September 15, 2025
Compare the top 7 Canadian penetration testing companies of 2025 DeepStrike, eSentire, Herjavec Group, Deloitte, and more. Learn costs, services, and how to choose the right partner.
Mohammed Khalil


Penetration testing companies in Canada specialize in ethical hacking services that simulate real attacks on your IT systems to find vulnerabilities. In other words, they hack you before the bad guys do,so you can fix weaknesses first.
In 2025, demand for these services is higher than ever. Why? Because cyber threats are constantly evolving, nearly 44% of Canadian organizations faced a cyber attack in the past 12 months, and one study found 73% of successful breaches are achieved via vulnerable web applications. High-profile incidents and costly data breaches the average breach in Canada costs CA$6.3 million underscore that even well-defended companies are at risk.
Penetration testing isn’t a nice-to-have. It's become essential for Canadian businesses to validate their security posture, meet standards like ISO 27001 and PCI DSS, and protect sensitive customer data from breaches.
If you’re researching the best pen testing companies in Canada, this guide has you covered. We’ll explain what penetration testing involves, why it matters for 2025 threats, how to choose a qualified vendor hint: look for top certifications and a manual approach, what a typical penetration testing engagement costs in Canada, and who the top providers are in the Canadian market.
By the end, you’ll know how to find the right partner to strengthen your defenses whether you’re a small startup or a large enterprise needing advanced security testing. For perspectives beyond Canada, see our reviews of the top rated penetration testing companies in the US and Penetration Testing Companies UK as well.
Let’s dive in!
Penetration testing or pentesting means hiring authorized ethical hackers to attack your systems under controlled conditions. The goal is to identify security weaknesses before malicious actors do.
A formal definition from NIST describes penetration testing as security testing in which evaluators mimic real-world attacks in an attempt to identify ways to circumvent the security features of an application, system, or network.
In practical terms, that means skilled testers use the same tools and techniques as cybercriminals to probe your defenses but with permission and for your benefit..
During a penetration test, the testers will try to exploit any vulnerability they can find: outdated software, misconfigured servers, weak passwords, missing patches, logical flaws in applications, you name it.
Unlike basic automated scanners or vulnerability assessment tools, a real pen test is highly manual and creative. Testers might chain together multiple low-risk vulnerabilities to achieve a full system compromise, mimicking the complex attack chains a real adversary would use.
