August 24, 2025
Updated: August 24, 2025
An in-depth 2025 analysis of IoT and OT security threats, real-world attack statistics, industry impact, and regulatory shifts shaping the future of connected device security.
Mohammed Khalil


The most critical internet of things hacking statistics for 2025 paint a stark picture: a world of unprecedented convenience built on a dangerously fragile foundation. With the global count of connected devices projected to surpass 35.2 billion this year, cybercriminals are exploiting a vast and vulnerable attack surface with alarming efficiency.
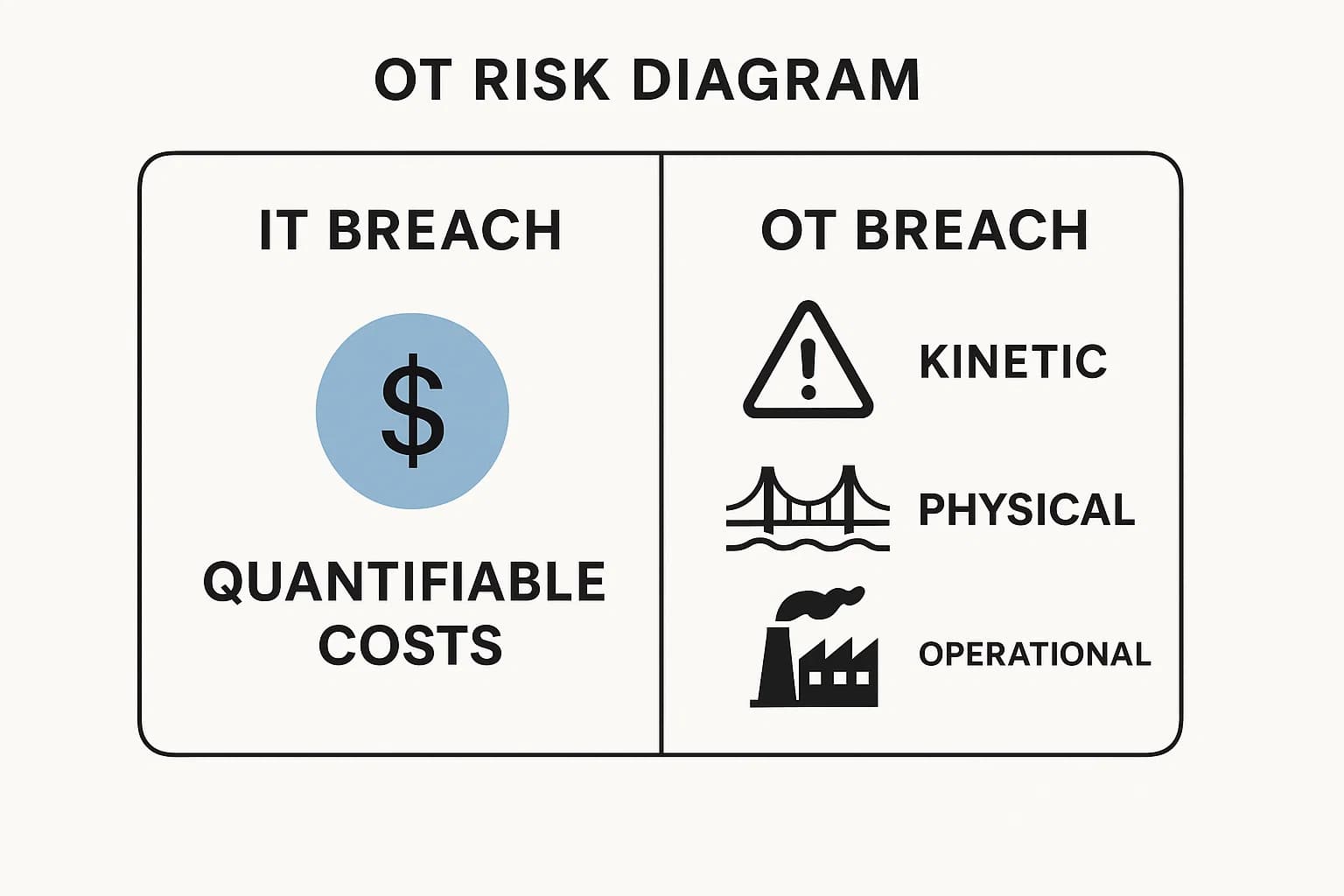
However, the conversation has moved far beyond stolen data. The threat is now physical. A compromised medical device can endanger patient safety, a hacked water treatment plant can threaten public health, and a disabled power grid can cause widespread chaos. This convergence of digital and physical risk means that IoT security is no longer just an IT problem; it is a fundamental issue of business resilience and public safety.
