September 2, 2025
Updated: September 2, 2025
A practitioner’s blueprint for mastering SOC 2, ISO 27001, HIPAA, PCI DSS, and the Shared Responsibility Model powered by Zero Trust, CSPM/CNAPP, and audit-ready pentesting.
Mohammed Khalil

Let's get one thing straight: cloud security compliance is the essential practice of ensuring your cloud infrastructure, applications, and data adhere to a complex web of industry and government regulations. Think of it as the rulebook for operating securely in the cloud.
For years, many saw compliance as a grudge purchase a box to check for the auditors. That mindset is now a direct threat to your business. The move to the cloud is complete, but the consequences of getting security wrong are escalating at an alarming rate. Consider this: 82% of data breaches now involve data stored in the cloud. IBM's latest report pegs the average cost of a data breach at an all time high of $4.88 million, and that number jumps significantly when compliance failures are involved. Projections from Cybersecurity Ventures estimate the global cost of cybercrime will hit a staggering $10.5 trillion annually by 2025.
This guide isn't just theory. It's a practitioner's blueprint, drawing on real world experience from the trenches of red team engagements and security architecture. We'll help you navigate the complexities of compliance, avoid the common pitfalls that lead to breaches, and turn your compliance program from a cost center into a powerful competitive advantage.
The most immediate driver for compliance is avoiding the eye watering penalties for failure. The cost of non compliance isn't just a hypothetical risk; it's a well documented financial drain that shows up in regulatory fines, legal fees, and breach remediation costs.
For instance, under GDPR, organizations can be fined up to 4% of their annual global turnover, a potentially business ending figure. In the U.S., the SEC levied $8.2 billion in financial remedies in FY2024 alone, with hundreds of millions in penalties for recordkeeping failures. The average cost of a data breach for organizations with high levels of compliance failures is millions more than for those with mature programs. These aren't just numbers on a page; they represent real financial and reputational damage that can erode shareholder value by 30% or more post violation.
Here’s the big shift: compliance is no longer just a defensive play. It's one of the most powerful offensive tools in your sales arsenal. For any B2B SaaS company today, a SOC 2 penetration testing requirements report is table stakes. It’s the ticket to the game. Without it, you can't even get a seat at the table with most enterprise customers.
Achieving certifications like SOC 2 or ISO 27001 provides verifiable, third party assurance that you are a responsible and secure partner. This de-risks the procurement process for your clients, shortens sales cycles, and unlocks access to highly regulated and lucrative markets like finance and healthcare. In fact, 73% of business leaders agree that meeting compliance standards improves the public perception of their business. This transforms compliance from a reactive, cost centric activity into a proactive, revenue enabling investment.
Compliance frameworks provide a structured, battle tested methodology for improving your overall security. Adhering to standards like the NIST Cybersecurity Framework (CSF) forces a rigorous and systematic approach to risk management. The process requires you to:
By following this structured approach, you inherently improve your data security and privacy practices, safeguarding sensitive information from unauthorized access and breaches.
In the past, security and finance teams often operated in silos. Security would implement necessary controls, and finance would get a surprise on the next cloud bill. This is no longer sustainable. Compliance requirements, especially around logging and monitoring, can generate massive amounts of data, leading to spiraling storage and processing costs.
This is where FinOps for security compliance comes in. FinOps is a cultural practice that brings financial accountability to the variable spend model of the cloud, creating collaboration between engineering, finance, and security teams. By applying a FinOps lens, you can analyze the cost of compliance controls and make data driven decisions. For example, you can optimize log retention policies to meet compliance needs without paying for unnecessary storage or choose more cost effective security tools that provide the same level of protection. This approach ensures your compliance program is not only effective but also financially sustainable.
