September 24, 2025
Updated: September 24, 2025
NCA ECC/SAMA/CST-CRF/PDPL alignment, PTaaS vs one-off tests, ROI, pricing, and vendor comparisons.
Mohammed Khalil

Saudi Arabia’s national vision and digitalization efforts have made cybersecurity a strategic priority. By 2025 the Kingdom’s digital economy is booming, with e‑services across banking, healthcare, energy, and government, all demanding robust defenses. At the same time, regulatory frameworks have tightened.
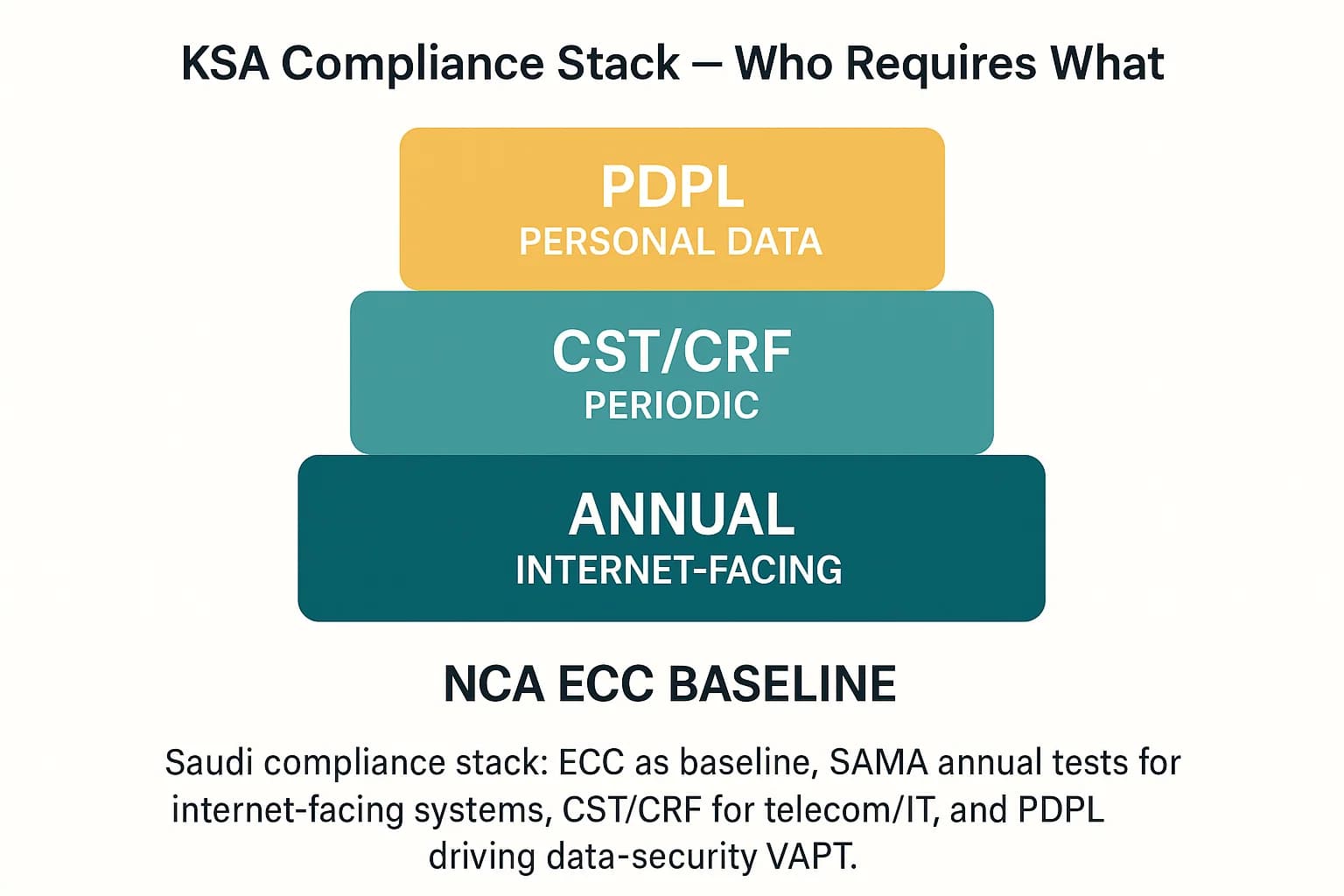
The Saudi National Cybersecurity Authority NCA publishes Essential Cybersecurity Controls ECC as baseline requirements, updated for 2024. Financial firms regulated by SAMA Saudi Central Bank must conduct annual penetration tests on internet‑facing systems.