This shift has fundamentally altered the risk calculus for corporate boards and executives. The "cost" of a traditional IT breach, while significant, is often quantifiable in terms of data recovery, regulatory fines, and reputational damage. The cost of an OT breach, however, is kinetic. As detailed in recent threat reports, successful attacks on manufacturing sites and water utilities lead to immediate and complete operational shutdowns. This operational stoppage has a direct, immediate, and often uncapped impact on revenue and, in the case of critical infrastructure, public safety. This gives attackers immense leverage. They are not merely threatening data; they are threatening the core function of the business or public service. This new reality explains the aggressive pivot by sophisticated ransomware actors toward OT environments, where the pressure to pay for decryption keys is highest.
The sheer volume of malicious activity targeting IoT devices is staggering. In 2025, the ecosystem weathers an average of 820,000 hacking attempts every day, a 46% increase from the previous year. This translates to a constant, automated hum of malicious activity that creates a state of continuous compromise for any internet facing device.
This headline number is part of a much larger wave of cyber threats. In the first quarter of 2025 alone, Kaspersky's security solutions blocked over 629 million attacks originating from online resources, demonstrating the scale of the infrastructure used to find and exploit vulnerable IoT endpoints. The threat is not confined to enterprise networks; even the average home network now faces approximately 10 distinct attack attempts every 24 hours.
It is crucial to understand the nature of these "attempts." The vast majority are not targeted, human driven efforts. Instead, they represent the output of a global, automated reconnaissance machine. Threat intelligence from Fortinet's 2025 Global Threat Landscape Report reveals a 16.7% worldwide rise in active scanning, as adversaries deploy automated tools to create a near real time map of the internet's attack surface. These scans relentlessly probe for open ports, outdated firmware, and default credentials, the low hanging fruit of the IoT world.
This high volume of unsuccessful daily attacks should not be interpreted as a sign of effective security. Rather, it is a measure of the adversary's investment in intelligence gathering. By the time a sophisticated, targeted attack is launched, the adversary has often already completed their mapping and identified the weakest points of entry. This reality underscores the futility of a purely reactive defense posture. Proactive strategies, such as attack surface reduction and continuous security validation, are the only logical response to an adversary that is always watching.
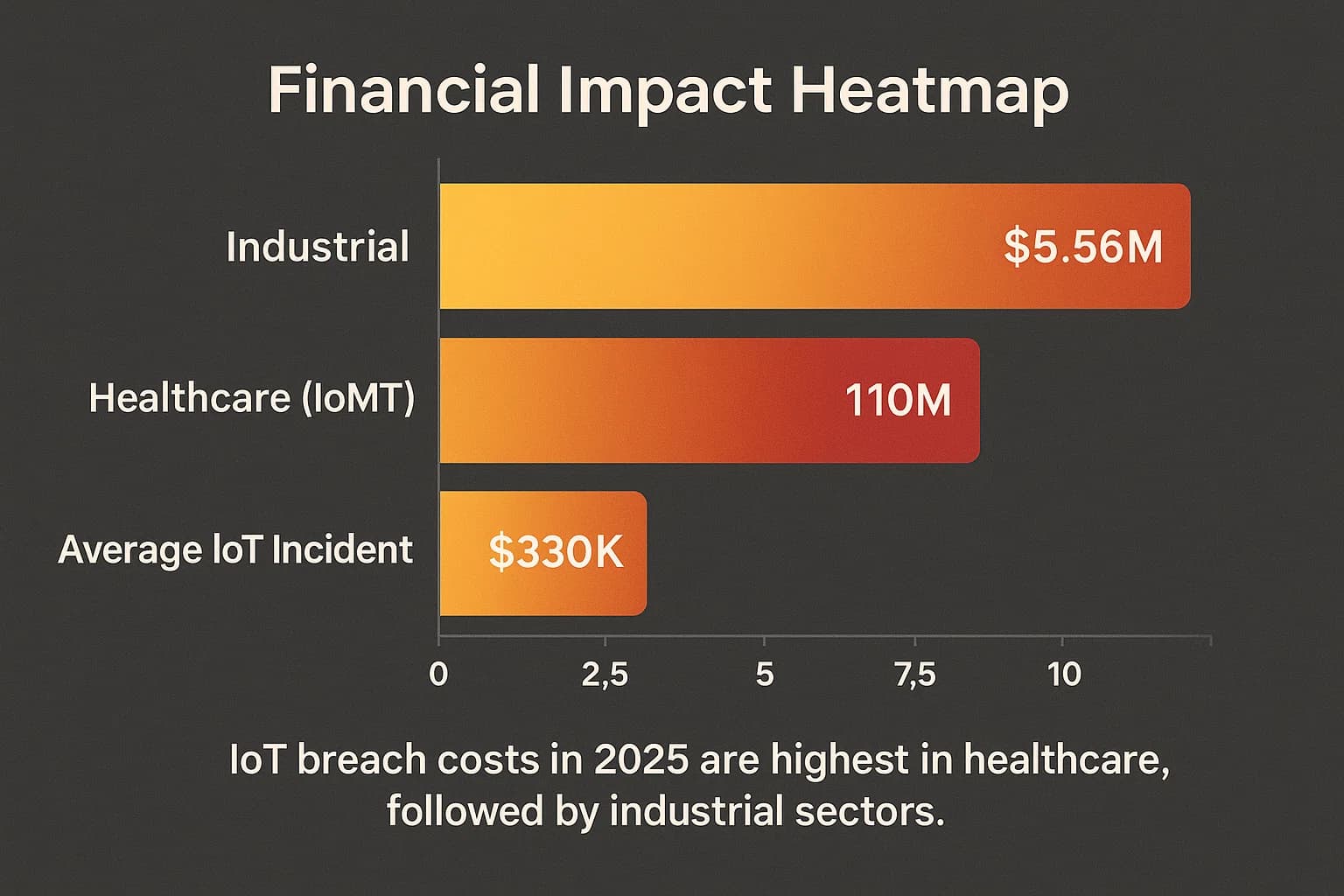
The financial consequences of an IoT security failure are severe and escalating, particularly when operational technology is involved. While a single successful attack on an IoT device can cost an average of $330,000, these incidents often serve as the initial entry point for much larger, more devastating enterprise breaches.
