June 26, 2025
Updated: June 26, 2025
Explore how the U.S., China, UK, Germany, Japan, and Australia are leading global cybersecurity investment and what it means for enterprise security strategy.
Mohammed Khalil

We are living in a $10.5 trillion cybercrime economy. By 2025, the annual cost of cybercrime is projected to dwarf the GDP of most nations, making it the world's third largest "economy" after the U.S. and China. This isn't a distant threat; it's a direct and escalating tax on global business. The sheer scale of this problem is staggering, as detailed in our latest cyber crime statistics report.
In response, global cybersecurity spending by country and by enterprise is experiencing unprecedented growth. Gartner forecasts that worldwide end user spending on information security will hit $212 billion in 2025, a sharp 15.1% increase from 2024. This surge is not optional; it's a fundamental reaction to a hyper evolving threat landscape.
Understanding these global spending dynamics is no longer a niche IT concern. It is a critical strategic imperative for CISOs, CFOs, and boards. This report moves beyond the headlines to dissect who is spending, why they are spending, and how they are allocating their budgets. We will analyze national priorities, uncover the key drivers forcing investment, and provide a framework for calculating the real return on your security spend. This is your guide to navigating the financial realities of cyber defense in 2025.
The macroeconomic view of cybersecurity spending reveals a market compelled into a state of rapid, sustained growth. Faced with threats that are more automated, sophisticated, and widespread than ever before, nations and corporations are left with no choice but to escalate their defensive investments. This section breaks down the top line forecasts and dissects the spending patterns of the world's key economic powers.
Multiple top tier analyst firms project strong, double digit growth for the cybersecurity market, signaling a powerful and non negotiable investment cycle. While specific figures vary based on methodology such as tracking end user spending versus total market value the consensus points to a market that is not just growing, but accelerating.
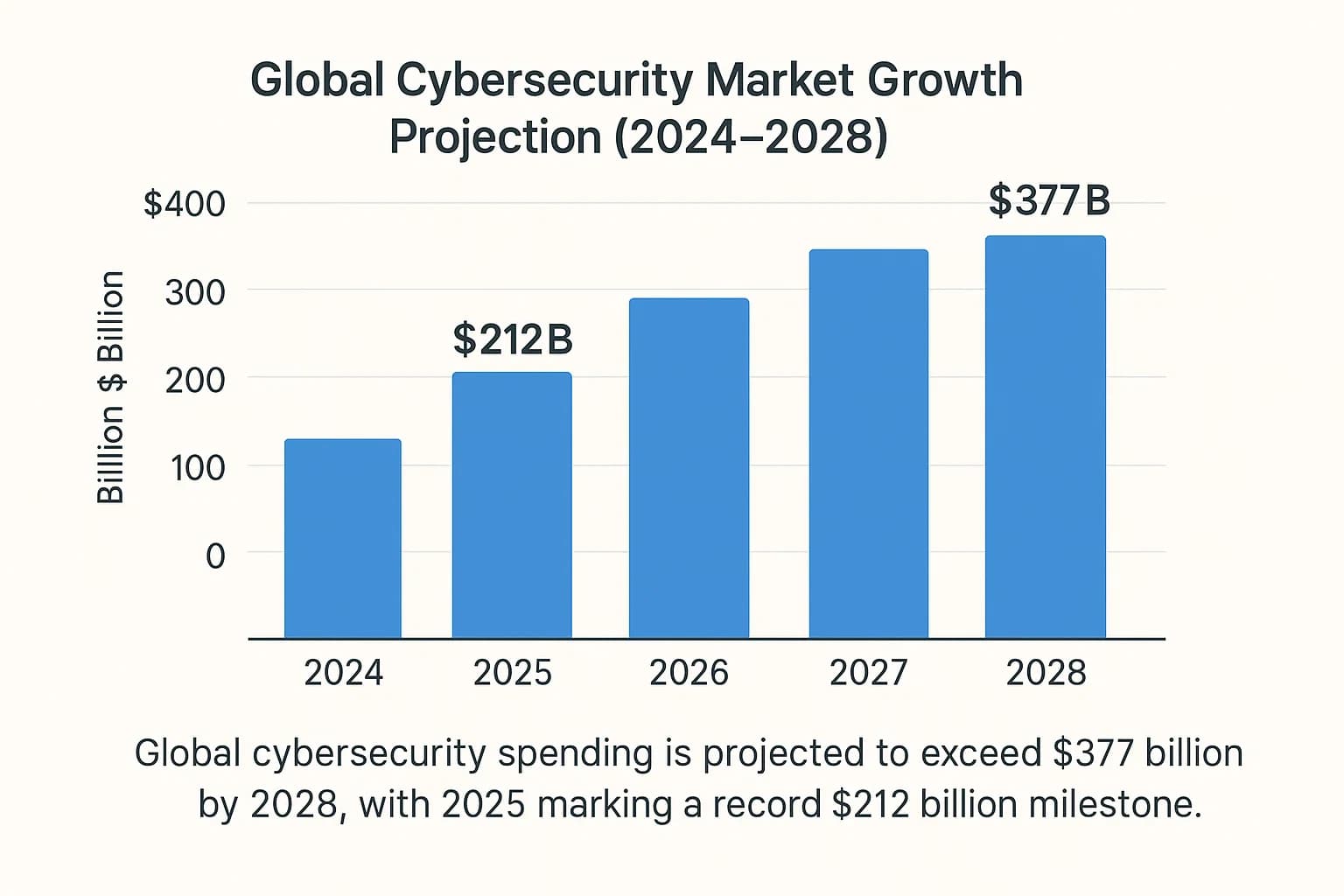
Gartner provides the most widely cited benchmark, projecting a 15.1% year over year growth to reach $212 billion in 2025. This marks a three year growth peak, indicating that investment is picking up pace, not slowing down. The International Data Corporation (IDC) offers a slightly more conservative 12.2% growth forecast for 2025 but sees a longer term trend of sustained investment, predicting the market will hit $377 billion by 2028.
