August 15, 2025
Updated: August 15, 2025
2025’s top threats to financial institutions $6.08M average breach costs, case studies, and proven Zero Trust defenses for SEC & DORA compliance.
Mohammed Khalil

If you're a CISO in the financial sector, the question isn't if you'll face a data breach. It's when, how bad it'll be, and how fast you can clean up the mess. And here's the kicker: the cost of getting it wrong is now the highest of any industry on the planet. Financial firms are the top prize for cybercriminals, not just for the data they hoard, but because that data is a direct pipeline to cash. The average cost of a breach has now hit an eye watering $6.08 million. That’s not just a number, it's the real world pain of forensic teams, systems being down, massive fines, and trying to win back customer trust.
So, why is this a bigger deal than ever in 2025? Because the game has completely changed. We're way past simple viruses. Today’s attackers are organized, smart, and running their operations like a business. They’re using GenAI to write perfect phishing emails that could fool anyone. They're hitting your trusted software vendors to get to you, turning your supply chain into a minefield. And they're using Ransomware as a Service (RaaS) models that make it easy for anyone to launch a devastating attack.
On top of all that, the regulators are breathing down your neck. Agencies like the U.S. Securities and Exchange Commission (SEC) are now demanding you report a major breach in just four business days. There's no room for error. This article breaks down these threats, looks at what we can learn from recent real world breaches, and gives you a practical playbook for defending your organization when the risks have never been higher.
To build a solid defense, you’ve got to know what you're up against. The latest numbers show an industry that's constantly in the crosshairs.
