November 4, 2025
Updated: November 4, 2025
The power sector ranks among the top 5 most attacked industries. Learn how utilities protect critical infrastructure from ransomware, ICS malware, and IoT threats using NERC CIP, NIST, IEC 62443, and zero-trust security.
Mohammed Khalil


Cybersecurity in the power sector means protecting utilities’ digital and control systems. Modern grids use SCADA networks, IoT sensors, and cloud platforms greatly expanding the attack surface. Hackers from nation states to cybercriminals now target energy networks to disrupt operations. Utilities must safeguard everything from power plants and substations to smart meters and operator consoles. In 2025 this is mission critical: one analysis ranked energy the fourth most attacked industry. Notorious incidents Russian cyberattacks on Ukraine’s grid, Colonial Pipeline ransomware show that grid outages are a very real threat. Governments and regulators have noticed: for example, the EU’s NIS2 Directive now mandates strong cybersecurity for electricity networks.
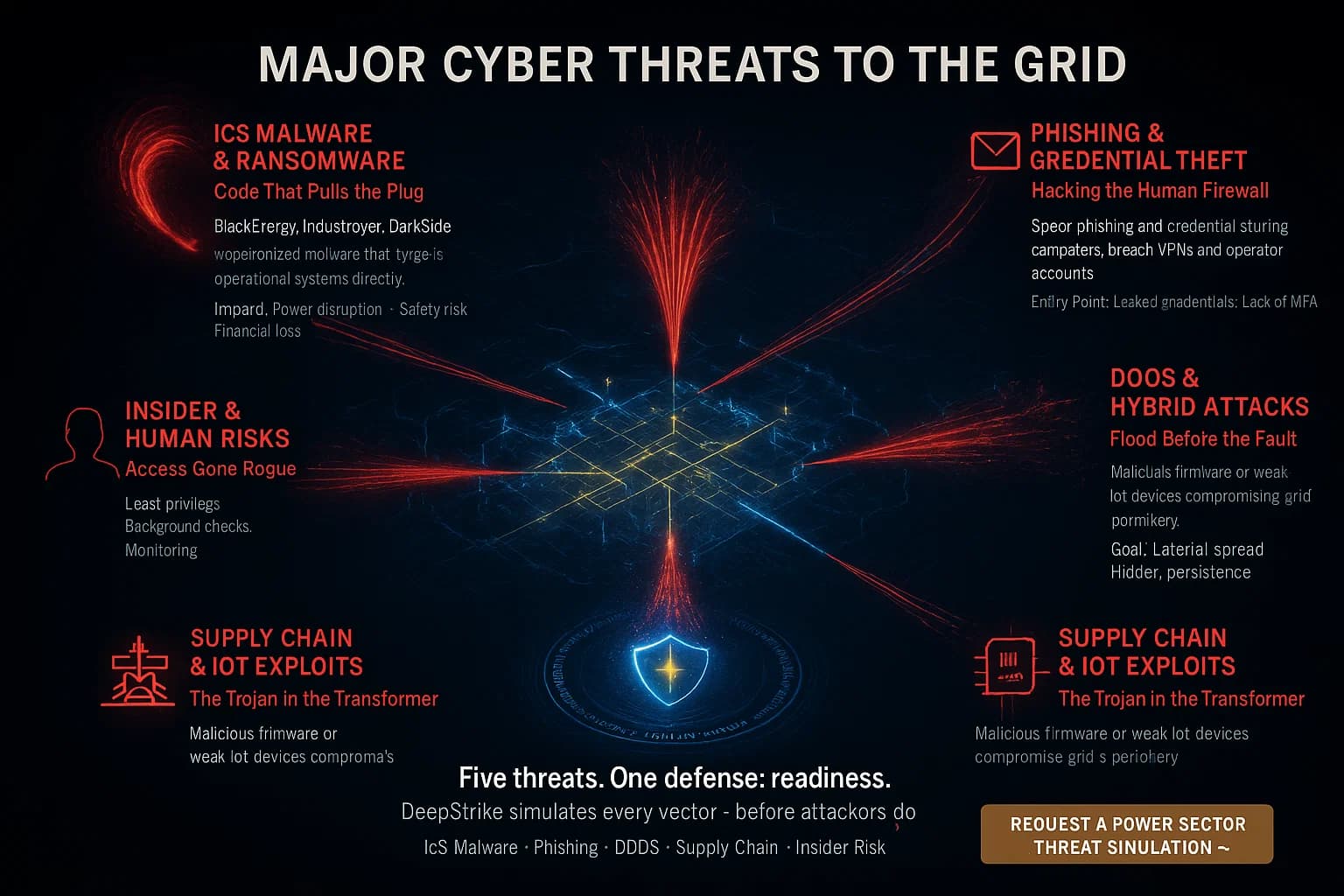
Utilities face a range of cyber threats:
These threats have already caused damage. In 2015- 2016, Russian hackers remotely tripped circuit breakers in Ukraine’s power grid. In 2021, DarkSide ransomware shut down the Colonial Pipeline, causing fuel shortages. Surveys show 56% of utilities have suffered a cyber related outage or data loss recently, underlining the need for robust protection.
