September 9, 2025
Updated: September 9, 2025
A deep dive into the rise of SIM swap scams, $26M in U.S. losses, and why UK cases surged 1,055% in 2024.
Mohammed Khalil

A sim swap scam also known as SIM hijacking or a port-out scam is an account takeover attack where a criminal hijacks your phone number. They don’t need to hack your phone; they simply convince your mobile carrier like Verizon, T-Mobile, or AT&T to transfer your service to a SIM card they control. This gives them the master key to your digital life: your text messages.
This isn't a minor threat. In 2024 alone, The FBI's Internet Crime Complaint Center (IC3) tracked $25,983,946 in reported losses from SIM swapping in the U.S.. Globally, the trend is even more alarming.
The UK's fraud prevention service, Cifas, reported a mind-boggling 1,055% increase in unauthorized SIM swaps, with nearly 3,000 cases filed in 2024 compared to just 289 the year before.
We've hit a perfect storm. The widespread availability of personal data from countless data breaches provides the fuel for attackers. Our collective reliance on insecure SMS for two-factor authentication creates the vulnerability. And the rise of easily transferable digital assets, especially cryptocurrency, provides a massive financial incentive for these attacks.
The data paints a clear picture of a rapidly escalating global threat. While headlines often focus on complex malware or zero-day exploits, SIM swapping demonstrates that sometimes the most devastating attacks exploit the simplest weaknesses.
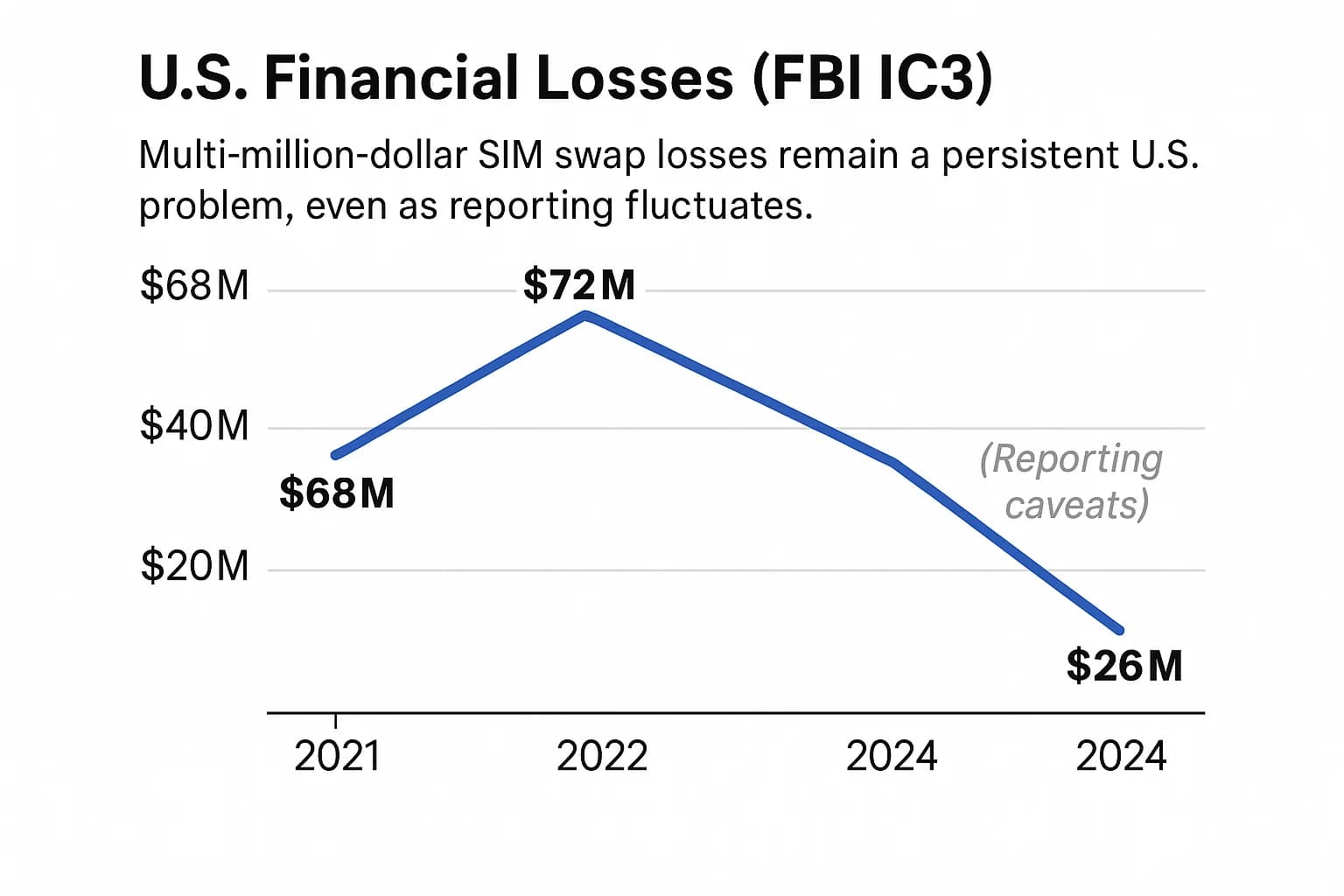
The FBI's 2024 IC3 report provides the clearest financial snapshot in the U.S., citing 982 complaints that led to nearly $26 million in losses. This figure continues a dangerous trend observed over the past several years, building on the $72 million reported in 2022 and $68 million in 2021.
