November 6, 2025
Updated: November 6, 2025
Discover how wireless penetration testing secures Wi-Fi, Bluetooth, and IoT networks through real-world attack simulations, tools, and best practices.
Mohammed Khalil

Wireless penetration testing is a specialized security audit of radio based networks Wi‑Fi, Bluetooth, Zigbee, RFID, etc. using hacker style techniques. Think of it as a safe, authorized war driving mission: testers attack your wireless infrastructure with real world exploits to see how an adversary could break in. This includes evaluating Wi‑Fi access points, SSIDs, encryption, WPS settings, Bluetooth devices pairing, GATT services, and IoT radios for weaknesses. Wireless pentests go beyond a wired network scan by focusing on radio signals and protocols and uncover issues a standard scan might miss. For example, BreachCraft notes wireless tests probe access points, network cards and connected devices exactly as attackers would, looking for any misconfiguration or exposed service. Like all pentests, a wireless test must be done with explicit written permission and clear rules of engagement.
Unlike passive vulnerability scans, a wireless pentest often triggers devices to reveal hidden information. Testers might detect even hidden non broadcast SSIDs, SSID probing, and legacy WEP networks. As NIST emphasizes, conducting wireless scans with passive analyzers helps organizations determine corrective actions to mitigate risks posed by wireless enabled technologies. In short, wireless pentesting reveals gaps, weak keys, open guest networks, rogue APs, etc. before real attackers exploit them.

