November 11, 2025
Updated: November 11, 2025
Discover the best dark web monitoring tools of 2025 compare free, open source, and enterprise solutions to detect leaked data before attackers do.
Mohammed Khalil


Dark web monitoring tools are security solutions that continuously scan the dark, hidden corners of the internet for signs of your sensitive data. In plain terms, they alert you if your accounts, passwords, customer records, or other confidential information show up for sale or sharing on underground sites. In 2025, with data breaches hitting record highs the average breach costs organizations $4.88 million, these tools have shifted from a nice to have to a must have early warning system. Why does this matter now? Because stolen credentials and personal data often surface on the dark web long before victims realize it. Catching those red flags quickly can be the difference between a contained incident and a full blown, costly breach.
This article will break down what dark web monitoring tools are, how they work, and how to choose between free vs paid solutions. We’ll cover options for individual users and enterprise security teams, compare key features including a comparison table, and provide real world insights on using these tools effectively. Let’s dive in.
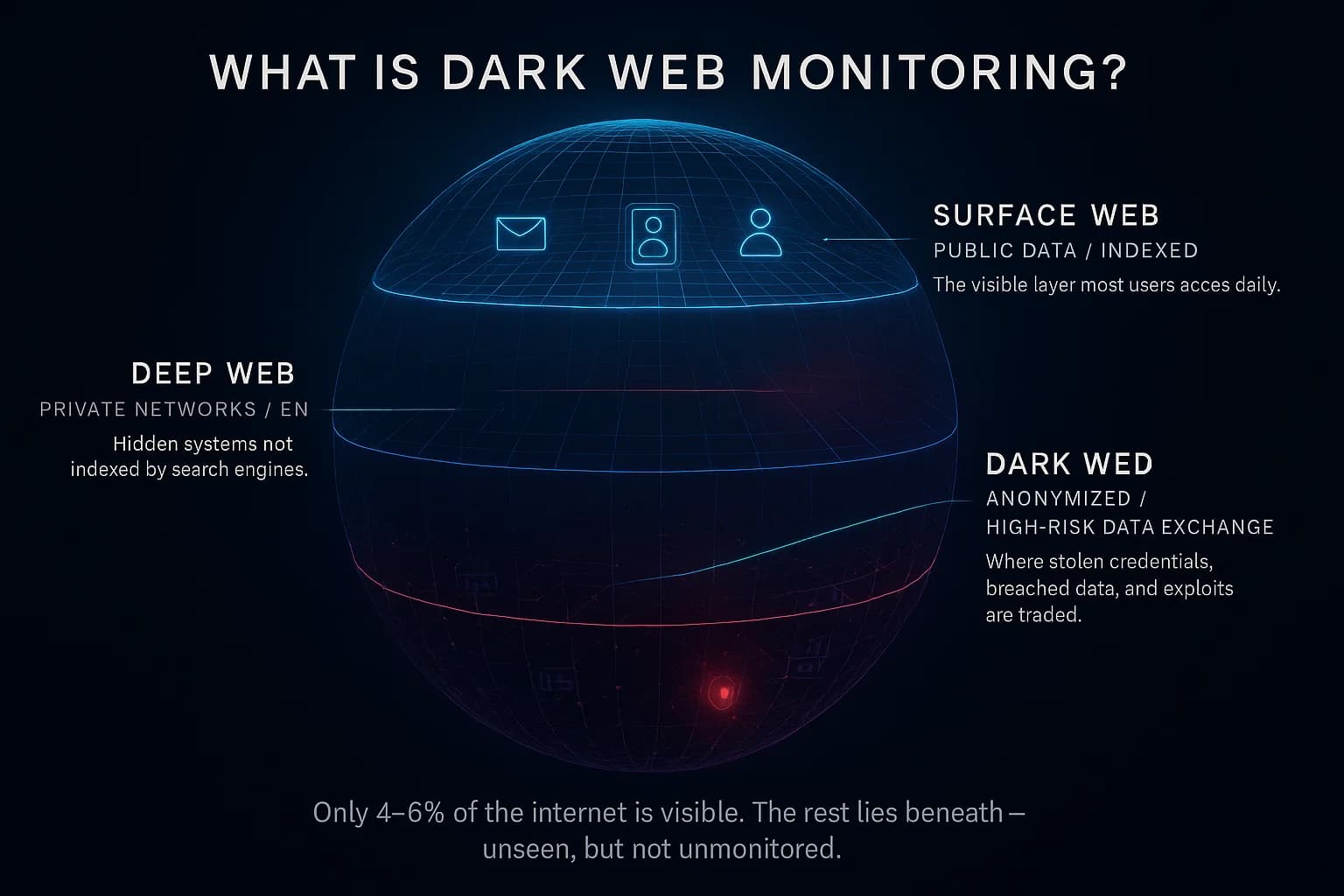
Dark web monitoring is the practice of tracking and scanning the dark web for sensitive or stolen data related to you or your organization. The dark web refers to the network of hidden websites accessible only via special browsers like Tor, a haven for hackers and cybercriminal marketplaces. Monitoring tools continually crawl these hidden forums, black markets, paste sites, and even encrypted chat rooms for any mention of your emails, passwords, customer data, intellectual property, or other indicators that suggest a breach. When a match is found, say your employee database or login credentials appear in a dump the tool triggers an alert so you can respond e.g. reset passwords, notify affected parties, involve law enforcement.
In short, dark web monitoring acts like an early warning radar. Instead of waiting months to discover a breach through traditional means, you get a heads up the moment your data leaks in shady corners of the internet.
Why this matters: It currently takes organizations an average of 194 days to identify a breach without such measures. A dark web alert can dramatically shorten that discovery time, limiting the damage and cost. These tools have evolved from being a niche, optional activity to a standard layer of cyber defense especially for companies handling large volumes of sensitive data finance, healthcare, etc. where early detection is critical.
How does it work? Under the hood, dark web monitoring solutions employ web crawlers, scraping scripts, and threat intelligence networks to continuously scan hidden sites. Advanced platforms even use human analysts or machine learning to penetrate closed criminal communities and interpret multilingual hacker chatter. When they find stolen data matching your watch list like a company domain, email address, or keyword, they log the details and send you actionable information for example, 25 employee passwords found in a hacker forum on March 1, 2025 with a snippet or link for verification. This allows you to take proactive steps immediately, rather than discovering the leak months later when damage is already done.
