November 5, 2025
Updated: November 5, 2025
Discover how software testing ensures quality while security testing defends against real-world cyberattacks. Learn how SAST, DAST, SCA, and penetration testing strengthen DevSecOps pipelines.
Mohammed Khalil


Security testing examines software with an attacker’s perspective, trying unexpected or malicious inputs to reveal vulnerabilities, weak authentication, misconfigurations, injection flaws, etc.. This contrasts with normal functional testing, which checks features work for honest users e.g. can the user complete this task?. In short, functional tests verify correctness does the login work?, while security tests ask can an attacker break it?. Code Intelligence notes that security testing is a form of non functional testing it validates how the system handles malicious or unexpected scenarios. For example, a login form may pass functional tests but still be vulnerable to SQL injection or session hijacking, which only security tests catch.
By design, security testing assumes an adversary. NIST defines penetration testing a form of security testing as security testing in which assessors mimic real world attacks to identify methods for circumventing the security features of an application, system, or network. Security tests target the CIA triad Confidentiality, Integrity, Availability rather than just user facing requirements. This helps organizations protect sensitive data and prevent breaches. As one expert puts it: Security testing is essential for software that processes confidential data to prevent system intrusion by attackers.
Because security testing goes beyond typical QA, it complements functional testing. Both are needed: functional tests ensure features work as expected, and security tests ensure those features can’t be abused. In modern DevSecOps, teams shift left by automating both types of tests early in development.

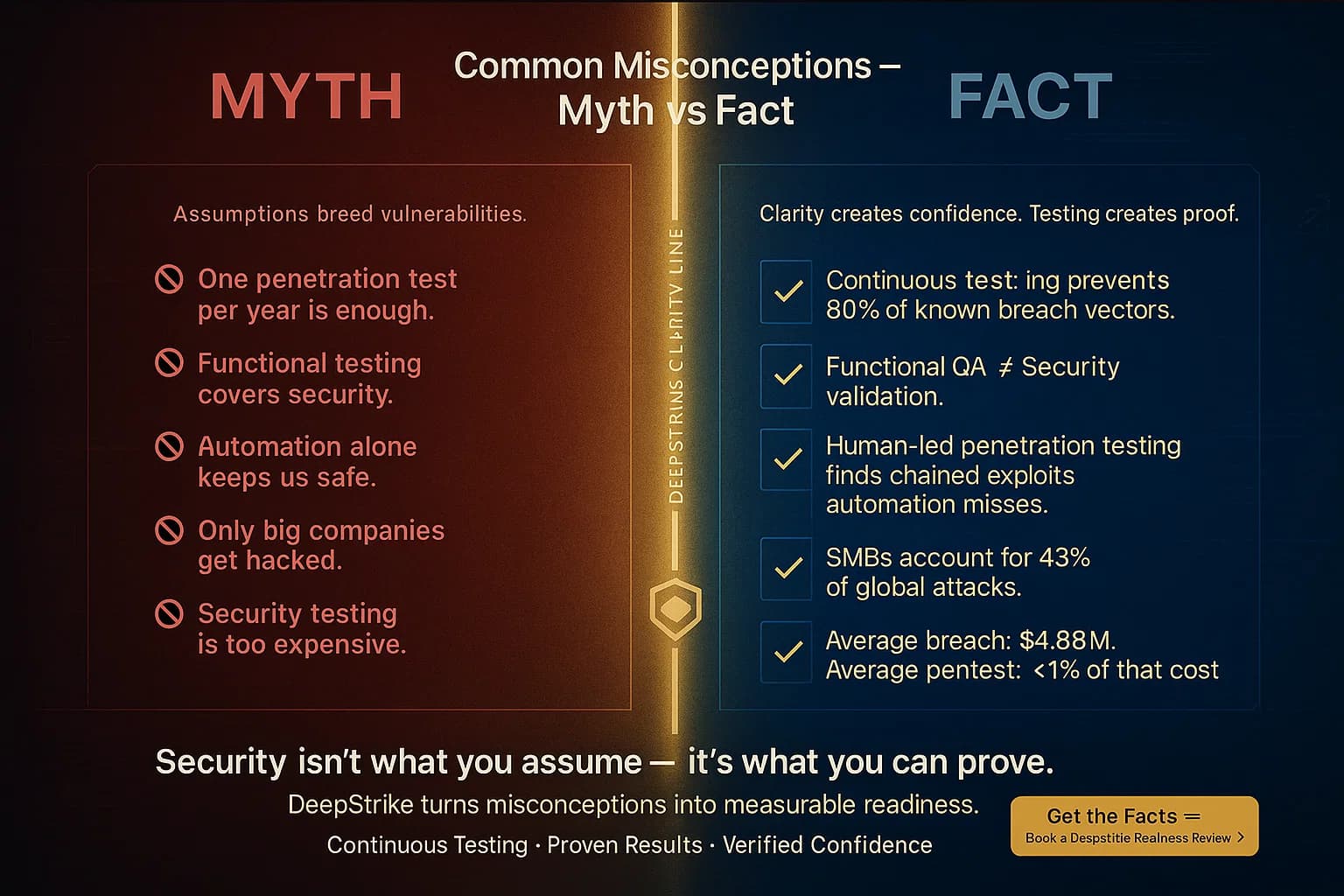
The stakes of security testing have never been higher. Cyberattacks are skyrocketing in scope and cost. IBM reports the average data breach cost reached $4.88 million in 2024, a record high, and global cybercrime damage is projected to top $10 trillion by 2025. Ransomware and data breaches hit a record number of organizations in 2023. Small and medium businesses are especially vulnerable: about 60% of SMBs now list cyber risk phishing, ransomware, etc. as a top concern. In short, no one is immune to cyberthreats, and reactive fixes post breach are very expensive.