A financial data breach is when an unauthorized person gets their hands on the sensitive data your firm holds. We're not just talking about credit card numbers. It’s the whole package of Personally Identifiable Information (PII) that makes up someone's digital life: Social Security numbers, bank accounts, tax IDs, birthdays, addresses, you name it. In fact, the latest research from the Ponemon Institute shows that almost half of all breaches involve this kind of customer PII.
This data is gold on the dark web because it’s a key to committing serious financial crime, like identity theft and account takeovers. For criminals, hitting a bank isn't just about stealing a list; it's about getting the tools to impersonate thousands of people.

The reason is simple: it’s where the money is. Attackers get an immediate payday and a ton of valuable data they can use again and again. This makes the financial sector the most attacked industry out there.
Here's the ironic part: regulations like Know Your Customer (KYC) and Anti Money Laundering (AML) actually make the problem worse. They force banks to collect and store huge amounts of sensitive data for years. While that's great for compliance with laws like the Bank Secrecy Act, it creates massive "data honey pots" that are incredibly tempting for attackers. It’s a tough spot for risk managers following one rule increases your risk under another.
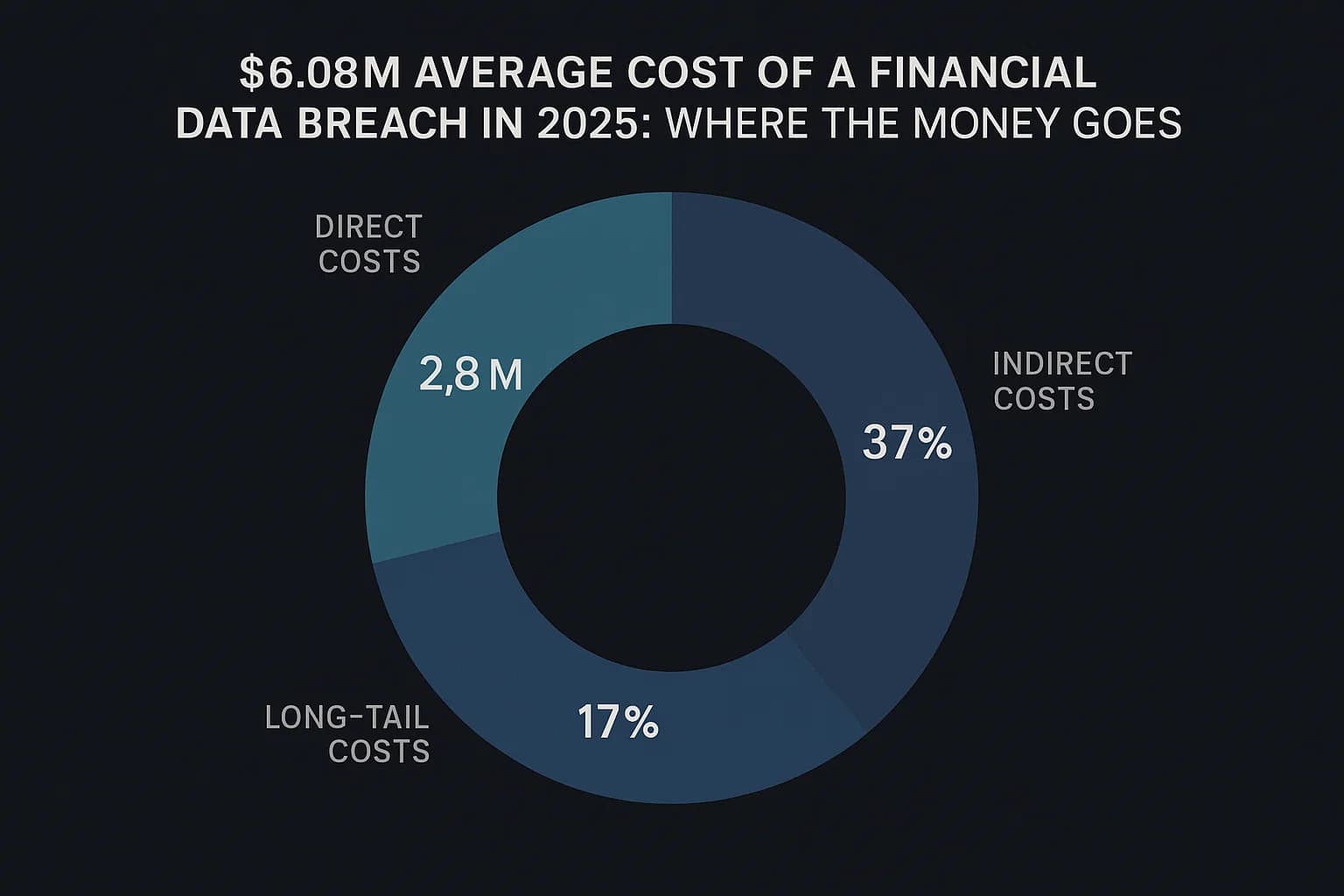
That $6.08 million figure isn't just one big bill. It's a mix of different costs that pile up after a breach, as detailed in the IBM Cost of a Data Breach Report from IBM and the Ponemon Institute :
These costs are becoming so common that they're being passed on to consumers. As companies eat these multi million dollar losses, they raise prices on their services, creating a hidden "cyber tax" that everyone pays.
Quick tip: Don't forget about the inside job. The data shows that breaches caused by a malicious insider are the most expensive, averaging $4.99 million. Your defense has to protect you from threats coming from both outside and within.
