September 7, 2025
Updated: September 7, 2025
Inside the latest data on phishing, BEC, vishing, and AI-powered social engineering attacks reshaping the 2025 threat landscape.
Mohammed Khalil

Let's get straight to it. The most significant threat to your organization in 2025 isn’t a zero day exploit or a complex piece of malware. It’s a well crafted email, a convincing phone call, or a deepfake video. Social engineering, the art of "human hacking," remains the number one cause of security breaches, and the latest social engineering attack statistics prove it's more dangerous than ever.
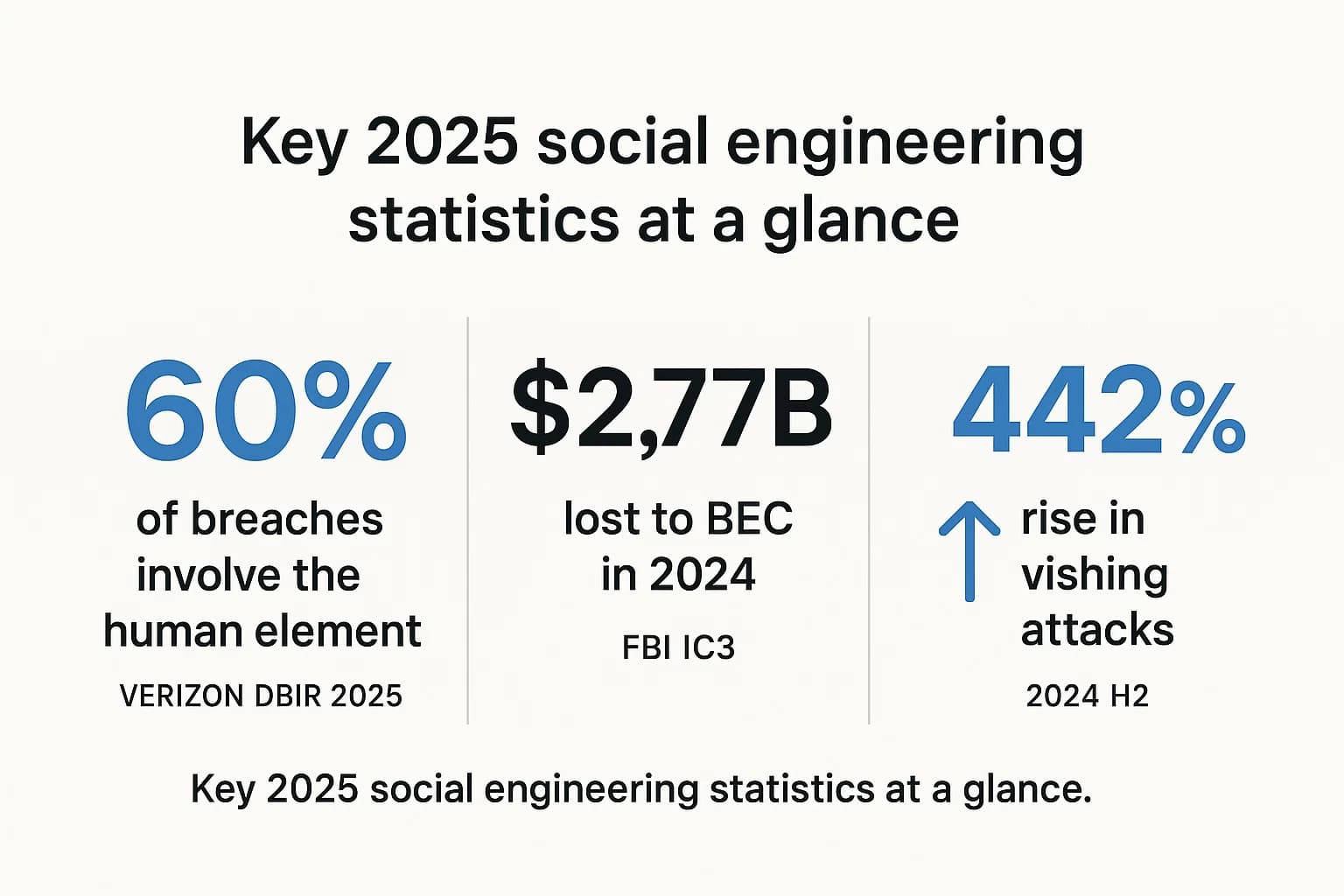
While technology has built formidable digital walls, attackers have simply learned to persuade someone on the inside to open the door. The data from sources like the 2025 Verizon Data Breach Investigations Report (DBIR) is clear: the human element is involved in around 60% of all breaches. This isn't a failure of technology; it's a feature of how attackers operate.