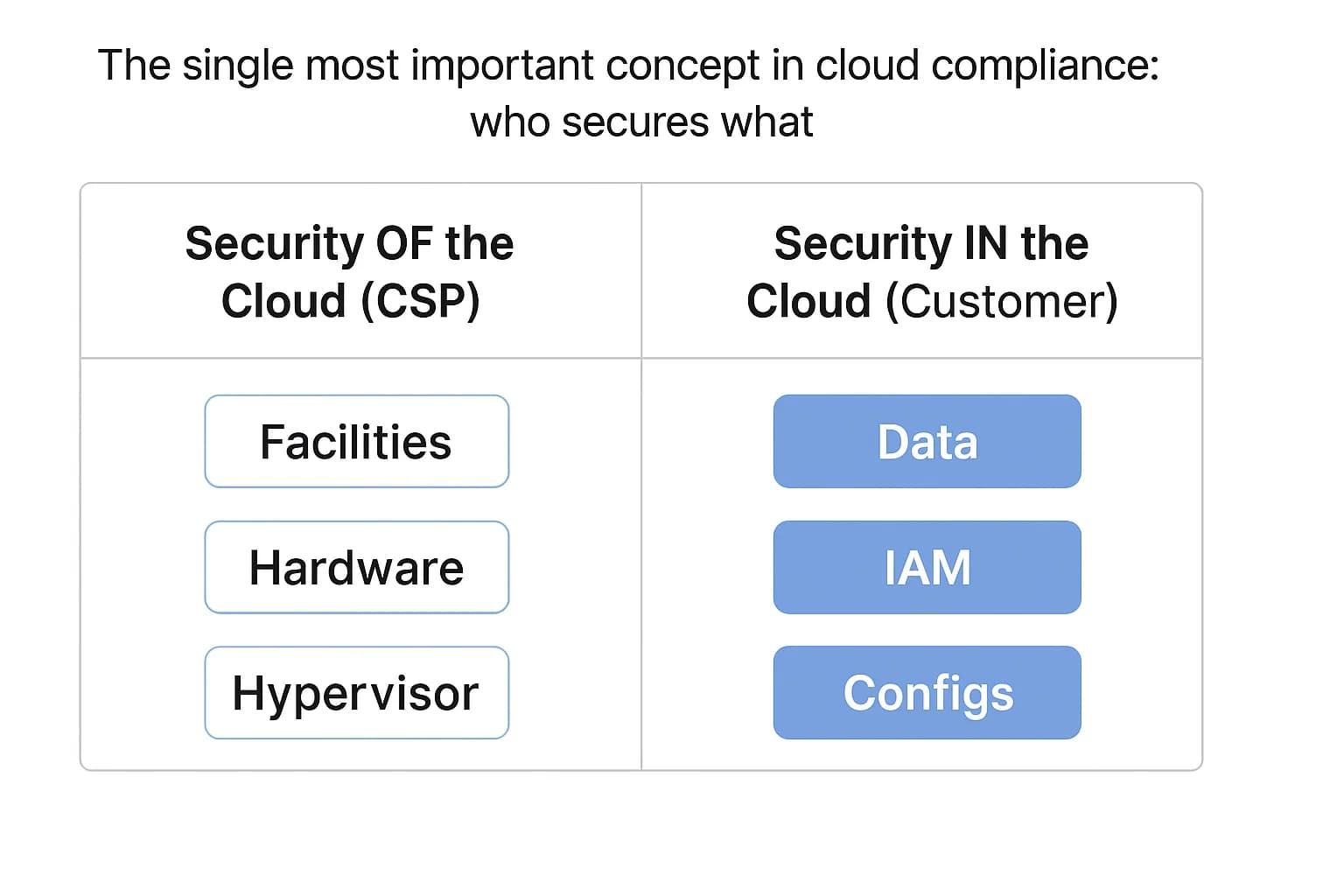
If there is one concept you must master in cloud security, it’s the Shared Responsibility Model. It's foundational, yet it remains the source of the most common and damaging cloud security failures. Gartner has consistently predicted that through 2025, 99% of cloud security failures will be the customer's fault. This isn't because cloud providers are perfect; it's because customers fundamentally misunderstand where their responsibility begins and ends.
At its core, the model is a framework that clearly delineates security obligations between the Cloud Service Provider (CSP) and you, the customer.
A simple analogy helps: The CSP provides a secure apartment building with a strong front door, security cameras in the lobby, and fire suppression systems. However, you are still responsible for locking your own apartment door, not leaving your windows open, and not giving your keys to strangers. If someone walks in through your unlocked door and steals your laptop, you can't blame the building manager.