Proactive security testing helps prevent or mitigate these issues. By finding bugs and misconfigurations before attackers do, organizations save money and reputational damage. Studies consistently show catching a security defect early during development or testing is far cheaper than after release or breach. For example, one industry analysis notes that a critical flaw is orders of magnitude more expensive to fix once exploited or in production often 10- 100x the cost.
Regulations and standards also drive demand for security testing. Frameworks like PCI DSS, ISO 27001, HIPAA, NIST’s SSDF, and others explicitly require regular penetration tests and vulnerability assessments. For instance, PCI DSS mandates yearly or after major change pen tests Requirement 11.3, and NIST guidelines encourage continuous automated analysis. Integrating security tests ensures compliance and avoids fines or audit failures.
Finally, real breaches underscore the need. Major companies like Adobe, Sony, and even nation wide services have been compromised through simple security oversights. Post incident, these organizations doubled down on security testing e.g. regular pentests, automated scanning to regain trust and harden their defenses. Today’s interconnected apps cloud, APIs, mobile expand the attack surface. Security testing uncovers hidden risks from broken access controls to insecure APIs so teams can fix them before attackers do.

Security testing encompasses a variety of techniques, each with a different focus. The most common methods include:
| Testing Method | How It Works | When to Use | Examples |
|---|---|---|---|
| SAST Static Analysis | Scans source code/bytecode for insecure patterns. | Early/commit builds | SonarQube, Checkmarx |
| DAST Dynamic Analysis | Injects attacks into live app to find runtime flaws. | QA/staging post build | OWASP ZAP, Burp Suite |
| SCA Dependency Scanning | Checks 3rd party libraries for known CVEs. | Build/deploy time | Snyk, Dependabot |
| Penetration Testing Manual | Ethical hackers simulate real attacks network/app. | End of cycle/annually | Metasploit, custom scripts |
| Vulnerability Scanning | Automated scanning of systems for known weaknesses. | Continuous/integration | Nessus, Qualys |
For example, SAST can catch a hard coded database password or missing input sanitization in code, while DAST would catch a misconfigured login page or missing HTTP security headers during runtime. A penetration test might chain several minor issues weak admin password + outdated software + missing patches to demonstrate a full breach that automated tools alone missed.