This report goes beyond the headlines. We'll break down the definitive social engineering statistics for 2025 from trusted sources, explore not just what is happening, but why it works, how much it costs, and how the rise of AI is changing the game forever.
To defend against social engineering, you first have to understand how it works. It’s less about code and more about cognition.
Defining "Human Hacking"
At its core, social engineering is an attempt to trick someone into revealing information (like a password) or performing an action (like transferring money) that can be used to attack systems or networks. As defined by NIST Cybersecurity Framework, it’s a psychological manipulation that targets human fallibility, not software vulnerabilities. Attackers know it’s often easier to fool a person than to break through a firewall.
The Psychology of Manipulation: Why We Fall For It
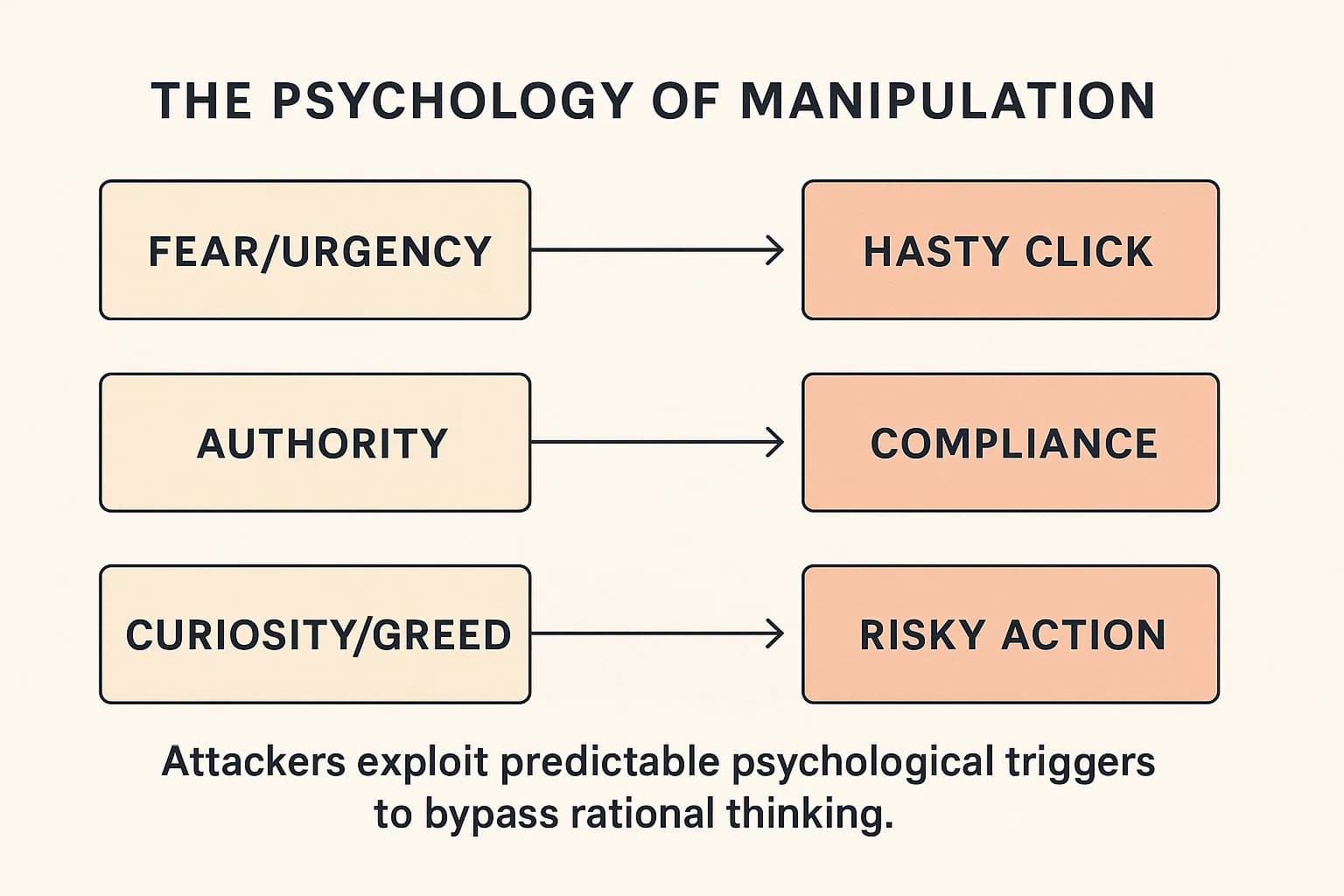
Here's the deal: attackers are amateur psychologists who exploit predictable cognitive biases to bypass our rational thought processes. They rely on a few key triggers:
The problem, however, goes deeper than just being tricked. Organizations invest heavily in security awareness training, yet breaches continue. This points to a profound "awareness action gap". Many employees know an action is risky but do it anyway for convenience or to save time. This reframes the "human element" problem. It's not always a user failure; it's often a security design failure.
