August 24, 2025
Updated: August 24, 2025
A 2025 guide to integrating penetration testing into DevOps pipelines using OWASP CI/CD risks and NIST SP 800-204D controls.
Mohammed Khalil

Penetration testing for DevOps is the practice of embedding automated and continuous security validation across the entire Software Development Lifecycle (SDLC). This approach augments, not replaces, human led pentests: automation covers breadth on every build, while experts probe complex business logic and chained exploits that scanners miss.
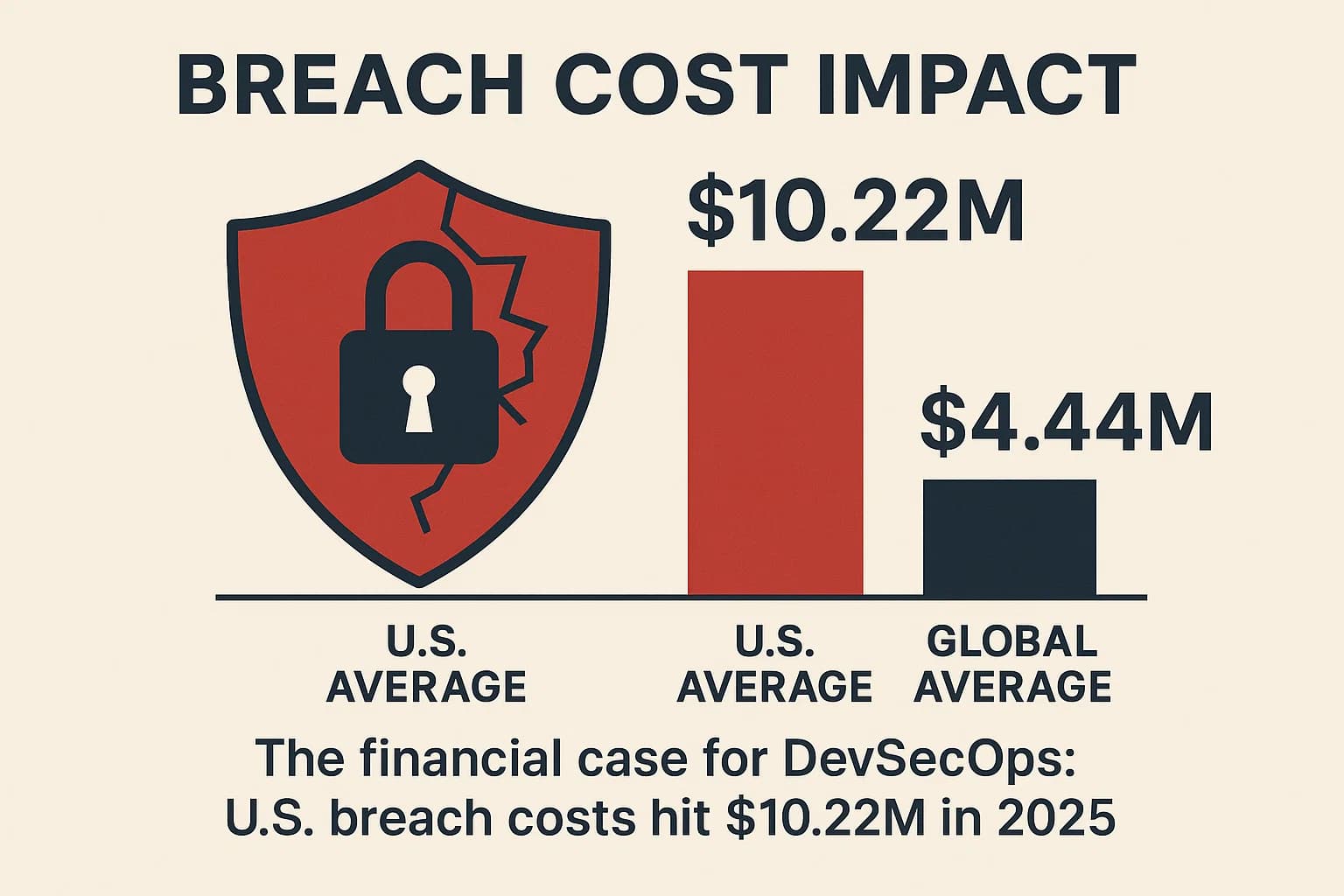
In 2025, this is non-negotiable. The CI/CD pipeline itself is a prime target. The XZ Utils upstream backdoor (CVE 2024 3094) showed how a sophisticated, patient attacker could compromise a core dependency and ripple into production systems worldwide. With breach costs in the U.S. averaging $10.22M in 2025 (versus a global average of $4.44M), proactive security is a financial necessity.
