November 11, 2025
Updated: November 11, 2025
Learn how the deep web and dark web differ in access, legality, and security and why understanding both matters for cybersecurity in 2025.
Mohammed Khalil


The deep web vs dark web question boils down to privacy versus anonymity. The deep web encompasses everything online that search engines can’t index, think of content behind passwords or blocked to Google. Every time you log into Gmail or your company intranet, you’re on the deep web. The dark web, on the other hand, is a portion of the deep web intentionally hidden and accessible only with special software like the Tor Browser.
In 2025, this distinction matters more than ever: as cyber threats rise, understanding these layers of the internet helps you avoid risks and protect your data. Many people conflate the two terms, but confusing the deep web with the dark web can lead to unnecessary fear or worse, a false sense of security about where the real dangers lie.
Why this matters now: Massive data breaches continue to flood dark web marketplaces with personal and corporate information. Meanwhile, privacy concerns and censorship drives more legitimate users to anonymizing tools. Knowing the difference between deep and dark web isn’t just trivia, it's key to gauging what threats if any you face when browsing, and what measures your business should take to stay safe.
Layers of the internet are often visualized like an iceberg: the Surface Web top is the small visible portion indexed by Google, the Deep Web middle is the huge mass of private or unindexed content below the surface, and the Dark Web bottom tip is a tiny hidden zone within the deep web requiring special access.

The deep web refers to all the online content not indexed by search engines. In other words, if you can’t find it via Google or Bing, it’s part of the deep web. This includes anything behind a login, paywall, or otherwise restricted from public view:
How to access the deep web: Generally, you use a normal web browser Chrome, Firefox, etc. and go directly to the URL or login page. There’s no special trick, the content is just not publicly listed. If you have the URL or proper credentials, you’re in. For instance, when you log in to view your online bank statement, you’re effectively diving into the deep web the content is private and unindexed without even realizing it. No special deep web browser is needed beyond the standard web.
Is the deep web safe? Yes the deep web is a normal, even necessary part of the internet. In fact, the majority of web content lives in the deep web by some estimates, over 90% of all web pages. There’s nothing inherently malicious about it. The deep web’s purpose is simply to keep private information private. As long as you’re on legitimate sites and protecting your login credentials, the deep web isn’t something to fear. The main security concern is making sure those private sites are secure using HTTPS, strong passwords, etc., because if a deep web site gets breached, the data exposed often ends up on the dark web more on that later. In short, being on the deep web is routine and legal it’s how we do online banking, email, and business every day.

The dark web is a specialized subset of the deep web that exists on overlay networks, a darknet and requires special software or configurations to access. The most common darknet is the Tor network short for The Onion Router, which hosts sites with .onion addresses. Unlike the regular web, dark web sites aren’t reachable with a normal browser or via a simple Google search you must use a tool like the Tor Browser or similar anonymizing software such as I2P or Freenet.
Key characteristics of the dark web:
How do you access the dark web? The typical method is to download the Tor Browser, a free browser that automatically connects you to the Tor network. Tor essentially wraps your connection in layers of encryption hence the onion metaphor. Once you’re on Tor, you can enter a dark web address which often looks like a random string of letters and numbers ending in .onion. For instance, the New York Times has a special .onion site for anonymous access. You can also find aggregated lists of onion sites on certain forums or use dark web search engines for known keywords. Some users further protect themselves by using a VPN before launching Tor this adds an extra layer of encryption and hides the fact that you’re using Tor from your internet provider. In summary, to enter the dark web, you need intentional steps and tools you won’t get there by accident. If you’re casually browsing the news or shopping on Amazon, you’re not going to stumble onto a dark web marketplace it just doesn’t happen without trying.