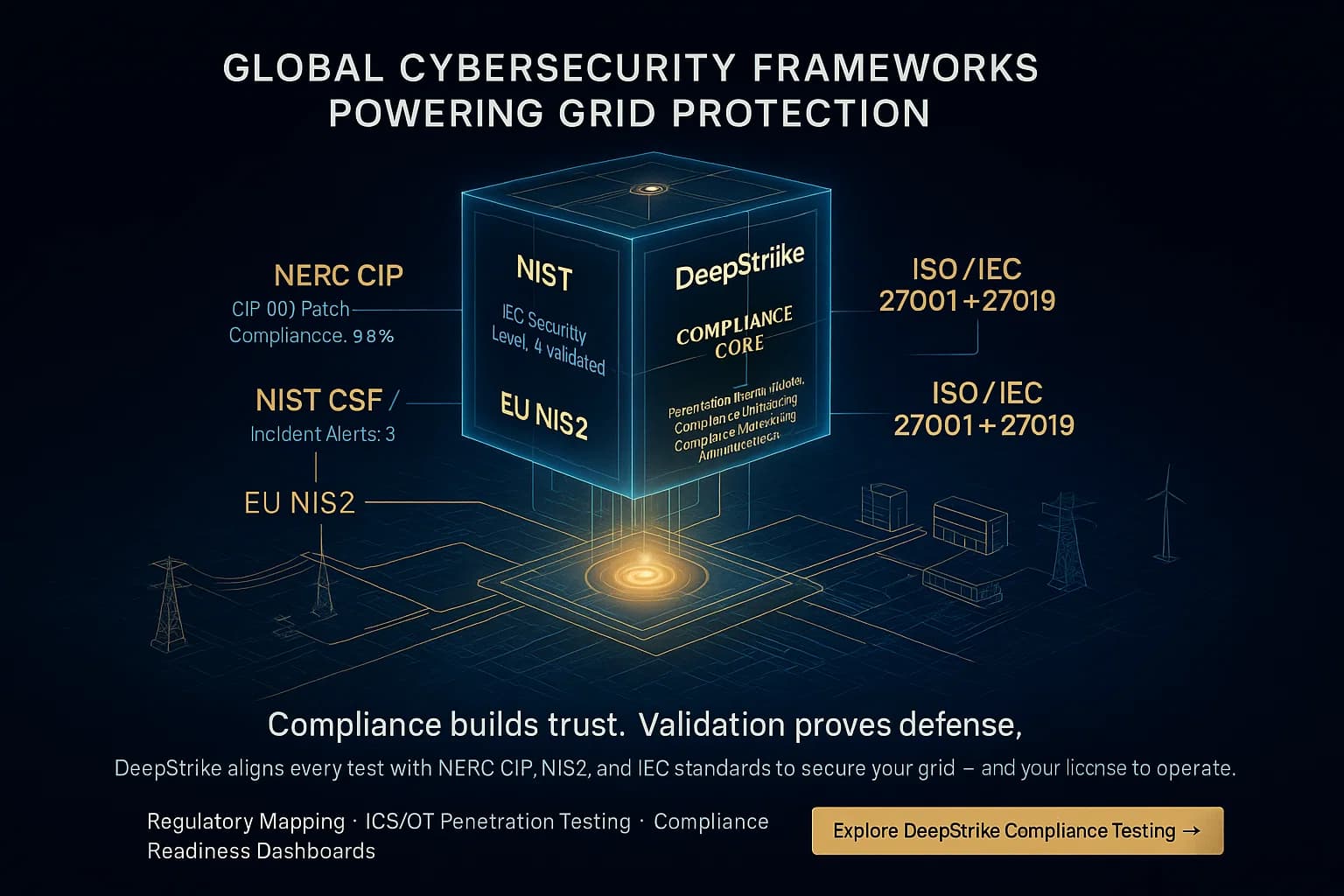
The power sector operates under very stringent rules. For example, NERC CIP Critical Infrastructure Protection is mandatory in North America for all bulk power utilities. It consists of 13 standards covering everything from asset inventory and access controls to incident response. Utilities must identify and categorize all critical equipment and apply perimeter defenses, employee training, and recovery plans. Violating CIP can bring heavy fines.
