May 20, 2025
Updated: May 20, 2025
How VA and PT differ in scope, depth, frequency, and real-world impact
Mohammed Khalil

Organizations often blur the line between vulnerability assessments and penetration tests, sometimes lumping both under the term VAPT. This confusion can lead to misguided security strategies. For example, a team might run an automated scanner and believe they’ve done a thorough pen test, or conversely, assume an annual pen test alone keeps them covered year round. In reality, these two approaches serve different purposes, and understanding the distinction is crucial for effective risk management.
A vulnerability assessment and a penetration test are like different medical exams: one is a routine health check up broad and preventative and the other is a focused stress test targeted and evaluative. If you only do one and not the other, you’re missing half the picture. This article clarifies the differences, explaining how each method works, when to use them, and why combining both gives the best security outcome.
Organizations that recognize the complementary roles of VA and PT can better prioritize fixes, comply with regulations, and strengthen their overall security posture. Let’s break down each approach and then compare them side by side.
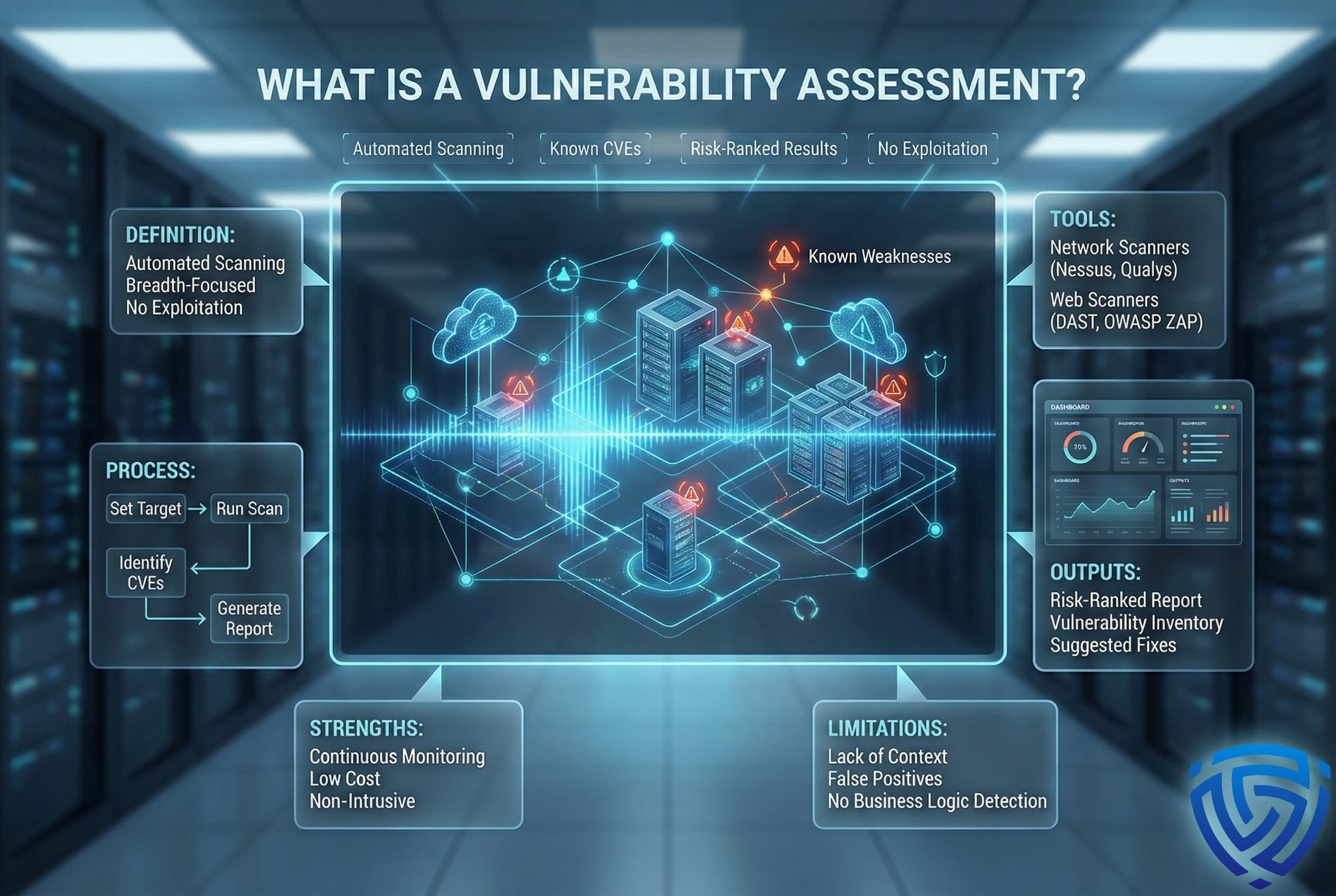
A Vulnerability Assessment is a systematic process to identify and quantify security vulnerabilities in an environment. It’s primarily an automated scan of systems, networks, or applications to find known weaknesses without actually exploiting them. The goal is breadth to review as many assets as possible for potential issues, providing a comprehensive view of where risks may exist.
Purpose and Methodology: The purpose of VA is to find as many known vulnerabilities as possible, like missing software patches, outdated libraries, misconfigured settings, or default passwords. Security tools vulnerability scanners compare system details against databases of known issues e.g., CVEs. For example, a scanner might detect that a server is running an old version of Apache and flag a related CVE as a vulnerability. The process is largely automated: you set a target IP range or application URL, run the scan, and wait for results. Modern scanners can check networks, web apps, cloud configurations, and more in one sweep.
Tools Used: Common vulnerability scanning tools include network scanners e.g., Nessus, Qualys, OpenVAS for infrastructure and web scanners DAST tools like OWASP ZAP or Burp Suite’s scanner for web applications. These tools send probes to systems, looking for known flaw signatures. They might send specific network packets, attempt various HTTP requests, or try logging in with default credentials. Because the scanning is automated, it can cover thousands of assets relatively quickly.
Typical Outputs: The output of a vulnerability assessment is a report or dashboard listing all discovered vulnerabilities, often sorted by severity or risk score. For each finding, you usually get details like the vulnerability name or CVE ID, affected systems, severity level e.g., High severity if it’s easily exploitable, and often a recommended fix e.g., apply patch X or disable TLS 1.0. It’s essentially an inventory of weaknesses. For instance, a VA report might say: 100 Windows servers are missing patch MSXX YYY, 20 databases have default passwords, 15 websites allow outdated SSL versions, etc.
