August 9, 2025
Updated: August 9, 2025
A deep dive into the strengths, weaknesses, and best use cases for manual and automated penetration testing and why 2025 demands a hybrid approach.
Mohammed Khalil

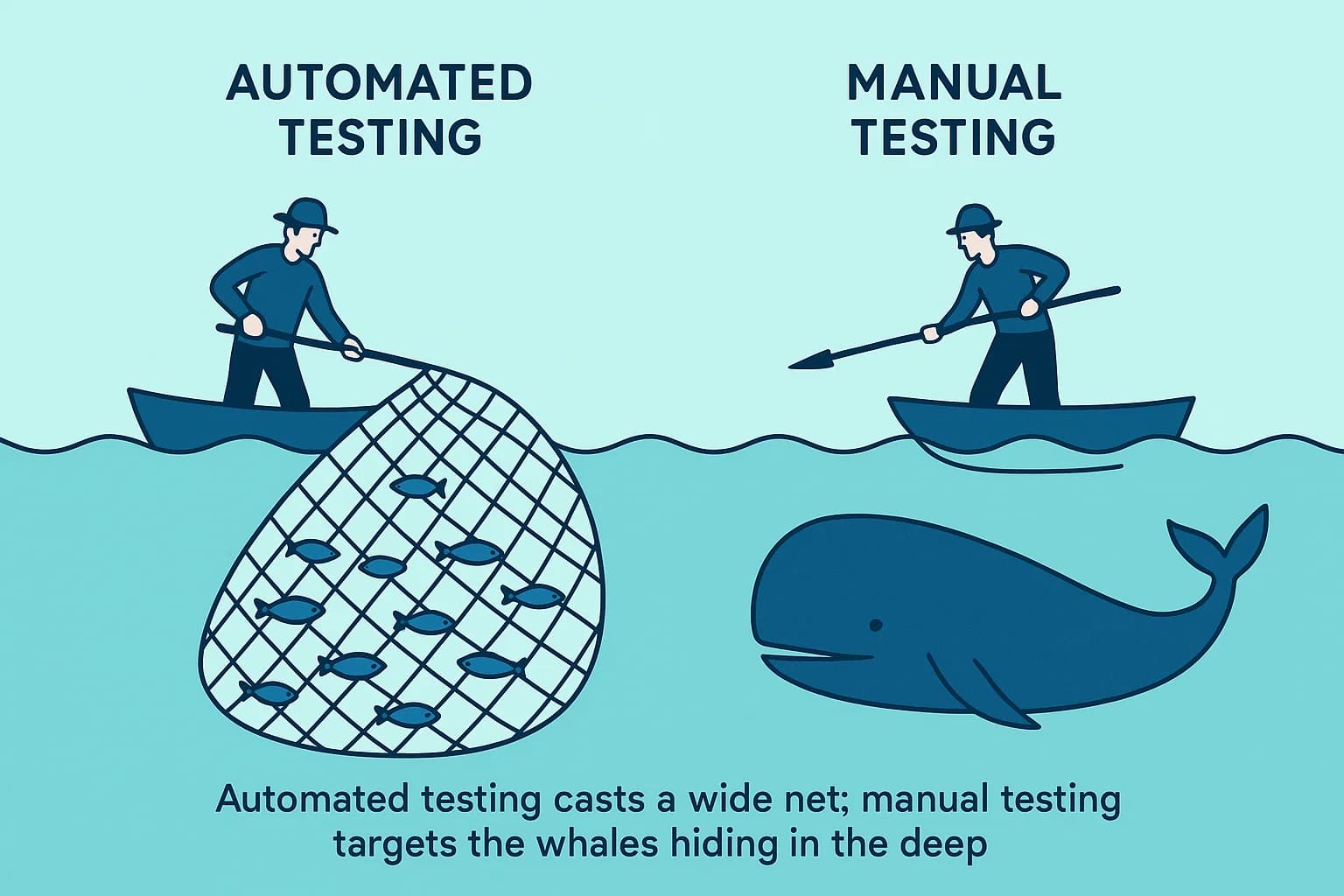
Let's start with a sobering fact. The 2025 Verizon Data Breach Investigations Report (DBIR) revealed a staggering 180% increase in attackers exploiting vulnerabilities to gain initial access. In this landscape, simply "finding bugs" isn't enough. The real goal is to stop attackers before they get a foothold, and that requires a smarter approach to security testing.
