August 31, 2025
Updated: August 31, 2025
Understand how much a vulnerability assessment costs in 2025, what drives pricing, and how to budget effectively for SMBs, mid-market, and enterprises.
Mohammed Khalil

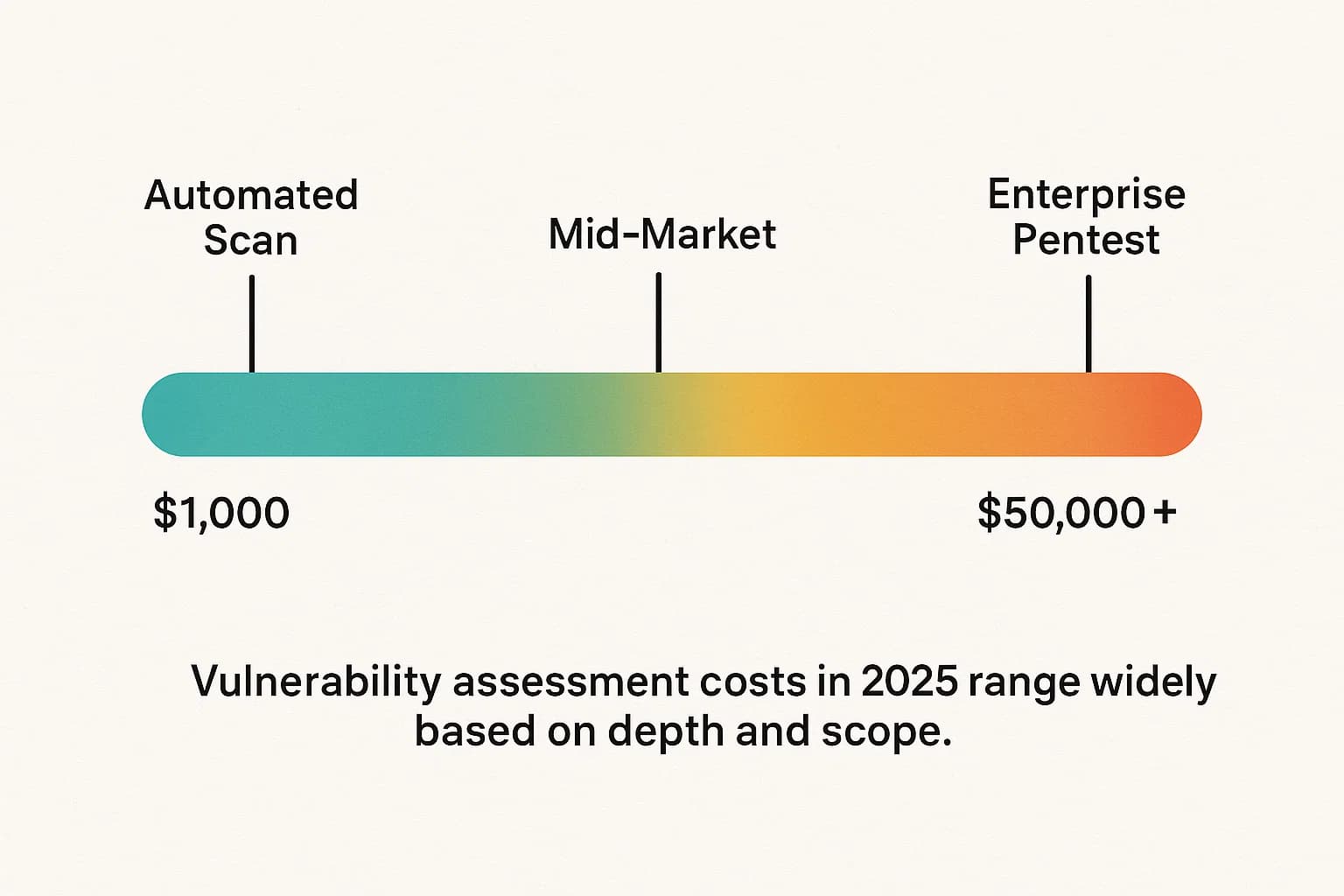
So, how much does a vulnerability assessment cost? The honest answer is a frustratingly wide range, typically from $1,000 for a simple automated scan to over $50,000 for a complex, manual engagement. But the number on the quote isn't the real story. The real story is about risk, and in 2025, the stakes have never been higher.