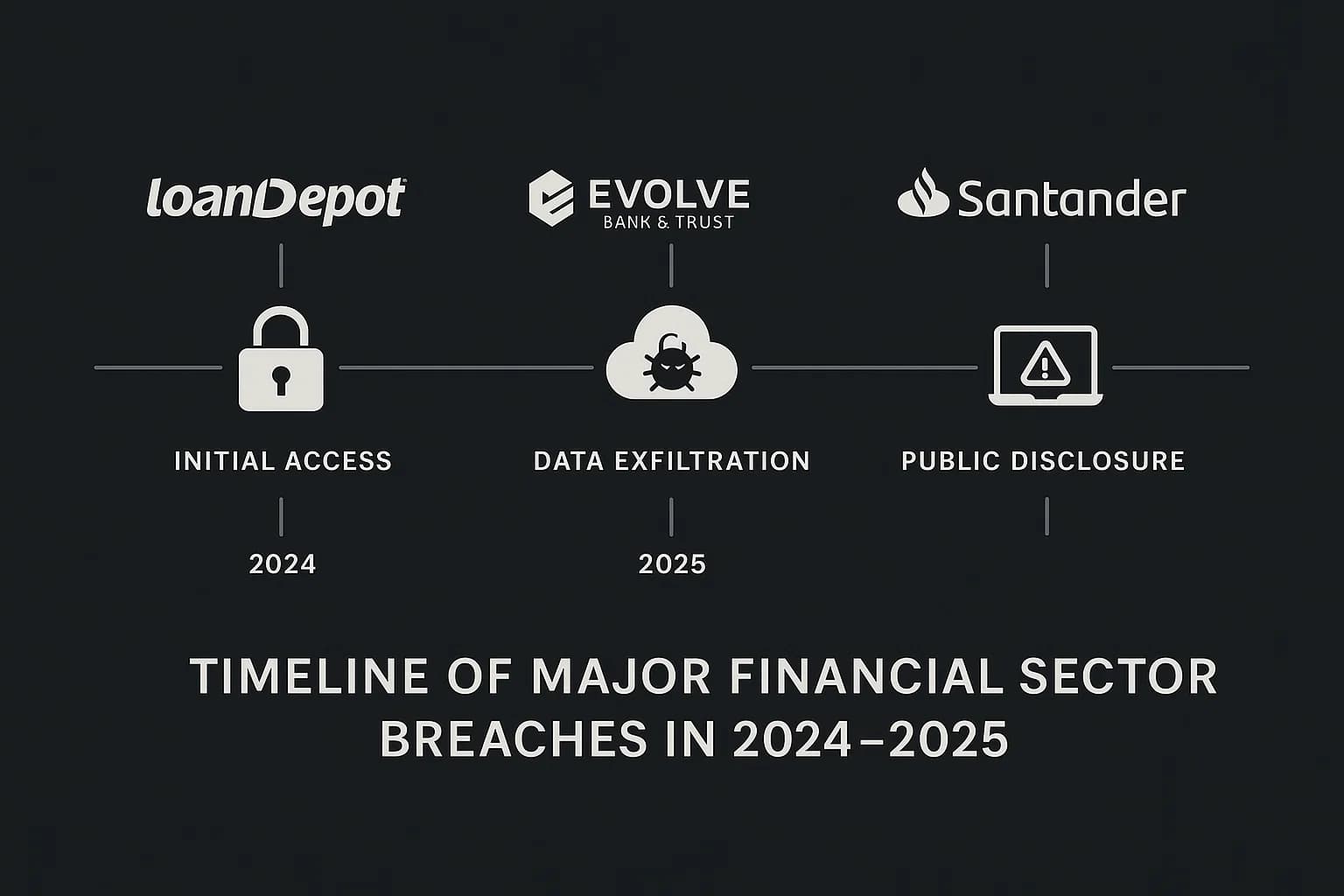
Stats are one thing, but real world stories show us what we can really learn. The breaches over the last year or so reveal exactly how modern cyberattacks work.
In 2024, several major financial players, including mortgage lender LoanDepot and institutions like Evolve Bank & Trust and Patelco Credit Union, were hit by some of the most notorious ransomware groups out there, like ALPHV/BlackCat and LockBit. These weren't just minor disruptions; they were perfect examples of modern ransomware attacks.
In 2024 and 2025, two huge global banks, Santander and DBS Bank, had major data breaches without their own systems ever being directly hacked. These are classic supply chain attacks, where attackers get to you by hitting one of your less secure partners first. You can learn more about these in our guide to supply chain attack trends 2025.
Not all threats come from the outside. In early 2025, the U.S. The Consumer Financial Protection Bureau (CFPB) had a major security incident that wasn't a hack at all, it was a malicious insider.