Wireless security is critical today. In 2025, enterprises typically have hundreds to thousands of IoT and wireless endpoints one report notes the average organization uses over 1,000 IoT devices and 63% have experienced an IoT related incident in the past year. Globally, connected devices exceed 35.2 billion, meaning an enormous invisible attack surface. An attacker can target your Wi‑Fi or Bluetooth from outside your building. BreachCraft warns that wireless networks form an invisible perimeter beyond walls. Any weak WPA2 passphrase, open Bluetooth profile, or unpatched IoT gadget can serve as an entry point.
Moreover, many compliance frameworks mandate wireless testing. For example, PCI DSS 11.3 now in DSS 4.0 requires quarterly tests of all in-scope networks this includes wireless if card data or guest networks are involved. HIPAA also demands strong wireless safeguards for patient data. A thorough wireless pentest not only uncovers security holes, it helps demonstrate compliance with PCI, HIPAA, SOC 2, and more. In short, as data breaches and IoT threats rise, wireless pentesting is no longer optional it’s a business necessity to protect data and reputation.
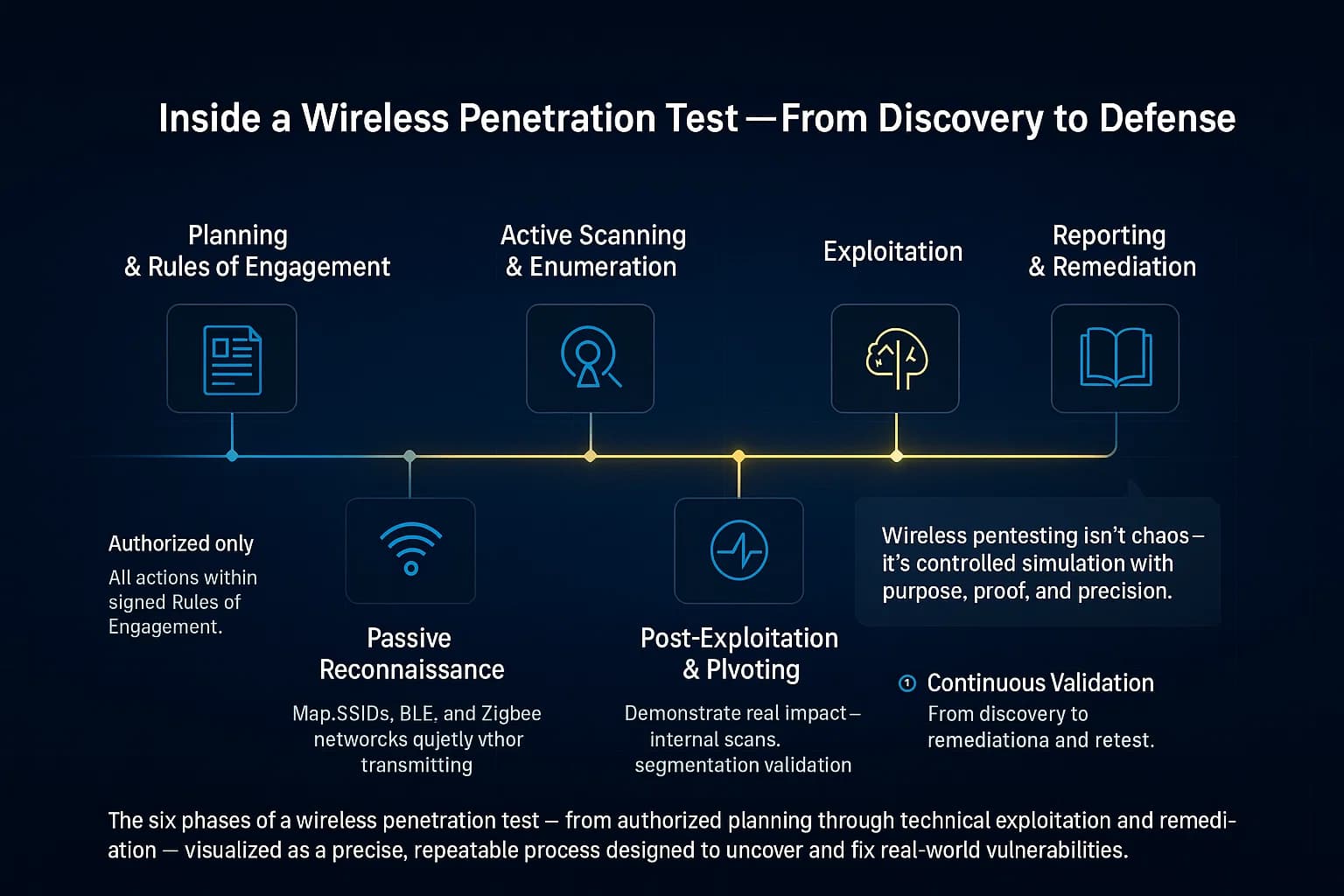
