October 28, 2025
Updated: October 28, 2025
Understand the 4 core AppSec testing methods SAST, DAST, IAST, and RASP and how to combine them for full-stack protection across your SDLC in 2025.
Mohammed Khalil

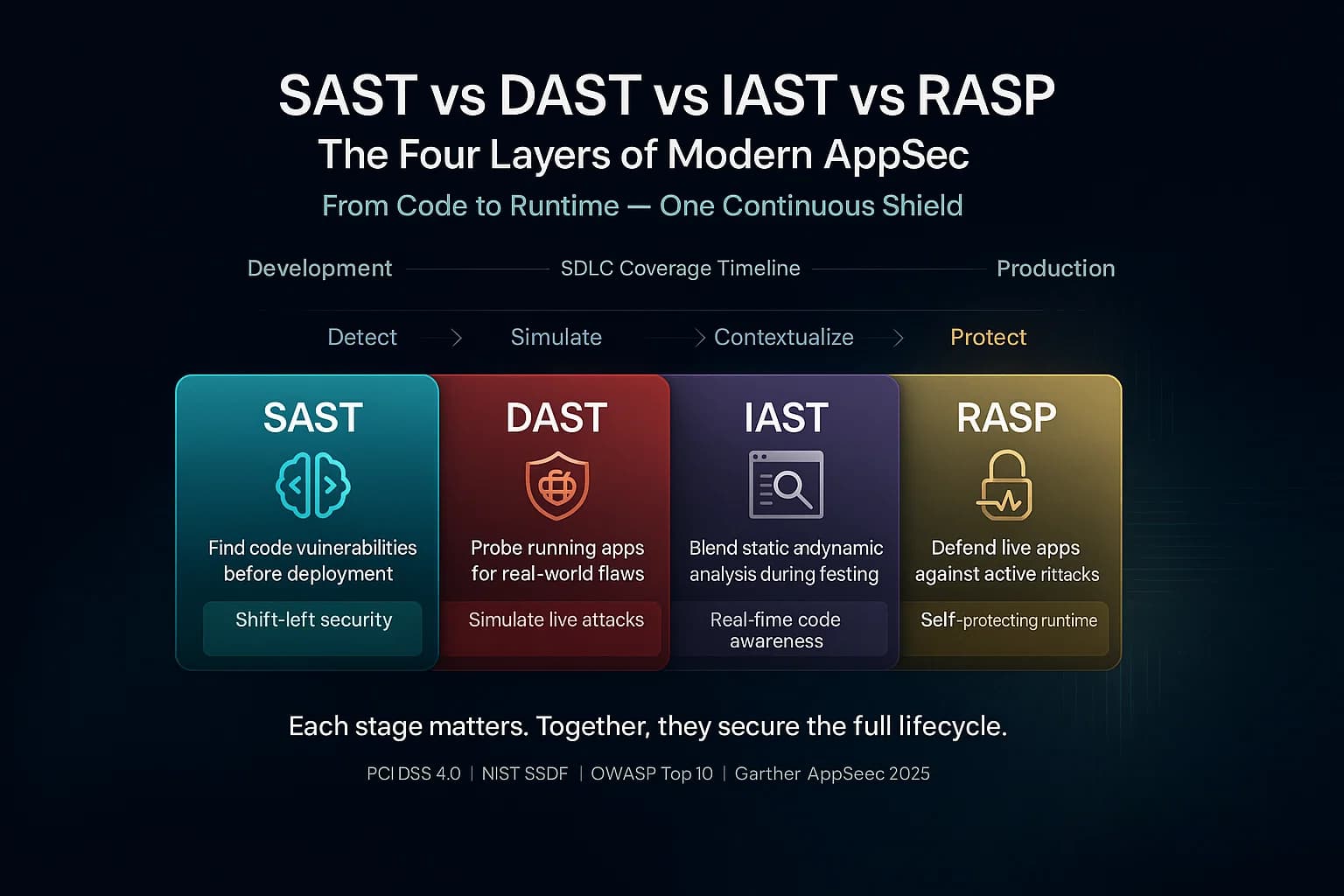
SAST vs DAST vs IAST vs RASP these acronyms represent four different phases and methods of application security testing. In simple terms, SAST analyzes your code for security bugs white box, DAST probes your running app for flaws black box, IAST combines both approaches with in app instrumentation, and RASP embeds a real time defender inside the app. Each has a distinct role: SAST catches errors early, DAST finds live issues, IAST gives context aware results during QA, and RASP protects production systems.
