May 18, 2025
Updated: May 18, 2025
A data-driven analysis of cybercrime losses, attack trends, and industry risks in 2025.
Mohammed Khalil

These findings combine law enforcement data, industry studies, and expert analysis to show cybercrime as a growing, systemic risk. The data underscore a tense reality: cybercrime is outpacing traditional defenses, demanding urgent, coordinated responses.
Cybercrime statistics quantify illegal activities executed through digital systems from data theft and online fraud to ransomware extortion and their financial, operational, and societal impacts. These statistics help organizations and governments gauge the scale of the threat and measure trends over time. In an era of ubiquitous connectivity, cybercrime has become a macro level economic force, inflicting costs that grow faster than global GDP. Reported losses now run in the trillions, with estimates ranging from ~$1–1.5 trillion annually up to ~$10.5 trillion, making cybercrime’s footprint comparable to the world’s largest economies.
Contributing factors include the professionalization of cybercrime cyber gangs operate like businesses, the mass availability of crime tools e.g. ransomware kits and phishing as a service, and new vectors like AI enabled attacks. Notably, identity based attacks have surged: criminals increasingly bypass firewalls by using stolen credentials and social engineering. The result is a broad, rapidly expanding attack surface.
Among the key takeaways from 2025 data are 1 explosive cost growth even conservative models put losses in the $1–1.5 trillion range, while other analyses warn the true economic drag is many times higher 2 attack volume escalation e.g. US complaint centers saw ~2,400 incidents per day in 2024 and 3 shifting tactics AI driven phishing campaigns, supply chain intrusions, and credential theft now outpace traditional malware. Together, the data paint a picture of a threat that is not only growing but also evolving in sophistication and scope.
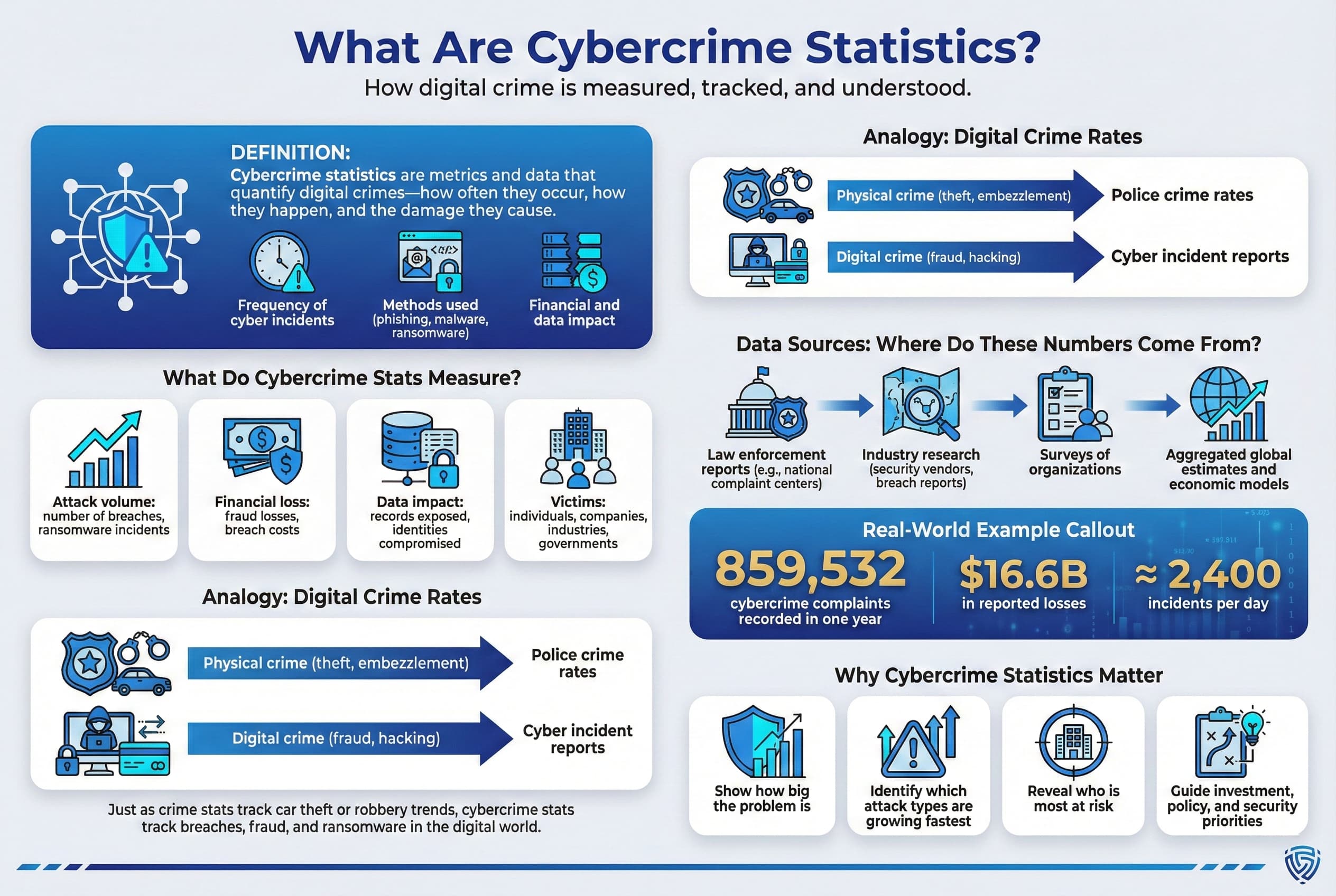
Cybercrime statistics are metrics and data that describe the incidence, methods, and impacts of crimes involving computers and networks. This includes measures of how often crimes occur, how much money or data they cost, and which victims or industries are affected. For example, counting the number of ransomware breaches or summing the total money lost to online fraud are both cybercrime statistics.
Think of cybercrime stats like the crime rates or loss estimates for traditional theft or embezzlement, but in the digital realm. Just as police might report that car thefts rose X% last year, law enforcement and industry collect data on how many data breaches happened, what attack vectors were used e.g. phishing, malware, and the financial toll. These stats often come from sources like complaint centers FBI IC3 in the US, security industry reports IBM DBIR, Verizon DBIR, and aggregated surveys of organizations.