For example, they might exploit a seemingly minor bug to perform an account takeover as seen in Real world account takeover case study or abuse misconfigured cloud endpoints for a server-side request forgery SSRF attack.
At the end of the engagement, the pentesters provide a detailed report showing how they broke in, what data they accessed, and clear remediation steps to fix the issues. The best providers will include both technical details for your IT teams and high-level summaries for executives.
Often, they’ll also hold a debrief session to walk through findings and answer questions. This ensures you’re not only discovering vulnerabilities but also learning how to fix root causes and strengthen your security processes.
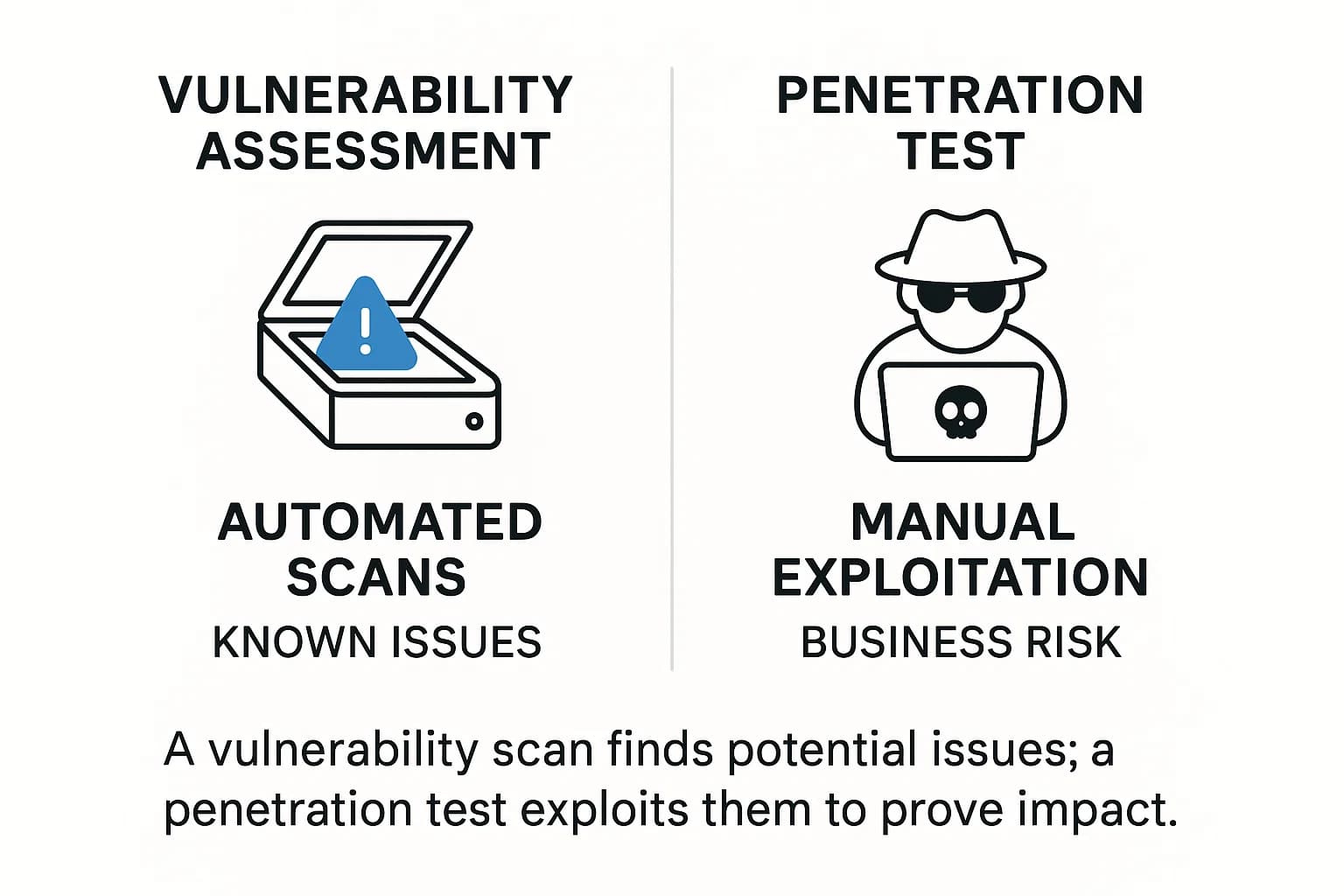
It’s worth noting the difference between a penetration test and a vulnerability assessment. A vulnerability scan is mostly automated and identifies known issues, whereas a pentest goes further by actively exploiting weaknesses to prove impact. Pentests are more thorough but also more resource-intensive.
Many companies use both vulnerability scans regularly, and penetration tests periodically for deeper assurance.
Not all penetration testing providers are created equal. Choosing a partner to trust with your security testing is a big decision. You need skilled testers who will do a thorough job, communicate well, and respect your systems.
No one wants a pentester accidentally crashing a production server with an uncoordinated scan!. Here are some key factors and tips for selecting the right penetration testing services provider in Canada:
1. Certifications and Accreditations: Look for industry-recognized qualifications that demonstrate expertise. In Canada, there isn’t a single mandatory accreditation for pentesting firms, but certifications are a strong indicator of skill.
Top companies will have team members certified as OSCP Offensive Security Certified Professional, OSWE Web Expert, CISSP, GIAC GPEN/GWAPT, or CEH, among others. Some firms are also accredited by bodies like CREST, a globally respected certification for pentesting quality or have PCI Qualified Security Assessors for compliance work.
In short, ask about the team’s credentials and reputable providers will be proud to share them. A strong certification roster signals that the testers have proven skills to tackle your engagement. For example, the NIST penetration testing framework SP 800-115 is often used as a guiding standard, so a provider familiar with NIST’s methodology is likely to be methodical and thorough.
2. Experience and Specialization: Consider the provider’s track record, especially in your industry or technology stack. If you’re a financial institution, you may prefer a company that has done extensive work in banking and understands regulations from the Office of the Superintendent of Financial Institutions OSFI.