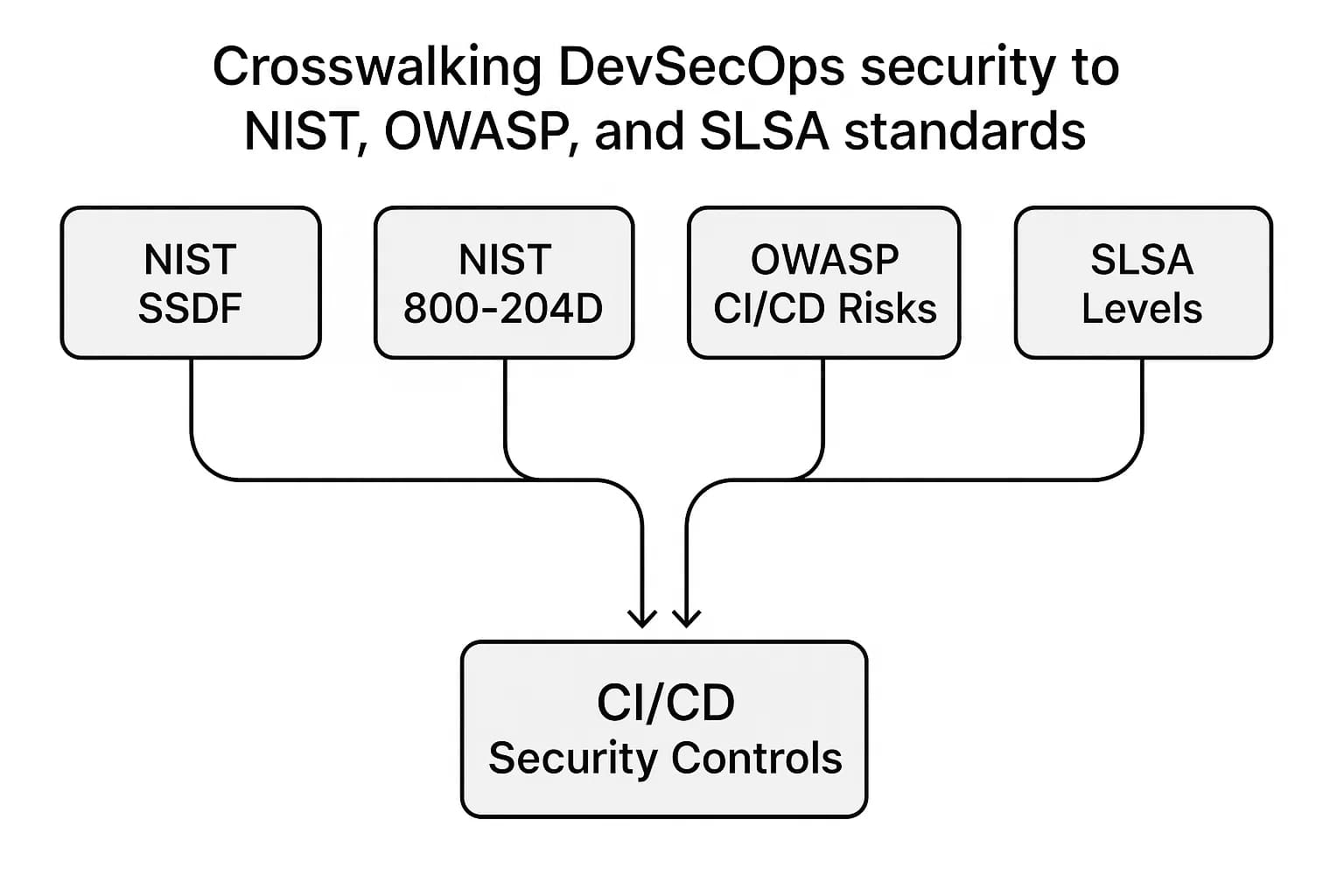
A modern DevSecOps program aligns with key industry standards that provide a battle tested roadmap for security.
