December 14, 2025
An independent, research-driven guide to the UK’s leading cybersecurity service providers
Mohammed Khalil

Choosing the right cybersecurity provider is mission critical in 2025. Cyber threats are at an all time high with AI driven attacks and more aggressive ransomware strains emerging while businesses face mounting compliance pressures GDPR, PCI DSS, ISO 27001, NIS2, etc. to prove their security due diligence. The UK cybersecurity market has matured, offering everything from boutique penetration testing specialists to large managed security service providers MSSPs . Selecting a provider isn’t just about finding the best in general, but finding the one best suited to your specific needs in terms of expertise, scope, and trustworthiness.
This independent, research driven ranking is designed to help UK organizations shortlist top cybersecurity companies confidently. We analyzed numerous firms against objective criteria detailed below to ensure an unbiased evaluation. Whether you’re a small fintech startup or a large government agency, this list will highlight providers known for excellence in their domains from offensive security testing to managed SOC monitoring. Editorial note: we’ve applied the same evaluation criteria to all companies on this list, including DeepStrike, the author’s firm , to maintain neutrality and transparency.
Below we present our researched picks for the leading UK headquartered cybersecurity companies, each with its unique strengths. All of these firms offer professional security assessment services such as penetration testing and red teaming , with some also providing managed security or compliance consulting. The list is not simply largest to smallest; each is highlighted for excelling in a particular niche or use case. All company data such as headquarters, founding year, size, etc., are as of late 2025.
Headquarters: London, UK
Founded: 2018 est.
Company Size: ~150 employees boutique
Primary Services: Penetration testing web, mobile, cloud, API , red team engagements, adversary simulation, vulnerability assessment, and PTaaS Penetration Testing as a Service platform.
Industries Served: Technology, finance, healthcare, hospitality, and other sectors requiring advanced security testing mid market to large enterprises
Why They Stand Out: DeepStrike is a next generation penetration testing provider that combines hands-on expertise with an innovative delivery platform. Unlike many traditional consultancies, DeepStrike emphasizes manual testing techniques to uncover complex vulnerabilities that automated tools often miss. They augment this human driven approach with a cloud based PTaaS platform that provides clients real time dashboards, continuous testing options, and free retesting of identified issues. This blend of elite human skill and modern technology gives clients both depth of testing and ongoing visibility. DeepStrike’s team is composed of senior testers with certifications like OSCP, OSWE, CISSP, and years of experience in offensive security. They have particular expertise in cloud and API security, reflecting the needs of today’s SaaS driven organizations. Clients frequently praise DeepStrike’s detailed, high quality reports and actionable remediation guidance, as well as their responsive communication. Despite being a smaller firm, DeepStrike is known to be flexible and fast moving, adapting to agile development cycles and providing a personalized engagement experience that some larger firms struggle to match.
Key Strengths:
Potential Limitations: As a growing boutique, DeepStrike does not have the massive global footprint of some competitors. Large enterprises with operations across dozens of countries might still engage a bigger firm for sheer scale. Additionally, DeepStrike’s focus on deep manual testing and quality means they may not be the cheapest option for very small engagements; budget sensitive clients with simple needs might find more basic testing providers. However, their value is in the thoroughness and support provided.
Best For: Mid size companies up through large enterprises that want top tier penetration testing with personalized service. Especially suitable for organizations embracing cloud technologies or fast paced dev cycles, who need a partner that can integrate continuous testing and work closely with development teams. Also a great choice for those who require strong technical expertise but appreciate a flexible alternative to big consultancies. Editorial note: DeepStrike is included in this list based on the same evaluation criteria applied to all providers.
Headquarters: Manchester, UK
Founded: 1999
Company Size: ~2,200 employees global
Primary Services: Cybersecurity consulting and assurance penetration testing, red teaming, risk assessment , managed security services SOC monitoring, threat intelligence , software escrow and verification, incident response.
Industries Served: Broad range financial services, government and public sector, telecom, critical infrastructure, retail, and more with a worldwide client base of over 15,000 businesses .
Why They Stand Out: NCC Group is one of the UK’s largest and most established cybersecurity firms, known for its scale and pedigree. As a public company listed on the London Stock Exchange FTSE 250 , NCC brings a high level of credibility and resources. They have teams across Europe, North America, and Asia, enabling truly global engagement delivery. NCC Group’s penetration testing and security assessment practice is decades old, having absorbed respected outfits like NGS Software and Fox IT over the years. This means they offer unparalleled breadth of expertise whether you need a simple web app test or a full scale Red Team operation mimicking nation state actors, NCC can field specialists for the job. They are CREST accredited and were a founding member of CREST, often contributing to industry standards. Their methodologies are research driven NCC researchers frequently present at Black Hat/DEF CON , and they maintain proprietary tools and vulnerability labs. Enterprise clients appreciate that NCC is likely already approved by regulators and on procurement lists for example, NCC is a CHECK service provider for UK government work . While their services come at a premium price, you get extensive quality assurance, peer review processes, and detailed documentation valuable for meeting compliance obligations. In short, NCC Group is often the go to when maximum assurance is required for critical systems.
