November 2, 2025
Updated: November 2, 2025
Under the updated FTC Safeguards Rule, financial institutions must perform annual penetration tests and semiannual vulnerability scans. Learn how GLBA testing works, who it applies to, and how to stay compliant.
Mohammed Khalil

Penetration testing under GLBA is no longer optional. It’s a compliance requirement and a proactive defense measure that helps financial firms find and fix hidden vulnerabilities before real attackers do.

GLBA the Gramm Leach Bliley Act mandates security programs for financial institutions that handle customer data. Its Safeguards Rule 16 CFR 314 requires firms to regularly test or otherwise monitor the effectiveness of the safeguards protecting nonpublic personal information NPI. In other words, penetration testing for GLBA means hiring qualified security testers to simulate attacks on any system that stores, processes, or transmits customer information.
A GLBA penetration test looks at an organization’s entire information system with the goal of exploiting vulnerabilities just as a real attacker would. This can include network infrastructure, cloud services, web/mobile applications, and even employees via phishing or onsite attempts. The difference vs a simple scan is that pentesters validate exploitability and impact showing exactly how an attacker could breach safeguards. The results feed into compliance reporting and drive remediation of risks.
Why focus on GLBA now? In 2023, the FTC’s amended Safeguards Rule took effect, making pentesting a clear mandate for covered entities. Before June 2023, some firms treated pentesting as optional or best practice. Today, regulators expect documented annual pen tests or continuous monitoring plus semiannual vulnerability scans. Ignoring this requirement invites enforcement fines and breaches of trust.

Financial cyberthreats are surging. The average cost of a data breach now exceeds $10M and ransomware payouts average $2M. Banks, credit unions, insurance firms and even auto dealers who finance vehicles hold rich troves of PII and are prime targets. For example, 43% of cyberattacks hit small/medium businesses, a fast growing GLBA segment. In this landscape, GLBA pentests give organizations critical fire drills proving that security controls, firewalls, MFA, encryption, etc. actually work.
Regulators agree. The updated Safeguards Rule explicitly ties compliance to testing: Institutions must conduct annual penetration testing, and vulnerability assessments… at least every six months if they lack real time monitoring. The NCUA for credit unions likewise says to regularly test the key controls, systems and procedures of the information security program, ideally by independent testers. Even FFIEC banking guidance notes penetration tests covering network, client side, web application, and social engineering should be conducted at a frequency driven by risk.
In short, GLBA pentesting now equals both regulatory insurance and real security benefit. It helps institutions: uncover unknown flaws, validate defenses, network segmentation, least privilege controls, incident response, and document to examiners that they take cybersecurity seriously.

Under 16 CFR 314.4d of the Safeguards Rule, covered firms must have a security program and regularly test… safeguards. Critically, the rule states: if the firm cannot continuously monitor threats, then it must do:
The FTC’s official guidance to auto dealers which parallels any financial firm’s obligations spells this out plainly: If you cannot continuously monitor, then you must conduct annual penetration testing and vulnerability assessments at least every six months. This matches exactly the language of the Safeguards Rule and its Preamble.
It’s worth noting who has to comply: financial institutions under GLBA is broadly defined. Beyond banks and credit unions, it includes mortgage lenders, insurers, auto financers, CPA firms, and others significantly engaged in financial activities. So many small lenders and fintech startups fall under GLBA’s scope too. Any entity covered by FTC or state banking regulators must expect examiners to check for a documented pen testing regimen.
Other U.S. regulators echo this. The Federal Financial Institutions Examination Council FFIEC handbook recommends risk based pentesting of external and internal networks, web apps, and even phishing. NCUA Appendix A directs credit unions to regularly test security controls, preferably via independent parties. Collectively, these guidelines make it clear: a risk driven program of penetration testing and remediation is required to satisfy GLBA’s technical safeguard mandates.

