November 23, 2025
Updated: November 23, 2025
Understanding DORA’s mandatory penetration testing and threat-led TLPT rules.
Mohammed Khalil

The Digital Operational Resilience Act DORA EU Regulation 2022/2554 took effect on January 17, 2025. In simple terms, DORA forces banks, insurers, payment firms, crypto providers, and other financial institutions to prove they can survive serious cyberattacks. That means hacking yourself on a schedule set by regulators. Specifically, all in scope firms must run robust penetration tests authorized attacks on their own systems as part of their resilience programs. For the most critical entities, DORA even mandates Threat-Led Penetration Testing TLPT a full scale, intelligence driven red team exercise. In this article, we explain what DORA penetration testing is, why it matters today, how TLPT under DORA differs from regular testing and from the ECB’s voluntary TIBER EU framework, and practical tips for compliance.

Under DORA, penetration testing becomes a legal requirement, not just a best practice. Essentially, any financial institution within DORA’s scope must maintain an ICT resilience testing program. This means regularly finding and fixing security holes before attackers do. The tests must cover all systems that support critical or important functions a DORA defined term. A penetration test or pen test is a controlled simulated cyberattack on an organization’s computer systems, applications or network to uncover vulnerabilities. If you’re new to this, see our guide What is Penetration Testing? for an overview. For DORA compliance, the stakes are higher: regulators expect financial firms to apply multiple test methods, vulnerability scans, code reviews, network tests, etc. on a risk based schedule, then promptly remediate any findings. In practice, this means annual testing of key applications and infrastructure.
Crucially, DORA introduces Threat-Led Penetration Testing TLPT as an advanced option for top tier firms. TLPT is like a realistic red teaming exercise: experts use the latest threat intelligence to mimic the tactics of real cybercriminals or nation state hackers against live production systems. Unlike a one off automated scan, a TLPT is a multi week campaign involving reconnaissance, simulated attacks, and even a purple team debrief where attackers and defenders collaborate to learn lessons. The goal is to test not just technical controls but the firm’s entire ability to detect, respond, and recover under fire. In short, DORA’s definition of penetration testing now ranges from standard app/network pentests to these full scale TLPT scenarios.

Cyber threats against financial institutions are intensifying. Ransomware, supply chain attacks, and sophisticated data breaches can shake market confidence and disrupt economies. Regulators realized that simply holding capital reserves traditional risk buffers isn’t enough. DORA closes a gap: it forces firms to prove they can fend off and survive cyber incidents.
For 2025 and beyond, this is urgent. Recent surveys show industry is reacting: one report found 92% of CISOs increased their overall security budgets in 2023, and 85% upped their annual pentesting spend. That trend reflects regulators’ push: DORA means yes, hacking yourself is mandatory. Penetration tests and especially TLPT are now not optional best practices but legal obligations.
Meeting these mandates is not just red tape, it delivers real benefits. A thorough DORA aligned pentest uncovers hidden weaknesses in systems handling transactions or customer data, so you can fix them proactively. It boosts customer confidence, as you can demonstrate you are finding and fixing issues on an ongoing basis in fact, proof of regular testing may be requested by cyber insurers. It also satisfies upcoming audits: many firms will need to show regulators test records, reports, and remediation logs.
Global cybersecurity spending is surging. Gartner forecasted that companies will spend $188.3B on risk & security in 2023 an 11.3% increase year over year. Within that, penetration testing budgets are especially growing: security leaders know it’s impossible to fix blind spots without proactive testing. Under DORA, this trend is set in stone for the EU financial sector. For readers curious about the overall security landscape, see our article on top cybersecurity statistics. The bottom line: for 2025, neglecting pentesting isn’t an option if you want to stay in business or avoid fines.