While the dollar amount reported for 2024 is lower than in 2022, this can be misleading. It may reflect changes in victim reporting habits or a shift in attack focus rather than a genuine decrease in the threat level. The core takeaway is that multi-million-dollar losses from this attack vector are a consistent and persistent problem.
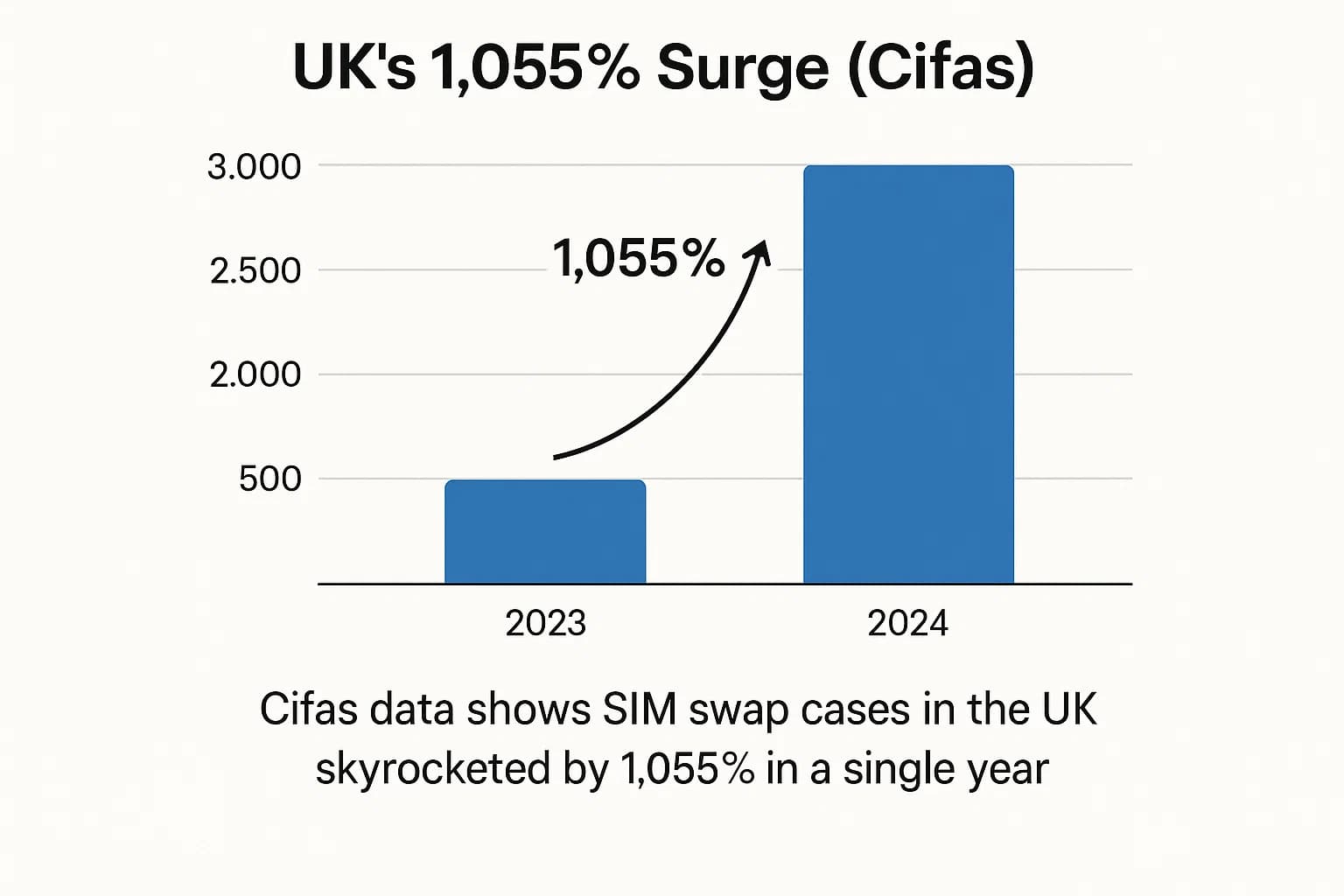
Perhaps the most shocking statistic comes from the UK's Cifas, which recorded a 1,055% surge in SIM swap cases in 2024. This highlights a crucial point: while the FBI tracks direct financial loss, the sheer volume of these attacks is exploding on a global scale.
The Cifas report reveals that telecoms have become a primary target for criminals. Facility takeovers (where an attacker seizes control of an existing account) jumped 76%, and 48% of all account takeovers in 2024 involved mobile phone accounts.
This data signals a clear tactical shift by criminal organizations toward weaponizing phone numbers as the entry point for broader fraud schemes.
