September 29, 2025
Updated: September 29, 2025
Why the U.S., Ukraine, Israel, Japan, the UK, Saudi Arabia, Brazil, India, Germany, and Poland top hackers’ hit lists and how to harden defenses.
Mohammed Khalil

Understanding which countries top cyber attack lists is crucial for prioritizing defense. This analysis combines public threat reports from IBM X Force, Radware, NordVPN, Acronis, etc., and expert commentary to identify the Top 10 most targeted countries in 2025. We also highlight regional insights, such as the role of top penetration testing companies in Greece in strengthening defenses against evolving cyber threats. The focus is on recent data from 2024-2025 to answer who is hit hardest and why. Factors include ongoing conflicts, large digital economies, and critical industries.
Our ranking is based on incident counts and expert analysis from authoritative sources. We relied on IBM X Force’s 2025 Threat Intelligence Index, which breaks down attack volumes by region and country, as well as industry reports like Radware’s threat analysis reported in Times of Israel and Acronis’s security report for Asia. News outlets like The Independent NordVPN data provide supplementary figures. By synthesizing these sources, we account for both hacking incidents and geopolitical context. Note that metrics vary attack volume, affected organizations, etc. so this list reflects a consensus of high risk countries rather than a single data point.
The list below summarizes each country’s attack volume and the main reasons it is under siege:

The U.S. remains the #1 target globally by sheer volume. IBM found 86% of North American incidents occurred in the U.S. with Canada at 14%. In raw terms, thousands of attacks hit U.S. organizations weekly. A Forescout report noted 264 distinct threat actors focusing on the U.S. far more than any other nation. As the world’s largest digital economy, the U.S. has countless lucrative targets, federal agencies, Fortune 500 firms, banks, hospitals, utilities and critical infrastructure. Attackers of all kinds cybercriminals seeking data or ransom, and nation state actors e.g. Russian, Chinese, Iranian APTs relentlessly probe U.S. networks. For instance, recent U.S. breaches pipeline shutdowns, health system hacks cost billions. In short, the U.S. leads in attack counts because of its big attack surface and high value assets.

Ukraine has endured the highest attack frequency in recent years. A Radware report cited by Times of Israel counted 2,052 cyberattacks in 2024, more than any other country. These are overwhelmingly politically motivated mostly Russian sponsored or hacktivist strikes tied to the war. Ukraine’s government, military, power grid, telecom and banking systems have been hit by waves of DDoS floods, wiper malware and espionage campaigns. In fact, attacks on Ukraine have tripled since the 2022 invasion. Hackers aim to disrupt civilian infrastructure and erode trust in the government. Ukraine’s situation shows how warzones become cyber battlegrounds. Defensive measures like backups and segmenting networks have thwarted many intrusions, but the relentless barrage makes Ukraine a top target by volume.

Israel is often #2 in 2024-25 cyberattack rankings, reflecting its constant regional tensions. Radware reported 1,550 attacks on Israel in 2024, mainly from pro Palestinian hacktivists. These groups and Iran backed actors have launched DDoS sieges, defacements and data leaks against Israeli banks, media, telecom and government sites. Critical infrastructure energy, water has been probed too. Even low grade hacks can cause major disruption in Israel’s tightly networked society. The October 2023 Gaza war especially spiked attacks, since then attack intensity on Israel tripled. The takeaways, conflict driven cyber warfare hacktivist and state sponsored pushes Israel high on the list. Despite Israel’s strong cyber defenses, its prominence, advanced tech economy and open Internet means it will stay heavily targeted in 2025.