You can start integrating security into your pipeline by following a clear, five step process. This checklist provides a structured way to begin shifting security left without overwhelming your development teams.
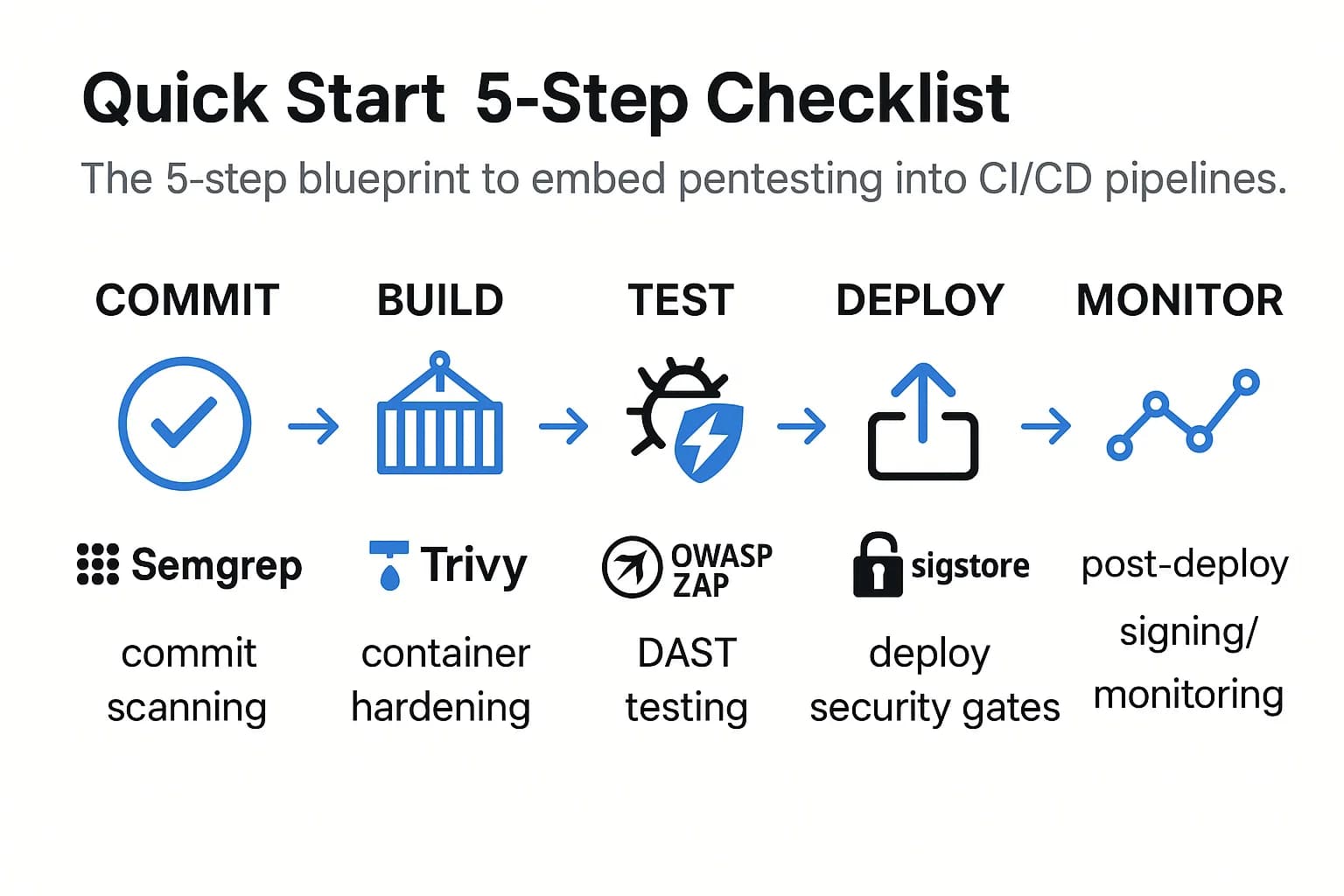
Each type of security scan plays a specific role at a different stage of the pipeline, providing a defense in depth strategy.
