August 5, 2025
Updated: August 5, 2025
Why the U.S. healthcare sector remains the costliest and most targeted industry for data breaches and how to stop it.
Mohammed Khalil

The threat of a healthcare data breach has evolved far beyond a simple IT problem. In 2025, it represents a systemic risk to patient safety, financial stability, and the operational integrity of the entire healthcare ecosystem. Attackers are no longer just stealing data; they're crippling hospital operations with ransomware, creating life or death scenarios where care is delayed or denied.
The core issue has become painfully clear: adversaries are exploiting foundational gaps in security, often basic, preventable weaknesses and the consequences have never been higher. This article provides a definitive look at the state of healthcare data breaches in 2025. We’ll break down the latest data breach statistics, dissect the most common attack vectors, learn from the year's most devastating breaches, and provide an actionable, expert backed plan to fortify your defenses.
The data for 2024 and early 2025 paints a stark picture. While some global trends show minor improvements, the situation in the U.S. healthcare sector has intensified, driven by mega breaches and a punitive regulatory environment.
Healthcare Remains the Costliest Industry for a Data Breach
For the 14th consecutive year, the healthcare industry suffers the most expensive data breaches. According to the average cost of a healthcare data breach in 2025, the average cost for a healthcare breach is $7.42 million. While this figure represents a decrease from the previous year's highs, it still towers over the global all industry average of $4.44 million.
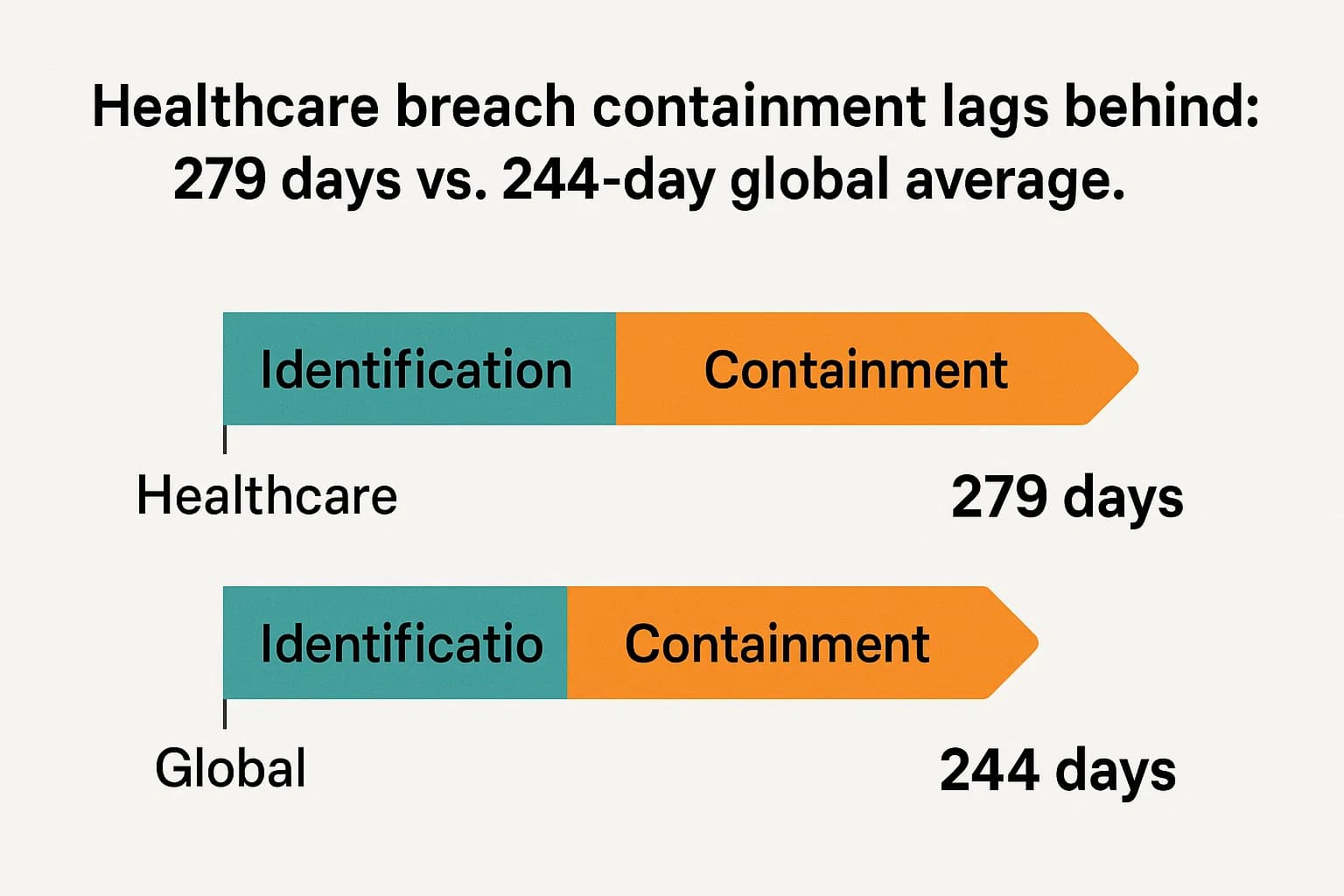
A key factor inflating these costs is the exceptionally long time it takes for healthcare organizations to respond. The average breach lifecycle in healthcare the time to identify and contain an incident is 279 days, a full five weeks longer than the global average. This extended dwell time gives attackers months to move through networks, exfiltrate data, and maximize damage, which directly translates to higher recovery and remediation costs.