The discrepancy between the FBI's reported financial losses in the U.S. and the massive surge in incident volume reported by Cifas in the UK is significant.
It suggests that the true scale of the problem is likely better represented by the growth in activity. Financial loss data is often subject to underreporting by victims who may feel embarrassed or believe the funds are unrecoverable.
The explosive growth in the number of attacks is a more direct indicator of how prevalent and successful this criminal tactic has become.
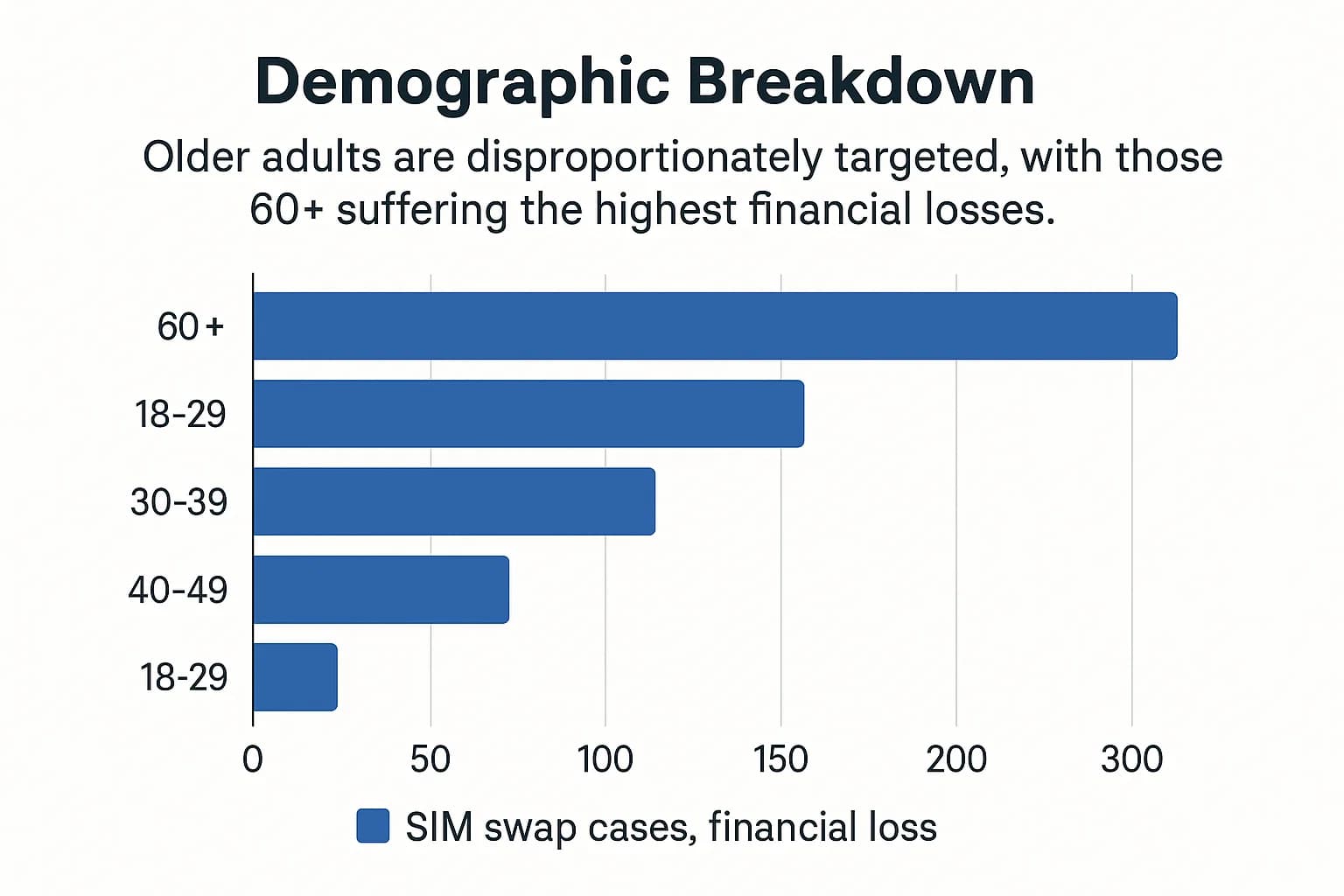
The data reveals a painful trend: older adults are disproportionately affected by SIM swapping. According to the FBI's 2024 data, victims aged 60 and over suffered the highest financial losses, totaling $6.3 million.
This trend is mirrored in the UK. Cifas data shows that individuals aged 61 and over now account for 29% of all account takeover victims, representing a 90% year-on-year increase for that demographic. This vulnerability may stem from a higher likelihood of using SMS-based 2FA and being more susceptible to the social engineering tactics that underpin these attacks.