In practice, a GLBA aligned penetration test is comprehensive. Typical scoping covers:
The tester typically chooses an approach black box, grey box, or white box per rules of engagement. In black box tests, attackers have no prior system knowledge, yielding realistic outside-in insight. Grey box gives minimal credentials or design docs, while white box gives full source code/access for maximum coverage. Often, a mix is used: GLBA guidance doesn’t forbid social testing, so many firms include phishing or insider simulation to test training and response.
Importantly, GLBA pentests must protect customer data. Trusted testers operate under strict NDAs and rules: they never actually steal or expose real NPI. Instead, they use dummy credentials or synthetic test accounts. For example, during an app test they might use encrypted test data instead of real SSNs. Detailed rules of engagement clarify that any discovered data must be handled securely and deleted after testing. This ensures GLBA’s encryption and disposal safeguards are respected even during the assessment.

Organizations should approach GLBA testing methodically:
Throughout, maintain records. GLBA audits will want to see policies e.g. a formal pentesting policy, scope documents, the RoE, the test report, and evidence of remediation. This paper trail is as important as the technical findings in satisfying compliance.
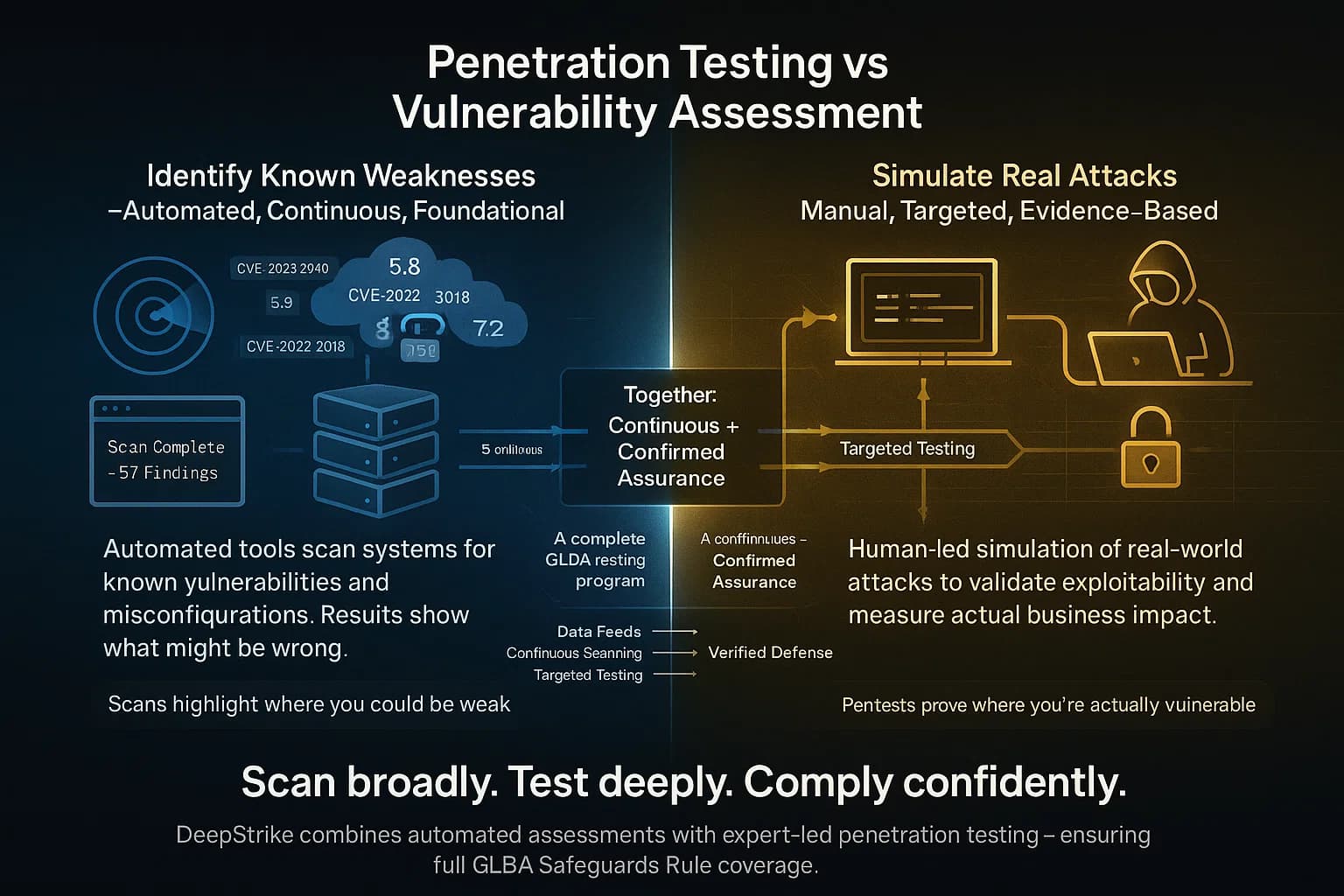
A common point of confusion is the difference between penetration testing and vulnerability assessment scanning. Under GLBA, both are required, but they serve distinct roles:
In short, scanning finds lots of potential issues; penetration testing shows which ones really matter. GLBA mandates both: semi annual scans vulnerability assessments and an annual pentest. Regulators expect the two to be part of a layered approach scans for broad hygiene, pentests for proof of exploit.