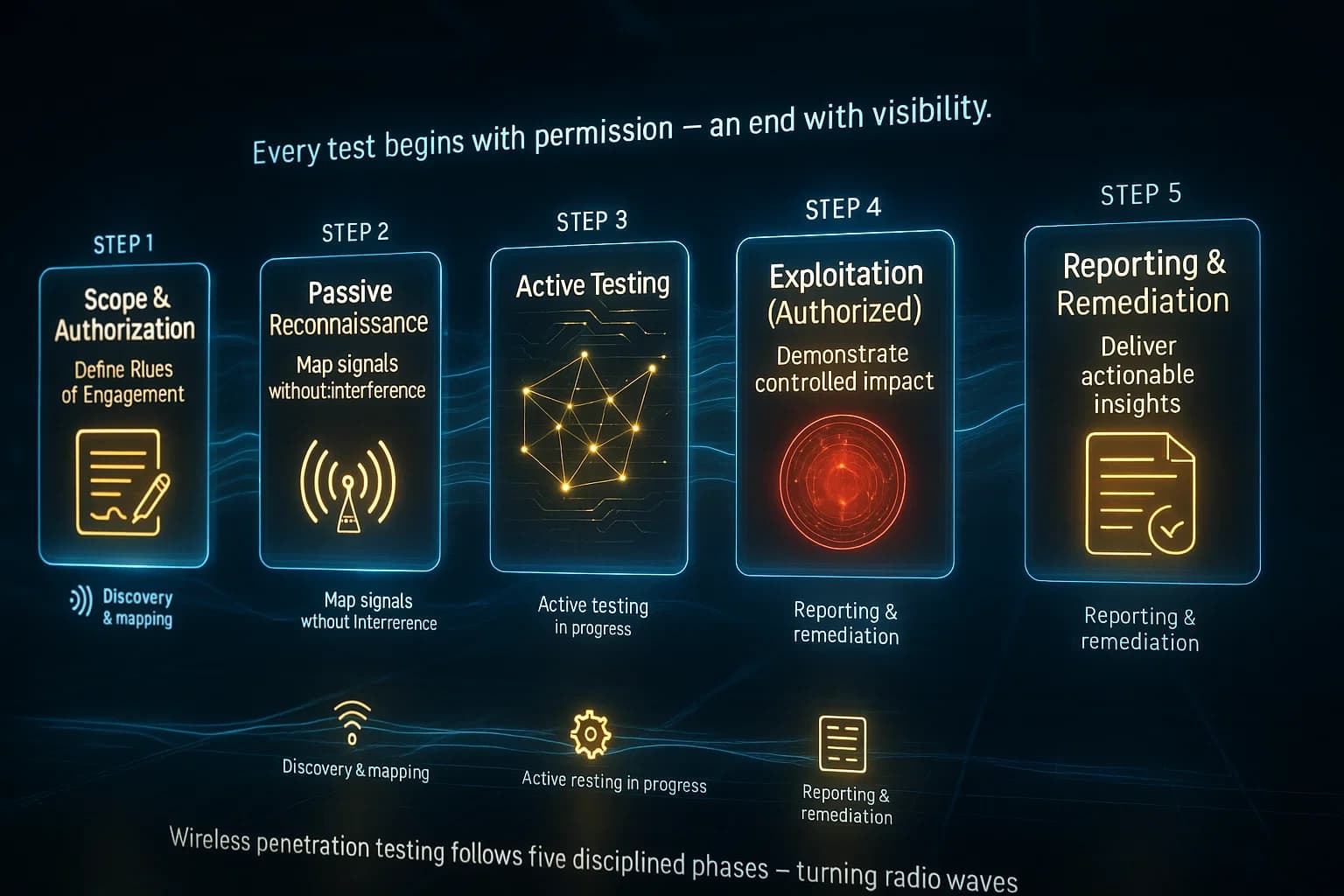
Wireless penetration testing follows familiar pentest phases, adapted for radio. Here’s the typical methodology:
| Aspect | Passive Scanning Stealth | Active Scanning Probing |
|---|---|---|
| What it does: | Listens to Wi Fi/Bluetooth/Lora networks without sending packets. | Actively sends probes e.g. deauth, probe requests, GATT requests. |
| Tools: | Kismet, Wireshark monitor mode, BlueHydra, RTL SDR sniffing mode. | airodump ng channel hop or targeted, wash WPS, bettercap deauth, BLE recon. |
| Pros: | Undetectable by target APs/IDS. Good for finding hidden SSIDs and listening to beacons and adverts. | Faster data gathering forces devices to respond, triggers handshakes. Reveals more details quickly. |
| Cons: | May miss information e.g. no handshake capture if no client activity. Slower, requires patience. | Loud devices/APs may notice e.g. deauth. Potentially noisy in logs. May violate stealth requirements. |
| Use Case: | Initial mapping of environment and unknown devices. When stealth is needed or for compliance with passive only rules. | When you need handshake captures, WPS info, or to prompt devices e.g. detach clients to sniff. Ideal for targeted exploitation steps. |
Use both methods together: start passive to map everything quietly, then selectively go active with permission to gather what passive can’t, like WPA handshakes or service enumeration.