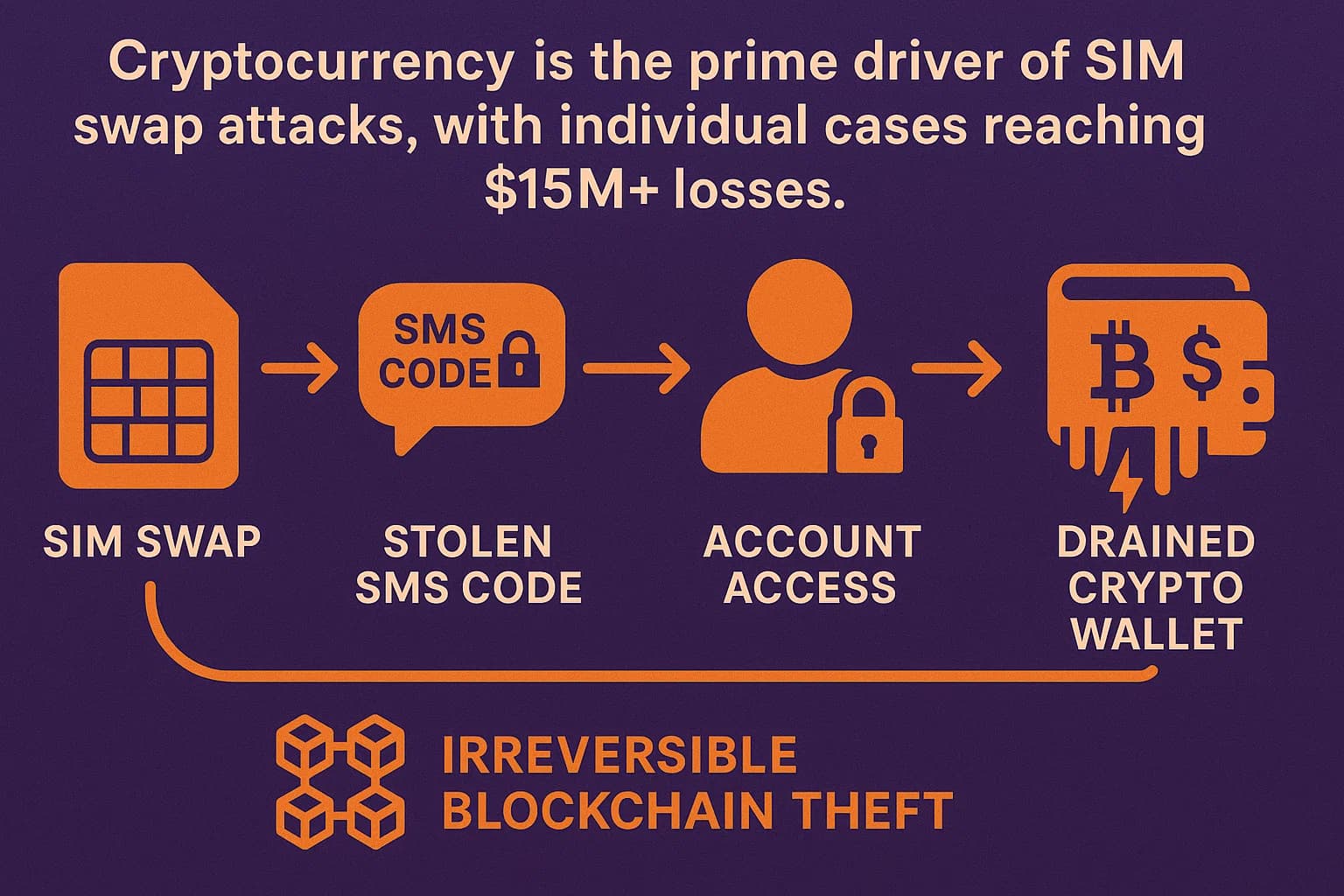
Cryptocurrency is a primary driver of SIM swapping's profitability. The irreversible and pseudonymous nature of blockchain transactions makes it a perfect target for thieves, as stolen funds are nearly impossible to recover.
The FBI's 2024 IC3 report shows that crimes with a cryptocurrency nexus accounted for a staggering $9.3 billion in losses across all categories, with SIM swapping being a key enabler for these thefts. For crypto SIM swap losses specifically, the total was reported at $28.4 million.
High-profile cases underscore the immense risk. In a landmark decision in March 2025, T-Mobile was ordered to pay $33 million in an arbitration case after a single SIM swap allowed thieves to drain a customer's cryptocurrency wallet.
One cybersecurity expert noted seeing as much as $15 million to $20 million stolen in a single swap from crypto accounts, highlighting the catastrophic potential of a single security lapse.
