent a clear and present danger.
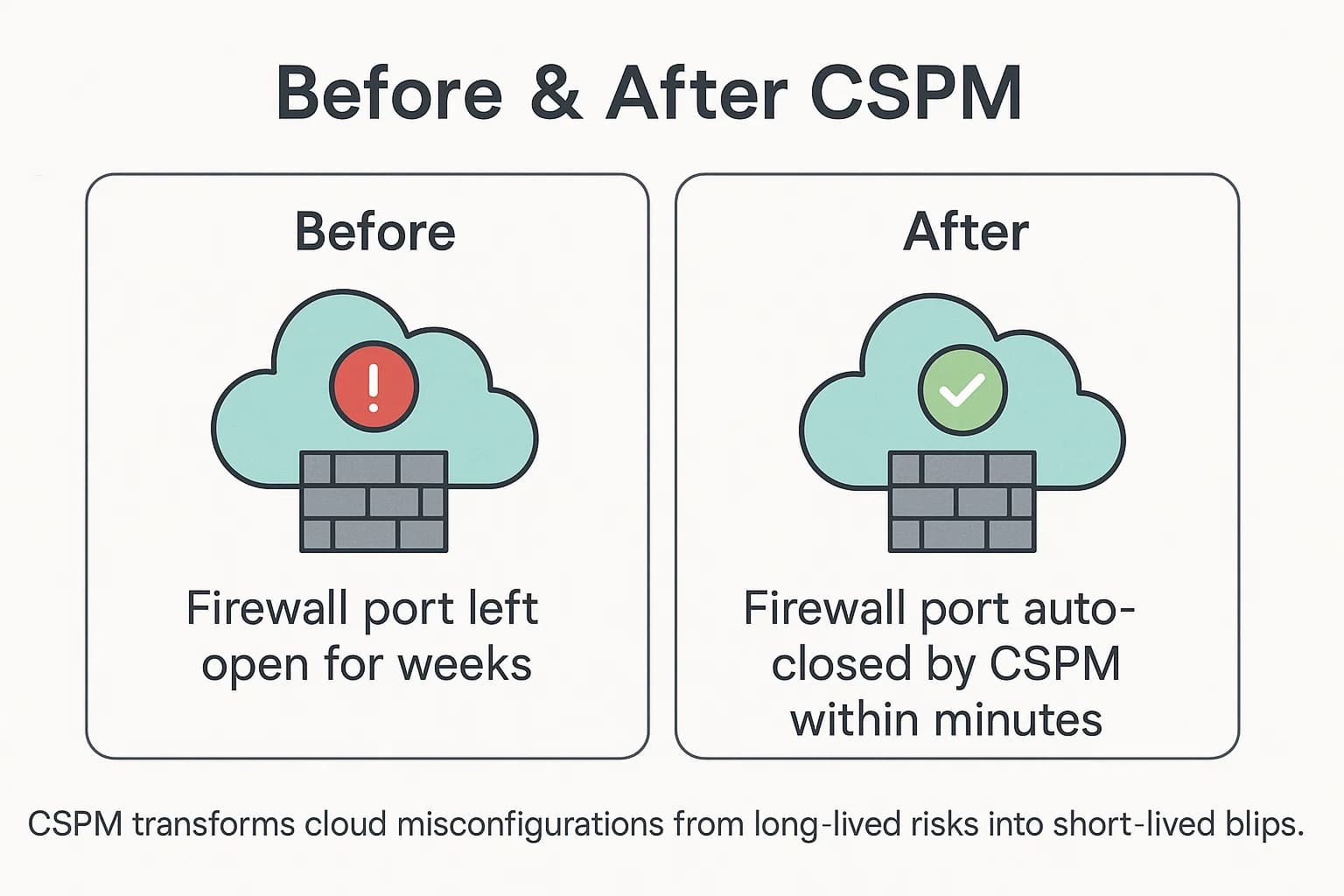
Finding a problem is only half the battle. A good CSPM provides clear, step by step instructions for remediation, often including the exact code or commands needed to fix the issue. More advanced tools offer automated remediation workflows, or "playbooks," that can correct common issues without human intervention. For instance, a playbook could automatically revoke public access to a newly created Amazon S3 bucket or add a restrictive firewall rule to an exposed virtual machine. This automation drastically reduces the mean time to remediate (MTTR) and shrinks the window of exposure from days or weeks to mere minutes.