Other helpful entities to be aware of for a comprehensive security posture include CISA, ENISA, CERT In, MFA, and infostealer malware.
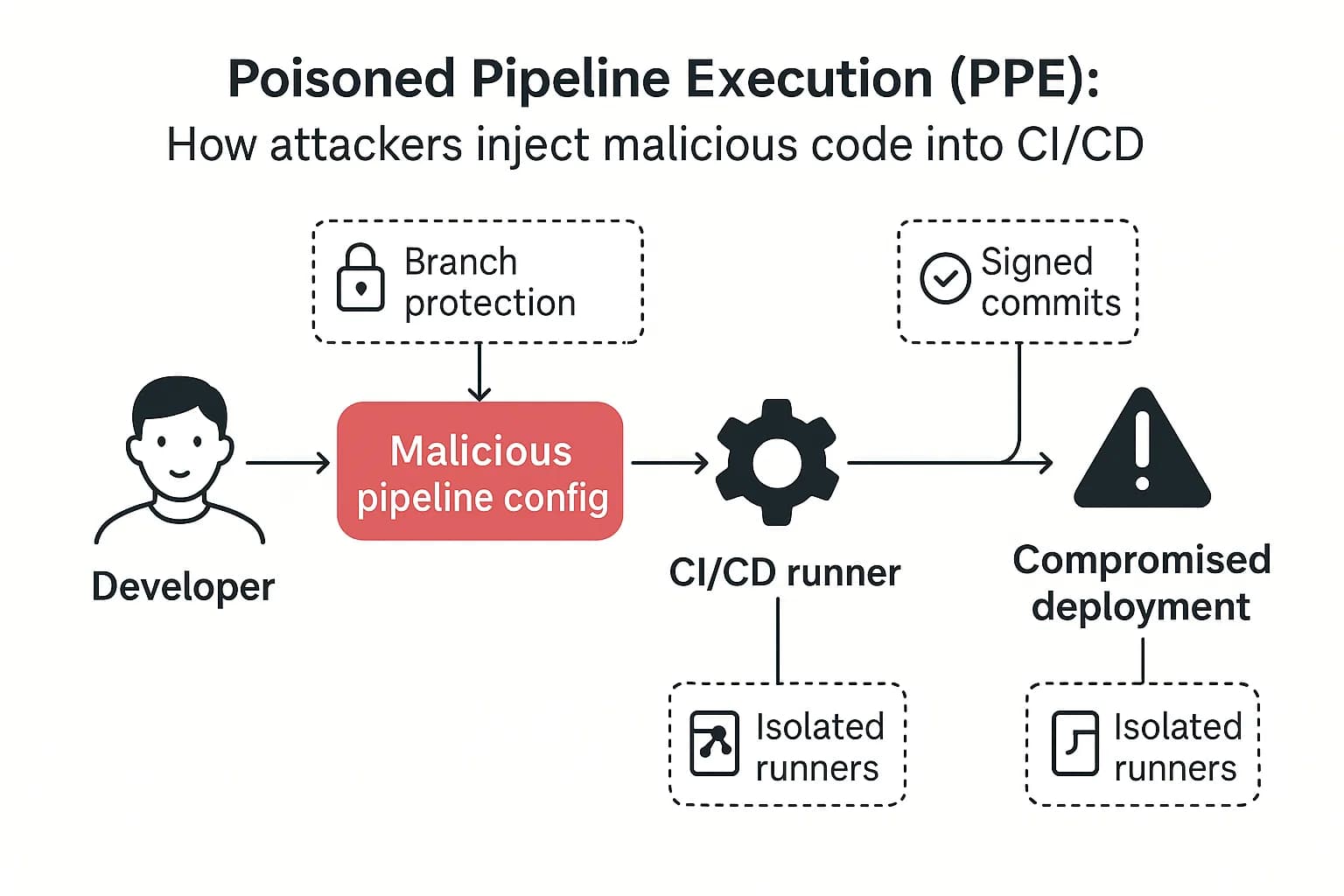
Poisoned Pipeline Execution (PPE) is an attack where malicious commands are injected into a pipeline's configuration file and run with the CI system's permissions. It's identified as CICD SEC 4 in the OWASP Top 10 CI/CD Security Risks.
