June 29, 2025
Updated: June 29, 2025
In 2025, cyber insurance claims reveal a harsh reality: 60% stem from BEC and FTF, ransomware losses average $292K, and breach costs hit $4.88M. This guide breaks down the stats behind denials, coverage gaps, and how to secure your policy payout.
Mohammed Khalil

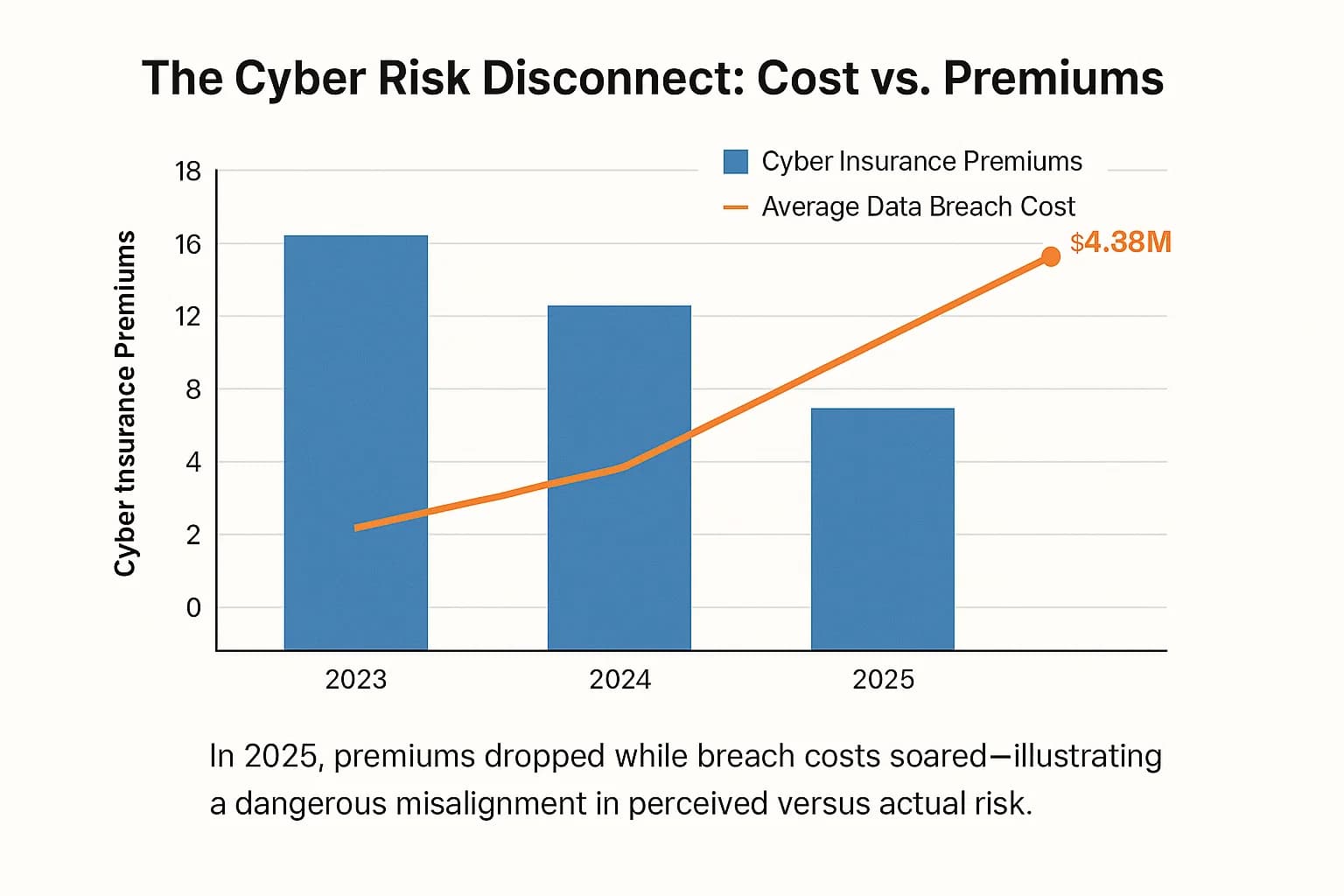
The cyber insurance landscape in 2025 presents a dangerous paradox for business leaders. For the first time in nearly a decade, cyber insurance premiums are falling. After years of relentless price hikes, a fiercely competitive market has created what looks like a golden opportunity for buyers. But here’s the catch: while the price of coverage is going down, the financial impact of a successful cyberattack has never been higher.