Key Strengths:
Potential Limitations: As a large firm, NCC Group’s processes can be more formal and less agile. Newer or smaller clients might find themselves navigating more bureaucracy proposal processes, scheduling, etc. compared to a nimble boutique. Their pricing is on the higher side you are partly paying for the brand name and overhead. Additionally, while they cover SMB needs too, very small companies might find NCC’s offerings beyond their scale NCC tends to focus on mid to large clients where the value of comprehensive assurance is worth the cost .
Best For: Large enterprises and regulated organizations finance, healthcare, government that need a proven, full service security partner. NCC Group is ideal when you require the confidence of a big player that auditors and boards recognize. It’s also a top choice for global companies seeking a one stop provider to handle engagements in multiple countries seamlessly.
Headquarters: London & Stevenage, UK
Founded: 2016 as Bulletproof Cyber
Company Size: ~100+ employees
Primary Services: Penetration testing web, mobile, infrastructure , vulnerability scanning, managed SIEM & SOC monitoring, compliance consulting ISO 27001, GDPR, PCI DSS , virtual CISO services, security awareness training.
Industries Served: Mid market and small enterprises across tech startups, SaaS, e commerce, fintech, and any organizations seeking cost effective security testing and compliance support.
Why They Stand Out: Bulletproof is a newer entrant relative to some giants, but it has quickly carved out a niche as a one stop security provider for SMB and mid sized clients. They pair traditional pentesting services with a strong emphasis on compliance needs for instance, they often bundle penetration tests as part of broader compliance packages PCI DSS audits, ISO 27001 readiness, Cyber Essentials certification in the UK . Bulletproof is CREST approved and ISO 27001 certified themselves, signaling credibility. Uniquely, they operate a UK based Security Operations Centre and can offer 24/7 threat monitoring and managed SIEM as an extension of their technical testing. This means clients can engage them not just for one off tests, but ongoing security operations if needed. Bulletproof’s approach is described as very accessible and customer friendly; they offer fixed price testing bundles ideal for smaller companies e.g. a simple external/internal test for a set fee , with quick turnaround. Their reports distill findings into business impact terms, avoiding heavy jargon, which is appreciated by IT managers who may not be security specialists. Many startups and mid size firms choose Bulletproof because they get both technical assurance e.g. a CREST certified pentest and guidance on improving policies and compliance, all from one provider. The company’s leadership including OSCP certified experts often shares insights via webinars and resources, further building trust with the community.
Key Strengths:
Potential Limitations: Being focused on SMB and mid market, Bulletproof might not have the same depth of specialty skills for extremely complex projects that some larger or niche firms do. For example, ultra sophisticated red team exercises or testing of very novel technologies like custom cryptographic systems may be outside their typical scope. Large enterprises with global offices might find Bulletproof’s geographic reach limited, primarily UK based, though they can service remote/global work to some extent . Also, if an organization only wants a very narrowly scoped technical test with no interest in the compliance add ons, they might find Bulletproof’s value add unnecessary such clients could opt for a specialist firm instead.
Best For: Small and mid sized organizations in the UK that need professional security testing and compliance support at a reasonable cost. Also suitable for mid market companies that lack in-house security staff, Bulletproof can function as an outsourced security partner, handling everything from testing to daily monitoring. It’s a great fit for SaaS companies, online retailers, and any business needing to meet standards like ISO 27001 or Cyber Essentials while also improving their security posture.
Headquarters: Leamington Spa, UK
Founded: 2003
Company Size: ~200+ employees acquired by Lloyd’s Register in 2018
Primary Services: Penetration testing network, app, cloud, IoT, OT , red teaming including regulated CBEST/TIBER tests for finance , vulnerability assessment, security auditing, governance/risk/compliance consulting, managed detection & response MDR , incident response.
Industries Served: Highly regulated sectors banking & financial services, insurance, government, marine and shipping, critical infrastructure energy, transportation , and any org needing both security assurance and compliance alignment.