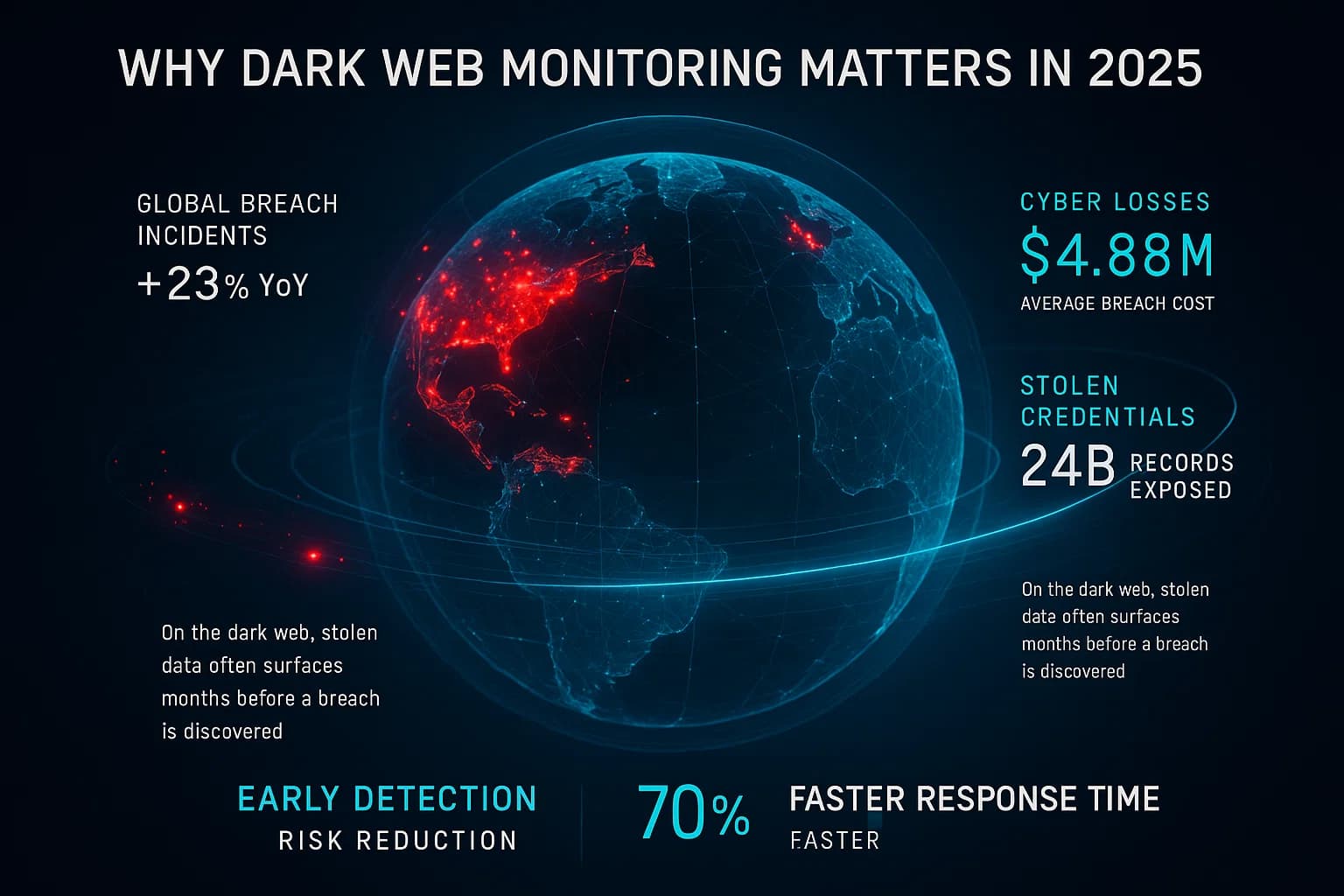
Cybercrime has only intensified. Stolen data is bought and sold in thriving underground marketplaces, fueling identity theft, fraud, and corporate espionage. Here’s why monitoring the dark web is so vital in 2025:
Dark web monitoring addresses a critical blind spot. It extends your visibility into areas where threats often lurk undetected. In the 2025 threat landscape, where ransomware gangs run private leak sites and initial access brokers auction off network access, you can’t afford to ignore what’s happening in the shadows. Monitoring the dark web is like having a DVR of criminal activity related to your business you’ll know if and when you’re a target, and you can respond decisively.