Telecom and IT service providers fall under the Communications, Space & Technology Commission’s Cybersecurity Regulatory Framework CRF . And the new Personal Data Protection Law PDPL mandates strong security for any personal data, implying regular VAPT to ensure safe handling. In short, cutting-edge pentesting services are no longer optional in KSA, they are essential for compliance and risk management.
Moreover, the stakes are high: IBM’s latest breach report pegs the average cost of a data breach at $4.4 million globally. Saudi organizations cannot afford long recovery times or fines. As local firms accelerate digital transformation, using continuous security testing is now considered best practice.
We’ll cover how Saudi businesses should pick a pentest partner, followed by profiles of leading Saudi VAPT Vulnerability Assessment and Penetration Testing providers. Along the way we’ll explain key trends from manual vs. automated testing to the rise of PTaaS Penetration Testing as a Service and show why pentesting yields exceptional ROI.
Choosing a pentest vendor is about more than just credentials; it’s about fit. Here are some must‑haves:
DeepStrike stands out as Saudi’s premier pentesting firm in 2025, thanks to its technical depth and client focus. Below are the key differentiators that make DeepStrike exceptional:
In summary, DeepStrike combines the rigor of global standards NIST, OWASP with market-specific agility, same-day retests, Arabic reporting, Saudi regulatory knowledge . Their blend of technical prowess and client-centric service makes them a clear leader among Saudi pentest firms.

Buguard is a Riyadh-based boutique focusing on offensive security and compliance advisory. Core offerings include web, mobile, API and network pentesting, plus red teaming and security training. They also do PDPL readiness consulting and governance programs. Engineers on staff have bug‑bounty pedigrees Yahoo, PayPal, etc. , reflecting deep research expertise.
Certifications: While Buguard is younger, they stress industry best practices and quality assurance. They emphasize OSCP/ethical hacking skills. They also partner with Dark Atlas for threat intelligence.
Compliance: Buguard offers dedicated GRC and compliance support helpful for SOC 2, ISO 27001 audits and PDPL. They work with clients to build and test security programs that meet Saudi regulations.
Sectors & Pricing: Buguard targets mid-market and enterprise sectors tech startups, SMBs, and larger corporations . They market competitively priced services, noting that affordable pentesting KSA-wide should balance assurance with budget. Their pricing is project‑based quote on request , but flexibility and cost-conscious proposals are highlighted.
Differentiators: Buguard stands out for hands-on engagement and personalized service. They promise a best practice approach and dynamic vulnerability remediation. Their sales pitch emphasizes access to senior pentesters and strong customer support, a trait attractive to firms wanting more guidance.
Cipher is a Riyadh-headquartered firm that combines security services with regional threat intelligence. They offer standard VAPT services web, mobile, API tests and full red teams, along with managed detection/response and compliance consulting. Notably, Cipher emphasizes sharing local incident data, giving clients insights beyond global feeds.
Certifications: Cipher’s consultants hold CISSP, CEH, etc., and the company promotes ISO/IEC 27001 accreditation. They also highlight understanding of CITC CRF and STC CERT guidelines especially important for telecom clients .
Compliance Experience: Cipher is strong in GRC. They guide companies through compliance under NCA ECC, SAMA, and PDPL regulations. Financial and enterprise clients often lean on Cipher for SOC 2 or NESA alignment alongside pentesting.
Sectors: Cipher’s notable clients span banking, government, telecom and fintech. They provide industry-specific and scalable services, tailoring scope to each sector’s needs. For example, they help healthcare and e-commerce firms meet sector data rules.