| Vendor | Key Services & GLBA Relevance |
|---|---|
| DeepStrike | Cloud based PTaaS with fully manual pentesting, continuous assessments, and real time dashboards. Offers integrations ticketing, CI/CD and unlimited retesting after fixes. Reports meet standards SOC 2, ISO 27001, HIPAA, etc., which align with GLBA’s data security goals. Tailors engagements for finance, insurance, credit unions and explicitly addresses frameworks like GLBA/FFIEC in its analysis. |
| Raxis | Specialist in financial sector pentesting. Follows NIST SP 800 115 methodology and emphasizes compliance readiness. Raxis notes that the GLBA Safeguards Rule makes annual pentesting and semi-annual vulnerability assessments a requirement. Their Continuous Penetration Testing and Red Team services are designed to meet these mandates, with detailed auditor friendly reports that map directly to GLBA requirements. |
| NetSPI | Enterprise grade PTaaS platform trusted by 90% of top U.S. banks. NetSPI combines a large team of 350+ security experts with AI driven workflows. It highlights its comprehensive PTaaS that produces regulatory ready documentation and expert validated findings with low false positives. In finance, NetSPI focuses on validating controls to meet PCI, SOX, GLBA, etc., delivering end to end campaigns, network, apps, social and strategic remediation guidance. |
| Praetorian | Offers a Continuous Offensive Security COS service: an ongoing penetration testing and red teaming platform. Praetorian notes that COS which includes manual pentesting satisfies compliance annual penetration testing requirements for frameworks like GLBA. It uses AI assisted reporting and an integrated approach pentests + attack surface management for continuous coverage aligning with GLBA’s emphasis on perpetual testing. |
| Coalfire | Large security and compliance firm with specialized services for financial clients. Coalfire supports GLBA as one of 80+ frameworks. While it isn’t purely a pentest vendor, its cybersecurity teams conduct GLBA aligned assessments, often as part of broader compliance engagements. Coalfire’s value is in deep regulatory expertise SOC audits, FedRAMP, etc. combined with pentesting to fulfill GLBA exam requirements. |
Other vendors: Crowdsourced PTaaS companies Synack, Bugcrowd and mainstream security firms Rapid7, Qualysec, Deloitte also offer GLBA aware pentesting. Firms typically choose providers based on industry experience, report quality, and ability to demonstrate compliance to regulators.