Historical data from Forrester shows that 34% of breaches involving IoT devices result in cumulative costs between $5 million and $10 million significantly higher than traditional IT incidents. The latest data from 2025 provides an even sharper picture, with sector specific costs highlighting where attackers are finding the most leverage:
These multi million dollar incidents contribute to a global cybercrime economy projected to inflict $10.5 trillion in damages in 2025. For a deeper analysis of these financial trends, explore our complete report on 2025 data breach statistics and trends.
The escalating cost of IoT/OT breaches is creating powerful secondary effects that are reshaping cybersecurity investment. The clear, quantifiable financial risk associated with an OT compromise provides the actuarial basis for insurance carriers to charge significantly higher premiums for organizations with insecure industrial environments. Simultaneously, new regulations, such as the SEC's requirement for public companies to disclose material cybersecurity incidents, make the financial impact of these attacks transparent to investors and regulators. This creates a pincer movement of market and regulatory pressure, compelling organizations to adopt stronger security controls not merely for protection, but as a non-negotiable cost of doing business and securing liability coverage.
The most unsettling aspect of the IoT threat landscape is that the vast majority of successful attacks do not rely on sophisticated, nation state level capabilities or complex zero day exploits. Instead, they prey on a handful of fundamental, systemic security failures that are baked into devices from the factory floor. For more on advanced threats, see our Zero day exploit lifecycle and prevention.
The core problems plaguing IoT security have been well documented for years. These foundational statistics, while older, remain critical for understanding the scale of the "security debt" the industry has accumulated:
The latest threat intelligence from 2025 confirms that these fundamental flaws remain the primary vectors for compromise:
These persistent failures map directly to the OWASP IoT Top 10, a project that catalogs the most critical security risks to Internet of Things devices. The issues of default credentials and unencrypted traffic fall squarely under categories like "I1 Weak, Guessable, or Hardcoded Passwords" and "I2 Insecure Network Services".
Ultimately, the IoT security crisis is not a technological failure but an economic one. For years, manufacturers have been economically incentivized to prioritize speed to market and low production costs over robust security. Implementing features like encryption chips, unique credential generation, and secure update servers adds to the bill of materials and can delay product launches. Because the manufacturer does not directly bear the cost when one of their devices is conscripted into a botnet, security has been treated as an externality. The collective cost of millions of insecure devices is borne by society at large the victims of massive DDoS attacks or enterprise ransomware campaigns. This fundamental market failure is the true root cause of the problem and is precisely what new government regulations are now attempting to correct.
These statistics represent real world attacks with tangible consequences. The following case studies illustrate the modern threats facing IoT and OT environments.

