November 18, 2025
Updated: November 18, 2025
A data-driven look at daily dark web activity users, markets, stolen data, cybercrime services, and the law-enforcement operations monitoring this hidden ecosystem.
Mohammed Khalil


Ever wonder what really goes on in the dark web each day? In simple terms, it hums with secret activity from millions of users worldwide. People log into anonymous networks Tor, I2P to buy and sell illicit goods from narcotics and weapons to stolen credit cards and hacking tools. Media sometimes focus on sensational stories, but the reality is a highly organized underground economy.
On the daily basis, this hidden network of sites roughly 0.01% of the Internet is dominated by illegal commerce and information exchange. For example, darknet drug markets saw about $470 million in sales in 2022, and over 15 billion stolen account credentials were being traded by then. Understanding these daily activities is crucial in 2025 because the dark web directly fuels modern cyberthreats every leaked password or malware kit there can lead to real world attacks. In short, staying on top of what’s happening in the dark web helps organizations protect themselves from breaches, extortion, and fraud.
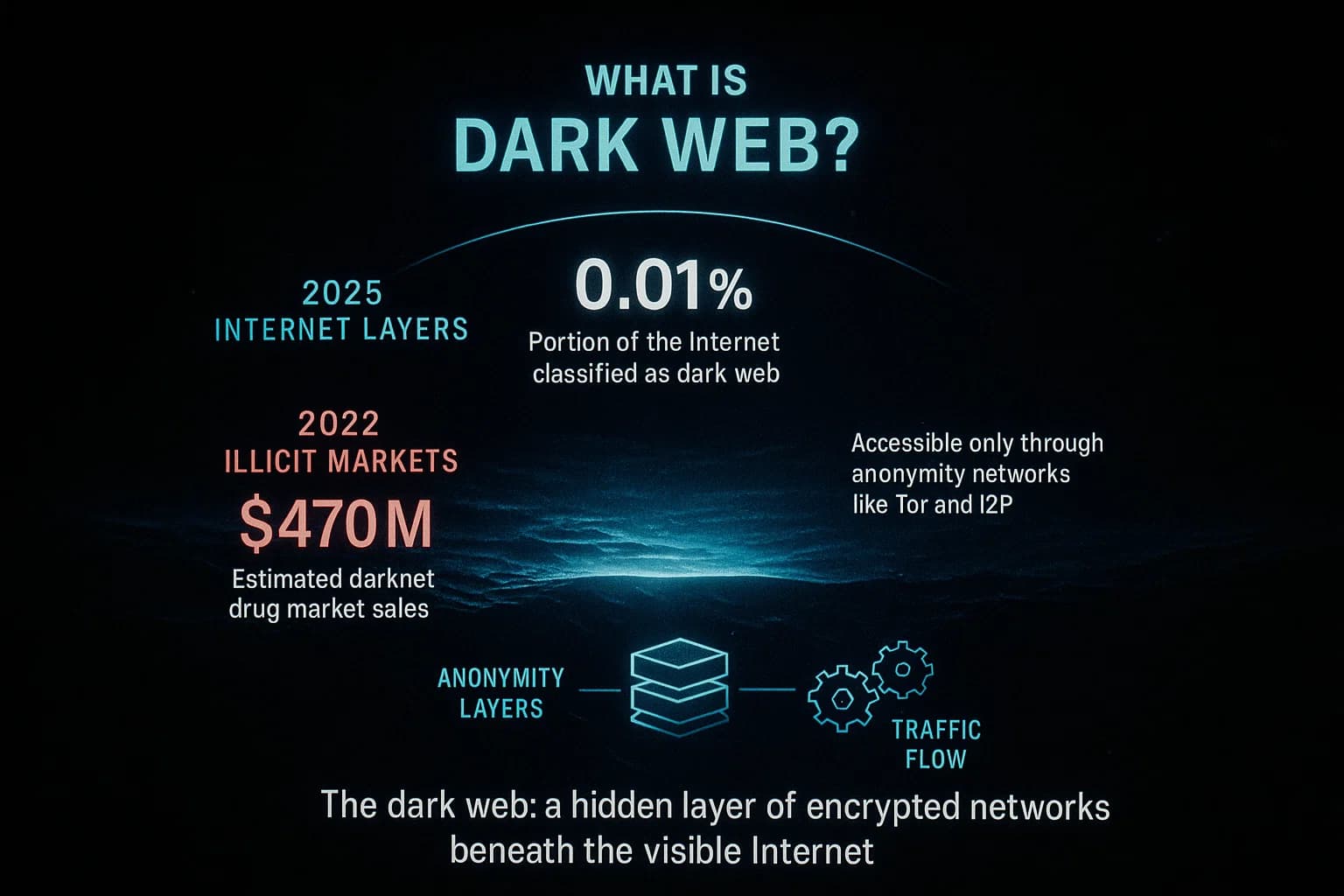
The dark web refers to websites hosted on encrypted networks like Tor or I2P that are not indexed by regular search engines. It’s essentially a hidden subsection of the broader deep web. While surface web the normal Internet contains public sites you can find via Google, and deep web includes private or password protected content e.g. online banking, the dark web is specifically hidden by design for anonymity. In practice, this means you need a special browser like the Tor Browser to visit .onion addresses and other concealed sites. Check out our Deep Web vs Dark Web guide.