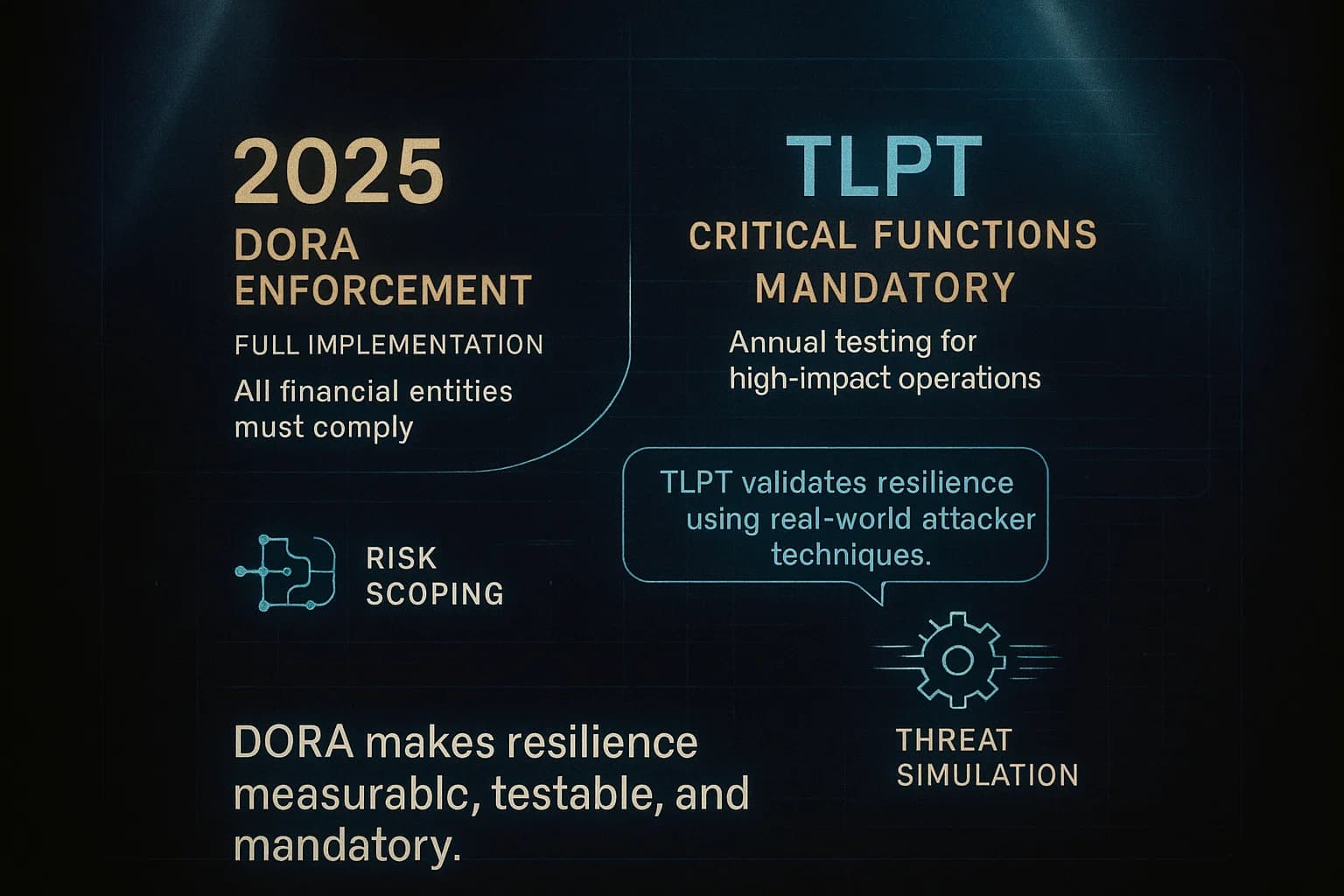
DORA defines a two tier testing regime:
In short, all DORA firms do regular annual tests, the big ones also do intense red team TLPT triennially. Think of basic pentesting vs TLPT like routine checkups vs a full body stress test. Table 1 below compares their key features:
| Feature | Threat-Led Penetration Test DORA TLPT | Traditional Penetration Test |
|---|---|---|
| Scope | Critical functions on live production systems incl. 3rd party providers. | Specific applications/networks, often lower risk or dev systems. |
| Frequency | At least once every 3 years or per regulator. | Risk based, often annual or per release. No strict cycle mandated. |
| Team | External qualified Red Team + Threat Intel internal only allowed rarely, with approval. Must use a Control Team for oversight. | Can be internal or external teams doing focused tests e.g., app pentest, network pentest. |
| Methodology | Full red team engagement: reconnaissance, stealth exploitation, with threat intelligence scenarios. Mandatory purple teaming debrief. | Usually limited duration attacks on known vulnerabilities, no mandated threat intelligence or purple teaming. |
| Objectives | Simulate a real attacker end to end: penetrate deeper, exfiltrate data, disrupt critical ops. | Find known vulnerabilities SQLi, XSS, misconfigs. Less emphasis on stealth persistence. |
| Reporting | Formal multi phase reports to both firm and regulator. Must include root causes, impact, and mandatory fix plans. | Detailed technical report for IT, often without third party oversight. |
The distinctions above highlight why TLPT is considered more rigorous. It borrows the established TIBER EU framework, updated under DORA. In fact, the EU’s ECB has aligned TIBER EU with DORA requirements, so doing a DORA TLPT using the TIBER methodology will generally check all the compliance boxes.