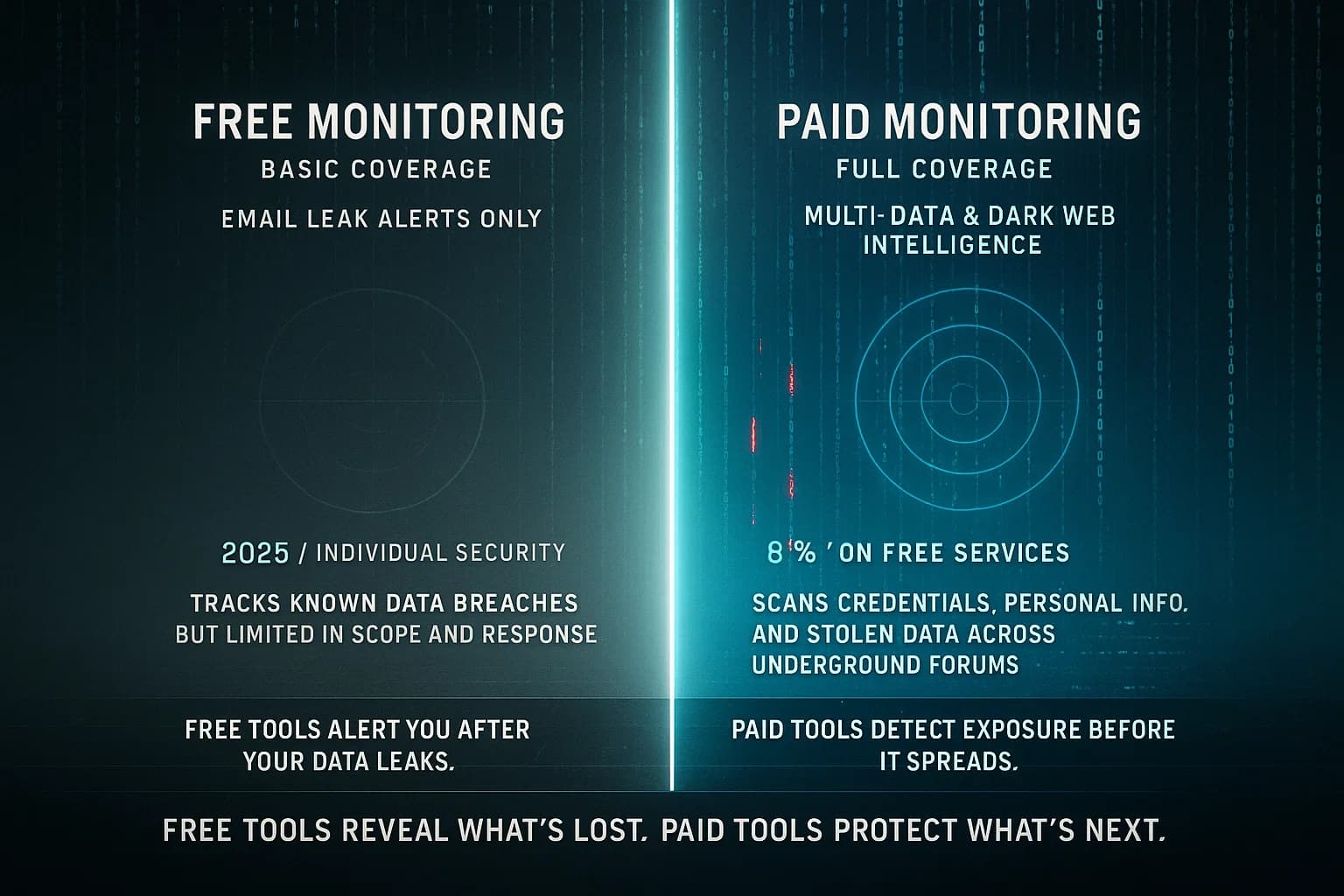
Dark web monitoring isn’t just for large enterprises; individuals can benefit too. If you’re worried that your personal data emails, passwords, credit card numbers, Social Security Number, etc. might be floating around the dark web, there are tools and services designed to help you. They generally fall into three buckets:
| Category | Examples | Features | Cost |
|---|---|---|---|
| Free Personal Checkers | Have I Been Pwned, Firefox Monitor, BreachAlarm | One time email or password breach lookups; opt in notifications for new breaches | $0 free |
| Freemium Security Apps | Keeper BreachWatch, NordPass, LastPass Monitor | Ongoing credential scanning against breach databases with real time alerts | Free basic scan; full monitoring in paid plans |
| Paid ID Protection | Experian Dark Web Scan, LifeLock, Identity Guard | Continuous dark web surveillance for personal info SSN, bank accounts, etc. + identity theft insurance | monthly subscription |
Free services: The most popular is Have I Been Pwned HIBP a website by security researcher Troy Hunt. You enter your email and it tells you if that email shows up in any publicly known breach databases. It’s essentially checking Have any known data dumps contained my account?. HIBP is widely used and even provides an API for integrations. Other free sites like Firefox Monitor by Mozilla use HIBP’s data to alert you about new breaches involving your accounts. These are great for one off peace of mind or curiosity. However, keep in mind they only cover known breaches that have been made public. If your data was stolen and sold privately, a simple public database check won’t catch it.
Example: You can quickly go to haveibeenpwned.com and see if your email appears in any of 600+ breach dumps. If yes, you’ll get a list of breaches and you’ll know to change that email’s password everywhere. If not, you get a green light for now. HIBP and similar services are free and easy, but they are reactive they don’t continuously watch for future threats unless you subscribe to notifications.
Freemium apps password managers: Many password managers and security apps now include a dark web scan feature as a selling point. For instance, Keeper Security’s BreachWatch will scan your stored passwords against breach data and alert if any of them have been found leaked. LastPass, NordPass, Dashlane and others offer similar monitoring for your vault. Often, you get a free initial scan, but continuous monitoring requires a premium subscription. These tools are handy because they integrate with what you already use to manage passwords. They can warn you Hey, this password was found in a breach, change it now as you go about your day. Just remember, they typically rely on the same publicly disclosed breach datasets plus some web crawling useful, but not infallible.
Paid identity monitoring services: For full coverage, individuals can subscribe to services like LifeLock Norton, Experian IdentityWorks, Identity Guard, or SpyCloud Personal. These services go beyond just emails and passwords. They’ll monitor black markets and dump sites for your Social Security Number, credit card numbers, bank account info, driver’s license, medical IDs, and more basically any personal identifiers you supply. If something pops up, you get an alert and often help from a restoration specialist to address identity theft issues. They frequently bundle insurance that covers certain losses from identity theft. The downside is cost: these run anywhere from $10 to $30+ per month. For someone who has had identity theft issues before or is just very proactive about personal data, it can be worth it. For others, a free scan here and there suffices.
Pros & Cons for Individuals: Free tools are a no-brainer you should absolutely take advantage of them because they cost nothing and can uncover past leaks. Just temper your expectations: a clean result doesn’t guarantee your data isn’t on the dark web, it just means it hasn’t been spotted in public breach records. Paid consumer monitoring offers peace of mind and convenience continuous scanning without you doing a thing, and support if bad news appears. But not everyone needs to spend hundreds per year on this. If you reuse passwords or have a lot of sensitive info e.g. you shared your SSN widely, a paid service adds a safety net. If you practice good cyber hygiene, unique passwords, watch financial statements, freeze your credit, you might get by with the free tools plus vigilance.