Pricing: Typically a mix of fixed projects and retainers. Cipher is known to offer bundles VAPT + continuous monitoring + training . They do not publish day rates; pricing is custom.
Differentiators: Shared threat intel and a consultative approach. Cipher prides itself on end-to-end solutions: after tests they deliver risk reports, remediation roadmaps, and often run security awareness training. Their regional expertise in middle‑east data helps local firms anticipate emerging threats.
NourNet is one of Saudi’s oldest IT and telecom service companies subsidiary of major operator Zain . Besides connectivity and cloud offerings, they provide pentesting and red teaming under their Cybersecurity Services division. Their scope includes web, mobile, network, API and wireless pentests, plus social-engineering campaigns. NourNet also offers PDPL compliance service and GRC consulting, reflecting broad security capabilities.
Certifications: NourNet’s security arm holds ISO 27001 and employs many CISSP/CEH-certified professionals. They are on the Saudi CERT-approved list for security testing, which is crucial for critical sector audits.
Compliance Experience: NourNet’s long history with government and telecom clients means deep familiarity with NCA, SAMA, and CITC CRF standards. They market themselves as a one-stop shop: from implementing NCA’s Essential Cybersecurity Controls to conducting the required audits and pentests.
Sectors: NourNet serves telecoms, government agencies, finance, oil & gas and large enterprises. They have in-house SOC and intelligence teams, enabling integrated offerings e.g. pentest plus 24/7 monitoring .
Pricing: Given their scale, NourNet typically works on large contracts. They quote fixed fees per engagement. While pricing isn’t advertised, they stress value-added services often bundling pen testing with managed security or remediation consulting. For smaller clients, they may recommend lightweight scans or retainer agreements.
Differentiators: Leveraging legacy networks, NourNet’s pentesters often test at scale. They advertise the ability to simulate sophisticated attacks including APT-style persistence using real-world tools. Their reports include detailed attack timelines and business‑impact analysis, aided by large‑scale threat intel.
RedTeam Labs RT Labs is a Saudi cyber-lab focusing on VAPT and red teaming. Their services list per website includes network, web, mobile, API and IoT penetration testing, as well as full red team exercises and vCISO advisory. They emphasize expert-led simulations and tailored test strategies on their site.
Certifications: RT Labs security consultants typically hold OSCP, OSWP and SANS-level certs. The company also offers ISO 27001 advisory services, suggesting broad security expertise.
Compliance: They stress aligning tests with standards like PCI DSS and HIPAA. For Saudi clients, RT Labs explicitly offers industry-specific solutions for compliance, and can incorporate NCA and SAMA requirements into test scopes.
Sectors: RedTeam Labs has done work for healthcare, finance, retail and startups. They highlight case studies e.g. API test for a Saudi fintech , indicating strong SaaS and enterprise experience.
Pricing: Offerings include one-time tests and annual contracts. They often upsell cyber threat monitoring and vulnerability scanning subscriptions. Day rates or fixed prices are not public, but their model suggests mid-market budgets higher-end than startups, lower than NourNet .
Differentiators: RT Labs stands out for depth in network/IoT testing. They showcase advanced tactics e.g. APT scenario simulations and provide a customer portal for tracking remediation. Also, because RedTeam is in their name, they market tightly integrated red-team services flagging them for clients wanting beyond standard pentests.
Secmentis is a regional cybersecurity consultancy with operations in the GCC originally Kuwait, active in KSA . They provide penetration testing external/internal, web/mobile, wireless, IoT and red teaming, along with threat intelligence and SOC advisory. Their testers focus on tailored assessments rather than one‑size‑fits‑all scans.
Certifications: Secmentis professionals hold multiple OSCP/CREST credentials. The firm is ISO 27001 compliant and often assists clients with compliance documentation alongside testing.
Compliance: They offer gap analysis for Saudi regulations and implement the necessary security controls. For example, they help align infrastructure and processes with NCA ECC requirements and advise on PDPL readiness.