This spending is not uniform across all categories. Security software remains the largest and fastest growing segment, projected to increase by 15% to nearly $101 billion in 2025. It is closely followed by security services, which are expected to jump 15.6% to over $86 billion. This dual focus highlights a clear market strategy: organizations are simultaneously acquiring advanced tools to combat modern threats while outsourcing the expertise needed to effectively manage them.
A significant portion of this growth is directly attributable to the rise of Generative AI. Gartner anticipates that the need to secure GenAI will trigger a 15% spike in security software spending as organizations grapple with protecting new AI driven workflows and defending against AI powered attacks.
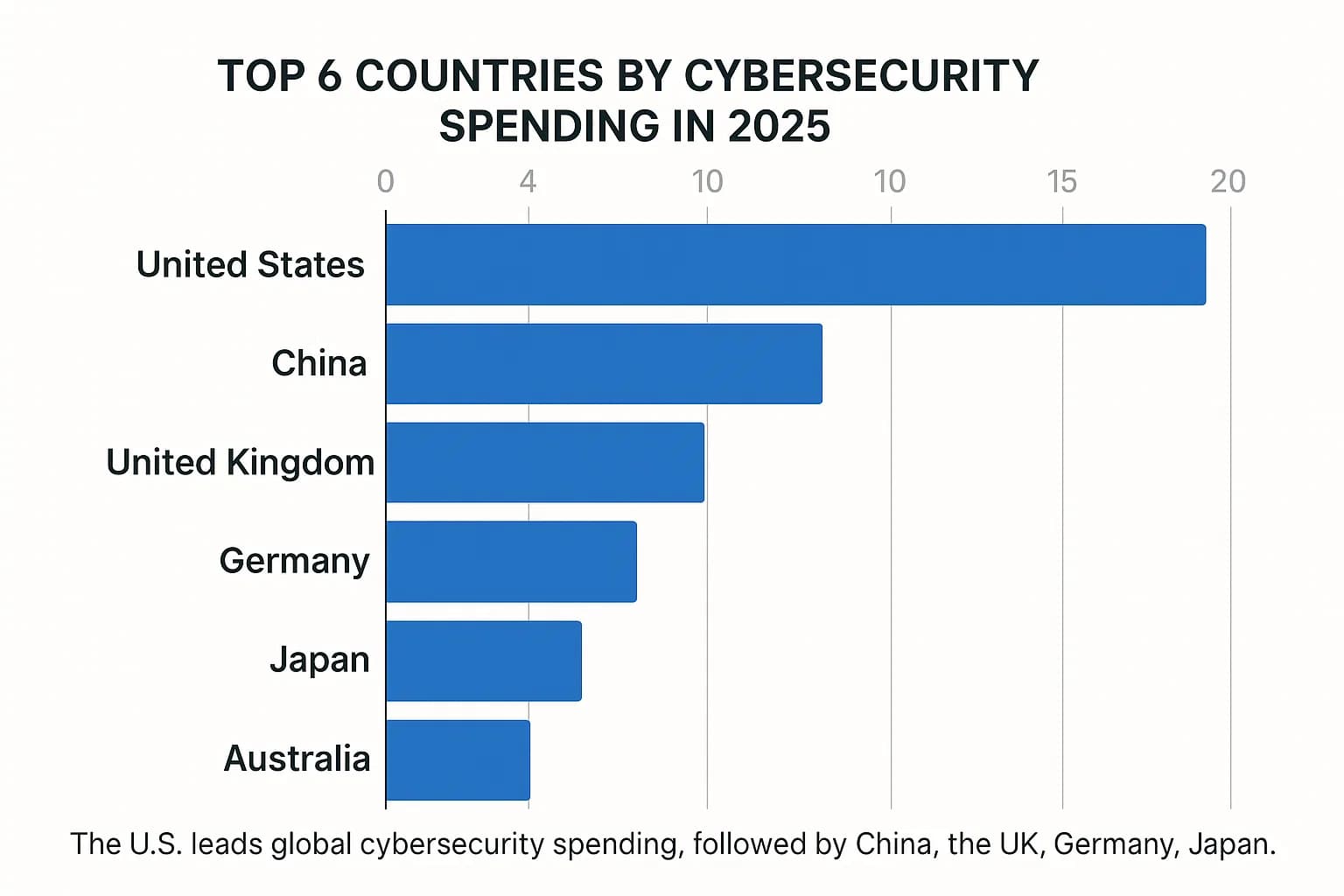
While global spending is on the rise, the distribution and strategic priorities vary significantly from one nation to another. A closer look reveals how national interests, economic structures, and geopolitical pressures shape cybersecurity investment strategies.