A practical example: in 2024 the FBI’s Internet Crime Complaint Center IC3 recorded 859,532 cybercrime complaints with $16.6 billion in reported losses. This single number conveys both the high frequency of nearly 2,400 incidents per day and the financial impact of tens of billions lost to cybercrime in one country. At the global level, analysts use models to project totals across all unreported and unquantifiable losses, resulting in figures like $1–10 trillion annual costs.
In short, cybercrime statistics help us understand how big is this problem? and where is it worst? by quantifying things like attack counts, dollar losses, types of crimes, ransomware, fraud, etc., and affected sectors. These insights are essential for prioritizing defenses and policy.
| Indicator | 2024 est. | 2025 est. | Trend | Notes |
|---|---|---|---|---|
| US IC3 complaints incidents | 795,000 approx. | 859,532 IC3 data | ↑ Rising | Daily avg ~~2,100 → ~~2,400 incidents |
| US reported losses FBI IC3 | ~$10.3 B 2023 | $16.6 B | ↑ Rising | About $45 M/day lost in 2024 |
| Global cost of cybercrime | ~$1.2–1.5 T est. | ~$1.2–1.5 T est. | ↑ Steady | Conservative direct losses view |
| Global holistic cost estimate | — | ~$10.5 T CV forecast | ↑ Rising | Includes indirect impacts economic drag |
| Avg. cost per breach global | $4.88 M | $4.44 M | ↓ Slight | Down 9% as detection improved |
| % orgs hit by phishing weekly | – | 57% daily/weekly attempts | – High | Phishing remains ubiquitous |
The data above illustrate the broad scale of cybercrime. US specific figures in the top two rows show a rising trend in complaints and monetary losses. Globally, while actual incident counts are hard to measure, aggregated loss estimates span from the low trillion range direct costs up into the ten trillion range including broader economic harm. Notably, the average cost of a data breach globally eased from $4.88M in 2024 to $4.44M in 2025 a sign of faster response, even as the US average jumped to $10.22M due to its high value environment. Overall, the year over year direction is upward for incident volume and aggregate losses.
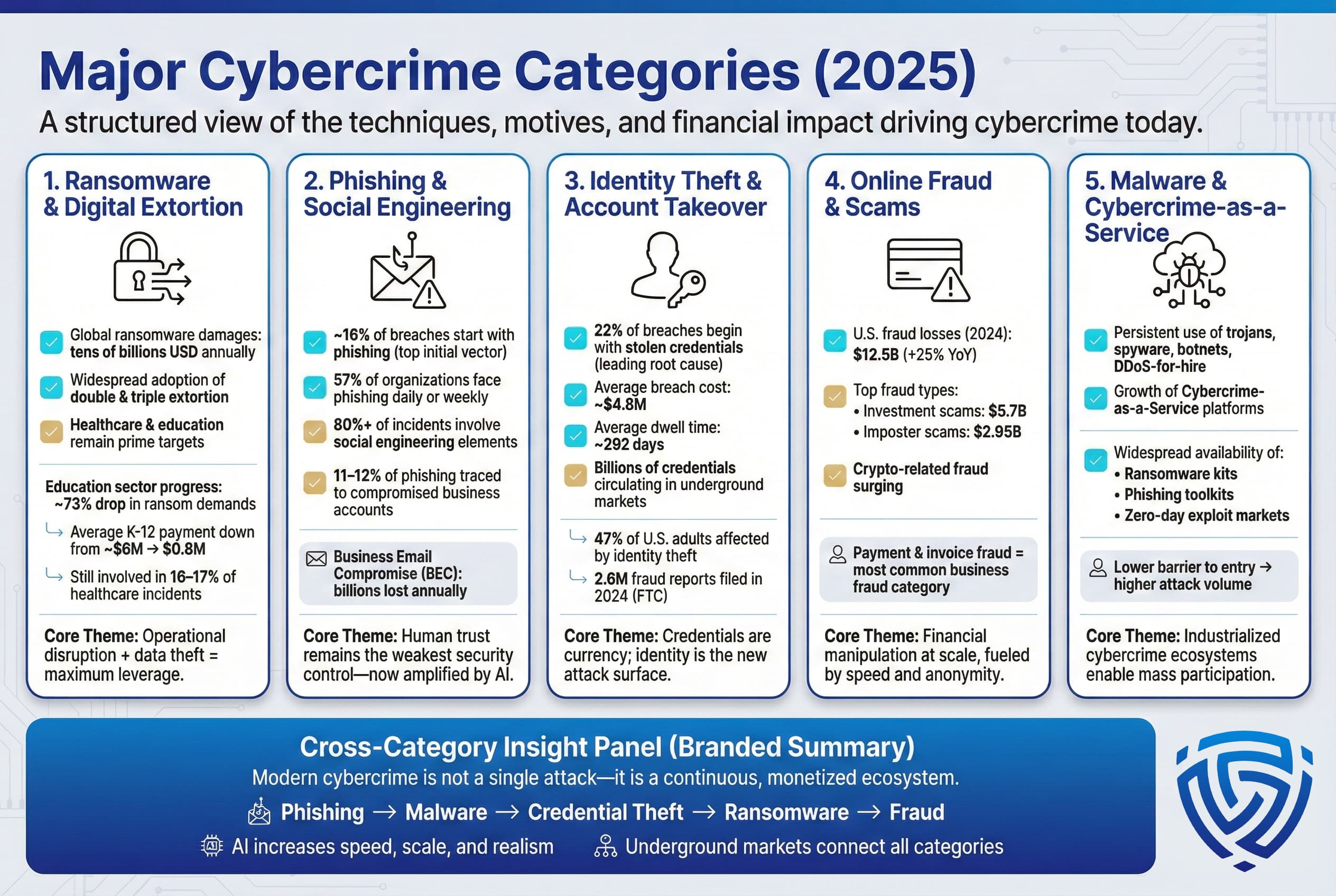
Cybercrime spans many techniques and motivations. The most impactful categories in 2025 include:
Each of these categories overlaps e.g. a phishing email may drop malware that encrypts files ransomware, which then leads to data theft extortion. The overall trend in 2025 is clear: attacks are more personalized, automated, and frequent. AI driven tools let criminals scale phishing and deepfake lures, while the underground market makes advanced techniques widely available. As a result, cybercrime is not a series of isolated attacks but a continuous, money making ecosystem.
