November 6, 2025
Updated: November 5, 2025
Discover how penetration testing reports translate vulnerabilities into business insights improving security posture, compliance, and resilience in 2025.
Mohammed Khalil

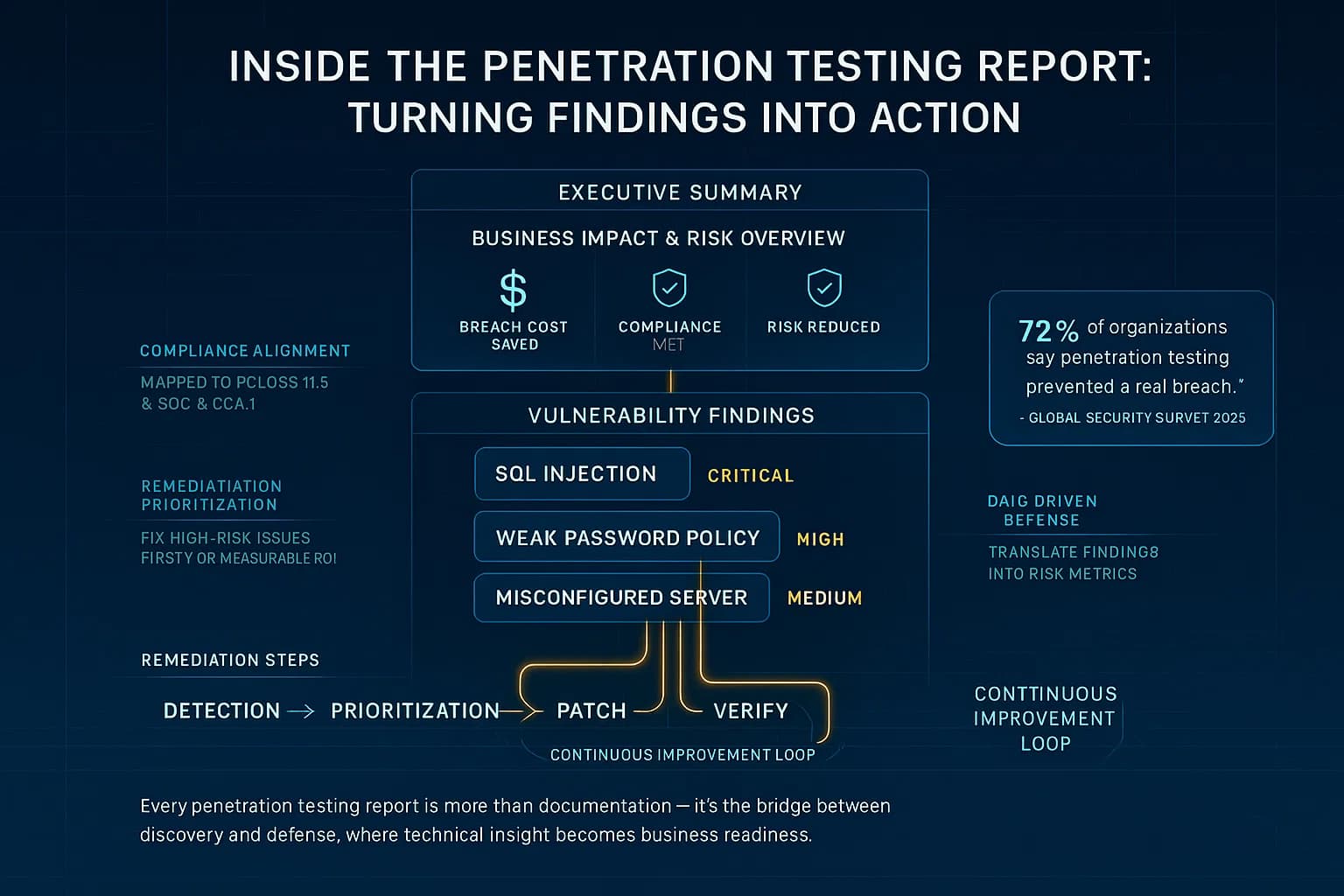
A penetration testing report is the final document produced after a pentest that lays out what was tested and what was found. It contains a detailed analysis of every vulnerability uncovered during the test describing each issue, its risk, and remediation steps. For example, one expert guide describes it as a document that contains a detailed analysis of the vulnerabilities uncovered during the security test. It records the vulnerabilities, the threat they pose, and possible remedial steps. In practice, a report always includes a high level executive summary for non technical stakeholders and in-depth technical findings for engineers.