This is the great disconnect of 2025. The global average cost of a data breach has surged to an all time high of $4.88 million, according to IBM's latest report. This creates a "buyer's trap," where a lower premium can lull an organization into a false sense of security. The reality is that insurers are competing on price by demanding higher standards of security from their clients. The burden of proof and the consequences of failure are shifting squarely onto the policyholder.
This article is an essential guide for leaders navigating this complex new reality. We’ll dive deep into the latest cyber insurance claims statistics, breaking down what’s driving losses, who is being targeted, and why claims get denied. By understanding the hard data, you can make smarter decisions to justify security investments, choose the right coverage, and ensure that when you need it most, your policy actually pays. Understanding your risk profile starts with a clear view of your vulnerabilities, and the latest cybersecurity vulnerability statistics paint a sobering picture.
On the surface, the cyber insurance market looks incredibly favorable for buyers. Reinsurance giant Munich Re projects the global market will grow to $16.3 billion in 2025, up from $15.3 billion in 2024, signaling massive demand. Yet, in the U.S., direct premiums written actually declined by 2.3% in 2024 the first drop ever recorded by the National Association of Insurance Commissioners (NAIC) since it began tracking this data in 2015.
So, what’s going on? This isn't a sign of reduced risk. It’s a market correction. During the recent hard market, insurers raised rates dramatically and became highly profitable, with loss ratios remaining comfortably below 50%. Now, that profitability has attracted intense competition, forcing carriers to lower prices to win business. This market shift is well documented by industry bodies like the National Association of Insurance Commissioners (NAIC), which provides foundational data for the U.S. market.
However, this price war comes with a critical string attached: insurers are tightening their underwriting requirements and scrutinizing claims more than ever before. They can only afford to offer lower premiums if they are confident their insureds are low risk. They achieve this by being highly selective and enforcing strict security controls as a prerequisite for coverage. This means the "deal" of a lower premium is contingent on the business already having a mature, defensible security program. For organizations that are prepared, it's a buyer's market. For those with weak security hygiene, it's a minefield.