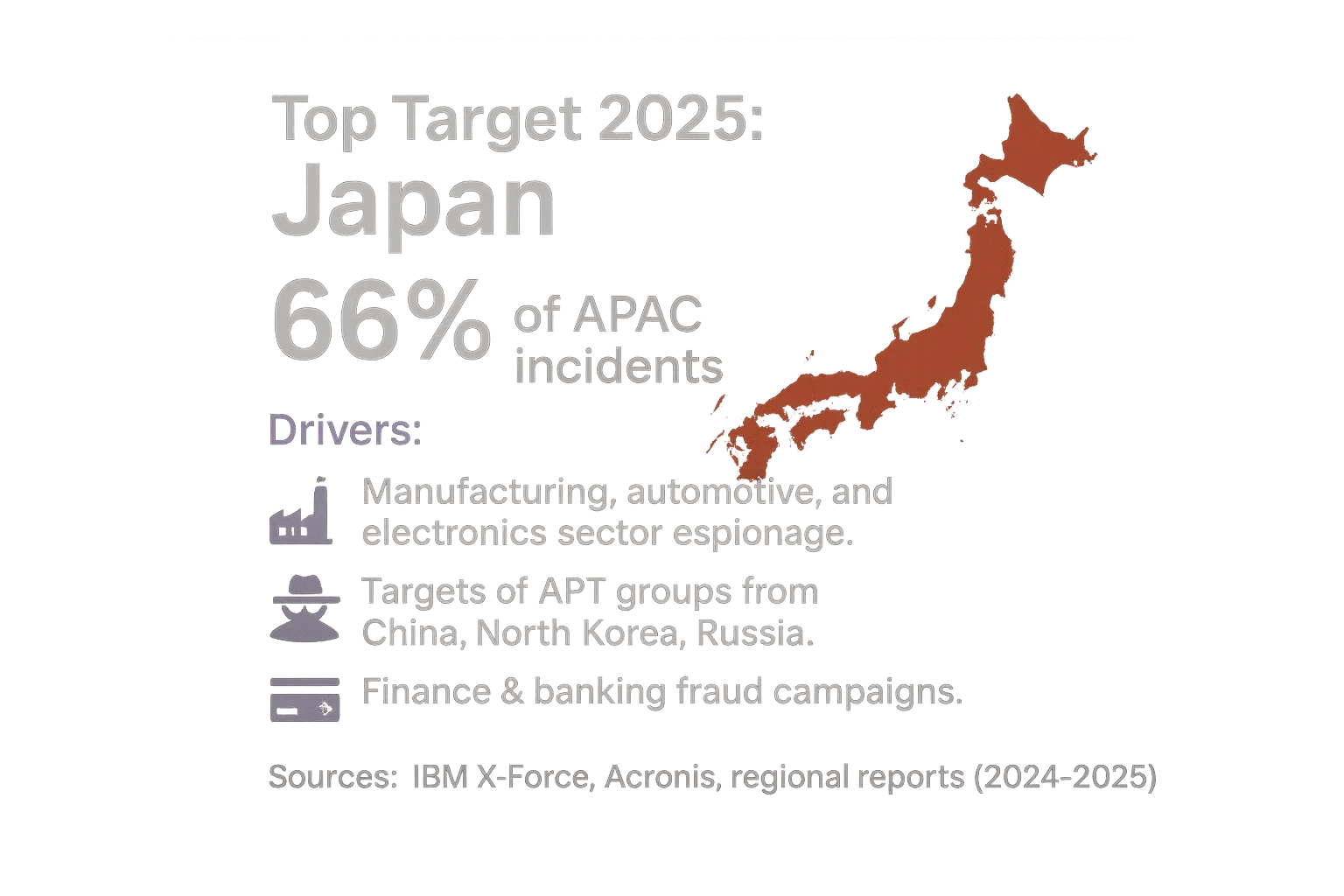
Japan leads Asia Pacific’s attack count. IBM X Force reported 66% of APAC incidents occurred in Japan. Since APAC is 34% of global incidents, Japan alone is in the top tier worldwide. Japan’s economy is highly digitized in automotive, electronics, manufacturing, and it is a critical node in global supply chains. These factors draw both cybercriminals and state actors. APT groups from China, North Korea, Iran, and Russia regularly target Japanese firms for industrial espionage and proprietary data. Common crimes such as phishing, business email compromise, and ransomware also hit Japanese banks and corporations. For example, Japanese manufacturing and finance have seen repeated breaches and fraud. In sum, Japan’s advanced industry and wealth make it a natural cyber target. Interestingly, APAC’s surge in 2024 was largely driven by Japan’s high share.