It’s important to mix methods. OWASP advises adding security tests throughout the pipeline: use SAST/SCA in CI, run DAST against test deployments, and schedule manual pentests or bug bounties periodically. This layered approach ensures fewer gaps.
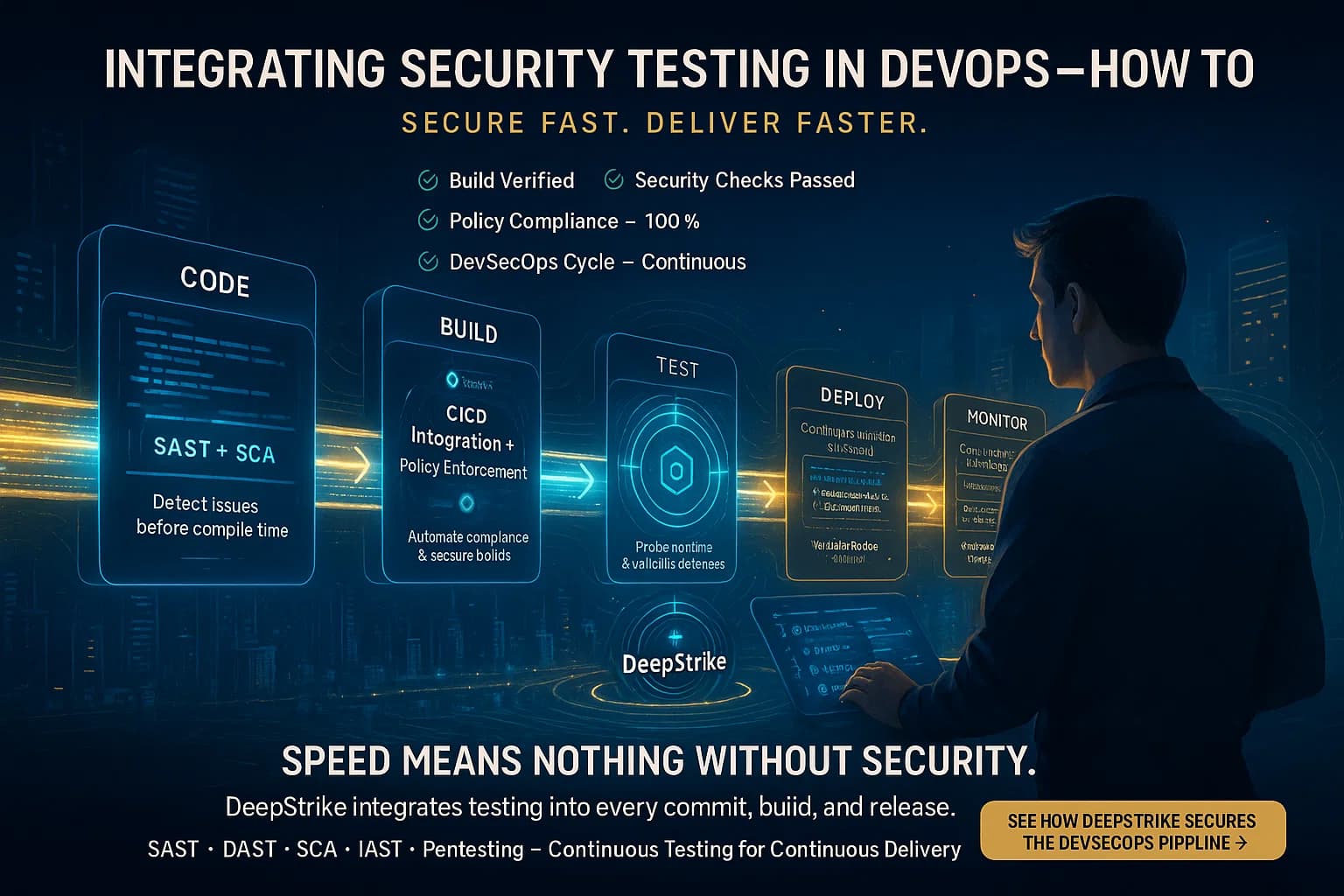
A robust software process includes security at every step. Here’s a step by step guide to embedding security testing in your SDLC:
Checklist:
By making security testing a habit not a one off, teams catch vulnerabilities early and build more secure software with less firefighting later.