When security controls create too much friction, they incentivize insecure workarounds. This suggests one of the most powerful security controls is investing in solutions with a better user experience (UX), championing a culture of "secure usability."
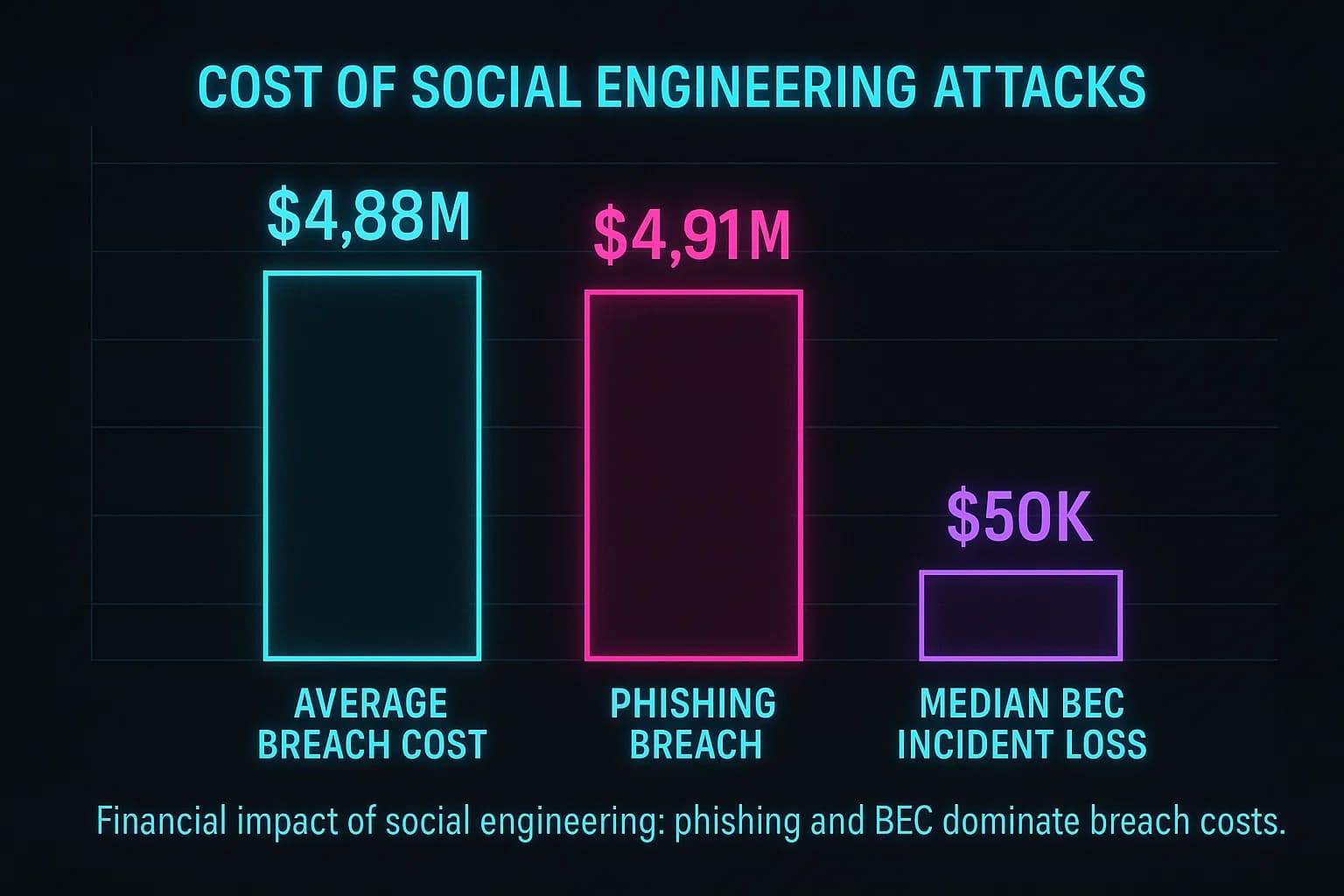
The numbers paint a stark picture. Social engineering isn't a fringe threat; it's the primary engine of cybercrime, and its financial impact is staggering.