In 2025’s complex threat landscape with cloud native apps, strict compliance e.g. PCI DSS, NIST SSDF, and rapid DevOps cycles using all of these tools in tandem is critical. For example, NIST’s secure development guidelines explicitly recommend automated static analysis to catch vulnerabilities early, while Gartner and OWASP highlight using layered testing to address the OWASP Top 10. For a broader view on testing strategies, see our article What is Penetration Testing?.
With attacks on the rise, relying on just one method leaves gaps. This guide explains how SAST, DAST, IAST, and RASP differ, their pros/cons, and how they fit together. We’ll also cover practical integration steps and common questions.

Static Application Security Testing SAST is white box analysis of your codebase. It inspects source code, bytecode, or binaries without running the program. Essentially, SAST tools parse your code and look for insecure patterns like unsanitized inputs or dangerous constructs. Because SAST has full visibility into all code paths, it can cover 100% of the code including dead code. Popular SAST tools e.g. Checkmarx, SonarQube, Fortify, GitHub CodeQL integrate into IDEs or CI pipelines to give developers instant feedback.
In practice, we often tune SAST rules and triage findings so dev teams focus on real vulnerabilities. SAST must be combined with other methods, as it alone won’t find every flaw. For example, a hardcoded API key might be flagged by SAST, but an open S3 bucket configuration would not.