| Layer / Category | Accessibility | Typical Content | Share of Internet |
|---|---|---|---|
| Surface Web | Standard browsers Chrome, etc. | Public websites news, shopping, social media | 5- 10% |
| Deep Web | Login/password protected | Private data bank accounts, emails, academic journals | 90% |
| Dark Web | Tor/I2P browsers | Anonymized sites illicit marketplaces, secret forums, whistleblower platforms | 0.01% |
This table shows that the dark web is tiny compared to the rest of the Internet. Yet, as with an iceberg, it hides a vast underground economy below the surface. Practically all content there aims for privacy or secrecy. About 57% of dark web sites host illegal material drugs, hacking tools, exploit code, etc.. The remainder includes legitimate uses, such as secure communication for journalists or activists.
Unlike the open web, the dark web has its own ecosystem: search engines e.g. Ahmia and directories let users find hidden sites, and forums serve as community hubs. Many attackers and researchers even develop specialized search tools for .onion domains. In short, the dark web is a small piece of the Internet where privacy and anonymity reign which is why it attracts criminals, but also some privacy conscious users.

On any given day in 2025, roughly 2- 3 million people connect to the Tor network. That may seem small compared to billions on the open web, but it’s substantial for an anonymous network. For context, Tor usage has been growing from about 2 million daily users in early 2025 to over 3 million a few months later. These users are concentrated in a few regions: the U.S. and Germany alone account for 30% of Tor traffic. India, the UK, Netherlands, and Indonesia are also common sources. Interestingly, Germany briefly became the #1 Tor using country in 2023, showing how usage patterns can shift.
In practice, only a minority of Tor users visit hidden sites daily. Many use Tor just for extra privacy on the surface web. Experts estimate only about 6- 7% of Tor traffic goes to .onion sites. Still, that 6- 7% translates to hundreds of thousands of individuals browsing dark web markets and forums every day.
Daily behavior varies by user:
Behind the scenes, technical activity runs 24/7: cryptocurrency transactions mostly in Bitcoin, Monero, etc. flow through the network to pay for goods, and encrypted chats and forums buzz with new posts. Automated bots index .onion sites and monitor chatter. In short, the dark web never sleeps: every hour sees new illicit deals, data trades, and criminal coordination.