This report is the bridge between security testing and security action. Executives use it to understand business impact and make risk decisions, while developers and IT staff use it to fix issues. In short, it’s both the elevator pitch for management and the field manual for remediation. Curious about the penetration test itself? See our article What is Penetration Testing? for background.

With cyber threats and regulations multiplying, a clear pentest report is more important than ever. Each year, attackers grow bolder and breaches more costly. IBM’s 2023 report found the U.S. average data breach cost $9.48 million. By identifying and documenting risks before an attacker does, organizations save money and prevent damage. In fact, a recent survey showed 72% of companies felt their pentests prevented a real breach. A good report helps teams fix high risk issues quickly and proves to stakeholders that you’re serious about security.
Compliance is another driving force. Many standards expect evidence of pen testing. For instance, PCI DSS 11.3 explicitly covers penetration testing: it states tests should cover both network and app layers internally and externally and that test methodologies and results should be documented and retained. Likewise, SOC 2’s Trust Services Criteria CC4.1 encourage diverse security evaluations, specifically mentioning penetration tests as one option. Even if not strictly mandated SOC 2 doesn’t require pentesting, auditors often expect one and review the report to confirm that critical vulnerabilities were addressed.
Moreover, customers and partners increasingly demand assurance. A polished pentest report or accompanying attestation can demonstrate robust defenses to clients, investors, or regulators. It can even be a marketing point: one firm notes that pentest reports help achieving compliance with industry standards and building trust with customers by showing you’re transparent about security.
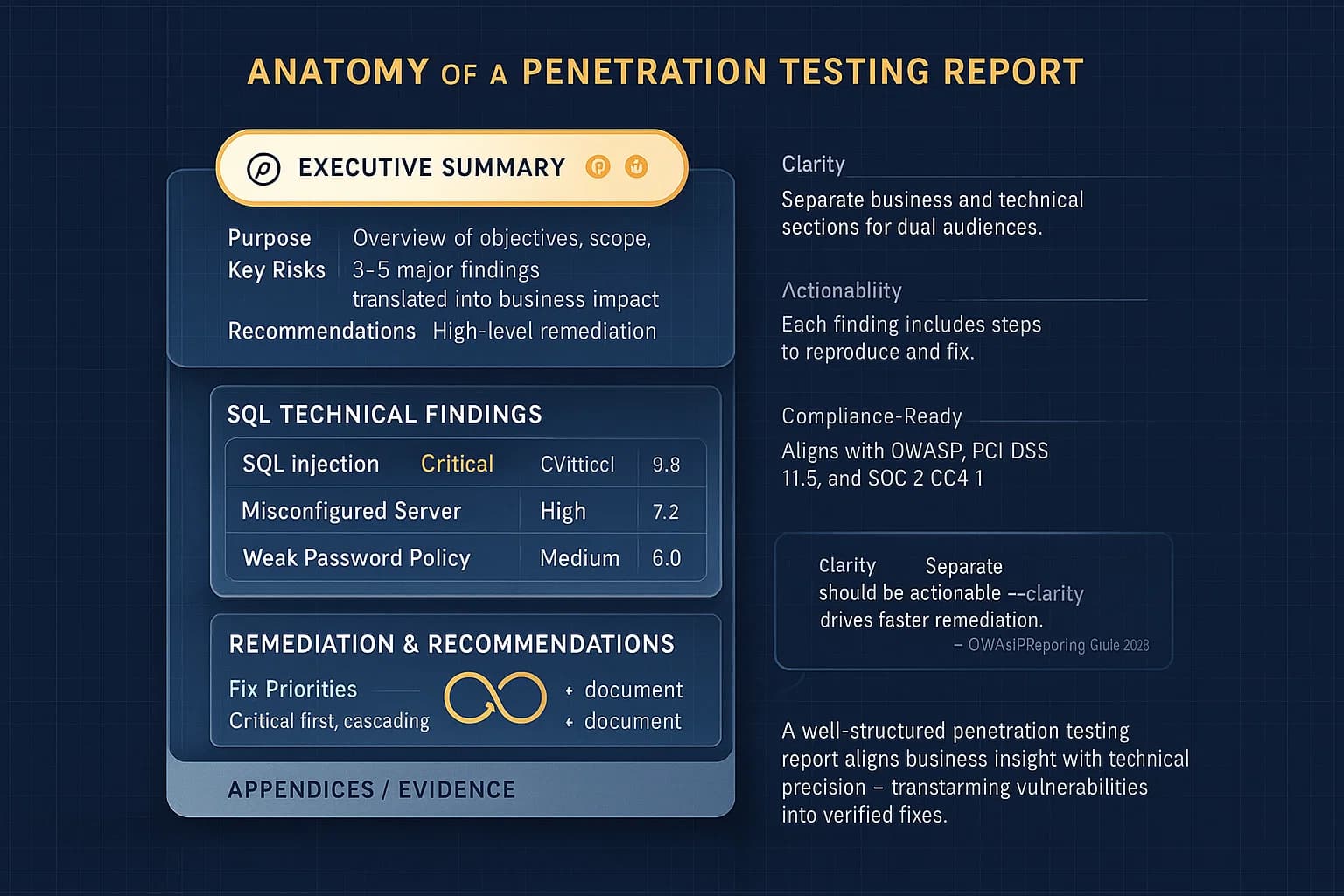
A professional report typically has three main parts:
Additional sections often include the scope and methodology what systems were tested, in what mode e.g. black box or gray box and appendices, detailed logs, tool output, evidence. For compliance, also include an attestation letter or summary that certifies the test was done by authorized testers and summarizes the overall result. Many organizations provide an attestation statement alongside the report to share with partners or regulators.