The global average cost of a data breach has hit an all time high of $4.88 million in 2024, a clear indicator of the escalating damage. Breaches that start with a phishing attack are even more expensive, averaging $4.91 million, according to the latest IBM X Force 2025 Cost of a Data Breach Report.
The real financial damage, however, is most visible in Business Email Compromise (BEC) attacks. The FBI’s IC3 Annual Report reveals that BEC alone accounted for $2.77 billion in reported losses. For small businesses, the consequences are often existential; an estimated 60% are forced to shut down within six months of a major cyber breach , making the fight against Cyber attacks on small businesses a matter of survival.
The velocity of these attacks is also alarming. The median time for a user to fall for a phishing email is less than 60 seconds. This means a compromise can happen before an automated security system or a SOC analyst has time to react.
The Human Element's Central Role in Breaches
The cornerstone statistic from the Verizon 2025 Data Breach Investigations Report (DBIR) is that the human element was a factor in approximately 60% of breaches. This figure, consistent with previous years, confirms that people, whether through error or manipulation, are at the center of most security incidents.
Furthermore, Social Engineering is consistently one of the top three attack patterns across nearly every industry Verizon analyzes, including Finance, Education, and Manufacturing. It's not a standalone threat but the "carrier wave" for other attacks like ransomware and data theft.
Attack Frequency and Speed
The velocity of these attacks is alarming. The median time for a user to fall for a phishing email is less than 60 seconds. This means a compromise can happen before an automated security system or a SOC analyst has time to react. This is compounded by the sheer volume of the threat, with an estimated 3.4 billion phishing emails sent daily.
The data also reveals a deliberate shift in attacker strategy. In the past, phishing often aimed to steal credentials, which then had to be monetized. Now, attackers are optimizing their business model.
The Verizon DBIR shows pretexting incidents the core of BEC have nearly doubled, overtaking phishing in frequency. At the same time, the FBI reports the median loss from a single BEC incident is around $50,000.
Attackers are bypassing the intermediate step of credential theft and going straight for the money. This has profound implications for defenders: while MFA is critical, it's not enough. Organizations must implement robust financial process controls, like out of band verification, as a last line of defense.
Social engineering is a broad category. Understanding the specific tactics attackers use is key to building a targeted defense.
Phishing: The Enduring Gateway to Compromise
Phishing remains the most common initial infection vector, identified in 16% of breaches analyzed by IBM. It's the primary delivery mechanism for ransomware, with 54% of all ransomware incidents originating from a phishing email. For a deeper look at these attacks, see the latest phishing attack trends and statistics.
Business Email Compromise (BEC): The Rise of Pretexting
As highlighted by the Verizon DBIR, pretexting incidents have almost doubled, now accounting for over 50% of all social engineering incidents.
These attacks are devastatingly effective because they don't rely on malware. Instead, they use impersonation and a believable story to trick employees into making fraudulent wire transfers. The FBI IC3 received over 21,442 BEC complaints in 2024, with losses totaling a staggering $2.77 billion.
Vishing & Smishing: The Attack Surface Expands Beyond Email
As email filters have improved, attackers have pivoted to other channels.