For organizations in regulated industries, proving compliance is a constant, labor intensive process. CSPM automates adherence to frameworks like HIPAA, pci dss penetration testing , GDPR, and soc 2 penetration testing. The tool maps your live cloud configurations to specific technical controls required by these standards. It then generates audit ready reports on demand, saving security and compliance teams hundreds of hours of manual evidence gathering and documentation.
Actionable Compliance Automation Checklist
To make compliance tangible, here’s how a CSPM automates checks for major frameworks:
The need for CSPM isn't theoretical; it's driven by the hard realities of the modern threat landscape and the operational complexity of the cloud. The data from recent years paints a clear picture of why a proactive approach to posture management is no longer optional.
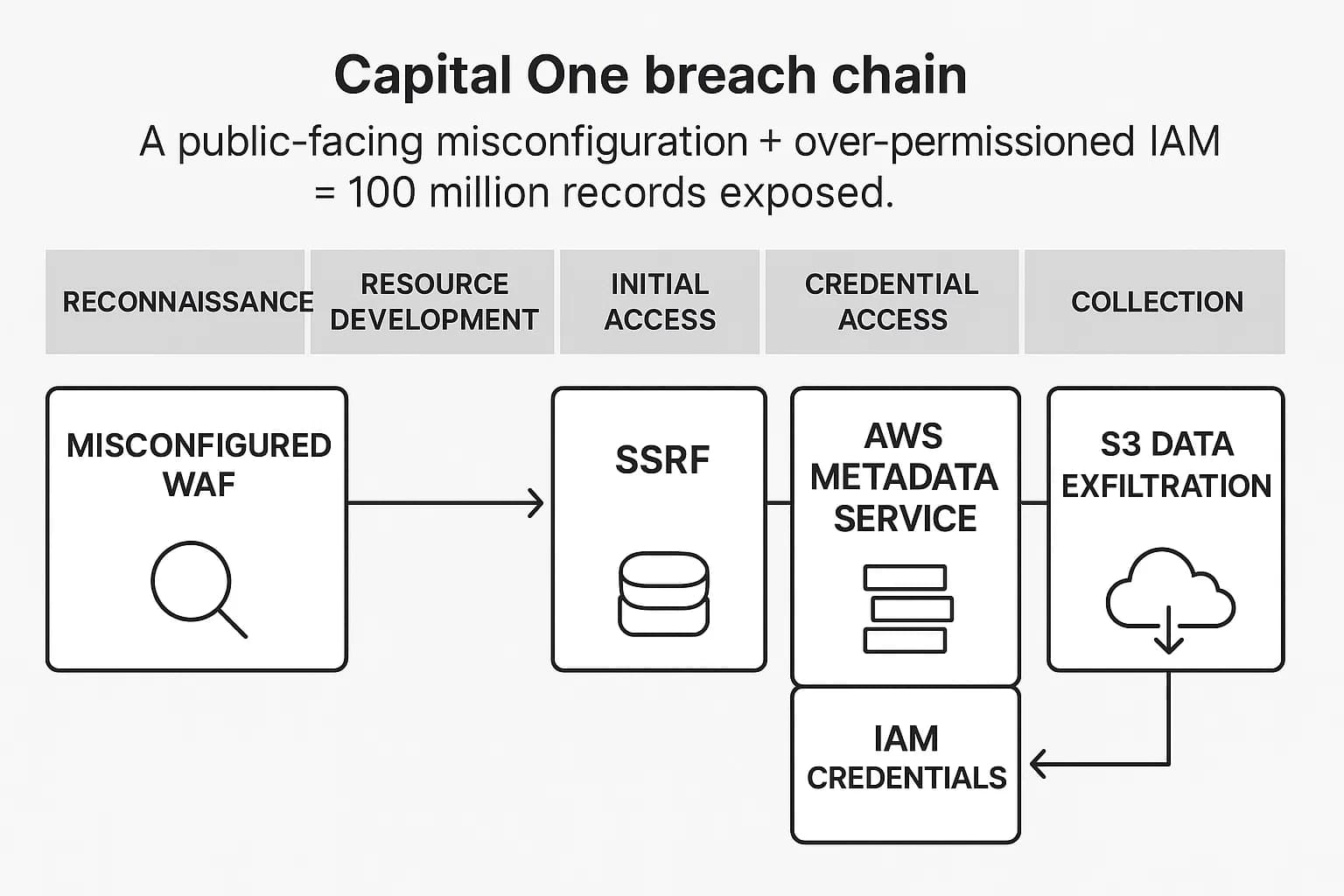
The 2019 Capital One breach remains the quintessential example of misconfiguration risk. The breach wasn't the result of a sophisticated zero day exploit; it was caused by a misconfigured web application firewall (WAF) on an AWS EC2 instance. This seemingly small error allowed an attacker to execute a Server Side Request Forgery (SSRF) attack, tricking the server into requesting its own IAM role credentials from the AWS metadata service. With these credentials, the attacker gained access to over 700 S3 buckets, exfiltrating the personal information of over 100 million customers.
This was a preventable, multi stage failure that a modern CSPM could have flagged at several points:
This problem has not gone away. Misconfigurations remain the root cause of the vast majority of cloud breaches. The IBM Cost of a Data Breach Report 2024 found that breaches involving data spread across multiple environments like public cloud, private cloud, and on premises were the most expensive, costing organizations over $5 million on average. These are precisely the kinds of complex environments where misconfigurations thrive.
Most enterprises today don't live in a single cloud; they operate in a multi cloud world, using a mix of AWS, Azure, and GCP to leverage the best services from each provider. This strategic choice, however, creates a massive security headache. Each platform has its own unique services, terminology (e.g., Amazon VPC vs Azure VNet), IAM models, and security controls. Managing security consistently across these disparate environments is a significant challenge.