Legitimate dark web monitoring services do NOT actually poke around with your personal credentials on shady sites they gather breach data safely via APIs or databases. For example, when you enter your email on Have I Been Pwned, it’s checking against a hashed database of known leaked emails, not literally entering your email into hacker forums. So using these services is safe and legal. Just be wary of any sketchy site that asks for too much info; stick to well known names.
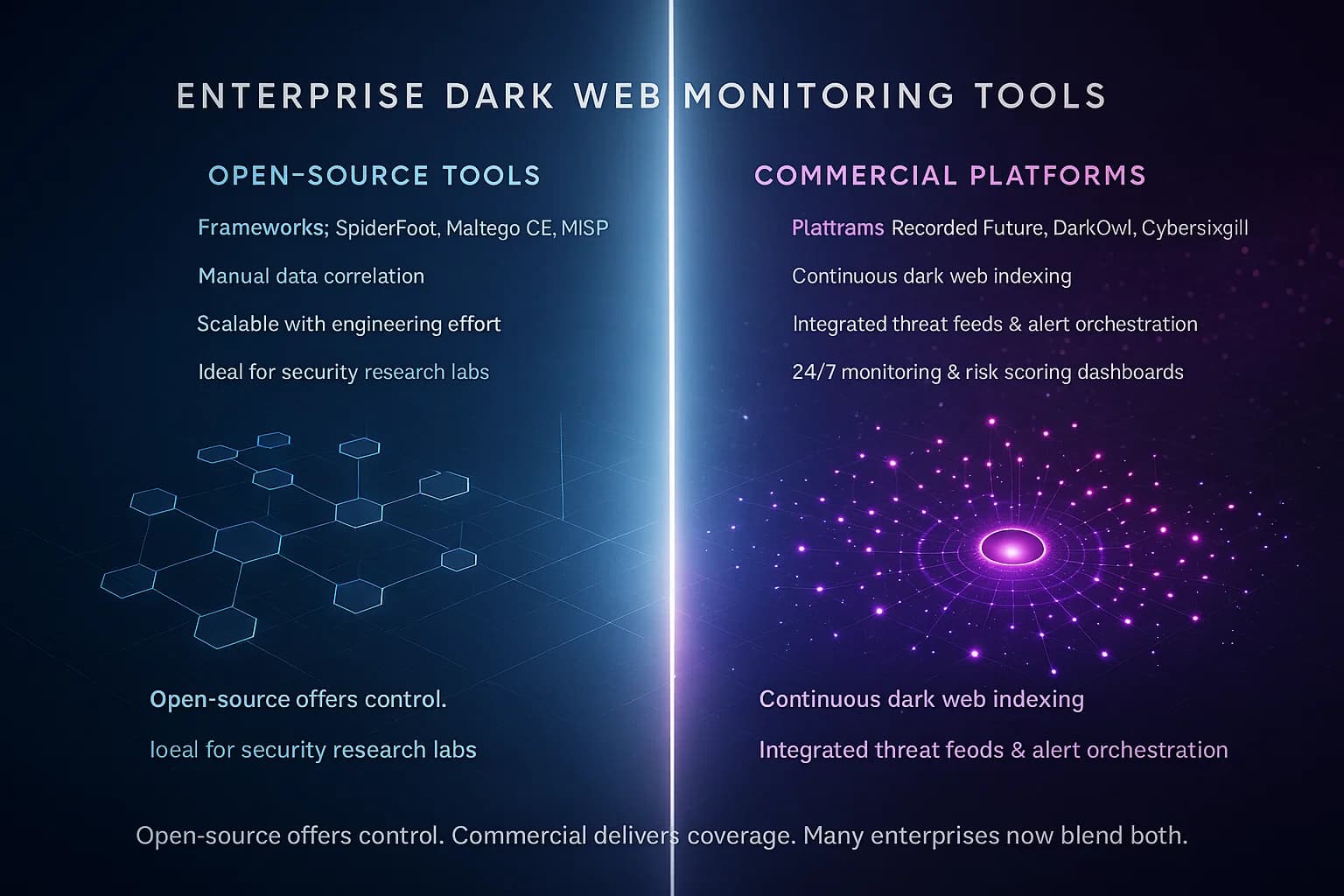
Organizations have much more at stake and typically require more comprehensive dark web monitoring. The tools available to businesses range from DIY open source projects that security teams can run themselves, to full service commercial platforms from cybersecurity vendors. Each has its place. Here we’ll explore both ends of the spectrum and how they compare.