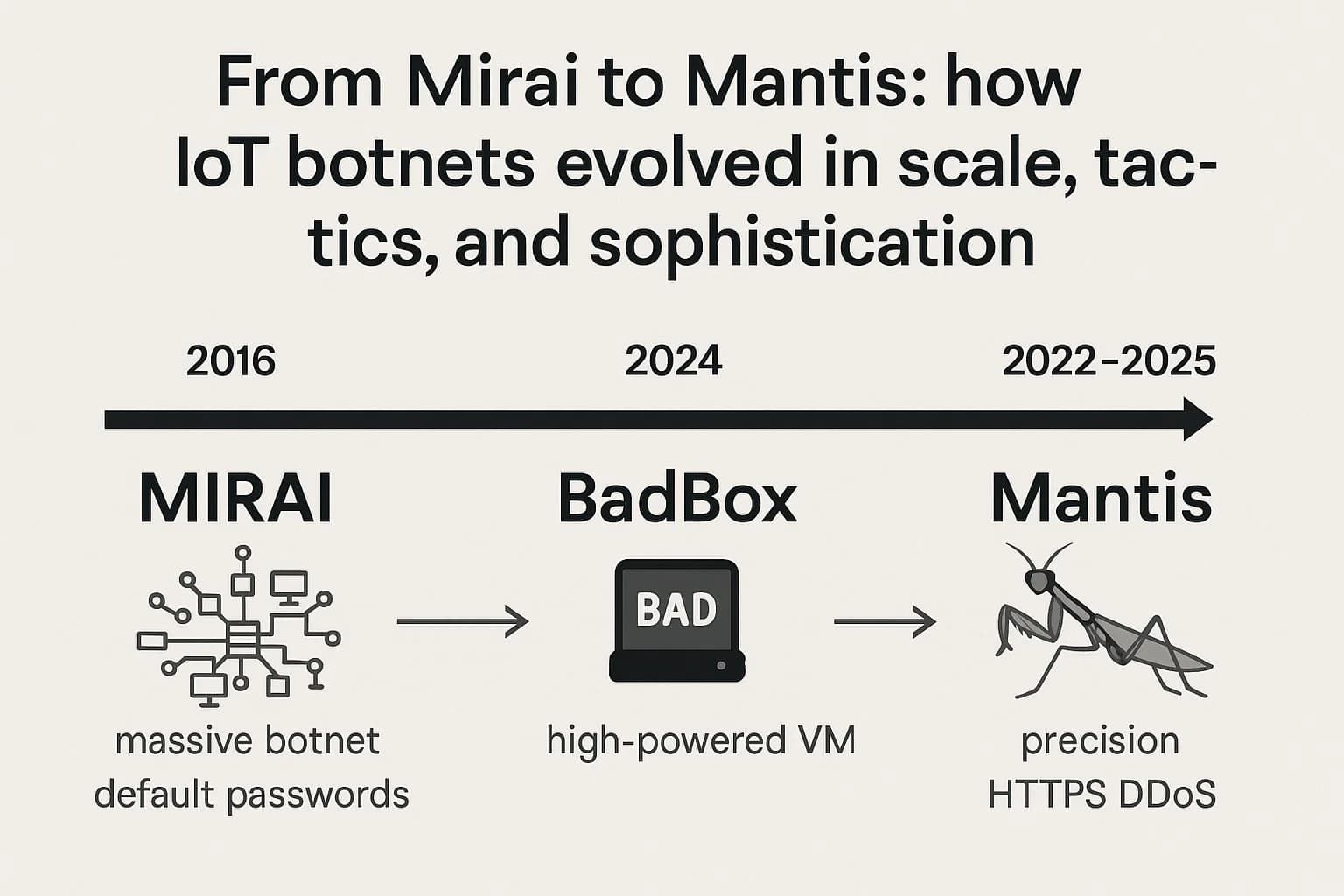
To understand the current threat landscape, it is essential to look at the evolution of IoT botnets.
This evolution from Mirai to Mantis signifies a critical change in adversary tactics, moving from "brute force" (quantity of bots) to "precision strike" (quality of bots). Mirai's strength was its sheer scale, and mitigation often involved blocking huge ranges of residential IP addresses. Mantis's strength is its power density, with each bot possessing high bandwidth and CPU resources. This enables complex application layer attacks that are harder to distinguish from legitimate traffic and originate from seemingly trustworthy sources like cloud providers and data centers. This shift demands more sophisticated, behavior based detection and mitigation strategies.