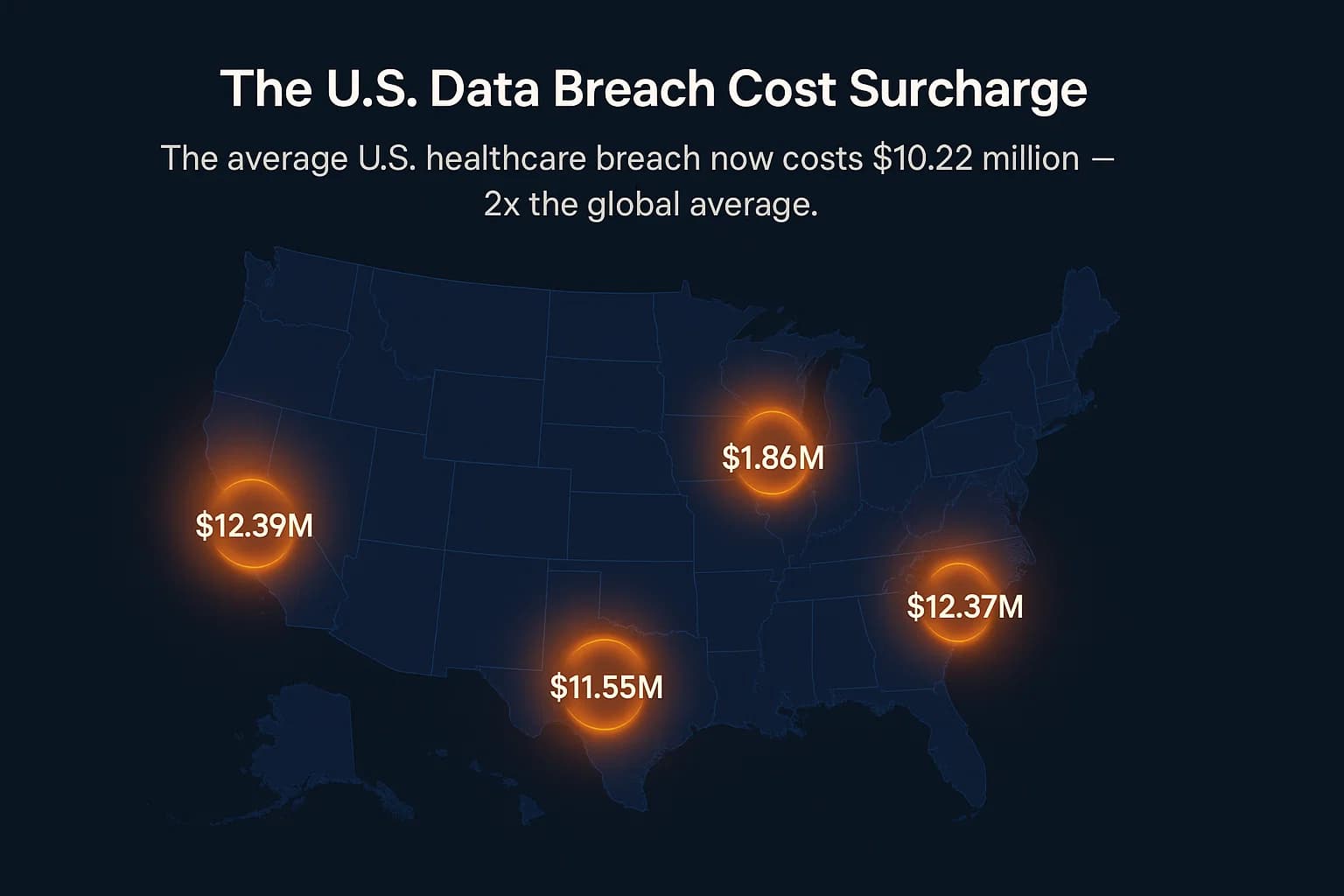
The "U.S. Surcharge": Why American Breaches Cost More
While the global average cost of a data breach actually decreased for the first time in five years, the cost in the United States surged by 9% to a new record of $10.22 million. This growing gap isn't just about technical cleanup; it's a reflection of America's unique and aggressive regulatory and legal landscape. The IBM report explicitly identifies "higher regulatory fines" as a primary driver of this "U.S. surcharge". This means that for any U.S. healthcare organization, the financial risk posed by OCR penalties and class action lawsuits is now a massive component of the total breach cost, demanding attention from not just the CISO, but the entire C suite.