The threat landscape is relentless. The Verizon 2025 Data Breach Investigations Report (DBIR) revealed that the exploitation of vulnerabilities is a top initial access vector for breaches, accounting for 20% of all incidents, a staggering 34% increase from the previous year. Attackers aren't just knocking on the door; they're actively looking for unlocked windows.
This is why understanding vulnerability assessment pricing is so critical. It’s not just a line item in your IT budget; it's a direct investment in your organization's resilience. The cost is fundamentally tied to the level of human expertise and the thoroughness of the methodology you're paying for. When you compare this investment to the potential fallout of a breach which the IBM 2025 Cost of a Data Breach Report pegs at an all-time high of $10.22 million for U.S. companies the value proposition becomes crystal clear.
Pricing at a Glance: Typical Annual Budgets

This guide breaks down every factor that goes into a quote, so you can make an informed decision that protects your business without breaking the bank.
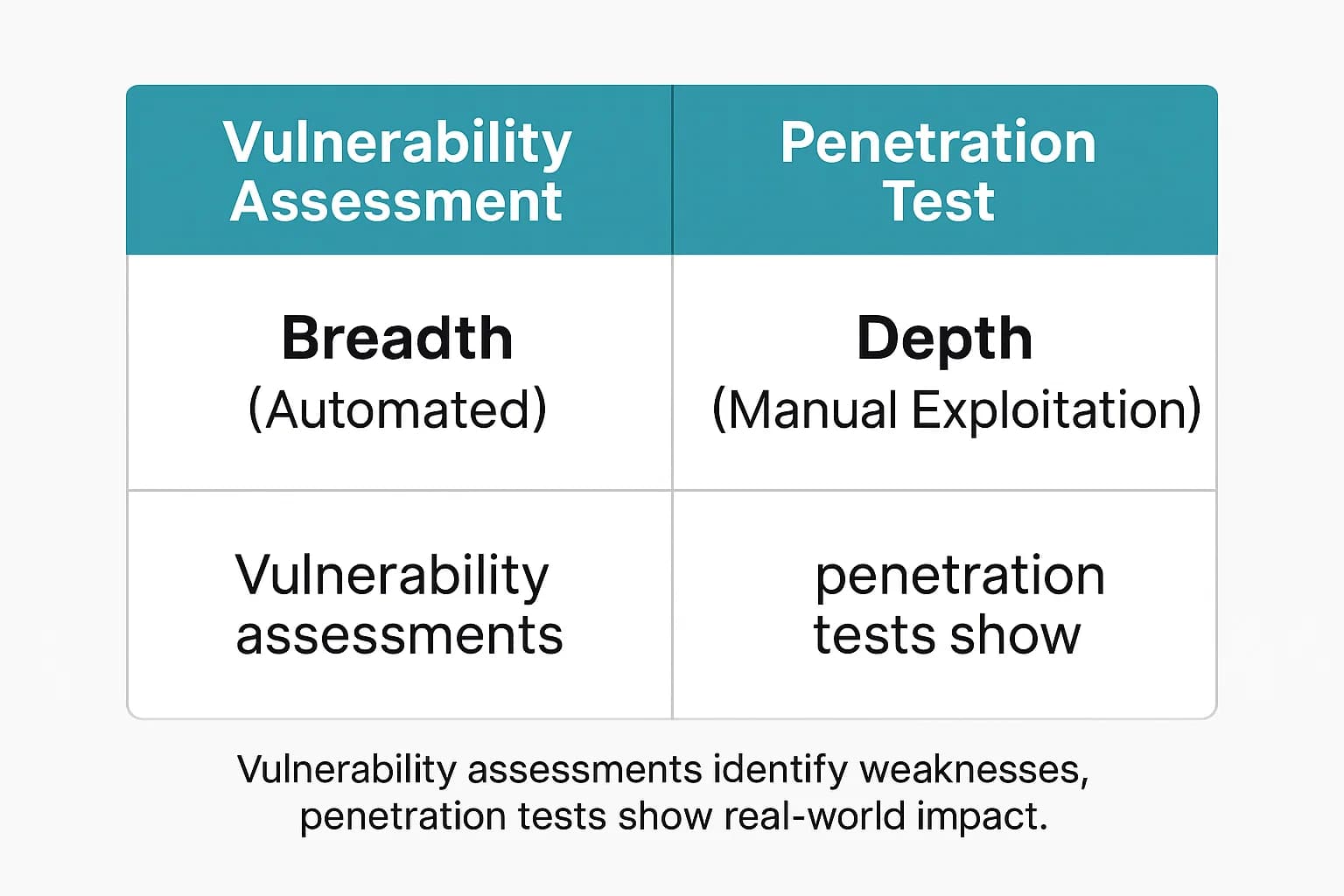
Before we talk numbers, we need to get the terminology right. This is where many businesses make their first, most critical mistake.