Example: Imagine a retail company runs a vulnerability assessment on its network. The scanner discovers that a legacy file server has an unpatched OpenSSL library, a known bug like Heartbleed. It flags this as a High severity issue in the report. It also lists several moderate findings, such as an FTP service allowing anonymous login and a set of workstations with outdated browser versions. The security team now has a punch list of issues to remediate. Notably, the scanner did not try to exploit any of these, it only observed that the conditions for a vulnerability are present e.g., software version X which is known to be vulnerable.
Strengths: Vulnerability assessments are great for coverage and continuous monitoring. They can be run frequently, many organizations scan at least monthly, and some weekly or even daily on critical systems. Because they’re automated, the marginal cost of scanning more assets or running scans regularly is low. VA is also relatively safe and non intrusive, it usually doesn’t disrupt systems since it’s not actively exploiting anything, just checking configurations and versions. This makes it suitable for production environments as a routine check up.
Limitations: The trade off for breadth is a lack of context. A scanner might flag hundreds of issues, including false positives or low risk items, and it cannot distinguish which of those vulnerabilities would truly lead to a serious breach. For example, it might report a database vulnerability on a server that is actually isolated from critical data, something a human would realize is low priority. Additionally, scanners only find known issues signature based detection. They won’t catch novel attack methods or complex chains of weaknesses. They also typically miss business logic flaws issues like user A can see user B’s records due to logic error because those aren’t identifiable via a generic signature.
Finally, a vulnerability assessment doesn’t prove exploitability. It answers What vulnerabilities exist? But what can an attacker do with them? This is where penetration testing comes into play.
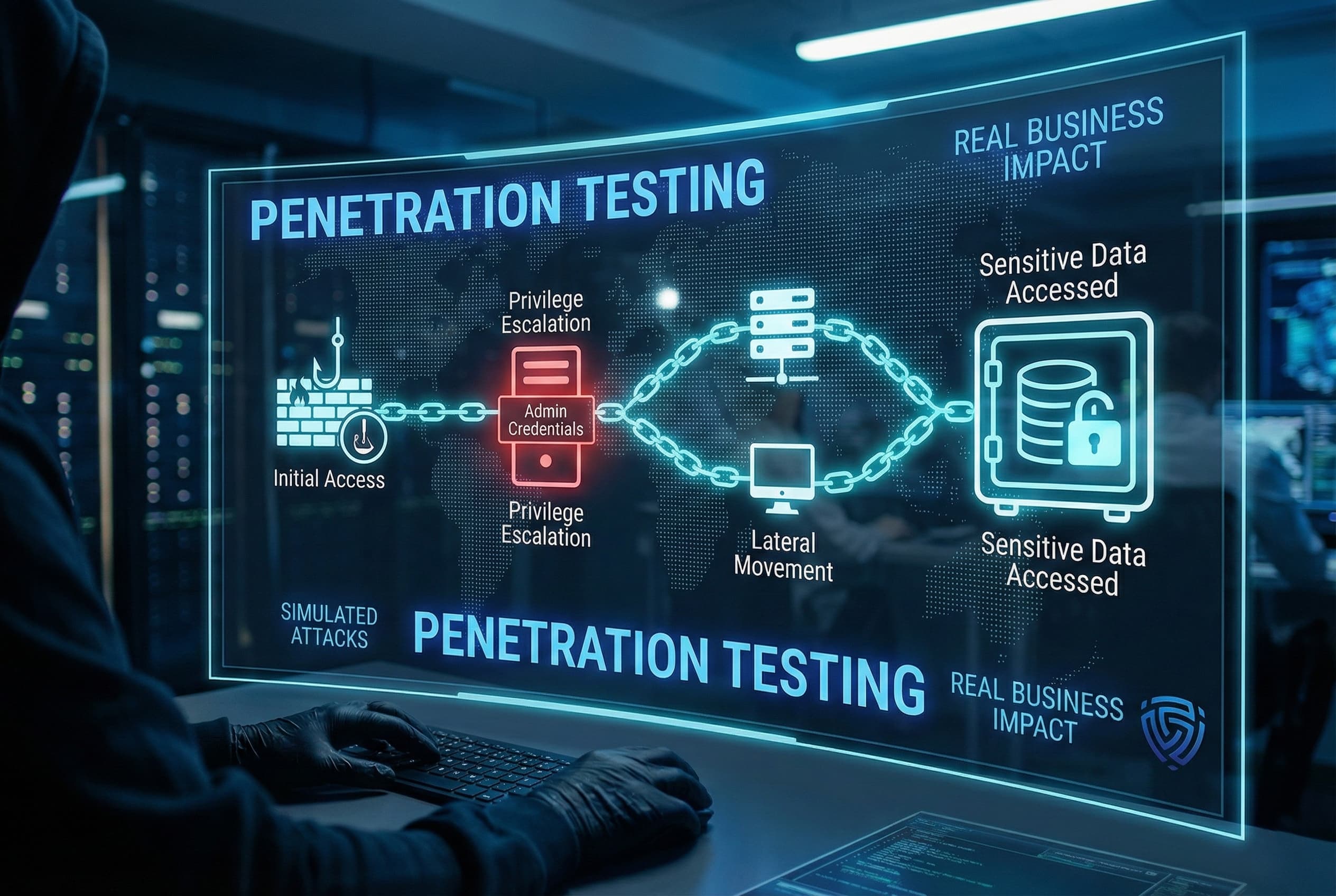
A Penetration Test is a controlled, authorized attempt to breach an organization’s systems and networks, mimicking the tactics of real attackers. In other words, it’s an ethical hacking exercise that goes beyond finding weaknesses, it actively exploits vulnerabilities with permission to determine what unauthorized access or damage is actually possible. The goal is depth: to assess the resilience of systems by trying to break in, much like a malicious hacker would.
Purpose and Approach: The purpose of PT is to validate security by simulating an attack. Pen testers ethical hackers use tools and creative techniques to chain together vulnerabilities and misconfigurations, attempting to penetrate defenses. Unlike automated scanning, penetration testing is human driven. Testers start with reconnaissance gathering information about the target e.g., what systems are running, what software versions, possible user accounts. Then they identify potential vulnerabilities sometimes using the results of a vulnerability scan as a starting point and attempt exploits. This could mean using publicly available exploit code, adjusting it to the situation, or even developing custom exploits on the fly. They might also employ tactics like social engineering for instance, sending a phishing email to an employee to gain a foothold which pure vulnerability scans cannot do.