Cybercrime inflicts both direct financial losses and indirect costs on victims. The table below summarizes key cost categories and ranges for 2025 global estimates:
| Impact Area | Estimated Range 2025 | Trend | Notes |
|---|---|---|---|
| Business Downtime & Productivity Loss | $500 B $1.0 T | ↑ Rising | Lost output, recovery & mitigation costs; largest single category by most models. |
| Nation State Attacks & Disruptions | $200 B+ estimate | ↑ Rising | State sponsored breaches, infrastructure sabotage includes indirect GDP impacts. |
| Direct Financial Theft & Fraud | $150 B $250 B | ↑ Rising | Fraudulent transfers, phishing loss, stolen funds. |
| Brand/Reputation Damage | $100 B+ | ↑ Rising | Loss of future revenue, stock value, customer trust after breaches or leaks. |
| Cyber Insurance Payouts & Premiums | $50 B $100 B | ↑ Rising | Payouts on policies and higher premiums; still a fraction of total losses. |
| Regulatory Penalties & Legal Fees | $10–20 B+ | ↑ Rising | GDPR fines, breach investigations, litigation e.g. SEC rules, data protection suits. |
These ranges sourced from industry analyses capture the scope of impact. For example, lost productivity due to breaches of systems offline, employee downtime is estimated in the half trillion to trillion dollar range globally. Direct theft, stolen funds and fraud payouts adds another few hundred billion. Even intangible impacts like reputation and legal fallout easily cross $100 billion. In total, all these costs sum to on the order of $1.2–1.5 trillion annually by conservative counts and would be much higher under broader definitions.
An illustrative breakdown Table 1 of one report shows these categories, reinforcing that cybercrime is far more than just stolen data or ransom payments; it's a pervasive tax on global business. Moreover, there is velocity to the losses: at a $10.5T/year rate, the world loses roughly $26 B per day, or $1.1 B per hour, to cybercrime by contrast, even these figures are often underestimates. For perspective, projected ransomware damages alone break down to over $100,000 per minute.
Recovery Burden: Victims also incur significant remediation costs. For each breach, organizations spend on incident response, digital forensics, legal compliance, credit monitoring, and rebuilding systems. The IBM Cost of a Breach Report 2025 notes that mature security with AI can shave ~$1.9 M off breach costs, underscoring how detection speed and preparedness materially affect the bottom line. Additionally, lost employee productivity, emergency IT fixes, and overtime add up; these often approach or exceed direct losses.
In summary, cybercrime imposes a massive, continuous drag on economies. Losses compound because the more profitable cybercrime becomes, the more investment goes into it fueling the cycle of attack and defense. The data clearly show upward trends: all categories are escalating year over year.
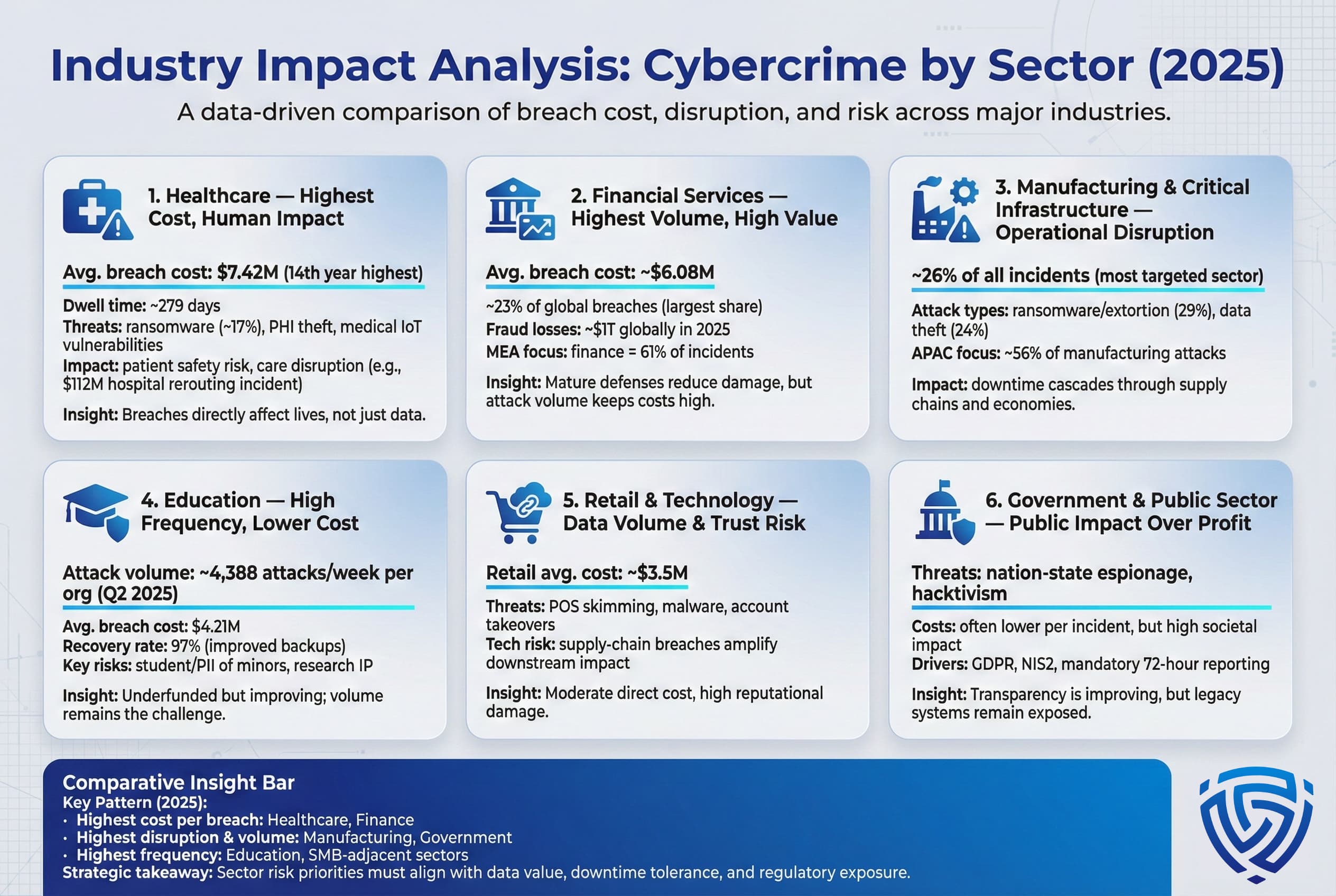
The impact of cybercrime varies widely by industry, reflecting data value and tolerance for downtime. Key findings for major sectors in 2025 include:
Broadly, healthcare and finance incur the highest losses per incident, manufacturing and government see the most disruption and attack volume, and education/SMBs grapple with sheer quantity of hits. These patterns guide risk priorities: sectors with high data value health, finance invest heavily in cyber defense, while traditionally underfunded sectors education, small business remain at risk.