The choice between manual vs automated penetration testing isn't about picking a "better" option; it's about understanding you're choosing between two different tools for two very different jobs. One is a wide net designed to catch common fish; the other is a spear for hunting the whales hiding in the deep.
Why does this distinction matter more than ever? In an era of complex, multi-layered cloud applications and emerging AI cybersecurity threats in 2025, relying on a single testing method is a critical mistake. Understanding the strengths and weaknesses of each approach is crucial for effective risk management, smart budget allocation, and achieving meaningful compliance not just checking a box.
The biggest misconception in cybersecurity testing is confusing automated scanning with true penetration testing. Let's clear that up right now.
At its core, manual penetration testing is a human led, objective driven engagement where a skilled ethical hacker simulates a real world attack to uncover and exploit vulnerabilities. It's not just about finding a flaw; it's about demonstrating its real world impact. This involves chaining exploits, pivoting through systems, and thinking creatively like an adversary would. This is precisely what the National Institute of Standards and Technology (NIST) defines as mimicking real world attacks to circumvent security features.
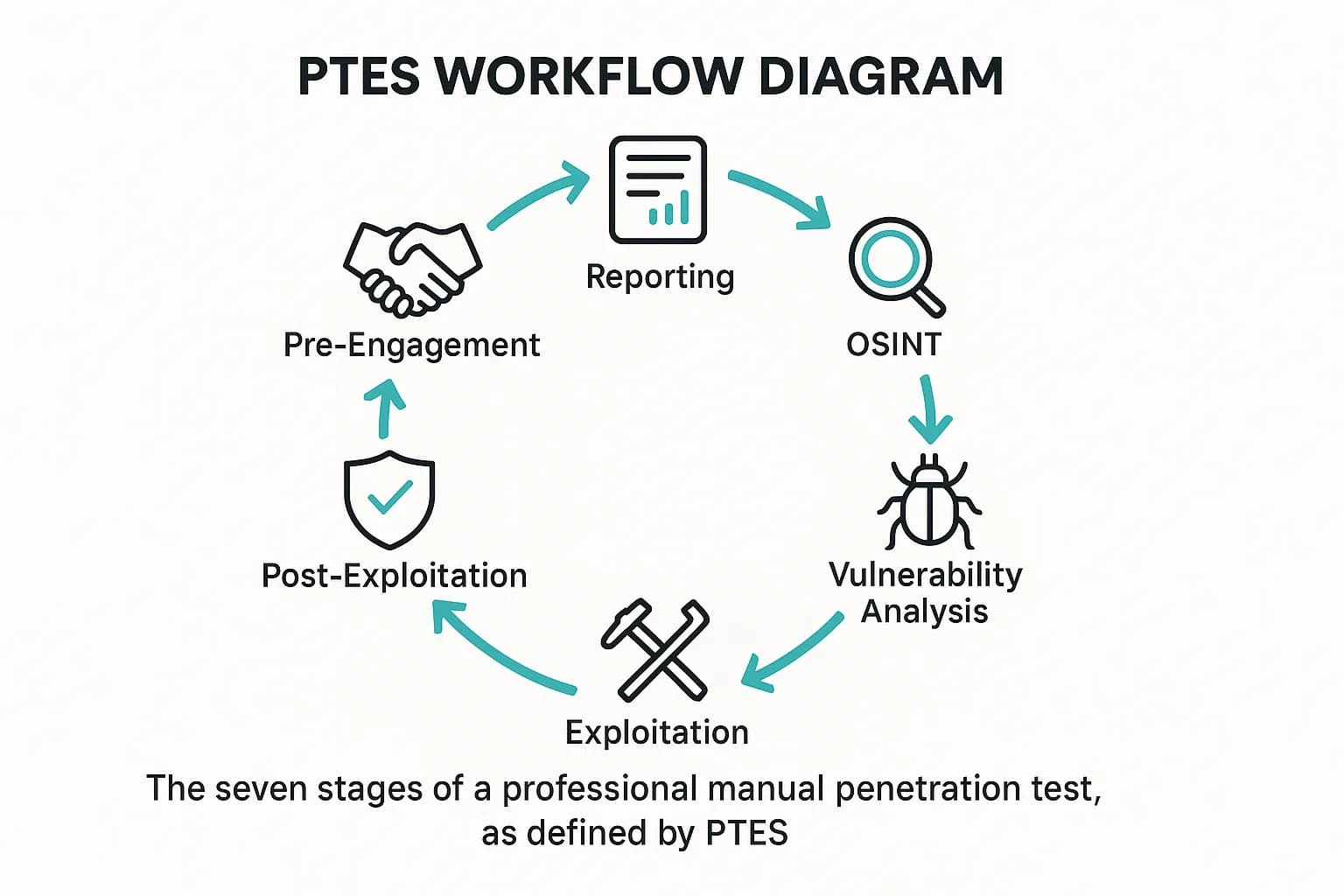