A strong PPE playbook includes these countermeasures:
GitLab Enable SAST on Every Merge Request You can enable SAST with a simple template include, then enforce a gate using Merge Request approval policies.
#.gitlab-ci.yml
include:
- template: Jobs/SAST.gitlab-ci.yml
# Then, enforce approvals when scanners report High/Critical findings
# via Project Settings » Merge requests » Approvals.
# Require "Security scan to pass" for a true gate.This configuration ensures SAST runs before code is merged, and the approval policy prevents insecure code from entering your main branch.
GitHub ZAP Baseline Action as a DAST Gate This GitHub Action runs an OWASP ZAP scan against a staging URL and can be configured to fail the build if it finds vulnerabilities.
#.github/workflows/zap.yml
name: ZAP baseline
on: [push, pull_request]
jobs:
zap:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: ZAP baseline scan
uses: zaproxy/action-baseline@v0.14.0
with:
target: https://staging.example.com
fail_action: true
rules_file_name: '.zap/rules.tsv' # Ignore tuned false positive rules
cmd_options: '-a' # Include active/passive checksThe fail_action: true parameter is what turns this scan into a practical security gate.
Cryptographically signing your artifacts provides a verifiable guarantee of their integrity. Sigstore's Cosign tool enables "keyless" signing, which is ideal for automated CI/CD environments.
# Build & push image first, then:
cosign sign --yes $IMAGE_DIGEST
trivy image --format spdx-json -o sbom.json $IMAGE
cosign attest --yes --predicate sbom.json --type spdx $IMAGE_DIGESTThis workflow signs a container image digest and attaches an SBOM as a verifiable attestation, using short lived certificates instead of manually managed keys.
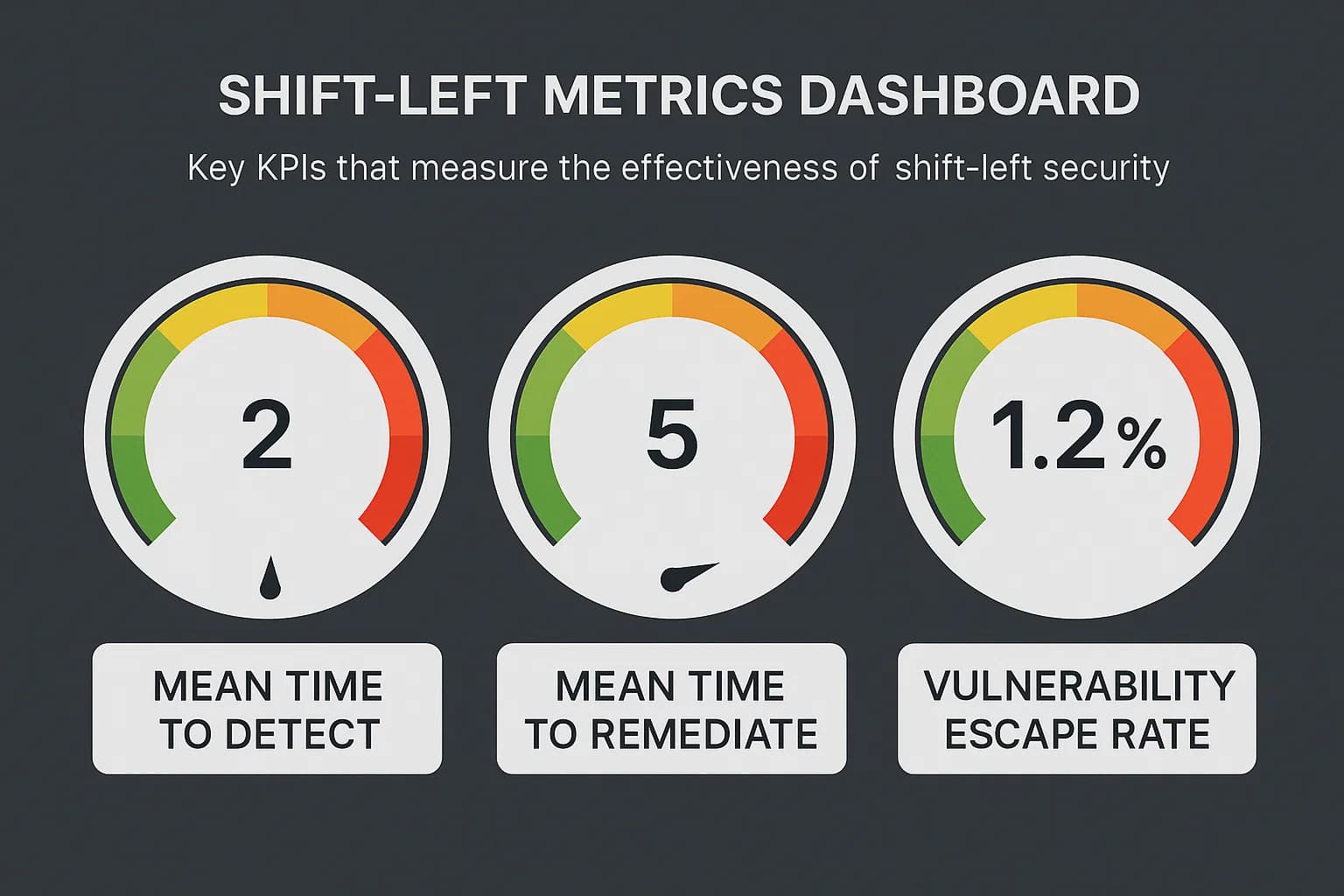