Penetration testing often follows a structured process or methodology. Standards like NIST SP 800-115 and the PTES Penetration Testing Execution Standard define phases such as planning, reconnaissance, vulnerability analysis, exploitation, post exploitation, and reporting. Throughout these phases, the tester thinks like an adversary: once they find one weakness, they exploit it to see what deeper access it grants, then pivot to the next target, and so on. For example, they might exploit a weak web application password to get into a system, then escalate privileges on that system using a local vulnerability, then use that system to reach a database on the internal network.
Scope and Depth: Pen tests can be broad or narrow in scope, but they’re usually narrower than a full vulnerability scan. You might have a network penetration test focusing on your external IP addresses, or an application penetration test focusing on a particular web/mobile app, or even a physical social engineering test like trying to tailgate into an office. Test depth is high, testers will often spend days or weeks on a narrow scope to find complex exploit chains. There are also different knowledge levels for tests: black box tester knows nothing in advance, simulating an outside attacker, white box tester is given full information, simulating an insider or to speed up the test, or gray box partial info. These affect efficiency and realism.
Typical Outputs: The output of a penetration test is a detailed report that usually includes: an Executive Summary high level risks and business impact for management, a technical narrative of how the tester broke in or what they attempted, specific findings with evidence screenshots, logs, or data extracts proving a vulnerability was exploited, and recommendations for remediation. For instance, a pen test report might document: Using a combination of a phishing attack and an unpatched server flaw, we gained administrator access to the HR database and extracted sample employee records, accompanied by a screenshot of the tester logged into the database. Each finding is typically rated by severity often critical/high for those that led to major access and includes suggested fixes e.g., apply a patch, enforce multi factor authentication, segment the network. This story driven output shows not just what vulnerabilities exist, but what an attacker could do with them, providing crucial context to prioritize security improvements.
Example: Consider a fintech company that undergoes a penetration test on a new web application. The ethical hacker finds a seemingly minor bug: the error messages on the login page reveal whether a username is valid. They enumerate a few employee usernames, then use a password spraying approach to try a list of common passwords. Because the company hadn’t set up account lockout, the tester manages to guess the password of a weak admin account. Now inside the application as an admin, they notice an Export Data function. Through manipulating parameters, an insecure direct object reference flaw, they get the system to export the entire customer database, which was not intended. In the report, the tester documents this chain: an information disclosure + weak password policy led to admin access, which led to a data breach. The output isn’t just here are vulnerabilities, it's a narrative of how those issues could materially harm the business.
Strengths: Penetration testing provides real world insight into security: it demonstrates actual exploitability and impact. It answers questions like Can someone actually break in? What data could they steal? Would our monitoring catch it?. This helps avoid false sense of security from just patch counts. Pen tests also find issues that automated scans miss particularly logic flaws or novel attack paths. A skilled tester might discover a unique configuration quirk or chain several low risk vulnerabilities together into a critical attack, which tools would not realize. Another strength is testing the people and processes as well: a pen test can reveal if the security team detects the intrusion or if incident response processes work, something a scanner alone can’t evaluate. It’s an excellent way to validate whether your preventative controls, firewalls, antivirus, and monitoring are actually effective against an active adversary.
Limitations: Pen tests are time-bound and scope-bound. They typically last a week or a few weeks on a defined target set. This means they provide a snapshot in time vulnerabilities that appear a month later or systems not in scope won’t be covered. They also might not find every vulnerability even in scope, testers prioritize paths they believe lead to impactful exploits, so some low hanging fruit might be skipped if it’s not seen as useful for the attack narrative. Another limitation is cost and labor pen testing is resource intensive, requiring skilled professionals. This makes it impractical to do so on every system frequently, especially for large organizations. In addition, because pen tests involve active exploitation, there’s a non zero risk of system downtime or data alteration if something goes wrong professional testers take great care to avoid this, but the risk exists. Proper rules of engagement, scope definition, and sometimes excluding particularly fragile systems from aggressive tests are ways organizations manage this risk.
To summarize the contrasts, here’s a side by side comparison of key aspects:
| Aspect | Vulnerability Assessment | Penetration Testing |
|---|---|---|
| Primary Goal | Find and inventory known weaknesses breadth of coverage. Ensure baseline security hygiene by identifying what needs patching or fixing. | Simulate real attacks to exploit weaknesses in depth of attack. Validate which vulnerabilities lead to actual breaches and how far an attacker could go. |
| Approach/Method | Automated scanning using tools and scripts. Checks systems against databases of known vulnerabilities and misconfigurations. Generally non intrusive no harmful payloads executed. | Manual and creative, using hacker tactics plus some automated tools. May involve exploiting vulnerabilities, social engineering, pivoting across systems. Can be intrusive running exploits, which are controlled but active. |
| Depth of Analysis | Shallow per vulnerability identifies the existence of a flaw but does not prove impact. Stops at vulnerability found, doesn’t chain issues together. | Deep goes from finding to exploiting vulnerabilities, often chaining multiple findings. Assesses the context of what the vulnerability means for the specific environment. |
| Frequency | Often continuous or very frequent e.g., weekly, monthly scans to track new vulnerabilities. Integrated into regular operations e.g., part of patch management cycle. | Performed periodically, such as annually or quarterly, and after major system changes. Too resource intensive to do constantly on all assets. |
| Skill & Effort | Relatively low effort per run: can be executed by automated tools or IT staff. Interpreting results may require a security analyst to filter false positives. | High skill required: conducted by cybersecurity experts ethical hackers with knowledge of attack techniques. Labor intensive planning, execution, and analysis for each engagement. |
| Output | Detailed list of vulnerabilities with risk ratings e.g., 75 hosts vulnerable to CVE 2025 1234. Includes remediation recommendations for each item, often generic patch, config change. | Detailed report of attack scenarios and confirmed impacts e.g., gained admin access to database via X exploit. Includes proof of concept screenshots, data obtained and specific fix recommendations, plus strategic security improvements. |
| Best Use Case | Ongoing vulnerability management maintains a secure baseline by catching known issues early and ensuring compliance e.g., PCI requires regular scans. Great for broad risk awareness across many systems and verifying that routine patches are applied | Adversarial assessment of critical assets e.g., testing a new application before going live, or annual security audit for a network segment. Ideal for uncovering high impact weaknesses, testing incident response, and getting attacker’s perspective on most crucial systems. |
It’s not either/or. These practices address different risk questions. A vulnerability assessment asks, What vulnerabilities might expose us? A penetration test asks, What damage could be done if these vulnerabilities are exploited? As one expert succinctly put it, a VA shows what could be exploited, whereas a PT shows how an attacker would exploit it, and together they show the full picture.