Legit or not? Accessing the dark web is legal in most jurisdictions. Simply using Tor or visiting a .onion site is not a crime the Tor network itself was originally developed by the U.S. Navy for secure communications. In fact, Tor is legal in nearly all countries, aside from a few that ban or block it e.g. China, Iran, Russia, where the government attempts to restrict anonymous internet use. For many people, the dark web is a lifeline for free speech journalists use it to communicate with sources securely, citizens in oppressive regimes use it to bypass censorship, etc. Organizations like Facebook, the BBC, and ProtonMail even offer official dark web mirrors of their services to provide safe access for users who need anonymity.
However, the dark web is heavily used for criminal purposes and those actions are very much illegal. It’s akin to a dark alley: walking through it isn’t illegal, but if you buy something illegal there, you’re breaking the law. Dark web marketplaces have sold drugs, weapons, stolen credit cards, counterfeit money, hacked accounts you name it. Law enforcement worldwide actively monitors dark web criminal sites. High profile busts like the FBI’s takedown of the Silk Road market in 2013 show that anonymity tools are not foolproof. If you engage in crimes on the dark web, you can still get caught via undercover stings, operational security mistakes, or malware that reveals identities. In short: Using the dark web for privacy is lawful; using it for crime is not.
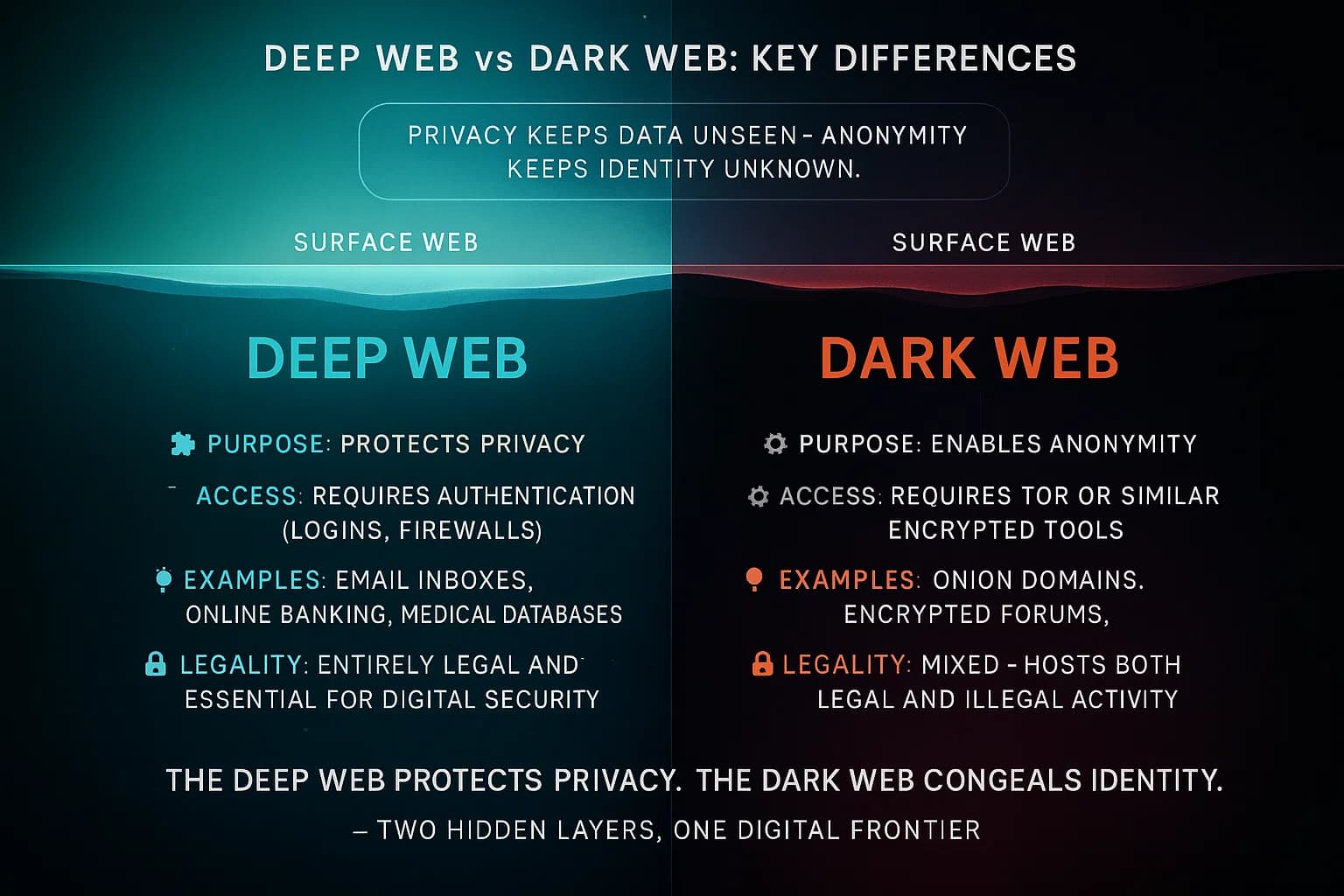
Let’s compare the deep and dark web side by side on a few important dimensions. Despite the overlap the dark web is technically part of the deep web, they serve very different purposes.