Penetration tests come in two flavors:
Both are essential. OWASP summarizes: External pentests tell you if bad guys can get in. Internal pentests show you how bad it could get if they do.. Together, they give a full picture of your security posture.
For example, DeepStrike’s guide on internal vs external testing notes that internal testing reveals issues like weak user privileges or file share access, while external testing finds open ports and vulnerable web apps. The schedule often includes an annual external pentest and an internal pentest sometimes mid year but needs vary by business.

Overall, spending on security testing tools and services is a fraction of the potential loss from breaches. Gartner projects global security spending to grow 15% in 2025 organizations are prioritizing this investment.
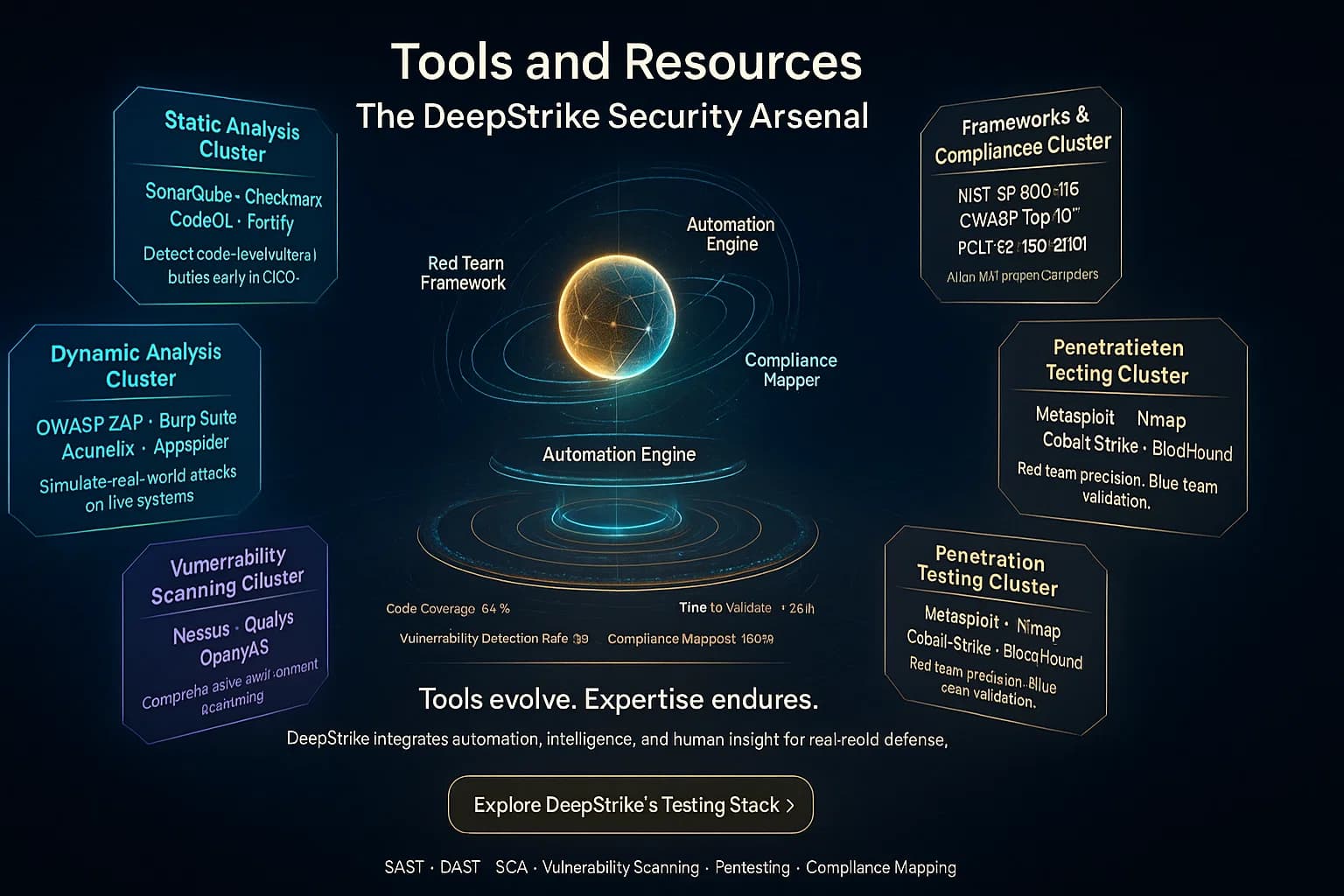
There are many tools to automate and aid security testing at different stages:
For guided processes, the NIST SP 800 115 provides methodology for planning/executing security tests. OWASP’s documentation Top 10, Testing Guide, DevSecOps guideline and CISA’s resources offer up to date attack examples and best practices.