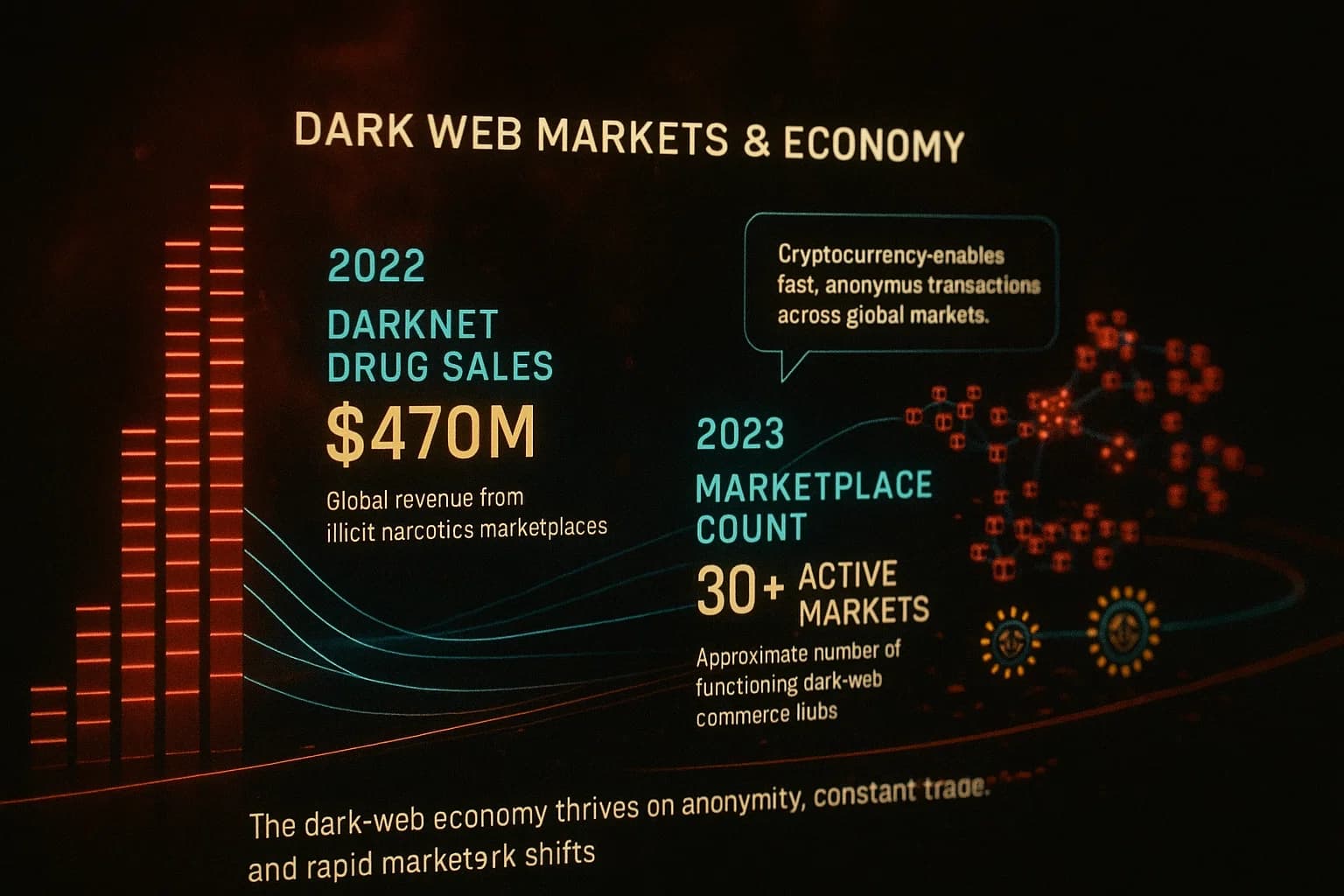
The core of daily dark web activity is marketplaces and forums. These hidden sites act like underground eBay or Amazon, but for illegal products. Typical examples include Abacus Market, Styx Market, Brian’s Club for stolen credit cards, Russian Market, etc. These sites list tens of thousands of items and services.
Top categories of illicit trade by volume are:
For example, popular markets have reputation systems and escrow, some even require vendor licenses, it’s a surprisingly professionalized ecosystem. A recent report noted 92% of major marketplaces offer escrow and dispute resolution, mimicking legal e-commerce trust models. Full details on specific markets can be found in our Top 7 Dark Web Marketplaces roundup.
The payment currency is almost always crypto. Buyers and sellers trade in Bitcoin, Monero, etc., to stay anonymous. Chainalysis estimates $20- 25 billion in crypto was moved through dark markets in 2022 drugs, data, and everything else combined. An Avast report even found 98% of dark web transactions use cryptocurrency.
Prices fluctuate daily with demand. For instance, law enforcement crackdowns or new vulnerabilities can spike interest and price in certain data. Monitoring these prices via a Dark Web Price Index gives insight into what attackers value. In short, the dark web’s economy is highly active every day people are constantly listing, bidding, and closing deals in this black market.
