November 4, 2025
Updated: November 4, 2025
Fintech now accounts for 27% of all data breaches, averaging $5.9M per incident. Learn the key breach trends, crypto losses, third-party risks, and how penetration testing helps stop attacks before they strike.
Mohammed Khalil

Fintech breach statistics refers to data on cybersecurity incidents affecting financial technology companies, banks, digital wallets, crypto exchanges, insurtech, etc.. These stats include breach frequency, costs, data types exposed, and trends over time. In practical terms, we track how often fintech firms are attacked, what is stolen, and the financial impact. This matters because fintech handles sensitive financial data, so breaches can erode trust and incur huge losses.
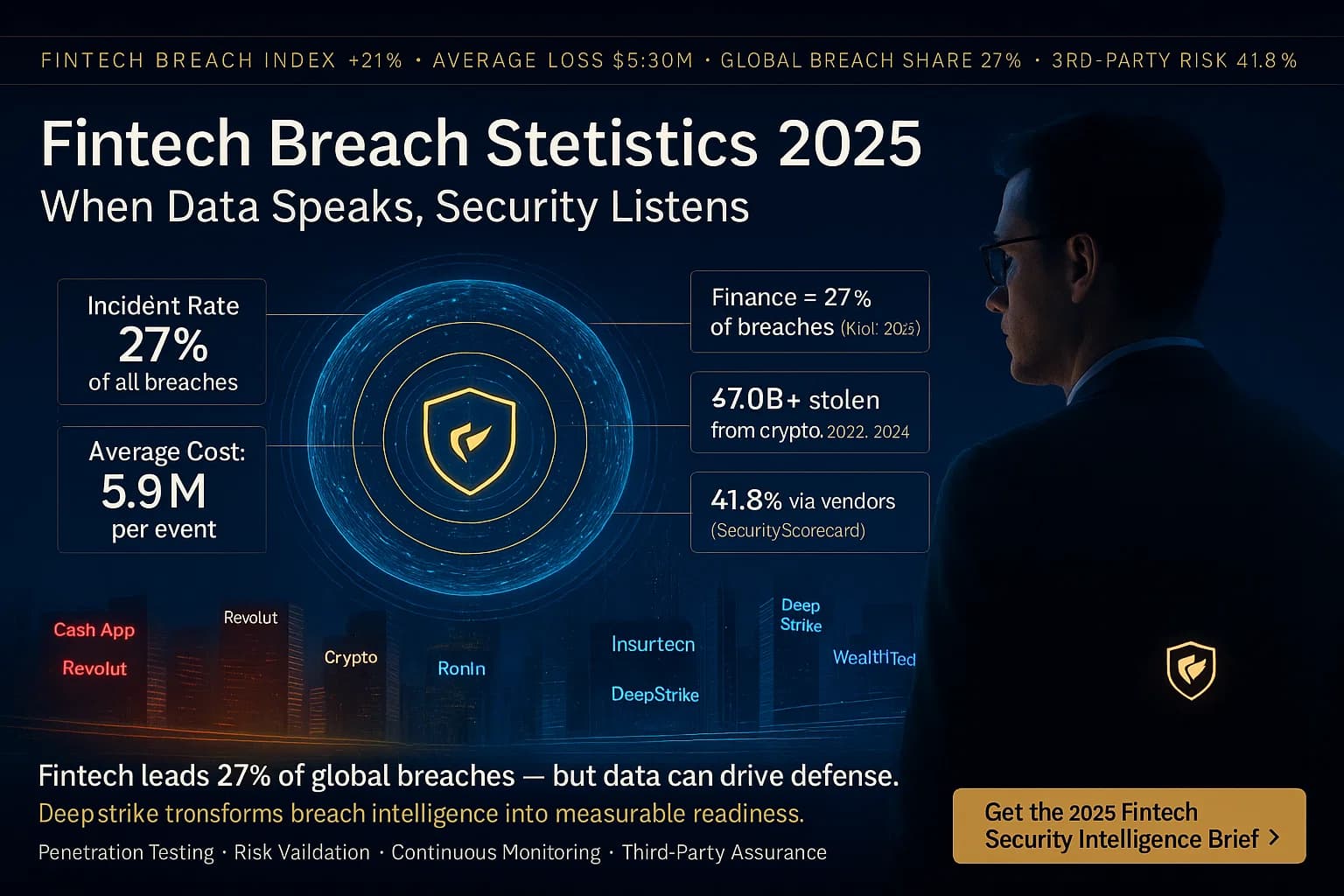
Fintech breaches have spiked in recent years. For example, Kroll’s 2024 report found the financial sector jumped to 27% of all breaches handled in 2023 up from 19% in 2022. In other words, 1 in 4 breaches Kroll dealt with was in finance. This aligns with more publicized hacks crypto thefts, bank hacks, payment app incidents and suggests fintech is now the most attacked industry. As DeepStrike cybersecurity analysts note, attackers see fintech as high value targets rich data and direct money transfers.