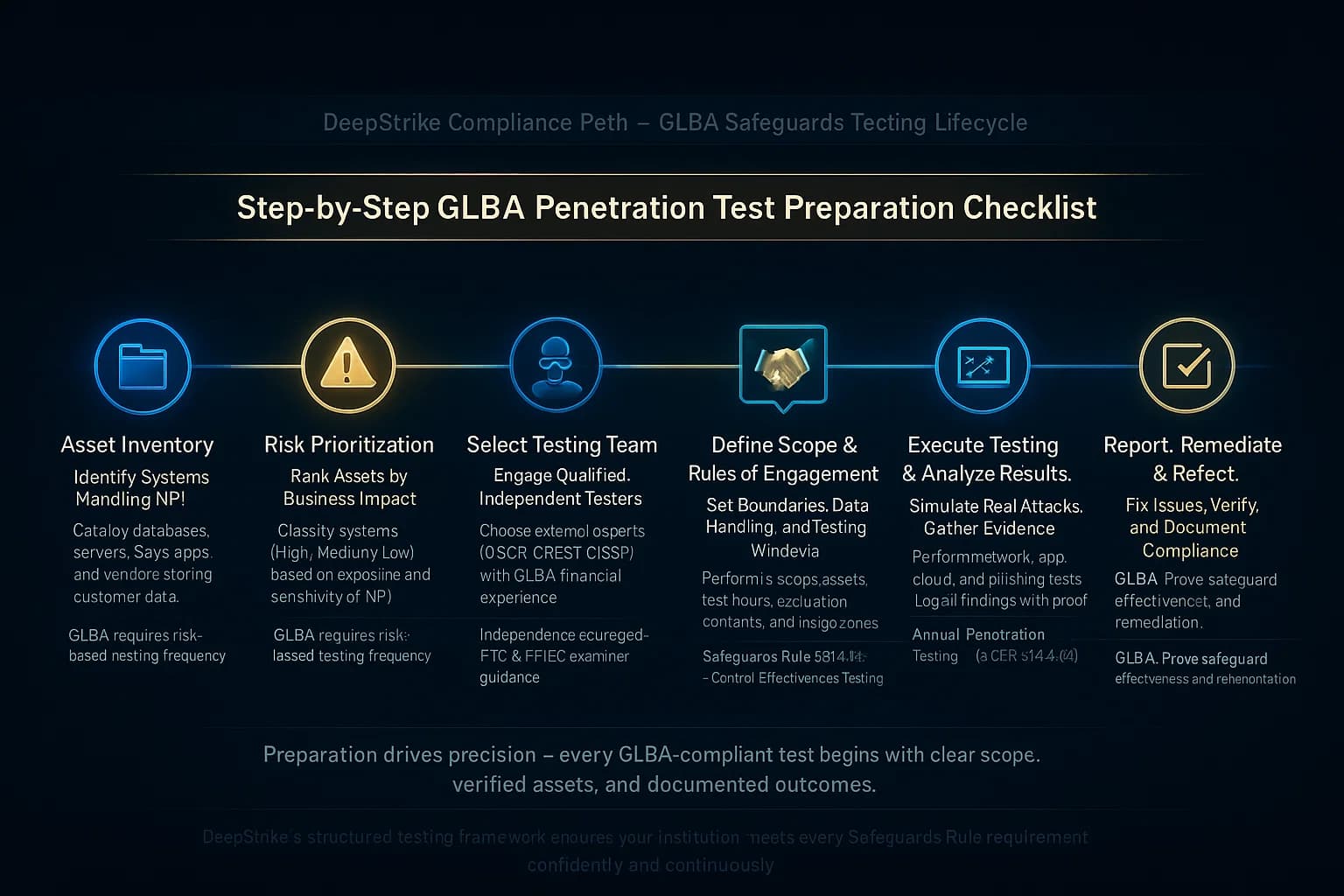
By following these steps, an organization can confidently meet GLBA’s requirements and greatly strengthen its security posture.
| Aspect | Vulnerability Assessment Scanning | Penetration Test |
|---|---|---|
| Goal | Identify all known weaknesses quickly broad scan | Exploit vulnerabilities to validate real risk in depth |
| Frequency | GLBA: ≥ every 6 months or continuous scanning | GLBA: ≥ annually or continuous monitoring |
| Tools | Automated scanners Nessus, Qualys, OpenVAS | Combination of tools and manual techniques Metasploit, Burp, custom exploits |
| Coverage | Checks CVEs and config issues across many assets | Targets high risk assets internal/external with manual methods |
| Outcome | Report of potential vulnerabilities CVSS scores | Proof of exploit PoC and business impact demonstration |
| Compliance Role | Satisfies GLBA’s semiannual assessment requirement | Satisfies GLBA’s annual pentest requirement |
Together, both activities form a complete security testing program. The assessment keeps you informed of known issues; the penetration test proves whether those issues can really be used by hackers to harm your data and operations.