From Frequent Incidents to Catastrophic Mega Breaches
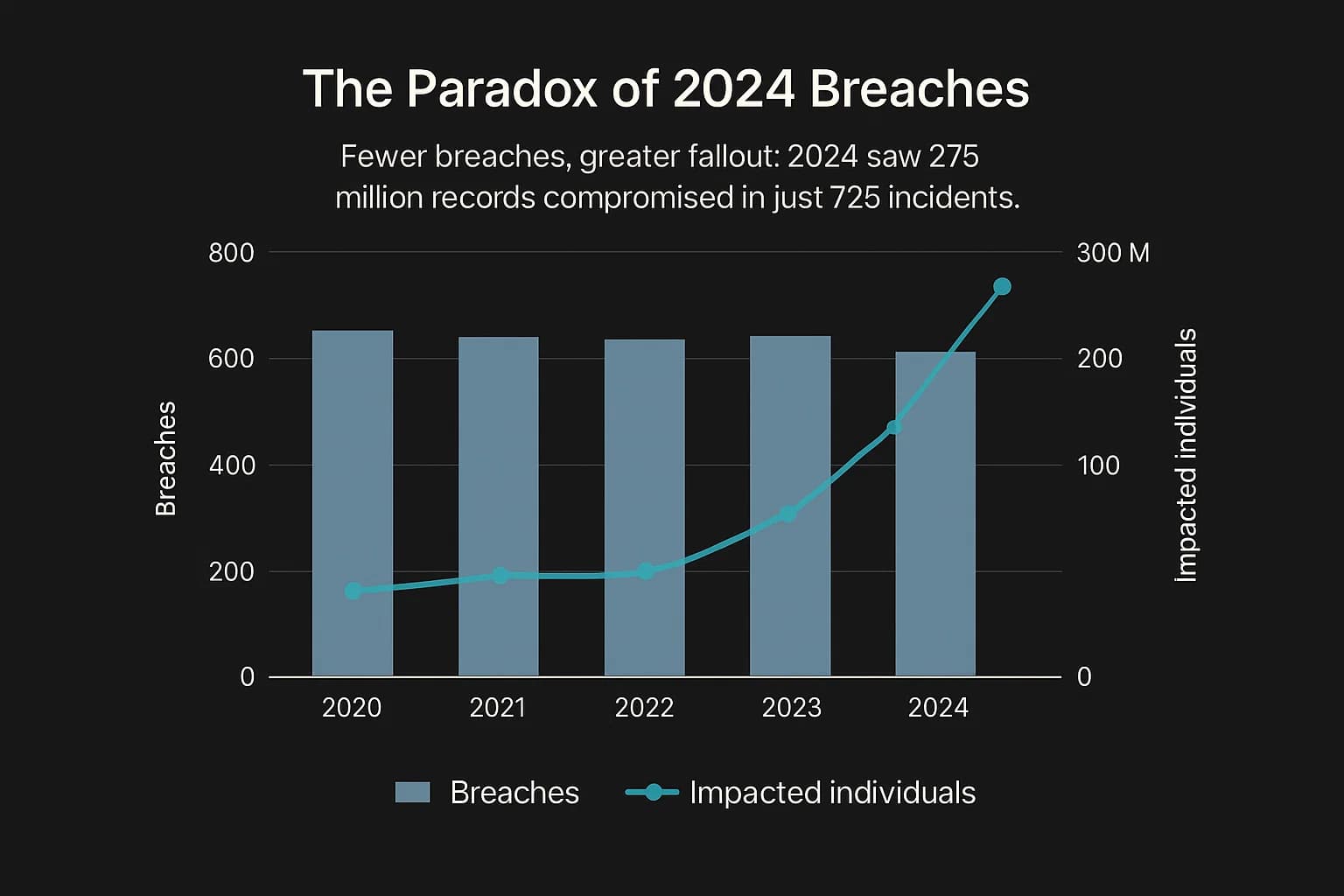
Perhaps the most telling trend is the shift from incident frequency to incident severity. The number of reported large scale breaches (affecting 500+ records) has remained high but relatively stable, with 725 incidents reported in 2024. However, the number of individuals impacted has exploded.
In 2024, a shocking 275 million healthcare records were compromised in the U.S., impacting a number of individuals equivalent to over 80% of the entire American population in a single year. This wasn't caused by thousands of small attacks. It was driven by a handful of "mega breaches," with the Change Healthcare incident alone accounting for an estimated 190 million records.
This reveals a dangerous concentration of systemic risk. The primary threat is no longer an isolated attack on a single hospital. It's a compromise of a critical, highly interconnected third party vendor that can trigger a domino effect, paralyzing the entire healthcare infrastructure. This reality fundamentally changes the defensive calculus, moving the focus from solely protecting internal assets to rigorously validating the security of every partner in the supply chain through services like compliance focused penetration testing.