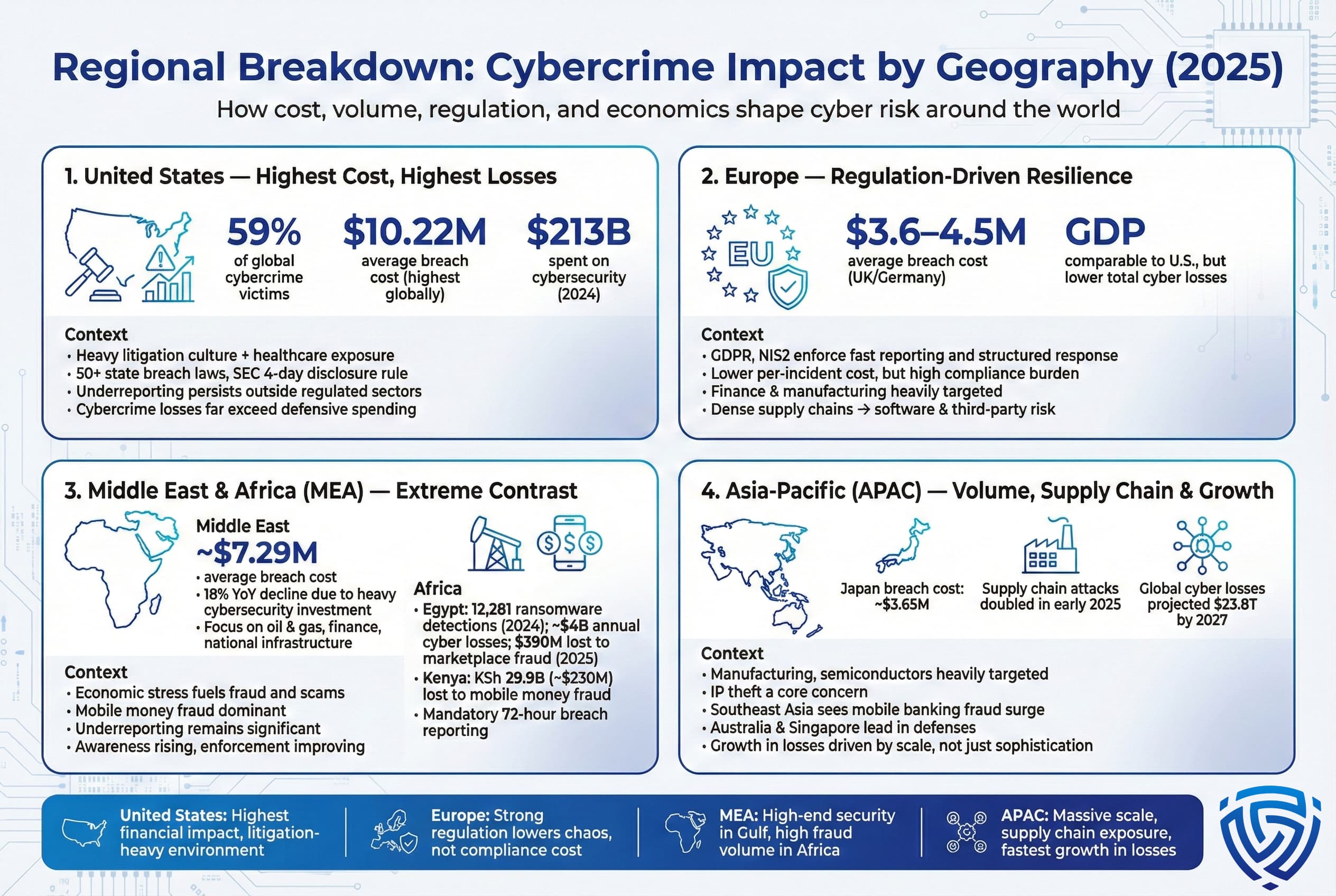
The US continues to suffer the greatest cybercrime costs. The IC3 data above show Americans filed the majority of global cybercrime complaints ~59% of all victims. The US average breach cost has reached $10.22 million in 2025 by far the highest of any country driven by expensive litigation, healthcare losses, and regulatory fines. There is no comprehensive national breach reporting requirement yet, so incidents are undercounted; however, regulated sectors like finance and healthcare report regularly. Recent SEC rules and state laws 50+ regulations are forcing rapid disclosure. In response to rising threats, U.S. businesses spent an estimated $213 billion on cybersecurity in 2024. Still, predicted losses $639.2 billion in 2025 far outpace spending, highlighting a defense shortfall.
European Union and UK organizations face a somewhat different environment. Strict privacy regulations GDPR, NIS2 create heavy compliance requirements but also standardized incident response that can mitigate cascade effects. Average breach costs are lower around $3.6–4.5M in UK/Germany compared to the US. EU reporting is improving: GDPR fines and mandatory notifications force visibility. Ransomware and fraud are top issues. Notably, while EU GDP is similar to the US, annual cybercrime costs in Europe remain below US levels, partly because victims often get less media attention. However, sectors like finance and manufacturing are hot spots Europe’s dense supply chains make it a prime target for software attacks.
The MEA region is diverse: oil rich Gulf states invest heavily in cybersecurity leading to improvements in breach detection and some decline in breach costs, e.g. a recent report noted Middle East breach costs fell 18% year over year to ~$7.29M. However, many African nations are seeing a cybercrime explosion driven by economic and governance factors. For example, Egypt's population ~104M has a severe currency crisis: the pound lost 70% of its value, creating fertile ground for fraud. According to regional reports, Egypt recorded 12,281 ransomware detections in 2024 second highest in Africa and about $4 billion in cyber losses annually. Online shopping and black market currency scams cost Egyptians hundreds of millions e.g. ~$390M lost to marketplace fraud in 2025. A notorious case Hoggpool crypto Ponzi may have cheated victims of tens to hundreds of millions Egyptian officials seized ~$615K, while lawyers estimate total losses up to ~$194M.