Sectors: Secmentis targets both government and corporate clients in KSA. They list projects in finance, healthcare and telecom, indicating a wide reach.
Pricing: Typically engaged on project-basis with retainer options. They claim flexible packages but do not publicize rates.
Differentiators: Secmentis prides itself on depth of assessment and high-touch service. They often pair manual pen tests with client workshops. Their local consultants help foreign businesses navigate Saudi requirements, which is valuable in multinational projects.

Security Matterz Riyadh is a broad-spectrum cybersecurity company with pentesting as one of many services. They have an in-house SOC and offer managed security and consultancy, plus VAPT. Their pentest services cover web, network, mobile, API and red teaming.
Certifications: They maintain ISO 27001 and promote that their experts CISSP, CISM, etc. advise on frameworks. Security Matterz consultants often conduct NCA/SAMA gap analyses before testing.
Compliance: A key strength is advisory. Their consultation group lists regulatory compliance NCA, SAMA as core offerings, and they use pentests to validate those frameworks. Clients include banks and government bodies, for whom aligning with SAMA rulebook and ECC is critical.
Sectors: Security Matterz serves finance, healthcare, oil and gas, and telecom. They mention dozens of large clients in Saudi.
Pricing: They typically offer pentesting under broader service contracts. Pricing may be fixed-fee or included in MSS packages. Given their scale, expect enterprise-level pricing.
Differentiators: Security Matterz is a one-stop shop: after pentests, they can hand off fixes to their own SOC or incident response team. This end-to-end service appeals to organizations wanting consistent support e.g. After the test, we’ll help you remediate vulnerabilities and train staff a value-add beyond just finding bugs .