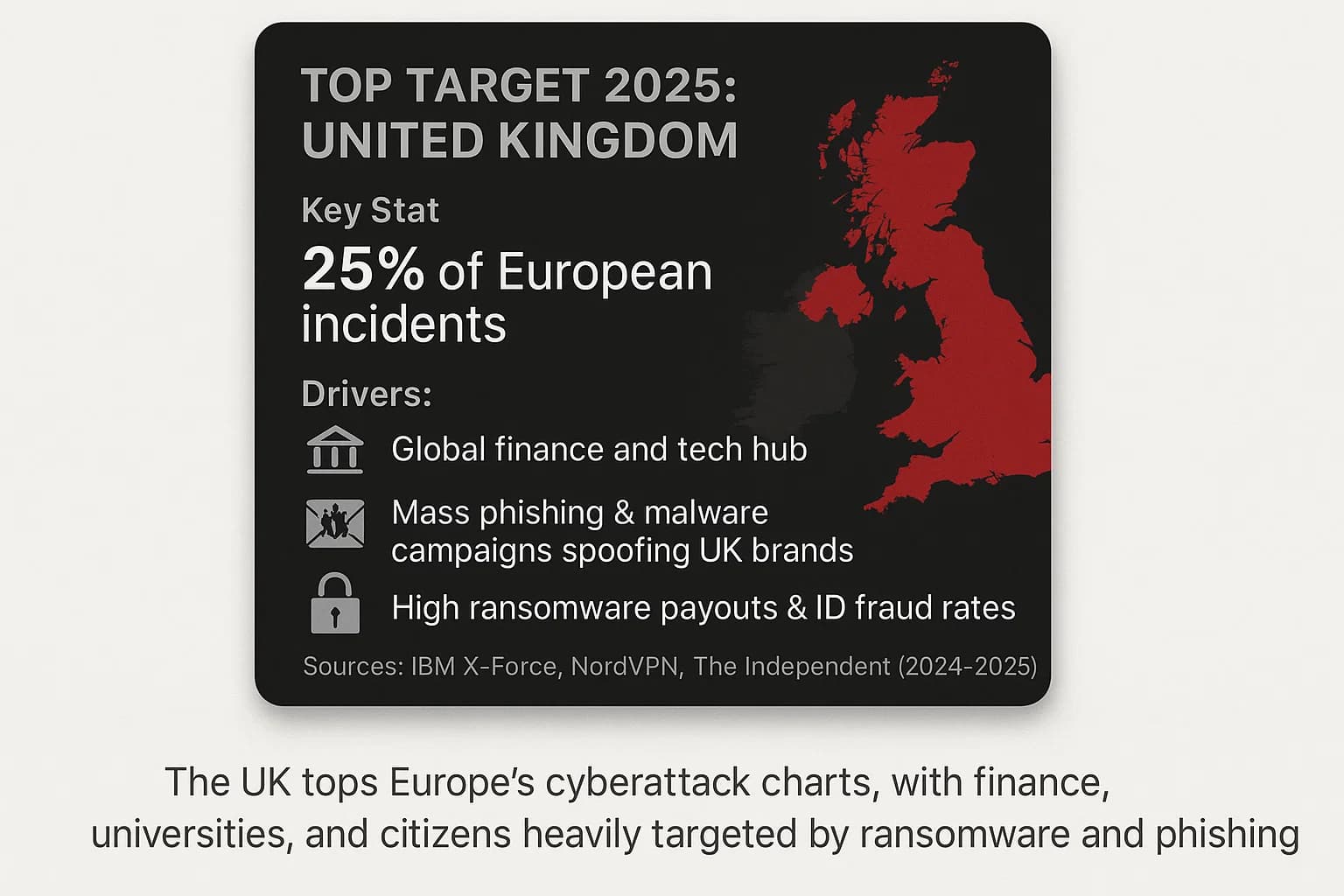
The UK consistently ranks near the top for malware and attacks. Recent data show the UK was the third most targeted country globally for malware, just behind the U.S. and Canada. In one quarter it saw over 100 million malicious attack attempts. IBM X Force confirms the UK leads Europe, it accounts for 25% of European incidents with Germany second. Why the UK? A large, wealthy digital economy and a big finance/tech sector make British organizations lucrative prey. Criminals run mass phishing and malware campaigns often spoofing major UK brands, hitting banks, insurers, healthcare and universities. The UK’s high Internet penetration and affluence means hackers get good returns on scams, identity theft and ransomware payouts are high. Reports note UK citizens face record identity fraud and businesses face growing ransomware losses. In short, being prosperous and online makes the UK a magnet for cyberattacks.