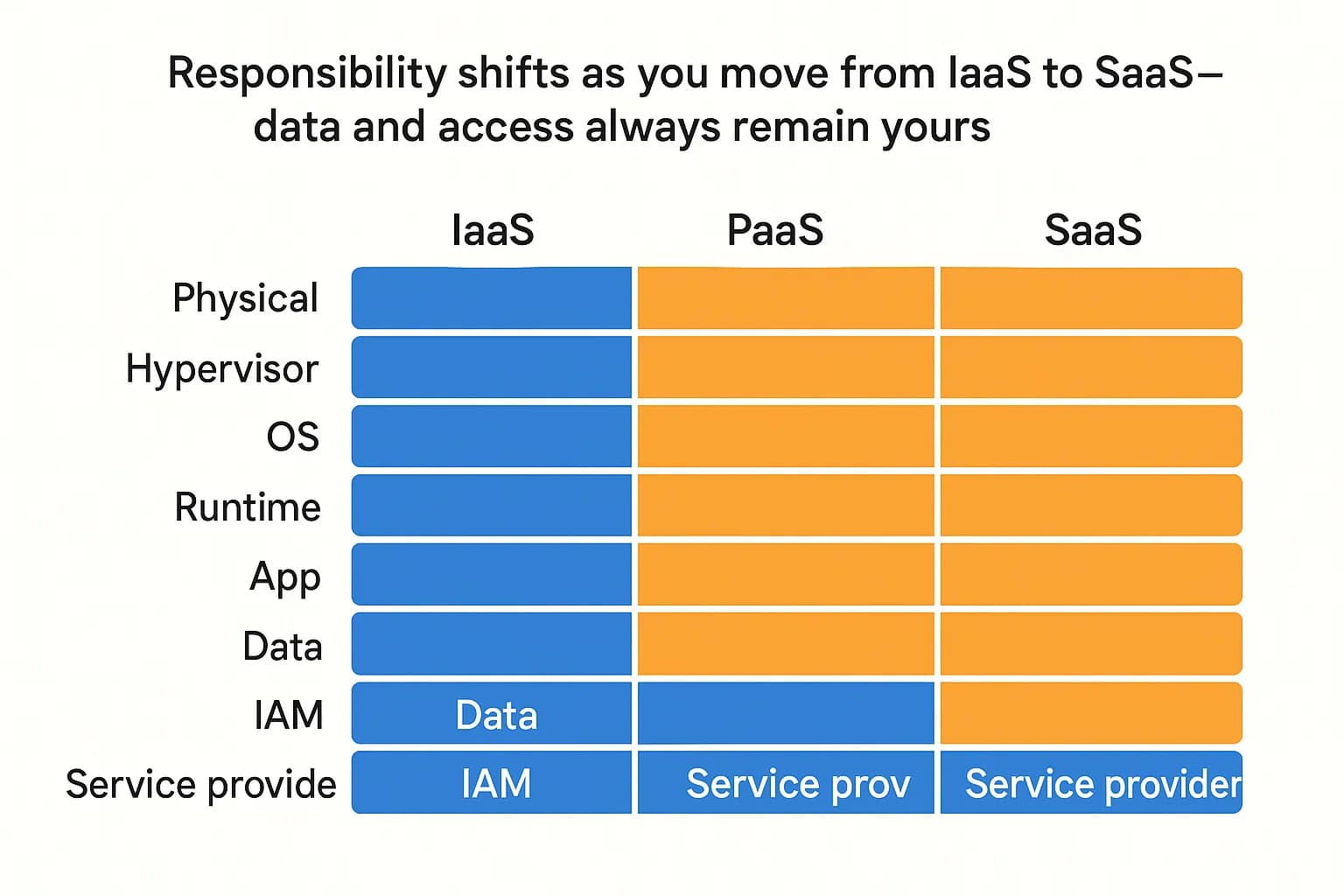
Your specific responsibilities shift depending on the type of cloud service you use. As you move from IaaS to SaaS, you offload more operational burden to the CSP, but you never offload responsibility for your data and user access.
The 2019 Capital One breach, which exposed the personal information of over 100 million customers, is a textbook example of a failure on the customer's side of the shared responsibility model. The attacker didn't breach AWS's core infrastructure. Instead, they exploited a misconfigured web application firewall (WAF) , a security control that was fully configured and managed by Capital One, to gain access to an EC2 instance. From there, they used the instance's overly permissive IAM role to access and exfiltrate data from S3 buckets.