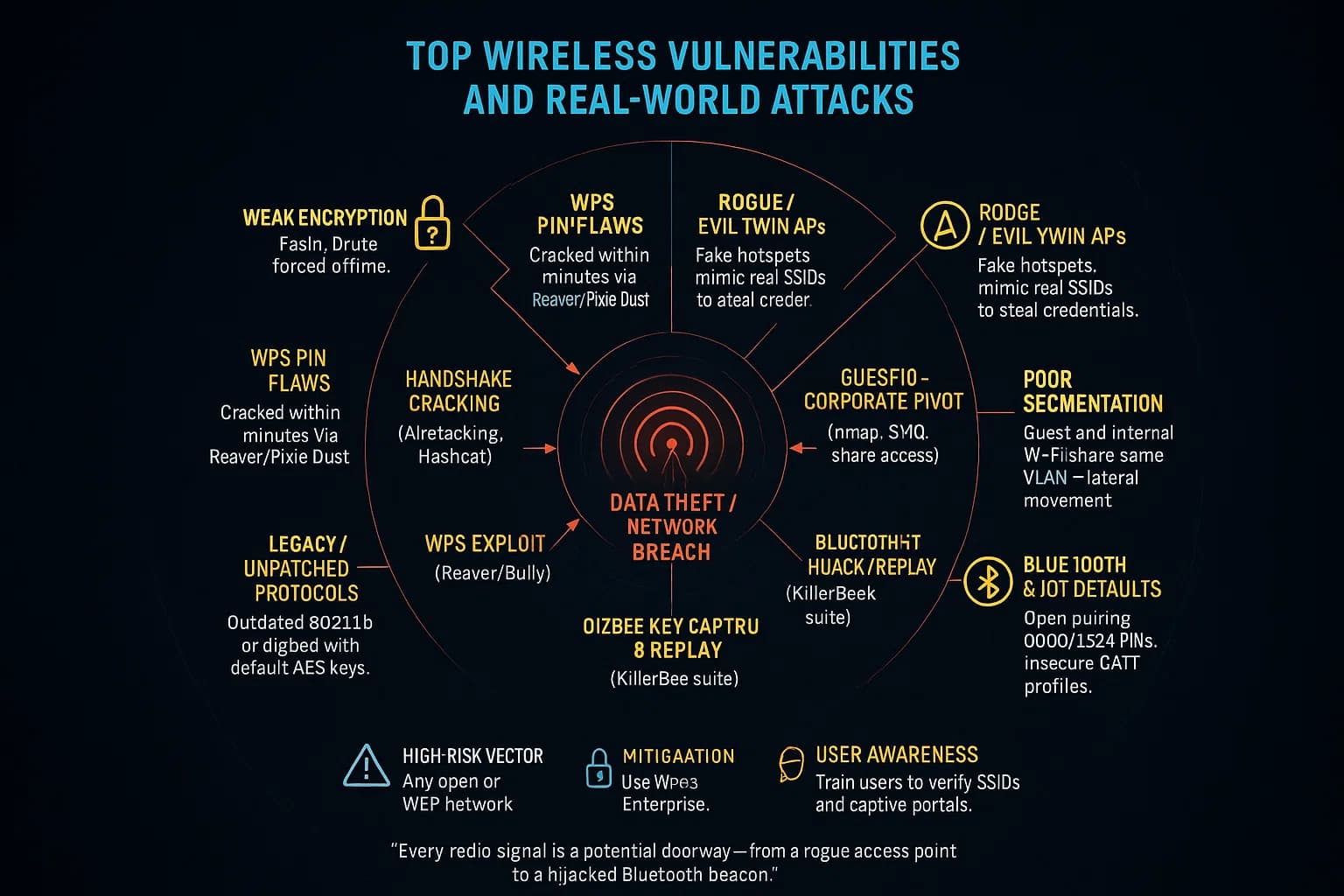
Wireless networks and devices have well known weak spots:
Attack examples like the Evil Twin fake Wi Fi hotspot show how dangerous wireless can be. Kaspersky explains an Evil Twin is a fake AP duplicating a legitimate SSID; any traffic from connected users then flows through the attacker’s machine. In one case, a victim at a café unknowingly connected to the attacker’s AP and then gave up banking logins through a fake captive portal, resulting in loss of funds. These illustrate why wireless pentesting must include social engineering scenarios like captive portal spoofing within scope to test user awareness.
By validating these attacks in a controlled test, you ensure controls are in place. For instance, use WPA3 Enterprise with 802.1X or strong WPA2 passphrases, disable WPS, isolate guest WLANs, and enforce BLE/IoT device enrollment processes. Wireless pentesting reveals where such improvements are needed.