Scope and Visibility: The deep web constitutes the majority of the internet, all the content that’s hidden from search engines, private pages, databases, etc.. The dark web, conversely, is a tiny fraction of the deep web, think a few thousand active sites vs billions of regular websites. The deep web isn’t indexed simply due to privacy or technical reasons, whereas dark web sites aren’t indexed by design they deliberately hide on networks like Tor.
Accessibility: Deep web content is accessed with normal browsers and standard internet connections. If you have a URL or login credentials, you can get to deep web pages using Chrome, Firefox, or any browser nothing special required. Dark web content requires specialized software/configurations Tor Browser or similar. You can’t load a .onion address in Chrome, for example. Additionally, deep web sites often use familiar .com, .edu, etc. domains just gated behind logins, whereas dark web addresses are often not human readable and use special TLDs like .onion.
Anonymity: On the deep web, the site might require you to identify yourself e.g. logging into your bank with your identity. There’s no inherent anonymity, it's just private from the general public. On the dark web, both users and site owners are typically anonymous or pseudonymous. The whole point of darknets is that neither party wants to reveal who or where they are. This allows for free speech in hostile environments and for criminals to operate marketplaces out of reach of authorities.
Content and Use Cases: Deep web content is usually legitimate and ordinary it’s your email, your company’s internal wiki, academic journal articles behind a paywall, etc. The dark web’s content skews heavily toward illicit or fringe. Yes, there are whistleblower drop sites, crisis forums, and even some dark web versions of popular sites for instance, there’s a dark web version of Wikipedia, but a large portion of dark web activity involves things like black markets, hacking forums, and illegal pornography. We’ll explore specific examples in the next section.
Legality: Simply put, there’s nothing illegal about the deep web. It’s a technical term, not a criminal realm. The deep web includes all the everyday stuff that’s supposed to be private. In contrast, the dark web is a mixed bag: the technology Tor, etc. is legal to use, but it’s infamous as a hotbed of illegal activity. Many dark web sites themselves facilitate crimes. It’s like the difference between a private members only club deep web vs an underground speakeasy where shady deals happen dark web. One is normal privacy; the other is privacy that can cloak wrongdoing.