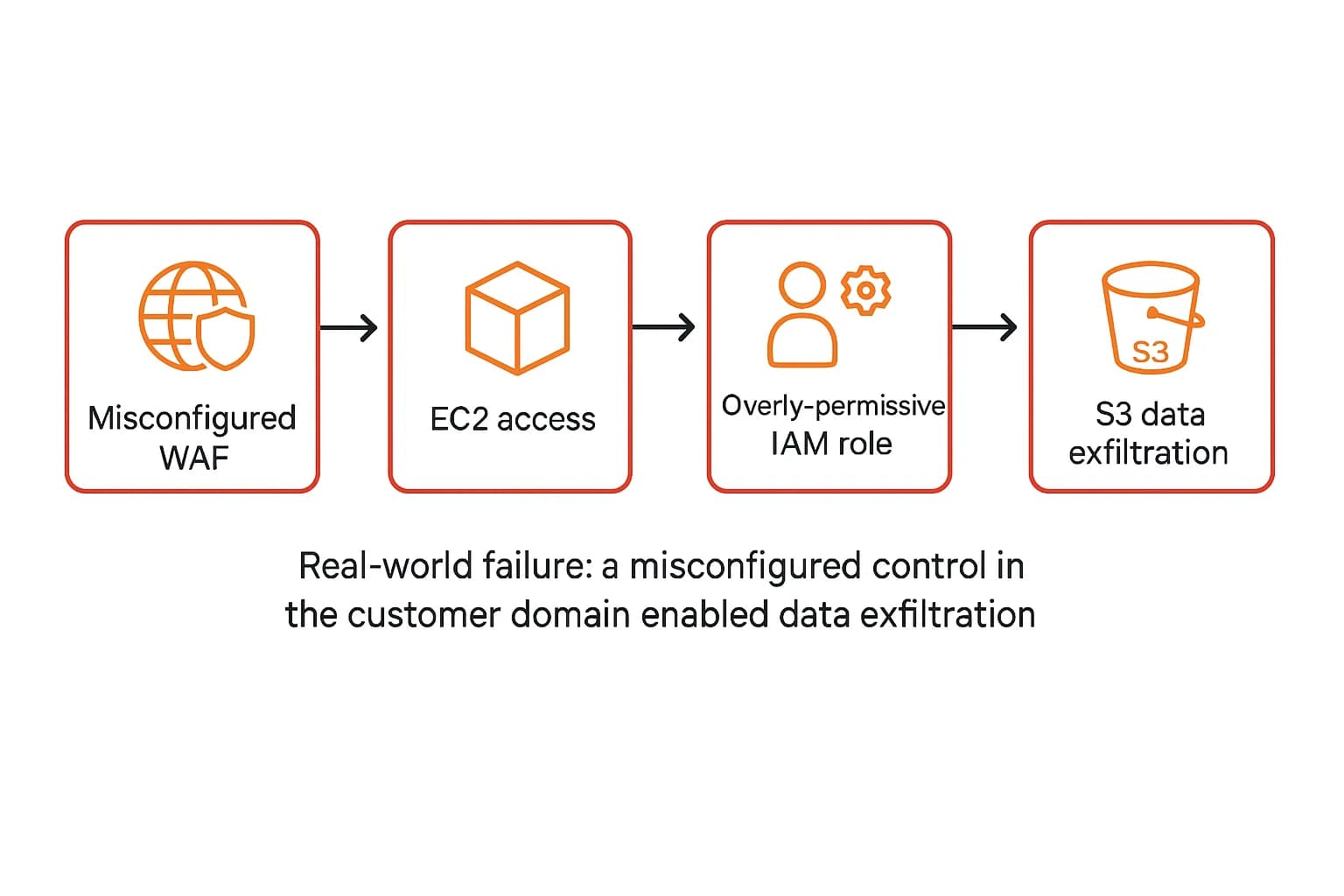
Every step of this attack chain exploited controls that were Capital One's responsibility to secure. This case powerfully illustrates that even when using a world class, secure provider like AWS, a single customer misconfiguration can lead to a catastrophic breach.
The traditional understanding of the Shared Responsibility Model is no longer sufficient. It's not a static legal document; it's a dynamic operational contract that expands and changes with every new cloud service you adopt. The greatest risk isn't a general misunderstanding of IaaS vs. PaaS, but the failure to apply the model to each new, specialized service your teams adopt. When a developer spins up a new managed Kubernetes service or an AI/ML platform, that service comes with its own unique shared responsibility matrix. Who is responsible for securing the container runtime in AWS Fargate versus a self managed Kubernetes cluster on EC2? The answers are different. The failure to perform this granular due diligence for every single service creates "responsibility gaps" areas where both you and the CSP assume the other party is responsible for a specific control. These gaps are the fertile ground where attackers plant their flags. Mature organizations must move toward a formal "Cloud Service Adoption Framework," where no new service is used in production until its specific shared responsibility model is documented and the customer side controls are assigned and automated.

The world of cloud compliance is a dizzying array of acronyms. Understanding which frameworks apply to your business is the first step toward building a coherent strategy. These standards can be broadly categorized into voluntary best practice frameworks, mandatory industry regulations, and global data privacy laws.
This overview is designed to help you quickly identify the standards most relevant to your business operations.
Achieving compliance in a dynamic cloud environment isn't a one time project; it's a continuous cycle of discovery, implementation, automation, and validation. Manual processes and point in time audits can't keep up. Here’s a modern, automation driven blueprint for success.