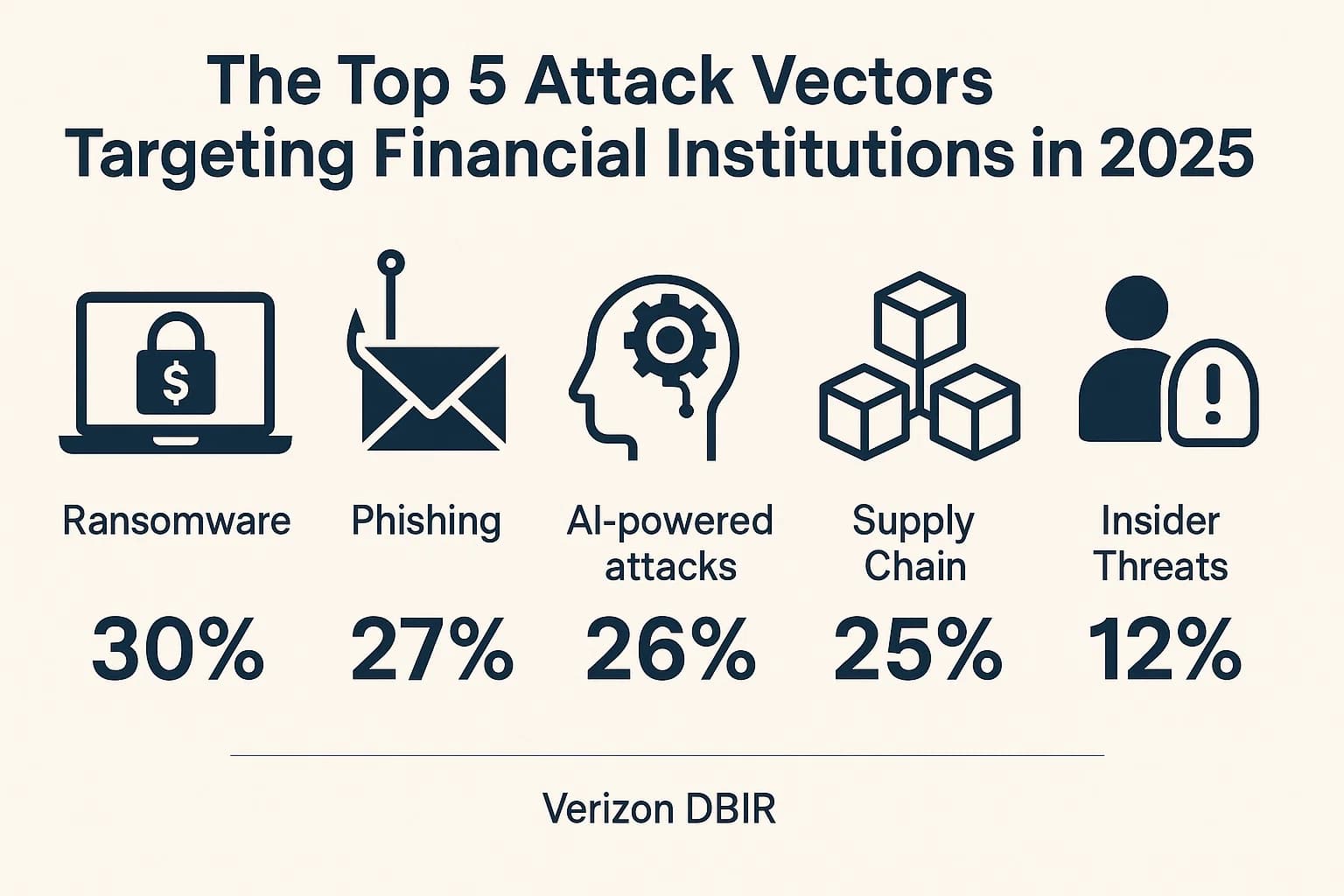
The case studies show a clear pattern. Attackers aren't inventing brand new methods; they're just getting better and faster at using what already works. Here’s what you need to watch out for.
In today's world, just trying to keep attackers out isn't enough. You have to assume they'll get in eventually and be ready for it. Here’s how you can build a truly resilient defense.
Before you get fancy, you have to nail the basics.