Dynamic Application Security Testing DAST is black box testing of a running application. Without looking at code, DAST tools send malicious payloads like SQLi or XSS attacks to the live app and inspect responses. Think of it as simulating an external attacker probing your web server or API. Because DAST works against the deployed app, it can uncover issues that only manifest at runtime, such as authentication/authorization errors, insecure server settings, or business logic flaws.
For example, Splunk notes DAST identifies vulnerabilities that only appear during application execution and works independently of the application’s language. However, DAST may miss insecure code logic that SAST would flag. In short, DAST is the last check that validates your defenses by acting like a hacker. Many teams run scheduled DAST scans during off hours or in a staging mirror to find any missed holes.
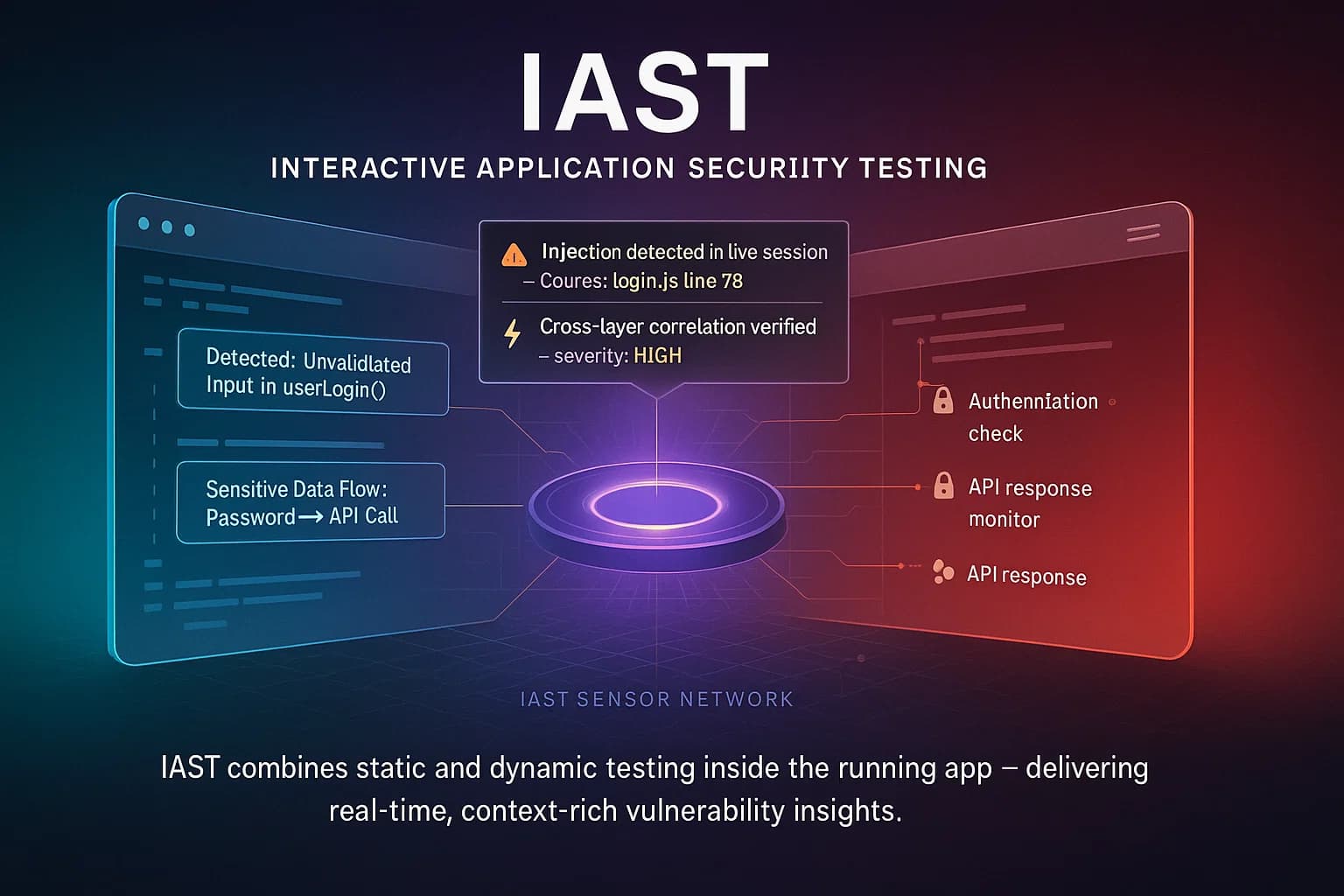
Interactive Application Security Testing IAST blends SAST and DAST. IAST tools install sensors or agents inside your app’s runtime e.g. as part of the server or test harness. As you or automated functional tests exercise the application, IAST continuously monitors dataflow and control flow within the live app. It can see both the source code execution and the HTTP requests/responses, giving it a gray box perspective.
In short, IAST acts like a smart overlay on your QA tests. As Imperva explains, IAST tools combine the two approaches: they evaluate code like SAST from inside the running app like DAST. Many teams use IAST to enrich their CI/CD pipeline for example, running an IAST scan whenever automated regression tests run, to catch issues before release.