Globally, many utilities follow voluntary frameworks. The NIST Cybersecurity Framework CSF is widely used in the U.S.; NIST SP 800 82 provides detailed ICS/OT guidance. ISO/IEC 27001 with sector supplement 27019 offers a risk management program applicable to any utility. The IEC 62443 series targets industrial control systems specifically: it defines secure zones, secure product development processes, and technical security levels. In practice, smart utilities map NERC CIP requirements to NIST/ISO/IEC controls, achieving both compliance and effective security.
In Europe, the NIS2 Directive 2022 now forces power operators to implement strong cyber measures and report incidents rapidly. It also tightens rules on critical IT/OT suppliers. Other regions have similar mandates e.g. Japan’s METI guidelines, Canada’s CIP program. The common thread is risk management: all these frameworks stress asset inventories, network segmentation, encryption, logging, and drills.
Comparison of Key Frameworks:
| Standard | Scope Mandatory? | Key Focus |
|---|---|---|
| NERC CIP | Bulk electric system NA, Mandatory | U.S./Canada mandatory grid protections physical & cyber. Asset categorization, personnel security, emergency response, etc. |
| NIST CSF / 800 82 | U.S. Voluntary | Broad IT/OT risk management framework. CSF’s core functions guide strategy; SP 800 82 details ICS controls. |
| IEC 62443 | Global Voluntary | OT/ICS security. Defines zones & conduits, device lifecycle security, and technical requirements for control systems. |
| EU NIS2 | EU Mandatory | Mandatory cybersecurity for energy. Requires risk management, breach notification, and strict supplier safeguards. |
Meeting these requirements is essentially the baseline for trust. Utilities that integrate NERC CIP, NIST, IEC, and ISO best practices build a robust defense while staying compliant.
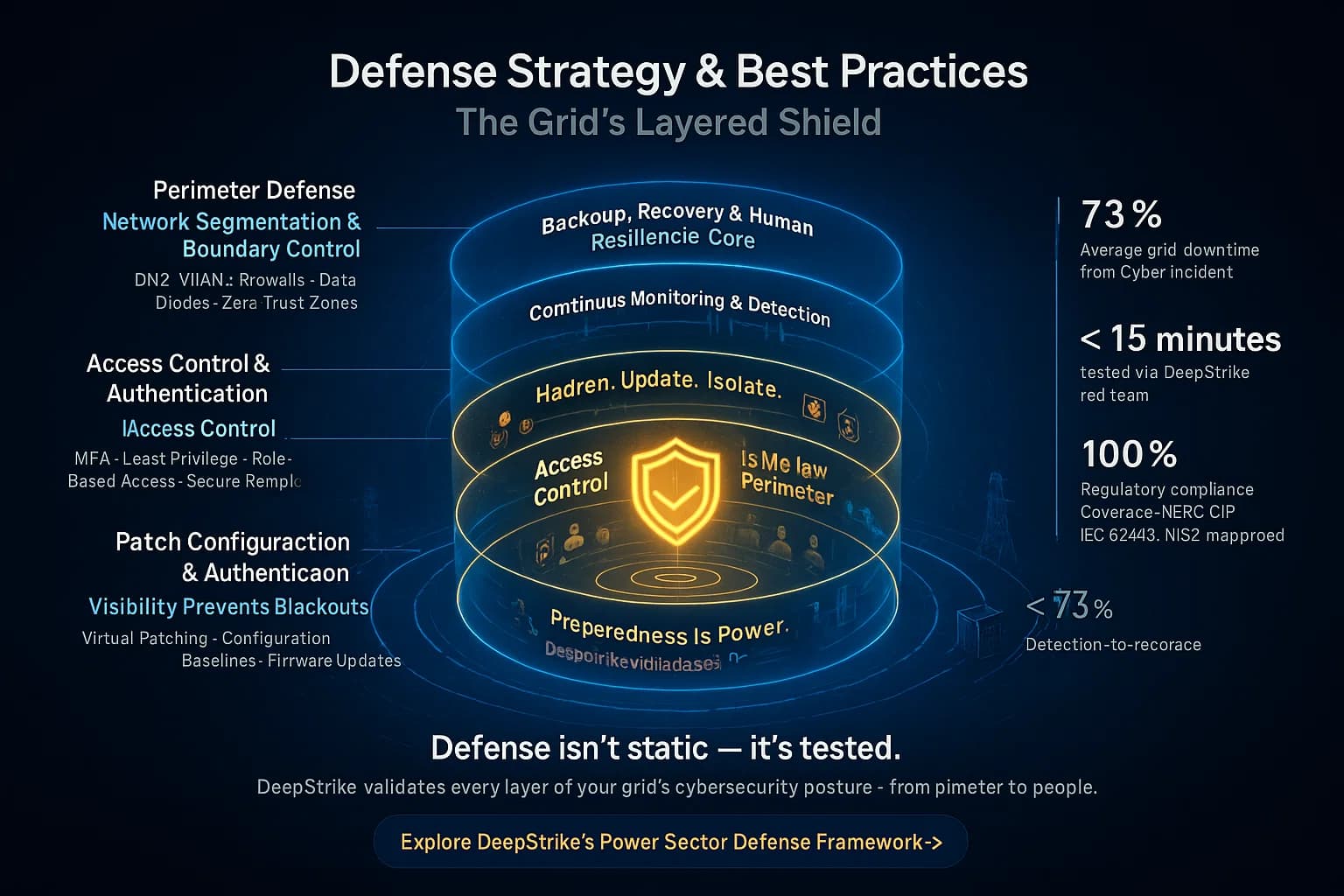
Utilities employ a defense in depth approach, layering multiple controls:
Each of these layers protects against different attack vectors. Together, they significantly raise the bar for attackers and mitigate impacts if one control is bypassed. Utilities routinely audit and test these defenses through red team exercises and specialized penetration testing services.
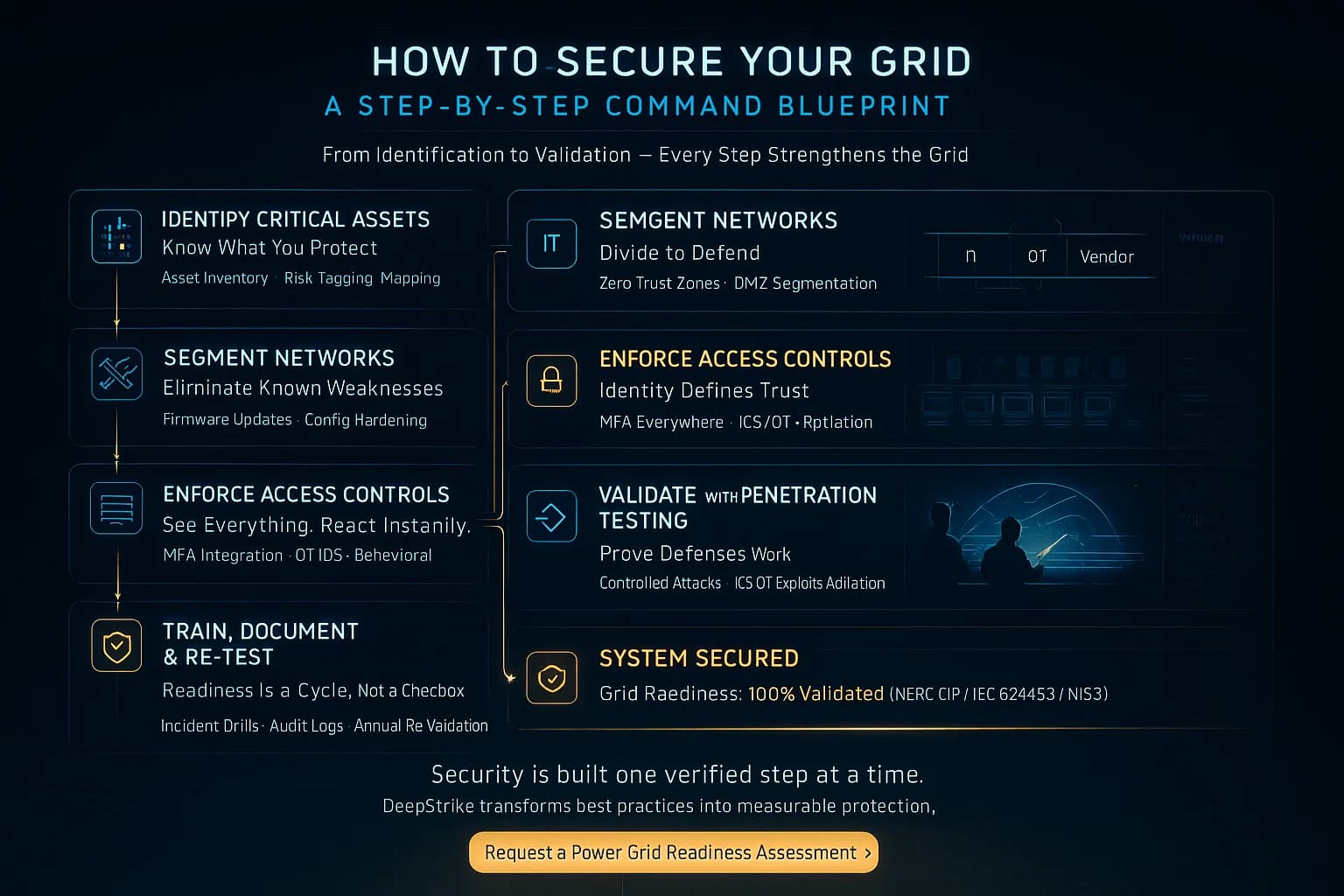
Following these steps based on industry experience builds a resilient security posture for any utility.