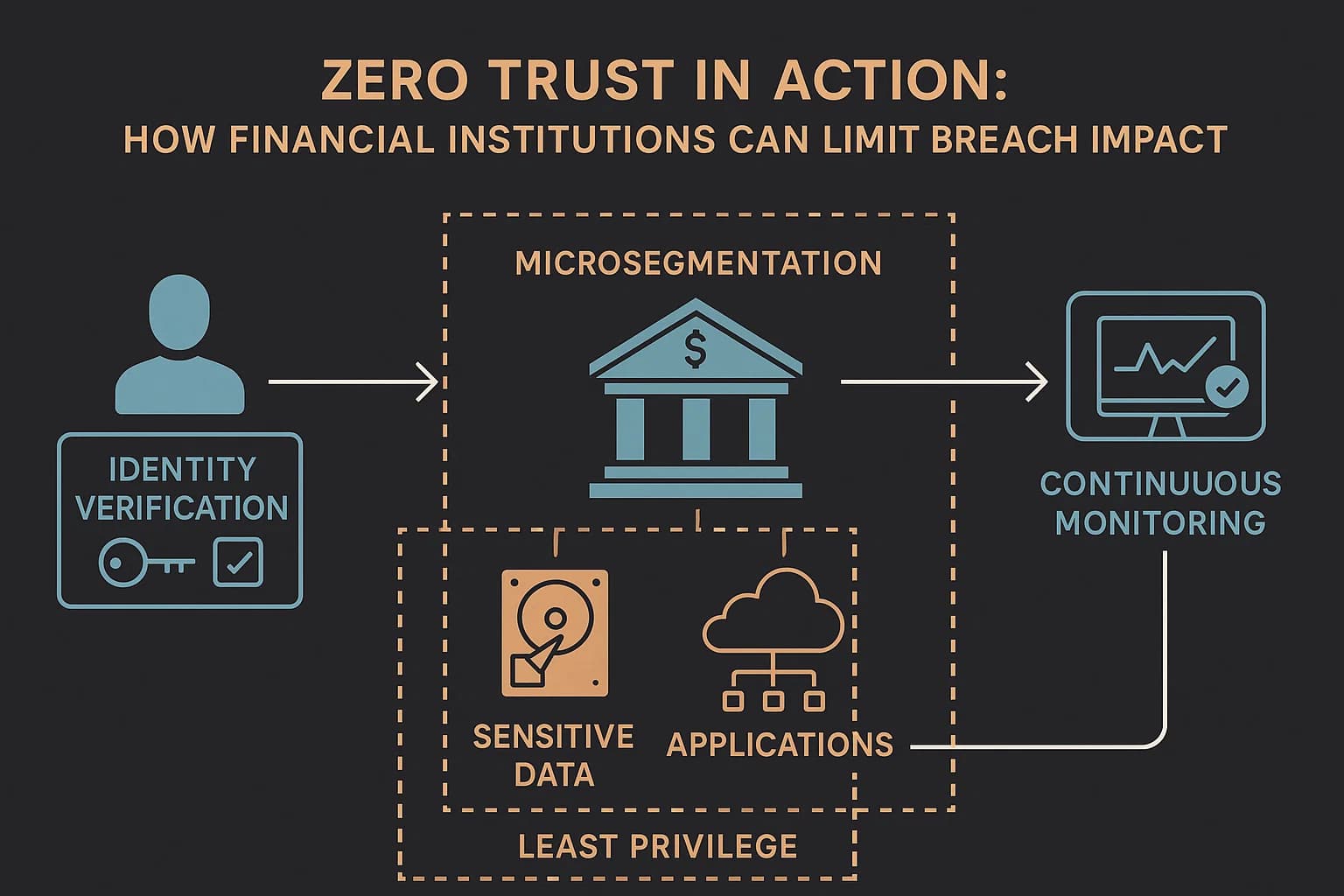
The old idea of a "trusted" internal network is dead. Zero Trust is a security model built on a simple but powerful idea: "never trust, always verify." It assumes attackers are already inside your network.