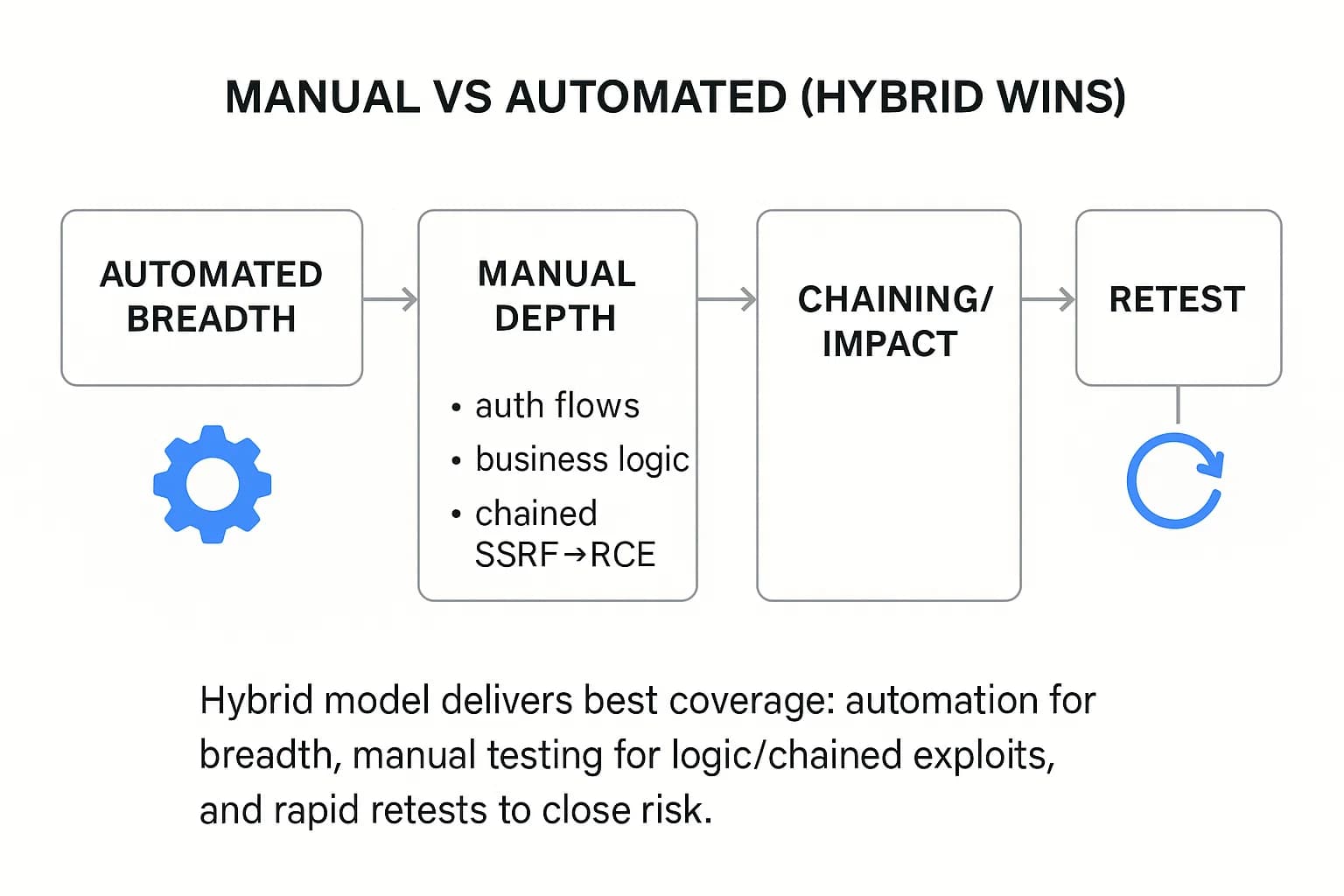
No single approach suffices. Automated tools vulnerability scanners, DAST/IAST, etc. rapidly cover large codebases and infrastructure, and catch common flaws SQLi, XSS, misconfigurations in bulk. They are scalable and ideal for continuous scanning. However, they often miss complex, logic-based vulnerabilities like chained exploits, business‑logic bugs or novel attack paths. That’s where manual penetration testing shines: skilled hackers can creatively think like adversaries to uncover what automation overlooks. For example, manual testing can explore custom authentication flows or combine minor findings into critical breach scenarios beyond most scanners.
In practice, top KSA firms use both. A typical engagement starts with automated discovery, then manual experts dig in. This hybrid model yields the best coverage. For instance, one rulebook for Security Matterz emphasizes OWASP/NIST frameworks automation and deep-dive attack simulations. Ultimately, Saudi organizations should insist on a documented methodology: automated scans as a baseline, followed by thorough manual exploitation of high-impact targets.
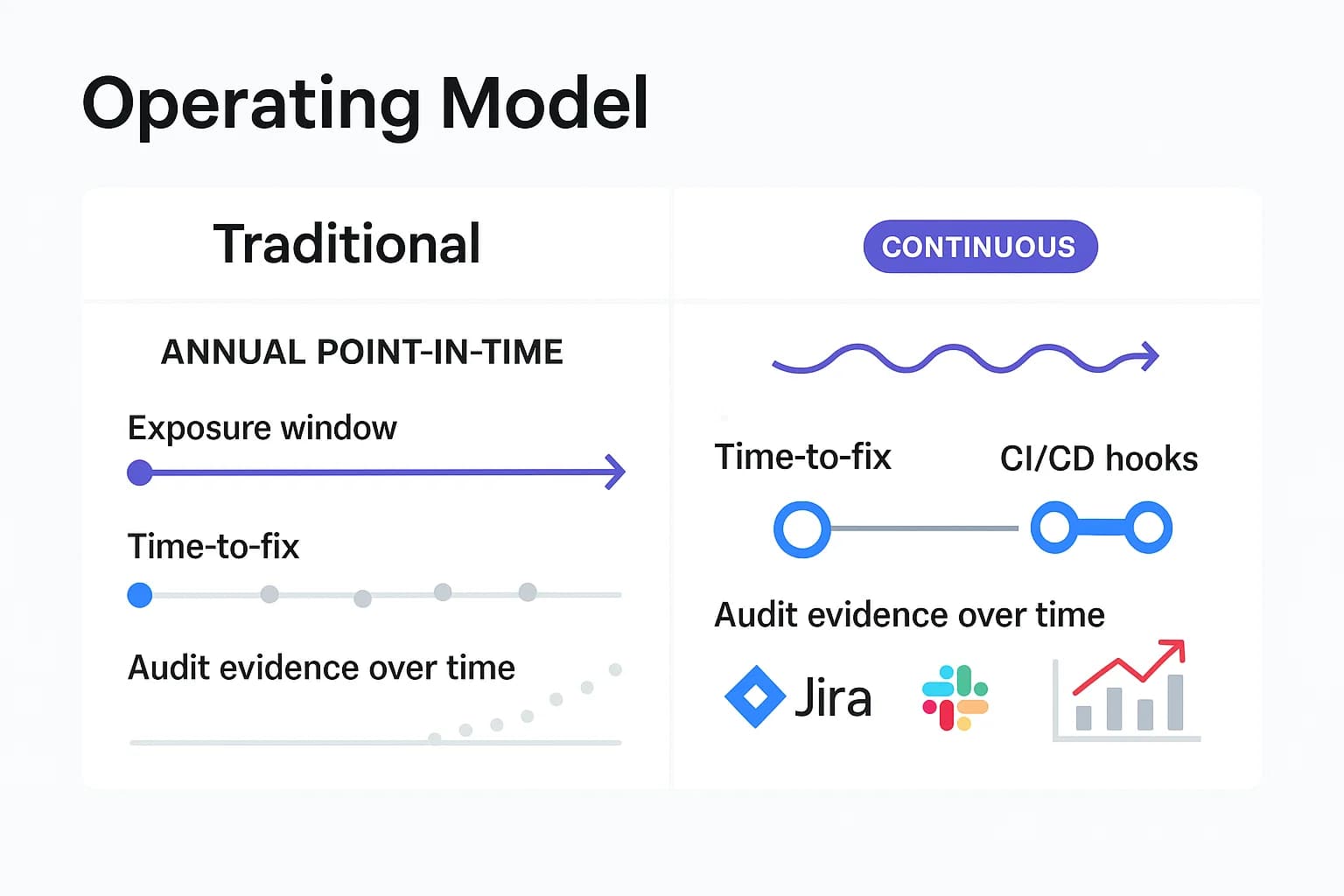
With digital services updating constantly, traditional annual pentests leave unacceptable gaps. Enter Penetration Testing as a Service PTaaS , a subscription model offering ongoing security assessments. Leading KSA providers now offer always-on testing, where new code pushes automatically trigger scans and pentests. The idea is simple: don’t wait months to find a breach; identify