These statistics are critical now because fintech is booming. Rapid digital adoption online banking, mobile wallets, crypto expands the attack surface. High profile incidents see below and regulatory fines underscore that breaches aren’t hypothetical they happen frequently and cost millions. Companies like DeepStrike often advise clients that knowing the stats helps prioritize security: e.g. focusing on third party risk or insider threats if those drive most breaches.

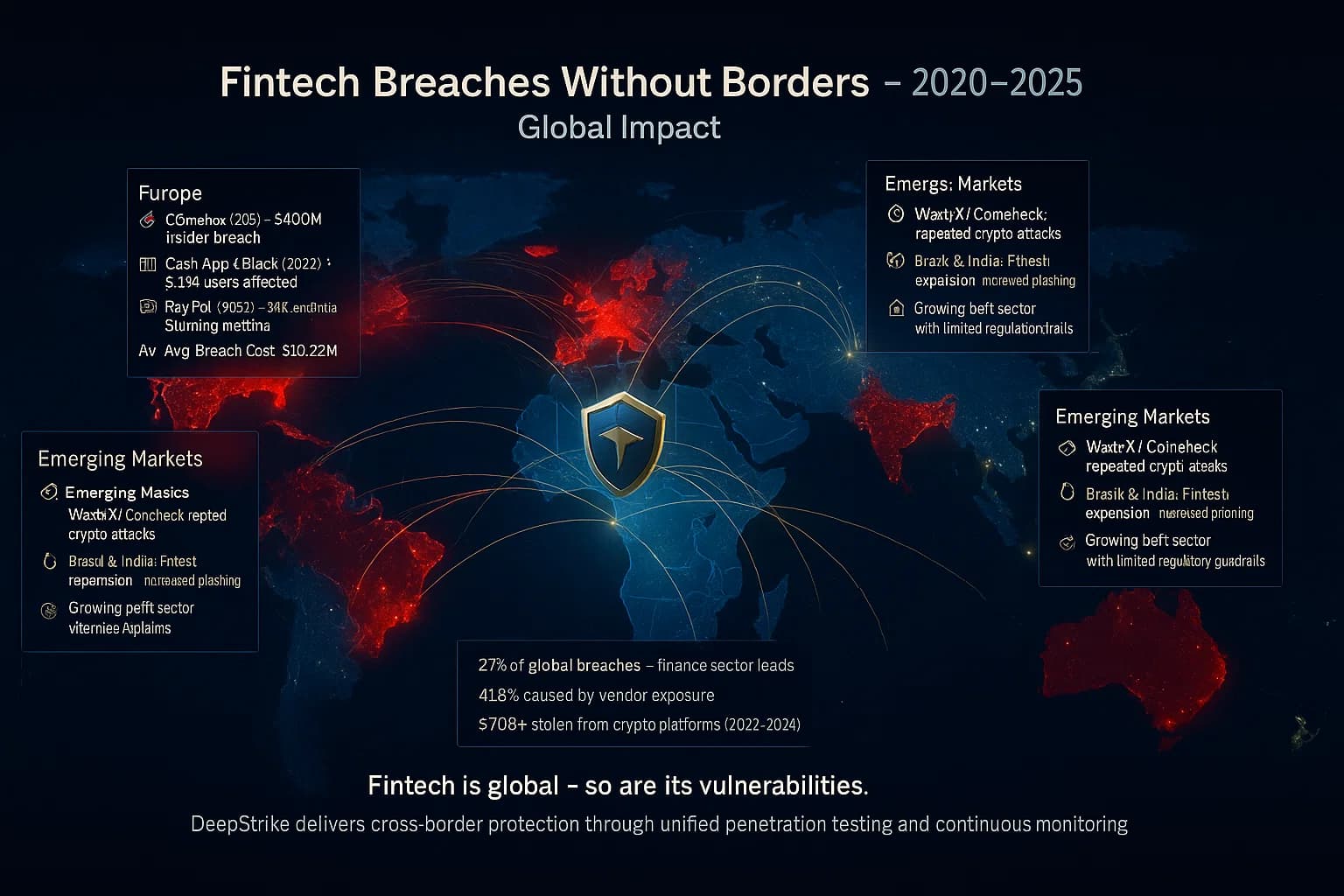
Fintech breaches are global. The US leads with many incidents Coinbase, PayPal, Lemonade, Root, Cash App. The UK/EU have high profile cases Revolut, Finastra and strict GDPR fines. Asia Pacific sees frequent crypto exchange hacks Coincheck, WazirX, KuCoin, DPRK linked attacks accounted for $660M in 2023, $1.34B in 2024. Emerging markets are also targeted: data leaks affect millions in Brazil, India, etc. Essentially, any country with active digital finance is at risk.