Kenya and other fintech adopters face a surge in mobile money fraud: Kenya reported KSh 29.9 billion ~$230M lost in 2025, with SIM swap and app based scams on the rise. Governments here are beginning to enforce reporting: Kenya now mandates breach reports within 72 hours. Overall, MEA has high cybercrime incident rates but improving awareness. The gap remains wide: urban/wealthy populations are targeted by sophisticated scams phishing, vishing, while many crimes in informal economies go unreported.
APAC nations see large scale cybercrime both from global criminal networks and regional actors. The US and China still hold most digital wealth, but APAC’s manufacturing and mobile user base drives crime volume. Supply chain attacks on semiconductor and industrial firms doubled in early 2025. Countries like Japan report moderate breach costs ~$3.65M but focus on intellectual property theft. Southeast Asia, with diverse economies, faces surges in mobile banking fraud akin to Kenya’s mobile money scams. Meanwhile, Australia and Singapore lead regionally in cyber defenses. Cybercrime costs in APAC are projected to climb steeply. Global reports predict overall cyber losses may reach ~$23.8T by 2027, much of the growth in APAC and emerging markets.
In summary, geography matters: wealthier nations face higher per-incident costs, emerging markets face high volume and different crime forms, fraud, currency scams, and global east manufacturing hubs face targeted infrastructure attacks. Regulatory regimes also shape statistics: tighter laws in Europe/US improve data but also publicize costs, whereas lax enforcement in some regions leads to underreporting.
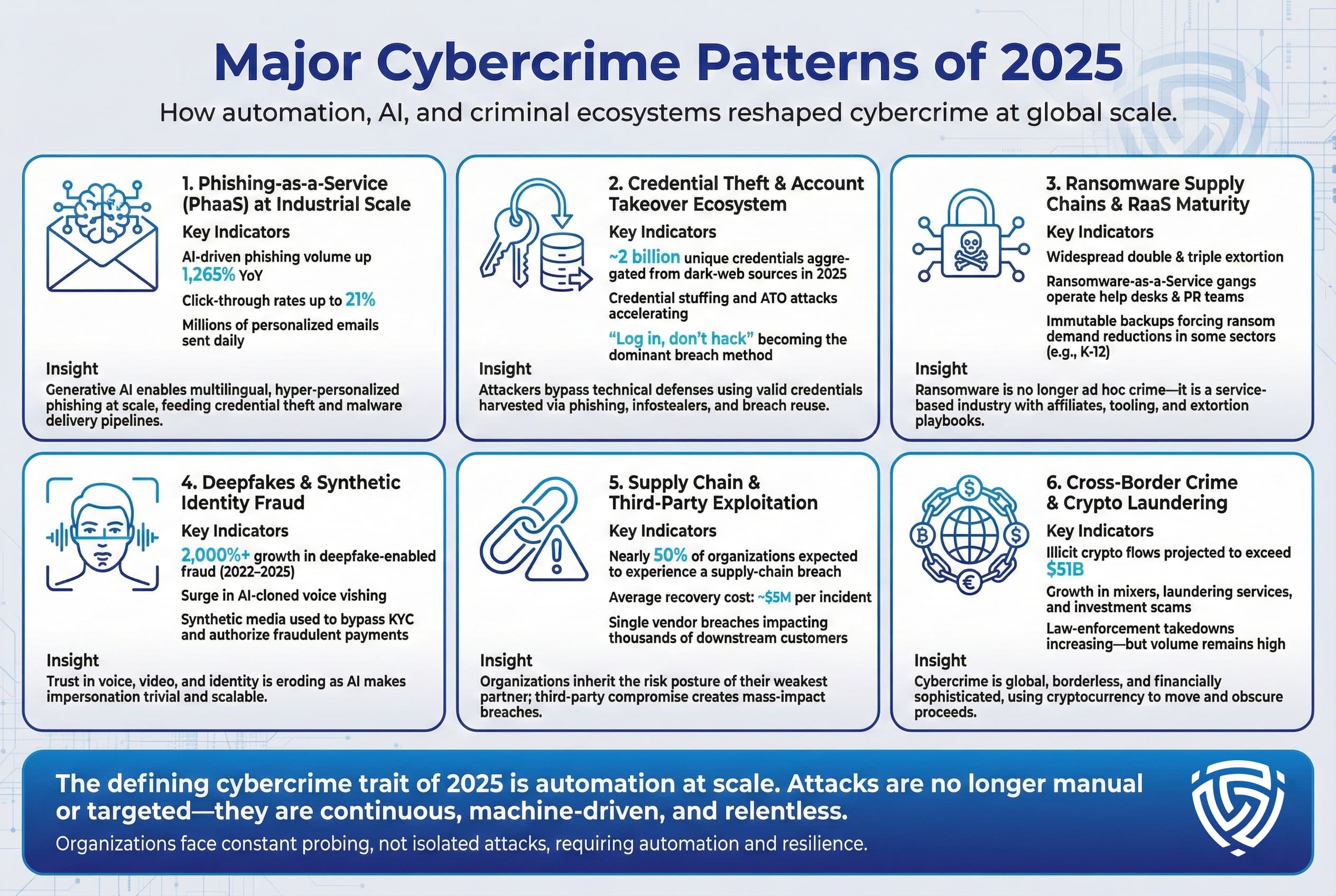
Cybercriminals often act in waves and campaigns that span multiple victims. Key patterns seen in 2025 include:
Across all patterns, one common thread is automation and scale. Attacks that once required manual effort phishing writing, invoice sending, credential checking are now massively parallelized. The result is that organizations are hit not by the occasional lone hacker, but by automated machines constantly probing for weaknesses. The statistics of 2025 reflect this: attacks per organization per week often number in the tens to hundreds, a crushing volume that any single security team would struggle to handle without automation.