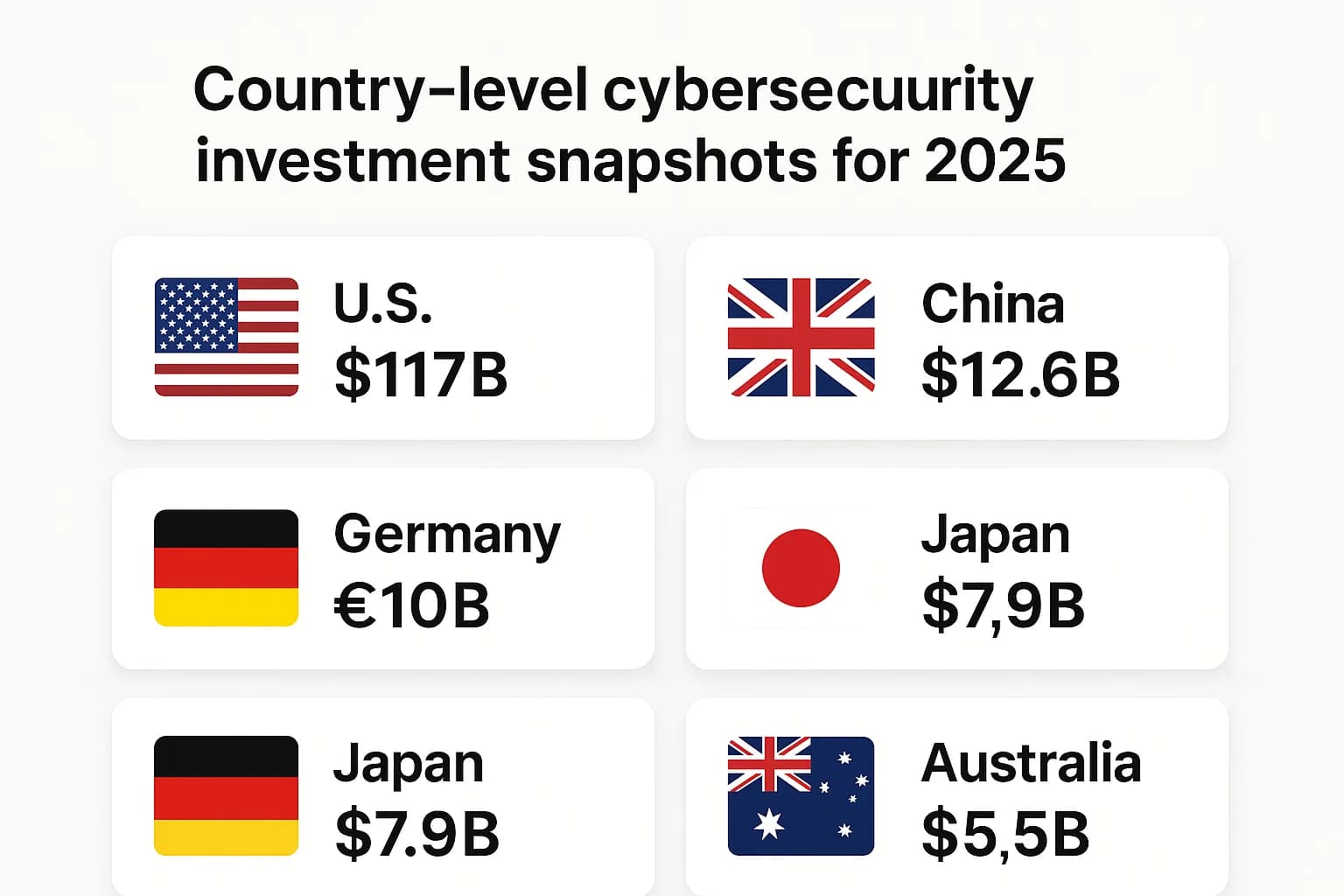
The spending data reveals a fascinating paradox. The United States leads in absolute spending by a massive margin, yet when measured by cyber readiness and preparedness indices like the National Cyber Security Index (NCSI), it often ranks behind smaller, more agile nations such as Belgium, Lithuania, and Estonia. This suggests that the way money is spent is more critical than the sheer amount. A smaller nation with a highly coordinated national strategy, strong public private partnerships, and an unwavering focus on foundational cyber hygiene can achieve greater resilience than a larger nation with a fragmented, tool heavy approach. This is a crucial lesson for CISOs: a bigger budget is not a silver bullet. Strategic allocation, process maturity, and investment in human factors are the real differentiators.
The surge in global cybersecurity spending is not happening in a vacuum. It is a direct reaction to a handful of powerful, interconnected forces that are fundamentally reshaping the digital risk landscape. Understanding these catalysts is essential for any leader tasked with building a defensible budget.
Artificial Intelligence is the single most disruptive force in cybersecurity today, acting as both a powerful weapon and an indispensable shield. On the one hand, attackers are weaponizing generative AI to create hyper realistic phishing emails, deepfake social engineering campaigns, and adaptive malware that can bypass traditional defenses. The barrier to entry for launching sophisticated attacks has been dramatically lowered. Gartner predicts that by 2027, 17% of all data breaches will involve generative AI in some capacity.
On the other hand, organizations are compelled to invest heavily in their own AI powered security tools for advanced threat detection, automated incident response, and behavioral anomaly analysis. The business case is compelling: organizations that extensively use security AI and automation save an average of $2.2 million in data breach costs compared to those that do not. This dual nature of AI is a primary spending driver, with Gartner directly linking the rise of GenAI to a projected 15% increase in security software spending. The rapid evolution of these threats is a central theme in our Malware Attacks and Infections analysis.