Watering Hole Attacks: Lying in Wait
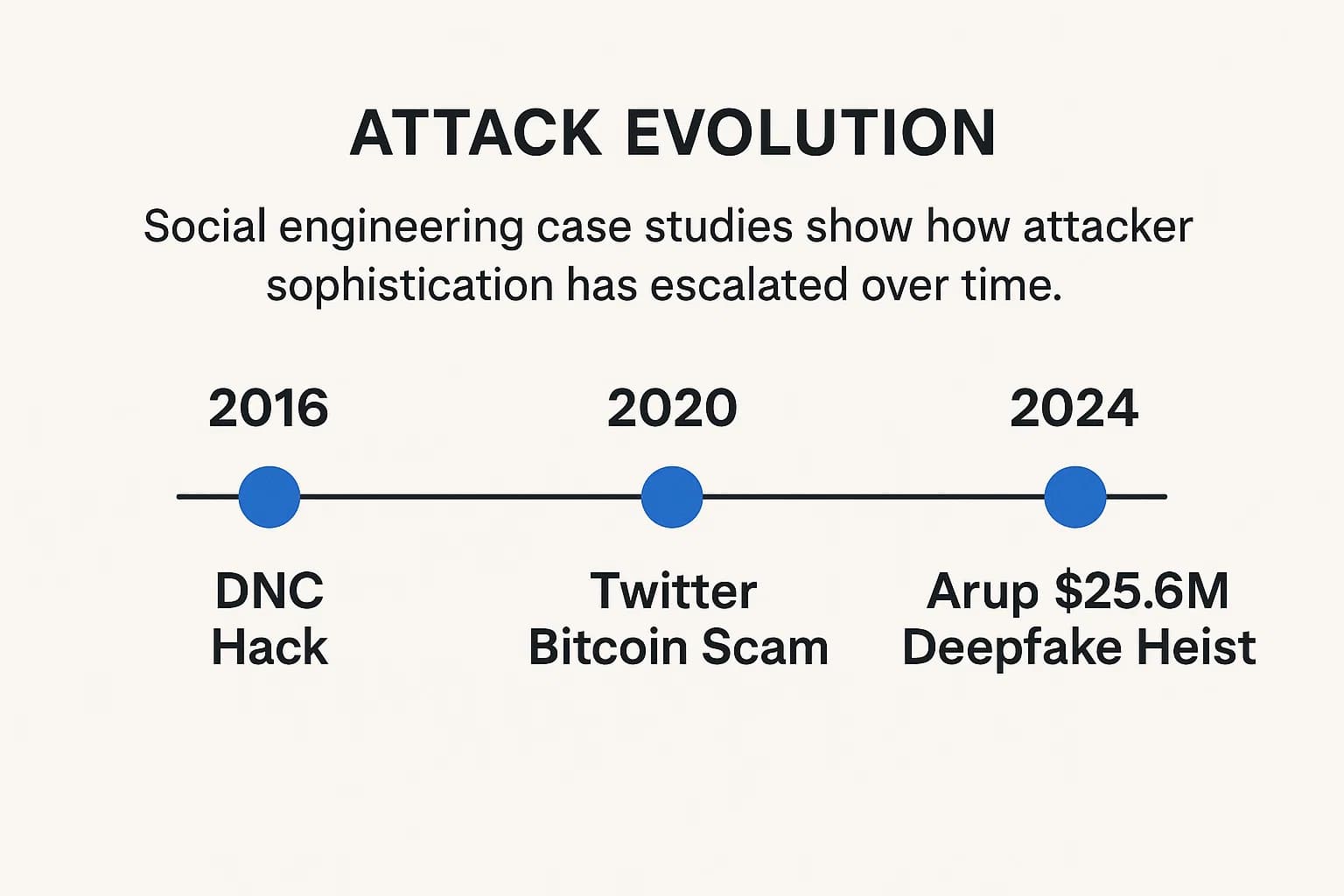
A more patient and targeted form of social engineering is the watering hole attack. Here, attackers compromise a legitimate website they know their targets frequent. A famous example is the 2017 NotPetya ransomware attack, which was initially spread through a compromised update server for a popular Ukrainian accounting software.
Statistics are powerful, but real world stories show the true impact of these attacks.
The $25.6M Deepfake Heist: The Arup Case Study (2024)
In early 2024, a finance worker at the global engineering firm Arup was tricked into transferring $25.6 million. The deception was unprecedented: the employee attended a video conference with what they believed were the company's CFO and other senior executives.