Use vulnerability assessments as your continuous security radar. For most organizations, regular vulnerability scanning is a foundational activity for good reason. Here are scenarios and needs where VA is the right choice:
In summary, use vulnerability assessments for breadth, frequency, and preventive maintenance. It’s the everyday workhorse of a security program akin to a routine health check. It won’t tell you everything about your security, but it will catch the low hanging fruit and regressions that, if unaddressed, are the easiest ways for attackers to get in.
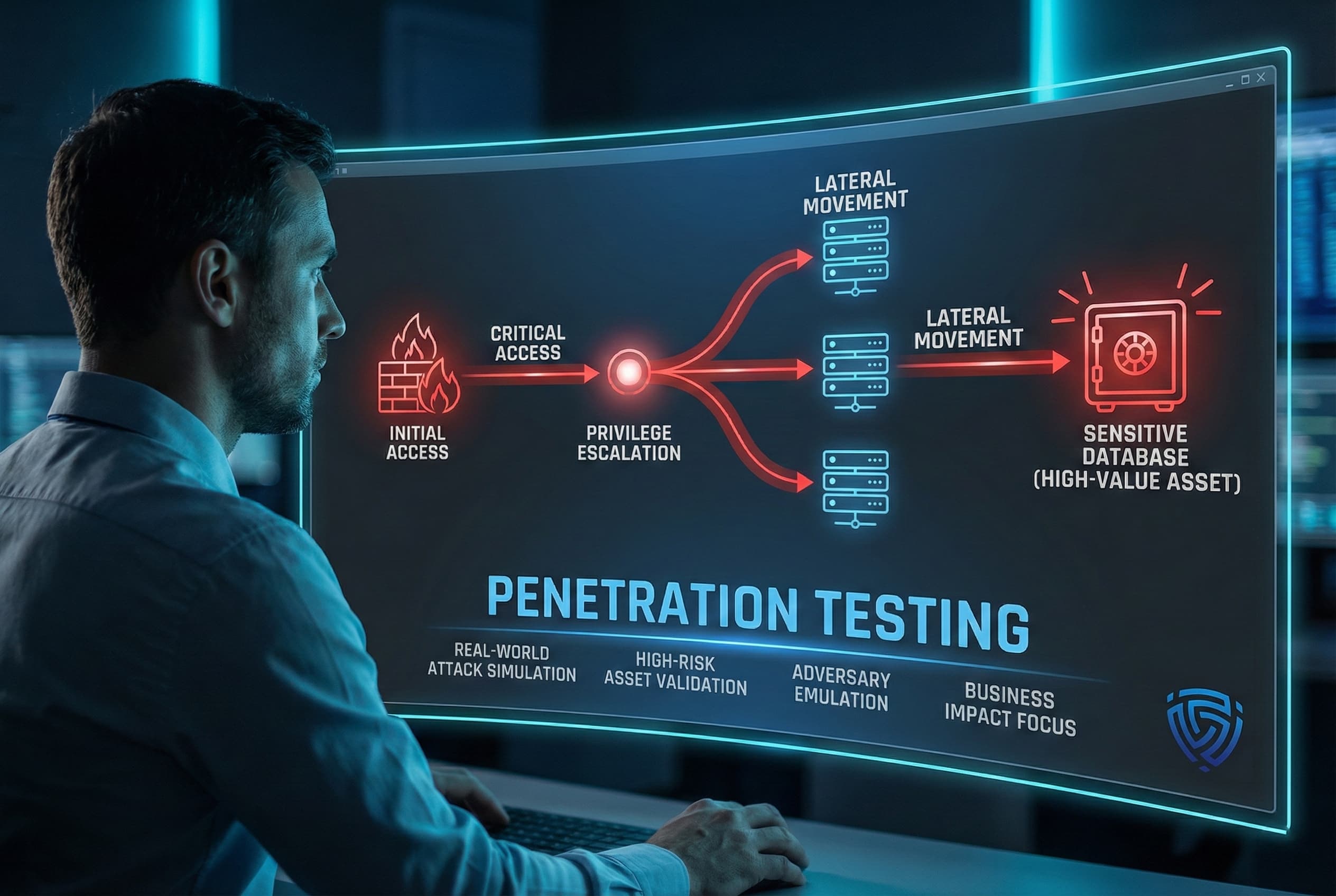
Choose penetration testing when you need a realistic attack simulation and assurance of your defenses under fire. There are several situations where a pen test is the appropriate or even necessary approach:
In summary, use penetration testing for depth, realism, and critical validation. It shines in situations where understanding the real impact of a breach is important, or where you need to test scenarios beyond the reach of automated tools, complex multi step attacks, social engineering, etc.. Pen tests are like fire drills for your cyber defenses best done before an actual emergency, so you can fix what went wrong in the drill.