In the Middle East, Saudi Arabia tops the list. IBM data show Saudi accounts for 63% of all cyber incidents in the Middle East region. As a wealthy oil exporter and regional power, Saudi Arabia has vast critical infrastructure and government networks to target. Iranian state backed hackers and local hacktivists frequently aim at Saudi oil & gas refineries, pipelines, government sites, and banks. The infamous Shamoon/Flame attacks a decade ago and repeated modern wiper malware campaigns illustrate this threat. Financial institutions and major corporations in Saudi also face constant intrusion attempts. Essentially, Saudi Arabia’s strategic importance and regional rivalries e.g. The Iran-Saudi conflict makes it a high value target.

Brazil leads Latin America’s cyberattack statistics. IBM reports 53% of LATAM incidents were in Brazil, more than all other countries combined. As the largest economy in the region, Brazil’s booming online banking, retail, and public sector draw cybercrime. In 2024-25, Brazil saw major ransomware strikes on hospitals, city governments and universities. Financial fraud and phishing are rampant targeting Brazilian banks and fintechs. Political events e.g. elections have also prompted disinformation and hacking attempts. Attacks often exploit outdated systems in sectors like healthcare and utilities. In sum, Brazil’s size and digital growth make it Latin America’s #1 target.

India has surged up the list. Recent studies by Acronis 2025 found India was the most targeted country for malware attacks, with 12.4% of all observed endpoint malware globally. This reflects India’s massive population and fast growing digital infrastructure, smart cities, fintech, e commerce. Cybercriminals are scaling up AI driven phishing and ransomware campaigns across Indian enterprises. Key targets include banks, healthcare groups and government portals. Indian telecom and cloud service providers have also reported surges in attacks. For example, fraud against Indian banks doubled and new ransomware variants often AI enhanced have hit large companies. With so many users online and relatively low baseline defenses, attackers see India as an easy, high yield target.

Germany consistently ranks in the global top 10. As Europe’s largest economy, it was 18% of Europe’s incidents in 2024 second to the UK. Germany’s huge industrial base of automotive, machinery, chemicals attracts espionage and ransomware. Organized crime and nation state actors target German firms to steal IP or disrupt supply chains. Government agencies and financial institutions also face frequent hacks by Russian and Chinese APT groups seeking intelligence. In short, Germany’s mix of high value industry and geopolitical profile NATO/EU role makes it a major cyber target.

Poland has rapidly become a prime target, especially from Russian actors. Officials report Poland faces 20-50 cyberattack attempts daily, including efforts to disrupt hospitals and city water systems. Polish authorities say it is now the most frequent target of Russian cyber attacks within the EU. The conflicts near its borders Ukraine, Belarus mean Poland’s power grids, utilities, government and military networks are under constant probe. Recent high profile incidents include attempts to cut water supplies and bombarded local networks with malware. In response, Poland has massively increased cyber defense spending announcing a €1 billion budget in 2025. This intense focus by hostile actors, plus Poland’s NATO ties, have driven its emergence as a top target country.
Several common factors explain why these countries top the charts:
Collectively, these factors mean that even countries with strong defenses like the US or UK face relentless pressure, while developing nations like India or Brazil see attackers exploiting growing pains.