In reality, every person on the call, except the victim, was an AI generated deepfake. This case marks a terrifying new era for BEC, proving that "seeing is no longer believing."
The Celebrity Hijack: The Twitter Bitcoin Scam (2020)
In July 2020, attackers used phone based social engineering to gain access to Twitter's internal admin tools. They then hijacked the accounts of high profile figures like Barack Obama and Elon Musk to promote a bitcoin scam, stealing over $118,000 in hours. The incident demonstrated how easily social engineering can compromise even major tech platforms.
Political Manipulation: The DNC Hack (2016)
This incident remains a classic example of social engineering's far reaching consequences. Russian intelligence groups used targeted spear phishing emails to compromise the Democratic National Committee's network. The resulting leak of sensitive emails had a significant influence on the 2016 U.S. presidential election.
The threat landscape is on the verge of a revolutionary shift, driven by the weaponization of Artificial Intelligence. The AI cybersecurity threats of today are more advanced and accessible than ever before.
AI Generated Phishing: Flawless Lures at Scale
Generative AI allows attackers to craft grammatically perfect, contextually aware, and highly personalized phishing emails in minutes, a task that previously took a human expert hours. Research shows that phishing emails generated entirely by AI can achieve a 42% higher click through rate than those written by humans.
The critical takeaway? The age old advice to "look for spelling and grammar mistakes" is now dangerously obsolete.
The Deepfake Threat: When You Can't Trust Your Eyes or Ears

As the Arup case demonstrated, deepfakes are no longer a theoretical threat. Deepfake fraud attempts have surged dramatically, with some reports indicating a 3,000% rise since 2023. Voice cloning technology now requires only a few seconds of audio to create a convincing fake, making vishing attacks incredibly potent. This technology fundamentally erodes trust in all digital communication.
The most significant long term impact of AI is the democratization of these advanced capabilities. Previously, crafting a hyper personalized spear phishing campaign or a deepfake required significant skill and resources. Now, publicly available generative AI tools allow even non technical criminals to launch these attacks with ease.
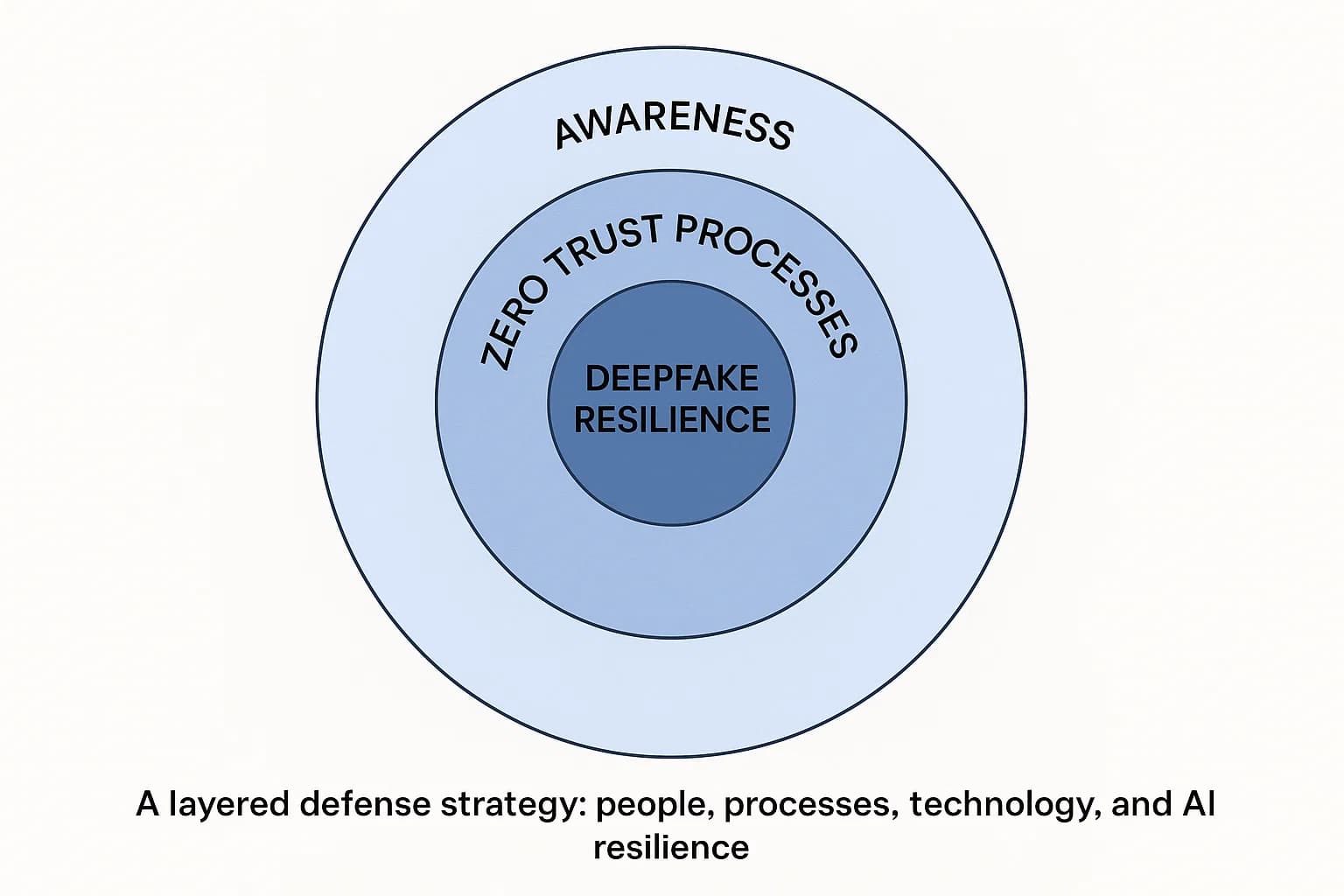
Defending against social engineering requires a multi-layered strategy that puts people and processes first. Here’s a practical, step by step approach.
Step 1: Move Beyond Awareness to a Human Centric Security Program
Acknowledge the "awareness action gap". The goal isn't just knowledge transfer; it's sustainable behavioral change.
Step 2: Implement Zero Trust for Human Processes
The principle of "never trust, always verify" must be applied to human interactions, not just networks.
Step 3: Bolster Your Technical Defenses