Healthcare organizations might look for experience with privacy laws like PHIPA/PIPEDA. Likewise, if your environment is heavy on cloud and DevOps, lean toward a firm known for cloud security testing if you have IoT or OT operational tech, find a team with that niche expertise. Ask for case studies or client references in your sector. An established firm that has been around for years, like CGI or KPMG, has decades of history and brings a wealth of tested methodology.
Newer boutique firms might be more agile and creative. There’s a trade-off but either way, ensure they have first-hand experience with the types of threats and systems you’re most concerned about. For example, have they performed a red team engagement similar to what you need? Have they tested large-scale apps with millions of users? This can give insight into their capabilities.
3. Methodology and Scope Definition: A good penetration testing company will be very clear about how they scope and conduct the test. Be cautious of any vendor that gives you a quote without asking detailed scoping questions. Proper scoping number of apps, IPs, user roles, credentials provided, etc. is crucial to get a realistic quote and outcome.
If a vendor doesn’t inquire about your environment and just offers a one-size-fits-all package, that’s a red flag you might end up with a shallow test. Reputable providers will outline their methodology: typically steps like reconnaissance, vulnerability analysis, exploitation, post-exploitation, and reporting, often aligning with guidance from OWASP and NIST SP 800-115.
They should use a mix of automated tools and deep manual techniques to ensure nothing is missed. Don’t hesitate to ask what tools and techniques they use, or even request a sample report. A sample penetration testing report, even a sanitized one will show you the depth of findings and clarity of recommendations.
High-quality reports are comprehensive and actionable, not just scanner output. Also, check if they include a debrief and retesting support. The best companies will walk you through the findings and help verify that your fixes close the gaps. Some even offer free retests of vulnerabilities after you patch them, an important value-add.
4. Service Range and Support: Depending on your needs, you might prefer a provider that can be a one-stop shop for security services. Many penetration testing companies in Canada also offer related services like vulnerability assessments, continuous penetration testing on a subscription or Pentest-as-a-Service model, incident response, or security training.
If you foresee needing ongoing testing or multiple services, consider a firm that provides them so it can streamline things and ensure consistency. Additionally, check their availability and flexibility. Are they booking tests two months out common for in-demand firms or can they start next week if you’re on a tight timeline? Do they offer testing outside regular hours if you need off-hour testing to avoid disruption? Also, consider if you prefer a local presence.
Some Canadian companies have offices in Toronto, Montreal, Vancouver, etc., which can be handy for on-site testing or just peace of mind that they understand the local context Canadian privacy laws, bilingual reporting needs, etc.. That said, many excellent providers operate remotely across Canada in today’s world, you can hire a top firm from anywhere.
It often comes down to your comfort: some organizations feel more secure with a provider that’s Canada-based for data sovereignty or easier communication, while others don’t mind an international team as long as they deliver results.
5. Cost and Value: We’ll dive into penetration testing cost in Canada in the next section, but when choosing a vendor, it’s wise not to simply pick the cheapest quote. In cybersecurity, you often get what you pay for. Super-low quotes suspiciously cheaper than others could indicate the test will be mostly automated or that the provider lacks experience.
On the other hand, the most expensive quote isn’t always the best either, some might overscope or upsell unnecessary hours. The key is value: a thorough test that fits your budget and provides actionable results. When comparing proposals, look at how many days of testing are included, the team composition are senior consultants involved or just juniors?, and whether things like a follow-up retest are included.
A fair pricing model should align with the effort and expertise provided. Remember, a penetration test is an investment in preventing costly breaches, not just an expense. Spending $10k on a test may save you millions by avoiding a data breach or ransomware incident.
Many providers will work with you to prioritize critical targets if the budget is limited for example, testing your most exposed systems first. Also, consider building a long-term relationship. Some firms offer discounts or flexible pricing if you plan ongoing engagements e.g. multiple tests per year or a multi-year contract.
Quick Tip: Create a checklist when evaluating vendors. Include things like: Are they certified OSCP, CREST, etc.? How many years of experience? Will they show a sample report? Do they provide references? Is a free retest included? Is their methodology documented clearly? By asking similar questions to each provider, you can objectively compare them.