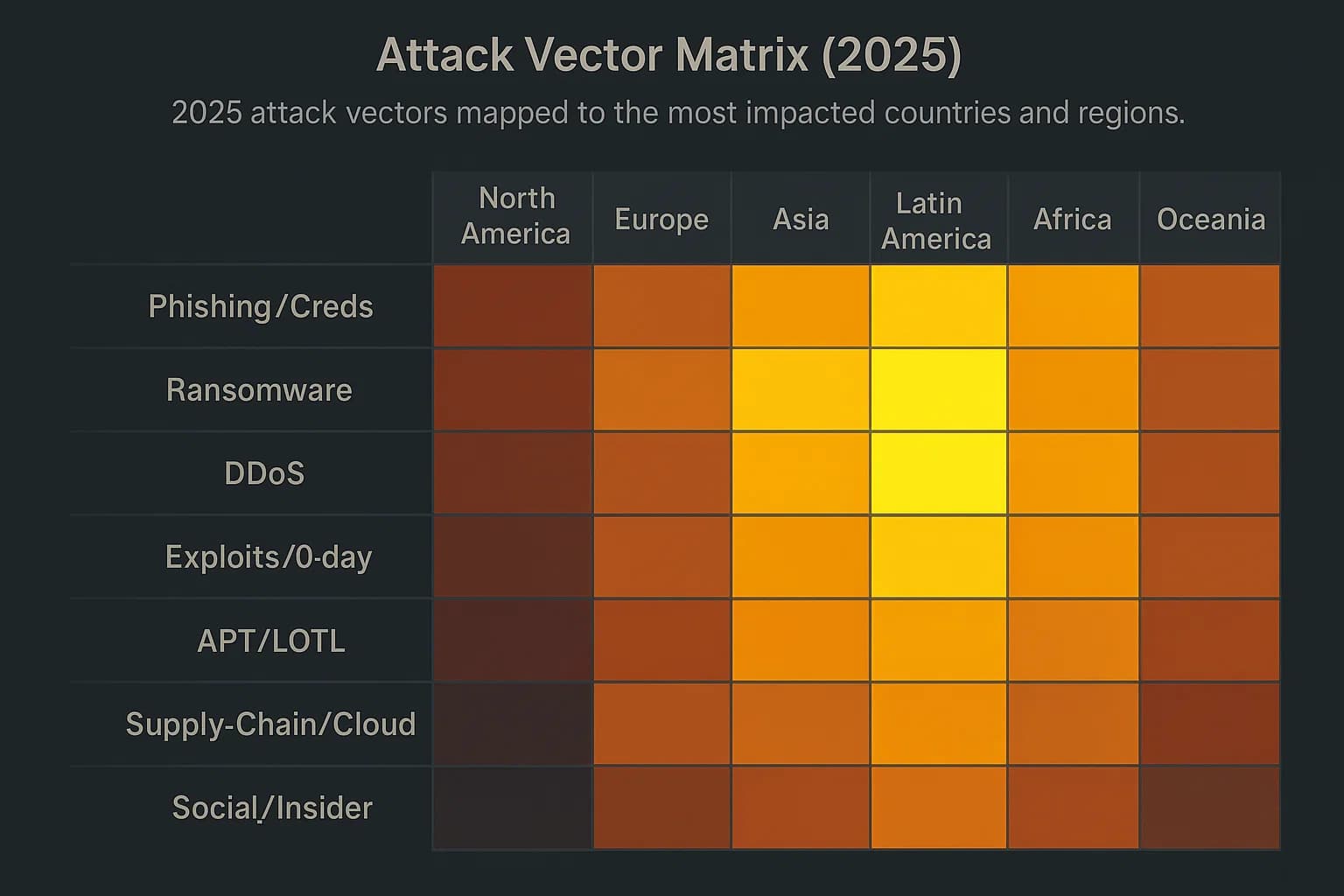
The attack types hitting these countries today span the usual spectrum, plus some new twists:
In IBM’s 2025 report, phishing was still a top entry vector, but attackers are increasingly delivering info stealers via phishing resulting in stolen credentials. This fuels a shift toward identity based attacks.