To demonstrate the ROI of your DevSecOps program, track these key metrics:
Key KPI Definitions

Yes. Automate routine SAST/DAST/SCA scans on each change and schedule human led pentests for high risk releases. This aligns with NIST SP 800 204D guidance for CI/CD supply chain controls.
Your pipeline should align with NIST SSDF (SP 800 218) for process maturity, NIST SP 800 204D for supply chain controls, OWASP Top 10 CI/CD for pipeline threats, and aim for SLSA Level 2 for provenance and signing.
Tune your rulesets. Start by only blocking on High/Critical findings. Use per-repository baseline or ignore lists (e.g., ZAP's rules.tsv or Semgrep's --baseline flag) to manage accepted risks and false positives.
Follow the OAuth 2.0 Security Best Current Practice and ensure your DAST tool is configured to handle token based authentication flows.
Integrating penetration testing into DevOps is the definitive way to build secure software at modern speeds. It’s a strategic shift from reactive, end of cycle security to a proactive, continuous, and developer centric model. By leveraging automation, aligning with modern standards like NIST SSDF and SLSA, and fostering a culture of shared responsibility, you can transform your CI/CD pipeline into your strongest security asset.
The journey starts with small, iterative steps: add one scanner, tune the results, and automate a single gate. Over time, these incremental improvements compound to create a resilient, secure, and efficient software delivery process that doesn't just meet compliance checkboxes for standards like the PCI DSS 11.3 penetration testing guide 2025 it builds trust with every release.

Ready to Strengthen Your Defenses?
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us