This isn't random, chaotic hacking. Professional engagements follow structured frameworks to ensure the assessment is comprehensive, methodical, and repeatable. The most respected of these is the Penetration Testing Execution Standard (PTES), which outlines seven distinct stages:
This structured approach is what separates professional from ad hoc efforts.
Automated penetration testing is the use of specialized software to rapidly scan for known security weaknesses and misconfigurations across a wide range of systems. These tools operate by comparing the state of a target system against a massive, constantly updated database of predefined vulnerability signatures, think outdated software versions, common configuration errors, or known Common Vulnerabilities and Exposures (CVEs).
Here’s the deal, though: the term "automated penetration testing" is often a marketing misnomer. A true penetration test, by definition, involves attempting to exploit vulnerabilities to achieve a specific objective, which requires context and creativity. Most tools marketed as "automated pentesting" platforms are actually advanced vulnerability scanners with some limited, scripted exploitation capabilities. They check for signatures; they don't model threats or adapt their strategy based on what they find.
This confusion is dangerous. It often leads organizations to purchase a scanning tool under the impression that they have fulfilled a true pentesting requirement, such as for a PCI DSS 11.3 penetration testing guide 2025. This creates a false sense of security, leaving them exposed to the very threats they thought they were protected against. If a human expert isn't validating findings and attempting to chain them together, it’s not a true penetration test.
This brings us to a crucial distinction. A are not the same thing, and using the terms interchangeably is a recipe for disaster.
Relying on a vulnerability scan when you need a penetration test for example, to meet SOC 2 penetration testing requirements 2025 or to qualify for cyber insurance eligibility can lead to compliance failures and, worse, unmitigated critical risks.
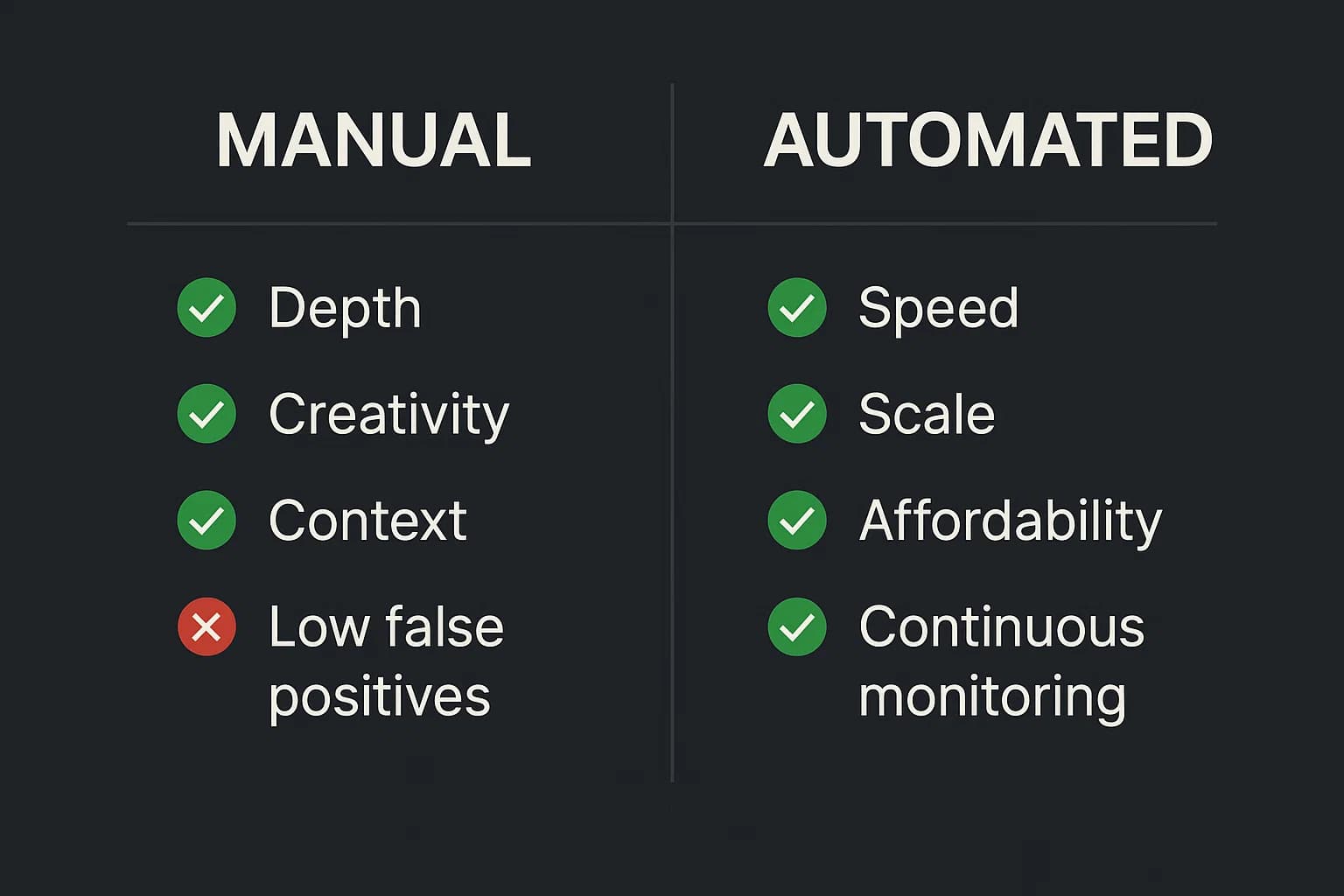
Let's break down the practical pros and cons of each approach to help you decide which is right for your situation.
The Case for Manual Testing: Depth, Accuracy, and Real World Insight
The primary advantage of manual testing is the human brain. A skilled tester brings creativity, intuition, and contextual awareness that no tool can replicate.
The Limitations of Manual Testing: Cost, Speed, and Scale
Despite its strengths, manual testing isn't a silver bullet. It has practical limitations.
The Power of Automated Testing: Unmatched Speed and Breadth
Where manual testing is deep, automated testing is wide. Its power lies in its efficiency and scale.
The Blind Spots of Automated Testing: False Positives and Lack of Context
The greatest strength of automation, its reliance on predefined rules is also its greatest weakness.