To summarize these distinctions, here’s a comparison table:
| Aspect | Deep Web | Dark Web |
|---|---|---|
| Size of Internet | 90% of web content, vast majority of sites/data online. Not indexed by Google but still accessible with standard tools. | < 1% of web, a tiny subset of the deep web, often cited around 0.01%. Very small number of hidden sites. |
| Accessibility | Standard browsers Chrome, Firefox, etc. over the normal internet. Requires a direct URL or login credentials, since search engines can’t find it. | Special software like Tor onion network or I2P needed. Uses non standard URLs e.g. .onion not accessible via normal browsers. |
| Content | Private & Everyday: e.g. personal emails, cloud docs, banking, corporate intranets, medical records. Generally legitimate content meant for specific people not public. | Anonymous & Often Illicit: e.g. forums and marketplaces for drugs, stolen data, hacking tools. Also some lawful content whistleblowing platforms, privacy focused sites but heavily criminal use. |
| Anonymity | Standard internet anonymity, or none sites usually know who you are, you log in with your identity. Users connect with traceable IPs though content is private from the public. | High anonymity: Both users and site owners hide identity via encryption and routing Tor. Often no login required unless a site chooses; many users operate under pseudonyms. |
| Legality | Legal to access. It’s just private web content. Illegal activity on the deep web like hacking into someone’s account is covered by normal laws, but accessing your own private accounts is absolutely legal. | Using Tor/dark web is legal in most countries. Criminal activity on the dark web is illegal buying/selling illicit goods, participating in cyberattacks, etc. Law enforcement actively targets dark web crimes. |