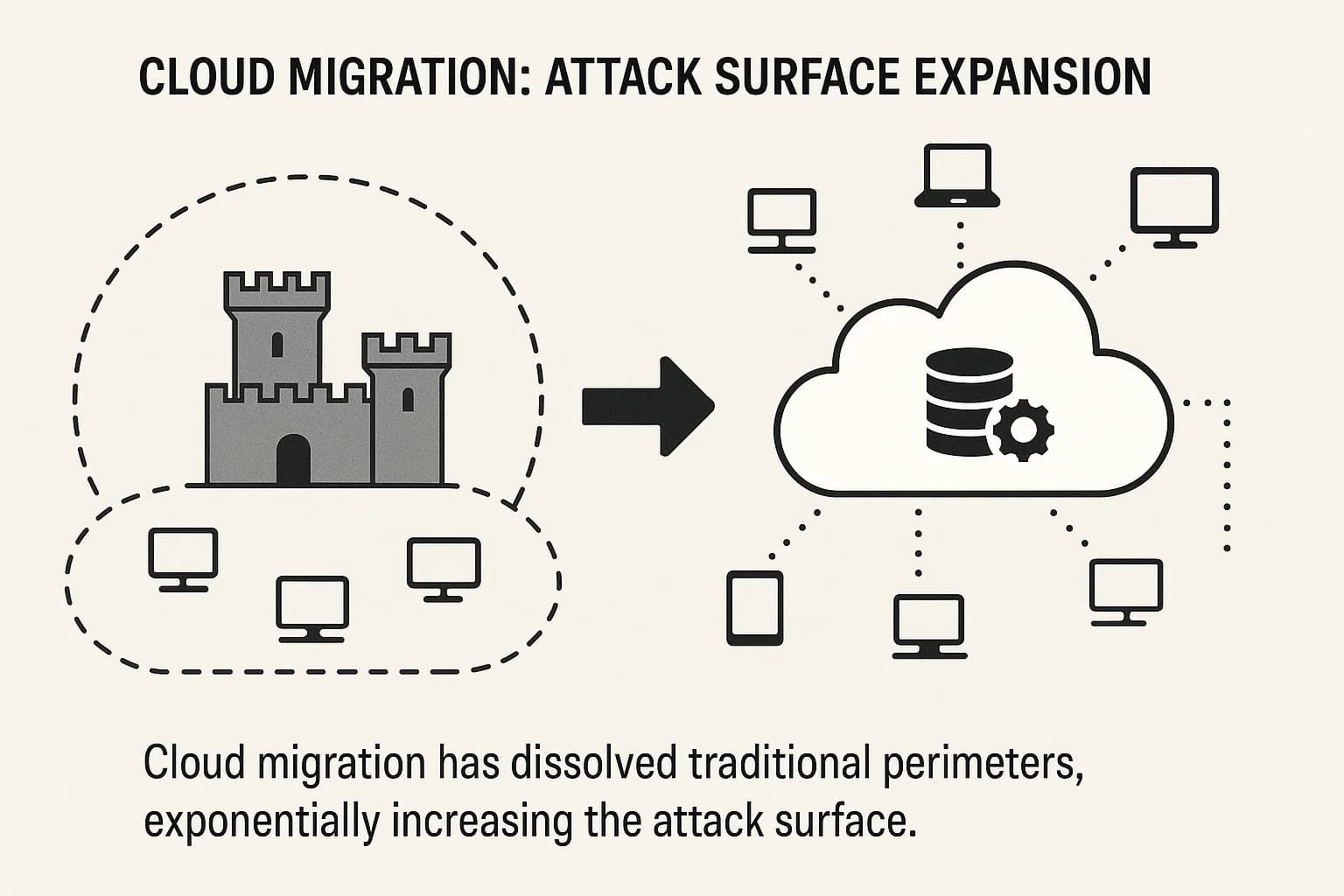
In 2025, digital transformation is synonymous with cloud adoption. However, this strategic shift from on premise data centers to sprawling, multi cloud environments has effectively dissolved the traditional network perimeter, dramatically expanding the attack surface. Security is no longer about building a strong wall around a castle; it's about protecting countless assets scattered across a borderless digital landscape.
Cloud specific risks now dominate the threat landscape. Misconfigurations, insecure APIs, and identity based attacks have become the most common entry points for adversaries. According to a recent IBM report, a staggering 82% of data breaches now involve data stored in the cloud. This reality is forcing a massive reallocation of security budgets toward cloud native security tools. The combined market for Cloud Access Security Brokers (CASB) and Cloud Workload Protection Platforms (CWPP) is estimated to hit $8.7 billion in 2025. Consequently, organizations are prioritizing investments in Cloud Security Posture Management (CSPM) and Identity and Access Management (IAM) to regain visibility and control. Securing these new architectures requires a deep understanding of cloud native weaknesses, including GraphQL API vulnerabilities.