Internal vs External Penetration Testing Quick Comparison
| Aspect | External Test | Internal Test |
|---|---|---|
| Threat Model | Simulates an outside attacker on public networks, websites, email, etc.. Targets firewalls, web apps, VPNs, etc. | Simulates an insider threat or compromised host inside the network. Targets internal servers, AD, Wi Fi, etc. |
| Access | Tester starts from the Internet with no credentials. | Tester has a foothold e.g., employee network access. |
| Common Findings | Open ports, misconfigured servers, outdated internet facing software. | Unpatched internal systems e.g. SMB/RDP exploits, weak credentials, misconfigured user permissions. |
| Goal | Breach perimeter defenses and access data from outside. | Move laterally within network to gain high privilege access. |
| Typical Use Cases | Compliance, assessing perimeter security posture. | Testing internal controls especially after breaches or in large LANs. |
External testing seeks to identify vulnerabilities that attackers may exploit on public networks, while Internal testing identifies vulnerabilities that could be exploited internally by malicious employees.
Another key comparison is between penetration testing vs vulnerability scanning. A vulnerability assessment or scan is typically an automated process that finds and lists potential issues. In contrast, penetration testing is an active attempt to exploit vulnerabilities. As PCI DSS notes, a vulnerability scan simply identifies and reports noted vulnerabilities, whereas a penetration test attempts to exploit the vulnerabilities to determine whether unauthorized access or other malicious activity is possible. In other words, scanning says X and Y are problems; pentesting says we exploited X to get admin, here’s proof, and here’s how to fix it.
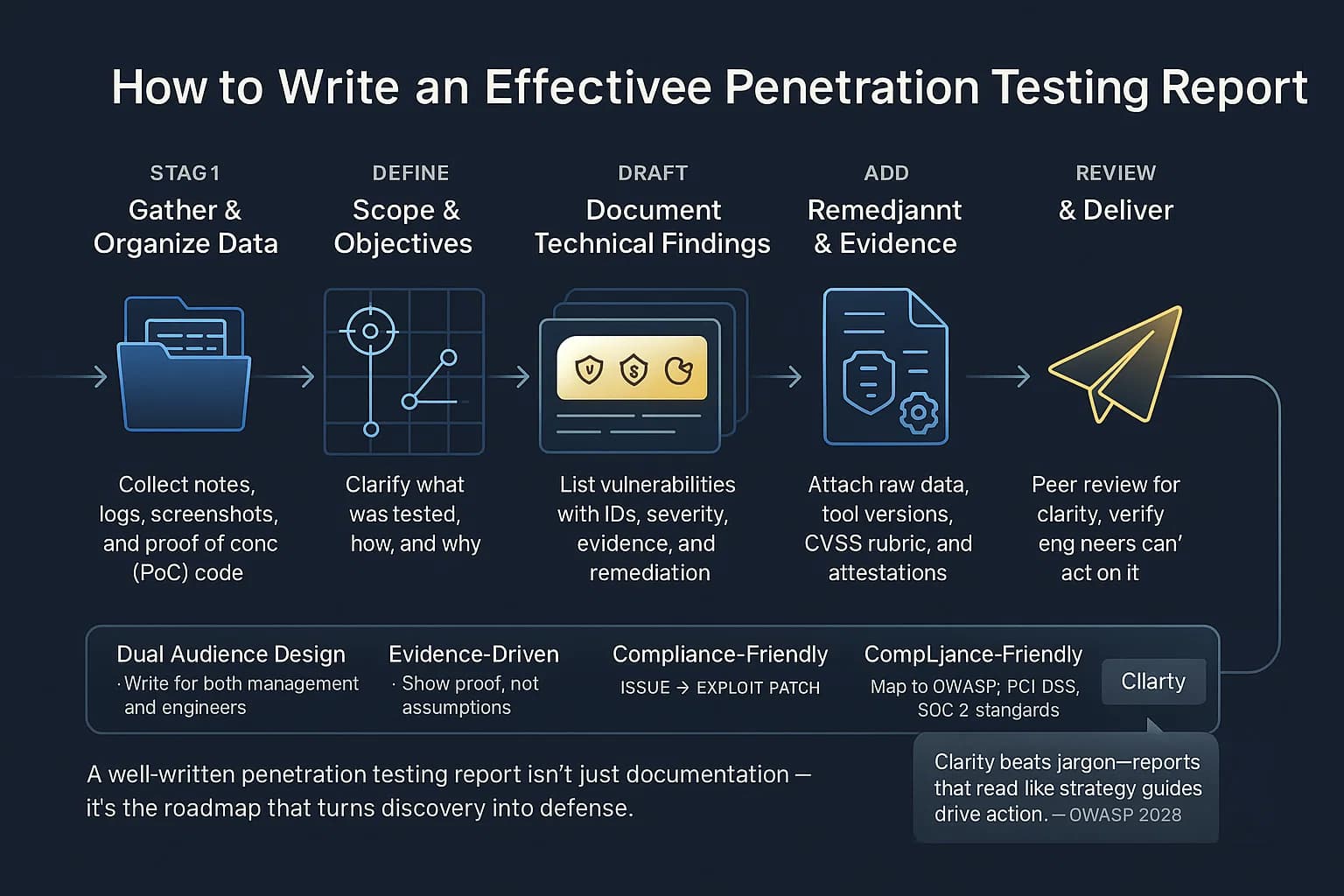
Putting the report together is as important as the test itself. Here are practical steps practitioners recommend:

By following a structured format and keeping the audience in mind, you’ll maximize the report’s value. Remember: the goal isn’t just to write a document, but to guide real security improvements.
Penetration testing reports are more than just paperwork they are the blueprint for fixing security gaps. By documenting findings clearly and recommending concrete fixes, a report turns a pen test from a one time audit into continuous security improvement. In today’s landscape with rampant cyber threats and strict audits, a well written report is essential for any organization serious about resilience.
Ready to strengthen your defenses? The threats of 2025 demand more than awareness they require readiness. If you want to validate your security posture, uncover hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of experienced practitioners provides clear, actionable guidance to protect your business.