A CSPM tool acts as a universal translator and a single pane of glass. It normalizes data from all connected clouds and presents it in a unified dashboard. This allows security teams to define one central security policy and enforce it consistently everywhere, preventing the dangerous visibility gaps and security silos that naturally arise from managing each cloud independently.
The role of CSPM has evolved dramatically. It is no longer just a runtime operational tool for security teams; it has become a critical component of the Auth0 security best practices workflow. In the past, security was a gate that developers had to pass through at the end of the development cycle. This created friction and slowed down innovation. Fixing a misconfiguration in a live production environment is slow, costly, and disruptive.
Today, most cloud infrastructure is defined as code (IaC) using templates like HashiCorp Terraform or AWS CloudFormation. Modern CSPM tools can scan these IaC templates for security issues before they are ever deployed to the cloud. By integrating directly into the CI/CD pipeline and providing feedback within developer tools like GitHub, CSPM "shifts security left." This proactive approach empowers developers to find and fix potential misconfigurations at the source code level, dramatically reducing the number of vulnerabilities that ever reach production. This transforms cloud security from a reactive, adversarial process into a proactive, collaborative one, addressing a major source of friction between security and development teams.
Implementing a CSPM solution follows a logical, cyclical process designed to establish and maintain a strong security posture. Here’s a breakdown of the key steps.
The journey begins by connecting the CSPM tool to your cloud accounts. This is typically done by creating an IAM role in your cloud environment (e.g., AWS, Azure, GCP) and granting the CSPM platform's service account read only API permissions to assume that role. This agentless approach is a key advantage, as it means no software needs to be installed on your individual workloads, making deployment fast, frictionless, and non disruptive to performance. Once connected, the tool immediately begins a discovery process, using the cloud provider's APIs to catalog every asset. This creates a complete and continuously updated inventory, often revealing dozens or even hundreds of previously unknown "shadow IT" resources.