Technology means little without skilled people, yet the sector faces a major skills gap. Studies estimate a global shortage of 3.4 million cybersecurity professionals see cybersecurity skills gap statistics and solutions. Utilities in particular struggle to recruit and retain OT security experts. To address this, the industry is investing in training programs, apprenticeships, and partnerships with universities and government. Many also rely on managed security providers or shared resources e.g. ISACs, federal grants to augment their teams. Closing the talent gap remains a critical challenge.
Modern grids are smarter and therefore more complex to secure. Renewable plants, battery systems, and IoT devices smart meters, sensors, home EV chargers are all networked together. Each connected device is a potential attack point. For example, vulnerable smart meters have been shown to leak credentials, enabling remote takeover.
To manage this, device manufacturers and regulators are pushing secure by design approaches. New grid communication standards IEC 61850, DNP3 now support encryption and authentication e.g. IEC 62351. Utilities are requiring strong security in procurement: firmware signing, automatic patch updates, and hardware root of trust for all field devices. They are also exploring zero trust architectures in OT where no device is automatically trusted and using advanced analytics. Real time anomaly detection, often AI enhanced, now watches over both IT and OT traffic.
In short, security must be built in from the outset for the digital grid. Efforts like secure hardware designs, incident transparency regulations e.g. EU Cybersecurity Act, and AI driven monitoring are key to protecting the next generation grid. For cloud and IT aspects, see our discussion of best CSPM tools for cloud security.
The power sector’s cybersecurity challenge is immense, but it can be met with diligence. Grids are too critical to ignore cyberattacks here can cause blackouts and economic havoc. The good news is that a clear roadmap exists. Utilities should assume they will be targeted and plan accordingly: identify all critical assets, segment and monitor networks, enforce MFA and hardening, and prepare incident response playbooks. This layered, standards based approach NERC CIP, NIST/IEC/ISO, etc. is the best defense. Key takeaways: segmentation, patching, access control, training, and testing are non negotiable.
The threats of 2025 demand readiness. If you’re looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help.

Our experts provide clear, actionable guidance. Ready to strengthen your defenses? Explore our penetration testing services to see how we can uncover vulnerabilities before attackers do.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Top threats include ICS targeted malware e.g. BlackEnergy, Industroyer and ransomware on operational networks. Phishing attacks that steal operator credentials are also common. Denial of service and combined cyber physical attacks on substations are major concerns. All of these can cause blackouts if not stopped.
NERC CIP Critical Infrastructure Protection is the mandatory North American cybersecurity standard for bulk electric utilities. It consists of multiple requirements CIP 002 through CIP 014 covering asset management, cyber and physical security controls, and recovery planning. Utilities must identify critical grid equipment and protect it under these rules.
Utilities use multiple layers: isolating OT networks, enforcing offline backups, and having tested recovery plans. Preventative measures include patch management, endpoint protection, and strict MFA no shared passwords. They also run regular pen tests and incident drills. If ransomware strikes, these steps limit downtime and damage.
Key steps include: identify and secure all critical grid assets; segment OT from IT networks with firewalls; enforce multi factor authentication; patch systems promptly; continuously monitor control systems; and regularly test defenses. Performing scheduled penetration tests and security audits is essential. For example, see our articles on common network vulnerabilities and Penetration Testing Services for guidance.
Smart grids involve many connected devices and automated controls. Each smart meter, sensor, or inverter is a potential entry point if insecure. Rapid IoT growth can outpace security measures. The larger, more complex network means utilities must be extra diligent about device hardening, encryption, and monitoring to manage the increased attack surface.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us