Understanding how these healthcare cyberattacks happen is the first step toward preventing them. Analysis from the phishing attack trends and statistics and other industry sources reveals a clear pattern of adversary behavior focused on exploiting the path of least resistance.
Hacking and System Intrusion Reign Supreme
Direct hacking and IT incidents are the undisputed top cause, responsible for nearly 80% of all healthcare breaches. The Verizon DBIR identifies "System Intrusion" which includes malware, ransomware, and lateral movement as the dominant attack pattern, present in 53% of breaches. Attackers are actively breaking in, not just waiting for an accidental disclosure.
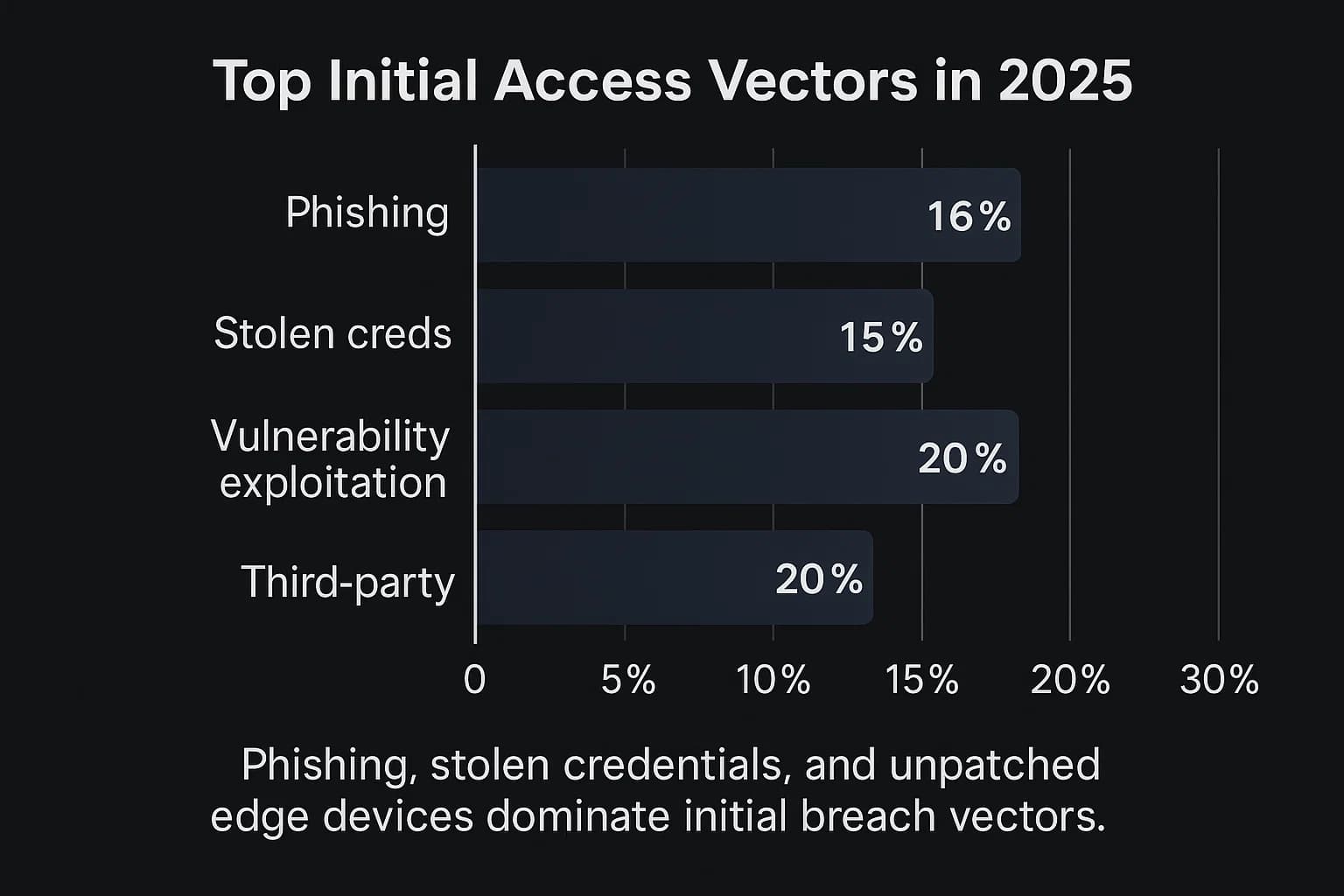
The Shifting Methods of Initial Access
How attackers get that initial foothold is evolving:
The Supply Chain: Healthcare's Soft Underbelly
The single most alarming trend is the explosion in third party breaches. According to Verizon, breaches involving a business associate or vendor doubled in just one year, jumping from 15% to 30% of all incidents.