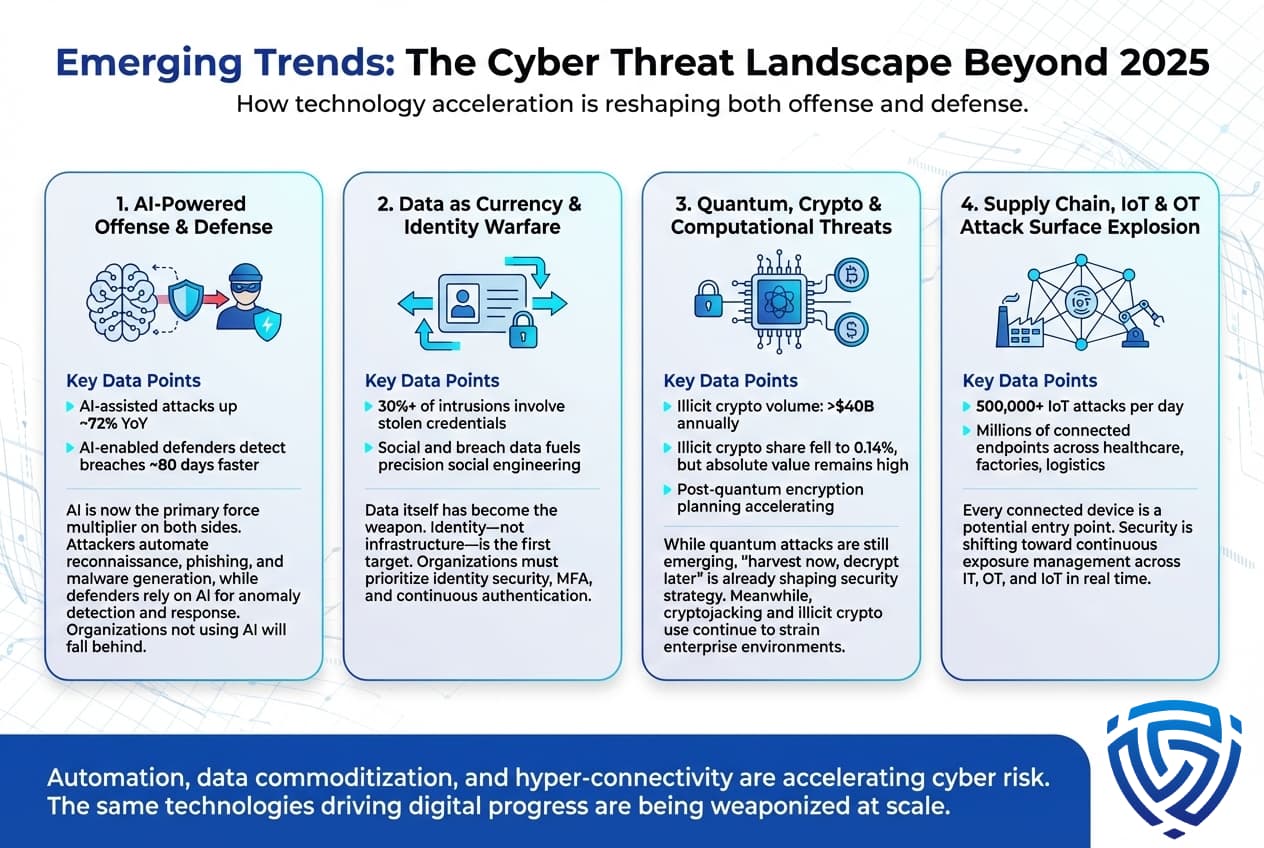
Looking beyond 2025, several emerging technologies and trends are reshaping the threat landscape:
In short, the trend lines point to greater automation of crime and faster proliferation of data. Technological progress AI, IoT, 5G, cloud that empowers society is simultaneously being weaponized by attackers. The statistics of 2025 show the early stage of these shifts: a significant fraction of breaches involve AI or stem from identity vulnerabilities. Going forward, we can expect these factors to grow, making cybercrime an even more integral part of the digital age economy.

The 2025 figures highlight several macro level insights and priorities:
Ultimately, no single defense solves it all. A layered strategy is required. The data illuminate the areas of greatest risk: where identity meets data, where high value assets lie, and where deterrence is weak. For example, realizing that 78% of breaches involve social vectors suggests that employee training awareness campaigns must be a core pillar. At the same time, understanding the high costs in healthcare highlights the need for sector specific controls, segmentation of medical devices, and encryption of PHI.
One practical implication is to invest in regular security validation. For instance, firms should implement penetration tests focused on login and access flows to catch weaknesses before criminals do. Also, network segmentation and continuous scanning of code and configurations can prevent a small intrusion from causing a multi million dollar outage. The statistics show that continuous, proactive measures pay off: organizations with automated detection and response were able to contain breaches 80 days sooner, saving an average of $1.9M each.
Finally, these trends underline that cybersecurity is everyone’s responsibility now. IT alone cannot shoulder this risk. Boards and executives must internalize that cybercrime is not just an IT issue it threatens national infrastructure, economic stability, and public safety. The enormous losses and ever growing attack surface demand integrated strategies across technology, governance, and policy realms.