| Examples | Webmail services, online banking portals, university library databases, subscription news sites, internal company sites, anything behind a login or unindexed. | Darknet markets e.g. the late Silk Road, ransomware gang leak sites, illicit forums, whistleblower submission sites SecureDrop, privacy focused services .onion mirrors of websites. |
Why this matters: Mixing up these terms can cause confusion. For instance, a company might panic that 90% of the web is dark web which is wrong; 90% is deep web mostly benign. The truly dangerous corner dark web is much smaller. Understanding that helps focus your security concerns appropriately. Next, let’s dive deeper into what people actually do on the deep vs dark web both the good and the bad.
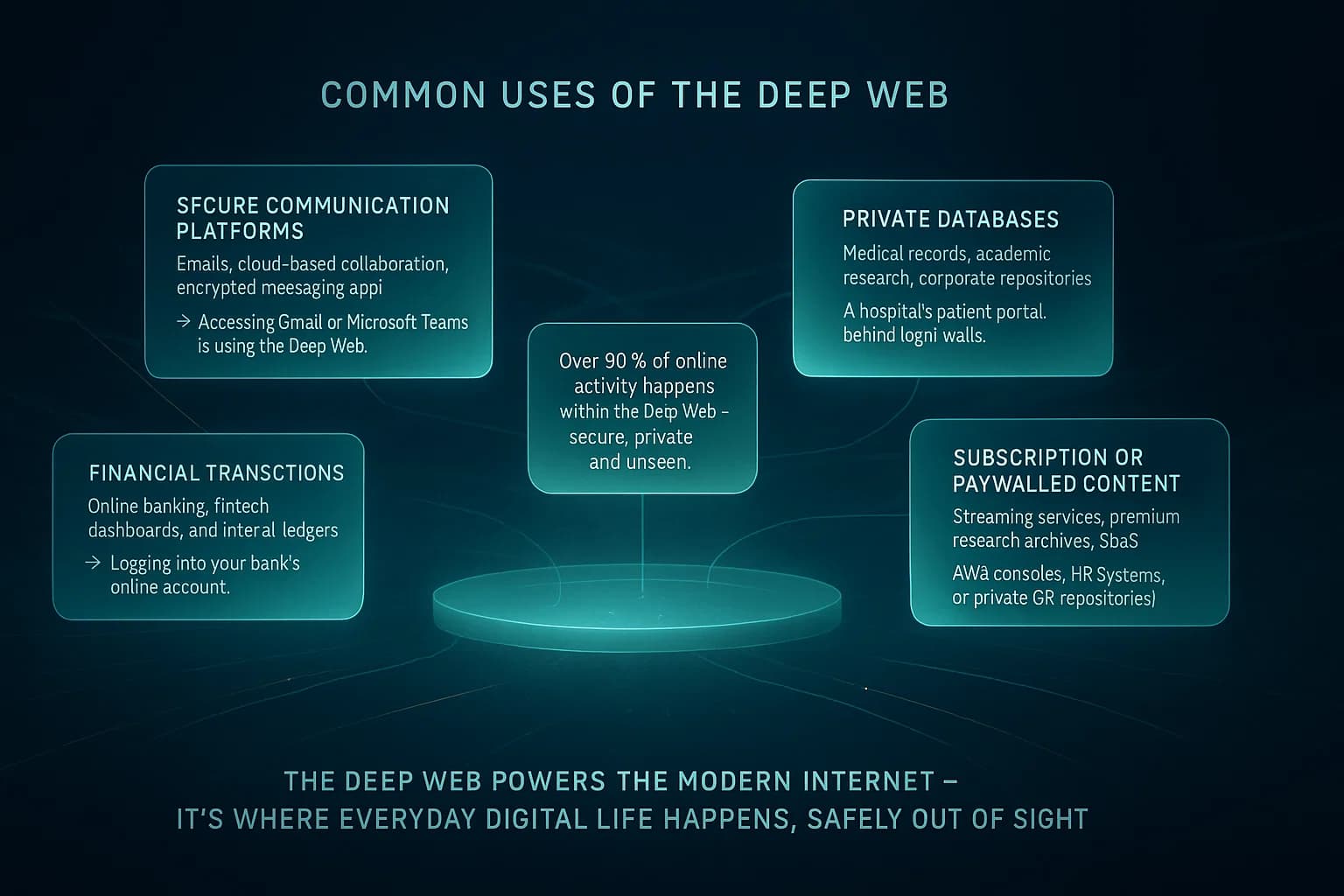
Legitimate Everyday Uses: The deep web’s primary role is to keep our private information and paid content out of public view. Here are some common legitimate uses of the deep web:
In short, the deep web is essential to the normal functioning of online services. It’s not shady, it's just not public. Every organization uses the deep web to store and share information privately. Without the deep web, we’d have a pretty unusable internet nobody wants their emails or business documents publicly searchable!.
Illicit Uses: There aren’t really special criminal uses of the deep web distinct from the rest of the internet it’s more that criminals might target deep web sites to get at data. For example, a hacker might attempt to breach a company’s internal network deep web to steal data, or phish users to log into a fake bank site. These actions, hacking, fraud are illegal regardless, but they’re not unique to a deep web context they’re just crimes targeting private web content. Sometimes people talk about hidden forums on the deep web used by criminals, but in practice serious criminal communities prefer the dark web for the stronger anonymity. So the deep web’s bad side is mainly that it can be a target for attackers because that’s where valuable data resides. If compromised, that data often gets sold or dumped on the dark web. This is a key interplay: the deep web holds the data, the dark web monetizes the stolen data.