TLPT = advanced, intelligence driven red teaming on steroids. For more on differences between TLPT and a routine test, see our comparison Penetration Testing Methodology guide.
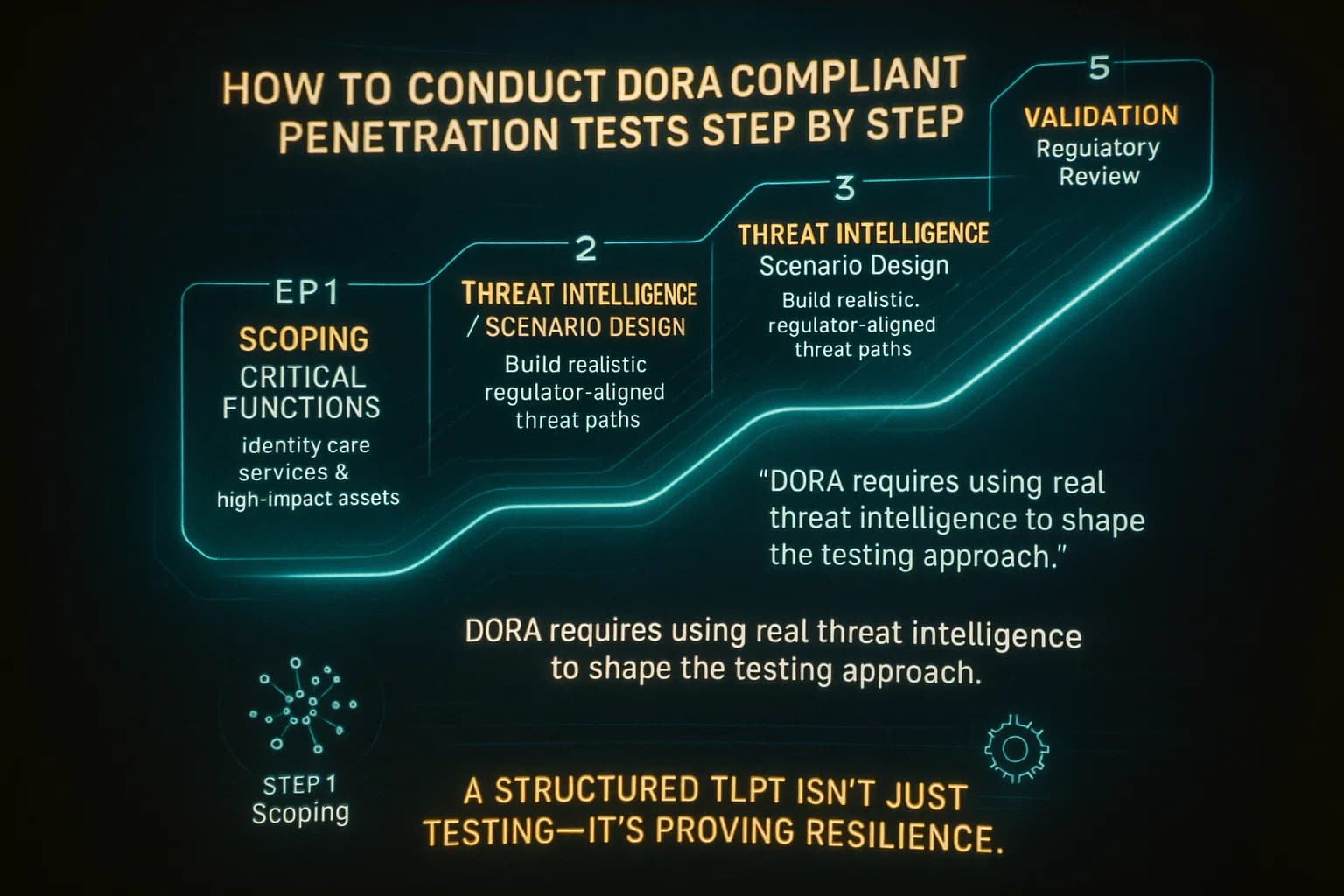
Here’s a practical checklist for firms under DORA:
Throughout this process, keep internal teams informed sans spoilers and document everything. Use tools or platforms if you have them some organizations use a continuous testing framework or a continuous penetration testing platform to track and automate parts of this cycle. And always align with recognized standards: following TIBER EU protocols ensures you cover DORA’s criteria.
Don’t treat DORA tests like checkboxes. For example, performing a quick scan and claiming we did a pentest won’t cut it. It’s not just about ticking the annual box, you need quality and follow through. Don’t ignore non technical controls either incident response processes and staff readiness count as part of resilience. And crucially, avoid using the same internal team without oversight. Regulators expect an objective third party at least periodically to validate your work.
DORA represents a paradigm shift: penetration testing is no longer optional in EU finance, it’s mandatory. Financial firms must build a continuous testing culture from automated vulnerability checks to full scale threat led war games to meet DORA’s requirements. Those who do will not only stay in the regulator’s good graces, but significantly beef up their cyber defenses. Ready to strengthen your defenses? The threats of 2025 demand action. If you need to validate your security posture, uncover hidden risks in your critical systems, or simply ensure compliance, DeepStrike can help. Our team of expert practitioners provides clear, actionable guidance to protect your business.
Explore our Penetration Testing Services to see how we can uncover vulnerabilities before attackers do. Drop us a line,we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