Why They Stand Out: Nettitude is known for bridging the gap between security testing and compliance requirements. Now part of LRQA Lloyd’s Register’s assurance division , Nettitude leverages its parent company’s legacy in standards and certifications. This means when Nettitude performs a penetration test, they keep an eye on how the findings relate to frameworks like ISO 27001, SOC 2, or sector specific regulations. They often provide one stop services: a company can get their required audits PCI DSS scans, ISO certification and their technical security testing done through a single engagement. Nettitude is a CREST member and also an approved CHECK provider, so they are cleared for UK government work. Their team carries not only technical certifications OSCP, GIAC GPEN etc. but also qualifications like PCI QSA and ISO 27001 Lead Auditor, a blend that supports both technical depth and paperwork rigor. Clients in finance and critical infrastructure often choose Nettitude for big red team exercises mandated by regulators such as Bank of England’s CBEST because Nettitude can deliver the adversarial testing while ensuring all compliance reporting boxes are checked. They produce very polished, executive friendly reports that map vulnerabilities to risk categories and compliance controls. In terms of innovation, Nettitude invests in developing tools and techniques being described as research-led , but always with an eye toward reliability and standards. Their approach tends to be very methodical and professional, making them a trusted advisor especially in boardrooms and audit committees.
Key Strengths:
Potential Limitations: Nettitude’s meticulous, compliance oriented approach might feel overkill for startups or unregulated small businesses. Their services are tailored to those who value governance and formal risk management. If you just want a quick and dirty security test, a smaller pentest only shop might be more straightforward. Also, since being acquired and integrated into a larger corporate structure, some clients might perceive Nettitude as less flexible on pricing and scheduling compared to independent boutiques. Lastly, while they do offer offensive security, uber technical buyers like product security teams might find other firms more cutting edge for niche exploits Nettitude tends to prioritize reliability and comprehensiveness over flashy hacks.
Best For: Banks, financial institutions, and enterprises in heavily regulated sectors e.g. finance, insurance, energy, government suppliers that need assurance of security testing and help with compliance outcomes. Also ideal for any mid to large company that must align security improvements with audits and standards. If your goal is to both harden your systems and check the compliance box with solid documentation, Nettitude is a top choice.
Headquarters: Buckingham Buckinghamshire , UK
Founded: 2010
Company Size: ~100+ employees
Primary Services: Specialized penetration testing and red teaming including web app, mobile app, API testing, network infrastructure, wireless, IoT/industrial control system ICS security, code review, cloud configuration reviews. Also provides incident response DFIR and bespoke security training.
Industries Served: Wide variety, with notable presence in critical infrastructure and industrial sectors energy, transport, manufacturing , finance, aerospace, and technology. Often engaged by organizations needing deep technical dives e.g. IoT device manufacturers, automotive and aviation systems, maritime .
Why They Stand Out: Pen Test Partners is often regarded as one of the UK’s most technically adept boutique security firms. They are the largest independent pen testing only consultancy in the UK, not part of a big conglomerate. This independence shows in their work: PTP consultants frequently publish research on zero day vulnerabilities, IoT hacks they’ve famously demonstrated car and smart ship hacks in conferences , and novel attack techniques. The team features well known experts like Ken Munro, and many are active in the security community. For clients, this translates to engagements where the testers go above and beyond default checklists; they'll spend time creatively exploring complex scenarios to find chained exploits. PTP is fully CREST accredited and certified for schemes like CHECK, CBEST, TIBER and PCI ASV, which means they meet all the formal criteria for quality. They also have a global footprint for a boutique, with offices or presence in the US and Europe, allowing them to service multinational clients while still being UK led. A standout area for PTP is IoT and OT security: few competitors can match their experience in testing embedded systems, vehicles, maritime systems, and industrial controls sectors where PTP has done pioneering work. They also offer a PTaaS Pentest as a Service portal for customers to manage findings, though their core selling point remains the depth of their manual testing. Clients that need an attacker mindset love PTP’s thoroughness; they have a reputation for not quitting until they’ve found a way in or exhausted every avenue.
Key Strengths:
Potential Limitations: As a boutique, PTP may not offer some services outside pure security testing for instance, they are not an MSSP, so they won’t run your SOC though they partner with others if needed . Organizations looking for a single vendor to also do managed security or extensive compliance consulting might need additional providers alongside PTP. Also, high demand for PTP’s top experts can sometimes mean scheduling tests well in advance, especially for large red team engagements. In terms of cost, they are not a bargain option; their pricing reflects the skill level of their team. This is usually justified by the results, but very small companies might find PTP’s services pricey compared to more junior consultants in the market.
Best For: Organizations that require top tier, in depth penetration testing expertise and value technical excellence over brand name. PTP is ideal for security conscious companies who want the best testers to poke at their systems for example, automotive or IoT product companies before launch, critical infrastructure operators seeking a thorough check, or any enterprise that already has decent security and needs testers who can really challenge their defenses. Also a great choice for red team exercises where stealth and creativity are paramount.