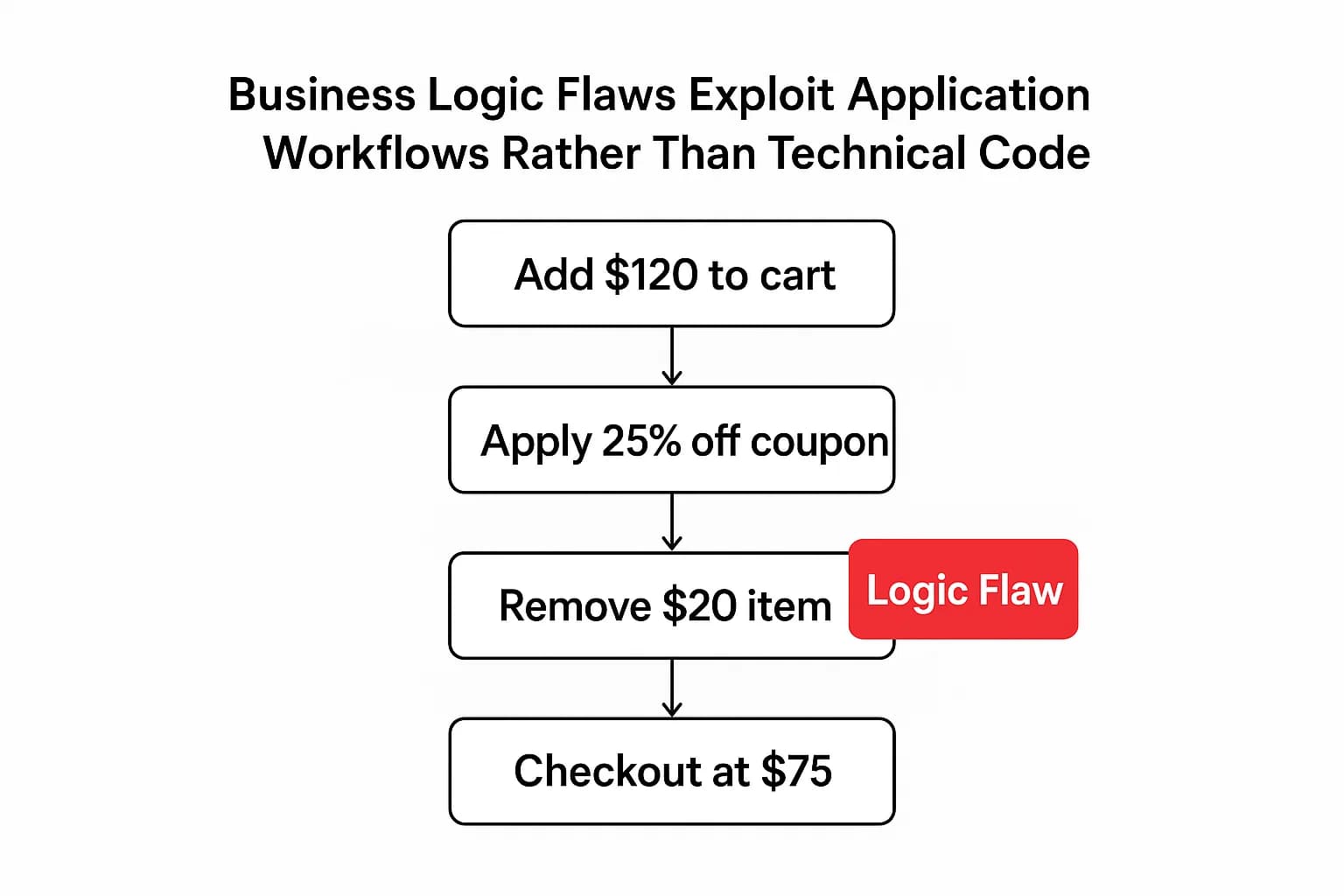
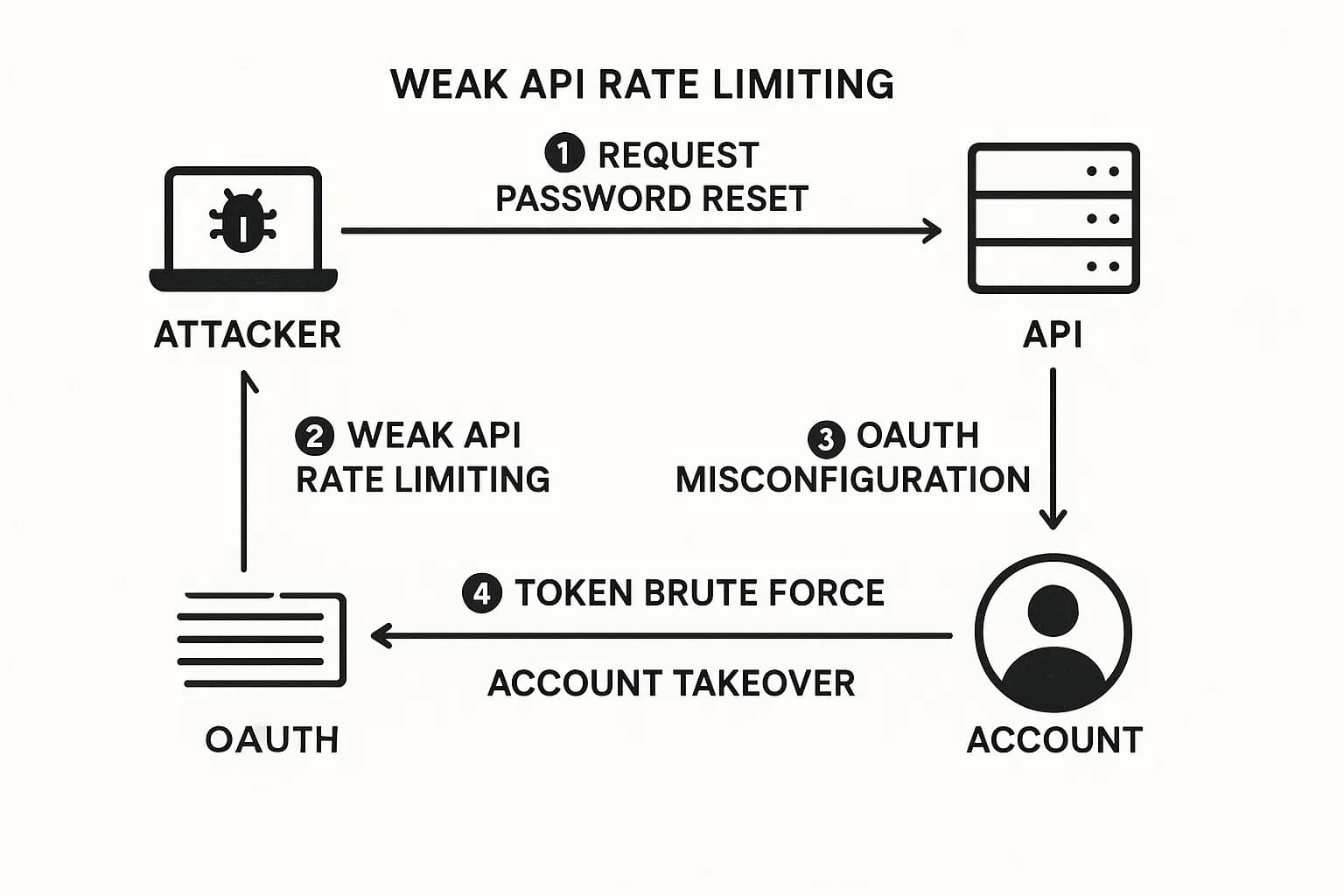
This lack of context is most apparent when it comes to business logic flaws. These are vulnerabilities not in the technical code itself, but in the rules and workflows of an application. The application works exactly as it was coded to, but its design allows for unintended, harmful outcomes that an attacker can exploit.
Here’s a real world example: an e-commerce site offers a "25% off orders over $100" coupon. An attacker adds $120 worth of items to their cart, applies the coupon, and the price drops to $90. Then, they remove a $20 item from the cart. The system fails to re-validate the coupon's conditions, and the attacker checks out, paying just $75 for $100 worth of goods. This is a flaw in the process, not a technical bug a scanner could ever find. It's a type of flaw that can be exploited through techniques like those used in.
This is why business logic flaws represent such a significant risk. They attack the very core of a company's unique processes and value propositions. A company's competitive advantage often lies in its proprietary logic, a unique pricing engine, a complex user permission model, and a specific transaction workflow. Automated scanners are designed to find common, generic vulnerabilities like those in the OWASP Top 10 across all applications. By definition, they cannot understand the unique, specific business context of an individual application.
An attacker using manual techniques can therefore target the heart of a business's operations, causing financial or reputational damage that is disproportionately high compared to a generic technical bug. For any business with custom, critical applications, relying solely on automated scanning is a dangerous oversight, as it leaves their most valuable digital assets completely untested for this entire class of threat. This is how many real world attacks, like those detailed in our Real world account takeover case study, are carried out.
Understanding the theory is one thing; putting it into practice is another. Here’s a look at the tools we actually use and a guide to help you choose the right approach.