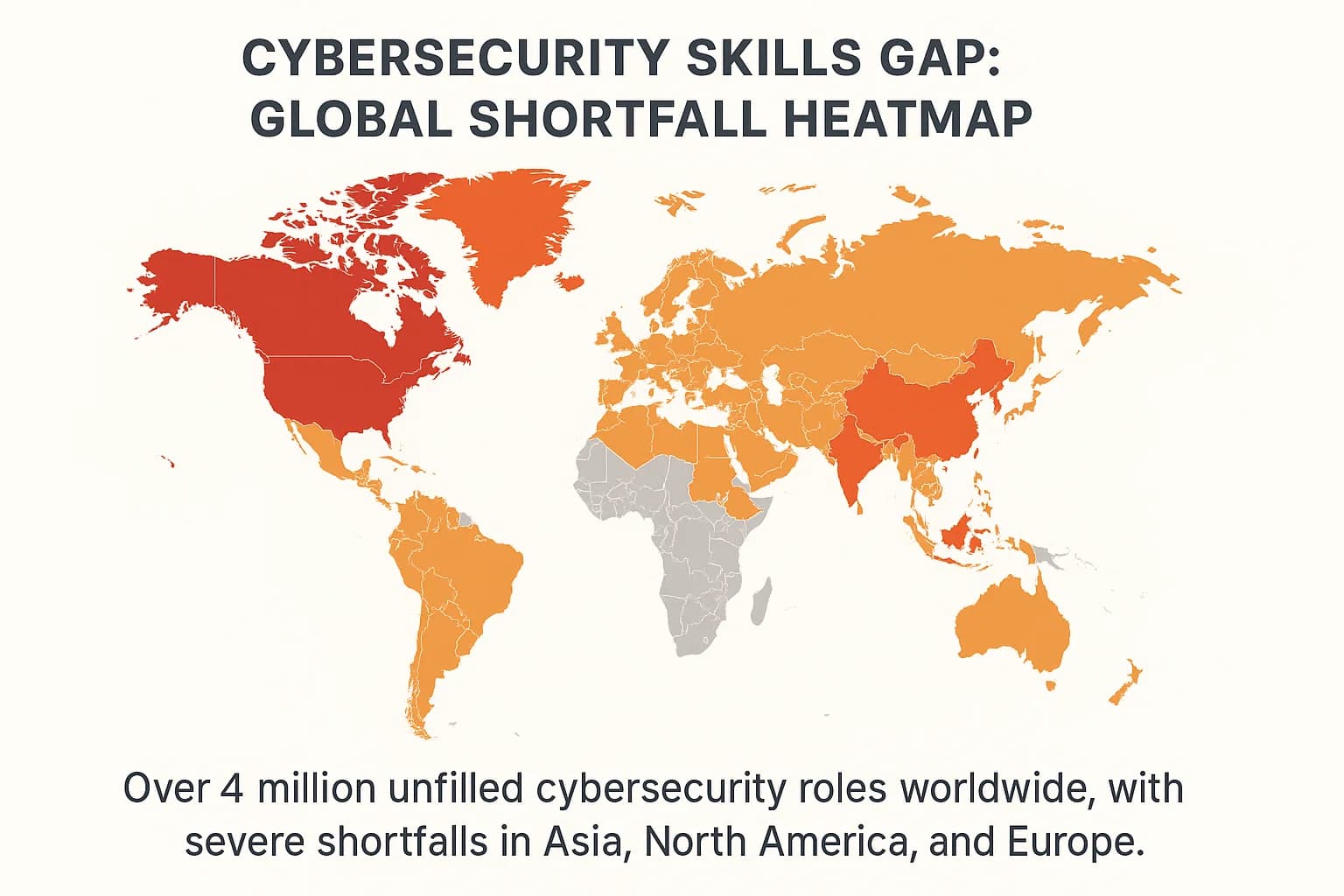
A critical, and often underestimated, driver of spending is the severe global shortage of skilled cybersecurity professionals. There is currently a talent gap of over 4 million workers worldwide, a figure the World Economic Forum projects could swell to 85 million by 2030. This isn't just an HR problem; it's a direct financial risk. Organizations reporting a high level skills shortage face average breach costs of $5.74 million, significantly higher than the $3.98 million faced by those with adequate staffing.
Unable to hire and retain the necessary in house talent, companies are increasingly turning to the security services market. This has fueled explosive growth in security consulting, managed security services, and flexible delivery models like penetration testing as a service ptaas. The security services market is now expected to grow faster than any other security segment, as businesses choose to "rent" the expertise they cannot "buy".
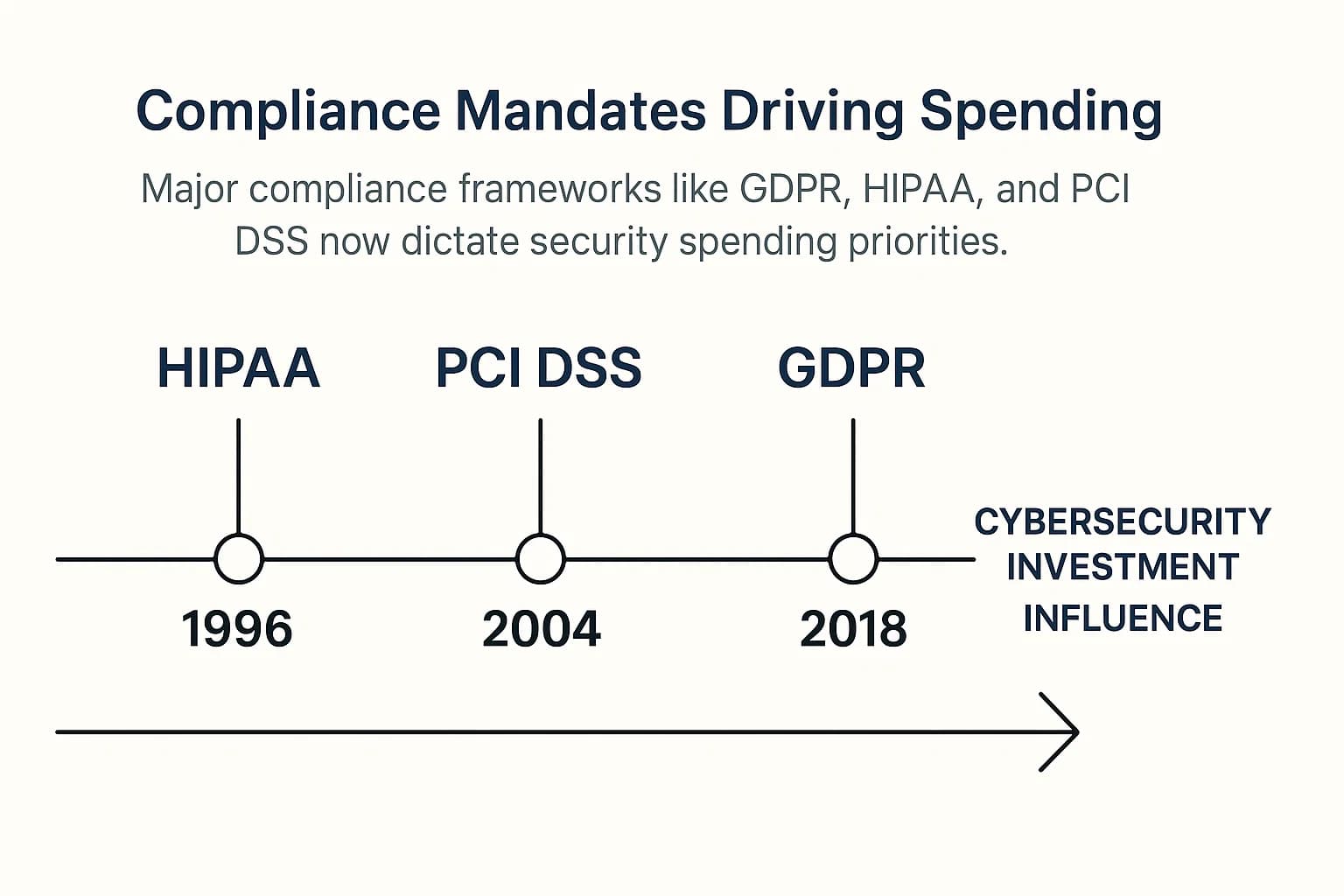
A complex and ever expanding web of regulations is acting as a powerful forcing function for cybersecurity investment. Mandates like the General Data Protection Regulation (GDPR) in Europe, the Health Insurance Portability and Accountability Act (HIPAA) in the U.S., and the Payment Card Industry Data Security Standard (PCI DSS) globally are no longer mere suggestions. They are strict legal requirements backed by severe financial penalties for non compliance.
These regulations often dictate specific security controls and validation activities, directly shaping budget allocations. For example, PCI DSS 4.0 explicitly requires both annual penetration tests and quarterly vulnerability scans by an Approved Scanning Vendor (ASV), leaving no room for interpretation. This regulatory pressure is a major factor in purchasing decisions; in Germany, for instance, 89% of organizations cite regulation as a significant driver of their increased cyber spending. As a result, compliance has become a top three driver for security investment, with budgets needing to account for audits, specialized tooling, and validation services to meet these legal obligations. For healthcare organizations, our HIPAA penetration testing guide breaks down these specific requirements in detail.