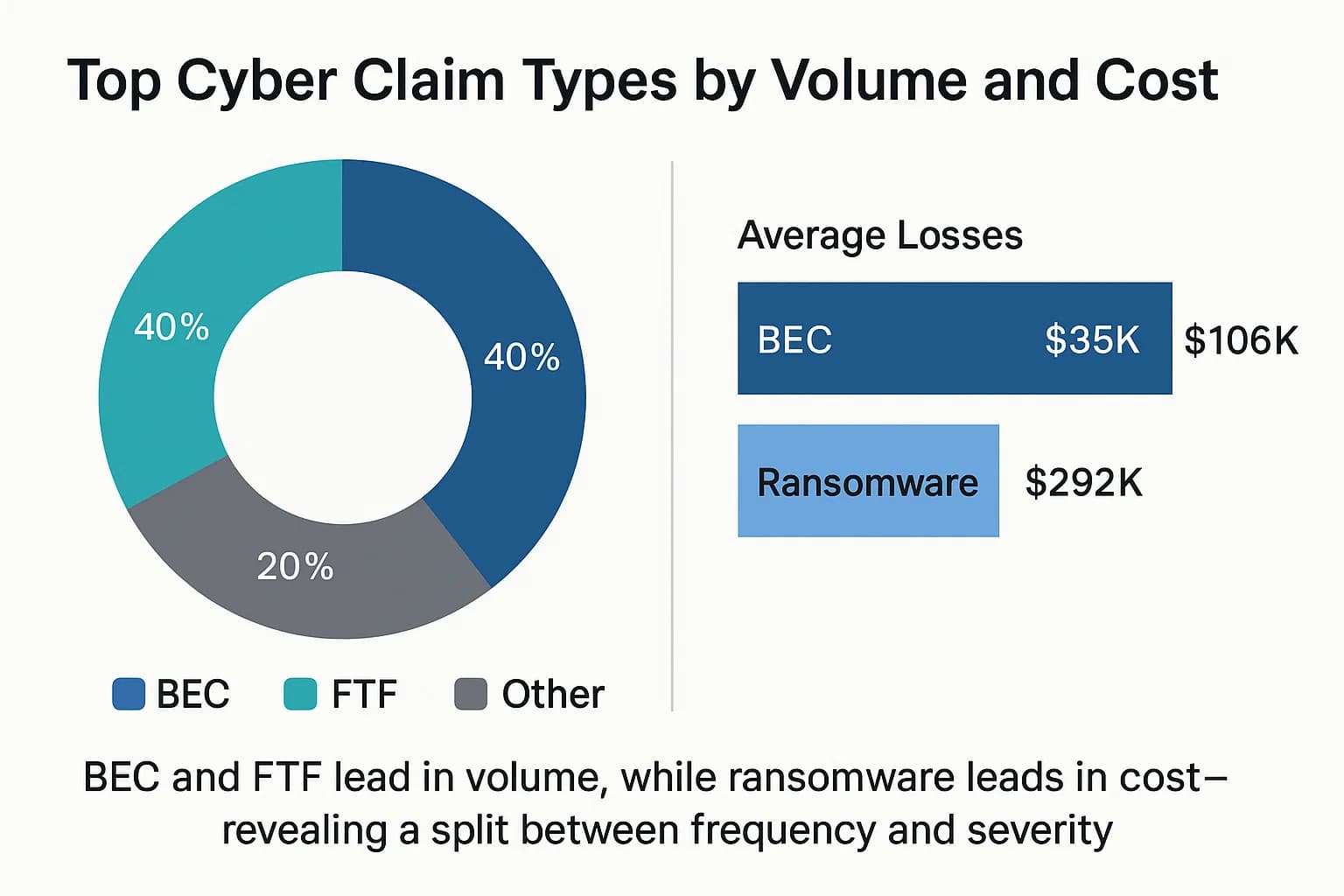
To navigate the market, you have to understand what’s actually driving claims. The data reveals a clear split between the most frequent types of claims and the most financially severe.
By a huge margin, the most common incidents are simple, low tech, and devastatingly effective. According to Coalition's 2025 Cyber Claims Report, Business Email Compromise (BEC) and Funds Transfer Fraud (FTF) together account for a staggering 60% of all cyber insurance claims.
While a standalone BEC incident where an attacker gains access to an email account to spy or steal data has a relatively low average cost of $35,000, that figure is up 23% year over year. The real damage occurs when BEC is used as a launchpad for FTF. When an attacker uses a compromised email account to trick an employee into wiring money to a fraudulent account, the average loss skyrockets to $106,000.
There is a silver lining here, but it requires swift action. Insurers and law enforcement have become adept at clawing back stolen funds if notified immediately. In 2024, Coalition's incident response efforts helped recover $31 million for its policyholders, with an average recovery of $278,000 per event. This proves that the first call you make after discovering a fraudulent transfer should be to your insurer’s claims hotline. These attacks are fundamentally a form of social engineering, a threat illuminated by the latest phishing statistics.
While BEC is the most frequent claim, ransomware remains the undisputed king of cost. Though it accounts for only about 21% of claims, ransomware inflicts the most financial damage, with an average loss of $292,000 per incident.
The dynamics of ransomware are changing rapidly. Here’s what the data shows:
However, the most critical insight is not about the ransomware itself, but how the attackers get in. At Bay's research provides a smoking gun: 80% of ransomware attacks originate from insecure remote access tools like Virtual Private Networks (VPNs) and Remote Desktop Protocol (RDP).