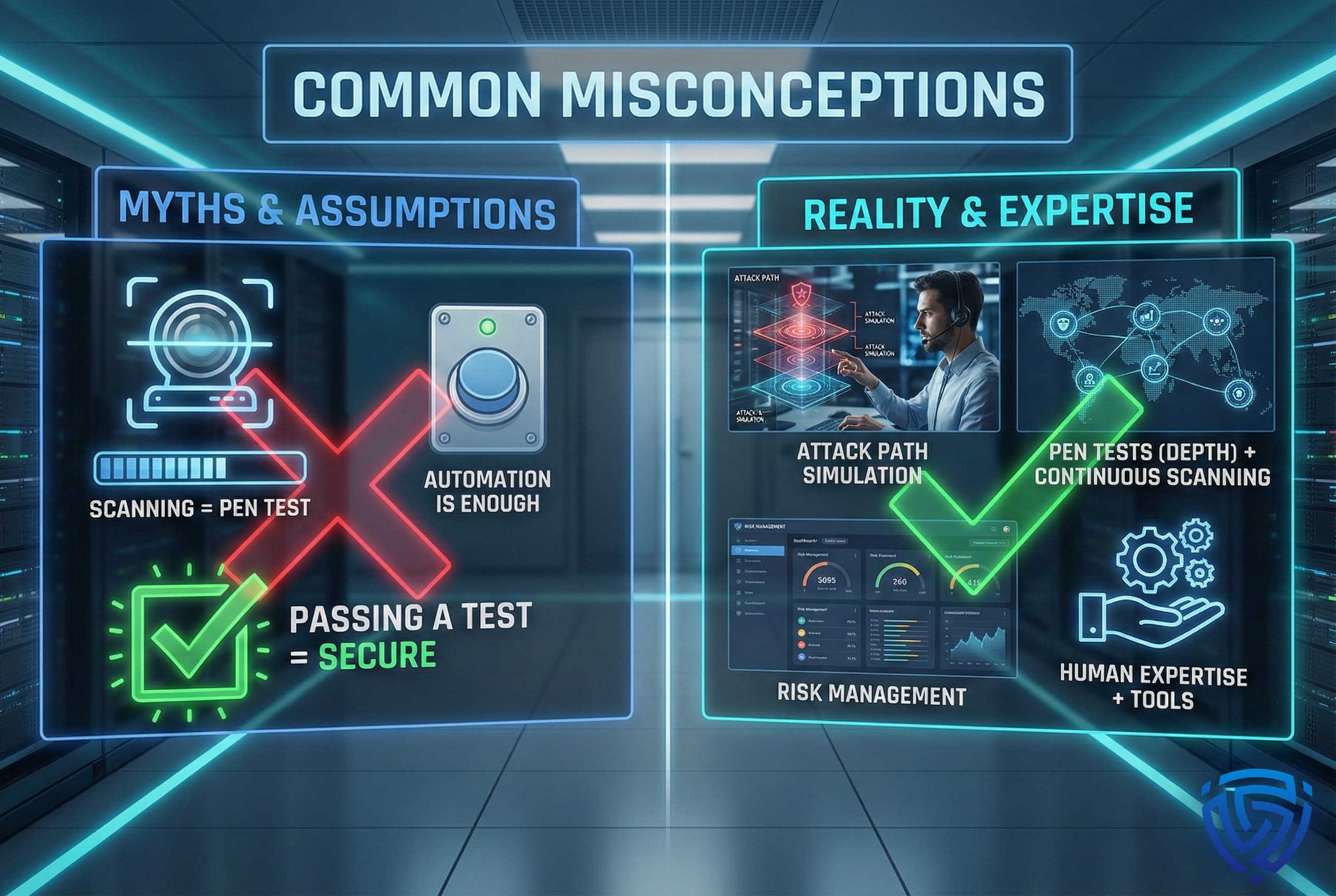
There are several myths and misunderstandings about vulnerability assessments and penetration tests. Let’s debunk a few:
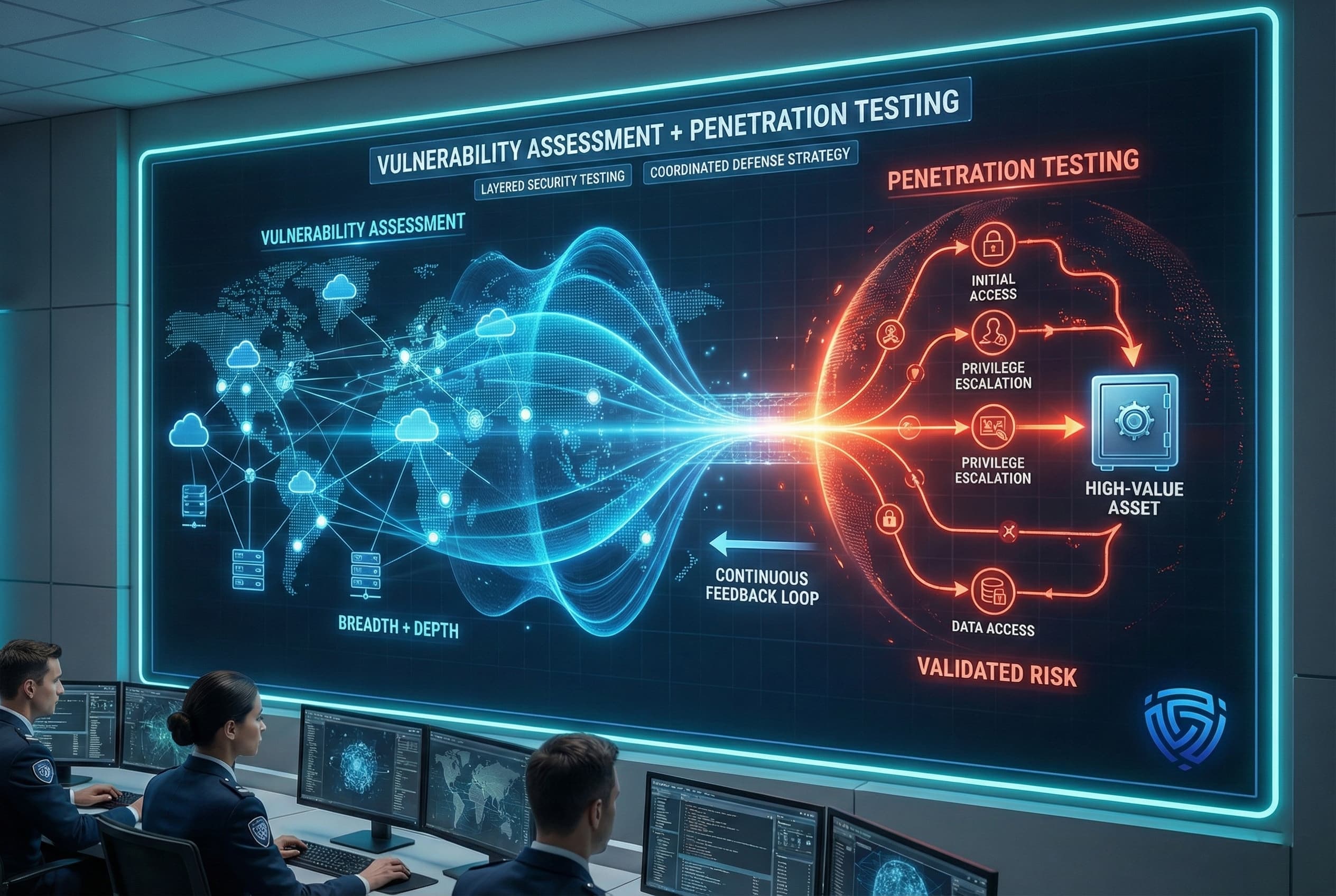
Absolutely and in fact, the best practice is to integrate vulnerability assessments and penetration testing into a coordinated strategy. Rather than choosing one over the other, savvy security programs use each to compensate for the other’s gaps, creating a layered defense testing approach.