These four drivers do not operate in isolation. They form a powerful, interconnected feedback loop. Consider a company undergoing a cloud migration that adopts new AI powered tools. This expands the attack surface, but the internal team lacks the skills to secure it due to the skills gap. This situation creates a high risk of non compliance with regulations like GDPR. The CISO is therefore compelled to allocate budget to a managed cloud security provider and a specialized PTaaS platform, a single strategic investment that addresses all four drivers simultaneously. Understanding this interconnectedness is the key to building a truly holistic and defensible budget.
In an environment of intense scrutiny, CISOs must evolve from technical managers into strategic business partners. This means building a cybersecurity budget that is not just a list of expenses, but a compelling business case rooted in risk reduction and value creation.
The most pervasive myth in cybersecurity budgeting is that a bigger budget automatically equates to better security. The data unequivocally proves this is false.
The 2025 CYE Cybersecurity Maturity Report explicitly confirms that more spending does not lead to safer businesses. The "Spend vs. Readiness" paradox observed at the national level provides further evidence: countries like Japan and Norway achieve higher cyber readiness scores than the US or UK, despite having smaller absolute budgets. This demonstrates that a well coordinated strategy and a focus on fundamentals can outperform raw spending.
The real issue is often not the size of the budget but its allocation. Many organizations fall into the trap of spending on "shiny new tools" while neglecting foundational cyber hygiene, such as patch management and user training. A lack of clear visibility into the true attack surface means that money is often spent protecting the wrong assets or defending against the wrong threats. The first step in smart spending is to understand your real world weaknesses, which is why differentiating between a vulnerability assessment vs penetration testing is so critical to an effective strategy.
For decades, CISOs have struggled to justify security spending in terms that resonate with the C suite. The perception of cybersecurity as a cost center persists, with only 18% of executives viewing it as a stand alone budget. A helpful way to reframe the conversation is to think of your cybersecurity budget like home insurance. You don’t buy it hoping to use it, but you’d never skip it. It's a strategic investment in protecting your most valuable assets. For the majority (68%), it remains part of the IT budget, forced to compete with other operational priorities.