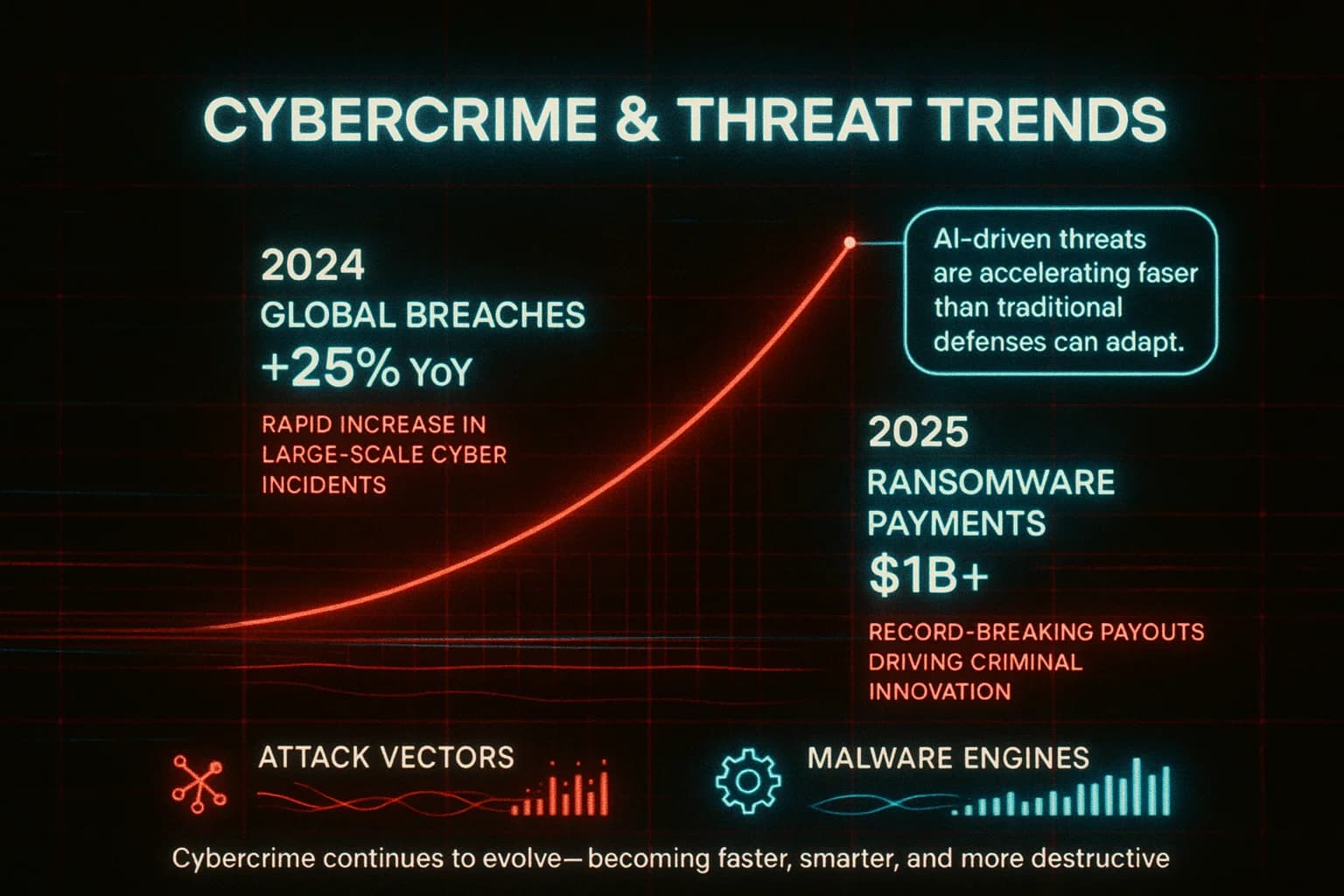
Every day the dark web fuels cyberthreats around the world. Some key trends to watch:
Overall, virtually any cyberattack element is available on the dark web. From a day to day perspective, new goods hacked databases, botnet services, stolen cookies and services hacking gigs, VPN exits continuously appear. This avalanche of resources accelerates attacks in the real world.