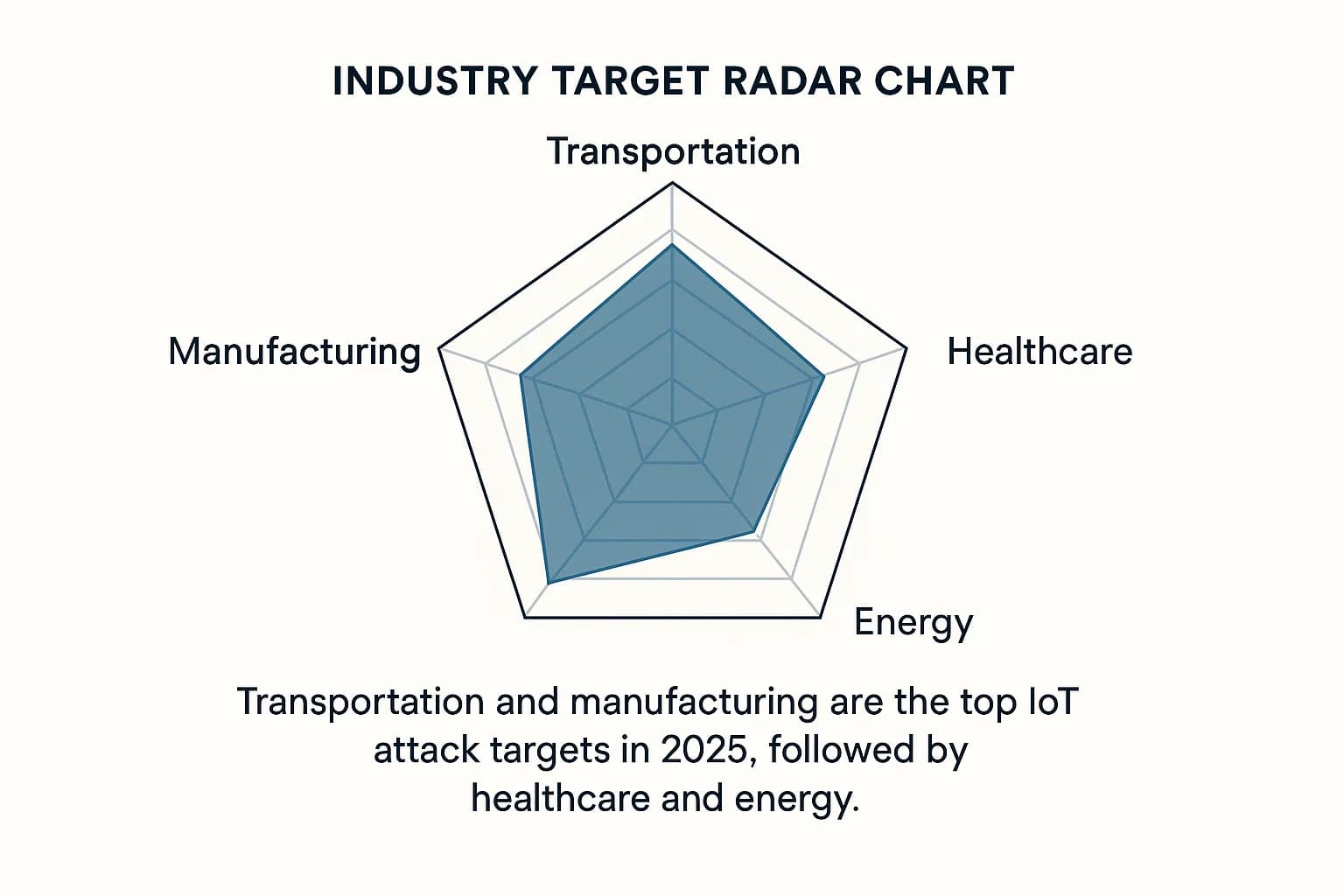
While all sectors are at risk, attackers are increasingly focusing their efforts on high value targets where a successful breach can cause maximum disruption and yield the largest payouts. The latest data from 2025 reveals a clear focus on industrial and critical infrastructure sectors.
Analysis from Nozomi Networks, based on real world telemetry from OT environments, places Transportation and Manufacturing as the top two most targeted sectors in 2025. This focus reflects a strategic choice by adversaries to target industries where operational continuity is paramount and the potential for disruptive leverage is highest.

In response to the crisis of "insecurity by design," governments are beginning to intervene. The most significant development is the United Kingdom's Product Security and Telecommunications Infrastructure (PSTI) Act, which came into full effect on April 29, 2024. This landmark legislation is the first of its kind to legally mandate baseline cybersecurity standards for consumer connectable products.