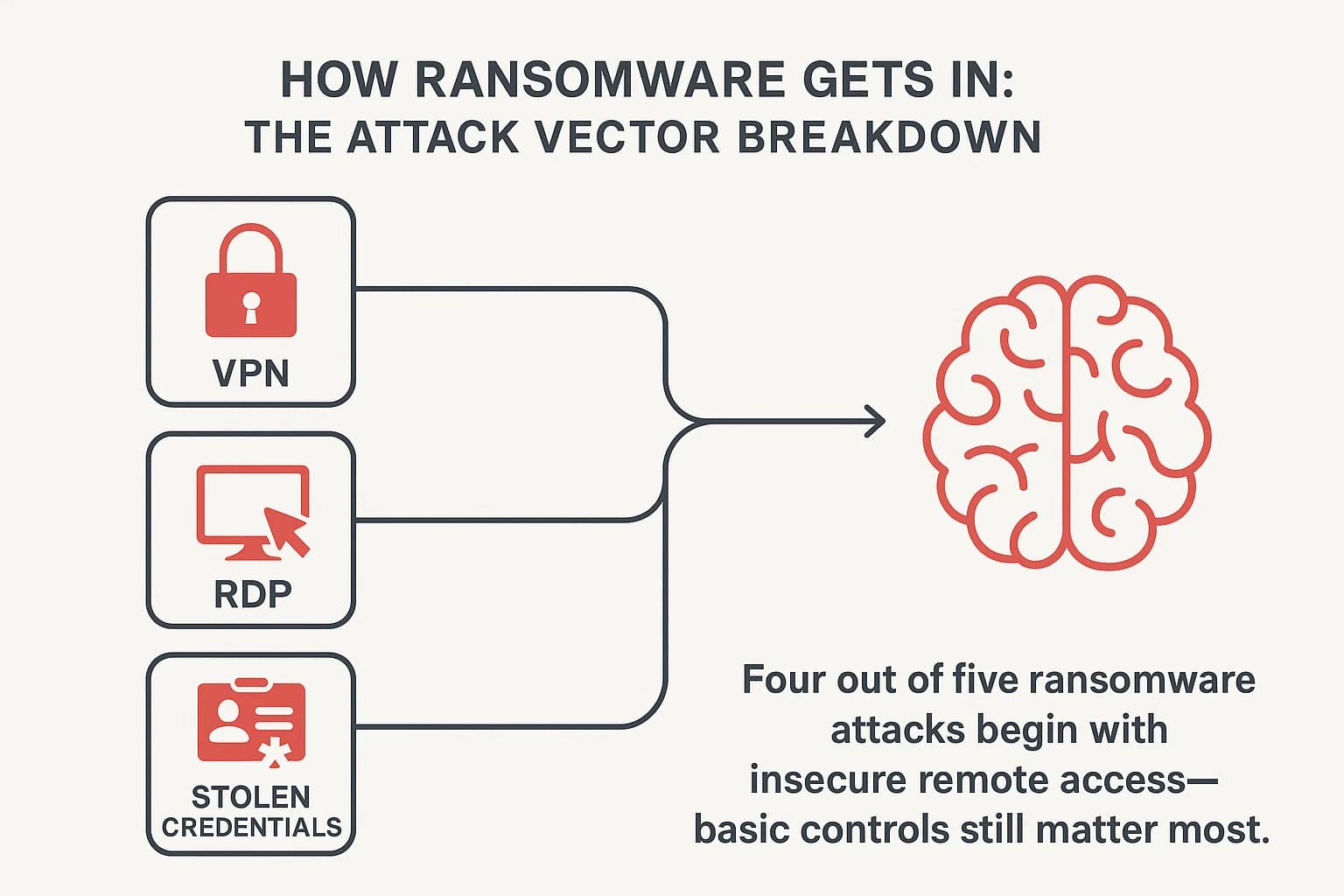
IBM's data corroborates this, identifying stolen or compromised credentials as the top initial attack vector in breaches.
This tells us that preventing the most expensive claims starts with mastering the basics: securing remote access, enforcing multi factor authentication, and patching compromised network vulnerabilities. Digging into the ransomware statistics shows just how prevalent these malware attacks have become.