We even wrote a guide on questions to ask a penetration testing provider feel free to use it to grill prospective partners! And finally, trust your gut to an extent you’ll be working closely with this team, possibly under time pressure, so you want people who communicate clearly and professionally.
The pre-sales interactions can be telling if they’re responsive and thoughtful now, they’ll likely be great during the test. If they are slow to respond or push a cookie-cutter approach without listening, maybe not the best fit.

One of the first questions organizations ask is: How much does a penetration test cost in Canada? The answer is it depends primarily on scope and complexity but we can discuss typical pricing to give you a ballpark.
Pricing Models: Most penetration testing companies charge either a fixed fee per engagement or more commonly a daily rate for the testers’ time using a Time & Materials model. Some newer services use a subscription or PTaaS Penetration Testing as a Service model, where you pay a flat monthly/annual fee or buy testing credits for ongoing testing.
Each model has pros and cons: fixed-price offers budget predictability but can be inflexible if scope changes, whereas day-rate or T&M is flexible but can have budget uncertainty.
PTaaS subscriptions can be efficient for continuous testing needs, often integrating automated scanning + manual tests via an online dashboard studies show PTaaS can be 31% cheaper than traditional projects by streamlining workflows. The best approach depends on whether you need a one-time test or year-round assurance.
Typical Rates: In Canada, rates for a manual penetration test by a professional usually range roughly C$1,000 to $2,500 per day of testing, depending on the provider’s reputation and the expertise level required. An average thorough test by a certified consultant might be around $1,500/day.
Highly specialized testing or urgent projects could be above $2.5k/day, while bulk deals or smaller firms might be on the lower end. To illustrate, an engagement scoped at 5 days of work might cost on the order of $7,500 5 × $1.5k/day give or take.
Typical Total Costs: The total cost = day rate × number of days. How many days a test takes will depend on the scope. A small test, say a simple web application or a small office network might require 3–5 days of effort, translating to roughly $5,000 to $10,000 CAD as a rough estimate.
A larger test, such as a comprehensive assessment of multiple websites, a corporate network, and some cloud infrastructure for a mid-size company, could be 10–20 days of work, costing perhaps $20,000 to $40,000+. Very extensive engagements or full-scope red team simulations running over several weeks can run into the high tens of thousands e.g. $50k and up.
According to industry data, the average cost of a penetration test in Canada ranges from about $3,500 to $70,000 CAD depending on scope, a very wide range because every situation is different.
It helps to get quotes from a few reputable firms, but be sure they are quoting comparable scopes. One vendor might propose 5 days of testing while another recommends 10 days for the same assets if one quote is much lower, check if they underestimated the scope or plan to rely heavily on automation. Always clarify what’s included: number of targets, testing depth, and deliverables.
Factors Influencing Cost: Several variables drive the price of a pentest:
For example, a web application penetration testing engagement will scale with how many pages and features need to be tested. A small app might take 3 days a large, feature-rich app might take 15+ days.
A black-box test with no prior knowledge can take longer than a white box test with logins or source code provided because testers have to spend more time in discovery. Discuss these factors with providers to ensure you’re comparing apples to apples.
Compliance-focused tests can run on the higher side of estimates due to reporting overhead. For instance, PCI DSS tests often involve segmentation checks and formal attestation that may cost more than a standard test.
Sometimes a lower-cost boutique is a great value other times, too cheap could be risky. Never compromise quality for cost when it comes to security testing the stakes are simply too high.
Also remember the internal effort, your team will spend time coordinating the test and fixing issues afterwards these are hidden costs to factor in.
Ultimately, you should view penetration testing as an investment in risk reduction. Breaches are far more expensive than tests. According to IBM’s 2024 report, a single data breach in Canada now costs an average of $6.32 million. Compare that to a $20k pentest the return on investment is huge if a test prevents even one serious incident.
Or put another way, spending, say, $30,000 on a comprehensive test that helps you plug holes could save you hundreds of times that amount by averting a breach. As one cybersecurity expert put it, A penetration test might cost you five figures, but a breach could cost you seven. It's money well spent.”
If budget is a concern, start by testing your most critical systems, those facing the internet or holding sensitive data. Many providers will help tailor a scope to your risk priorities. Also, consider continuous testing or annual contracts some companies offer Pentest-as-a-Service platforms or ongoing testing bundles that reduce the per-test cost and keep your security posture in check year-round.