The PSTI Act imposes three core requirements on manufacturers, importers, and distributors of smart devices sold in the UK:
Enforcement is robust, with the UK's Office for Product Safety and Standards (OPSS) empowered to issue fines of up to £10 million or 4% of a company's global revenue, whichever is higher, for non compliance.
The PSTI Act represents a direct legislative attempt to correct the economic market failure that has fueled the IoT security crisis. By imposing a significant financial penalty for insecure practices, the law fundamentally alters the economic calculation for manufacturers. A global device maker now faces a choice: create a separate, more secure (and potentially more expensive) product line just for the UK market, or elevate the security baseline of their entire global product line to meet PSTI standards. Given the immense logistical complexity and cost of managing separate SKUs, firmware branches, and supply chains, it is often more efficient to adopt the strictest standard as the global default. Consequently, this UK specific law is expected to have a significant ripple effect, improving the security of IoT devices sold worldwide.
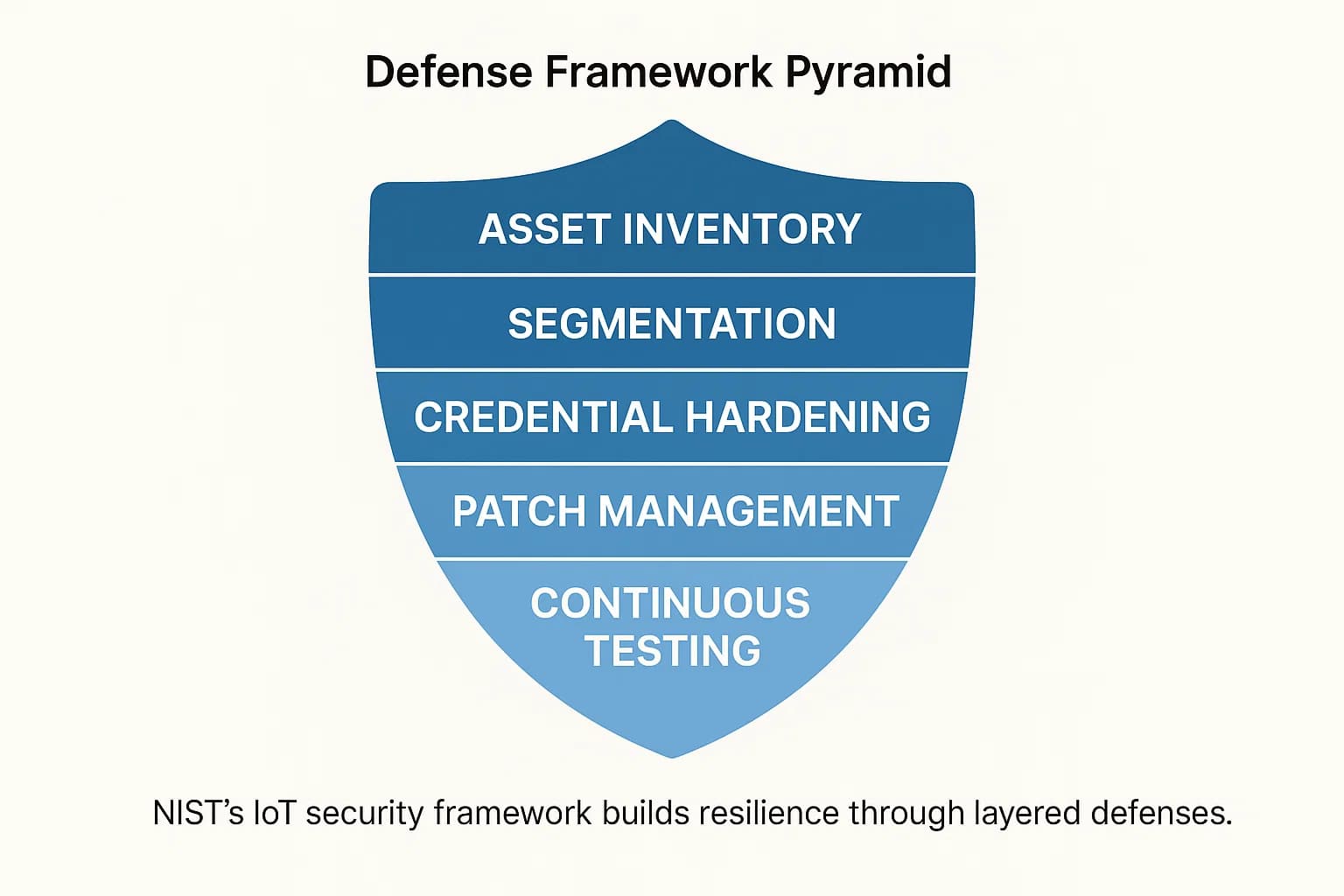
Defending against these evolving threats requires a structured, proactive approach. The NIST Cybersecurity Framework for IoT provides an authoritative, risk based model for building a resilient security posture. The following steps are essential for any organization deploying IoT and OT devices.