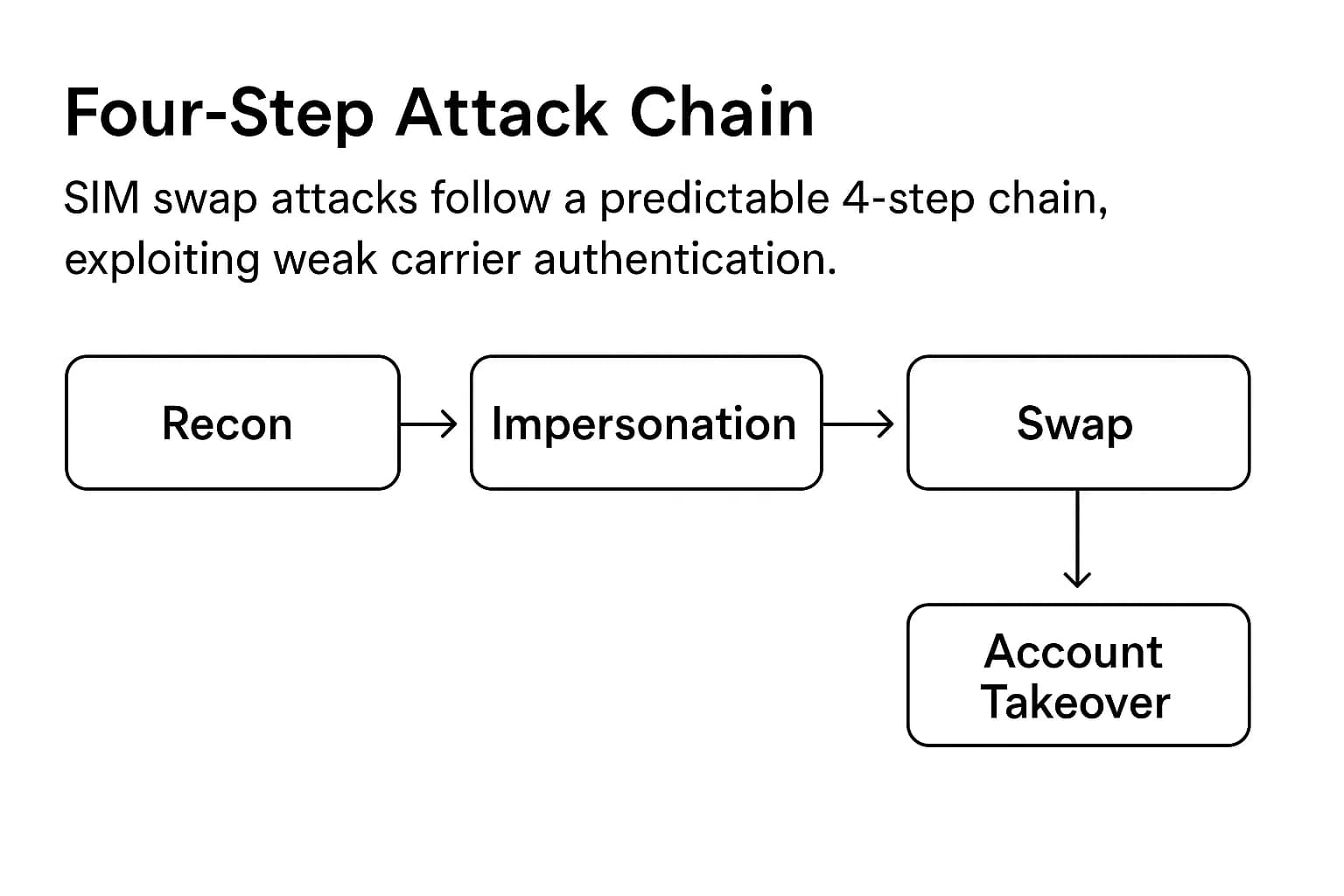
The crucial thing to understand is that SIM swapping is not about malware or hacking your device's encryption. It is a social engineering attack that targets the weakest link in the security chain: the customer service representatives at mobile carriers.
In fact, research shows that 96% of SIM swap cases involve social engineering or insider collusion, not a sophisticated technical exploit.
The attack follows a predictable and effective pattern:
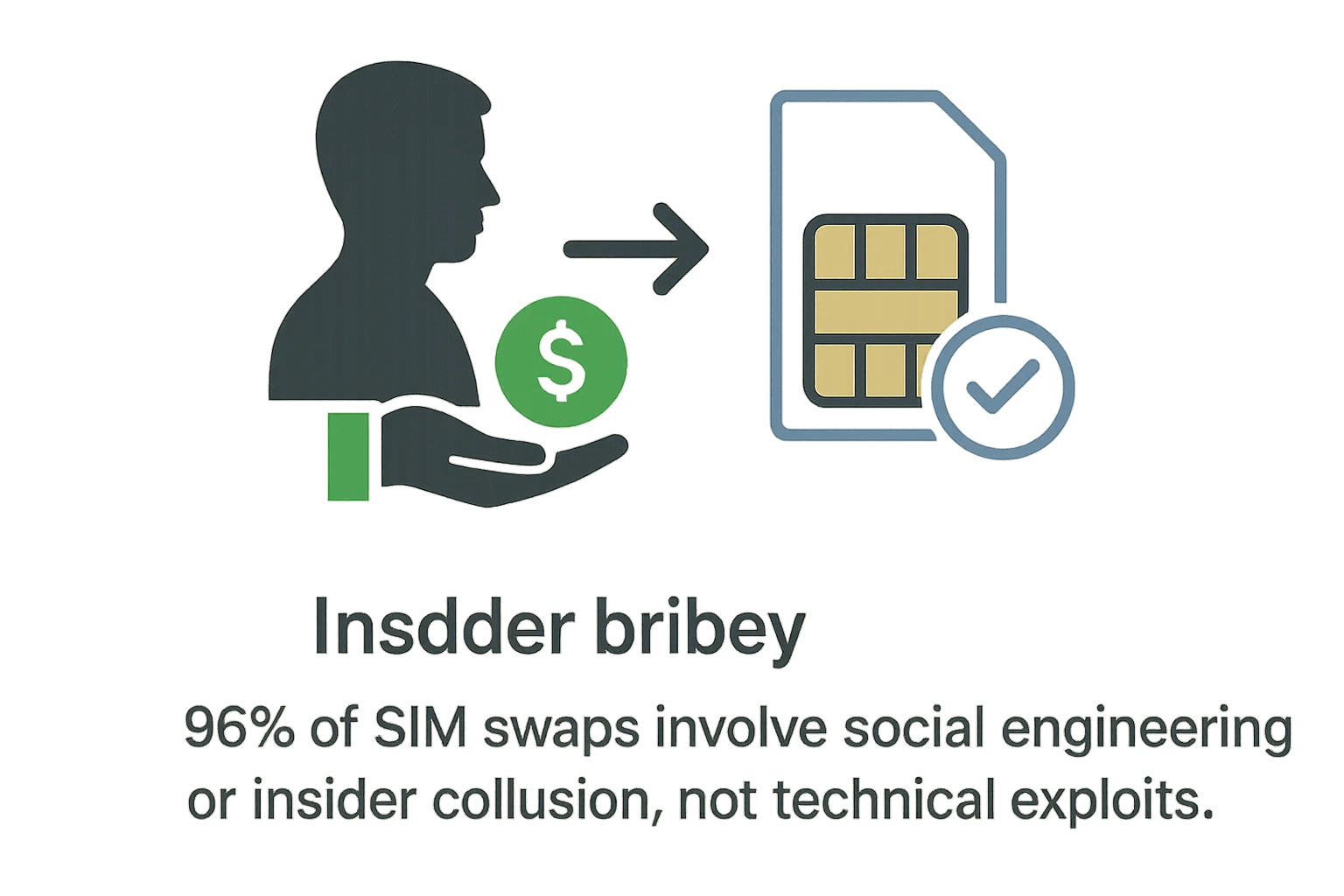
A more sinister and highly effective method involves bribing carrier employees directly. This form of insider collusion is a growing problem. Investigations have revealed that attackers openly offer telecom staff $300 per fraudulent swap to bypass all security protocols entirely.