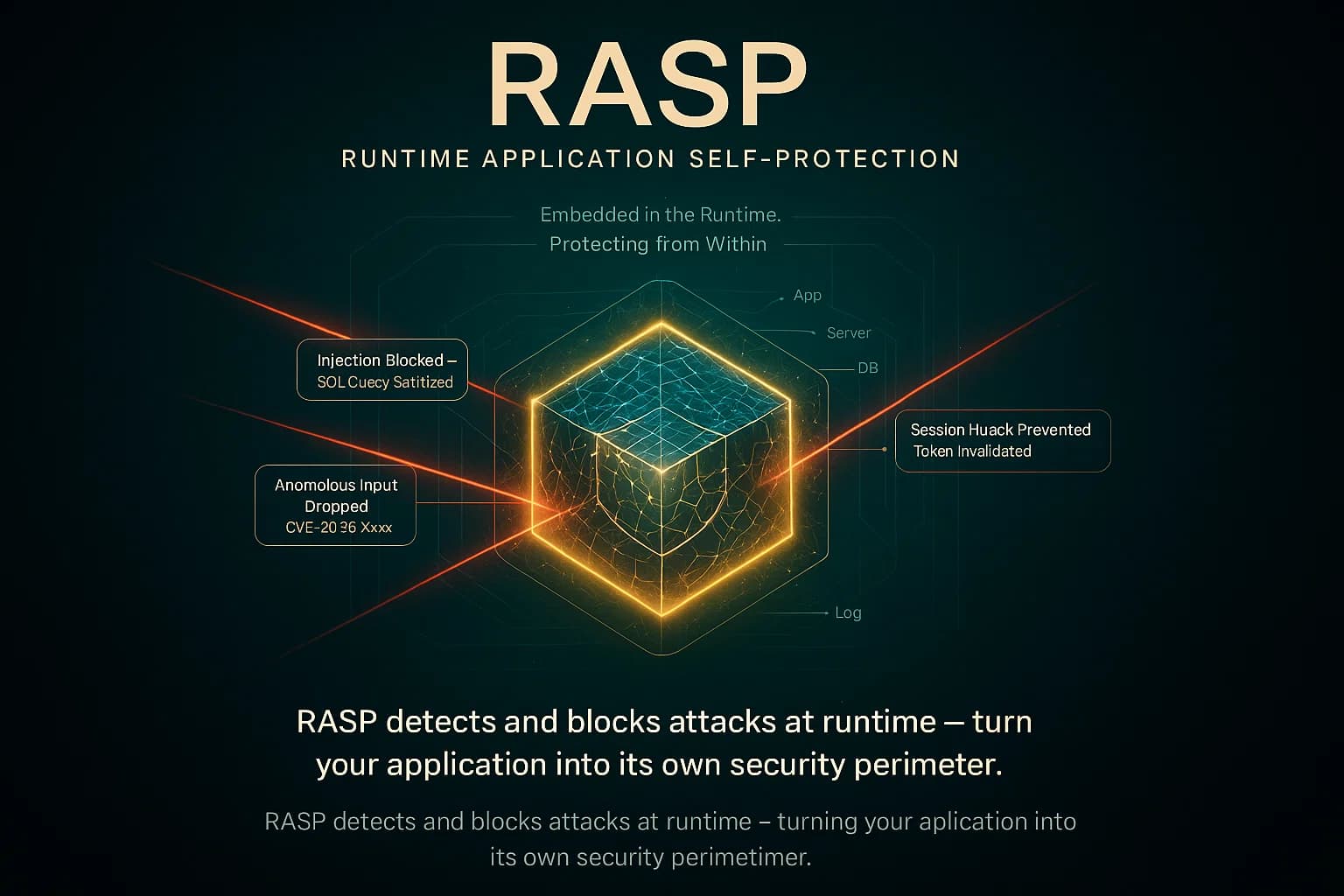
Runtime Application Self Protection RASP is not a testing tool but an in application shield. A RASP agent is embedded within the deployed app or its server environment. It continuously monitors application inputs, data flows, and behavior in real time. If an attack or exploit is detected for example, an SQL injection attempt or a malicious payload RASP can immediately block the request or terminate the session. In effect, the app becomes self protecting.
As GitHub explains, RASP is like an immune system built into the app. It monitors, detects, analyzes, and protects against malicious activity. in real time while the app is running. For example, RASP can automatically stop an SQL injection mid attack, giving your team time to patch. NIST even notes RASP monitors the program during operation for internal security faults before they become system failures. In practice, RASP is used as a last line of defense or as a stop gap for hard to fix legacy apps. It often complements a WAF: the WAF filters known bad requests at the edge, while RASP catches anything that slips through or originates internally.