You cannot protect what you do not know you have. The first and most critical step is to conduct a thorough discovery process to create a complete and accurate inventory of every connected device on your network. This inventory is the foundation of any effective risk management program.
Never allow your IoT and OT devices to share the same network as your critical IT systems (e.g., file servers, domain controllers). By creating separate, isolated networks (VLANs), you can contain a potential breach. If a smart camera gets compromised, segmentation prevents the attacker from "pivoting" into your core corporate network. This is a core tenet of a defense in depth strategy.
This is non-negotiable. Immediately change all default passwords on every device. Implement a policy that requires strong, unique passwords and enable multi factor authentication (MFA) wherever it is supported. Access should be granted on a principle of least privilege, ensuring users and devices only have the permissions absolutely necessary to function.
The fundamental weakness of passwords is a primary driver of IoT compromise. A powerful modern solution is FIDO2/WebAuthn, an open authentication standard that enables passwordless logins. It uses public key cryptography to create unique, unphishable credentials that are bound to a user's physical device (like a laptop's fingerprint reader or a hardware security key). When a user registers with a service, their device creates a private key (which never leaves the device) and a public key (which is sent to the server). To log in, the server sends a challenge, which the device signs with the private key. This process is immune to credential stuffing, phishing, and password theft, directly countering the attack vectors used in breaches like the 2024 Roku incident.
With a significant percentage of breaches exploiting unpatched firmware, a formal, repeatable process for tracking, testing, and deploying security updates is essential. This cannot be an ad hoc activity; it must be a core operational security function with clear ownership and accountability.
Assuming your security controls are effective is a critical mistake. To ensure resilience against evolving threats like OT targeted ransomware, organizations must proactively validate their defenses. The key difference between a vulnerability assessment and a penetration test is that the latter actively tries to exploit weaknesses to simulate a real world attack.
You can simulate real world attack chains and uncover the hidden vulnerabilities that automated scanners miss. For organizations with dynamic IT/OT environments, a continuous testing model is crucial for staying ahead of attackers. Learn more in our guide to Penetration Testing for DevOps.
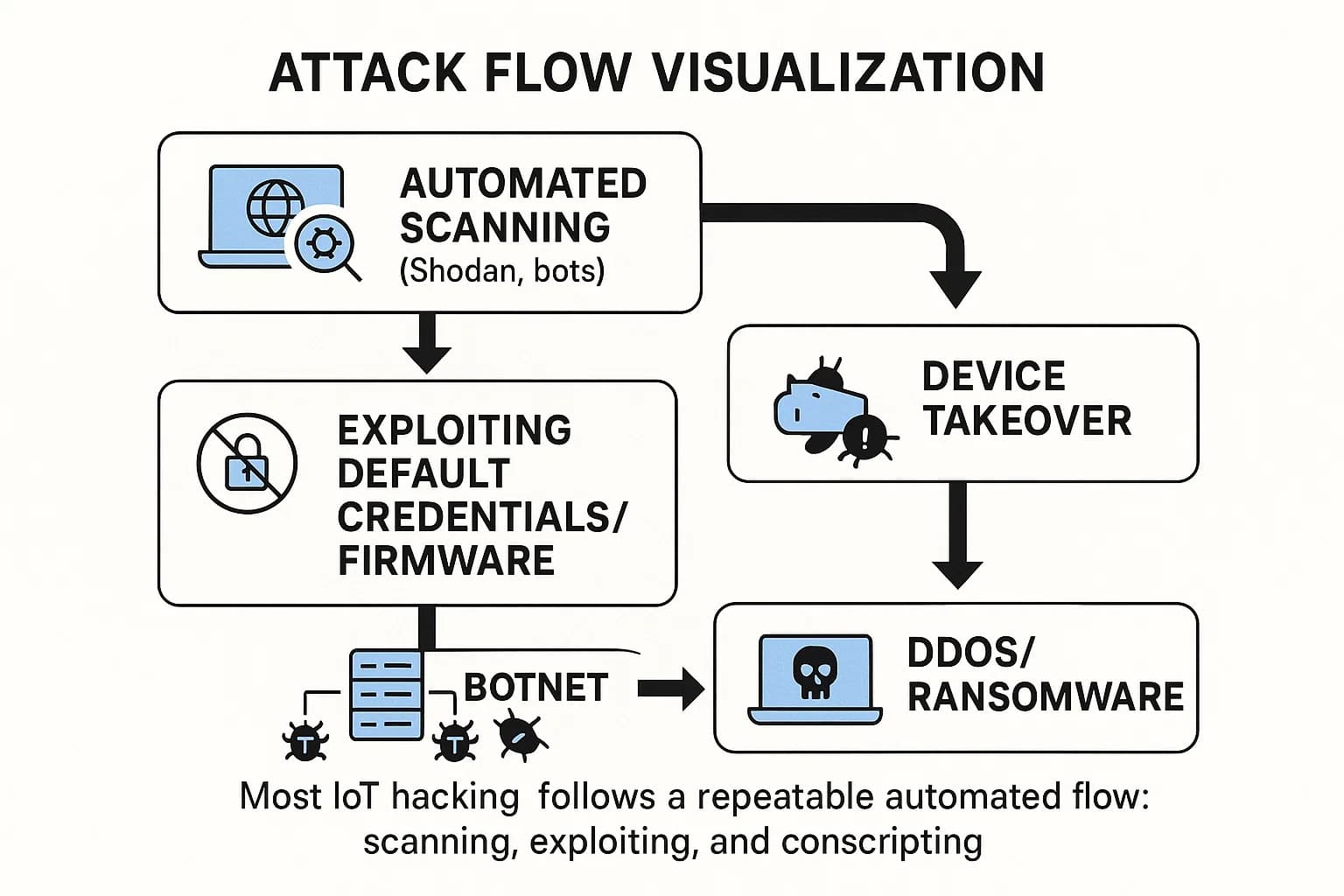
The most common attacks are automated and opportunistic, leveraging fundamental weaknesses. Brute force attacks that try thousands of common or default passwords against unencrypted protocols like Telnet are the primary method of infection. Once compromised, devices are often absorbed into botnets to conduct large scale DDoS attacks.