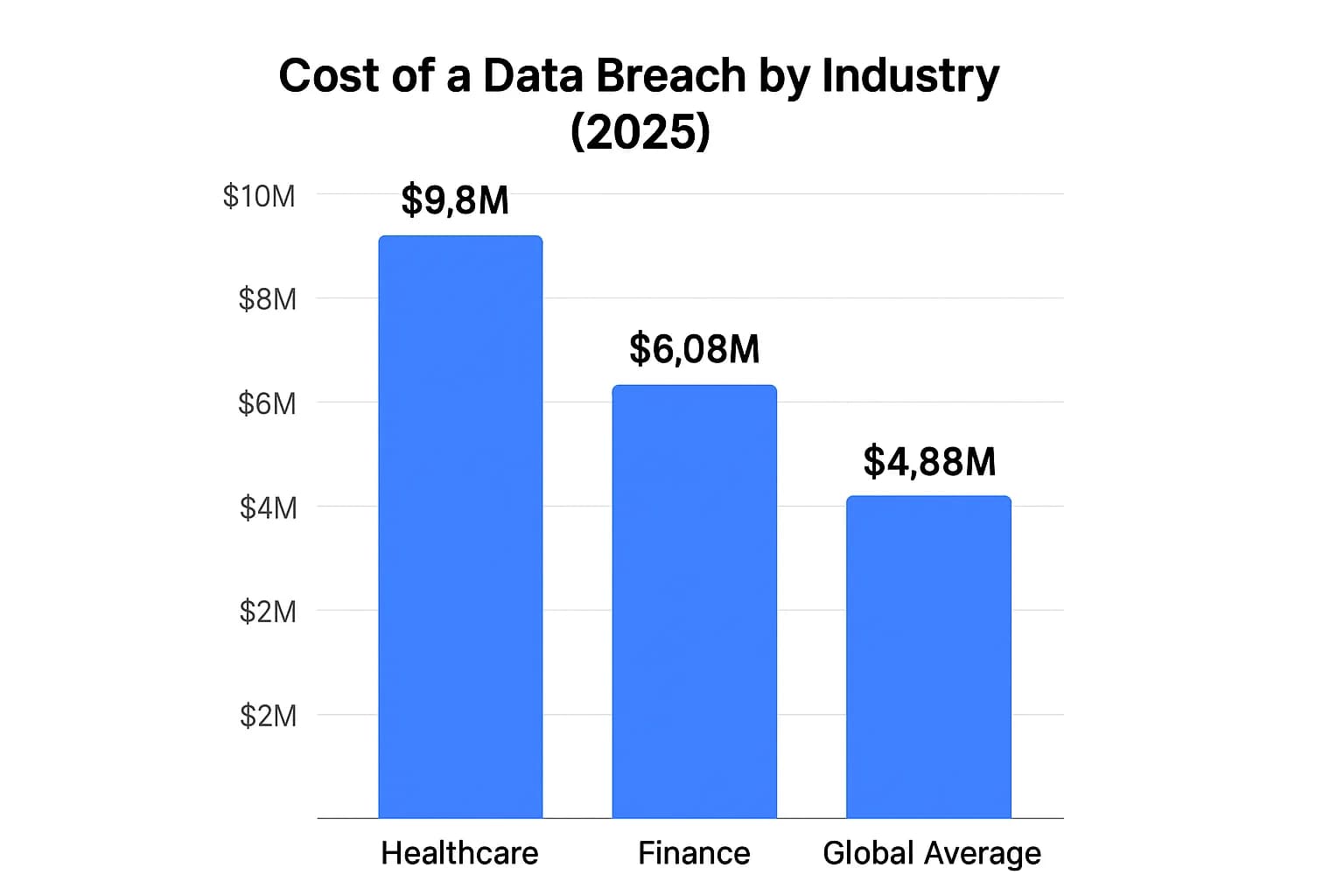
The final piece of the claims puzzle is the data breach itself, and its costs are spiraling. The 2024 IBM Cost of a Data Breach Report revealed that the global average cost has hit an all time high of $4.88 million. For heavily regulated sectors like finance and healthcare, the figures are even more terrifying. The average breach in the financial industry costs $6.08 million, while healthcare tops the list at nearly $9.8 million.
What’s driving this astronomical cost? It's not just IT recovery and downtime anymore. The biggest drivers are regulatory fines and class action lawsuits. Allianz reports that "non attack" privacy breaches claims arising from improper data collection or usage, not a hack are a major new source of large losses, especially in the litigious U.S. market.
This signals a fundamental shift. The definition of a "cyber incident" is expanding beyond traditional security breaches to include failures in data governance and privacy compliance. A company can now face a multi million dollar claim without a single malicious actor ever touching its network. The mounting financial and reputational damage is reflected in the latest data breach statistics.
Understanding who is being targeted is just as important as knowing how. The claims data reveals clear patterns based on company size and industry sector, allowing leaders to benchmark their own risk.
If your company has annual revenues between $25 million and $100 million, you are in the cybercriminal's crosshairs. At Bay identifies this segment as the "sweet spot" for attackers, noting this group saw a 46% increase in ransomware claims in 2024. Aon's data confirms this trend, showing that mid sized organizations file more than half of all cyber claims, despite making up a smaller portion of the overall market.