Application security is no longer optional. Cyber attacks have grown more sophisticated: in 2025, many breaches start with vulnerable application code or configs. Tools like SAST/DAST/IAST/RASP help meet modern challenges: cloud native apps, microservices, and tight compliance. For instance, regulatory standards PCI DSS 4.0, HIPAA, NIST 800 218 SSDF now require secure coding practices and security testing. As noted, NIST’s SSDF framework explicitly calls for static analysis to find bugs early. The OWASP Top 10 the industry standard for web risk highlights issues injection, auth flaws, etc. that directly map to what these tools find.
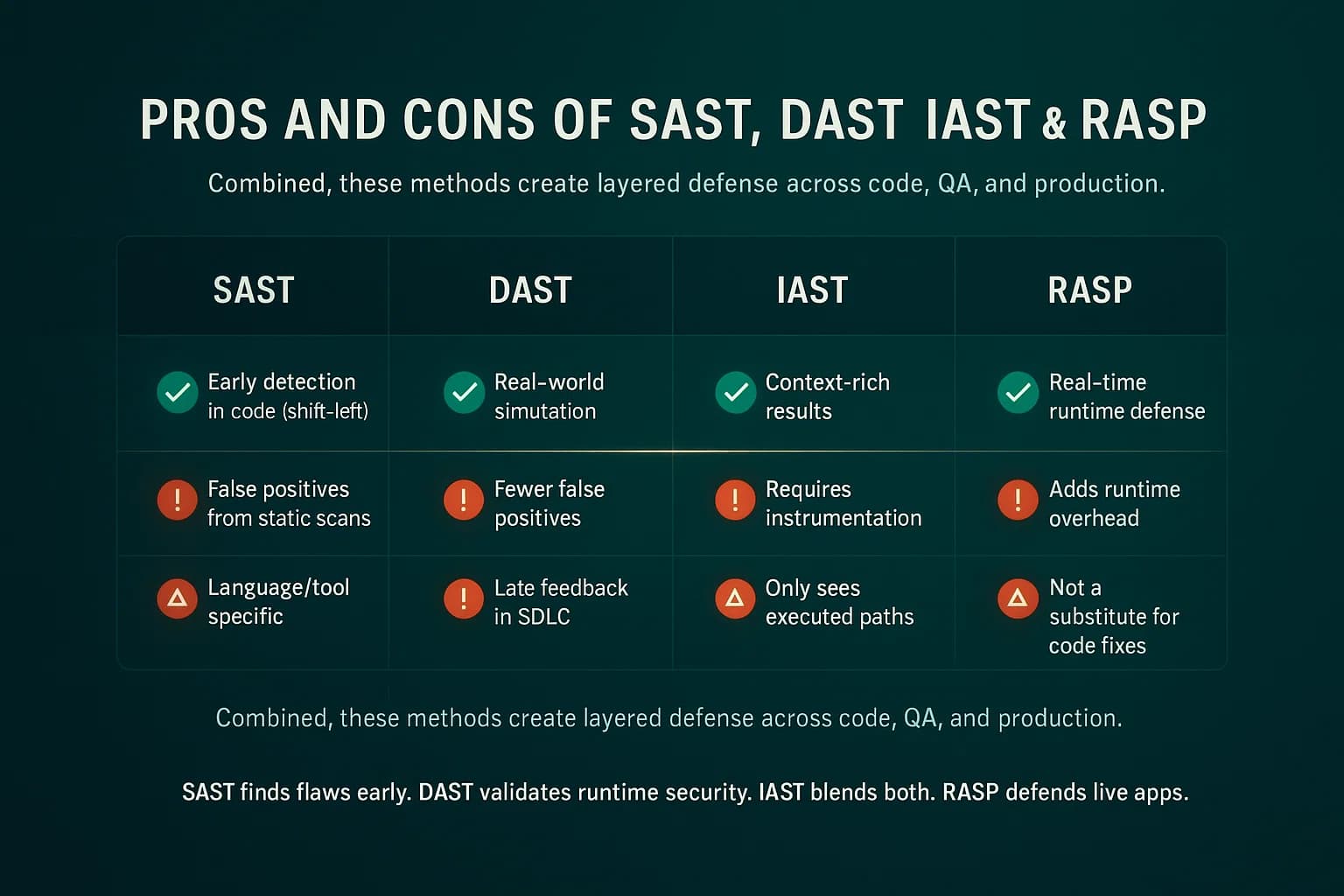
Layered security: No single tool catches everything. Combining them is the key:
Together, they align with DevSecOps: SAST and IAST integrate into Dev/CI tools, while DAST and RASP protect later stages. For example, Splunk points out you can automate SAST in CI pipelines and DAST in staging to catch flaws fast. In practice, we’ve seen organizations cut vulnerability remediation costs by using SAST early fixing bugs at $100 each instead of thousands in production and using RASP to prevent costly incidents. According to industry analysis, shifting tests earlier can yield a significant ROI and faster time to fix.