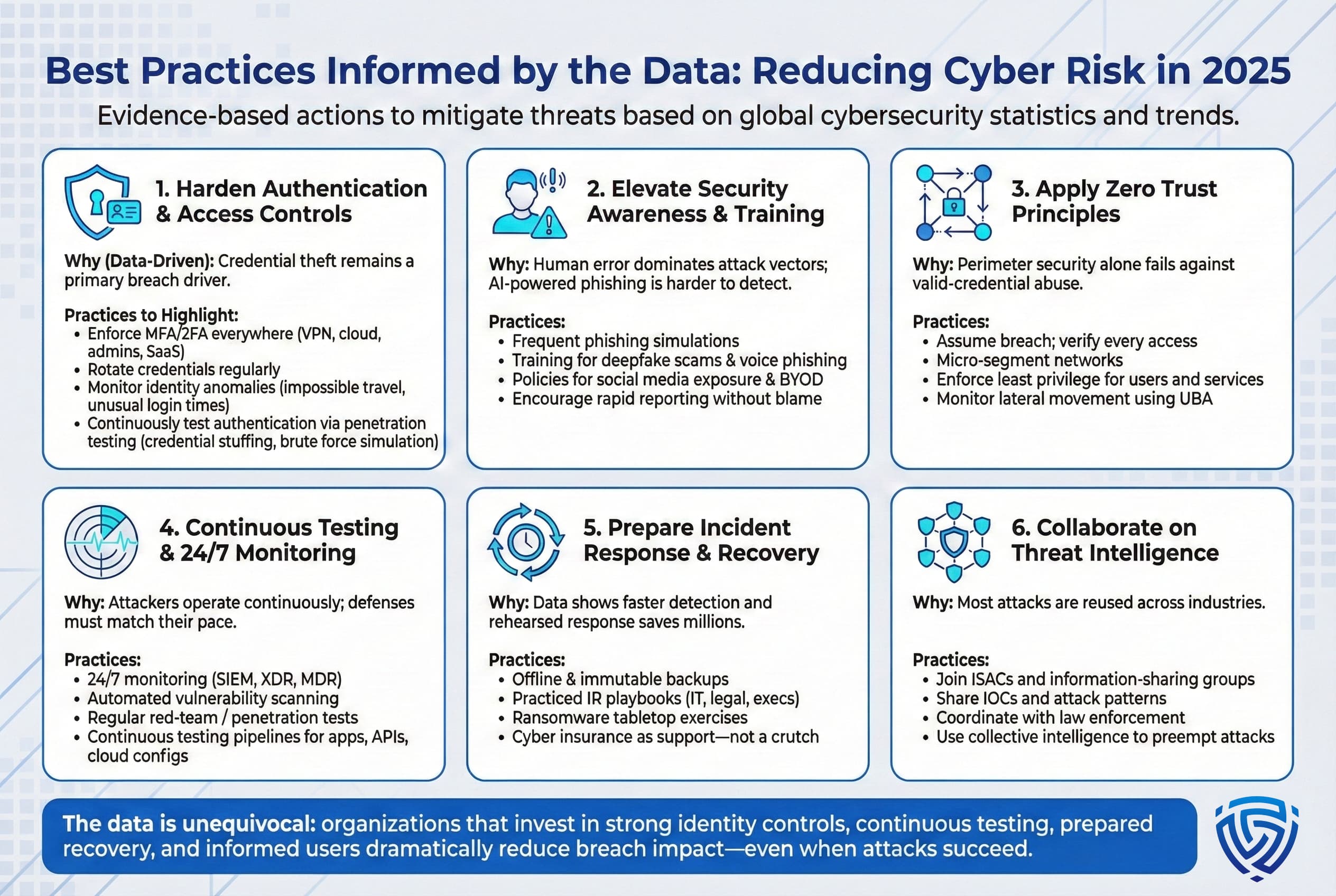
Based on the 2025 statistics, effective risk reduction strategies include:
These practices grounded in the 2025 data help close the gaps exposed by the statistics. They are foundational and do not rely on any single vendor solution. For instance, strengthening authentication via multi factor and password-less logins directly counters the credential theft trend, while continuous testing addresses the acceleration of automated attacks.
When the numbers are this stark that small businesses face existential risk 60% of hacked SMBs shut down and top sectors lose millions per incident organizational leaders must treat cybersecurity as a top priority. Security is no longer just an IT checkbox; it’s a fundamental business imperative. Robust user education, relentless testing e.g. via continuous penetration testing, and collaboration with peers and authorities are all proven ways to bend the trend lines of the next year.
Cybercrime is exceedingly common and growing. Millions of incidents are reported worldwide each year. In 2024, the FBI logged ~859,000 complaints just in the United States, and billions of dollars were lost. Global estimates suggest that hundreds of millions of people and businesses are targeted annually. Phishing, malware, and fraud attempts reach most internet users frequently for example, 57% of organizations faced phishing attacks weekly or daily in 2025. Many incidents go unreported due to embarrassment or lack of detection, so the true number of crimes is likely much higher.
Ransomware and large scale fraud are the biggest drain on the economy. Combined, they account for tens of billions of dollars in global losses each year. Ransomware alone is projected to cause about $57 billion in damages by 2025. Traditional financial fraud investment scams, payment fraud, identity theft also inflicts massive losses US consumers lost $12.5 billion to scams in 2024. Business Email Compromise high dollar invoice fraud has cost businesses over $2 billion annually. Even minor crimes add up: every minute, an estimated $300,000 is stolen worldwide in cyber enabled theft. If cybercrime were a GDP it would be among the top global economies. In contrast, identity theft of single credit cards or account logins is smaller per incident but extremely common, affecting millions.
Several factors cause underreporting. Victims may not realize they’ve been attacked or may assume it’s a minor issue. Businesses often fear reputational damage or legal liability especially under strict privacy laws, so they may keep incidents secret. In some countries, reporting requirements are weak or enforcement is lax. Importantly, illegality of the underlying transaction can deter reporting. For example, Egypt’s HoggPool crypto scam victims hesitated to report losses because cryptocurrency trading is banned in Egypt. Smaller businesses often lack expertise or fear the cost of reporting. Surveys suggest only a fraction of breaches become public, so official statistics represent the tip of the iceberg.
It varies by sector, but global averages are in the low millions. The 2025 IBM report found a global average of $4.44 million per breach. US breaches are far higher around $10.22M on average due to factors like healthcare and class action suits. Industry wise, healthcare had the highest average in 2025 $7.42M, finance was ~$6.08M, while sectors like retail and education were in the $3–4M range. Small businesses face smaller absolute losses ~$250K on average but even that can be crippling. These figures include lost business and response costs but not the full indirect economic drag which is much larger.
Phishing social engineering and stolen credentials lead the list. In 2025, 16–22% of breaches began with these methods. Other common entry points include exploiting unpatched vulnerabilities in internet facing applications ~16% of breaches, or gaining access through valid accounts credential stuffing or reused passwords, ~22% of breaches. Malware downloads and drive by website attacks are also prevalent. Traditional methods like unsecured RDP remote desktops and misconfigured cloud storage continue to cause incidents. Essentially, attackers often bypass perimeter defenses by tricking people or using legitimate credentials.