Here’s how they complement each other:
In practice, a combined approach might look like this: do frequent VAs to keep the vulnerability count manageable, conduct a pen test to simulate a breach the pen test report highlights a few critical issues, feed those back into the vulnerability management process to patch and fix, then maybe even re test those specific fixes. Some organizations formalize this through Continuous Threat Exposure Management CTEM programs, which integrate asset discovery, vuln scanning, pen testing, and even breach and attack simulation into a loop of constant security assessment and improvement.
VA and PT are stronger together. As one security blog noted, used in tandem they allow teams to identify risks and validate which ones are truly exploitable, enabling smarter prioritization and more robust defense.
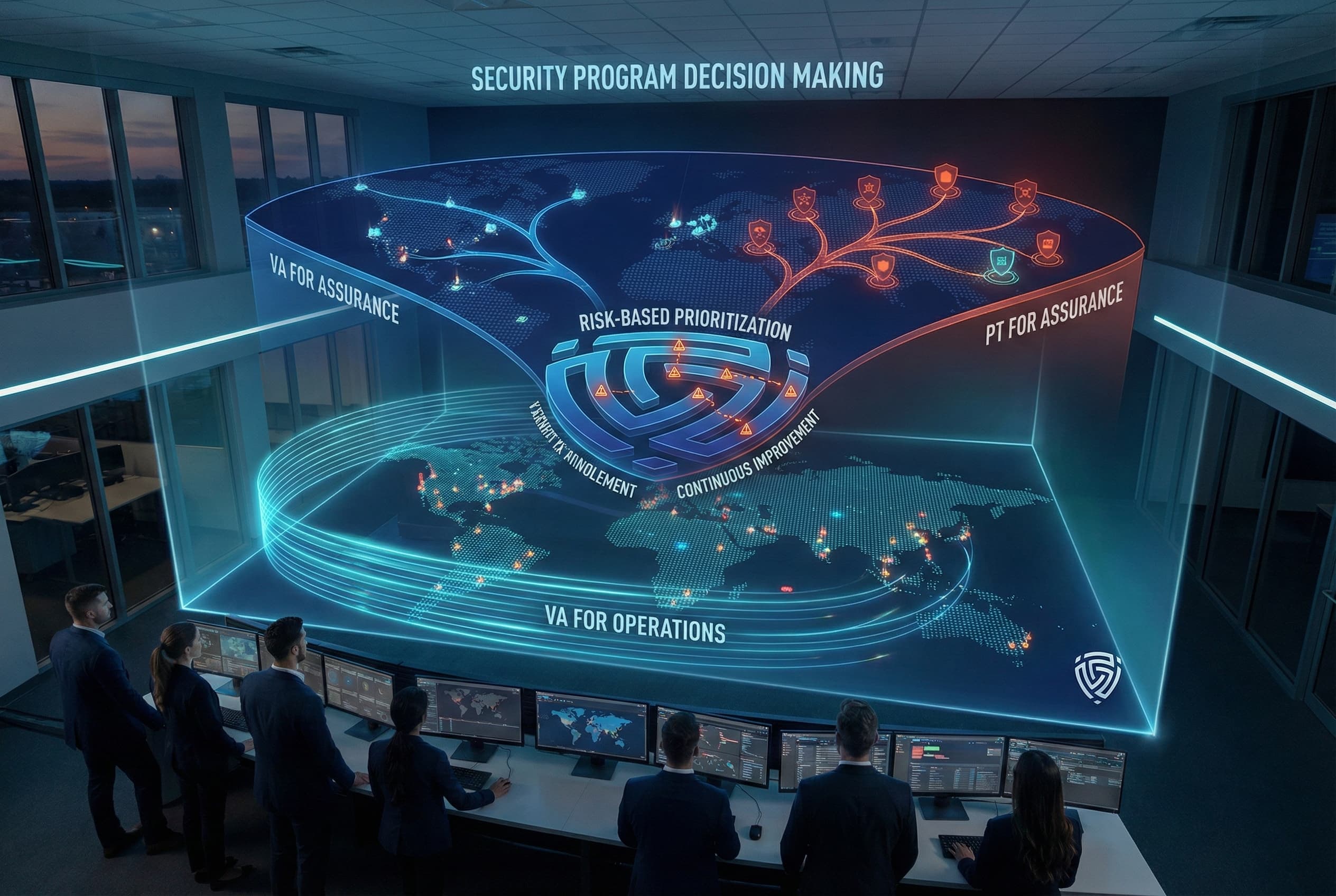
For security teams and decision makers, understanding the VA vs PT distinction translates into concrete program decisions:
In essence, security teams should use vulnerability assessments and penetration tests as complementary tools in their arsenal. Each provides a different lens on the organization’s security, one wide angle, one zoomed in. By combining the continuous vigilance of VA with the adversarial insight of PT, teams can achieve a more resilient security posture. It’s about covering both the known vulnerabilities you can find and fix and the unknown creative attack scenarios you uncover through testing. That comprehensive approach is what ultimately reduces the risk of breaches.
By applying both VA and PT in a coordinated way, teams can catch weaknesses early, prevent common attacks like account takeover trends from easily succeeding, and also be prepared for sophisticated threats that require a human led attack to uncover. The result is stronger defense and faster response when new threats emerge.
Not usually by itself. Most robust compliance standards call for both periodic scanning and penetration testing. For example, PCI DSS requires quarterly vulnerability scans and an annual penetration test plus after significant changes. The scans satisfy the need for ongoing oversight of known issues, while the pen test demonstrates a deeper evaluation of security controls. Other frameworks like HIPAA, NIST 800 53, and ISO 27001 implicitly expect organizations to perform regular technical testing. A vulnerability assessment alone might help meet parts of compliance identifying known vulns, but without a pen test you could fall short on requirements to evaluate security effectiveness. Always check the specific language of your compliance obligations often the term penetration testing is explicitly mentioned as a requirement for a comprehensive security program. At a minimum, regulators will ask if you have a process for continuous vulnerability management, having only an annual scan would be viewed as insufficient.