A once a year penetration test just doesn't cut it anymore. Your systems are constantly changing, and so are the threats. You need to move to a model of continuous security validation.
This means using a mix of automated tools and expert led testing to get a real time picture of your security. A modern continuous penetration testing platform can scan for new vulnerabilities automatically, while your expert teams focus on simulating real world attacks using frameworks like MITRE ATT&CK to model adversary behavior. This approach should also include specialized testing for your most critical assets, like your mobile app penetration testing solution and web application penetration testing services.
A single click can cause a multi million dollar breach, so you can't ignore your people. But the old school, once a year training videos aren't very effective. Here's what to do instead:
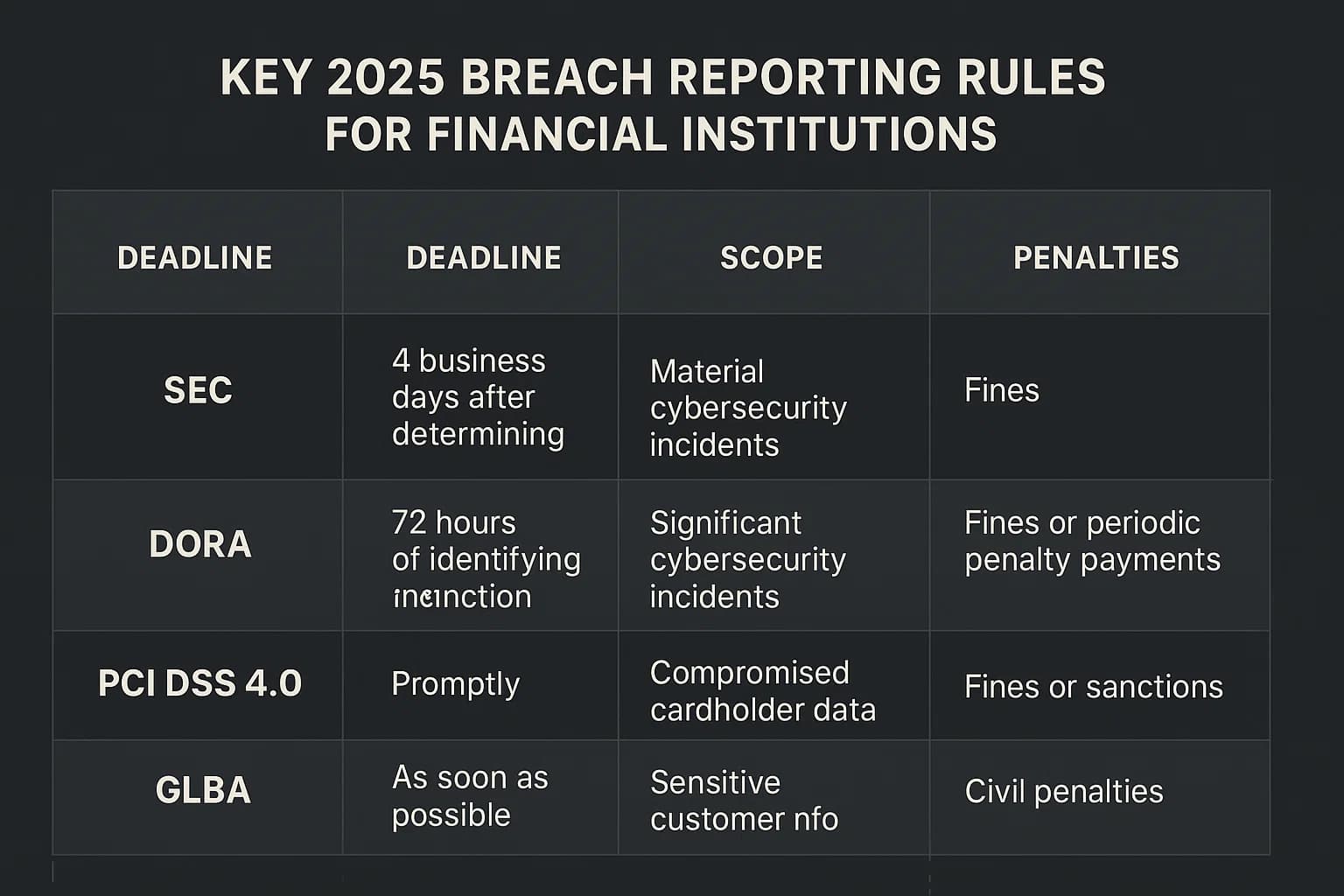
The rules for cybersecurity are getting tougher, with regulators demanding faster reporting and more accountability. For banks, compliance isn't just about checking a box; it's a huge part of managing risk.