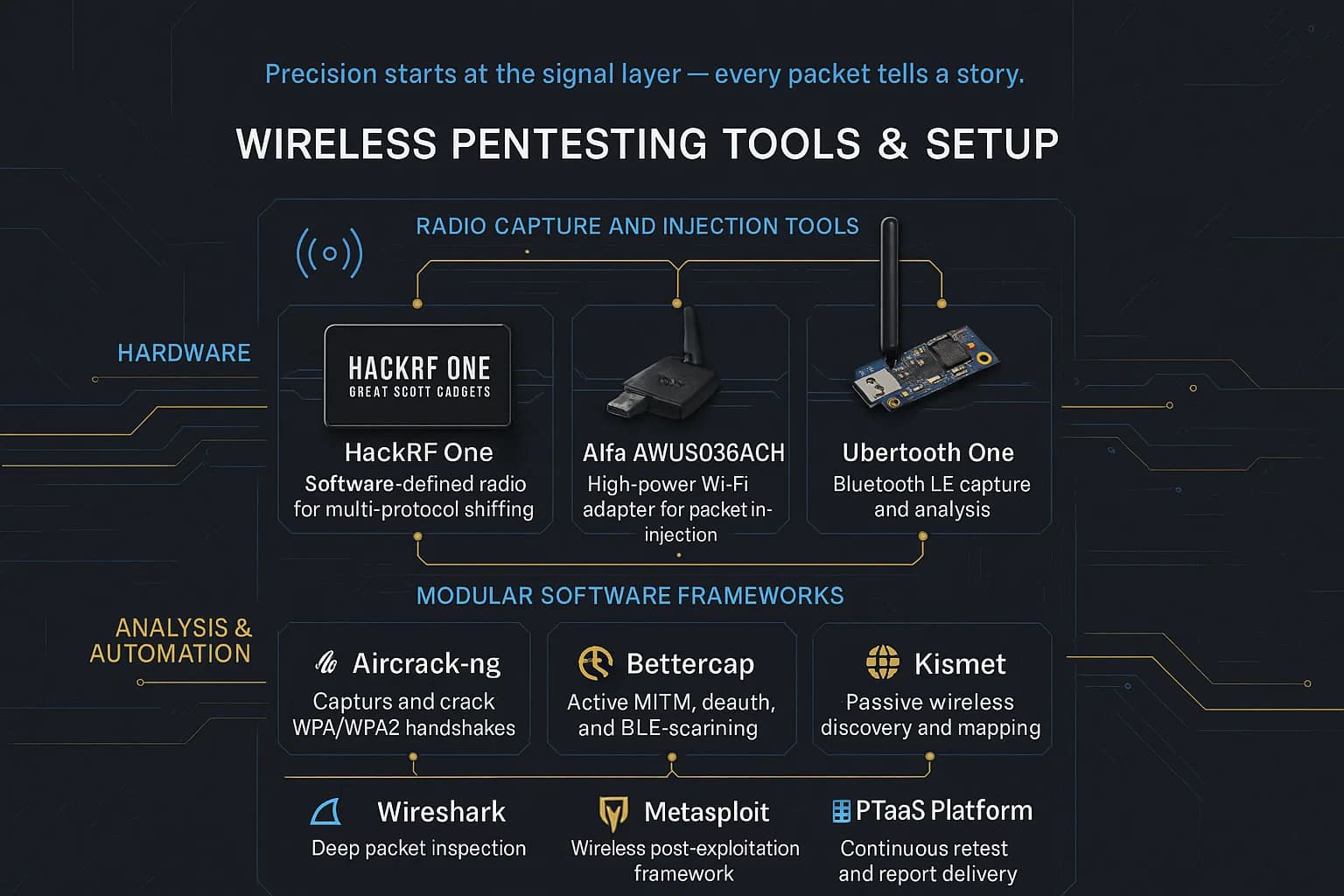
A successful wireless pentest relies on the right hardware and software:
NIST even recommends using a mobile device with analyzer software that supports both passive and active scanning. In practice, testers may script tasks with Python/Scapy or use automated tools like Wifite or Airgeddon for broad sweeps. The combination of these tools enables a thorough wireless assessment in any environment.