Industry best practices suggest at least once a year for a full scope penetration test on critical systems, and additionally whenever there are major changes. Many organizations do an annual external pen test and an internal one, or combine them. However, more frequent testing is recommended if possible some do semi annual or quarterly tests on different areas, ensuring all key assets get tested over time. Keep in mind that threats evolve quickly, so a yearly test is a bare minimum. If you’re in a high security environment like finance, healthcare, etc., you might also consider continuous penetration testing approaches or rolling tests on different applications throughout the year. The emergence of PTaaS platforms means you can have certain tests running or triggered on demand for example, testing a new app right before deployment, rather than waiting for the annual cycle. Critical moments to do an extra pen test include: after migrating to cloud, after a big network redesign, after major software upgrades, or if threat intelligence suggests new attack techniques targeting your sector. Also, don’t forget to pen test your defenses periodically. Some organizations schedule a red team exercise every couple of years which is like an extended pen test that also checks detection/response.
Ideally, yes scaled to their needs. A small company might have fewer assets, but a single security breach could be devastating e.g., ransomware locking up a few critical systems can cripple a small business. Vulnerability assessments for a small company can be as simple as running a network scanner on their IP range or using a managed service that scans their web presence. It’s a quick way to catch obvious issues: open ports, outdated software that are the common cause of attacks, and often these issues are straightforward to fix, apply updates, and close ports. Penetration testing for a small company can often be scoped and budgeted appropriately, perhaps focusing on the primary public facing application or the corporate network’s external exposure. Some security providers offer lightweight pen tests or pentest lite engagements for SMBs that are shorter in duration but still check for the most critical holes. While a mom and pop shop might not do a full pen test, any company handling sensitive data or reliant on IT should at least do basic external pen testing to ensure there isn’t an easy way in. If budgets are tight, one strategy is to leverage free/low cost VA tools regularly, and engage a professional for a pen test once every year or two, focusing on what you’re most concerned about like your e-commerce site or your customer database. Remember, attackers don’t discriminate by size, automated bots scan the internet for any vulnerable systems. Using both VA and PT, even at a smaller scale, dramatically improves a small organization’s security by covering both routine fixes and deep checking for lurking dangers.
In common usage, the terms vulnerability scanning and vulnerability assessment are often used interchangeably, and both refer to the process of using automated tools to find known vulnerabilities. Technically, one might differentiate: a vulnerability scan is the act of running the tool to identify issues, while a vulnerability assessment could imply the broader process which includes scanning, analyzing the results, and maybe validating or prioritizing them. In practice, most people mean the same general activity of automated detection of vulnerabilities when they say either term. The key distinction is with penetration testing unlike a scan, a pen test involves exploitation and a human element. Some vendors also use vulnerability assessment to mean an on demand or one time scan, whereas vulnerability management is the ongoing program of scanning and remediation. But if someone offers a vulnerability assessment service, you should clarify whether they include any manual validation of findings or if it’s purely tool driven. Often, an assessment will include an expert’s review to weed out false positives from the raw scan results. In summary: vulnerability scanning = automated tool finds possible vulns, vulnerability assessment = scan + maybe some expert analysis of scan results. Both stop short of actual exploitation.
It depends on your team’s skill set and the requirements. Some organizations have internal security professionals or red teams capable of conducting penetration tests. The advantage of an internal team is they are deeply familiar with the environment though that can also bias them and be available for continuous testing. However, many regulations and cyber insurance policies prefer or require an independent test meaning a third party to ensure objectivity. External pen testers bring a fresh perspective and specialized expertise since they test different companies year round. They might find issues an internal person overlooks due to familiarity or assumptions. If you choose to do it internally, ensure the team has proper training, tools, and a methodology and ideally is somewhat separate from the teams that built the systems, to avoid conflict of interest. For critical systems or compliance needs, it’s wise to get an external pen test at least periodically, even if you do internal testing in between. A hybrid approach can work well: an internal team performs frequent light pen tests or attack simulations to catch obvious gaps continuously, and an external firm is engaged annually for a deeper, comprehensive test and to validate the internal team’s effectiveness. Keep in mind that if you do go internal, you must still adhere to safe practices scope definition, getting approvals, not exceeding boundaries just as a third party would. And document everything you’ll need evidence of tests and findings for audits or management.
In an ideal scenario, findings from both should feed into a unified prioritization scheme. However, penetration test findings often highlight more urgent, exploitable risks especially if the tester achieved a significant breach in the simulation. If a pen test report shows, for example, a database of customer records was compromised via vulnerability X, that specific vulnerability X should be a top priority fix, even if a scanner had it rated as, say, medium severity. Pen test findings provide concrete impact, so they typically warrant immediate attention. On the other hand, vulnerability scan findings might include many high severity issues that pen testers didn’t look at, perhaps out of scope or they didn’t need to exploit them. You shouldn’t ignore these, instead, address them in parallel based on their criticality. A practical approach: address any confirmed exploitable paths first from pen test, and simultaneously continue chipping away at the broader list from scans starting with highest severities. Often, the overlap between the two will guide you e.g., if both the scanner and the pen tester call out a particular flaw the scanner flags it and the tester exploits it, that’s clearly critical. Another factor is effort vs risk: some scan findings might be easy, quick wins like an open port that just needs closing, fix those quickly too, rather than waiting. In short, use pen test results to adjust your priorities. They might reveal your true critical risks, but don’t neglect the general upkeep that scan results represent. The best outcome is when your routine scanning has already fixed so many things that the pen testers struggled to find a way that means your program is working!