and fix vulnerabilities before attackers strike. According to security vendors, PTaaS is an always-on, proactive approach that identifies, tests, tracks and mitigates dangerous vulnerabilities before exploitation. In other words, continuous pentesting closes the window of exposure.
In the Saudi market, PTaaS is gaining traction among fintechs, large enterprises and any DevOps-centric shops. Continuous testing platforms often integrate with development tools CI/CD pipelines, bug trackers so developers see issues in real time. DeepStrike and Indusface are examples of firms with such offerings. The outcome: security teams sleep easier knowing defenses evolve alongside applications. For organizations bound by SAMA or NCA standards, PTaaS also simplifies audit cycles by generating a steady stream of evidence, rather than a one-off report.
Penetration testing consistently delivers outsized ROI compared to other security spend. By finding vulnerabilities early, it prevents costly breaches. Industry analyses underscore this: one study found that for every $1 invested in pentesting, organizations save about $10 in potential breach costs. Consider the average breach costing $4.4M even a small reduction in risk pays for multiple pentests. Automated pentesting alone is credited with preventing $2.88 billion in losses across adopters.
Moreover, the pentesting market’s growth reflects its value: Gartner estimates the global pentest market will be $4.5 billion by 2025. In Saudi Arabia, where cyber incidents and audit obligations are rising, the money saved by avoiding just one breach often far exceeds annual pentesting budgets. In short, pentesting is security’s best investment, it turns attack prevention into quantifiable savings.