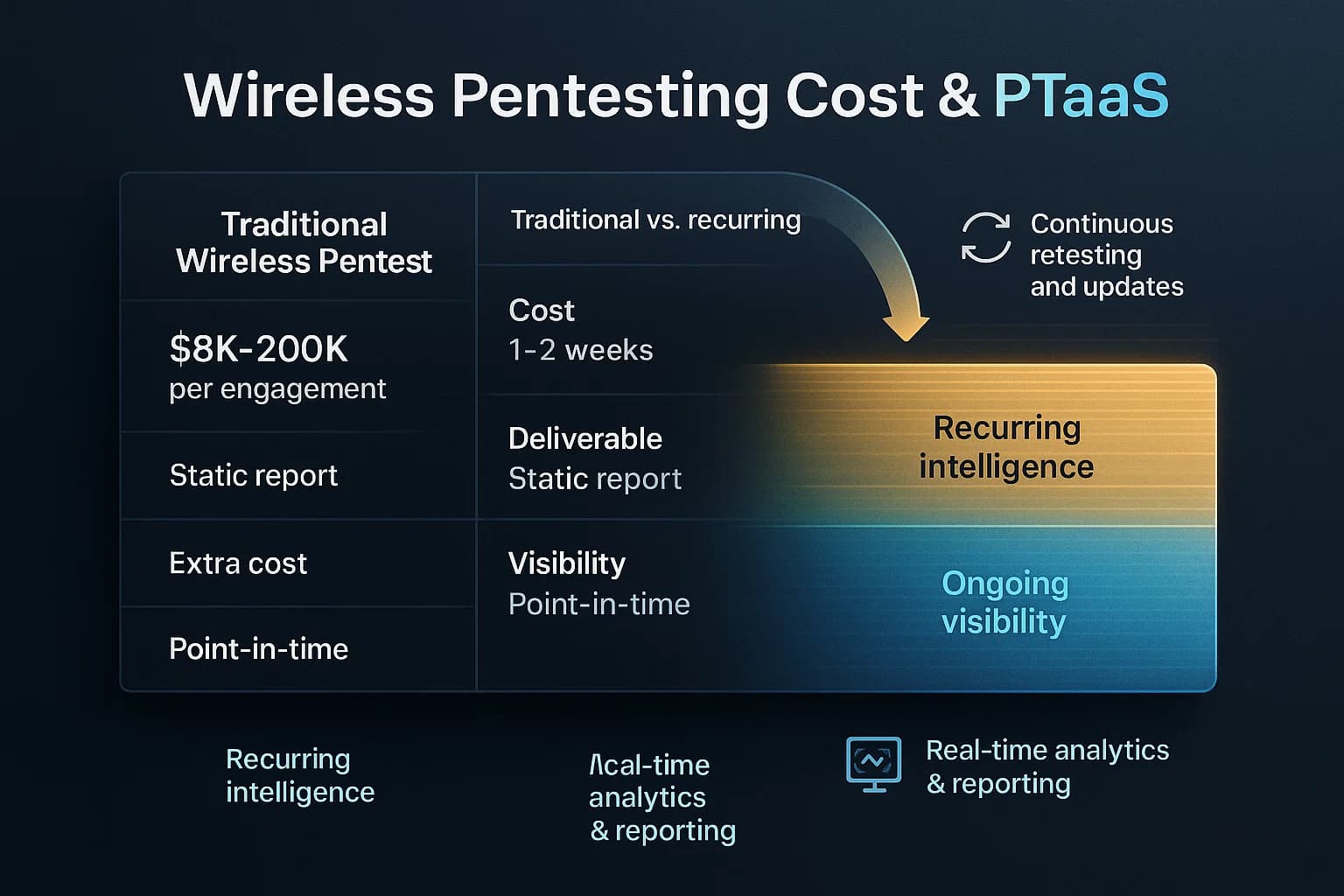
Pricing for wireless pentesting varies by scope and engagement model. Typically, wireless testing is part of a broader pentest or a specialized add on. According to industry data, a full pentest generally ranges from $5,000 to $50,000 depending on size and complexity. Larger enterprises or very complex environments can exceed $100K. The cost drivers include the number of sites, APs, and devices tested, as well as tester experience. For example, DeepStrike notes professional pentests cost roughly $5K- $50K. A purely wireless focused test might be on the lower end if limited in scope, but bundling with internal/external network tests is common.
Some organizations prefer a continuous or on demand model Penetration Testing as a Service PTaaS over one off tests. PTaaS platforms let you spin up a wireless test whenever needed even after each major update and view results in real time, rather than waiting months for a static report. This fits modern DevOps workflows and can be more cost effective long term. DeepStrike itself offers a continuous penetration testing platform that integrates into development pipelines, providing ongoing wireless and network testing.
For a ballpark, small businesses might pay just a few thousand dollars for a wireless assessment, whereas large regulated firms should expect mid five to six figure contracts when combined with full network pentesting. Always ensure the scope is clear e.g., exactly which SSIDs, physical sites, and IoT classes are included. See DeepStrike’s Wireless Penetration Testing Services for specific offerings.