Lastly, keep an eye on credible industry reports: IBM’s annual Cost of a Breach, Verizon’s DBIR, OWASP Top 10, etc., for trending threats to focus your testing on.
Security testing ensures your software not only works, but survives real world attacks. By weaving security tests into every phase of development from code commit static scans to deployment dynamic scans to pre release pentests you catch vulnerabilities early, save costs, and build trust. The threats of 2025 demand more than just awareness; they require readiness.
Ready to strengthen your defenses? DeepStrike’s team of security practitioners can uncover hidden risks before attackers do.
Explore our penetration testing services and related solutions. Whether you need a one time audit or continuous testing, we help you validate your security posture and implement a resilient defense strategy. Drop us a line we’re always ready to dive in.
About the Author: Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Security testing is the practice of evaluating software for vulnerabilities by simulating attacks or malicious inputs. It focuses on the software’s confidentiality, integrity, and availability. Unlike functional testing which assumes honest users, security testing assumes attackers might misuse the system. Tests include code analysis, dynamic scans, and penetration testing to ensure the system can withstand cyber threats.
Regular functional testing checks if features work as intended for end users e.g. does login accept valid credentials?. Security testing, on the other hand, checks for weaknesses an attacker could exploit e.g. can an attacker bypass login or inject a payload?. In other words, functional testing asks Does it do what it should? ; security testing asks Can someone make it do something it shouldn’t?.
Key methods include SAST static analysis of code, DAST dynamic scans of live apps, IAST combined interactive analysis, SCA scanning open source dependencies, and penentration testing manual ethical hacking. Each method covers different layers for example, SAST finds code errors early, while DAST catches runtime issues like misconfigurations. A comprehensive program uses multiple methods together.
Ideally, security testing is continuous. Integrate tests into every stage: run static and SCA scans on code commits and builds; run dynamic scans on each deployment; and schedule manual penetration tests regularly e.g. annually or before major releases. The earlier you catch vulnerabilities e.g. during development, the cheaper and easier they are to fix.
Yes. Vulnerability scanning automated and penetration testing manual serve complementary roles. Scanning provides broad coverage to flag known issues, while pentesting actually exploits them to show real risk. As DeepStrike explains in its Vulnerability Assessment vs Penetration Testing guide, combined, they provide full coverage: automated scans for visibility and manual tests for validation.
Security testing often requires specialized skills. SAST/DAST tools can be used by developers or QA with training, but effective pentesting usually needs experienced security professionals, penetration testers, red teamers. These experts know common attack techniques, networking, cryptography, etc. Certification OSCP, CEH, CISSP is common. Many organizations augment their QA teams with security experts or outsource pentesting to specialists.
Automation can handle many routine checks SAST, DAST, SCA, container scans. However, automated tools have limits they may miss complex logic flaws or chain vulnerabilities. Manual assessment or skilled pentesters are still needed to creatively probe business logic, social engineering, and complex exploits. The best practice is automated plus manual testing for critical systems.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us