Headquarters: Manchester, UK
Founded: 2001
Company Size: ~40–50 employees specialist firm
Primary Services: Adversarial simulation and penetration testing with an offensive security focus red teaming including physical & social engineering , network and application pentesting, social engineering assessments, and continuous penetration testing services PTaaS . Historically also engaged in security research and tool development.
Industries Served: Healthcare NHS trusts , financial tech fintech startups, payment processors , energy and utilities, and government/defense related organizations essentially clients facing advanced threats who need to test against determined attackers.
Why They Stand Out: Secarma is a UK boutique known for its attacker mindset and persistence in engagements. Spun out of the UKFast technology group in Manchester, Secarma built its name doing hardcore penetration tests and red team exercises that mimic real threat actors. They approach testing with a philosophy of we don't quit until every door and window is checked. In practice, a Secarma red team might run for weeks, blending cyber attacks with physical intrusion attempts like tailgating into offices and crafty social engineering phishing campaigns, USB drops to fully challenge an organization’s detection and response. This relentless approach has uncovered serious gaps for their clients, making them a valued partner for improving security postures. Secarma also invests in R&D: for example, they have developed custom malware implants and tools one known example is the EndView implant referenced in industry chatter to use in engagements, which gives them an edge in sophistication. They were early contributors to intelligence led testing frameworks in the UK like helping shape some CBEST exercises . Despite being smaller, Secarma has a tight knit team of OSCP/GIAC certified consultants who often punch above their weight. Clients, including parts of the NHS and others, choose Secarma for engagements where they want a fresh perspective and true bad guy simulation, rather than a compliance checkbox pentest. Additionally, Secarma offers a Penetration Testing as a Service model for continuous testing showing they keep up with modern delivery trends.
Key Strengths:
Potential Limitations: Given their size about 40 staff as of a few years ago , Secarma may have capacity constraints. Very large projects or tight deadlines might be challenging to staff compared to bigger companies. They also do not provide defensive or managed services, so after a red team you’d need another vendor or your own team to implement 24/7 defense Secarma’s role ends with the assessment and advice. Some highly structured organizations might find Secarma’s style a bit unorthodox, as they are less about formal reports for compliance and more about raw security insights though they do provide professional reports, just with a focus on attack narrative . Lastly, since they focus on high end engagements, the cost of a months long red team by Secarma could be significant potentially outside the budget of smaller firms.
Best For: Mature organizations and critical infrastructure providers that want to rigorously test themselves against the latest threats. If you have a solid security program and now need to probe for blind spots with an offensive specialist team, Secarma is ideal. This includes companies preparing for something like CBEST testing, or those who experienced incidents and want an attacker’s perspective to prevent a next one. Also a fit for security conscious mid sized companies who prefer a boutique feel but with top notch skills.
Headquarters: Reading, UK
Founded: 2013
Company Size: ~300+ employees as of 2025
Primary Services: Managed Security Service Provider MSSP offerings 24x7 Security Operations Center, managed SIEM, threat intelligence, incident response , cyber security consulting strategy, risk, architecture design , penetration testing and security assessments, cloud security, data privacy and GDPR consulting.
Industries Served: Broad, with strong focus on Critical National Infrastructure CNI and regulated industries e.g. aviation, utilities, government agencies, financial services as well as large enterprises in various sectors requiring around the clock security operations.
Why They Stand Out: Bridewell has rapidly grown in the UK to become a leading independent cybersecurity services company, known particularly for its managed security services combined with expert consulting. They essentially bridge the gap between a consulting firm and an MSSP. On one hand, Bridewell offers advisory services and assessments including CREST accredited penetration testing , and on the other, they operate a state of the art SOC that can monitor and defend client networks. This dual capability means clients can engage Bridewell for strategic projects like a security architecture review or one off pentest and then transition into ongoing operational support under one roof. Bridewell has invested heavily in serving critical industries; for example, they have experience securing operational technology OT environments for transport and energy, which few MSSPs do. They emphasize having UK government cleared staff and high trust accreditations; they hold NCSC Cyber Incident Response accreditation, among others . Bridewell’s growth and partnerships they recently entered a strategic partnership with France’s I TRACING to form a European cyber powerhouse indicate they are on an ambitious trajectory.. Clients like Bridewell combine the feel of an independent firm with customer service and flexibility with the scale to handle big projects, 300+ employees and expanding . They also leverage innovative tech in their SOC cloud native SIEM, automation which can benefit clients looking for modern, efficient detection and response.