A Vulnerability Assessment (VA) is a systematic process of identifying, quantifying, and prioritizing security weaknesses in a system. Think of it as a comprehensive inventory of potential problems. VAs are often automated and rely on scanning tools like Tenable Nessus, Qualys, or OpenVAS to check your systems against a massive database of known vulnerabilities (CVEs). The primary goal is breadth to find as many known issues as possible across a wide range of assets. It answers the question:
“What are our weaknesses?”
A Penetration Test (Pentest), on the other hand, simulates a real-world attack. A pentester doesn't just find vulnerabilities; they actively try to exploit them to gauge the actual business impact. This process is heavily manual and uncovers issues automated scanners can't see. A pentest answers the question: “What can an attacker actually do with our weaknesses?” For a deeper dive, see our guide on the vulnerability assessment vs penetration testing debate.
Buyer Beware: A Word on "Penetration Tests" Under $4,000 Be extremely wary of any service advertised as a "penetration test" for less than $4,000. A true pentest involves days of a certified expert's time and creativity. A sub-$4k price tag almost guarantees you're just buying a basic, automated vulnerability scan, not a human-led test.
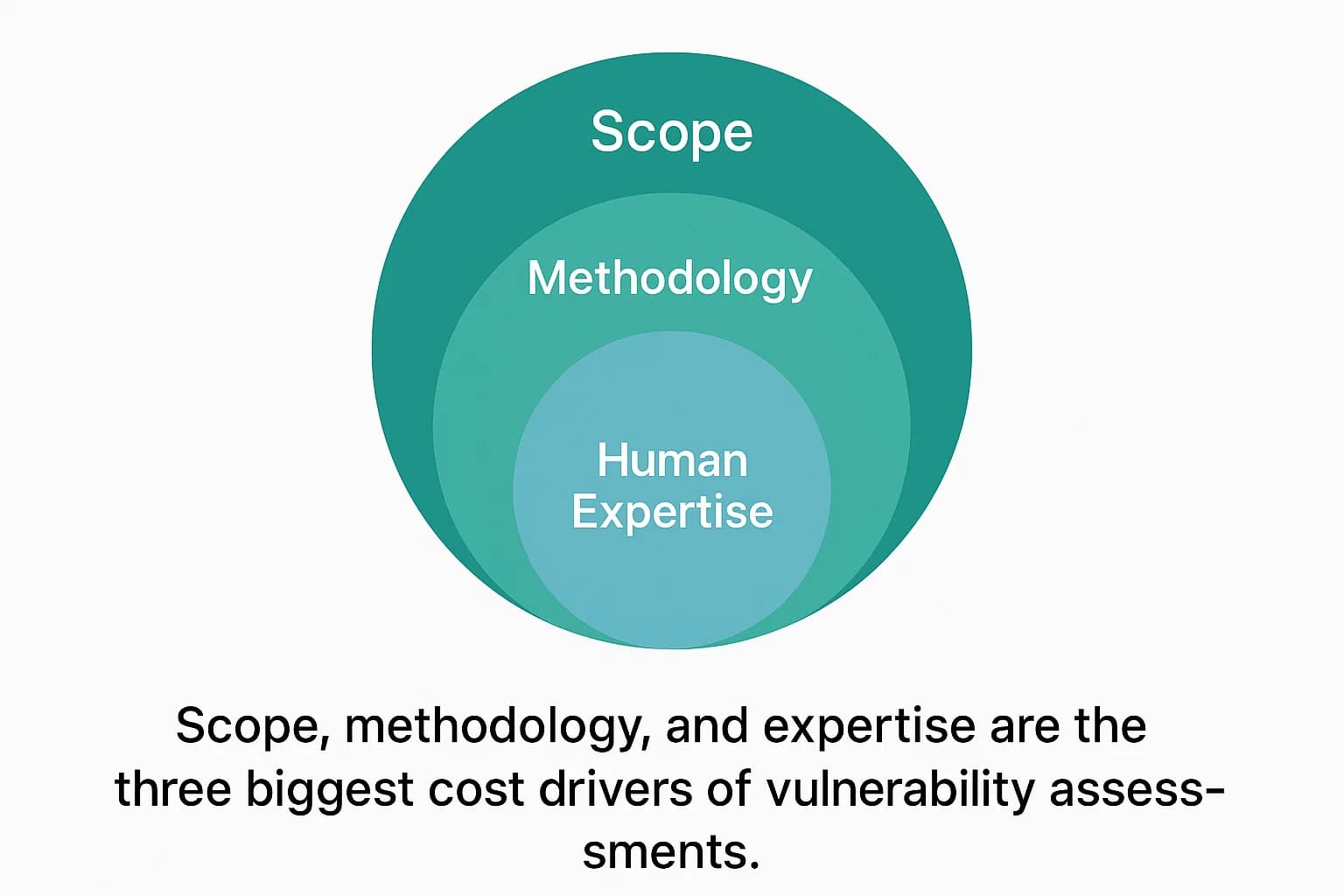
The cost of a vulnerability assessment is primarily driven by the scope and complexity of the assets being tested, the testing methodology (black, white, or grey box), and the experience of the security professionals involved.