This is a strategic pivot by adversaries. They've realized it's often easier to hack a smaller, less secure software vendor or service provider to gain trusted access to their ultimate target: a major hospital or health plan. This makes third party risk management a mission critical security function. Your organization is no longer as secure as your own defenses; you're only as secure as your most vulnerable vendor. This reality demands robust vendor security assessments, including demanding proof of regularity .
Statistics tell part of the story, but case studies reveal the real world failures behind the numbers. Three major breaches from 2024 serve as critical learning opportunities.
Case Study 1: The Change Healthcare Catastrophe – A Systemic Failure
The February 2024 ransomware attack on Change Healthcare wasn't just a data breach; it was a critical infrastructure failure that brought the U.S. healthcare payment system to its knees.
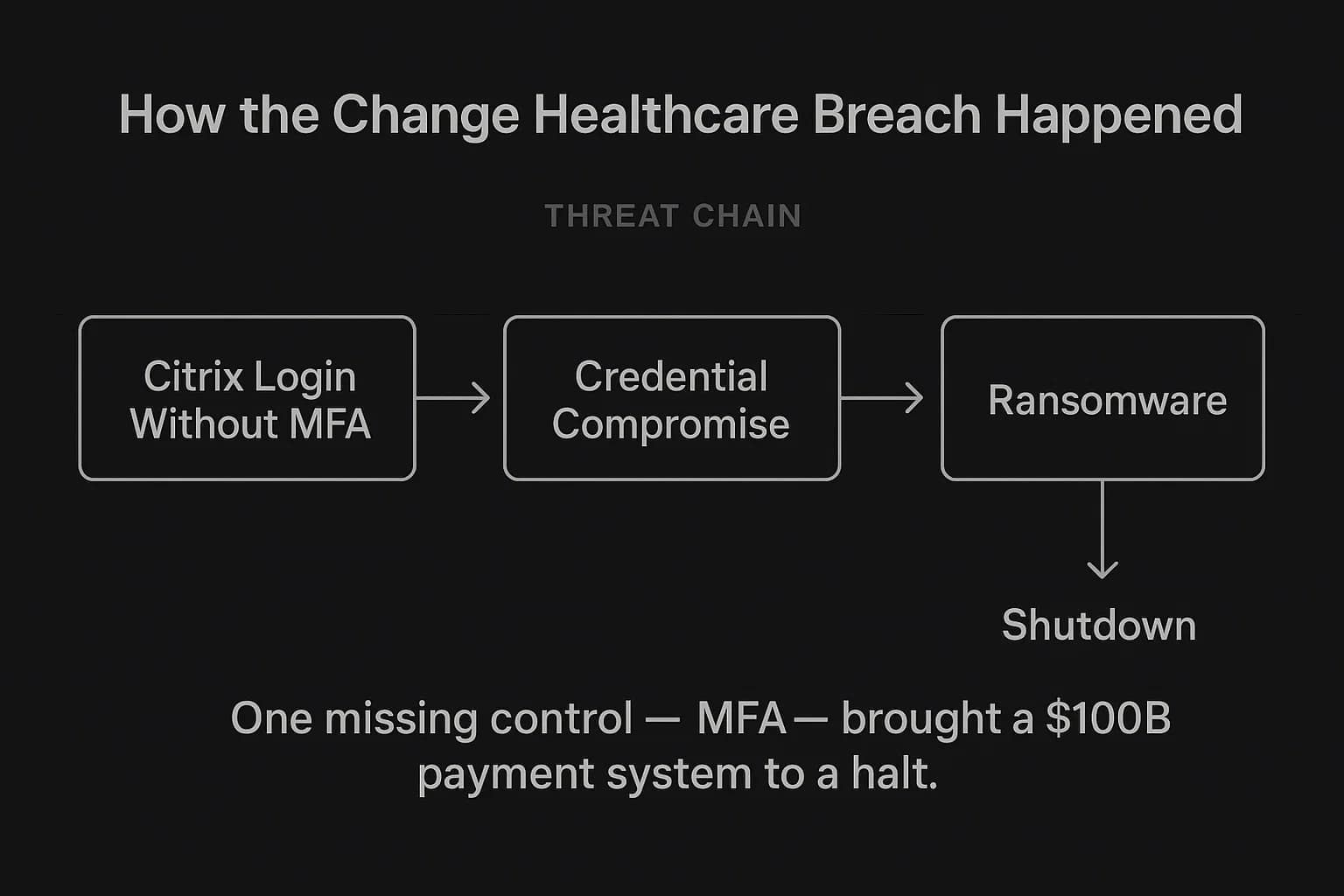
Case Study 2: The Ascension Health Ransomware Attack – A Threat to Life
The May 2024 attack on Ascension, one of the nation's largest non profit health systems, demonstrates how cyberattacks have become direct threats to patient safety.