Key Strengths:
Potential Limitations: Bridewell is becoming a large player, but not as globally present as some competitors yet though they have a U.S. office, their footprint is mainly UK . Large multinational clients might require partners in regions Bridewell isn’t in, which could add complexity. Additionally, organizations purely looking for a specialized penetration test might consider Bridewell’s pentest team solid but not as singularly focused as a pure play offensive firm Bridewell’s breadth is a strength, but for depth in one area, niche firms might edge them out for example, for an advanced IoT device test, a boutique like PTP might be preferred . Also, some very small businesses could find Bridewell’s comprehensive offerings beyond what they need; Bridewell’s typical clients are mid to large, so they may not market low cost small business packages as much as others.
Best For: Enterprises and critical infrastructure operators that want a capable UK based partner to both advise on and operationally manage cybersecurity. If you are a company that doesn’t just want findings, but help fixing them and monitoring afterward, Bridewell is ideal. It’s especially suited for those in regulated or high threat environments financial services, energy, transport, etc. where a combination of advisory and 24/7 protection is needed. Also a good fit for organizations looking to outsource their SOC to a trusted UK provider without going to one of the huge global MSSPs.
Headquarters: London/Guildford, UK BAE Systems AI division
Founded: 1971 as Detica, became BAE Applied Intelligence in 2010s
Company Size: ~4,000 employees cyber division of BAE Systems
Primary Services: Broad cybersecurity and intelligence solutions consulting and advisory risk assessment, strategy , systems integration, managed security services, threat intelligence, penetration testing and red teaming, cyber defence products monitoring platforms , and support for national security programs.
Industries Served: Government and public sector defence, intelligence agencies, central government departments , large financial institutions, telecommunications, and other global enterprises requiring high assurance security, often with an emphasis on nation state level threats.
Why They Stand Out: BAE Systems Applied Intelligence AI is the cybersecurity arm of BAE Systems, a major defense contractor. It brings a defense grade approach to commercial cybersecurity challenges. With roots in Detica, a renowned UK defense/intel consultancy , BAE AI has a legacy of working on classified government projects and the methodologies from that world inform their services to banks, telcos, and others. They are known for handling incredibly complex, large scale security projects: e.g., building secure systems integration for government networks, running security operations centers that analyze nation state threat actors, etc. For penetration testing and red teaming, BAE AI can deploy elite teams often composed of ex military or intelligence personnel alongside top tier ethical hackers. They tend to simulate sophisticated threat actors, leveraging internal threat intel feeds. A key differentiator is that BAE pairs cyber technology solutions they have proprietary software for threat detection, analytics, etc. with consulting. So a client might engage BAE to implement a big data security analytics platform and also test their infrastructure. BAE’s global reach is extensive, over 4,000 staff in 40 offices worldwide meaning they can operate wherever the client is, often with local clearance. They also have deep expertise in protecting critical systems like military tech, satellites, etc. , which can translate into assurance for critical enterprise systems. While BAE’s services are not cheap and often geared to large projects, the advantage is a one stop powerhouse that can marshal vast resources. Their reports and deliverables carry an authoritative tone that can be useful when presenting to boards or regulators having BAE’s name on a security assessment often instills confidence that it was done to a high standard.
Key Strengths:
Potential Limitations: For many commercial businesses, BAE Systems AI can be overkill. Their engagement processes, inherited from defense contracting, are very formal and can be slower. They tend to focus on very large clients; a mid-sized company might find themselves a smaller fish in BAE’s client roster and possibly not get the same level of attentiveness they would from a smaller provider. The cost is high, you're partly paying for the BAE brand and extensive overhead. Also, because BAE offers so many services, if you only need a quick pentest, the sales and delivery process might feel too cumbersome compared to a specialist firm. In short, BAE is not as agile or cost efficient for straightforward needs. Some tech startups or agile companies might also feel that BAE’s style is too conservative or old school in approach, as they are very process driven.
Best For: Government agencies, defense contractors, and large enterprises that require the utmost assurance and have the budget to match. Also suitable for banks or telecom giants that want a provider with equal global stature and the ability to handle projects that intersect with national security. If an organization values having a big name defense expert and possibly needs a combination of software + services, BAE Systems Applied Intelligence is a top contender. Essentially, when the stakes are extremely high and you need a partner who has seen the most advanced cyber warfare techniques, BAE fits the bill.