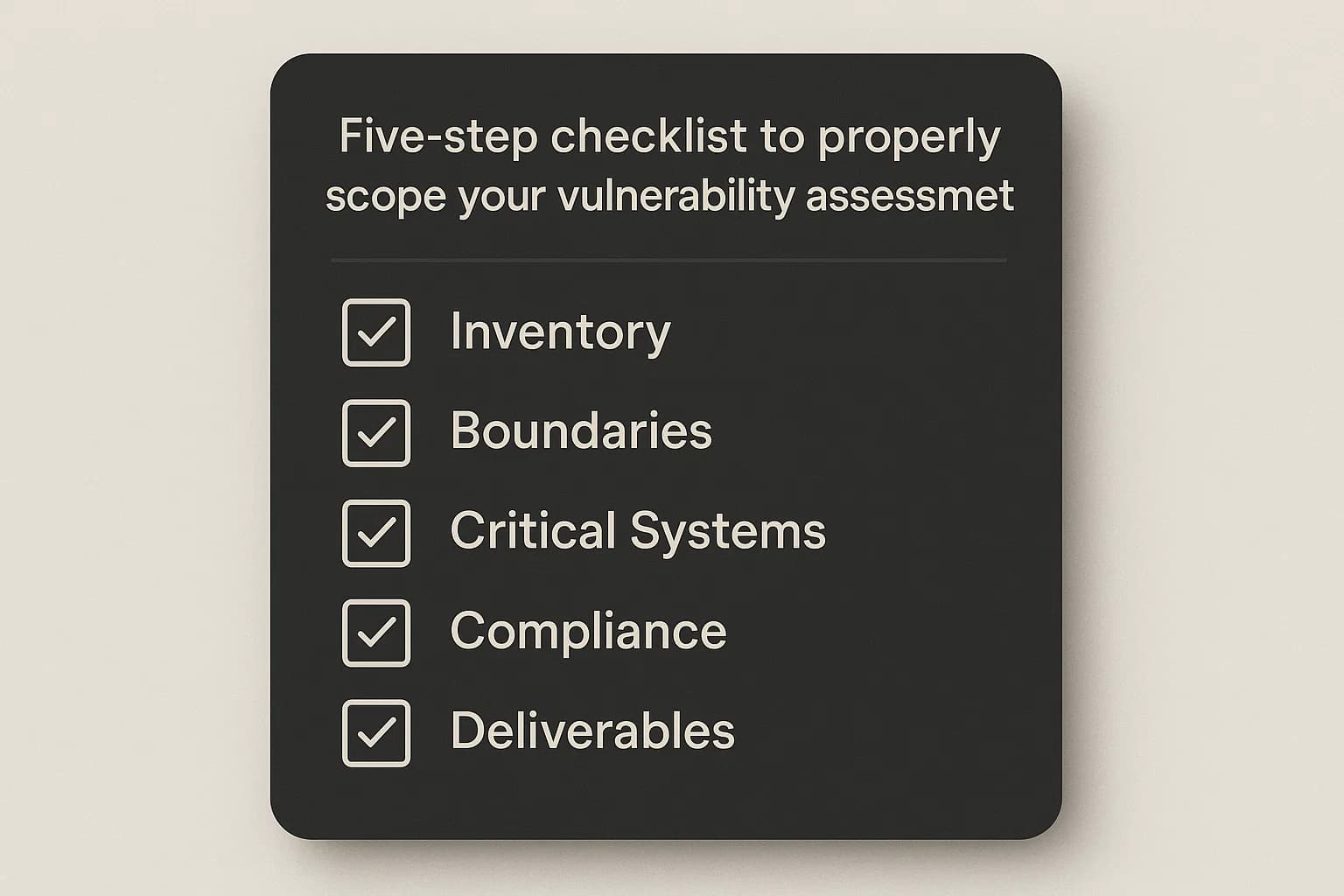
An ambiguous scope is the leading cause of a failed engagement. Use this checklist to ensure you get an accurate quote for the work you actually need.
Annual security testing budgets typically range from $8,000-$20,000 for small businesses to over $50,000 for large enterprises, covering a mix of network, web, and cloud assessments.
For example, one 200-asset mid-market SaaS company invested $18,000 in a comprehensive assessment that included a free retest within 60 days. This process helped them reduce their critical vulnerabilities by 86% in just six months, saving an estimated $1M in annual costs by improving their remediation processes and reducing man-hours. For a full overview of options, explore our vapt services provider.
If you need an assessment to satisfy a compliance requirement, expect the cost to be higher. Regulations transform a technical exercise into a formal, audit-readiness engagement where the reporting and documentation standards are just as important as the testing itself.
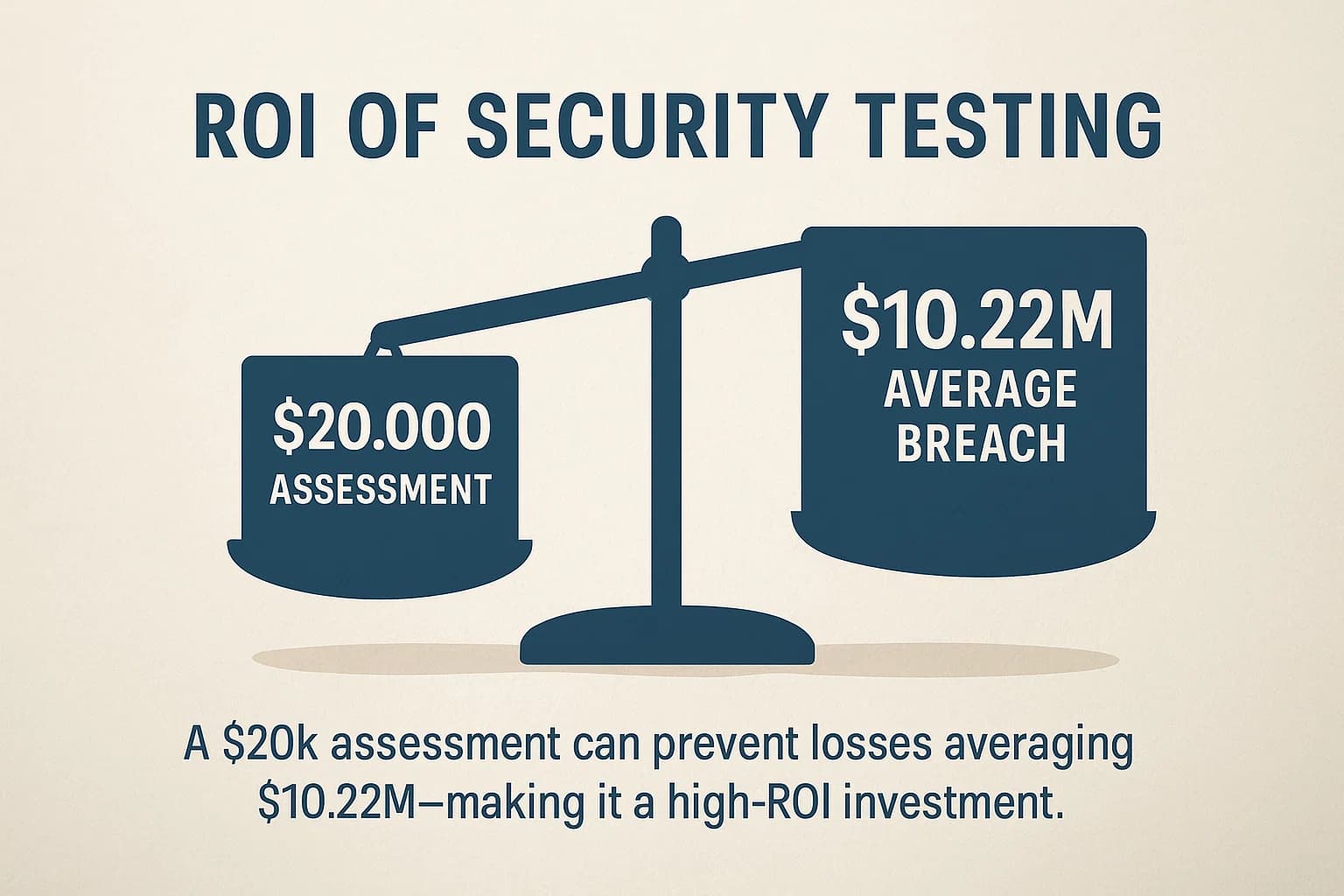
It's easy to see a $20,000 penetration test as an expense. It's more accurate to see it as an investment with a massive potential return. The math is simple: a $20,000 assessment versus a $10.22 million average breach cost.
One study found that if a $20,000 assessment reduces the risk of a $1 million breach by just 40%, the expected loss reduction is $400,000 a 20x return on investment.