Technology is still a critical layer of defense.
Step 4: Prepare for the Deepfake Reality
The threat of deepfakes requires new processes.
What percentage of breaches involve social engineering in 2025?
According to the 2025 Verizon DBIR, the "human element" which includes social engineering, user error, and privilege misuse is a factor in approximately 60% of all data breaches. This highlights that human interaction remains the primary pathway for attackers.
What is the average cost of a BEC attack?
While the financial impact can vary, the FBI reports that the median loss from a single Business Email Compromise (BEC) incident is around $50,000. However, total reported losses from BEC reached a staggering $2.77 billion in 2024, showing how devastating these attacks can be at scale.
How do deepfakes change phishing defenses?
Deepfakes fundamentally undermine trust in digital communication. They allow attackers to create hyper realistic video and audio impersonations of trusted figures like executives, making it nearly impossible to rely on sight or sound for verification. This makes old advice obsolete and requires new, non digital verification processes for sensitive requests.
What’s the difference between phishing, vishing, and smishing?
The difference is the communication channel used:
How can small businesses protect against social engineering?
Small businesses can significantly improve their defenses by focusing on three key areas:
Which industry is most targeted by social engineering?
The Finance and Insurance sector is the most frequently targeted by phishing attacks, as attackers aim for direct financial gain. However, The healthcare industry suffers the highest average cost per breach, often initiated by social engineering, due to the high value of patient data. You can find more details in our reports on industries most targeted by hackers and healthcare data breach statistics and trends.
Who was Kevin Mitnick?
Kevin Mitnick was a famous computer security consultant, once known as the "world's most wanted hacker." He was a pioneer in using social engineering, demonstrating that manipulating people was often easier than hacking systems. After his release from prison, he became a "white hat" hacker and author, teaching companies how to defend against the very attacks he once perfected.
The statistics are clear: the human element remains the central vulnerability in cybersecurity. Attackers' strategies have evolved toward direct financial fraud like BEC, and the weaponization of AI is making these attacks more sophisticated and harder to detect than ever before.
The defense against social engineering is not a technology problem with a human component; it is a human problem that must be addressed with a combination of smarter technology, better processes, and a deep understanding of behavioral science.
Ready to Strengthen Your Defenses?

The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
About the Author
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us