| Aspect | SAST | DAST | IAST | RASP |
|---|---|---|---|---|
| Testing style | White box static code | Black box dynamic | Gray box instrumented | Runtime defense in app |
| Code visibility | Full source/bytecode | None external only | Partial uses sensors | Full runtime context |
| SDLC stage | Early dev/CI | Late QA/pre prod | Mid test automation | Production runtime |
| Detects | Code flaws SQLi, XSS, hardcoded creds | Runtime issues config, auth flaws | Code & runtime issues only in executed flows | Active attacks/exploits blocks 0 day threats |
| False alerts | Higher no context | Lower actual behavior | Low context aware | Very low real usage |
| Examples of tools | Checkmarx, SonarQube, GitHub CodeQL | OWASP ZAP, Burp, Acunetix | Contrast Assess, Seeker, HCL AppScan IAST | Imperva RASP, Contrast Protect, Fortify AppDefender |
Each tool has its sweet spot. SAST is best at shifting left to catch coding mistakes. DAST excels at finding flaws in live apps and provides an attacker’s eye view. IAST gives high confidence with detailed code traces. RASP is unique: it doesn’t find bugs ahead of time but stops real attacks in flight.
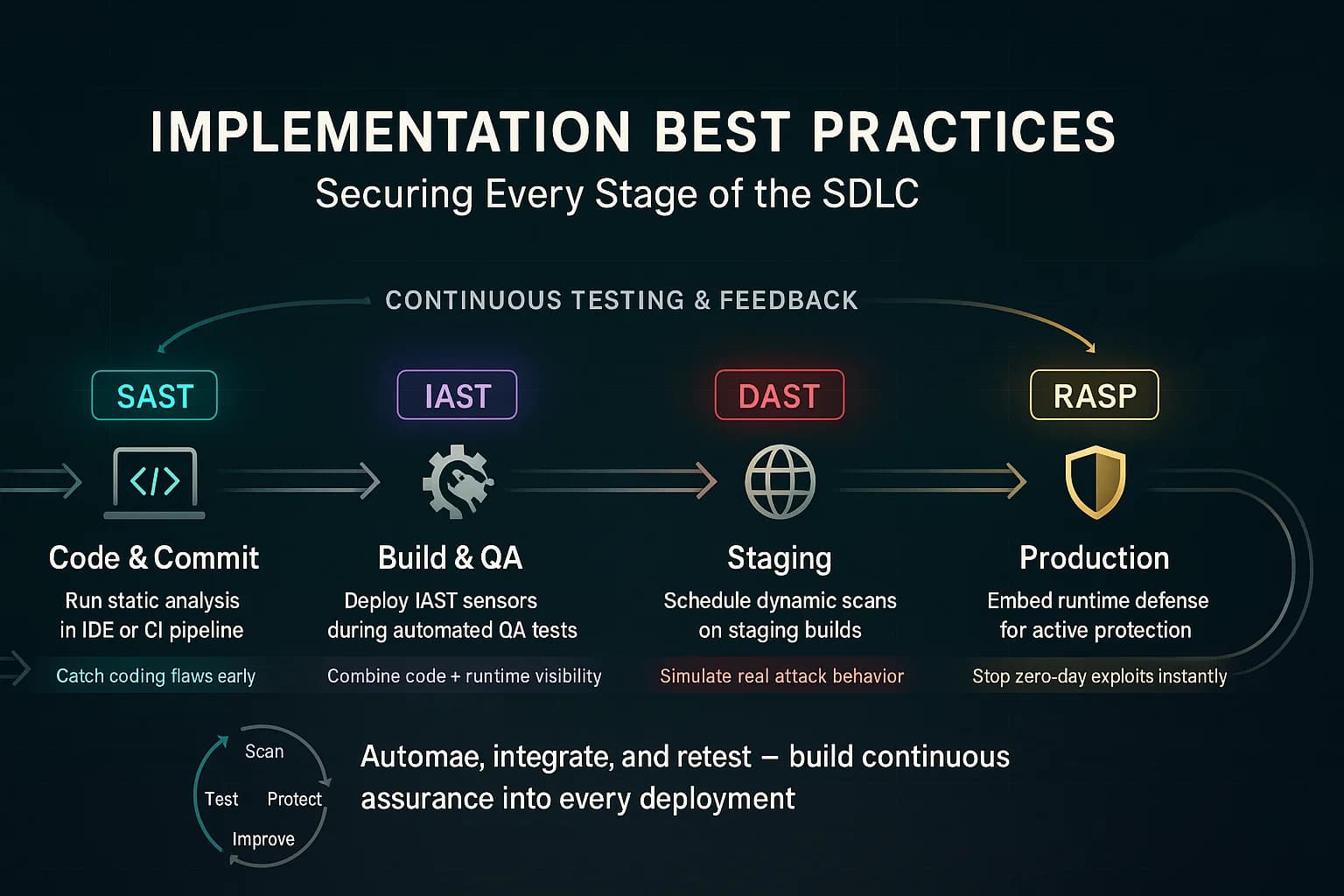
Here’s how to practically integrate these tools into your workflow:
Quick Tips:
Understanding SAST, DAST, IAST, and RASP is essential for a robust AppSec program in 2025. Each method catches different types of issues at different stages: from code review SAST to live defense RASP. By layering these tools and following best practices, you build multiple safety nets.

Ready to Strengthen Your Defenses? The threats of 2025 demand more than just awareness; they require readiness. If you’re looking to validate your security posture and build a resilient defense strategy, DeepStrike can help. Our penetration testing experts guide you through implementing SAST/DAST/IAST/RASP, and beyond.