Explore our penetration testing services to see how we can uncover vulnerabilities before attackers do. Drop us a line our experts are always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
A penetration testing report is the end result of a pentest. It’s a written document that details all vulnerabilities found, how they can be exploited, and how to fix them. Think of it as a roadmap for improving security: it includes a high level executive summary plus detailed technical sections covering each finding.
Typically, a professional report has an Executive Summary goals, overall risk, business impact, Technical Findings each vulnerability with severity, description, evidence, and remediation, and Recommendations prioritized fixes and next steps. Appendices often list test scope/methodology, tool output, and references. OWASP’s guidelines and industry templates recommend this structure to clearly address both management and technical audiences.
Multiple roles: Executives and managers read the summary to understand business risk and compliance status. Security and IT teams use the technical details to implement fixes. Developers examine specific code or config issues. It can even be shared with auditors or clients as proof of diligence. In fact, a pentest report can support certifications like SOC 2 or ISO 27001, demonstrating you’ve tested and fixed vulnerabilities.
Industry best practices suggest at least annually or after any major change. For example, PCI DSS requires yearly tests or after significant upgrades. In dynamic environments like continuous deployment, more frequent or continuous testing via a PTaaS model is recommended. Regular reports keep security posture up to date. At a minimum, updating your report annually and after each re-test ensures new vulnerabilities haven’t crept in.
It depends on the standard. Some explicitly require documented pentests PCI DSS 11.3, HIPAA guidance, etc., while others like SOC 2 consider them a strong recommendation but not mandatory. For instance, SOC 2’s CC4.1 trusts ongoing evaluations including penetration testing, so doing a pentest helps demonstrate your controls. In general, even if not strictly required, a good report can greatly simplify an audit and provide valuable evidence of security efforts.
A vulnerability scan assessment automatically finds known issues and lists them. A pentest goes further by actively exploiting vulnerabilities to show their real impact. In simple terms: a scan says these issues exist, whereas penetration testing proves how they can be used maliciously. Thus, pentest reports usually have more depth, context, and prioritization than simple scan reports.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us