Determine your objective and context. If you need a broad sweep to uncover as many issues as possible across an environment, especially if it hasn’t been checked recently, start with a vulnerability assessment. It’s faster and will give you a to-do list of fixes. This is often the case for new IT environments or after significant time without any formal security checks scanning provides a baseline. Also choose a VA if you require a quick check for compliance e.g., an external scan for a network segment to meet a requirement or as part of routine maintenance. On the other hand, if you have a specific concern like Could someone break into this new application? or Are we protected against a skilled attacker targeting us? Then a penetration test is warranted. Pen testing is also the choice when a mere list of vulnerabilities isn’t enough, you need to demonstrate impact to motivate action or to verify that your crown jewels are secure. In many cases, the answer is to do both eventually. A good strategy is: conduct a vulnerability assessment first to clean up the low hanging fruit, then follow up with a penetration test to probe deeper into the remaining security posture. If you must pick one due to constraints, consider risk: if you’re about to launch a product or face an audit and fear a breach, a penetration test might provide more assurance. If you’re trying to establish a security program and don’t even know where you stand, a vulnerability assessment is a prudent first step. Always clarify the outcome you want: inventory of issues > VA vs. impact analysis > PT.
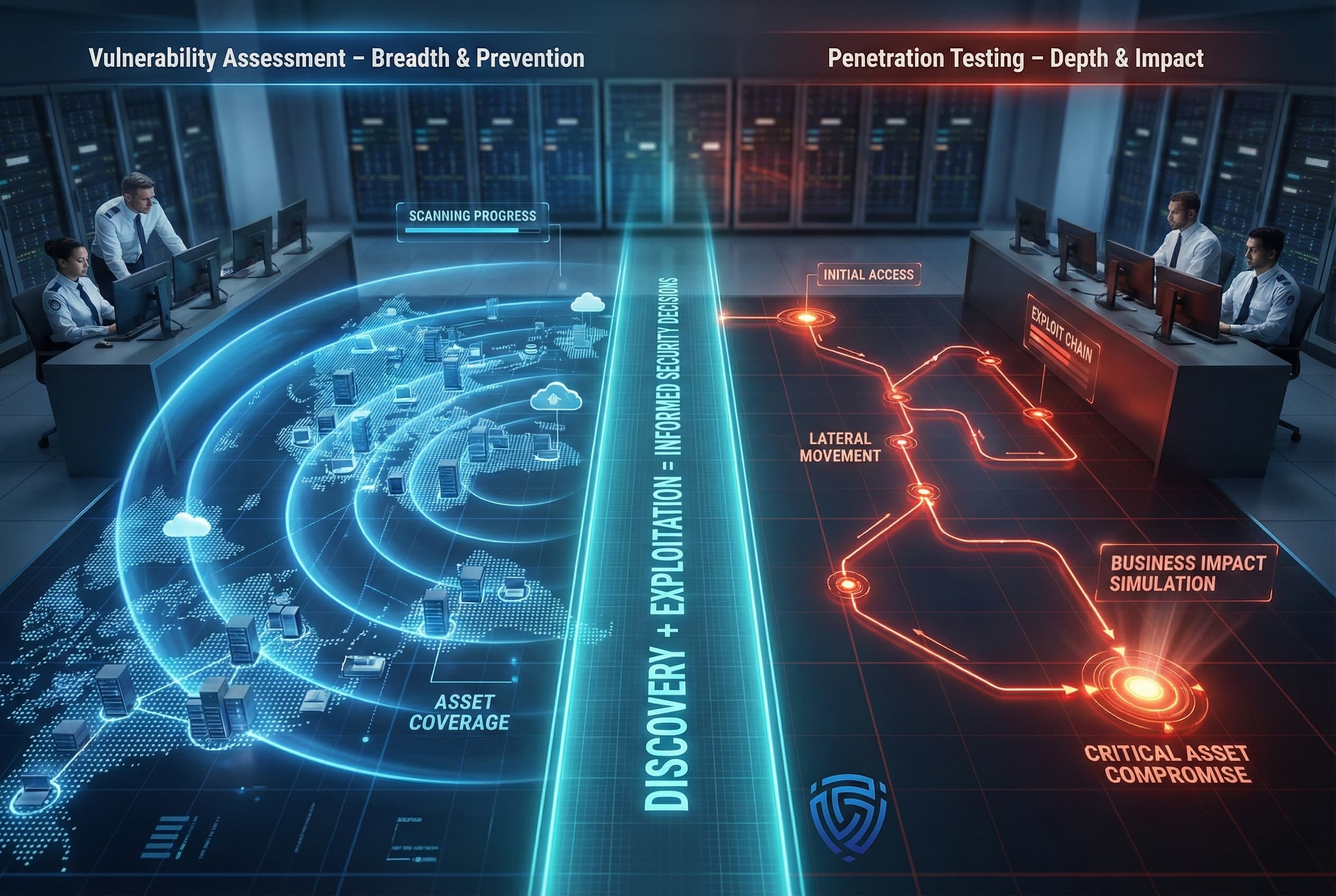
Vulnerability assessments and penetration testing are two sides of the security testing coin distinct in approach but complementary in purpose. A vulnerability assessment offers wide coverage, automatically identifying where known weaknesses lie across your IT assets. It’s about casting the net wide to improve your baseline security finding and fixing the known bad configurations and missing patches. Penetration testing, in contrast, is a deep dive into your defenses, simulating how an actual attacker could exploit weaknesses to achieve a foothold or compromise critical data. It’s focused on demonstrating impact and uncovering complex attack paths that scanners cannot.
Neither approach alone is better universally, they serve different needs. Vulnerability assessments excel at continuous monitoring and prevention, ensuring you catch easy to fix issues before attackers do. Penetration tests excel at validation and realistic attack insight, ensuring that your security measures actually hold up against skilled adversaries and that you haven’t missed anything critical. Organizations that leverage both will benefit from the strengths of each: the assessment’s breadth and the test’s depth. This combined strategy allows you to maintain strong day to day security hygiene and also regularly evaluate your readiness against real threats.
In summary, don’t view it as Vulnerability Assessment vs. Penetration Testing in a competitive sense, but rather VA + PT as complementary components of a robust security program. Use automated scans to keep your ship in order, and use human driven tests to challenge your assumptions and reinforce the most important defenses. By doing so, you will significantly enhance your organization’s resilience against cyber attacks catching the small cracks before they widen, and fortifying the big gates against determined intruders.
Finding vulnerabilities is important, but so is understanding their impact. Combining both methods gives you the full story from discovery to exploitation enabling smarter security decisions and ultimately a safer environment.
References:
About the Author: Mohammed Khalil is a Cybersecurity Architect at DeepStrike. Specializing in advanced penetration testing and offensive security operations, he holds certifications including CISSP, OSCP, and OSWE. Mohammed has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us