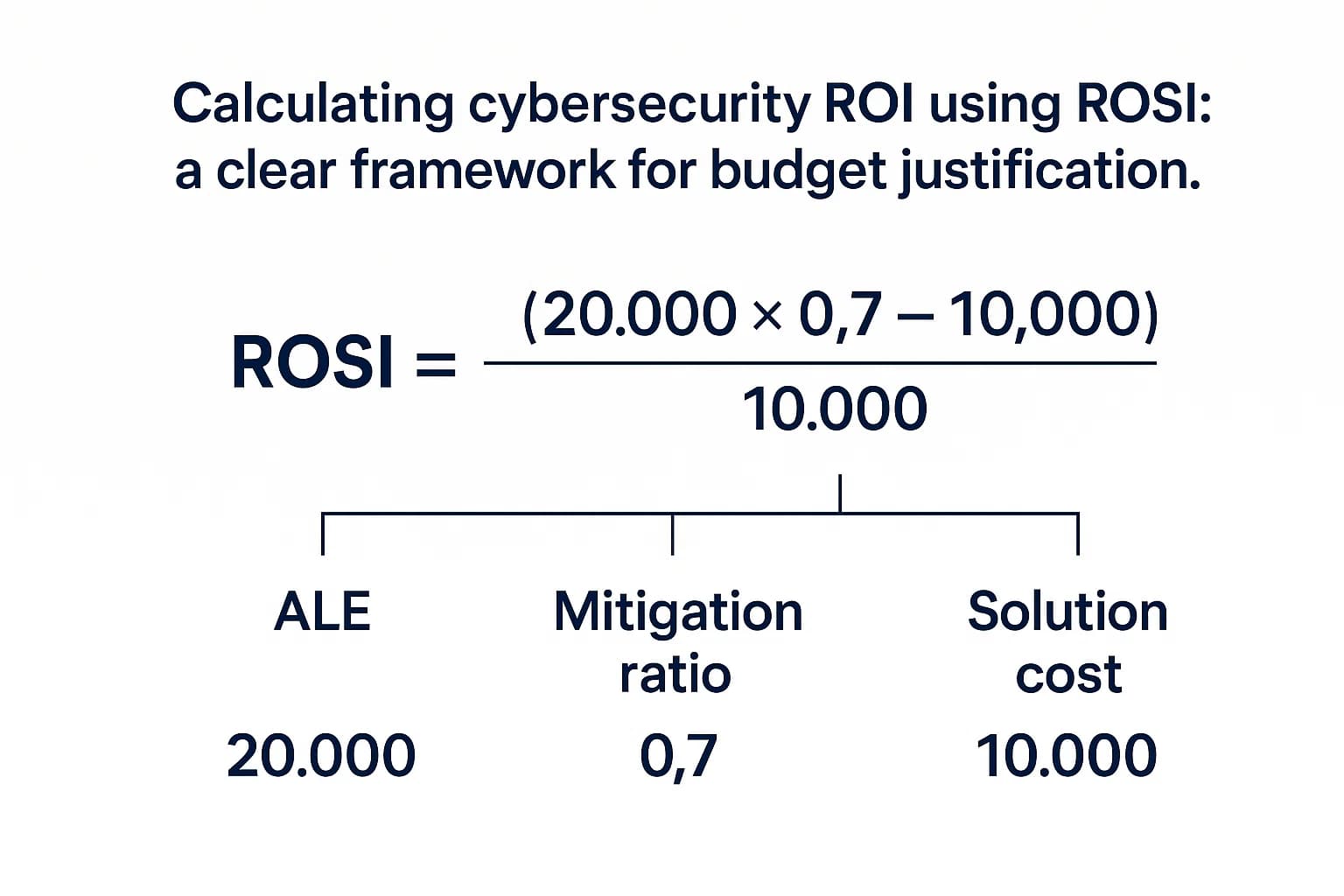
The solution is to shift the conversation from cost to value by calculating the Return on Security Investment (ROSI). This financial framework reframes security as a mechanism for loss prevention and business enablement.
The formula is straightforward: ROSI = ( – Cost of Solution) / Cost of Solution
Here’s a practical example:
This calculation transforms the budget request. The conversation is no longer, "Can we afford this $150,000 tool?" Instead, it becomes, "Can we afford not to invest $150,000 to prevent a potential loss of $890,000?" To calculate your potential losses accurately, you need up to date figures from our data breach statistics report.
Building a modern, defensible budget requires a focus on strategic priorities that deliver the greatest risk reduction.
To illustrate these principles in action, consider the case of "FinSecure," a composite mid sized global bank based on real world scenarios.
FinSecure faced a familiar predicament: rising cyber insurance premiums, mounting pressure from regulators, and a security budget that was growing but failing to improve their actual risk posture. Their traditional approach consisted of annual, compliance driven spending that left them perpetually behind the threat curve. The breaking point came after a minor but costly data breach originating from a third party vendor, which exposed critical weaknesses in their supply chain security and incident response capabilities.
The new CISO initiated a fundamental strategic shift, moving the budget away from a reactive, tool based model to a proactive, risk based one.