Case Study 3: The Medibank Breach (Australia) – A Global Blueprint for Failure
This international case proves that these security failures are universal. It also provides a chilling example of the psychological damage inflicted when attackers weaponize sensitive health data.

As Josh Corman, former head of CISA's COVID 19 task force, noted, “Hospitals' systems were already fragile before the pandemic. Then the ransomware attacks became more varied, more aggressive, and with higher payment demands.” While organizations grapple with financial and operational fallout, patients bear the most personal and painful consequences of these attacks.
Medical Identity Theft and Financial Fraud
Stolen Protected Health Information (PHI) is a goldmine for criminals. Unlike a credit card, which can be quickly canceled, your medical identity name, date of birth, Social Security number, and health history is permanent. This data is used to:
On the dark web, a complete medical record can sell for up to $1,000, whereas a stolen credit card number might fetch only a few dollars, because medical fraud is harder to detect and the data has a much longer shelf life.
Corruption of Medical Records and Disruption of Care
The most terrifying risk is the alteration of a patient's medical file. An attacker could change a patient's blood type, add a false allergy, or alter a diagnosis, creating the potential for a life threatening medical error years down the line.
More immediately, ransomware attacks directly disrupt and endanger patient care. Real world incidents and academic studies have linked these attacks to:
This demonstrates that a hospital data breach isn't an abstract risk. It creates a "permanent risk" for patients, a latent threat to their physical and financial well being that can persist indefinitely. The harm isn't fully realized at the moment of the breach but can continue for a lifetime, making prevention in this sector more critical than any other.
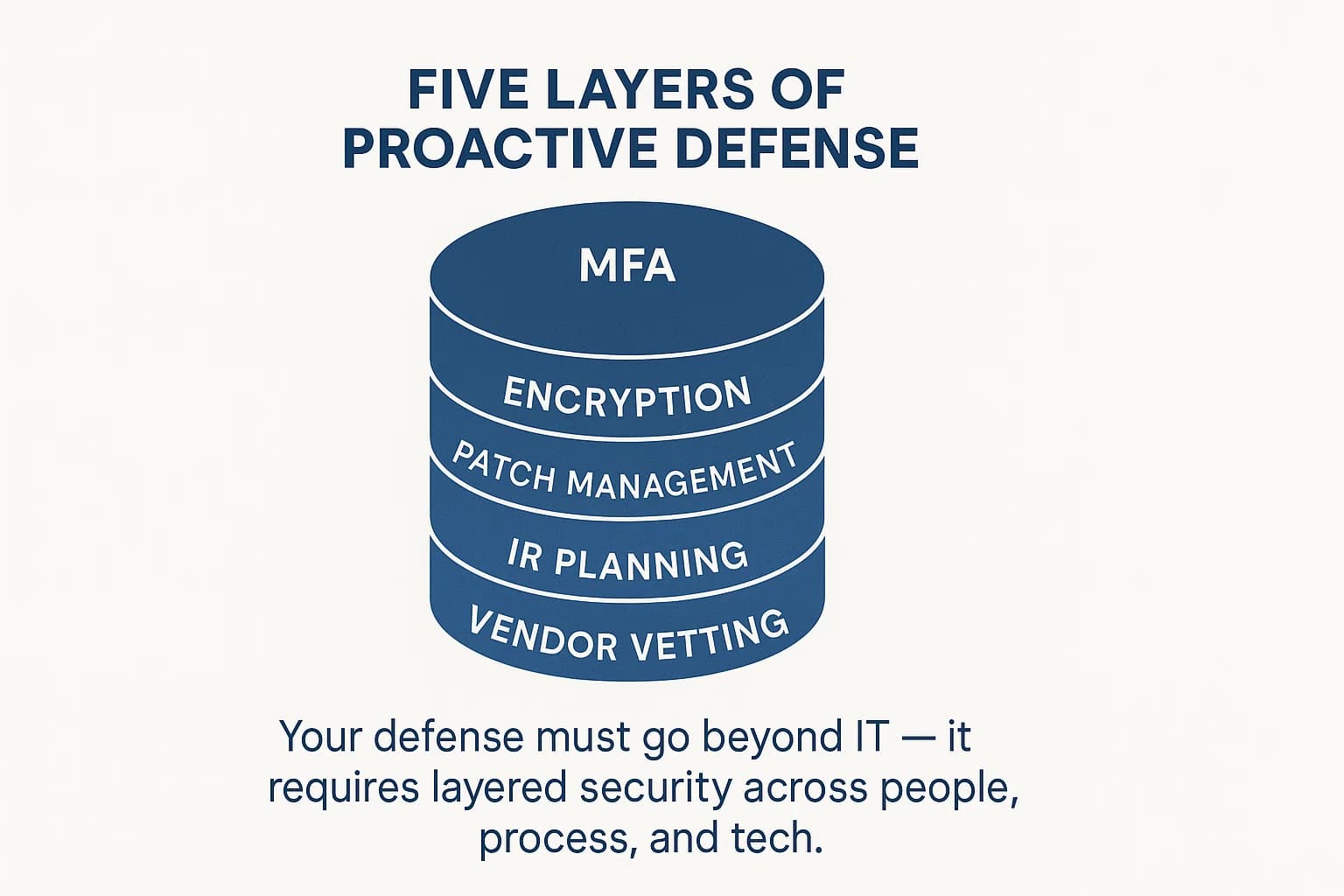
Preventing a breach in 2025 requires a defense in depth strategy built on authoritative best practices from bodies like the HIPAA penetration testing checklist 2025 and the cybersecurity vulnerability statistics 2025. Here's an actionable plan.