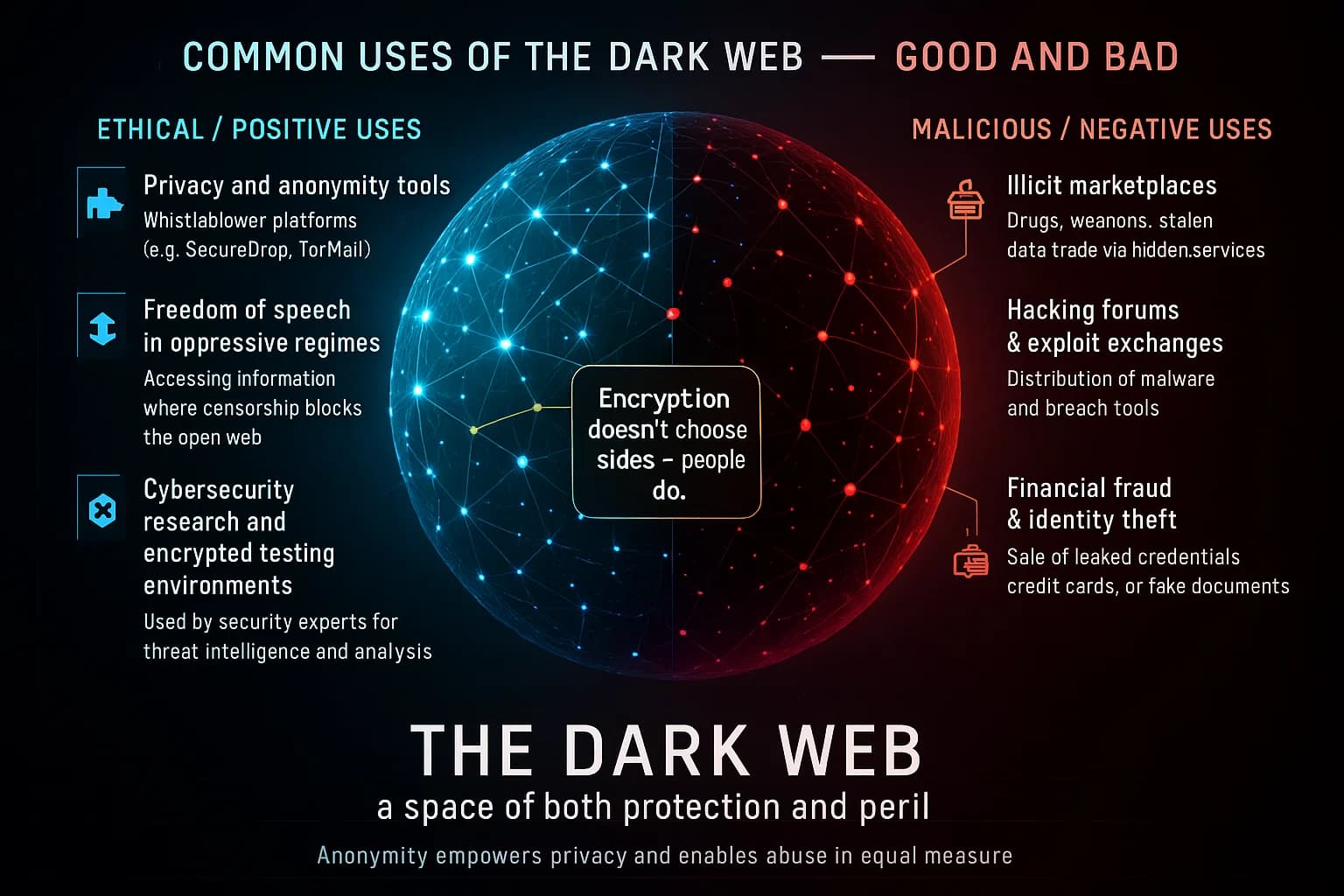
The dark web is famously a wild west of content. Let’s break down both legitimate and illegitimate uses:
Legitimate Uses of the Dark Web: It might surprise some, but not everything on the dark web is illegal. Some notable positive or at least lawful uses include:
Illicit Uses of the Dark Web: Unfortunately, the dark web earned its dark reputation for a reason. Some of the most common illegal activities are:
To put in perspective: A study noted that identity theft related listings made up about 65% of dark web market items, think stolen logins, bank details, and another analysis counted 15+ billion compromised account credentials circulating on dark web forums by 2022. The dark web is the dumping ground and bazaar for data that was stolen from the deep web or surface web companies. It’s also a platform for criminals to connect and trade tools.

By now it’s clear: the dark web carries far more risk than the normal web or deep web. Let’s break down the major dangers:
Are there risks on the deep web? By comparison, the deep web’s risks are more mundane but still important. The deep web itself won’t infect you with malware just by logging into Gmail. The main dangers are phishing and breaches: if you fall for a phishing email and enter your login on a fake deep web page, the attacker then has your credentials. Or if the private site you use has a security flaw, hackers might break in and steal data. These are essentially the same risks any secure site faces keep your guard up with strong passwords and 2FA, because a lot of sensitive info lives in the deep web. Also, be aware that if any of your deep web accounts say a cloud storage or a database get compromised, that data could quickly end up for sale on the dark web, amplifying the fallout.