Typical fintech breaches leak:
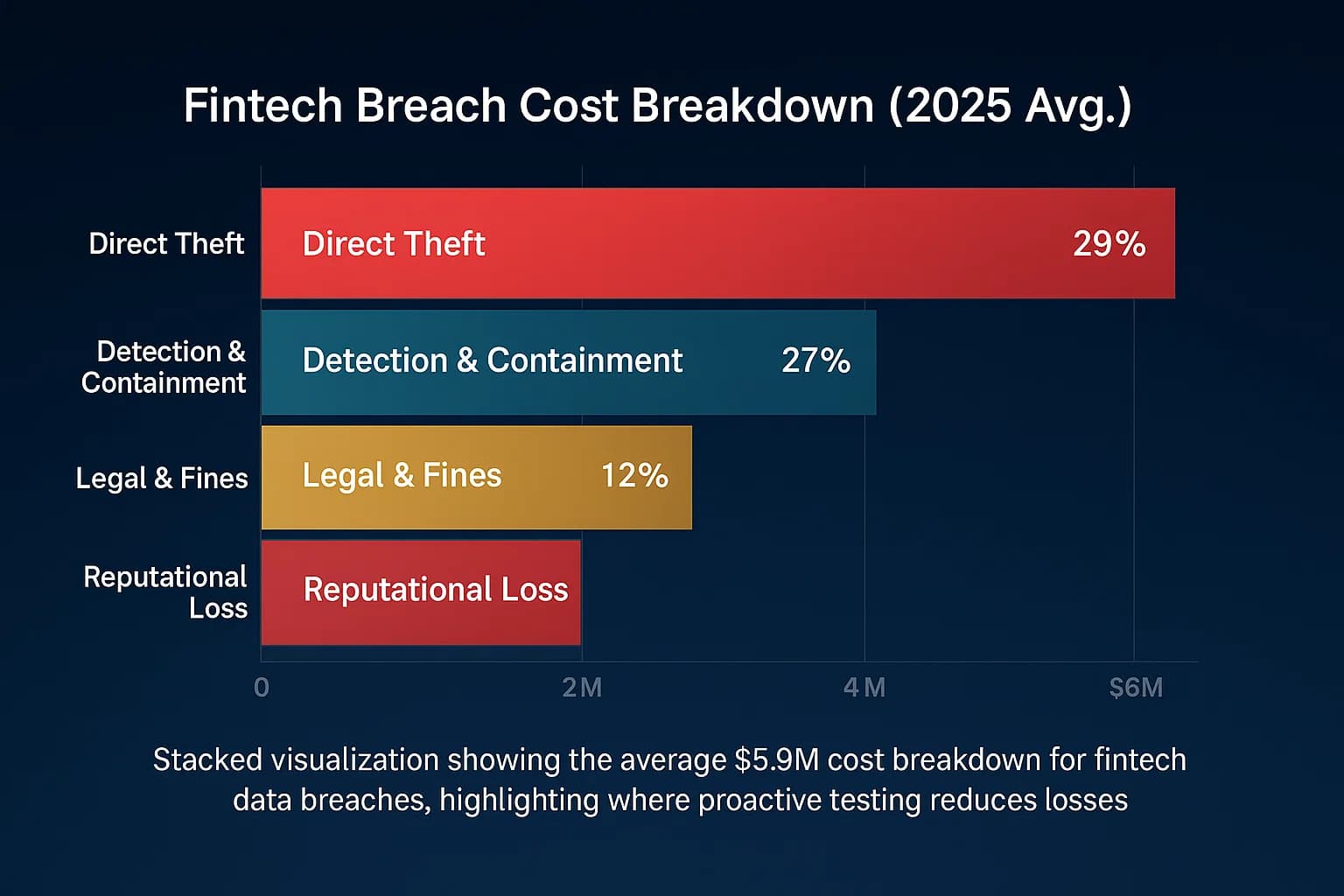
The costs are staggering. Direct theft in crypto reached billions per year: Chainalysis tallies $3.7B stolen in 2022, $1.7B in 2023, $2.2B in 2024. Meanwhile, remediation costs for companies are millions. IBM’s Cost of a Data Breach reports show finance firms averaging $5.90M per breach versus $4.45M overall. And breaches linger: over 50% of breach costs occur after one year.