Cyber threats are not one-time events, so many Canadian businesses are shifting toward more frequent assessments instead of a single pentest once a year.
Remember: The goal is not to find the cheapest hacker-for-hire, but to find a trustworthy partner who will genuinely help improve your security. A good penetration test provides tangible value in peace of mind and breach prevention.
It’s often a requirement for things like cyber insurance insurers increasingly ask if you do regular pentests. And it’s an integral part of a mature security program.
Now that we’ve covered the why, what, and how much of pentesting, let’s look at who the top providers are in Canada.
Canada is home to a mix of boutique security firms and global companies offering penetration testing. Below we highlight seven of the top penetration testing service providers in Canada for 2025, based on industry reputation, expertise, and client feedback. Each of these companies has a strong track record in helping organizations identify and remediate vulnerabilities:




Of course, Canada has other reputable players in the pentesting space beyond these seven. Honorable mentions include firms like Packetlabs, Vumetric, Software Secured, CyberHunter, Calian, Control Gap, and others. When evaluating providers, always consider the specific expertise you need and the rapport you build during initial discussions.
How much does a penetration test cost in Canada?
The cost of a penetration test in Canada can vary widely depending on scope and provider. On average, a small test e.g. one web app or a basic network might cost around C$5,000 to $10,000, while a large-scale or comprehensive test could range from $20,000 up to $50,000 or more. Industry data shows typical Canadian pentest costs spanning C$3.5k to $70k in total. Hourly or daily rates usually fall in the $1,000–$2,000 per day range. Keep in mind that compliance-oriented tests for PCI, SOC 2, etc. may cost more due to extra reporting requirements. It’s best to get a custom quote the provider will assess your number of targets, complexity, and depth of testing needed. Don’t choose based on price alone a cheap quote might mean a shallow automated scan, whereas a proper manual pentest costs more but gives much more value. Tip: Ask if the quote includes a follow-up retest of fixes. Some companies include it free, others charge extra.
How often should we conduct penetration testing?
Best practice is to perform penetration testing at least annually. Many Canadian organizations do a full-scope pentest once per year as part of their security program or compliance requirements. However, more frequent testing is advisable if you have a high threat profile or frequent changes. For example, critical applications might be tested twice a year, and some companies adopt continuous penetration testing through a PTaaS platform for ongoing coverage. Also, you should do ad-hoc pentests after major system changes say you launched a new web portal or made significant infrastructure updates and after major incidents to validate that similar vulnerabilities are now fixed. Essentially, regular testing plus testing after changes is the way to go. Remember that new vulnerabilities are discovered all the time, so a system that was clean last year might have new flaws this year. Many standards, PCI DSS, etc. mandate at least annual tests and whenever significant changes occur. In 2025’s threat environment, a continuous testing approach can provide the greatest assurance, but if that’s not feasible, aim for annual and supplement with smaller targeted tests in between if possible.
What is the difference between penetration testing and vulnerability assessment?
A vulnerability assessment is an automated or semi-automated scan of your systems to identify known security issues, misconfigurations, missing patches, etc., usually using tools that compare your systems against vulnerability databases. It results in a list of potential vulnerabilities, often with severity ratings. A penetration test, on the other hand, goes a step or several steps further. It's a hands-on attempt to exploit vulnerabilities in your environment, carried out by skilled security professionals and ethical hackers. The pentesters validate which vulnerabilities are truly exploitable, often chain multiple findings together, and assess the impact by actually compromising systems in a safe manner. The outcome is a more actionable report showing exactly what an attacker could do in your environment. Think of a vulnerability scan as finding the doors and windows left open, whereas a pentest is actually breaking in through those openings to demonstrate the risk. Pentests require more expertise and effort, but yield far richer insights including false positive elimination and custom attack scenarios. In practice, organizations often use both: run frequent vulnerability scans which are cheaper and automated and schedule periodic penetration tests to simulate real attacks and catch what scanners miss.
Is penetration testing required for compliance e.g. PCI DSS, SOC 2, ISO 27001?