With full visibility established, the CSPM tool compares your environment's configurations against a chosen security framework. This serves as the "golden standard" or baseline for what a secure configuration should look like in your organization. Most CSPM tools come with a rich library of pre built policy packs that map to industry standards like the CIS Benchmarks, regulatory frameworks like pci dss penetration testing, or security principles outlined by the fedramp penetration testing. You can also create your own custom policies tailored to your organization's specific risk appetite.
The tool continuously scans for any deviations from your established baseline. When a misconfiguration is found such as an unencrypted database, an overly permissive IAM role, or a public facing port on a server it doesn't just generate a generic alert. This is where modern CSPM platforms truly shine. They analyze the full context of the finding. The platform asks critical questions: Is this exposed resource connected to the public internet? Does it contain sensitive data? Could an attacker pivot from this resource to gain higher privileges? By correlating multiple risk factors, the tool builds a graph of potential attack paths, assigns a risk score, and prioritizes the handful of issues that pose a genuine, immediate threat to your organization.
For the high priority risks that have been identified, the CSPM tool provides actionable, guided remediation steps. This often includes the exact CLI command or console instructions needed to fix the issue, eliminating guesswork for the operations team. For many common misconfigurations, the platform can trigger automated remediation. This might be a one click action in the console or a fully automated playbook that runs without any human intervention, such as quarantining a resource or reverting a risky change. To streamline the process and ensure accountability, these alerts and remediation workflows can be integrated directly into developer and operations tools like Jira, Slack, or ServiceNow.
Before and After: A Remediation Scenario