Beyond direct losses, regulators are punishing breaches. For example, PayPal paid $2.0M in 2025 for a 2022 credential stuffing failure, and insurers Root/Noblr paid $975K/$500K for quote data leaks affecting tens of thousands.
Customers also bear costs: identity theft, fraud, leaked crypto funds unsurprisingly, victims of Lazarus Group hacks have lost millions.
Finance sector breaches rose sharply 27% of Kroll cases in 2023. IBM says $5.90M average breach cost for finance. Chainalysis: $7+ billion in crypto stolen 2022- 2024. SecurityScorecard: 41.8% of fintech breaches via third parties. These figures highlight why fintech security is now mission critical.
The table below compares example breaches across fintech industries:
| Subsector | Example Breach Year | Data Compromised | Impact |
|---|---|---|---|
| Crypto Exchanges & DeFi | Ronin Network Mar 2023 | None just funds stolen | $625M stolen |
| Neobanks/Digital Banks | Revolut 2022 | PII names, addresses, emails, partial card data | 50,150 users; $23M lost |
| Payments & Wallet Apps | Cash App/Block Dec 2022 | PII & financials names, brokerage account IDs, portfolio data | 8.2M users |
| Payments/Cards | SlimCD Jun 2024 | Card data names, card numbers, expiry dates, addresses | 1.7M credit cards |
| Payment Providers | PayPal Dec 2022 | Account credentials/PII names, SSNs, etc. | 35K accounts |
| Insurtech | Lemonade Apr 2025 | PII 190K driver’s license numbers | 190K applicants |
| Fintech Service Provider | Finastra Nov 2024 | Client financial data 400 GB from banks | Enterprise clients; unknown cost |
This mix of examples illustrates that everyone is at risk. Crypto bridges see multi million thefts of coins. Challenger banks suffer both fraud and data leaks. Payment apps face insider leaks and credential stuffing. And even service providers like Finastra can spill sensitive files for top banks. The stolen data ranges from basic PII to massive sums of money.
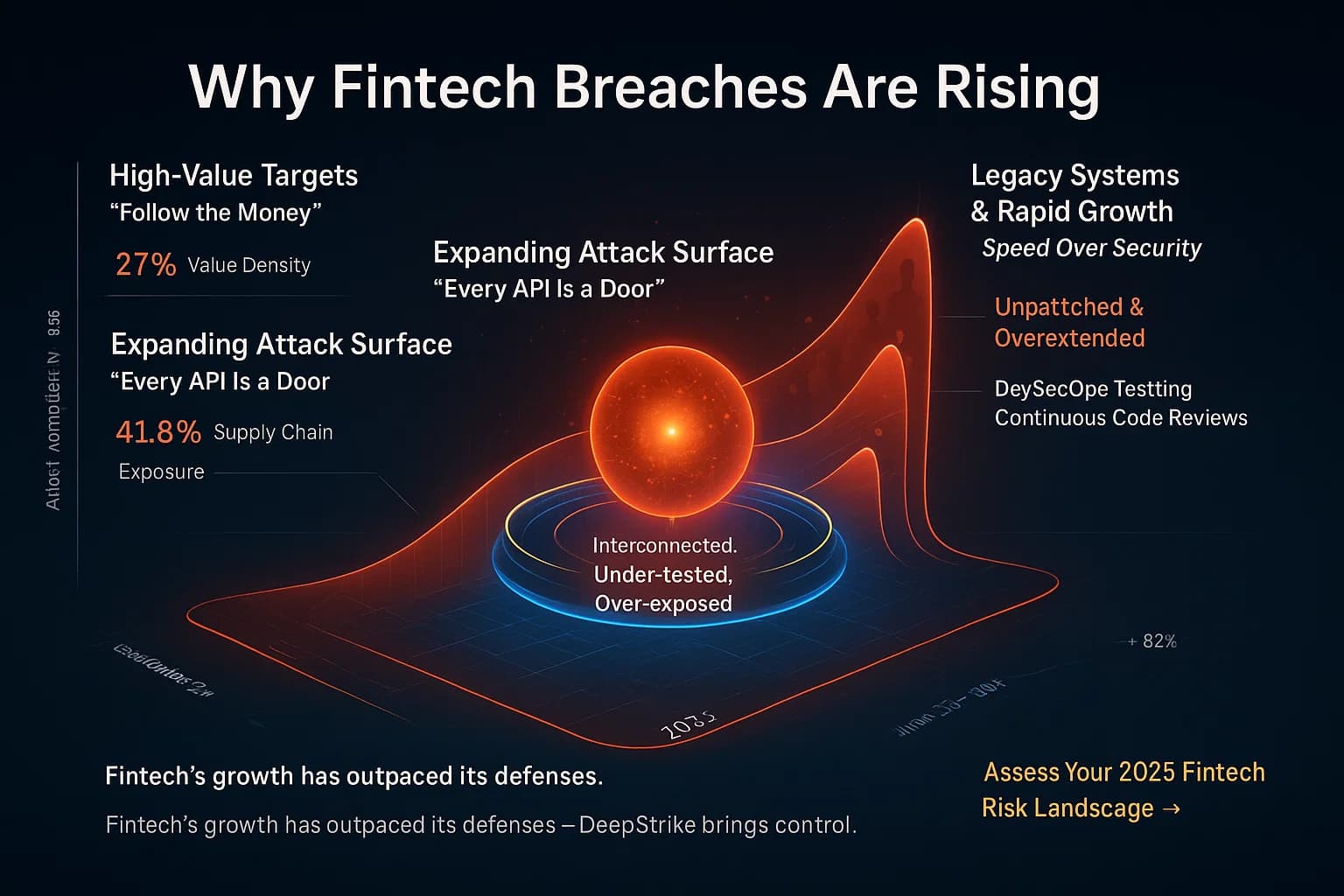
Several factors fuel fintech breach stats:
In short, fintech firms are rich targets with hard problems. Attackers adapt rapidly, so continuous vigilance is needed.

The good news: knowing these stats guides defenses. Fintech security teams can take action:
As one DeepStrike consultant puts it: Fintech security is not a one off checkbox; it’s an ongoing practice. Leveraging Penetration Testing Services and secure engineering is not just ideal but necessary. Even simple fixes patching servers, closing idle ports, DDoS protection add up. Given the stakes, fintechs should budget for continuous testing and advanced monitoring tools like XDR or CSPM. In short, secure by design must be a priority.