The logic behind this is simple and ruthless. Attackers are rational economic actors. Very small businesses may not have enough money to make a sophisticated attack worthwhile. Large enterprises, on the other hand, have massive security budgets and dedicated 24/7 security operations centers. Mid sized companies represent the perfect intersection of value and vulnerability: they have significant revenue, valuable data, and critical operational dependencies, but often lack the mature, enterprise grade security posture of their larger peers. If you are in this "squeezed middle," you are not flying under the radar you are a prime target.
The risk profile also changes dramatically by industry. The data shows a clear difference between which sectors experience the most frequent attacks versus which suffer the most expensive ones.
This data provides a powerful lens for risk management. A leader at a manufacturing firm should be acutely aware of their ransomware exposure and prioritize operational resilience. A real estate company, which handles large wire transfers, should focus intensely on preventing FTF. For organizations in healthcare and finance, navigating HIPAA compliance challenges and meeting PCI DSS Penetration Testing Guide is not just a matter of compliance, but a core defense against crippling claims.

One of the most persistent myths in the industry is that "insurers never pay claims". The reality is that claim denials are rare, but when they happen, they are almost always rooted in a contractual failure by the policyholder. A cyber insurance policy is a legal contract with strict obligations. The following real world cases are powerful cautionary tales that every business leader should understand.
To avoid the pitfalls highlighted in the case studies, leaders must understand the fundamental structure of their cyber insurance policies. These are not standardized products, and the details matter immensely.
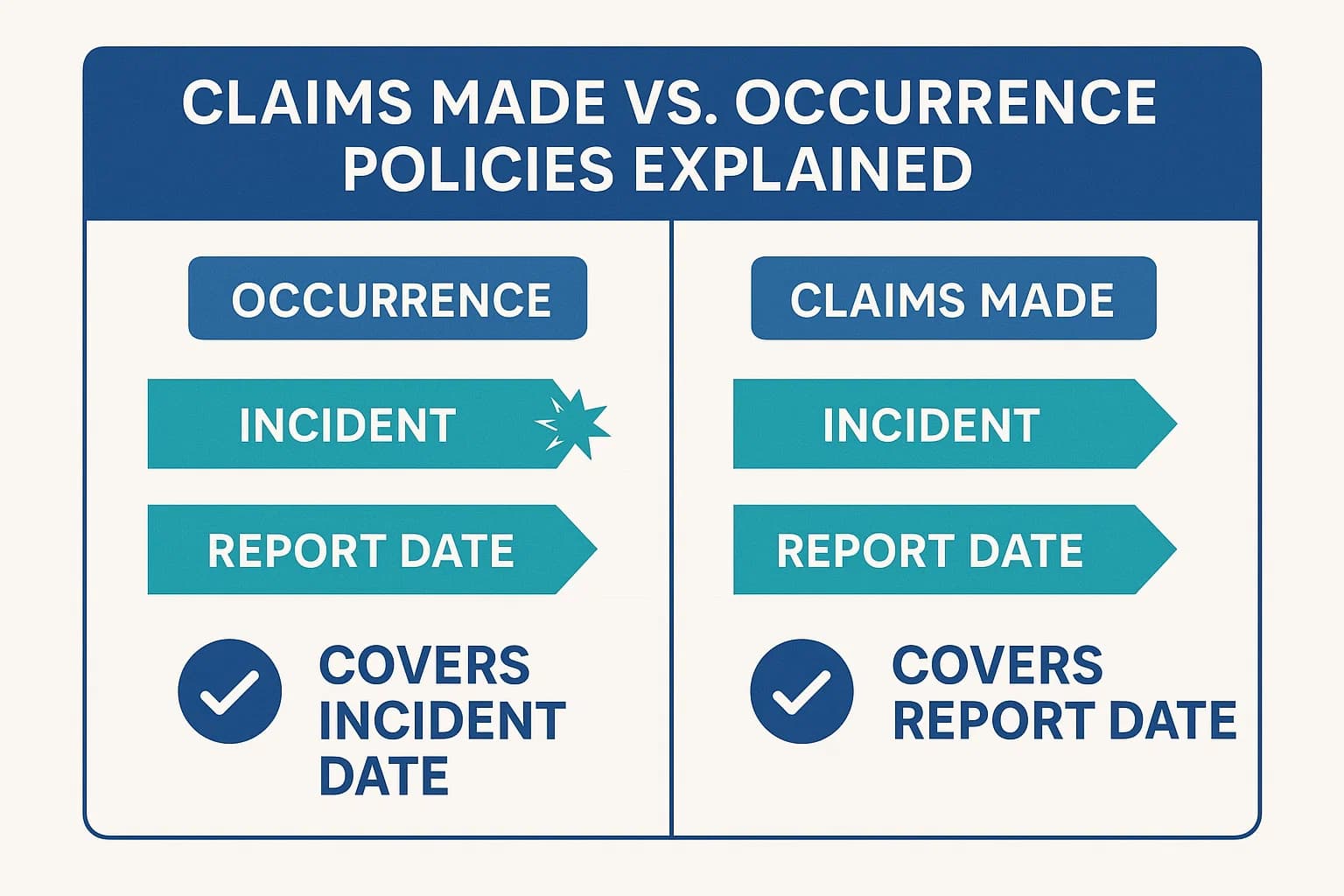
Liability policies come in two main flavors, and for cyber insurance, this distinction is everything.
This structure introduces two critical concepts:
The key takeaway is that the claims made nature of cyber insurance makes continuous, uninterrupted coverage essential. Any gap in coverage can leave your organization completely exposed for past actions.
Every policy has exclusions, but in the evolving world of cyber, some are more critical than others. Based on analysis from legal experts at firms like Reed Smith, here are the key exclusions to scrutinize :
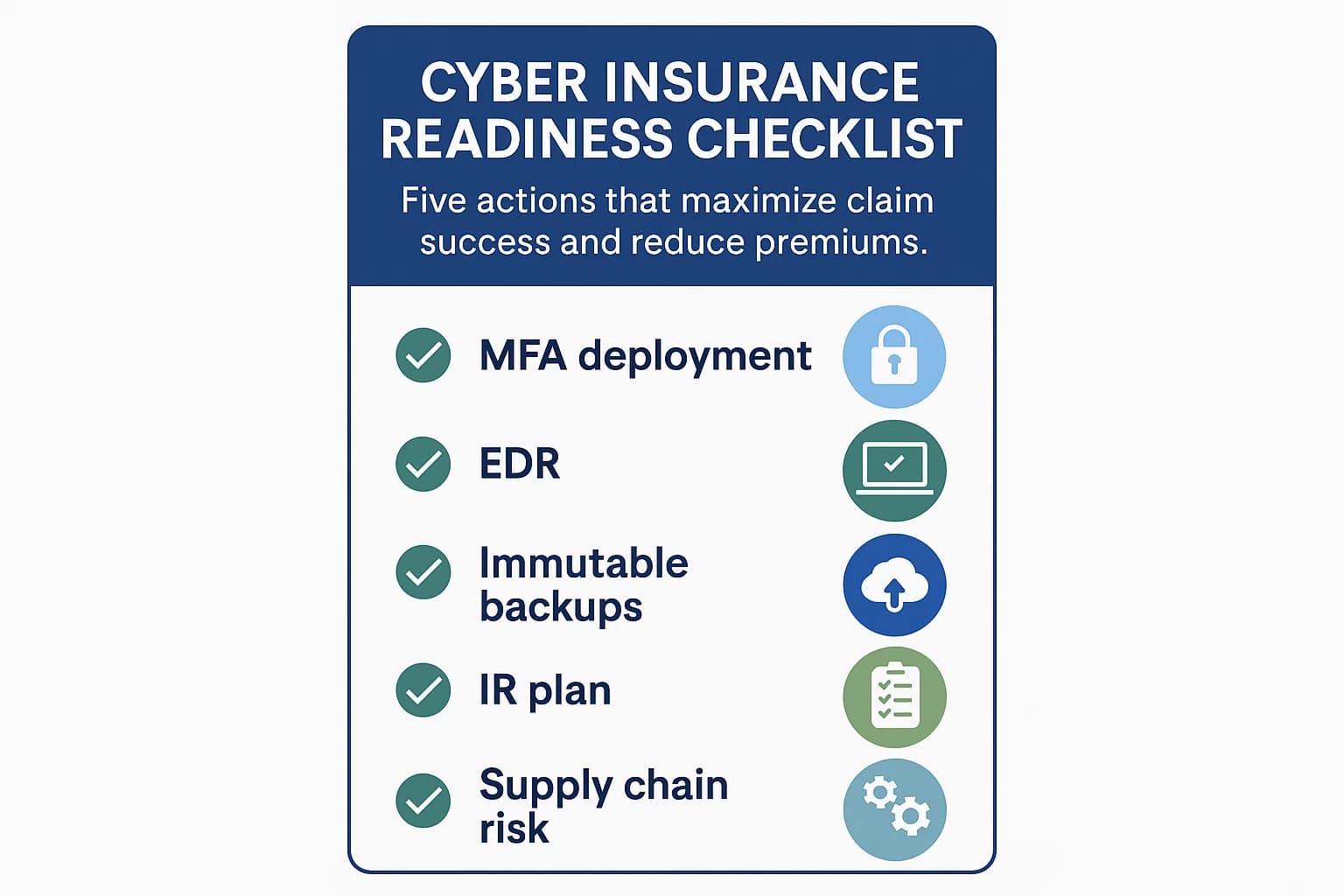
Translating this analysis into action is the final step. The following checklist provides a practical guide for business leaders to improve their insurability and maximize the chances of a successful claim recovery.
It varies dramatically by incident type. The average overall loss amount across all claims is $115,000. However, ransomware claims average a much higher $292,000 , and the total cost of a major data breach, including regulatory fines and legal fees, can reach a staggering $4.88 million.
Business Email Compromise (BEC) and the resulting Funds Transfer Fraud (FTF) are by far the most common, collectively making up 60% of all claims filed in 2024. These attacks target employees through social engineering and are often successful due to human error.
Yes, most cyber policies provide coverage for ransom payments where it is legally permissible to pay. However, insurers almost always require that you use their panel of expert negotiators, who are highly effective at reducing the final payment amount by an average of 60%, according to Coalition. It's important to note that fewer companies are choosing to pay, and some governments are considering banning payments for public sector entities, which could change the landscape.
In the current competitive market, the single best way to lower your premiums is by demonstrating a strong, mature, and evidence backed security posture. Implementing and being able to prove the effectiveness of mandatory controls like comprehensive MFA, EDR, regular vulnerability scanning, employee security training, and having a tested incident response plan will make you a more attractive risk to insurers and can lead to significant premium reductions.