Although hidden, the dark web is far from lawless. Agencies worldwide actively track and infiltrate it every day. Undercover agents pose as buyers or sellers on forums; automated crawlers index secret sites. Cryptoforensics teams trace Bitcoin flows to link addresses. When criminals slip up reusing an email, accessing outside Tor, etc., they can be unmasked.
Several high profile takedowns occurred in recent years, showing how global police follow dark web activity closely:
These actions demonstrate daily vigilance. Whenever major players or transactions emerge, law enforcement works undercover to intercept them. For more on these methods, see our article How Law Enforcement Tracks Criminals On The Dark Web. That said, a successful takedown only temporarily disrupts trade the dark web economy is resilient, with new markets springing up quickly after any closure.
In parallel, corporate defenders also monitor the dark web daily. Organizations use specialized Dark Web Monitoring Tools to scan paste sites, forums, and marketplaces for leaked company data. Threat intelligence analysts parse dark chats and listings to spot targeted attack plans. Continuous monitoring turned on 24/7 means defenders can get early warning if, for example, employee credentials or proprietary data appear online. Similarly, in boards and security operations centers, analysts check dark web indicators alongside open source chatter. All of this means that what happens on the dark web daily doesn’t stay secret someone is listening and documenting it.
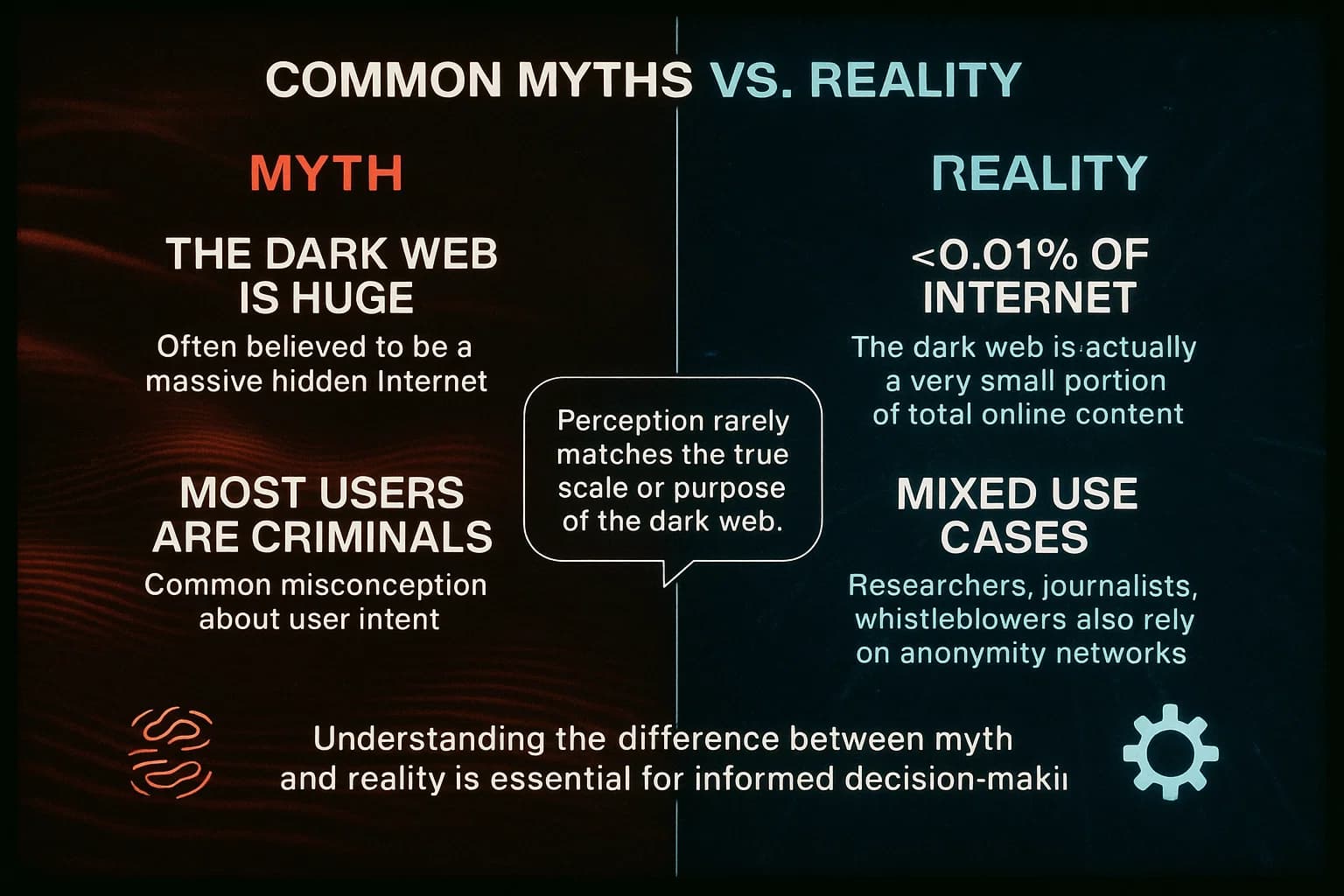
Because the dark web is mysterious, there are lots of myths about it. Here are some truths drawn from daily observations:
For more common misconceptions, check out our Dark Web Myths vs Reality guide, which digs deeper into these misunderstandings.