1. Implement Foundational "Non Negotiable" Controls
These are the absolute basics. A failure in any of these areas is a direct invitation for an attack. In my own penetration testing engagements, I frequently find that a lack of basic controls like MFA is the most common and dangerous oversight.
2. Master Vulnerability and Patch Management
With vulnerability exploitation on the rise, a proactive approach is essential.
3. Build and Test a Resilient Incident Response (IR) Plan
Assume a breach will happen and be prepared to respond effectively.
4. Fortify Your Human Firewall
The human element was a factor in around 60% of breaches.
5. Secure Your Supply Chain
Your security is only as strong as your weakest vendor.
A strong technical defense must be paired with a deep understanding of the regulatory landscape. In 2025, regulators are losing patience with non compliance.
The HIPAA Breach Notification Rule Explained
Under HIPAA, a data breach is any impermissible use or disclosure of PHI unless the organization can prove a "low probability of compromise" through a formal 4 factor risk assessment. If a breach occurs, the rules are clear:
The Global Perspective: GDPR
For organizations that handle the data of EU residents, the General Data Protection Regulation (GDPR) imposes even stricter rules. GDPR mandates that qualifying data breaches must be reported to the relevant Data Protection Authority (DPA) within 72 hours of discovery. Fines for non compliance are severe and can reach up to €20 million or 4% of a company's global annual turnover, whichever is higher. For example, a Portuguese hospital was fined €400,000 for inadequate access controls that allowed non medical staff to view patient data, demonstrating that regulators will penalize a lack of diligence even without a malicious attack.
The Game Changer: Proposed 2025 HIPAA Security Rule Updates
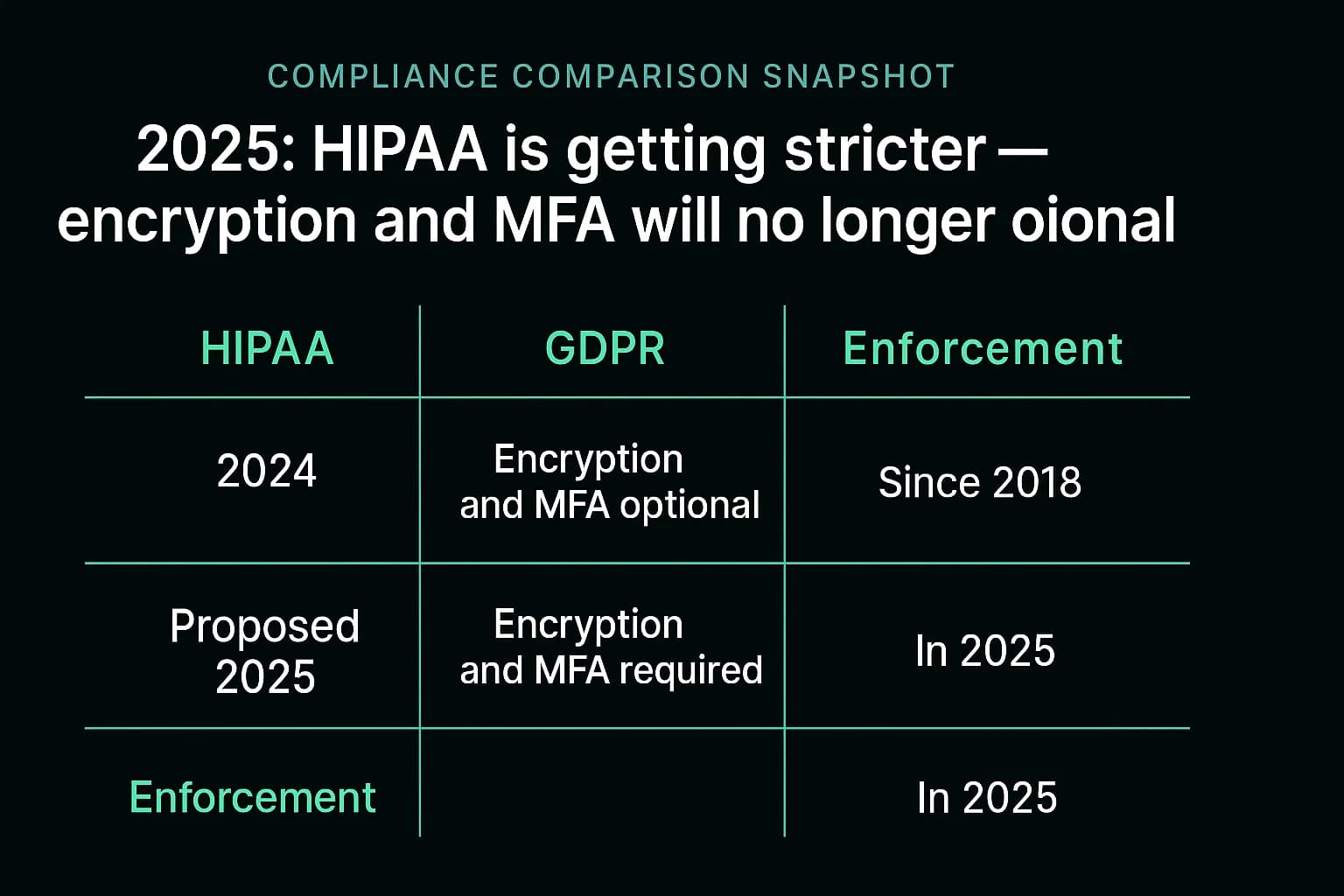
In early 2025, HHS issued a Notice of Proposed Rulemaking (NPRM) to overhaul the HIPAA Security Rule for the first time in over a decade. These proposed changes signal a major shift from a flexible, risk based framework to a more prescriptive one.
The most significant change is the proposed removal of the distinction between "required" and "addressable" implementation specifications. This means key security controls that were once considered flexible like encryption and multi factor authentication would become mandatory for all covered entities and business associates, with very limited exceptions. This is a direct regulatory response to the root causes of recent mega breaches and effectively closes the loophole that allows organizations to "accept the risk" of not implementing fundamental controls.
OCR Enforcement: A Laser Focus on Risk Analysis
The HHS Office for Civil Rights (OCR) has made its enforcement priorities clear. In 2024, it launched a "Risk Analysis Initiative," and the results are evident in its 2024 2025 enforcement actions.
A review of recent multi million dollar settlements like those with Solara Medical Supplies HIPAA settlement and Warby Parker HIPAA enforcement action reveals a consistent theme: OCR is penalizing organizations for the failure to conduct a thorough, enterprise wide security risk analysis. This failure is cited as a core violation regardless of whether the breach itself was caused by ransomware, phishing, or an insider threat.