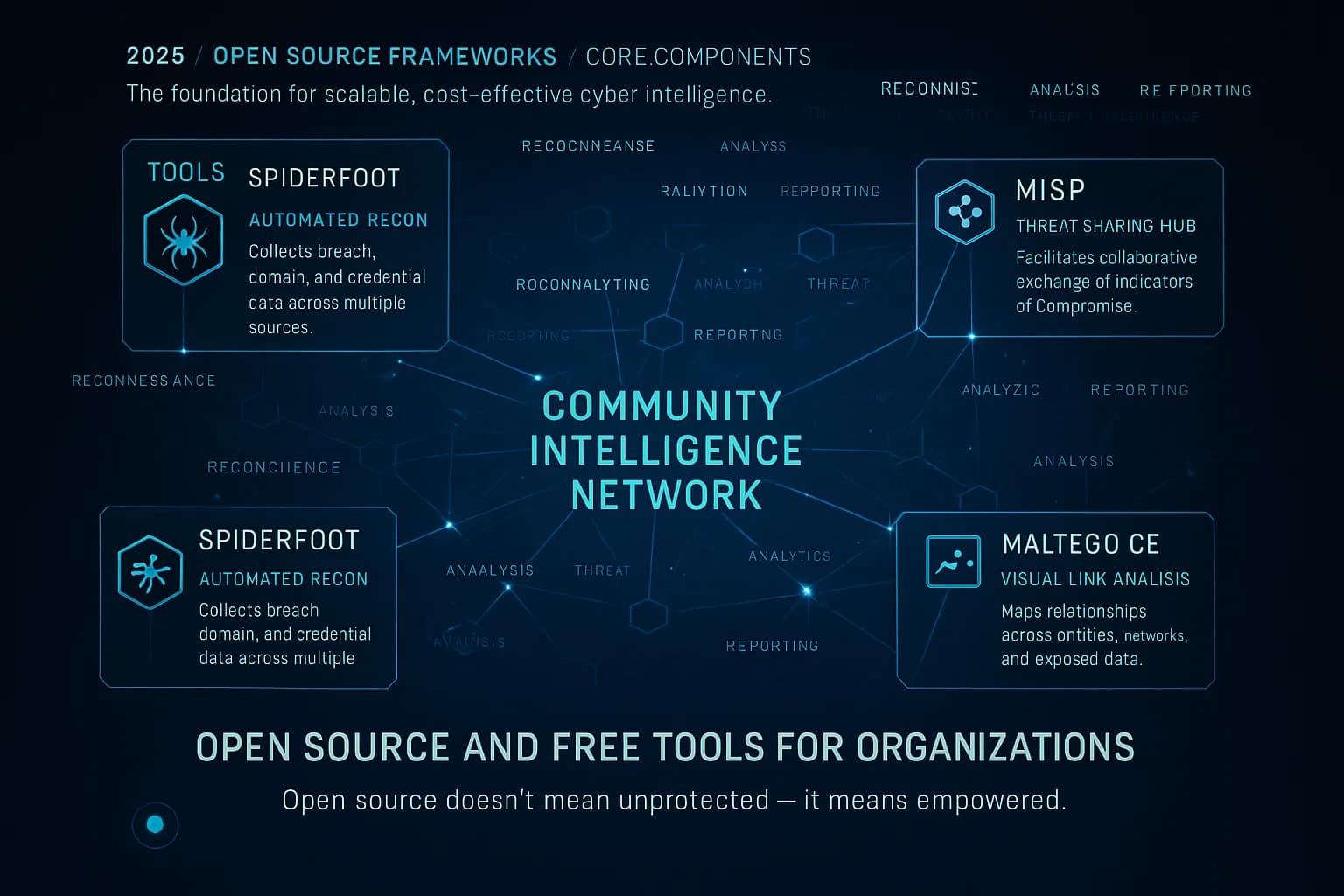
There’s a robust community of open source tools aimed at dark web OSINT Open Source Intelligence. These tools are free to use and modifiable, which appeals to teams with technical expertise and tight budgets. Some of the well known ones include:
What’s the upside of open source? In a word, control. You see exactly what the tool is doing, you can customize it, and you’re not paying licenses. For a security engineer or researcher, open tools are fantastic for digging into specific questions has this domain ever been mentioned on a hacker forum? and for integrating into custom workflows. They’re also great for learning and demonstrating concepts. Plus, open source fosters sharing platforms like MISP let companies exchange threat data easily, which can include dark web findings.
And the downside? These tools require TLC tender loving care. You or your team must install them, configure them, update them, and interpret the results. Coverage is a huge limitation: most open source dark web tools only touch the surface of what’s out there. They might catch public dump sites and some Tor search results, but they won’t have credentials to log into closed forums or the language skills to parse deep underground chatter. It’s the difference between looking through a keyhole vs opening the door as one expert put it, open source gives a peek, while paid solutions turn on the lights in the whole room. Open tools also lack the polished features companies often need, like instant alerting, report generation, or integration with compliance programs. You get what you pay for: no dedicated support, no guarantees. If a script breaks or a source disappears, it’s on you to fix it.
Finally, open source solutions do not provide compliance certificates or SLAs. You can’t tell an auditor we use a Python script from GitHub, trust us. Regulated industries often need the imprimatur of a vendor or at least documented processes. Open source projects don’t generate formal reports aligned to standards like HIPAA or ISO 27001. So while they help you technically, they might not check the box for auditors without extra effort.
Real world use: Many organizations take a hybrid approach they play with open source tools to augment and validate what their paid services find. For example, a security analyst might use SpiderFoot and Maltego to enrich an alert that came from a commercial feed, or to do a one off investigation into a specific threat actor. But for day to day coverage and on call alerts at 3 AM, they’ll lean on a managed solution.

On the other side of the spectrum, we have professional platforms offered by cybersecurity companies. These are typically subscription based services SaaS or managed service that promise full coverage of dark web sources, easy to use dashboards, and integration into your security operations. Some key players and categories include:
| Category | Examples | Key Features | Typical Pricing |
|---|---|---|---|
| Open Source DIY | MISP, SpiderFoot, TorBot, OnionScan, Ahmia | Community threat intel sharing; OSINT crawlers for public leaks and .onion sites; highly customizable | Free but labor intensive |
| Threat Intel Platforms | Recorded Future, DeepStrike, CrowdStrike Recon, SentinelOne, SOCRadar | Automated 24/7 crawling including private forums; AI driven analysis; SIEM/SOAR integrations; broad threat intelligence | Enterprise subscription |
| Digital Risk Protection | ReliaQuest GreyMatter, ZeroFox, Digital Shadows | Brand & VIP protection; monitors dark web + surface social media, domains; curated alerts and takedown services | Enterprise subscription |
| Credential Monitoring | Dark Web ID Kaseya, SpyCloud, SpyEye/BreachSense | Focus on stolen credentials and PII; huge breach data repositories; validated alerts for compromised accounts | SaaS licensing often , varies by org size |
| Data Feed/API | DarkOwl Vision, Webz.io, Sixgill | Raw access to indexed dark web content and IOCs; search and integrate into custom apps | Paid by data volume or subscription |
| Compliance Oriented | ImmuniWeb DWM, ManageEngine Constella | Pre mapped to GDPR, HIPAA etc. controls; reporting for audits; often part of larger security suite | Paid varies, often add on |
Enterprise dark web monitoring platforms typically offer unified dashboards to review leaked data and threats in real time. The example above shows a dark web monitoring interface listing exposed credentials found on underground forums. These solutions aggregate data from myriad dark web sources from hacker marketplaces to illicit Telegram channels and present actionable alerts with details like breach source and date in one place. Analysts can triage and investigate these findings through the portal, and many tools also allow integration, so alerts funnel into your SIEM or incident management system.