Hackers use automated scanning tools (like Shodan) that constantly probe the entire internet for devices responding on specific network ports, such as Telnet port 23 or SSH port 22. When a device responds, malware like Mirai automatically attempts to log in using a predefined list of common default credentials.
Absolutely. If your smart TV is on the same Wi Fi network as your work laptop and personal phone, an attacker who compromises the TV can use it as a "pivot point." From there, they can scan your internal network to find and attack more valuable targets. This is precisely why network segmentation is a critical security control.
The biggest risks stem from a combination of factors: manufacturers rushing products to market with little to no security built in ("insecurity by design"), users failing to change weak default passwords, and the lack of a consistent, automated mechanism for security updates. This creates a perfect storm for widespread, automated attacks.
Warning signs can include a sudden increase in network traffic from the device, unusually sluggish performance, device settings changing without your input, or the device rebooting unexpectedly. However, many infections are designed to be stealthy. Proactive security measures are far more effective than waiting for obvious symptoms.
Encryption is fundamental. It scrambles data so that it cannot be read or understood by anyone who might intercept it. With 98% of IoT traffic being unencrypted, sensitive information like video feeds from a security camera, login credentials, or commands sent to a device are transmitted in plain text, making them trivial for an attacker to steal or manipulate.
They can be, but their safety is a shared responsibility. It depends on both the manufacturer's commitment to security and the user's diligence. To use these devices safely, you must change default passwords, enable MFA, apply updates promptly, and secure your home Wi Fi network. It is also crucial to purchase devices from reputable manufacturers that have a track record of supporting their products with security patches.
The statistics for 2025 are unequivocal: IoT and OT threats are growing at an unsustainable rate, fueled by basic, preventable security failures with multi million dollar consequences. The industrialization of attacks against cyber physical systems, the economic incentives that perpetuate insecure by design products, and the nascent regulatory response all point to a landscape of increasing complexity and risk.
The sheer scale of the problem can feel overwhelming, but the path forward is not about finding a single, complex solution. It is about a consistent, disciplined commitment to foundational security hygiene. Moving from a state of passive awareness to one of proactive readiness is the only viable strategy. This means implementing the fundamentals of strong credential management, rigorous network segmentation, and timely patching. Most critically, it means rigorously validating those defenses through continuous, expert led testing. In the hyper connected world of 2025, assuming you are a target is the first and most essential step toward building a truly resilient defense.
Ready to Strengthen Your Defenses?
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
About the Author
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us