This "insider-as-a-service" model makes many consumer-facing security measures, like an account PIN, potentially useless if a compromised employee has the authority to override them. These insider threats statistics show a growing trend across all industries.
The proliferation of SIM swapping is a direct consequence of systemic security failures within the telecommunications industry. In response, regulators are finally starting to intervene, but progress has been slow.
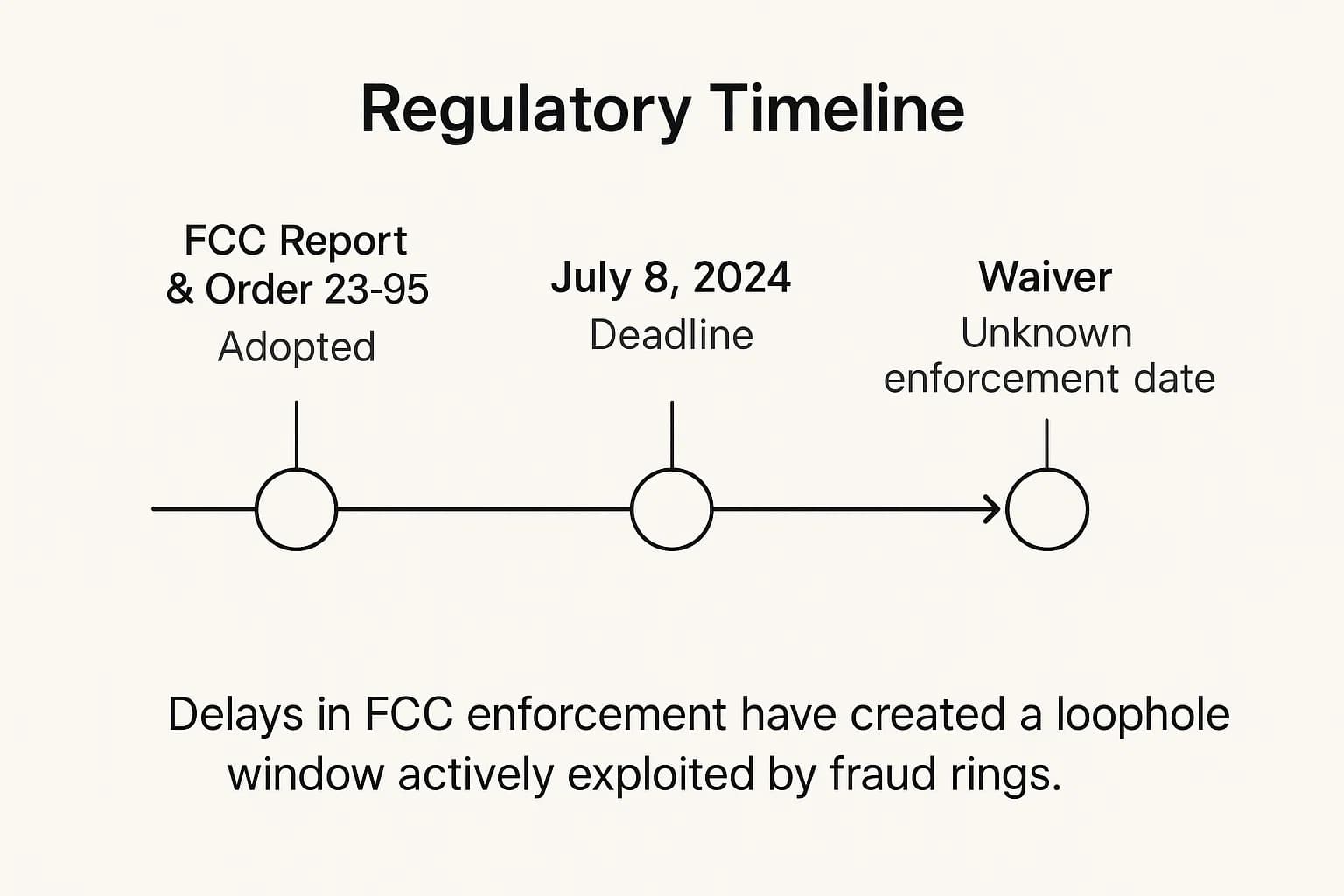
Recognizing this systemic failure, the U.S. Federal Communications Commission (FCC) adopted new rules (FCC Report & Order 23-95) in late 2023 to compel carriers to improve their security measures.