This shows that a data breach is often just the trigger for an investigation. The penalty is determined by the pre existing state of your compliance program. Having a documented, up to date risk analysis, often validated through a comprehensive , is the single most important defensive document an organization can possess when facing regulators.
What is the most common cause of healthcare data breaches?
Hacking and IT incidents are the most common cause, accounting for the vast majority of breaches and compromised records. Within this category, attacks leveraging stolen credentials, phishing emails, and the exploitation of unpatched software vulnerabilities are the primary initial access vectors used by criminals.
What are the penalties for a HIPAA data breach?
Penalties are tiered based on the level of negligence and can range from $141 per violation up to an annual cap of over $2.1 million for the same violation type. In addition to these Civil Monetary Penalties (CMPs), the HHS Office for Civil Rights (OCR) almost always requires a formal Corrective Action Plan, which involves multiple years of strict government monitoring and mandated security improvements.
How long do hospitals have to report a data breach?
Under the HIPAA Breach Notification Rule, covered entities must notify affected individuals and HHS without unreasonable delay, and in no case later than 60 calendar days from the discovery of the breach. If the breach affects fewer than 500 individuals, it can be reported to HHS annually.
Can a patient sue a hospital for a data breach?
Yes. In addition to regulatory fines from HHS, healthcare organizations frequently face class action lawsuits filed by patients whose patient data breach occurred. These lawsuits typically allege negligence in protecting sensitive information and seek financial damages for the victims, representing a separate and significant financial risk for the breached entity.
What should I do if my health data is breached?
If you receive a breach notification, take immediate action. First, sign up for the free credit and identity theft monitoring services offered by the breached organization. Second, carefully review all Explanation of Benefits (EOB) statements from your insurer for any services you don't recognize, as this is a key sign of medical identity theft. Finally, be extremely vigilant for phishing emails or phone calls that use your stolen data to sound more convincing.
The threat landscape in 2025 leaves no room for complacency. The rise of systemic risk through the supply chain, the weaponization of ransomware against patient care, and the intensifying scrutiny from regulators create a perfect storm of risk. The key takeaway from the year's devastating breaches is that they were largely preventable. They stemmed not from hyper advanced attacks, but from failures to implement foundational, well understood security controls. Building a resilient defense for the future means returning to these fundamentals with relentless discipline: master MFA, patch your systems, conduct thorough risk analyses, train your people, and hold your vendors accountable.
Ready to Strengthen Your Defenses?

The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us