Advantages of paid solutions: The obvious one is coverage. Commercial providers have teams of analysts and automated bots lurking in places that an outsider simply can’t reach. They might operate sock puppet accounts on closed forums, have access to invite only groups, or buy data from brokers to include in their feeds. For example, ReliaQuest’s DRP boasts an archive of over 15 billion stolen credentials and tracks mentions of a client’s brand or assets across the open, deep, and dark web. That kind of scope is hard to replicate on your own. Secondly, you get real time, automated alerts without fiddling. The moment something pops up, they alert you often with context you’re not running manual searches each week and hoping to catch something. Integration and workflow are also key: these services often plug into your existing security operations. Got a SIEM like Splunk? The feed can go there. Using ServiceNow for tickets? They can auto generate one when a critical leak is detected. This means your team can respond faster and document actions, which is crucial during incident response.
Another selling point is expertise on tap. Many vendors include access to their intelligence analysts for clarification or takedowns. Let’s say you get an alert that someone on a forum is offering access to Your Company network starting bid 5 BTC. That’s scary and possibly time sensitive. A good vendor will not only alert you but can provide additional details e.g. how credible is this seller? have they sold access before? and guidance on what to do next. They might even coordinate with law enforcement if appropriate. This level of support and context is something DIY solutions won’t give you.
Compliance and reporting: As mentioned, paid tools help demonstrate that you’re exercising due diligence. Many platforms generate monthly or on demand reports showing all the findings, which can be handed to auditors or executives. They often highlight metrics like X credentials found and reset, Y credit card numbers found and flagged etc., showing that security is actively monitoring leakage. In sectors like healthcare or finance, having a formal vendor in this role can satisfy requirements in frameworks like SOC 2 or PCI DSS that call for threat monitoring. SentinelOne notes that dark web monitoring can help businesses maintain due compliance by ensuring they’re informed about potential breaches quickly.
The downside of paid tools: Cost is number one. These solutions can be expensive, often priced by the size of your organization or the number of assets you want to track. A small company might get a package in the low five figures annually, whereas a large enterprise or MSSP monitoring many clients could be looking at six figures. You’re also to some degree trusting a black box the vendors usually don’t reveal exactly how they gather their intel trade secrets and to prevent tipping off the bad guys. This lack of transparency can be uncomfortable for some; you have to trust the vendor’s ethics and security because ironically, they could potentially be handling or storing sensitive breach data from your org. Due diligence in choosing a reputable provider is important.