The new rules mandate that wireless providers must:
The original compliance date for these critical rules was July 8, 2024. However, after telecommunication companies requested more time to upgrade their systems and train employees, the FCC waived the deadline for all rules adopted in FCC 23-95, with no new enforcement date yet announced.
This regulatory delay is more than just a procedural issue; it is an active security vulnerability. The period between the announcement of new security rules and their enforcement creates a publicly known "loophole window" that fraud rings are actively exploiting.
Criminals are aware that these mandatory protections are coming and are racing to capitalize on the current weaknesses before carriers are forced to fix them. This highlights a critical disconnect between the speed of regulation and the speed of cybercrime, where delays in protection are functionally equivalent to enabling attacks.
Even without the FCC mandate, the major carriers have rolled out voluntary protection features. You must enable these manually, as they are not turned on by default.
For Verizon Customers: Enable Number Lock & SIM Protection
For T-Mobile Customers: Enable Account Takeover Protection
For AT&T Customers: Enable Wireless Account Lock
Hardening your mobile account is the first step, but the most critical change you can make is to stop relying on SMS for security.
SMS-based 2FA was designed to prove you have your phone. A SIM swap attack breaks this model entirely because the attacker, not you, now has your "phone" from the network's perspective.
Any service that relies on sending a code to your number for login or password reset is vulnerable. This fundamental weakness is a key reason why password security statistics show stubbornly high rates of account takeover, even with 2FA adoption.
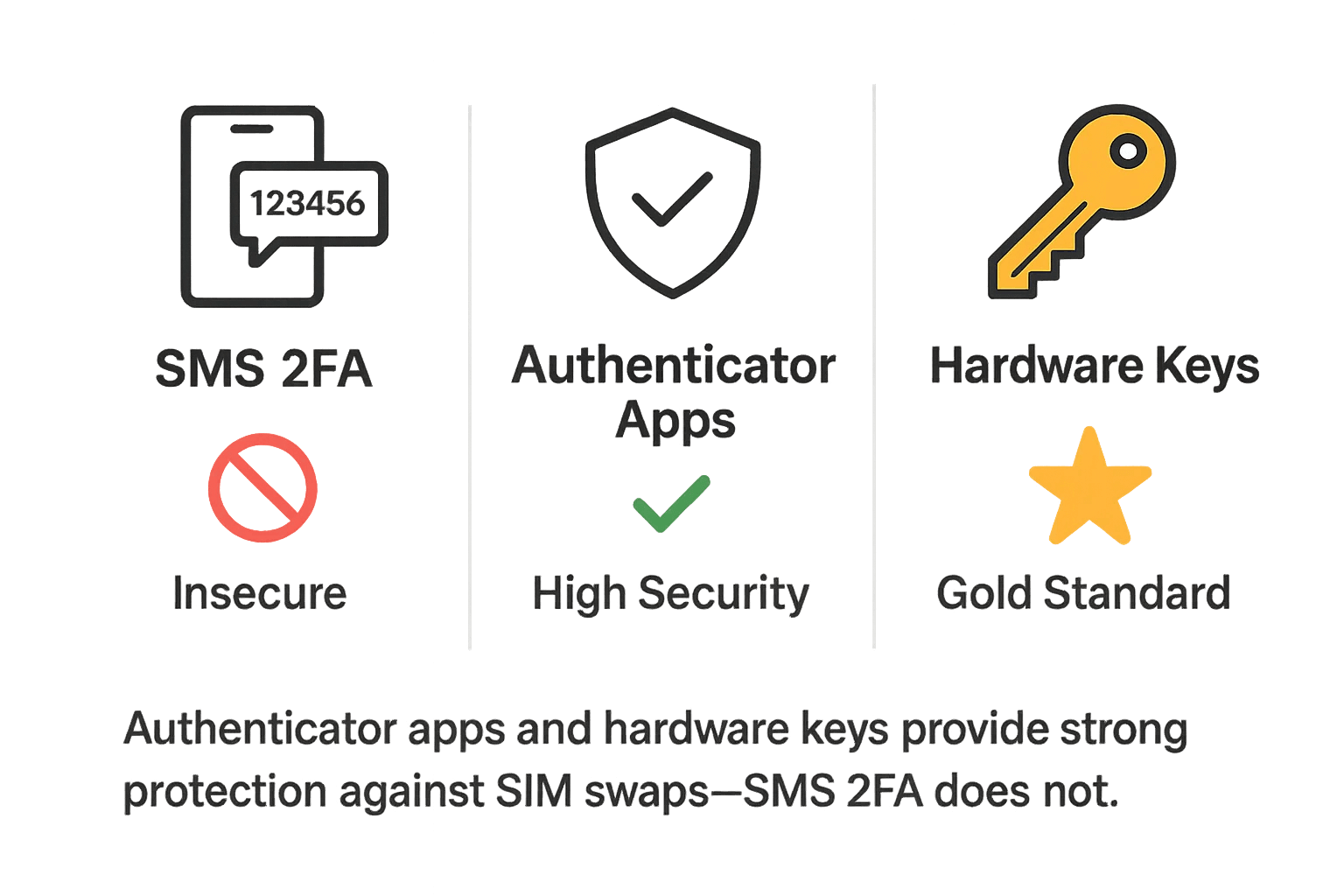
Here’s how the alternatives stack up against SIM swap attacks. This aligns with guidance from the National Institute of Standards and Technology (NIST SP 800-63), which has formally downgraded SMS as a viable authenticator for high-assurance scenarios, a position reinforced by security frameworks like the OWASP Authentication Cheat Sheet.
Method 1: SMS / Text Message 2FA
Method 2: Authenticator Apps (e.g., Google Authenticator, Authy)
Method 3: Hardware Security Keys (e.g., YubiKey, Google Titan Key) & FIDO2 Passkeys
Many believe eSIMs are inherently safer against SIM swapping. Because they are embedded directly into your device's hardware, they can't be physically removed and stolen if your phone is lost. This provides a clear advantage against physical theft.
However, this misses the point of a remote SIM swap attack. This attack relies on socially engineering a carrier employee, not on stealing the physical card. An attacker can convince a carrier to provision a new eSIM profile on their own device just as easily as they can activate a new physical SIM, a form of eSIM provisioning fraud.