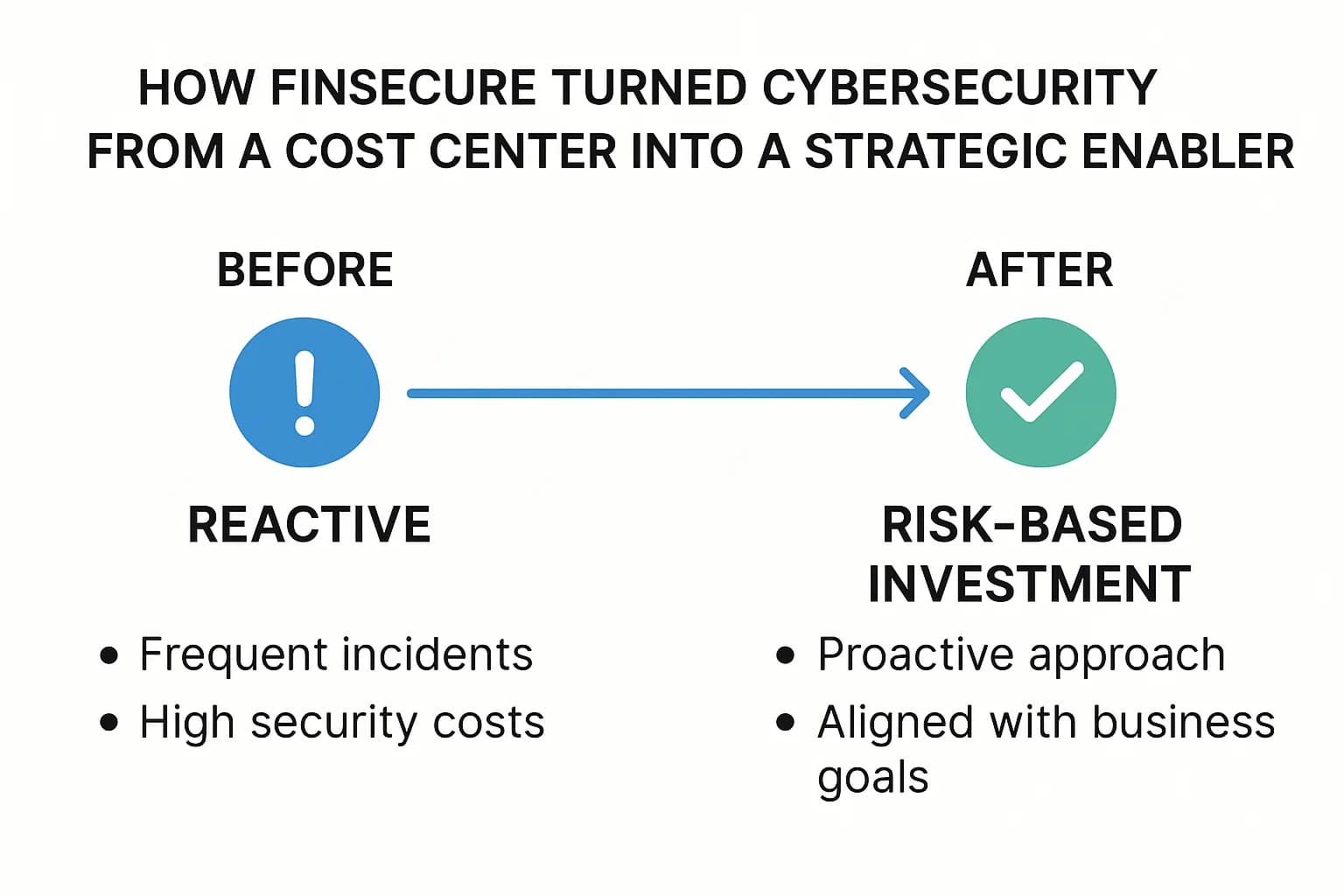
The results were transformative. Within 18 months, FinSecure reduced its mean time to detect (MTTD) threats by over 60%, lowered its projected Annualized Loss Expectancy (ALE) by 45%, and successfully negotiated a 15% reduction in its cyber insurance premium. Their security budget was no longer a contentious cost center but a defensible, value driving investment. Their success was driven by a deeper understanding of their true attack surface, a core benefit of evolving from simple vulnerability scanning to a full red team vs blue team exercise model.
The United States is the largest spender in absolute terms, accounting for over 40% of the global market. Its cybersecurity market value was $79.37 billion in 2023 and continues to lead all other nations by a significant margin.
This varies dramatically by company size and industry. As a benchmark, large enterprises are expected to allocate approximately 13.2% of their total IT budget to security. For small and medium sized businesses (SMBs), the allocation typically ranges from 4% to 15% of their IT budget, depending on their risk profile.
There is no single magic number, but industry benchmarks for 2025 suggest a range of 8% to 15% of the total IT budget is a common and defensible allocation, up significantly from the 5% average seen in 2019. High risk industries, such as finance and healthcare, often allocate more, typically in the 10% to 13.3% range.
The top drivers are the dual threats and opportunities presented by Artificial Intelligence, the security complexities of mass migration to the cloud, the persistent global cybersecurity skills shortage forcing reliance on services, and increasing pressure from government and industry regulations.
Yes, all major analyst firms predict sustained, double digit annual growth for the foreseeable future. IDC, for example, forecasts the global cybersecurity market will reach $377 billion by 2028, driven by the escalating cost and sophistication of global cybercrime.
The most common method is calculating the Return on Security Investment (ROSI). This is done by comparing the cost of a security solution to the amount of financial loss it prevents. The formula involves multiplying the Annualized Loss Expectancy (ALE) by the solution's mitigation rate, subtracting the solution's cost, and then dividing by the solution's cost.
While high profile threats like ransomware command attention, the most pervasive threat vector remains the human element. Attackers exploit people via phishing and the use of stolen credentials in over 80% of all breaches. This reality drives consistent, heavy spending on Identity and Access Management (IAM), Multi Factor Authentication (MFA), and continuous security awareness training, a fact underscored by our latest password statistics.
The era of cybersecurity as a simple IT line item is definitively over. In 2025, global spending will continue its relentless climb, but the narrative has fundamentally shifted from quantity to quality. The data is clear: throwing money at the problem is a failing strategy. The world's most cyber resilient nations and organizations are pivoting from reactive, compliance driven spending to proactive, risk based investment.
The key takeaways are unmistakable:
Your cybersecurity budget is more than a defense mechanism; it's a strategic enabler for digital transformation, a protector of customer trust, and a core pillar of business continuity. Navigating this complex landscape requires more than just data; it requires expert guidance.
Need expert guidance? We’re here to help. Whether you’re planning a security strategy, facing compliance challenges, or just want an expert opinion, Reach out. At DeepStrike, we don’t sell fluff, just clear, actionable advice from real world practitioners.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us