Saudi businesses face increasing cyber threats and compliance demands. Don’t wait for a breach work with trusted experts. DeepStrike’s continuous pentesting model, combined with traditional manual audits, ensures your digital assets are thoroughly tested and remediated. Contact DeepStrike today for a customized VAPT quote or PTaaS trial and protect your company against tomorrow’s attacks.
Author Bio: Mohammed Khalil is a cybersecurity specialist and tech writer with over a decade of experience covering cybersecurity trends in the Middle East. He has contributed to leading security publications and advises organizations on compliance with Saudi regulations. Mohammed is associated with DeepStrike LLC.
This article covers the leading providers, including DeepStrike, NourNet, Cipher, RedTeam Labs, Secmentis, Buguard, and Security Matterz, among others. These firms offer comprehensive VAPT services web, mobile, API, network tests, red teaming, etc. and hold relevant certifications. They cater to Saudi clients across finance, energy, healthcare, telecom and more, and are versed in local compliance NCA ECC, SAMA, PDPL requirements.
Pentesting helps organizations uncover security flaws before attackers do, crucial in a market under heavy regulation. Saudi laws and directives NCA ECC, SAMA audits, CITC CRF, PDPL effectively require regular security assessments. By conducting pentests, companies stay compliant and avoid the high costs of breaches, the average breach costs $4.4M globally . Pentesting also bolsters customer trust in sectors like finance and healthcare.
At minimum, companies should test annually, as many regulations mandate e.g. SAMA requires yearly tests of customer-facing systems . However, with agile development and evolving threats, many firms now test quarterly or on each major release. Continuous PTaaS subscriptions can automate this cadence. In high-risk sectors banking, oil & gas, government , more frequent or ongoing testing is recommended.
Automated tools scanners efficiently cover large systems but only catch common issues. Manual testing skilled ethical hackers using creative techniques uncovers complex vulnerabilities like logic flaws or chained exploits that tools miss. The best approach is a combination: automated scans for breadth, plus manual attack simulations for depth. All top Saudi pentesters offer both.
PTaaS is a subscription model for pentesting. Instead of one-off tests, clients get continuous, on-demand assessments via a platform. New code pushes trigger scans, and all findings flow into a real-time portal. PTaaS is growing in KSA because it matches the fast pace of devops. It keeps security always on, detecting vulnerabilities before a formal audit. For example, DeepStrike offers a PTaaS dashboard for live vulnerability tracking.
Costs vary by scope. Basic web app tests might run a few thousand riyals, whereas large enterprise or red team assessments can go much higher. Many firms quote per-project or per-day. As a benchmark, penetration testing day rates in Riyadh often start around a few thousand SAR. Vendors like Buguard emphasize competitive rates, but always clarify what’s included retesting, reporting, and support to gauge true value.
Yes, in practice. While Saudi law doesn’t explicitly say you must pentest, regulatory frameworks make it compulsory for many entities. For example, SAMA requires banks/fintech to annually audit cybersecurity which practically means VAPT . CITC’s CRF obliges telecom/IT providers to maintain high security standards. The NCA ECC is a de facto national standard that mandates regular security checks. And with the new PDPL, organizations handling personal data are expected to assess their security posture often via VAPT to protect data. In summary, virtually every large organization in KSA ends up legally needing penetration tests.
Look for internationally recognized certs: OSCP/OSWE, CREST, CISSP, CEH are common. Firms with Saudi accreditation like CERT-In empanelment in India aren’t the norm here, but ISO 27001 certification or PCI/QSA credentials can signal rigor. Many top companies advertise CREST membership or specialized accreditations for example, Security Matterz highlights ISO 27001 and CISSP trained staff .
Any sector processing sensitive data needs pentests, but key ones include: Finance and Banking due to SAMA rules , Oil & Gas/Energy critical infrastructure , Healthcare patient data under PDPL , Government national security , and Telecom/IT CITC CRF . Even SMBs handling customer data or operating e-commerce platforms benefit from affordable VAPT solutions.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us