It depends on the framework, but penetration testing is either required or strongly recommended in most major security standards. For example, PCI DSS for payment card data explicitly requires penetration tests at least annually and after any significant changes to the cardholder environment Requirement 11.3. So if you process credit cards in Canada, you must do regular pentesting to stay PCI compliant. SOC 2 common for tech service companies doesn’t explicitly mandate pentests, but in practice, auditors and customers expect to see that you conduct them as part of showing a mature security program. It's often considered necessary evidence that your controls are working . ISO 27001 requires an information security risk management process, and pentesting is a recommended control to identify technical risks. NIST frameworks also endorse regular testing. Additionally, sectors like finance have regulator expectations: OSFI’s guidelines for banks include conducting independent testing of controls which can be fulfilled by pentests. Bottom line: If you have to meet any security compliance or certification, penetration testing is either explicitly required or will greatly help satisfy the requirements. It demonstrates due diligence. Be sure to use a reputable firm and document the results for your auditors.
Do small businesses in Canada need penetration testing?
Yes small businesses can benefit from penetration testing, and arguably need it as much as large ones. There’s a myth that attackers only go after big companies, but in reality 73% of small businesses have experienced a cybersecurity incident in recent years. Cyber criminals often view small and mid-sized SMBs as softer targets with weaker security. A penetration test can help a small business uncover hidden vulnerabilities like an exposed database or weak admin credentials before a hacker finds them. It’s true that budget is a concern, but there are affordable options some firms offer scaled-down tests or SMB packages. Even a focused test on your primary web app or network perimeter is far better than nothing. Pentesting for small businesses is also increasingly requested by partners or cyber insurance providers. You might need a security assessment to win a client contract or to get insured. So, while the scope might be smaller, small businesses absolutely should do pentesting to protect their assets and reputation. Think of it as an investment to avoid catastrophic damage. A single breach can be fatal for a small company.
What is PTaaS Penetration Testing as a Service?
PTaaS is a modern delivery model for penetration testing where services are provided on a continuous or on-demand basis via a platform. Instead of a one-time test with PDF report, PTaaS typically involves a subscription to a cloud-based platform where you can request tests, see results in real-time, and collaborate with the pentesters. It combines automated vulnerability scanning with manual expert testing in a streamlined way. The idea is to integrate with agile development and DevOps cycles, providing more frequent testing feedback. PTaaS platforms often offer dashboards, integration with issue trackers like JIRA, and retesting at the click of a button. This can significantly reduce the turnaround time for finding and fixing vulnerabilities. For example, DeepStrike and some others in Canada provide continuous pentesting services where you get incremental results as they test, rather than waiting weeks for a final report. PTaaS is ideal for companies that deploy new features often or want to shift left by catching security issues during development. It can also be cost-effective compared to purchasing separate one-off tests; some studies suggest PTaaS can be 30% cheaper over time. Essentially, PTaaS turns pentesting into a more collaborative, ongoing process rather than a once-a-year project. If your organization is looking for continuous assurance, it’s worth exploring PTaaS offerings.
What’s the difference between black box, grey box, and white box penetration testing?
These terms refer to the level of knowledge and access given to the pentesters:
Good providers will discuss which model fits your goals. Also, note that internal vs external pentest is different from black/grey/white box internal vs external refers to testing from inside your network vs outside on the internet. Black/grey/white refers to knowledge given. You could have a black-box external test, or a grey-box internal test, etc.
Cyber threats in 2025 demand more than just reactive defenses they require proactive testing and continuous vigilance. By now, you should have a clear understanding of why penetration testing is so critical for Canadian businesses and how to go about choosing the right provider. We’ve also spotlighted some of the top penetration testing companies in Canada, any of which could be a valuable partner in strengthening your security posture. The key is to pick a team that understands your needs, has the expertise to find the hard-to-detect vulnerabilities, and will work with you to remediate and improve.
In summary, regular penetration testing whether through one-off engagements or a continuous PTaaS model is one of the best investments you can make to protect your organization’s data, reputation, and customers. The threats are real, but with the right preparation and the right people on your side, you can stay one step ahead of cyber attackers.
Ready to Strengthen Your Defenses?

The threats of 2025 demand more than just awareness they require action and readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of seasoned practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in and help you stay one step ahead of cyber threats.
About the Author
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us