Manual Testing Arsenal: The Craftsman's Tools
A manual pentester uses a suite of tools not as a crutch, but as an extension of their own expertise. The workflow often looks like this:
Automated Scanning Platforms: The Dragnet
Automated tools are designed for speed and breadth, casting a wide net to catch common issues.
The right choice depends entirely on your objective.
Choose Manual Testing For...
Choose Automated Testing For...
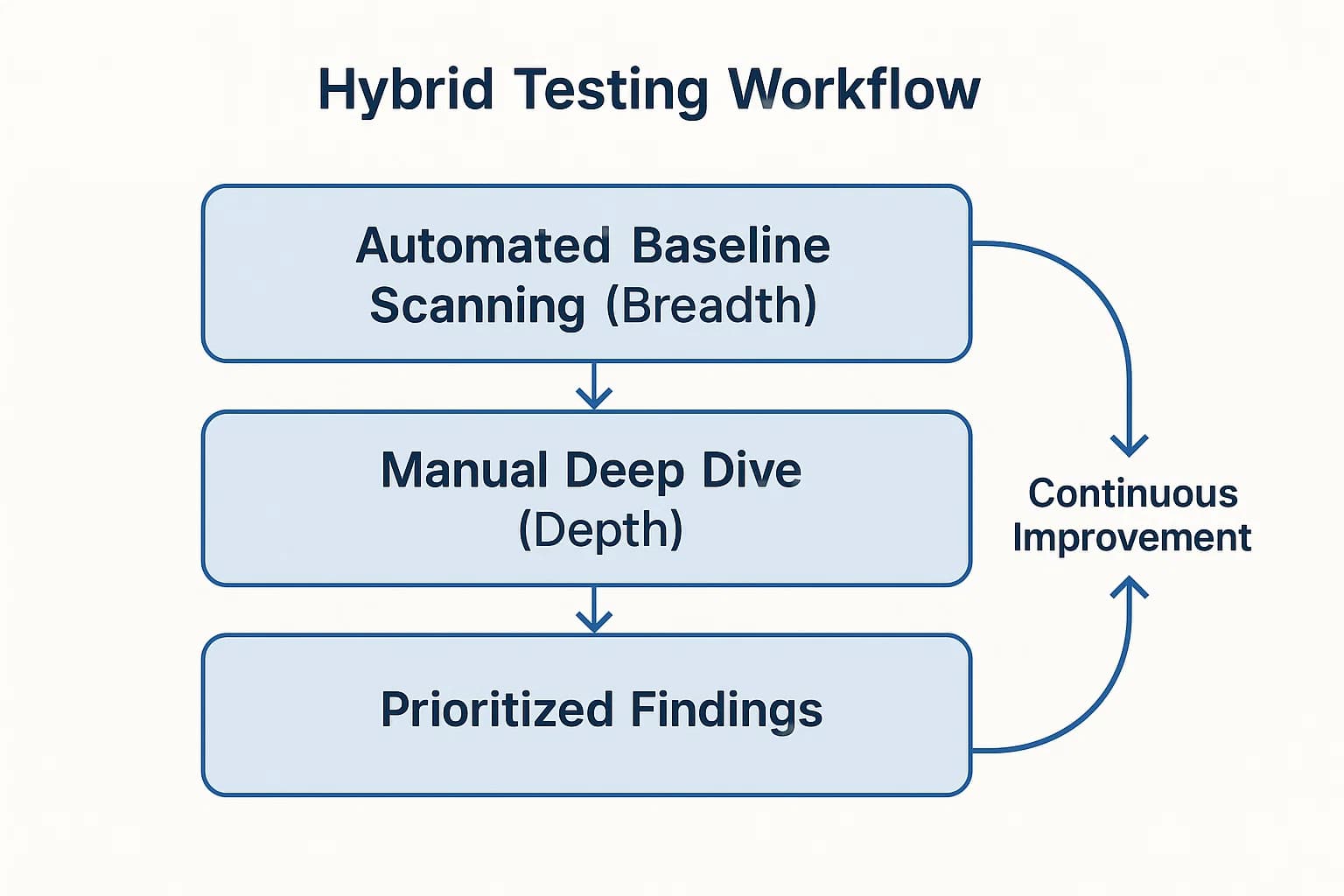
The "manual vs automated" debate is ultimately a false dichotomy. The modern, resilient organization doesn't choose one or the other; it strategically integrates both into a hybrid model.