Another consideration is false sense of security. It’s easy to deploy a fancy monitoring tool and feel like Alright, we’re covered on dark web intel. But these tools, while powerful, aren’t magic. Something truly never before seen like a fresh zero day exploit being shared in a closed cell of criminals might not get caught. Or, the tool might alert you to something benign false positive that still needs analyst time to verify. You still need skilled staff to respond to the intel. Think of the tool as a burglar alarm it rings, but you must investigate and catch the burglar.
In practice: Enterprises often evaluate several providers. It’s common to do a trial where the vendor does an initial sweep of the dark web for your assets sometimes called a Dark Web Risk Assessment or similar. They’ll show you sample findings e.g. we found 3 GitHub tokens and 200 user passwords for your domain on the dark web. This gives you a taste of the value. If you engage them, you’ll typically configure a list of things to monitor: your company names, domains, key employee emails, project codewords, customer data patterns, etc. The service then runs continuously. You get a portal to log into and see all alerts, often categorized by severity. Many services also allow you to set up automated responses for example, if a user’s password is found, it can trigger an automatic password reset enforcement via your identity management system some integrations exist between dark web monitors and Active Directory or IAM tools to do this, as seen with DeepStrike’s identity protection integration.
To sum up, commercial dark web monitoring gives you scale, speed, and support that is hard to match. It fills in the blind spots that open source leaves and adds professional polish. The best approach is to use each for what they’re best at: leverage open source for flexibility and niche investigations, and rely on paid solutions for comprehensive, around the clock coverage and compliance needs.
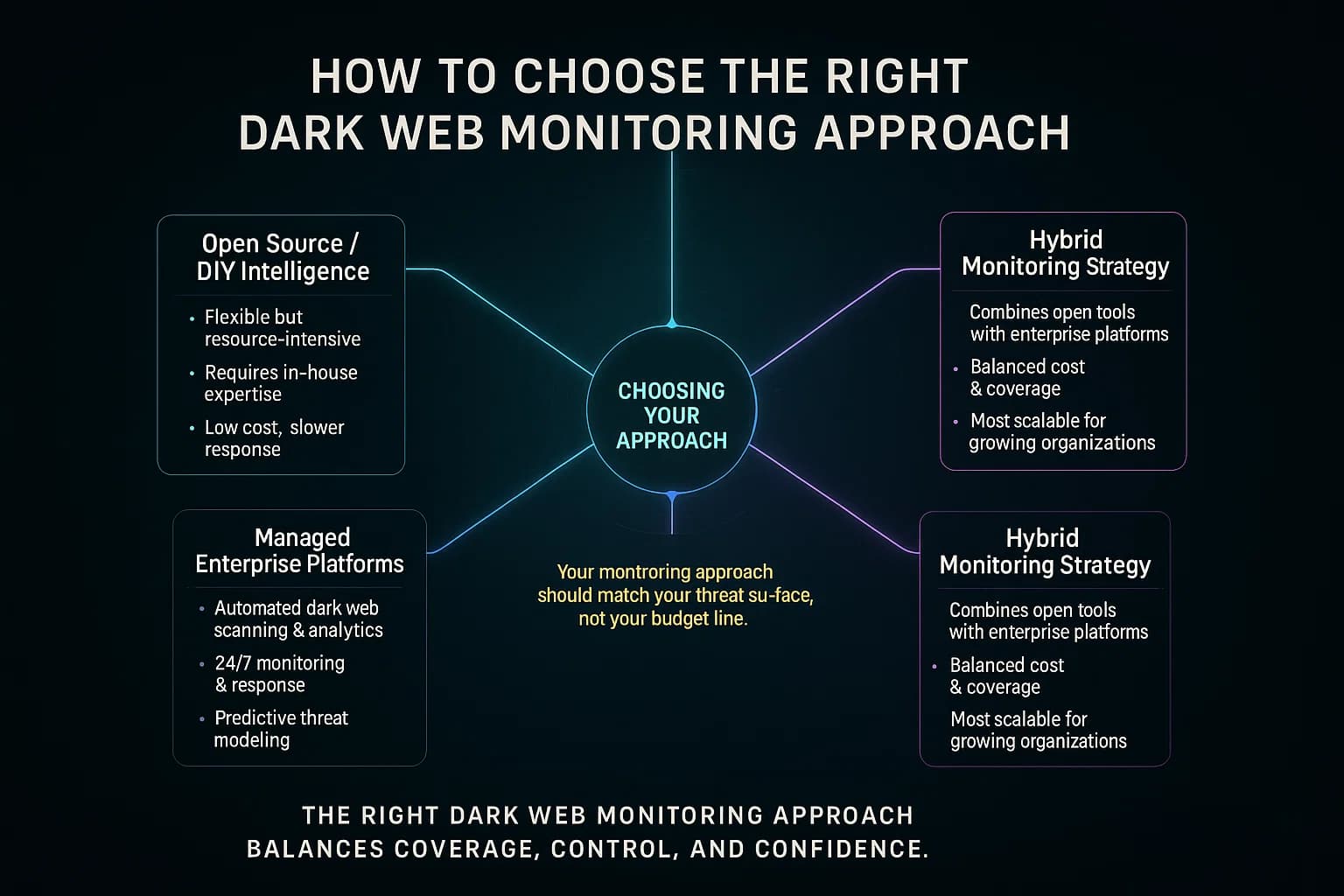
If you’re reading this and wondering, So… should I go with a free tool, buy a service, or both? here’s a practical way to approach the decision:
In many cases, organizations start with a free or low cost approach and then graduate to a paid service once they hit certain growth or an incident that proves the value. It’s not an either/or forever; you can pivot as needed. Also, don’t forget the simplest measure: security basics reduce the need for dark web findings. Strong passwords and using multi factor auth mean that even if credentials leak, they’re less useful. Good network monitoring means even if some data pops up online, you might have already caught the breach internally. Dark web monitoring is one layer of defense not a substitute for others like penetration testing or security awareness training.
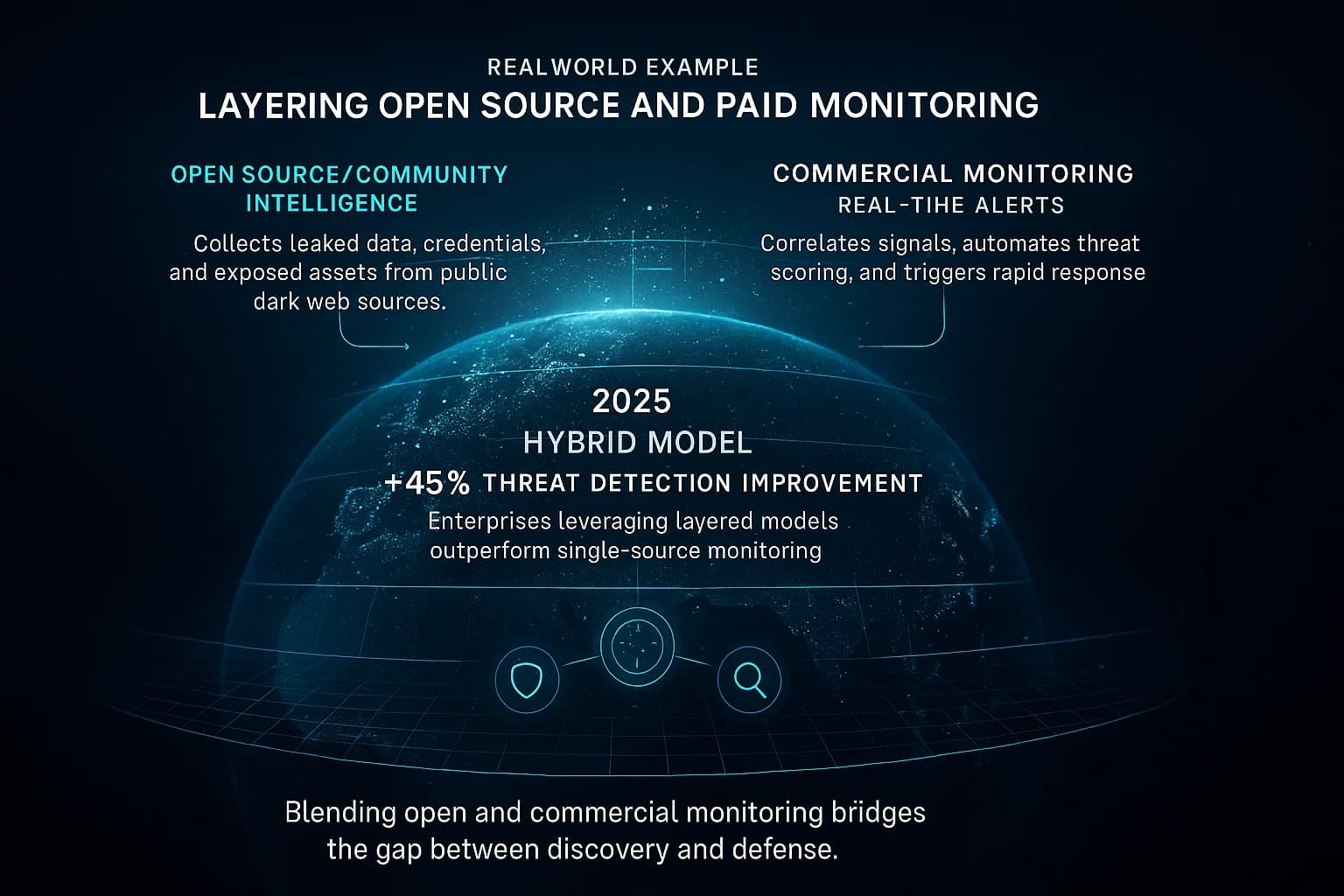
To illustrate, consider a mid sized tech company AcmeCorp. They handle user data and are concerned about leaks but can’t immediately invest in a top tier platform.