The dark web should only be approached with extreme caution if at all by individuals. For most people, there’s no pressing need to go there you can live a full digital life entirely on the surface and deep web safely. If you are curious or have a specific reason e.g. researching something, use best practices: Tor Browser only, maybe a VPN on top, disable scripts, don’t download files, and stick to known sites. Treat every offer or link with skepticism. And always remember anonymity works both ways: you don’t know who you’re dealing with on the dark web. It could be a scammer, a predator, or an undercover agent.

So far we’ve treated this topic in general terms. But you might wonder, beyond personal curiosity, why should businesses or professionals care about the deep vs dark web distinction in 2025? Here’s why:
Understanding the deep vs dark web isn’t just academic. For individuals, it helps you stay safe online don’t fear the deep web, but approach the dark web carefully. For organizations, it underscores where to focus security efforts, lock down your private deep web data, and keep an eye on dark web channels for threats. The dark web acts as a barometer of cyber risk: a thriving marketplace for stolen data and attack tools means everyone needs to be vigilant. In 2025, with cybercrime damages projected in the trillions of dollars, bridging the gap between what’s happening on the dark web and your own security posture is crucial.
![[Quick Tips for Readers] — a flowing infographic that presents concise, actionable cybersecurity or privacy best practices in a visually structured, dynamic way.](/_next/image?url=https%3A%2F%2Fcdn.sanity.io%2Fimages%2Fa3jopls3%2Ftestdataset%2Fc178626314383cf1177273b1fd69fcd361a4df64-1536x1024.jpg&w=3840&q=100&dpl=dpl_BjhsCtHQBLhABnbdJpAwxwE59Vnr)
The internet is often visualized as an iceberg: the surface web what we browse daily is just the tip. Beneath lies the deep web, a massive layer of private, unindexed content that we access constantly for legitimate reasons. And further hidden is the dark web, a small but notorious zone where anonymity reigns attracting both those seeking privacy and those with nefarious intent.
The deep web is a normal, even beneficial part of the online ecosystem it protects our private data. The dark web, while having some positive uses for freedom and privacy, is largely dominated by illicit activity and demands extreme caution. In 2025, cyber threats are increasingly linked to the dark web’s clandestine markets, whether it’s your stolen password being sold for a few bucks or ransomware gangs coordinating attacks. So, understanding these terms isn’t just trivia, it's part of being cyber aware.
Ready to Strengthen Your Defenses?The threats of 2025 demand more than just awareness; they require readiness. If you’re looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help.
Our team of practitioners provides clear, actionable guidance to protect your business. We can simulate real world attacks through our professional penetration testing services to uncover vulnerabilities before attackers do, and guide you in shoring up defenses. We also stay on top of dark web threat intelligence to inform our strategies, so you get the most up to date protection.

Explore our Penetration Testing Services to see how we can uncover vulnerabilities before attackers do. Drop us a line. We're always ready to dive in and help fortify your security posture. Don’t wait for a breach to find out if your data is on some dark web forum proactively test and strengthen your defenses now.
About the Author:Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
No simply accessing the dark web via Tor or another browser is not illegal in most countries. Many people use Tor for privacy or to reach blocked sites. However, what you do on the dark web can be illegal. For example, buying drugs or hacking services on a darknet marketplace is very much against the law. Think of the dark web like a private, anonymous internet: using it isn’t a crime, but if you partake in criminal transactions there, you’re breaking the law. Also note, a few countries do ban or block Tor usage like China and Iran. But in the U.S., UK, and most of the world, Tor and the dark web are legal to use, just tread carefully and lawfully.
The deep web makes up the majority of the internet at least 90% of all web pages, by most estimates. Only a small fraction, often cited 10% is the surface web that search engines index. The rest databases, private sites, archives lives in the deep web. Keep in mind, though, that a lot of the deep web’s content is pretty mundane every email in every inbox, for instance, counts toward its size. The dark web is only a minute portion of the deep web, significantly less than 1%. So when you hear most of the internet is the deep web, it’s true, but that’s not cause for alarm it mostly consists of ordinary private or dynamic content.