It’s the EU mandated requirement for financial firms to run structured cybersecurity tests. This includes routine vulnerability scans and pen tests each year, plus advanced red team exercises TLPT for critical institutions. The goal is to prove the firm can withstand serious cyberattacks under DORA rules.
DORA specifies categories of large or systemically important entities, big banks, insurers, trading venues, etc.. If your regulator identifies you as in scope for TLPT, you have to run a threat led red team test at least once every 3 years. Smaller firms still must do basic pen testing annually but aren’t required to do TLPT unless designated. Micro enterprises very small firms are largely exempt.
TLPT is more intense and realistic. A typical pentest might be a 1- 2 week test of one app or network segment. A DORA TLPT lasts 3 months, targets the firm’s crown jewels e.g. payment engines, uses real attacker TTPs, and includes mandatory purple teaming at the end. Also, TLPT results are reported to regulators, whereas regular pentest reports normally stay internal.
DORA allows internal testers, but only if they’re truly independent, not maintaining those systems and have regulator approval. Even then, one in three TLPT rounds must be done by an external provider for quality control. In practice, using a certified external red team e.g. CREST certified is the safer choice.
For general pentesting, at least once per year for each critical system. For TLPT if applicable, at least once every 3 years. Remember, additional testing is recommended after major changes or incidents.
Regulators can impose fines, force remediation, or take corrective actions. Since DORA is already in effect, supervisory exams will check testing records. Non compliance is now considered a serious breach of duty in most EU countries.
Look for experience in financial cyber resilience and DORA/TIBER frameworks. CREST accreditation or OSCP/OSWE certifications are good signs. Ensure the firm offers the required TLPT components: threat intelligence, red teaming, purple teaming, and solid remediation reporting. See our Penetration Testing Services for how DeepStrike approaches DORA TLPT.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us