The Verdict: An eSIM is physically more secure, but it does not inherently protect you from a remote SIM swap attack. The vulnerability lies with the carrier's human and procedural authentication process, not the form factor of the SIM.

If your phone suddenly shows "No Service," you must act immediately. You are in a race against the attacker to contain the damage.
What’s the fastest way to stop an active SIM swap?
The first and most critical step is to immediately call your mobile carrier's fraud department from a different phone. Explain that you are the victim of an unauthorized SIM swap and demand they deactivate the fraudulent SIM card and restore service to your device. This cuts off the attacker's access to your calls and texts.
Is eSIM actually safer than a physical SIM against SIM swapping?
Physically, yes. An eSIM is embedded in your device and can't be stolen like a physical card. However, for remote attacks where a scammer tricks your carrier, an eSIM offers no extra protection. The vulnerability is the carrier's authentication process, not the type of SIM.
Which 2FA method is safest against SIM swaps?
The safest methods are hardware security keys (like YubiKey) and FIDO2 passkeys, as they are immune to both SIM swapping and phishing. The next best option is an authenticator app (like Google Authenticator). The least secure method is SMS-based 2FA, which you should avoid for all important accounts.
Can I sue my carrier after a SIM swap?
Yes, and victims are increasingly successful. A landmark arbitration case in March 2025 ordered T-Mobile to pay $33 million to a customer who lost cryptocurrency after a SIM swap, setting a powerful precedent for carrier liability and negligence.
How do I lock my number with Verizon, T-Mobile, or AT&T?
All three major carriers offer free security features you must enable manually. For Verizon, it's "Number Lock" and "SIM Protection" in the My Verizon app. For T-Mobile, it's "Port Out Protection" and "SIM Protection" on their website or app. For AT&T, it's "Wireless Account Lock" in the myAT&T app.
How can a business create a corporate SIM swap prevention policy?
A strong corporate policy should include a checklist of mandatory controls:
The statistics are clear: SIM swapping is an industrialized, high-growth crime that weaponizes the weakest link in our security chain human trust. It thrives on our collective over-reliance on the fundamentally insecure SMS protocol for identity verification. As the data shows, the financial and personal devastation from a successful attack can be life-altering.
But you are not powerless. By hardening your mobile carrier account, systematically migrating your critical accounts to stronger forms of authentication, and practicing good digital hygiene, you can significantly reduce your risk and build a resilient defense against this pervasive threat.
Ready to Strengthen Your Defenses?

The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us