This scenario is common. Free tools gave some value, but a dedicated service was needed to catch the really critical stuff in time. Together, they created a strong net.
In the era of 2025, where breaches are not a question of if but when, dark web monitoring tools have become a critical component of cybersecurity strategy. They offer a chance to see early warning signs, leaked passwords, customer data up for sale, your company’s name in a hacker’s conversation and act before a bad situation explodes into a crisis.
For individuals, simple free tools like Have I Been Pwned provide a baseline of protection, and investing in a paid monitoring service can add an extra layer of identity safety. For organizations, balancing open source and commercial solutions can yield the best coverage: use community tools to stay flexible and informed, and rely on enterprise platforms to ensure you don’t miss the big stuff lurking in the shadows.
The key takeaways:
By staying vigilant and leveraging the right mix of tools, you can significantly strengthen your security posture. The dark web may be dark, but it doesn’t have to keep you in the dark about threats to your data.
Ready to Strengthen Your Defenses?The threats of 2025 demand more than just awareness; they require readiness. If you’re looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our Penetration Testing Services to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
About the Author:Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
The deep web refers to any online content that isn’t indexed by standard search engines for example, your private email account, database entries behind a password, company intranets, etc. It’s hidden in the sense that Google can’t crawl it, but it’s not illegal or malicious most of the internet is actually deep web. The dark web is a subset of the deep web that requires specific software like the Tor browser or authorization to access. Dark web sites often use encrypted networks and anonymization to hide their location and user identities. While the dark web itself is not inherently illegal, it’s become a breeding ground for criminal activity because of that anonymity. In short: deep web = unindexed but benign content, dark web = intentionally hidden, often shady content. Dark web monitoring specifically targets those hidden dark web sites, whereas general threat intelligence might also look at deep web sources like closed databases or chat logs.
Yes, monitoring the dark web is legal in most jurisdictions, as long as you’re simply observing or gathering publicly available information. Think of it like hiring a private investigator to walk through a bad neighborhood and report what they see; that’s generally fine. What would be illegal is actively participating in crimes on the dark web e.g. buying stolen data, distributing illicit material or unauthorized access to systems hacking into a dark site. Reputable dark web monitoring services operate by scraping forums, marketplaces, and paste sites without engaging in criminal transactions. They abide by the law while collecting intel. If you DIY, use caution: don’t download files or software from dark web sites, and obviously don’t log into anything or attempt to purchase illegal goods. Stick to passive collection. Another legal consideration: ensure compliance with data privacy laws e.g., if you find personal data of EU citizens on the dark web, handling that data still requires GDPR care but since it’s about preventing crime, it’s usually within legitimate interests to use it for security purposes. When in doubt, consult legal counsel, especially if venturing into gray areas like interacting with threat actors.
They use a mix of automated crawlers, human intelligence, and data partnerships. Automated crawlers bots are programmed to visit known dark web sites continuously these could be marketplaces, forums, or even torrent networks and scrape content. The tools parse this content for keywords or patterns like email addresses, or strings that look like credit card numbers. Many advanced tools employ machine learning to flag suspicious content for example, clustering discussions about certain company names or new exploits. Besides automation, vendors often have humans threat intel analysts who undercoverly join closed groups or scour hacker communities for invite codes, extending the reach of the monitoring. Some rely on data feeds from third parties for instance, a threat intel company might purchase dumps of stolen data from law enforcement or from other hackers and integrate that into their platform. In short, it’s an ever adapting game of web crawling + spying. The dark web isn’t indexed by Google, so these tools essentially build their own indexes through continuous effort.
It varies widely. For individuals, many identity protection services include dark web monitoring for $10- 30 per month as part of their package. For businesses, pricing depends on the provider and scope:
It’s important to note the potential ROI: One prevented breach could save you millions. Many companies justify the cost that way. If budget is tight, consider starting with a limited scope e.g. monitor just your top 50 employees and most sensitive data or seek vendors that work with MSSPs who can provide a multi-tenant service at lower cost.
To an extent, yes, you can DIY, but with caveats. You can set up an array of open source tools and scripts as discussed earlier, use SpiderFoot to aggregate OSINT, manually search on tor sites for your info, subscribe to free breach alert services, etc. Tech savvy individuals do this all the time for personal curiosity or research. However, doing it effectively at scale and continuously is a big task. If you go this route, you’ll need:
So yes, you can monitor on your own, but expect limited success unless you invest serious effort. For a one off check e.g. searching if your email is on a forum, DIY is fine. For continuous broad monitoring like an organization would need, that’s what commercial solutions are built for. A middle ground approach is to use a dark web scan free trial from a reputable vendor many will do an initial scan as a promo. This can supplement your DIY efforts by revealing things you might have missed.
Don’t panic, but act promptly and strategically. The steps depend on what data is found:
In all cases, document everything what was found, where, when, and actions taken. This is useful for any legal follow up and for improving future security. If you have cyber insurance, notify your provider as well; they often have resources to assist and you don’t want to violate terms by not informing them of an incident. Finally, learn from it: treat it as a fire drill to strengthen your defenses so it hopefully doesn’t happen again.
Not directly, they are more of a detection and intelligence tool than a preventative control. Think of it this way: dark web monitoring will tell you that your car’s alarm was bypassed and thieves are selling your stereo downtown… but it doesn’t stop them from breaking in, that’s what the locks and alarm were for. In cybersecurity terms, your preventative measures are things like firewalls, encryption, strong auth, employee training to avoid phishing, etc. Dark web monitoring kicks in after something has potentially gone wrong credentials stolen, data exfiltrated to limit the damage by informing you quickly. That said, it can have a preventative effect in a broader sense: by learning what attackers are up to, like seeing discussions of a new exploit targeting your industry, you can shore up defenses proactively preventing an attack that might have hit you if you were unaware. Also, if attackers know an organization uses dark web monitoring, they might be less inclined to use or sell that org’s data since it’ll get noticed fast and lose value. But generally, view it as part of your detection and response arsenal, not a shield that keeps attacks out to begin with. It complements penetration testing and other proactive security efforts; it doesn’t replace them.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us