With the FFIEC retiring its old assessment tool, regulators are pushing banks to use more modern frameworks. The top choice is the NIST Cybersecurity Framework (CSF).
The new version, CSF 2.0, adds a brand new function: Govern. This highlights how important it is to make cybersecurity a part of your overall enterprise risk strategy. The framework's six functions
Govern, Identify, Protect, Detect, Respond, and Recover give you a flexible, risk based way to manage cybersecurity that can help you meet multiple regulatory requirements at once. Many of the requirements in these regulations, like those in the PCI DSS 11.3 penetration testing guide 2025, align directly with the NIST 800 53.
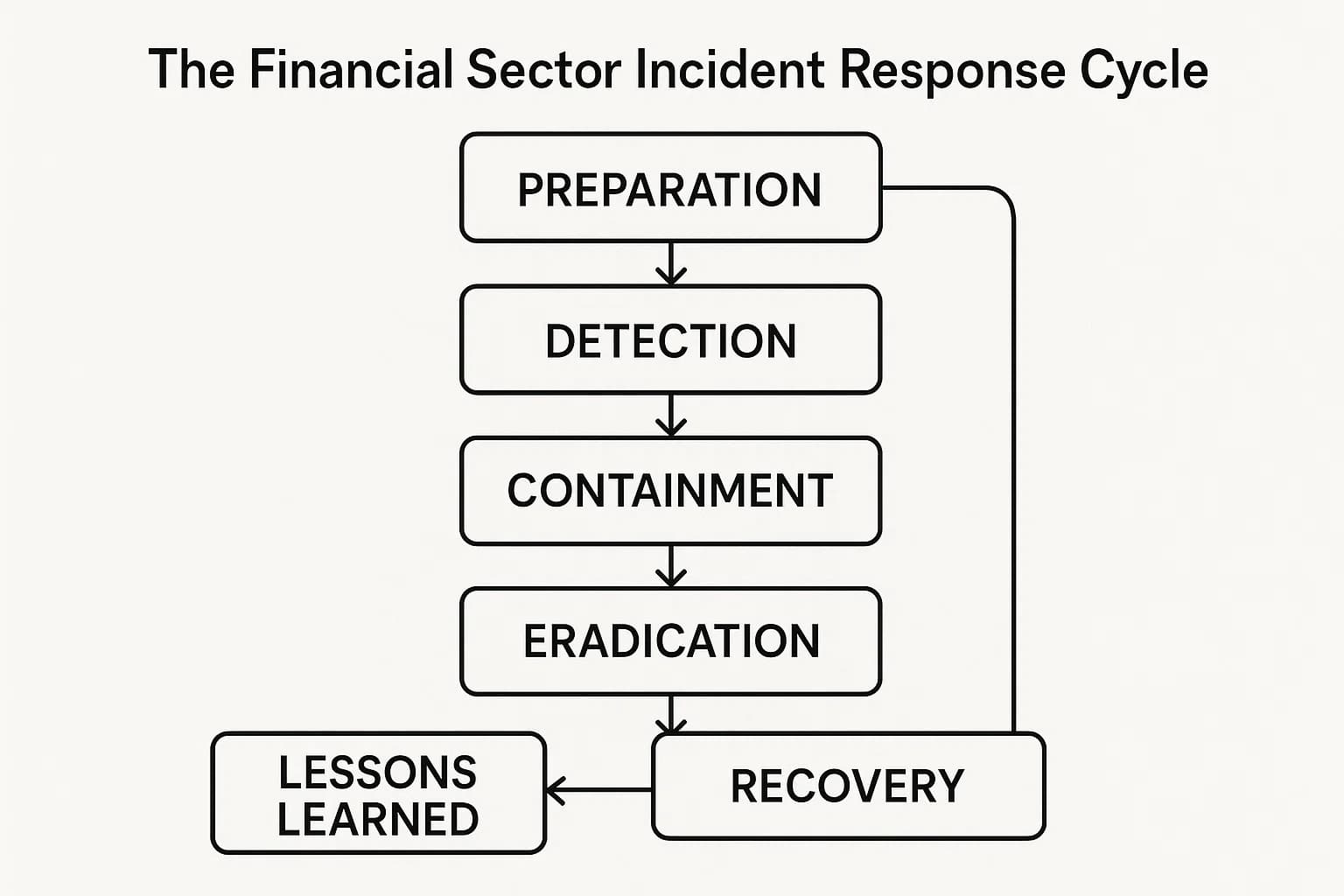
A good, well practiced incident response (IR) plan is the best way to minimize the damage from a breach. Companies with a tested plan save hundreds of thousands of dollars per incident. Based on best practices from CISA and the NIST Cybersecurity Framework, here’s what your plan should look like :
Why are financial institutions frequently targeted by cybercriminals?
It's simple: they have the money and the data. A successful breach gives criminals immediate cash or a ton of valuable personal information they can sell. In fact, one report found that 27% of all global breaches in 2023 hit the financial industry.
What is the average cost of a data breach in the financial sector?
It's incredibly high. According to IBM Cost of a Data Breach Report, the average cost is $6.08 million per incident, the highest of any industry. This covers everything from the investigation and recovery to fines and lost customers.
What types of data are usually stolen in a bank data breach?
Attackers go for customer PII and financial data. This includes names, Social Security numbers, dates of birth, addresses, bank account numbers, and login credentials. This is the information they need to commit identity theft and fraud.
What are common methods attackers use to breach financial firms?
The top methods are ransomware and phishing/social engineering. Ransomware groups like LockBit encrypt and steal data for ransom. Phishing emails trick employees into giving up their passwords or installing malware. We're also seeing a huge increase in supply chain attacks, where attackers hit a company's software vendors to get in.