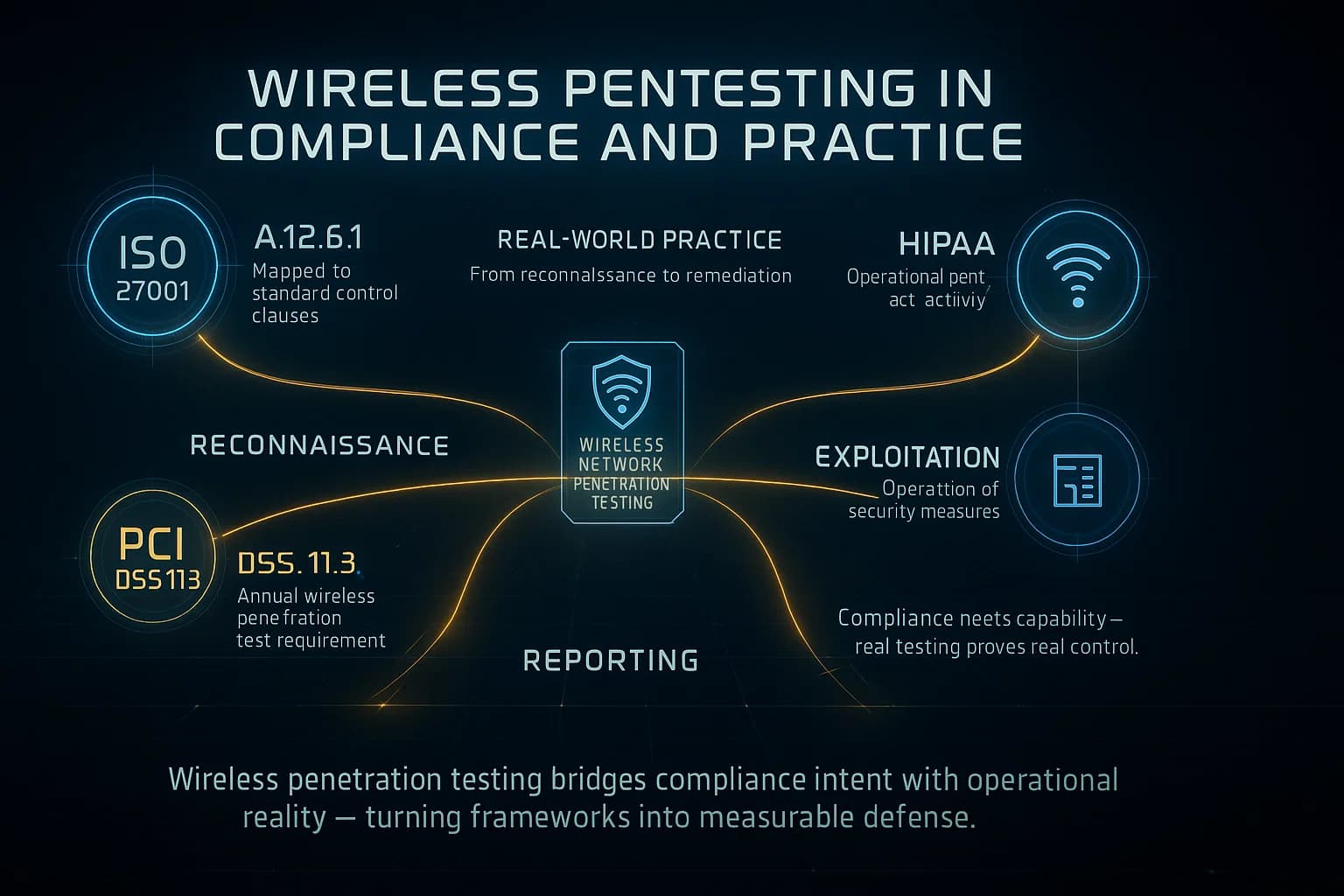
A wireless pentest is often part of a larger compliance or risk strategy. For example, PCI DSS explicitly calls for penetration testing of all in-scope networks including wireless to protect cardholder data. HIPAA’s Security Rule similarly requires safeguards on wireless PHI transmissions. Meeting these mandates usually means performing wireless tests at least annually or after major changes. Security teams often incorporate wireless pentests into vendor risk assessments, cyber insurance criteria, and audits.