To help summarize these companies’ core focus and fit, the comparison table below highlights key attributes:
| Company | Specialization | Best For | Region Coverage | Compliance Credentials | Ideal Client Size |
|---|---|---|---|---|---|
| DeepStrike | Manual pentesting + PTaaS platform | Balanced needs quality + agility | UK focused global remote | CREST anticipated , OSCP certified team | Mid size to Enterprise |
| NCC Group | Full spectrum assurance & consulting | Highly regulated enterprises, gov | Global HQ in UK | CREST, CHECK, multiple global accreditations | Large Enterprise |
| Bulletproof | Pentesting & 24/7 SOC for SMBs | Small/medium businesses, mid market | UK services global remotely | CREST, ISO 27001, Cyber Essentials | Small to Mid size |
| Nettitude | Pentesting + compliance integration | Audit driven orgs finance, critical | UK, EU, US LRQA network | CREST, CHECK, PCI QSA, ISO 27001 LRQA | Mid to Large Enterprise |
| Pen Test Partners | Deep dive technical testing | Technical & IoT/ICS focused testing | UK, EU, US boutique global | CREST, CHECK, CBEST/TIBER certified | Mid to Large Enterprise |
| Secarma | Adversarial red teaming | Advanced threat simulation | UK with some global reach | CREST, CHECK offensive focus | Mid to Large with mature sec |
| Bridewell | Managed SOC + consulting hybrid | Continuous security management | UK, USA Europe via partners | CREST, NCSC CIR, ISO 27001, CE+ | Mid to Large Enterprise |
| BAE Systems AI | Defense grade cyber solutions | High assurance security programs | Global 40+ offices | NCSC Certified, NATO/defense contracts | Large Enterprise/Government |

Our ranking methodology is grounded in E E A T principles Experience, Expertise, Authoritativeness, Trustworthiness and procurement friendly transparency. We evaluated each company on multiple factors:
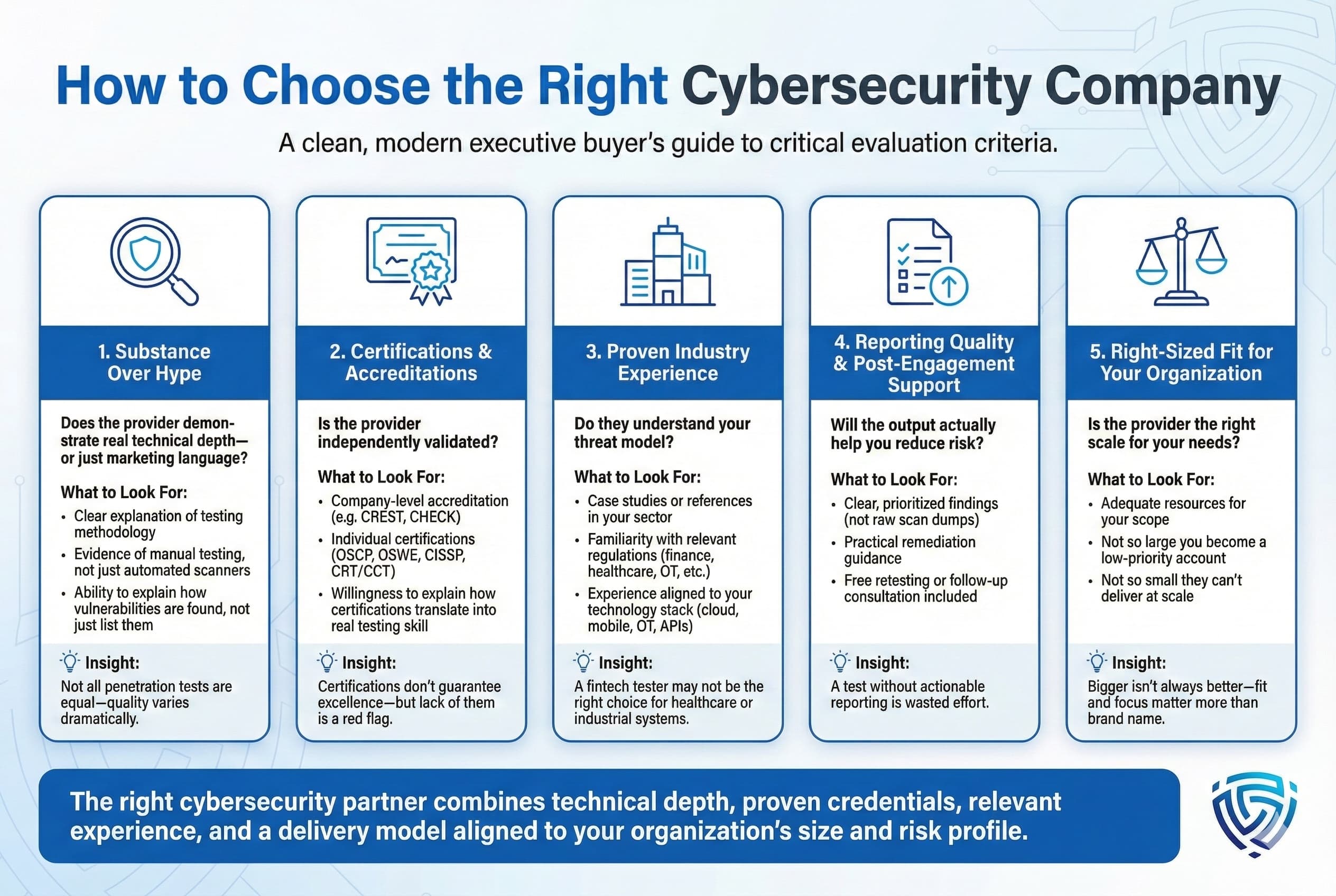
Not all cybersecurity vendors are created equal, and choosing poorly can waste budget or, worse, leave you exposed. Here are key considerations when selecting a provider:
By considering these factors and asking the right questions, you can avoid common pitfalls like choosing solely on price or brand name without fit and select a cybersecurity partner that truly matches your organization’s risk profile and culture.