The most popular option is the Tor Browser, which is a modified Firefox browser configured to connect to the Tor network. It’s as easy to install as any other browser, and when you run it, it will route your traffic through Tor’s encrypted relay system. You can then access .onion addresses dark web sites directly. Other specialized tools include Brave browser has built in Tor in private mode and networks like I2P with its own browser setup, but if you’re new, Tor Browser is the recommended and simplest route. Always download it from the official Tor Project website. Important: Regular browsers like Chrome or Safari cannot open dark web sites. Also, for safety, keep the Tor Browser’s security settings on their defaults or higher, don't install plugins or enable scripts unless you know what you’re doing, as these can compromise your anonymity or security.
DuckDuckGo is a privacy focused search engine on the surface web it doesn’t track you and it’s a great alternative to Google for privacy. DuckDuckGo does have a .onion version an address on the Tor network, which allows you to use it over Tor securely. However, DuckDuckGo’s results are still for the surface web it doesn’t index deep web pages or most dark web sites. In other words, DuckDuckGo is not a dark web index; it’s just a search engine that respects privacy, and it offers an onion site so you can search the open web anonymously. There are other search engines like Ahmia that specifically index some dark web pages, but coverage is limited. Many dark web sites simply aren’t indexed anywhere by design. So, DuckDuckGo = great for private search of the normal web and you can access it via Tor, but it’s not going to list hidden marketplaces or anything.
True anonymity on the dark web is tricky. Tor is designed to hide your identity by bouncing traffic through multiple nodes, and if used correctly it’s very effective. However, mistakes or advanced techniques can expose you. For example, if you enable browser plugins, download files and open them outside of Tor, or allow scripts to run, you might reveal your real IP or identity. There have been instances where law enforcement or researchers set up malicious Tor nodes or hidden services that exploited vulnerabilities to unmask users. Also, agencies can sometimes correlate traffic coming into and out of the Tor network with enough resources this is difficult, but theoretically possible. The average person won’t be actively tracked if they just browse innocuous sites with Tor, but if you become a target of interest, say, investigated for a crime and you slip up operationally, your dark web activity could be discovered. So while Tor greatly enhances privacy, it’s not 100% foolproof. As the saying goes, attacks only get better with time. For most people, the bigger risk is accidentally revealing themselves through logins or etc. rather than some omniscient tracker. But the bottom line: assume nothing is perfectly anonymous.
Absolutely, yes. The deep web is where private but legitimate content resides it’s no more dangerous than the public internet, arguably less, since pages are not public. The primary dangers on the deep web are just the usual cybersecurity concerns e.g. if you use a weak password on your bank account, someone might hack it but that’s not the deep web’s fault. The dark web, by contrast, is rife with inherently dangerous content and activities: malware, scams, illegal goods, and interactions with criminals. Visiting the dark web can expose you to threats you’d likely never encounter on the normal web, especially if you stray from well known, reputable onion sites. Also, the lack of oversight means you could engage with malicious actors unknowingly. It’s the difference between walking in a well lit mall deep web usage and walking down a dark alley known for illicit deals dark web usage. One is part of everyday life; the other you generally avoid unless you have a good reason and some protection. So in terms of personal safety both digital and legal, the dark web is far more dangerous. Always exercise caution if you decide to explore it.
This is a critical question for both individuals and organizations. The unfortunate truth is you can’t guarantee your data will never hit the dark web because breaches can happen outside your control e.g. a company you use gets hacked. However, you can greatly reduce risk and impact:
Even with all that, breaches might happen no one is 100% safe, but these steps mean if your data shows up on the dark web, it’s likely old or not the keys to the kingdom. And for any data that does appear, swift action password changes, notifying banks, etc. can prevent further damage.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us