Generally, yes. Policies are designed to respond to incidents that arise from employee mistakes, such as clicking on a phishing link, misconfiguring a cloud server, or falling for a social engineering scam. However, policies typically exclude intentional malicious acts by insiders. If your own employee intentionally steals data or sabotages systems, that would likely need to be covered by a separate Crime or Fidelity insurance policy.
The most common reasons are contractual failures by the policyholder These include:
1) Misrepresenting the state of your security controls on the insurance application (e.g., saying you have MFA everywhere when you don't);
2) The specific incident falls under a clear policy exclusion (like an act of war or a failure of public infrastructure);
3) Failure to report the incident to the insurer within the strict timeframe required by the policy.
The cyber insurance claims statistics for 2025 paint a clear picture of a market at a crossroads. The era of buying a policy as a simple financial backstop for poor security is over. Today, lower prices are directly tied to higher expectations, and proactive, evidence based cybersecurity is no longer optional; it's a prerequisite for insurability.
The data shows that attackers are targeting the path of least resistance, whether through a simple phishing email leading to a massive wire transfer or an unpatched VPN leading to a crippling ransomware event. The most powerful takeaway from this analysis is that your insurance policy is a contract, and your application is a legally binding promise. Understanding the language of that contract and fulfilling your security obligations is the final, critical line of defense.
Ultimately, business leaders should reframe their view of cyber insurance. It is no longer just a tool for risk transfer; it is a strategic partnership. The requirements set forth by insurers are not arbitrary hurdles; they are a data backed blueprint for building a more resilient, defensible, and successful organization in the face of ever present digital risk.
Security questions don’t wait. Neither should you. Whether you're evaluating PTaaS, need help with a red team assessment, or just want to see what DeepStrike can uncover Reach out. We’re always happy to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us