One critical consideration is whether your organization will be best served by a large enterprise scale provider or a smaller boutique firm or something in between like a mid sized specialist . Both have pros and cons, depending on your needs:
In many cases, organizations adopt a hybrid approach using big providers for certain needs e.g., an annual compliance mandated test or managed SOC services and niche experts for others e.g., a one off IoT device assessment or a second opinion test on a critical app . What’s key is to understand your own requirements, risk appetite, and resource constraints, so you can engage the right type of vendor for each aspect of your security program.
Penetration testing costs can vary widely based on scope, depth, and provider. In the UK, a basic internal/external test for a small business might start around a few thousand pounds, whereas a comprehensive multi week red team engagement for a large enterprise can run tens of thousands. Boutique firms often charge on a per project or daily rate basis e.g. £800- £1200 per consultant per day is a rough figure , while large consultancies might have higher day rates but can throw more people at a project. Be cautious of quotes that seem too good to be true , extremely low cost offers a few hundred pounds likely indicate a superficial automated scan rather than a real pentest. Always ask what’s included manual testing hours, number of testers, retests, etc. . Also, consider value over cost: a more expensive test that finds serious vulnerabilities and provides remediation guidance is far better than a cheap test that misses things. Many providers, like those in this list, will discuss your needs and give a custom quote or even a checklist to scope cost transparently. As a rule of thumb, set aside a budget that aligns with the criticality of your systems e.g., a customer facing financial app warrants more testing investment than an internal brochure site.
Certifications and tools are both important in different ways. Certifications for both companies and individuals act as trust signals: a CREST certified company has been vetted for processes, and an OSCP certified tester has proven they can hack into systems in a lab scenario. These indicate baseline competence and commitment to professionalism. Tools, on the other hand, are the means to test good tools whether commercial scanners, custom scripts, or exploit frameworks enable breadth and depth in finding issues. However, the key is how they’re used. A highly certified team that only runs automated tools without creativity might miss business logic flaws. Conversely, an uncertified tester with great tool skills might find bugs but could be inconsistent or unreliable in approach. Ideally, you want experienced people who often have certs as one indication of their knowledge using the right tools judiciously. Human expertise will determine how tools are configured and how results are interpreted. So, certifications are not everything, but they help you shortlist qualified providers; tools are necessary but not sufficient without skilled operators. A quality provider will have both: certified experts who also develop and utilize advanced tools as needed.
The duration of a penetration test depends on the scope and complexity. A small scale test, say, a single web application or a small office network might be completed in 1-2 weeks including reporting. A large organization’s infrastructure, however, could take 4-6 weeks or longer, especially if it involves thousands of IPs, multiple locations, or a full red team exercise. Red teaming engagements, which simulate a determined attacker, often run for several weeks to a few months in a covert manner to allow the team to discover multiple ways in and test detection. It’s important to allocate time for scoping and preparation as well. A good provider will spend time upfront understanding your environment and setting rules of engagement. After active testing, reporting can take a few days to a week to compile, especially if it’s a detailed report with executive summary, technical details, and mitigation advice. Always discuss the timeline with your provider and align it with any deadlines you have e.g., compliance deadlines or product launch dates . Remember not to rush the process unduly; a hurried test might miss something. Many companies do annual testing or even quarterly testing on critical assets, treating it as an ongoing process rather than a one time sprint.
A professional penetration test report typically contains: an Executive Summary overview of the assessment, high level findings, and overall risk rating meant for management , a Technical Findings section detailed description of each vulnerability found, steps to reproduce, impact analysis, evidence like screenshots or tool output, and recommended fixes , and possibly additional sections like Methodology what tests were done, tools used, scope details , and Appendices raw scan data or detailed configurations if relevant . Good reports will prioritize findings critical, high, medium, low so you know where to focus first. They should be written clearly, avoiding excessive jargon, and should map issues to any relevant frameworks for example, OWASP Top 10 category for a web app issue, or CWE references, or compliance requirements . Some providers also include a management presentation or debrief meeting to walk through the report, which can be very helpful. In this list, companies like DeepStrike, NCC, Nettitude, etc., are all known for providing thorough and actionable reports. When scoping a project, you can ask for a sample redacted report to judge the quality. Beware of reports that are just scanner printouts you want human analysis. Also check if the provider offers free retesting of vulnerabilities after you fix them; many will issue an addendum confirming issues are resolved, which is useful for auditors or customers.