The goal of a hybrid strategy is to create a continuous feedback loop. You use automation for its breadth and frequency, and you use manual testing for its depth and validation. Crucially, the findings from manual tests should be used to create custom rules and refine your automated scans, making the entire program smarter over time. A growing trend in this space is the adoption of Penetration Testing as a Service (PTaaS) platforms, which aim to blend ongoing automated scanning with on demand access to human experts, though they still cannot fully replace the deep, creative analysis of a dedicated manual engagement.
How To: A Step by Step Guide to a Hybrid Penetration Test
Here’s how a practical hybrid engagement works:
Real World Case Insight: Securing a Cloud Native App with a Hybrid Model
Consider a fintech company deploying a new payment application on AWS, built with microservices and numerous APIs.
How This Approach Helps with Cyber Insurance and Compliance
In 2025, securing penetration testing for cyber insurance eligibility is getting tougher. Underwriters are no longer satisfied with a clean automated scan report. They want to see evidence of rigorous, manual testing that validates the effectiveness of security controls against realistic, modern attack scenarios. A hybrid testing report, which shows both broad automated coverage and deep manual validation, provides exactly the evidence they need. This same principle applies to any Compliance focused penetration testing engagement.
What is the main difference between manual and automated penetration testing?
The main difference is the "who" and the "how." Automated testing uses software tools to quickly scan for a large number of known vulnerabilities based on predefined signatures. Manual testing uses a skilled human expert who leverages creativity, context, and intuition to find unknown and complex vulnerabilities, like business logic flaws, that tools can't detect.
Is automated penetration testing enough for PCI DSS compliance?
No. While automated scanning is a part of PCI DSS, Requirement 11.3 explicitly calls for penetration testing that includes manual validation. Testers must manually verify that vulnerabilities are exploitable and test application and network layers for flaws that automated tools are known to miss. Relying solely on automation will result in a compliance failure.
How much does penetration testing cost?
The cost varies dramatically. Automated scanning tools can range from a few hundred to a few thousand dollars per month. Manual penetration tests are priced based on scope and complexity, typically ranging from $5,000 for a very small application to over $100,000 for a large, complex enterprise environment.
Can a vulnerability scan replace a penetration test?
Absolutely not. A vulnerability scan identifies potential weaknesses. A penetration test confirms if they are exploitable and determines the potential business impact. They are complementary security activities, not interchangeable ones. A scan gives you a list of possibilities; a pentest gives you a list of certainties.
How often should we conduct penetration testing?
Best practice is to conduct a manual penetration test at least annually, and always after any significant changes to your applications or infrastructure. Automated vulnerability scanning should be performed much more frequently ideally on a continuous basis within a CI/CD pipeline, or at least weekly or monthly.
What's the difference between black box vs white box testing?
It refers to the level of knowledge given to the tester. In black box vs white box testing explained, black box means the tester has no prior knowledge of the system, just like an external attacker. White box means the tester has full knowledge, including access to source code and architecture diagrams. Gray box is in the middle, where the tester has some limited knowledge, like user level credentials.
Why can't automated scanners find business logic flaws?
Because business logic is unique to each application's purpose and workflows. Automated scanners rely on universal signatures to find common technical bugs (e.g., a specific pattern indicating an SQL injection). They lack the contextual understanding to recognize that a sequence of valid actions in a custom checkout process is actually a flaw that can be abused.
The "manual vs automated" debate is outdated. The modern, resilient organization doesn't choose one or the other; it strategically integrates both. Automation provides the constant vigilance and scale needed to manage the high volume of common threats that make up the bulk of today's attacks. Manual testing provides the critical, deep insight needed to find the unique, high impact flaws that automated tools will forever miss the ones that can bring a business to its knees.
Your security posture is only as strong as the sum of its parts. In 2025, that means combining the relentless breadth of a machine with the insightful depth of a human mind. Neglecting either leaves a critical gap for attackers to exploit.
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us