Fintech breach statistics show one thing clearly: the threat is real and escalating. From massive crypto thefts to sneaky API vulnerabilities, the attacks of 2025 demand more than just awareness they require action. DeepStrike’s hands-on experience affirms that breaches in fintech cost millions and erode trust. The solutions are proactive: regular Penetration Testing Services, vigilant monitoring, and strong security culture.
Ready to Strengthen Your Defenses? The threats of 2025 demand readiness. If you need to validate your security posture, identify hidden risks, or build a resilient defense, DeepStrike can help. Our team of expert penetration testers and red teamers provides clear, actionable guidance to protect your fintech business.

Explore our penetration testing services to see how we uncover vulnerabilities before attackers do. Drop us a line we’re always ready to dive in.
About the AuthorMohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Very common. Breaches in the financial sector have surged in 2023, finance topped breach counts 27% of Kroll cases. SecurityScorecard found 18.4% of top fintechs had public breaches by 2024. With many high profile incidents each year, assume any fintech is at risk without proper security.
Mostly customer PII and financial info. Attackers grab names, emails, addresses, SSNs, and credit card details. Crypto hacks typically steal funds, not personal info. Insurtech breaches often leak SSNs/licenses from quote forms. Any stored credentials or tokens are especially valuable if compromised.
Extremely costly. IBM’s 2023 report says average $5.90M for financial breaches, higher than most industries. Those costs include remediation, fines, legal fees, and customer churn. Crypto losses dwarf that billions stolen, but even a single data leak can force regulatory fines in the millions e.g. fines against PayPal, Lemonade.
Crypto platforms see larger heists due to stored funds on chain. For example, over $7B was stolen from crypto in 2022- 2024. Traditional banks generally deal more in data leaks PII, account takeover. Both face threats: crypto = big money hacks, banks = third party attacks and fraud. In practice, both must secure smart contract code, keys, and customer data.
Greatly. Phishing is a top entry point. Kroll noted a 21% rise in business email compromises in 2023. Many fintech users fall for scams that lead to credential theft. Fintech firms train employees and clients on these threats. We link to phishing attack trends and statistics for more context.
They must try. Breaches at startups can be catastrophic. Solutions like cloud penetration testing or managed security services SOC as a service scale to budget. Regulators also push smaller firms to follow frameworks NIST, ISO 27001. Our advice: prioritize security early it’s cheaper than cleaning up a breach later.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us