Security testing is not a one and done exercise. At minimum, an annual penetration test is recommended for most organizations on critical systems. However, the trend especially in 2025 is moving toward more frequent and continuous testing. Why? Because new threats emerge constantly and your IT environment changes with updates, new features, infrastructure changes, etc. Many companies do major tests annually and smaller check ups quarterly. For web applications that undergo frequent releases, some are integrating security testing into every release cycle; this could be lighter touch testing or automated scans with periodic deep dives . If you have a high threat profile, say you’re a fintech handling sensitive data , continuous testing via a PTaaS platform or recurring engagements might be warranted. Also consider event driven tests: e.g., after significant changes, launch of a new application, big network overhaul, cloud migration or after an incident to ensure similar attack paths are closed . From a compliance standpoint, standards like PCI DSS require at least annual tests and after major changes. Ultimately, the cadence should align with your risk tolerance rule of thumb: the more an asset is critical to your business and exposed to internet facing or mission critical internally , the more frequently it should be tested. All the companies listed here offer flexible engagement models, so you can set up a schedule and many will happily establish multi year testing roadmaps with you .
Having an internal security or IT team is fantastic, but an external perspective is still crucial. Internal teams can be great at day to day security and basic vulnerability scanning, but they might lack the attacker perspective that a specialized penetration tester has. There’s also the issue of objectivity: an external tester has no assumptions about how your systems should work and can often find issues that internal folks overlook due to familiarity or bias. Many organizations use a mix: internal teams do routine scans and fixes, and external experts are brought in for deeper testing or to audit the internal team’s effectiveness. Another model is to engage external testers to augment your internal team; for example, during a red team, your internal blue team defenders can practice detecting the external red team’s actions, a great training exercise. Using a top company from this list in collaboration with your team can elevate your program. Also, certifications and regulators sometimes explicitly require third party testing, so even the most advanced companies like Google, Amazon all have internal security but still hire external pentesters regularly to practice this. If you have specific knowledge internally, say you know your proprietary app inside out , you can help the external testers with that info to make tests more efficient. In short, internal and external efforts are complementary, not an either/or choice.
Generally, the role of a penetration testing firm is to identify and report vulnerabilities, not necessarily to fix them; fixing is typically done by your developers or IT staff. However, most of the providers in this list do offer guidance and support that can be considered part of remediation. For instance, they might conduct a walkthrough session with your team to ensure understanding of each issue and suggest how to fix it. Some have consulting services where they can be more hands-on: e.g., a firm like Bridewell or NCC might have separate consultancy units that can assist in redesigning a network segment or configuring a security control. A few, especially those that are also MSSPs or full service consultancies, may even implement solutions for example, configuring a Web Application Firewall to virtually patch a vulnerability until code is fixed . That said, be cautious: the testing team should remain somewhat independent to retest objectively after fixes. It’s often a good practice to have the testers perform a retest after your team does remediation and indeed most include one retest round free of charge. If you lack developer capacity, you might ask if the provider can do a secure code review to help patch the code, or if they have partners who do. So while they won’t usually just jump in and edit your code or reconfigure your firewall as part of the test, they won’t leave you hanging either. The goal is to improve security, and reputable firms are invested in that outcome. They will certainly point you clearly in the right direction for each finding, and some will even provide snippets of hardened configuration or pseudocode as examples for your team.
In today’s high stakes cyber landscape, choosing the right security partner can make all the difference between a resilient organization and one that’s caught off guard by threats. We’ve presented a range of top tier UK cybersecurity companies from agile boutiques to industry heavyweights each with proven strengths. This list has been compiled independently with a research driven approach and with the buyer’s perspective in mind. Our goal is to equip you with insight into what makes each provider unique and how they might align with your needs.
Remember that best is contextual: the best provider for a global bank will differ from that for a tech startup. Use the information and comparisons above to narrow down a shortlist, but also do your own due diligence. Request consultations, ask the tough questions about methodologies and deliverables, and evaluate cultural fit. A truly effective partnership will be one built on trust, clarity, and matched expectations.
We remain neutral and have no incentive to favor one over another ultimately, the right choice is the one that empowers you to strengthen your security posture confidently. By assessing your options carefully considering factors like those in our methodology , you’ll be well on your way to making an informed decision that bolsters your organization’s defense for 2025 and beyond.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us