GLBA penetration testing is now a compliance mandate and a security imperative for financial institutions. By rigorously testing every system that holds customer data, organizations not only check the GLBA box but also uncover and fix real world risks. A risk based pentesting program ideally via an experienced PTaaS provider provides documented proof of security effectiveness and actionable findings to improve defenses.
Ready to Strengthen Your Defenses? The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services to see how we can uncover vulnerabilities before attackers do. Drop us a line we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
Under 16 CFR 314.4, GLBA requires covered institutions to annually penetration test systems that handle customer NPI, and also to perform vulnerability assessments scans at least every six months. If the organization already has an effective continuous monitoring system, some flexibility exists, but otherwise annual tests are mandatory. The tests must be risk based focus on critical systems and documented. Regulators expect tests of both external and internal networks, applications, and even social engineering as appropriate.
Any business classed as a financial institution under GLBA not just banks. This includes credit unions, insurers, mortgage lenders, auto finance companies, brokers, even some retailers offering financing. Essentially, if your company is in the business of lending or financing and handles customer financial info, you fall under GLBA. The Safeguards Rule is enforced by the FTC and state regulators for most non bank institutions, and by banking regulators FFIEC, OCC, etc. for banks. In all cases, these entities must follow the penetration testing requirements.
GLBA’s focus is on protecting customer financial information. PCI DSS specifically covers payment card data, and HIPAA covers health data. However, the technical approach penetration testing of networks and apps is very similar. The difference is largely in scope and drivers: GLBA mandates pentesting of systems with customer NPI annually, whereas PCI requires annual network and application pentests for cardholder data environments, and HIPAA requires a risk analysis pen tests are highly encouraged but not always explicitly mandated. Many firms combine these audits. For example, DeepStrike’s reports cite SOC 2, ISO 27001, HIPAA, PCI and GLBA alike.
GLBA strongly implies testing by qualified, independent parties. PCI DSS explicitly requires qualified external testers. For GLBA, while the rule doesn’t forbid in house testing, examiners expect independence. A house pen test may be scrutinized for bias. It’s best to hire or partner with experienced external pentesters or a PTaaS vendor. Their fresh perspective often finds issues that internal teams overlook. After the test, your internal team can handle remediation with guidance from the report.
Costs vary widely by scope and vendor. A small fintech might spend a few thousand dollars per year for basic external and web app tests, while a large bank could spend tens or even hundreds of thousands for comprehensive assessments network, cloud, apps, internal staff tests and continuous monitoring. As a rule of thumb, penetration testing budgets are often in the 0.10.5% range of IT spend. The return on investment is significant considering the potential multi million dollar fines or losses from breaches. For detailed pricing, many firms offer guides or calculators see DeepStrike’s Pricing or industry RFP templates for benchmarks.
An external pentest simulates an attacker from outside your perimeter e.g. over the internet. It targets firewalls, VPNs, public web apps, and cloud interfaces. An internal pentest assumes an attacker is already inside e.g. a disgruntled employee or a compromised device. It focuses on internal networks, servers, and user privileges. GLBA guidance and FFIEC expect both perspectives. An outside attacker might be stopped by your edge defenses, but an insider with domain access could wreak havoc if controls are weak. So financial institutions typically conduct both external and internal tests as part of their GLBA compliance program.
Though GLBA itself doesn’t prescribe methodology, integrating pentesting into DevOps DevSecOps is increasingly popular for fast moving firms. For example, a continuous pentesting platform can automatically test code deployments see our Penetration Testing for DevOps guide. This ensures that any change to production is evaluated for security. It also helps satisfy GLBA’s risk based requirement by giving higher frequency of tests to rapidly changing systems. Continuous testing doesn’t eliminate the need for a formal annual audit, but it strengthens ongoing compliance.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us