Finally, the CSPM tool aggregates all this data into intuitive dashboards and actionable reports. Security leaders can track posture trends over time and measure improvement. Development teams can see a prioritized list of the specific issues assigned to them. And Governance, Risk, and Compliance (GRC) teams can generate on demand compliance reports for auditors with the click of a button, complete with evidence of control effectiveness. This creates a continuous feedback loop that drives ongoing improvement of the organization's overall security posture.
Selecting a CSPM solution is a critical decision. Not all tools are created equal, and the right choice depends on your specific environment, team skills, and security goals. Use this checklist to evaluate potential vendors and find the best fit for your organization.
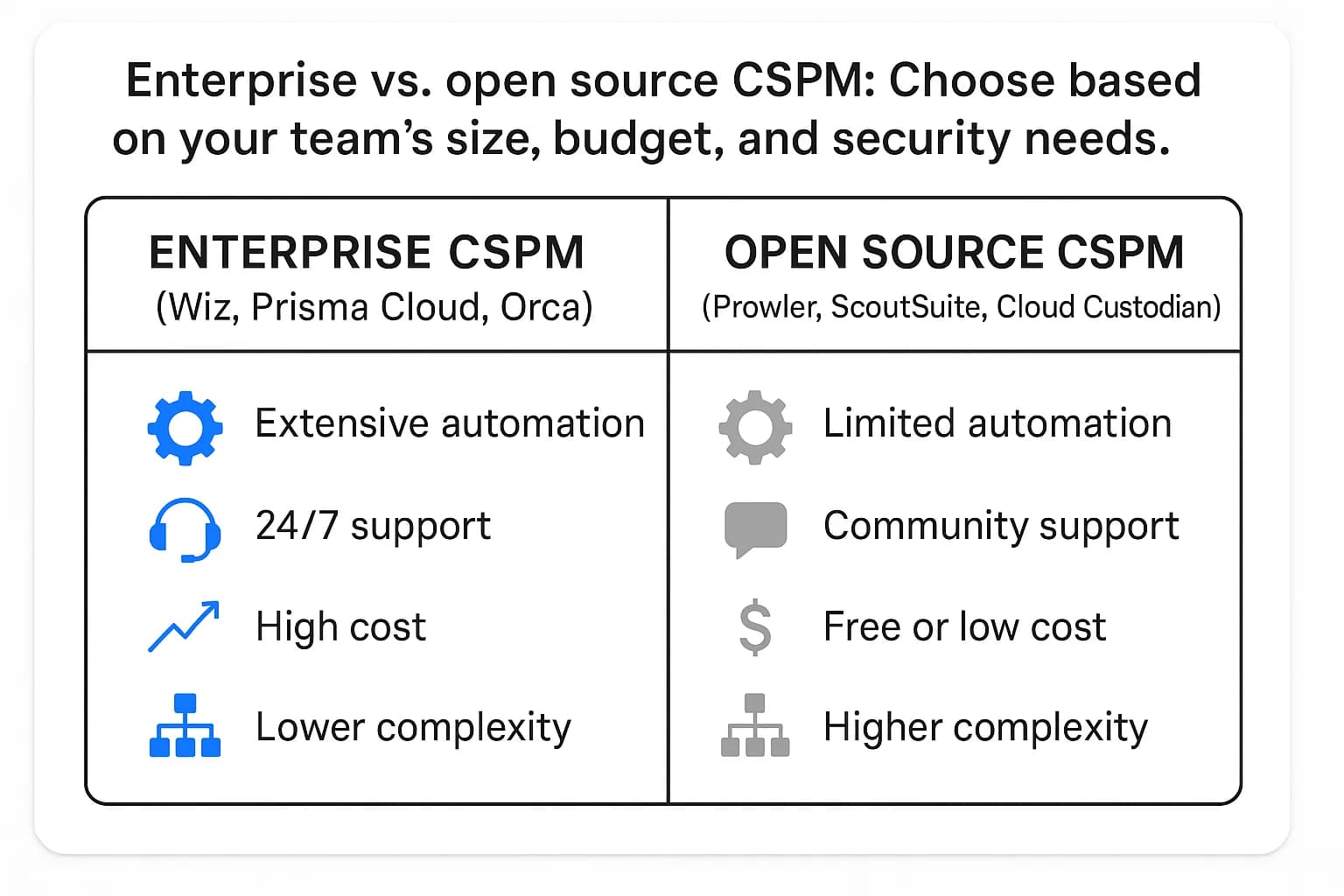
Choosing the right CSPM tool depends heavily on your organization's resources, expertise, and specific needs. The market is broadly divided into two categories: comprehensive enterprise platforms and focused open source tools.
Enterprise grade tools like Wiz, Palo Alto Networks Prisma Cloud, and Orca Security are designed as comprehensive, all in one solutions, often as part of a broader Cloud Native Application Protection Platform (CNAPP). These platforms offer a unified dashboard for multi cloud environments (AWS, Azure, GCP), combining CSPM with other critical functions like CWPP (workload protection) and CIEM (identity management). According to the Gartner® Peer Insights™ 'Voice of the Customer' for Cloud Security Posture Management, these vendors are consistently recognized for their vision and execution.
Open source tools like Prowler (primarily for AWS, with growing Azure/GCP support), ScoutSuite, and Cloud Custodian offer powerful, community driven scanning capabilities. They are excellent for performing specific, targeted security checks and integrating into custom scripts and CI/CD pipelines.
Quick Comparison: Top Open Source CSPM Tools
Modern CSPM has evolved far beyond simple compliance checklists. Its real power lies in its ability to facilitate threat modeling by connecting individual, seemingly low risk misconfigurations into a visual map of a potential attack path. By understanding how CSPM prevents data breaches, you can prioritize fixes that break the attacker's kill chain.