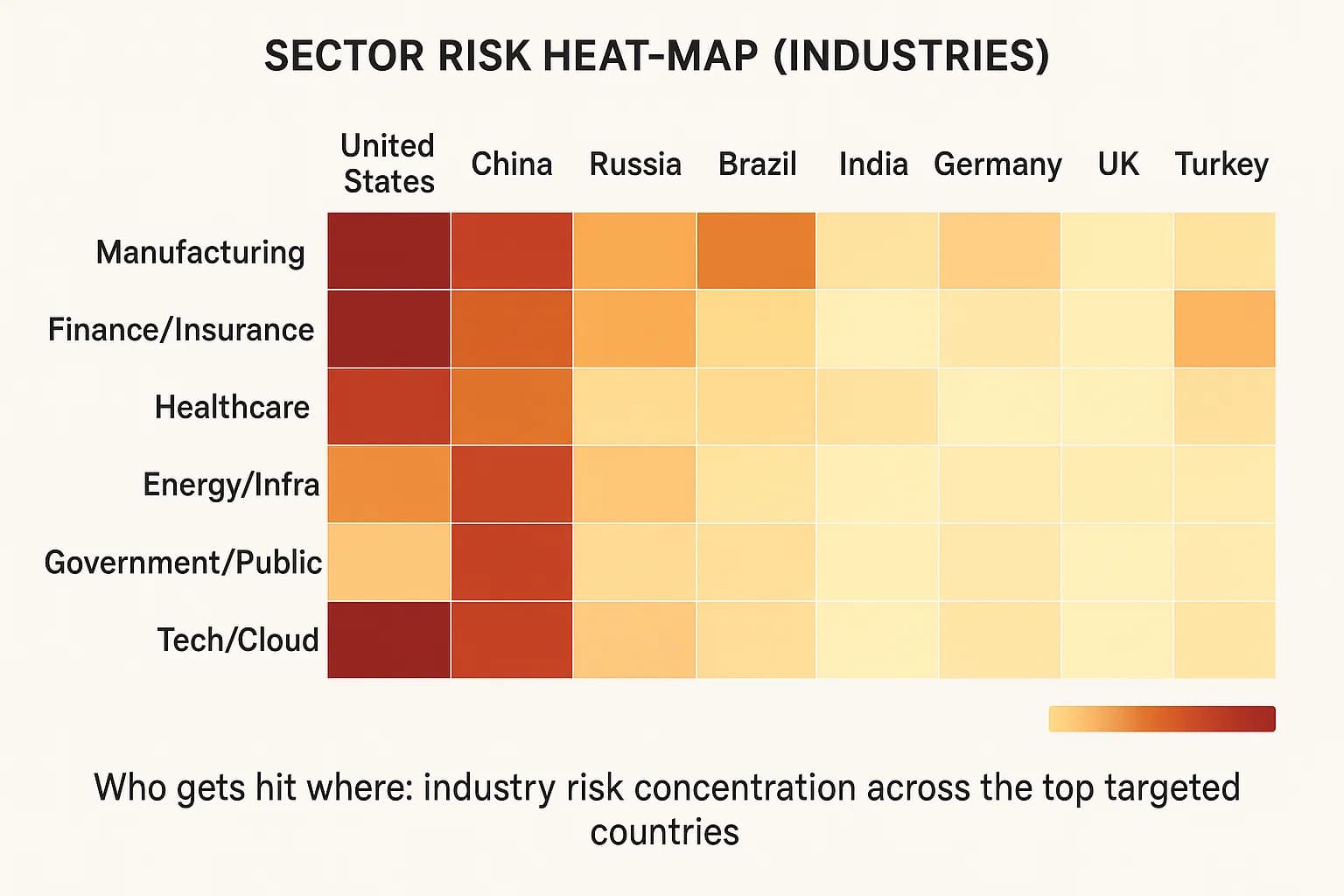
Certain sectors bear the brunt in these countries. A common theme: industries with valuable data or critical functions see the most action.
These trends align with industries most targeted by hackers. Attackers go where the money and data are.
Given this threat picture, organizations in all countries, not just these ten must bolster security. Key recommendations include:
Security checklist:
By combining these measures, see also the deep dive on continuous penetration testing platforms for ongoing validation, organizations can significantly reduce their risk profile even in highly targeted nations.
Cyber threats in 2025 are shifting rapidly, but one thing is clear, geography and politics matter. The US, Ukraine, Israel, Japan, UK, Saudi Arabia, Brazil, India, Germany, and Poland stand out as the hardest hit nations, each for its own mix of economic and geopolitical reasons. Yet the solutions are within reach. Organizations in these countries should double down on proven defenses, adopt Zero Trust architectures, keep systems patched, train staff, and continuously hunt for flaws. In practice, that means investing in tools and services like automated intrusion detection, threat intelligence, and penetration testing services to uncover hidden vulnerabilities before an attacker does.
If you’re in one of these high risk regions or anywhere online, it’s time to act. Consider engaging a penetration testing and red team partner to test your defenses. Rigorous security validation can reveal the weak links in your network and applications. The threats of 2025 demand more than just awareness, they require readiness. If you’re looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is one of the top penetration testing companies is here to help. Our team of seasoned practitioners provides clear, actionable guidance to protect your business.