Given all these daily dark web activities, organizations need a playbook. Here’s a step by step approach:
By following these steps continuously, organizations flip the script: instead of being surprised by attacks, they proactively watch what happens on the dark web each day and adjust defenses. Many frameworks NIST CSF, ISO 27001 now emphasize external monitoring effectively mandating some form of dark web scanning.
Daily life on the dark web is a hidden one, but its effects spill into the open world. Every day, millions of users exchange data and services on encrypted networks, mostly criminals buying drugs, data, and hacking help. These activities power an underground economy worth billions annually. While law enforcement and security teams work tirelessly to watch this space, defenders must be just as vigilant.
In 2025, the key takeaways are clear: Know your enemy’s marketplace. Monitor the dark web for your data, keep an eye on illicit price trends, and simulate attacks with penetration testing. By treating the dark web as part of your threat landscape, you turn a blind spot into early warning. If you want to strengthen your defenses, our team can help.
Ready to Strengthen Your Defenses? The threats of 2025 demand more than just awareness they require readiness. If you’re looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help.

Our team of practitioners provides clear, actionable guidance to protect your business. Explore our Penetration Testing Services to see how we can uncover vulnerabilities before attackers do. Drop us a line we’re always ready to dive in.
About the AuthorMohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
The dark web is the hidden portion of the internet accessible only via special anonymizing browsers Tor, I2P. It is a subset of the deep web sites not indexed by Google. Unlike the deep web which includes private accounts and paywalled content, the dark web is specifically hidden to provide anonymity.
Estimates suggest about 2- 3 million people use Tor each day early 2025 data. That’s roughly 0.01% of total internet usage. The user base skews to countries like the U.S., Germany, India, and others.
Simply using Tor isn’t illegal, but much of the dark web is used for illegal trade. Approximately 57% of dark web content is estimated to be unlawful drugs, hacking, etc.. Many legitimate activities also happen privacy tools, activism, but the majority of dark sites facilitate crime.
Virtually everything illegal under the sun. Daily commerce includes: controlled substances cocaine, fentanyl, etc., stolen personal data SSNs, credit cards, social media accounts, malware and hacking tools, counterfeit documents IDs, diplomas, ransomware kits, and more. Cybercriminals can even hire services like money laundering or DDoS for hire. The dark web essentially has a black market for any illicit need.
Yes, agencies around the world actively monitor and infiltrate it. They use undercover agents and analysis like tracing cryptocurrency flows to identify criminals. Famous examples Silk Road, AlphaBay, Hydra were shut down by law enforcement. While anonymity tools make it hard, skilled investigators take advantage of mistakes and covert operations to break cases.
Organizations and individuals use dark web monitoring services. These services scan hidden sites and alert you if your email or company domain appears in any leaks. You can also check free breach notification tools like Have I Been Pwned to see if your accounts have been exposed. Proactively changing passwords and using MFA are best defenses.
Yes. Every day there is churn: new sites pop up, old ones go offline, administrators get arrested and replaced. Whenever a market is taken down, another rises quickly. Additionally, new cybercrime trends emerge AI generated phishing kits, new exploit marketplaces. Staying current requires continuous monitoring of the dark web ecosystem.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us