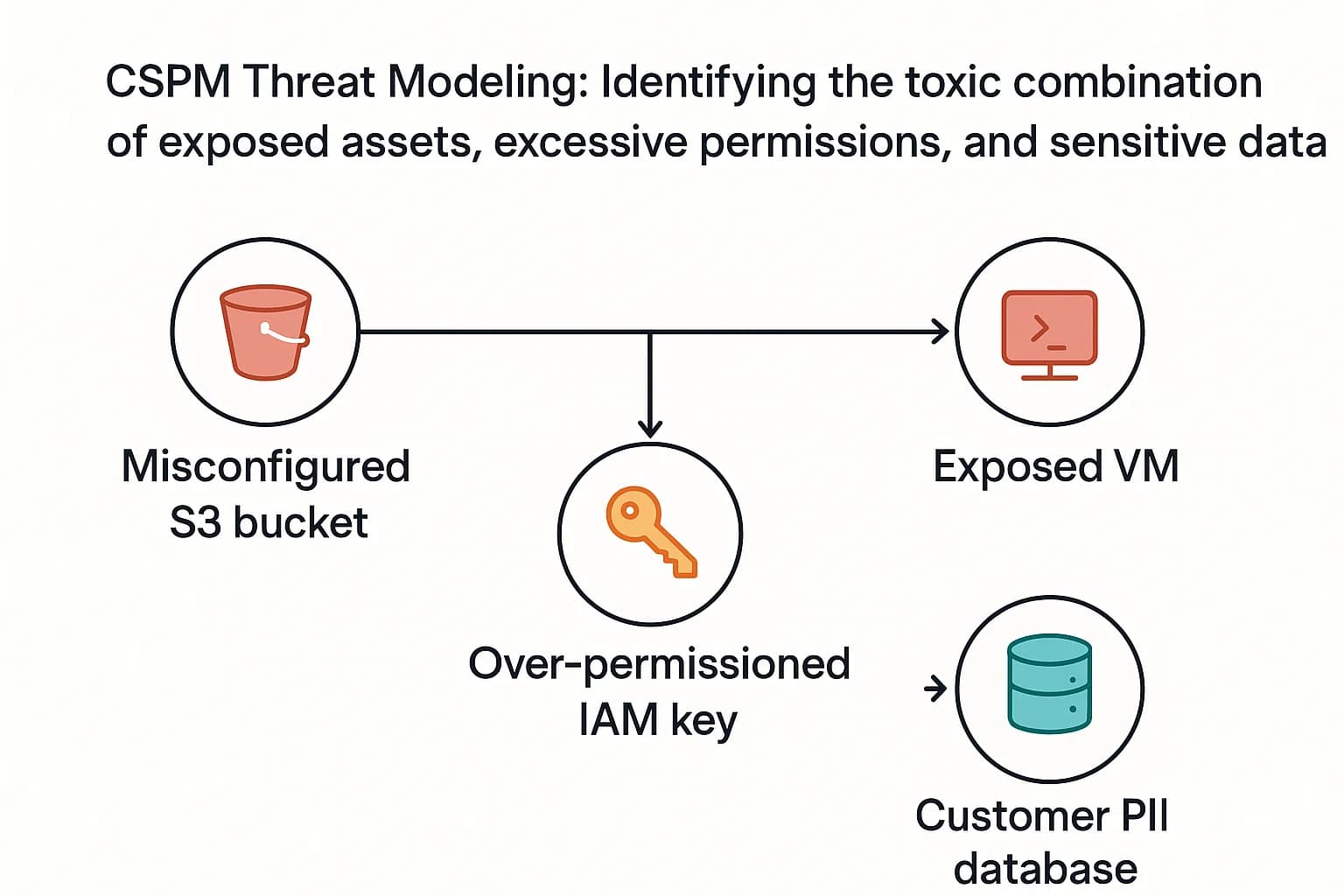
Let's walk through a common attack scenario, mapping each step to the MITRE ATT&CK® framework and seeing how an integrated CSPM/CNAPP solution would provide critical alerts.
The cloud security market is flooded with acronyms, creating significant confusion for buyers. Understanding the CSPM vs CIEM vs CWPP vs CASB distinction, and more importantly, how they are converging, is key to building a modern security strategy.