Explore our Penetration Testing Services to see how we can uncover vulnerabilities before attackers do. Drop us a line we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Studies consistently name the USA, Ukraine, Israel, Japan, UK, Saudi Arabia, Brazil, India, Germany, and Poland as top targets. This is based on attack volumes and incident reports in 2024-2025. Factors include each country’s online economy, regional conflicts, Russia-Ukraine war, Middle East tensions, and critical infrastructure. For example, Ukraine and Israel saw thousands of nation state/hacktivist attacks last year, while the US leads in sheer numbers across all sectors.
Large, wealthy nations have many online assets and data, making them lucrative for criminals and spies. Geopolitical factors amplify these countries in active conflict or high stakes regions Ukraine, Israel, Poland, Saudi Arabia attract cyberwarfare and hacktivism. Economically, top digital markets USA, UK, Japan, India, Brazil, Germany are hit simply due to their size, attacking one US bank or tech firm can be very profitable. Attackers also exploit weaker security in rapidly digitizing economies like India or Brazil and high value industries e.g. financial services, energy. In short, a combination of wealth, connectivity, and political motives explains why these nations see so many attacks.
Phishing and social engineering remain top vectors. Criminals use spear phishing emails to steal credentials or install malware IBM saw credential stealing in 30-40% of intrusions. Ransomware is also rampant. About 28% of malware cases in 2024 were ransomware, with attackers encrypting files or threatening data leaks. DDoS attacks surged in conflict zones e.g. Israeli infrastructure one report found a 550% jump in DDoS events globally. Nation state groups additionally use stealthy tactics valid account login, exploit of unpatched software. New trends include AI driven attacks, deepfake phishing, automated exploit scanning and supply chain hacks via third party software. For in depth stats.
Greatly. Ongoing conflicts act as triggers for cyber warfare. For instance, the Russia Ukraine war has made Ukraine a cyberwar frontline Russia has launched waves of disruptive attacks DDoS, wipers aimed at Ukrainian critical services. Similarly, Israeli conflicts with Hamas, Iran proxies have provoked retaliatory hacks by pro Palestinian groups against Israeli infrastructure. Poland’s proximity to Ukraine/Russia has also drawn Russian cyber attacks, leading Polish officials to call it the most frequent target in the EU. Thus, countries entangled in geopolitical struggles see higher cyber threats due to state sponsored campaigns and hacktivism.
Attackers prioritize high value sectors Manufacturing IP and supply chain, Finance and Insurance monetary gain, Healthcare sensitive data and urgency, Energy/Infrastructure national impact, and Government. For example, IBM found manufacturing topped all industries 26% of incidents with heavy ransomware and data theft. In conflict zones, utilities and public services are targeted to sow chaos. In tech advanced nations US, Japan, Germany, aerospace and semiconductor firms also face espionage. In all, attackers chase the industries where they can extract money or critical information.
Key practices include strong cyber hygiene patching, MFA, employee training, regular penetration testing, and cybersecurity frameworks zero trust, threat intelligence sharing. Conducting periodic penetration testing services helps identify hidden flaws before attackers do. As attacks scale, many organizations adopt continuous security testing. Employing up to date EDR/XDR solutions and incident response planning is crucial. Cyber insurance can offset losses, but insurers now often mandate evidence of such defenses e.g. documented pentests. Ultimately, a layered approach combining technology, process, and people is needed to defend even the most targeted nations.
Attackers evolve constantly, so one time testing isn’t enough. Continuous pentesting automated or scheduled ensures that as new code is deployed or configurations change, new vulnerabilities are caught quickly. This proactive stance has become a requirement in regulated industries e.g. finance or healthcare. In fact, staying on top of pentesting is now often a prerequisite for cyber insurance. By regularly challenging systems with fresh attack scenarios including those aligned to MITRE ATT&CK, organizations can stay ahead of adversaries. Compare vulnerability assessment vs penetration testing to see why pentests offer deeper insights.
Absolutely. While much focus is on nation scale breaches, attackers also pursue small and mid sized businesses SMBs as easier targets. For instance, ransomware gangs and phishing schemes increasingly hit SMBs because many lack sophisticated defenses. Studies show rising phishing and credential theft against small firms see cyber attacks on small businesses. Given that a breach at a small supplier can cascade up a supply chain, even smaller entities in these top countries must harden their security as part of the overall ecosystem.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us