Beyond preventing a catastrophic breach, a strong testing program delivers other tangible benefits. It's often a prerequisite for obtaining favorable terms for cyber insurance, directly impacting another business cost center. Furthermore, in an era where the Verizon DBIR notes that mass exploitation of new vulnerabilities happens in zero days, a proactive assessment program helps you find and fix flaws before they become a five-alarm fire drill. This is why continuous penetration testing matters.

Getting the most value from your security budget means avoiding common procurement pitfalls.
1. How much does a vulnerability assessment cost for SMBs?
For small businesses, a basic automated scan can cost $1,000-$5,000, while a more thorough manual assessment or penetration test for a critical asset typically starts between $5,000 and $15,000.
2. What are the main factors that drive the price of an assessment?
The primary cost drivers are the scope (number of assets like IPs or web pages), the complexity of the systems, the testing methodology (black, white, or grey box), and any specific compliance requirements like PCI DSS or HIPAA that demand more rigorous documentation.
3. How long does a vulnerability assessment take in 2025?
An automated vulnerability scan can be completed in hours. However, a comprehensive manual assessment or penetration test is a more involved process, typically taking one to three weeks depending on the scope and complexity of the environment.
4. Are remediation and retesting included in the cost?
It varies by vendor. Many quotes for manual penetration tests include one free retest of critical findings within a specific timeframe (e.g., 30-60 days). However, extensive remediation support or multiple retests often come at an additional cost, so it's crucial to clarify this upfront.
5. How often should we perform a vulnerability assessment?
According to best practices from frameworks like NIST, organizations should perform continuous automated scanning and conduct a manual penetration test at least annually on critical systems. For high-risk environments or to meet compliance, quarterly or semi-annual assessments are recommended.
For more answers, check out our comprehensive Pen Testing FAQs.
Understanding vulnerability assessment pricing isn't about finding the cheapest option, it's about making the smartest investment in your security. The cost is a direct function of scope, complexity, and the level of human expertise you bring in. While a low-cost automated scan can provide a baseline, a manual, expert-led penetration test is what uncovers the critical risks that lead to devastating breaches. By viewing this as a high-ROI investment against the catastrophic cost of a data breach, you can build a defensible business case for a security program that truly protects your organization.
Ready to Strengthen Your Defenses?

The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re...source healthcare, and technology sectors.
About the Author
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us