How can banks and lenders protect themselves from data breaches?
You need a defense in depth strategy. Key steps include encrypting all sensitive data, enforcing MFA everywhere, adopting a Zero Trust model, and keeping all your systems patched. This has to be backed up by strong employee training, including regular phishing tests, and a well practiced incident response plan based on frameworks from the NIST Cybersecurity Framework and CISA’s StopRansomware resources.
What regulations require banks to report data breaches?
There are a lot of them. In the U.S., the new SEC rule requires reporting a material incident within four business days. Federal banking regulators often require notification within 36 72 hours. In Europe, you have GDPR and the new DORA regulation. And if you handle payment cards, you have to follow PCI DSS rules.
How should a bank respond immediately after discovering a data breach?
Your first moves are Contain, Assess, and Activate. First, contain the breach by taking affected systems offline and disabling compromised accounts. Next, assess the damage to figure out what was taken. Then, activate your incident response plan, which means calling your legal team, executives, and law enforcement.
Data breaches in financial institutions are no longer just a technical issue; they're a multi million dollar business risk. The threats in 2025 are more sophisticated than ever, with professional cybercrime gangs, vulnerable supply chains, and AI powered attacks.
Staying safe means shifting from a reactive defense to proactive resilience. You have to assume a breach will happen and be ready for it. This means building your security around Zero Trust, continuously testing your defenses, and having an incident response plan that's ready to go at a moment's notice. The new, tougher regulations aren't just a headache; they're a wake up call, pushing cybersecurity from the server room to the boardroom where it belongs.
Ready to Strengthen Your Defenses?
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us