Beyond compliance, wireless testing validates that your segmentation and encryption policies are effective. For instance, you may believe your guest Wi Fi is isolated, but a pentest might reveal a VLAN misconfiguration. Or you might discover that a connected IoT device uses a common password. Catching these issues is priceless: the cost of a data breach now averaging $4.88M per IBM 2025 is far higher than the pentesting budget. In short, wireless pentesting proves that your organization’s cybersecurity defenses actually work under attack. It closes the validation gap that audits and scanners alone can’t fill.
Wireless penetration testing uncovers the blind spots in your radio networks before attackers find them. In this guide we outlined the multi step methodology from passive discovery to active exploitation and reporting that ensures you cover Wi Fi, Bluetooth, IoT and other wireless assets in scope. By following industry best practices NIST/OWASP frameworks and using proven tools Aircrack ng, Kismet, Bettercap, etc., you can simulate real threats like Evil Twin APs or WPS PIN attacks in a safe, authorized manner.
Ready to strengthen your defenses? The threats of 2025 demand more than awareness they require readiness. If you want to validate your wireless security posture, identify hidden Wi Fi risks, or meet compliance mandates, DeepStrike is here to help.

Our team of certified testers provides clear, actionable guidance on fixing wireless vulnerabilities. Explore our Wireless penetration testing services to see how we can uncover weaknesses before attackers do.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Wireless penetration testing is a security assessment focused on radio based networks Wi Fi, Bluetooth, Zigbee, etc.. Testers use hacker tools to probe these wireless systems for vulnerabilities, just as an attacker would. Unlike a wired network scan, it includes discovering SSIDs, capturing authentication handshakes, testing WPS and Bluetooth pairing, and even setting up fake access points. The goal is to find and fix wireless specific flaws weak encryption, rogue APs, insecure IoT radios before real attackers exploit them.
The process typically follows standard pentest phases:
A typical toolkit includes: a USB Wi Fi adapter capable of monitor mode e.g. Alfa AWUS, Aircrack ng suite airodump, aireplay, aircrack, Wash/Reaver for WPS attacks, hcxdumptool for PMKID capture, Kismet for mapping networks, Bettercap for Evil Twin and BLE attacks, BlueHydra or gatttool for Bluetooth scanning, and Wireshark for analysis. An SDR HackRF, RTL SDR is useful for non Wi Fi radios. Also carry a packet injection capable Linux laptop Kali or Parrot OS with these tools. The exact tools may vary, but they all aim to sniff, crack, or spoof wireless signals.
An Evil Twin attack is when a hacker creates a fake Wi Fi access point that mimics a legitimate SSID. They often do this in public or office networks. Unsuspecting users see the fake AP often with a stronger signal and connect to it. Then all their network traffic is routed through the attacker’s machine. Kaspersky explains that once connected to the fake AP, any data users send passes through the attacker’s server. The attacker can steal credentials or inject malware. In pentesting, setting up an Evil Twin for example with Bettercap’s wifi.ap feature tests whether users or devices would be fooled, and shows what data could be compromised.
Wireless networks should be tested at least annually, but ideally whenever there’s a significant change, new APs, firmware updates, configuration changes. Many regulations PCI DSS 11.3, HIPAA require yearly or quarterly tests. In practice, critical environments might even run quarterly or rolling tests. Automated scanners can run more frequently, but a full wireless pentest should be done regularly to catch new vulnerabilities, as common tools or new devices appear. Treat wireless pentests as an ongoing process, not a one off.
Costs vary based on scope. Generally, pentest engagements range from a few thousand dollars for small tests to tens of thousands for large environments. A dedicated wireless assessment covering all APs, IoT radios, etc. might cost at the low end of that range if limited in scope. Many firms include wireless as part of a network pentest or PTaaS subscription. Key factors are number of sites, APs, and tester expertise. As one guide notes, small orgs often pay thousands, while large enterprises pay tens or even hundreds of thousands. Ultimately, it’s an investment: a single breach could cost millions more, so pentest costs are often budgeted as risk reduction.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us