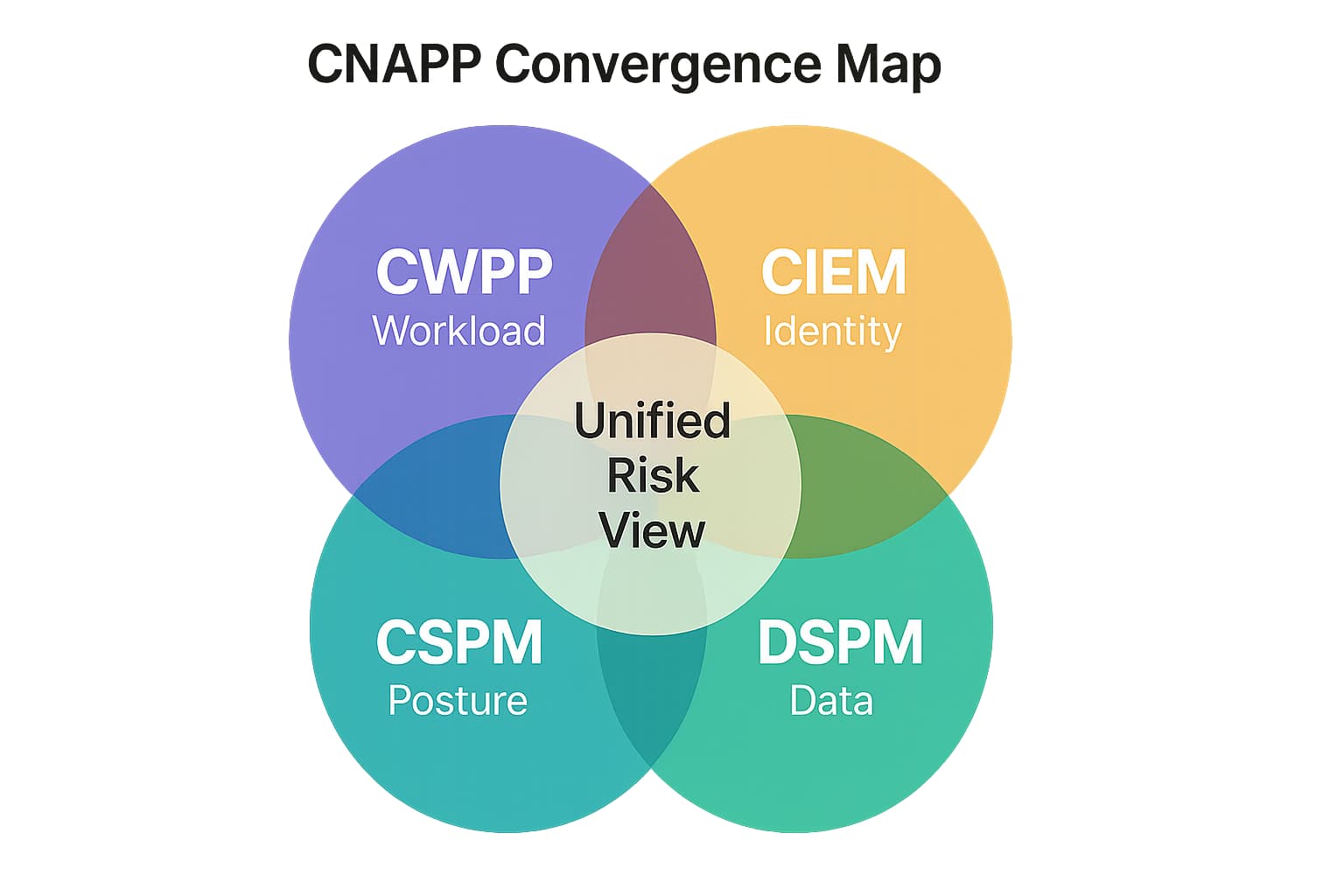
The "alphabet soup" of security tools CSPM, CWPP, CIEM, DSPM isn't just a random collection of products. It represents an evolutionary path that is rapidly converging toward a single, integrated platform: the Cloud Native Application Protection Platform (CNAPP).
Initially, organizations bought separate point solutions to solve specific problems: CSPM for infrastructure configuration, CWPP for workload protection, and CIEM for identity management. They quickly discovered a critical flaw in this approach: these tools operated in silos, creating fragmented visibility and a disjointed understanding of risk. A security team might get an alert from their CSPM about a public S3 bucket and a separate alert from their CWPP about a vulnerability on a VM. What they couldn't see was that the vulnerable VM had access to the public bucket, creating a critical, exploitable attack path.