Finance and healthcare are repeatedly top targets. Healthcare leads in cost of breaches, while finance sees the highest frequency of attacks due to its monetary assets. Manufacturing and critical infrastructure are also heavily targeted for ransomware reflecting the high cost of downtime. Education and small businesses get attacked in huge volumes as soft targets, though often for lower sums. Retail, tech, and government face a mix of data theft and disruption. In general, any industry with valuable data or critical operations is a target, but wealth and regulation level affect attack patterns and reported costs.
Rapidly on the order of double digit percent increases per year. Historic data show global cybercrime costs growing ~15% annually from $3T in 2015 to $10.5T projected by 2025. More recent forecasts suggest an even steeper climb by late 2020s $23.8T by 2027. In the US, costs are projected to nearly triple from $639B in 2025 to ~$1.8T by 2028. This growth outpaces global GDP growth, meaning cybercrime is a larger and larger drag on economic activity each year.
Total elimination is unlikely; technology will always have new vulnerabilities. The focus is on risk reduction and resilience. The 2025 data indicate that higher investment in security and smarter defense like AI automation can significantly reduce impact faster detection, lower costs. Public private cooperation, robust law enforcement, and global norms like sanctioning cybercrime proceeds can raise the cost for attackers. The trends do show some positive shifts e.g. ransomware payments falling in some sectors, better reporting uncovering crime, but countermeasures must keep pace with evolving threats. In short, we can slow and mitigate cybercrime’s growth, but vigilance and continuous improvement are essential.
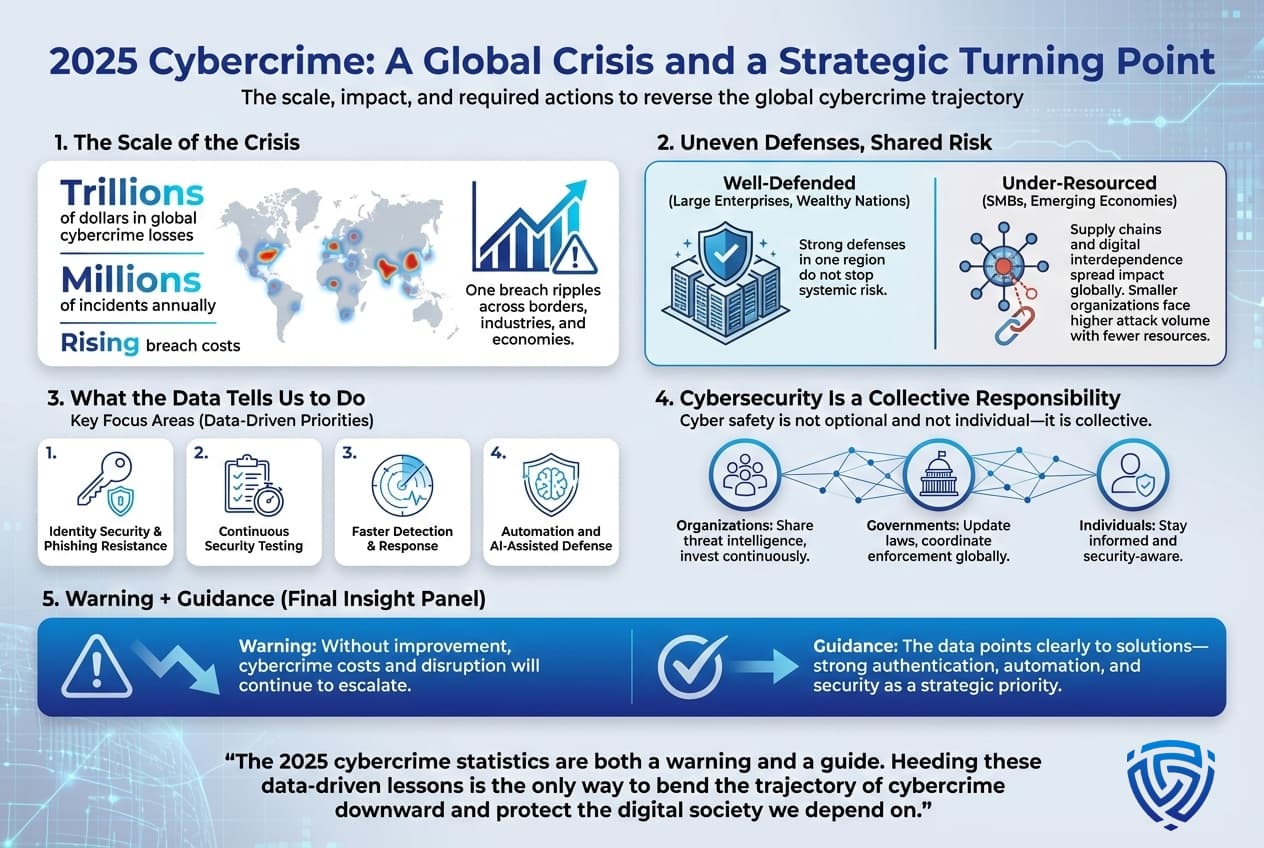
The 2025 cybercrime statistics paint a stark picture: this is not a niche problem but a global crisis with far reaching economic and social consequences. The numbers trillions of dollars in losses, millions of incidents, and soaring breach costs tell us that cybercrime has become a permanent, systemic threat. Large enterprises and wealthy nations are erecting formidable defenses, yet our interconnected world means even one breach can ripple widely. Meanwhile, smaller organizations and emerging economies face overwhelming attack volumes with fewer resources to fight back.
Closing the gap requires action on multiple fronts. Data driven insights like those above help prioritize where to focus: identity and phishing defenses, continuous testing, and rapid detection are key. A coordinated policy response from stronger international enforcement to incentives for security investments is urgently needed. Importantly, cyber safety is collective organizations must share threat intel, governments must update laws, and individuals must stay aware.
In sum, the 2025 statistics serve both as a warning and a guide. They warn that without improvement, costs and impacts will continue to soar. They guide us toward targeted solutions: shore up authentication, invest in automated defense, and treat security as an ongoing strategic priority. Only by heeding these data driven lessons can we hope to bend the trajectory of cybercrime downwards and protect the digital society we depend on.
About the Author: Mohammed Khalil is a Cybersecurity Architect at DeepStrike specializing in advanced penetration testing and offensive security operations. He holds CISSP, OSCP, and OSWE certifications and has led red team engagements for Fortune 500 clients across finance, healthcare, and technology, focusing on cloud security and adversary simulation.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us