Explore our penetration testing services internal link to see how we can uncover vulnerabilities before attackers do. Drop us a line we’re always ready to dive in.
About the Author: Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
In short, SAST scans your code for flaws before running the app white box, DAST attacks the running app to find weaknesses black box, IAST instruments the app during tests to combine both approaches, and RASP embeds in production to block real attacks at runtime. Each covers different parts of the SDLC.
Use SAST during development/CI to catch coding bugs early. Use DAST in QA or pre production to validate security in the deployed app. Use IAST during automated functional testing for deep insight when you have good test coverage. And use RASP in production as an ongoing defense against live threats.
Yes. Automated tools and RASP improve security drastically, but they complement not replace human pentesters. Penetration testing finds complex business logic or chain exploits that tools might miss. Think of SAST/DAST/IAST as continuous scanners, and pen tests as occasional red team check ups.
Both protect in real time, but at different layers. A WAF sits in front of the app, filtering HTTP requests at the network edge. RASP runs inside the application itself. This means RASP has deeper context, knows the app’s code and logic and can catch attacks that bypass or are invisible to a WAF. RASP can also block threats with very low false alarms.
Don’t rely on one tool alone, use them together. Beware of false positives common in SAST and false negatives possible in DAST. Avoid treating RASP as a silver bullet; it should not justify skipping code fixes. Also, ensure good test coverage for IAST, or it won’t see all code. Finally, keep tools up to date with the latest vulnerability patterns.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us