Gartner recognized this fundamental problem and defined the CNAPP category to describe platforms that integrate these functions. The market has validated this vision; Gartner predicts that by 2025, 75% of new CSPM purchases will be part of an integrated CNAPP offering. CSPM is the foundational layer of a CNAPP. It provides the essential context about the cloud infrastructure, the "map of the city" that allows other security functions to operate intelligently. Without CSPM, a CWPP doesn't know if a workload is exposed to the internet, and a CIEM doesn't know which identities have dangerous permissions to critical, misconfigured resources.
Here’s how CSPM compares to its peers and how they work together within a modern security architecture.
Despite its growing importance, several misconceptions about CSPM persist. Clearing these up is crucial for organizations to make informed decisions about their cloud security strategy.

Adopting a CSPM tool is a strategic move that requires a clear plan. Follow this checklist to ensure a successful implementation and maximize its value.
A CSPM tool automatically scans your cloud environments (like AWS, Azure, and GCP) to find and fix security misconfigurations. It provides a complete inventory of all your cloud assets, continuously monitors them for policy violations and compliance gaps, prioritizes the most critical risks, and helps automate the remediation process to prevent data breaches.
CSPM focuses on securing the cloud infrastructure and control plane (e.g., "Is this network configured correctly?"). A Cloud Workload Protection Platform (CWPP) focuses on the security of the individual workloads running on that infrastructure (e.g., "Is this running container infected with malware?"). They are complementary, and modern CNAPP solutions integrate both to provide comprehensive protection.
CSPM prevents data breaches primarily by identifying and remediating the root cause of most cloud attacks: misconfigurations. By automatically detecting issues like publicly exposed storage buckets, excessive user permissions, or unencrypted databases, CSPM tools close the security gaps that attackers exploit to gain initial access, escalate privileges, and exfiltrate data.
For AWS, leading enterprise CSPM tools like Wiz, Prisma Cloud, and Orca Security offer deep integration and contextual risk analysis. For those seeking open source solutions, Prowler is highly regarded for its extensive AWS specific security checks, while ScoutSuite and Cloud Custodian are also popular choices for auditing and automated governance.
Yes, absolutely. This is a core function of CSPM. These tools come with pre built policy packs that map directly to the technical controls required by frameworks like HIPAA, pci dss penetration testing, SOC 2, and GDPR. They automate compliance checks and generate audit ready reports.
The biggest challenge CSPM solves is the lack of visibility and control in complex, dynamic multi cloud environments. It automates the otherwise impossible task of manually tracking thousands of configurations, preventing the human error and configuration drift that lead to the majority of cloud data breaches.
While no single tool can "prevent" all ransomware attacks, CSPM plays a crucial defensive role. Ransomware campaigns often exploit misconfigurations to gain initial access or move laterally within a network. By hardening your cloud infrastructure, closing exposed ports, enforcing least privilege access, and identifying vulnerable configurations, CSPM significantly reduces the attack surface that ransomware actors depend on to succeed.
The journey to the cloud has created unprecedented opportunities for innovation, but it has also created an attack surface of immense scale and complexity. Relying on manual checks and traditional, siloed security tools is no longer a viable strategy in this new landscape. The data is clear: misconfigurations are the Achilles' heel of cloud security, and the financial and reputational costs of a resulting breach are staggering.
Cloud Security Posture Management is the definitive answer to this challenge. It is the foundational technology that enables organizations to move from a state of reactive, chaotic firefighting to one of proactive, disciplined cloud governance. By providing automated cloud security posture management with visibility, contextual risk prioritization, and continuous compliance, CSPM tools empower you to tame the complexity, secure your innovations, and build a resilient security posture that can stand up to the threats of 2025 and beyond.
Looking to secure your multi cloud infrastructure? Our penetration testers and cloud security engineers will audit your configuration and deploy CSPM best practices customized to your environment. for a 1:1 strategy session.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us