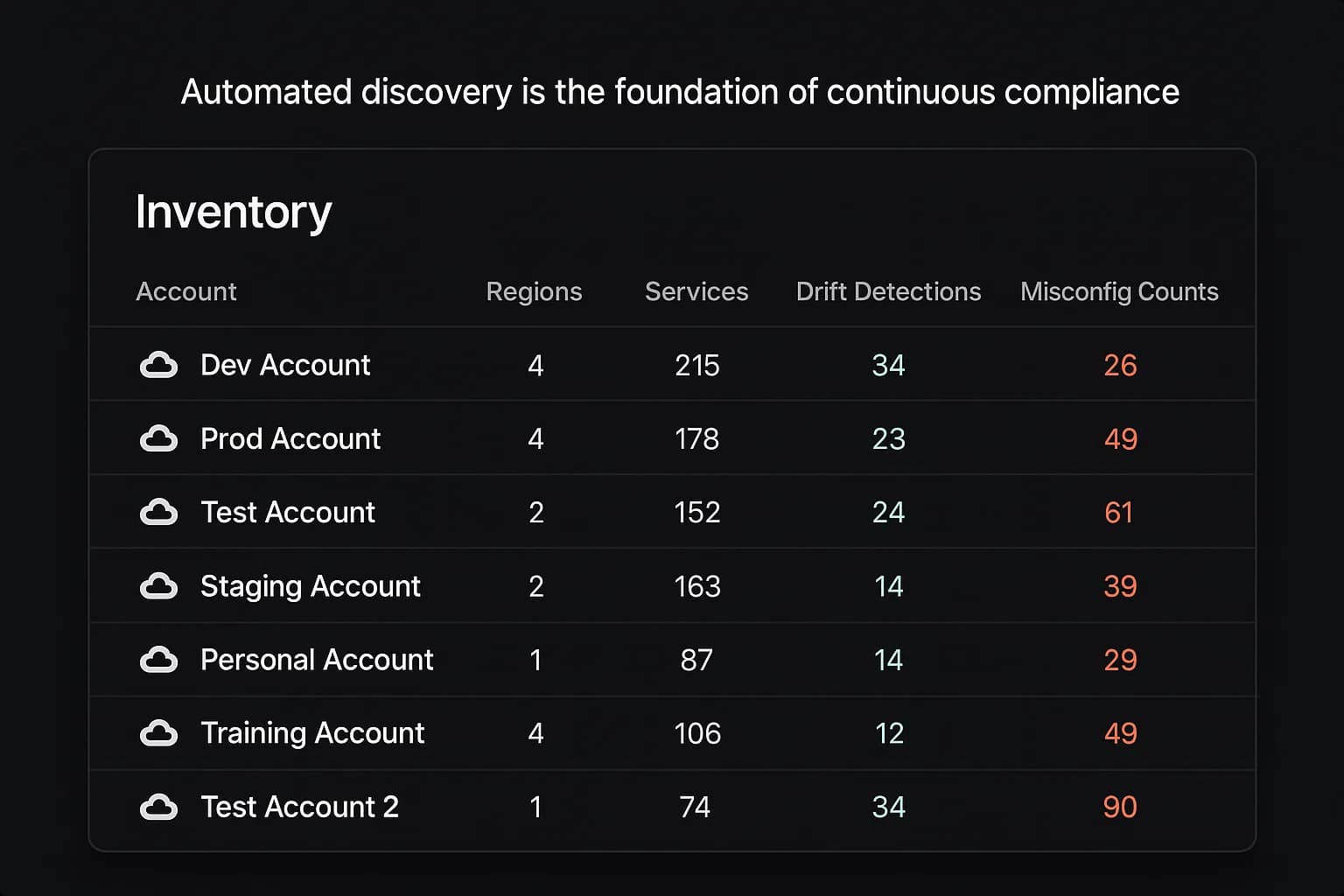
You can't protect what you don't know you have. The first step in any Data Security Audit is defining the scope of what needs to be protected. In the cloud, this is a constantly moving target. Developers can spin up new resources in minutes, often without IT's knowledge, a phenomenon known as "Shadow IT". These unmanaged assets are a massive blind spot and a primary source of compliance gaps.
The solution is to move from manual spreadsheets to automated discovery. Cloud Security Posture Management (CSPM) tools are essential here. They continuously scan your cloud environments (AWS, Azure, GCP) via APIs to create a real time, comprehensive inventory of all your assets VMs, storage buckets, databases, serverless functions, and more. This provides the foundational visibility needed for any compliance program. Check out our guide to the best CSPM tools for cloud security.
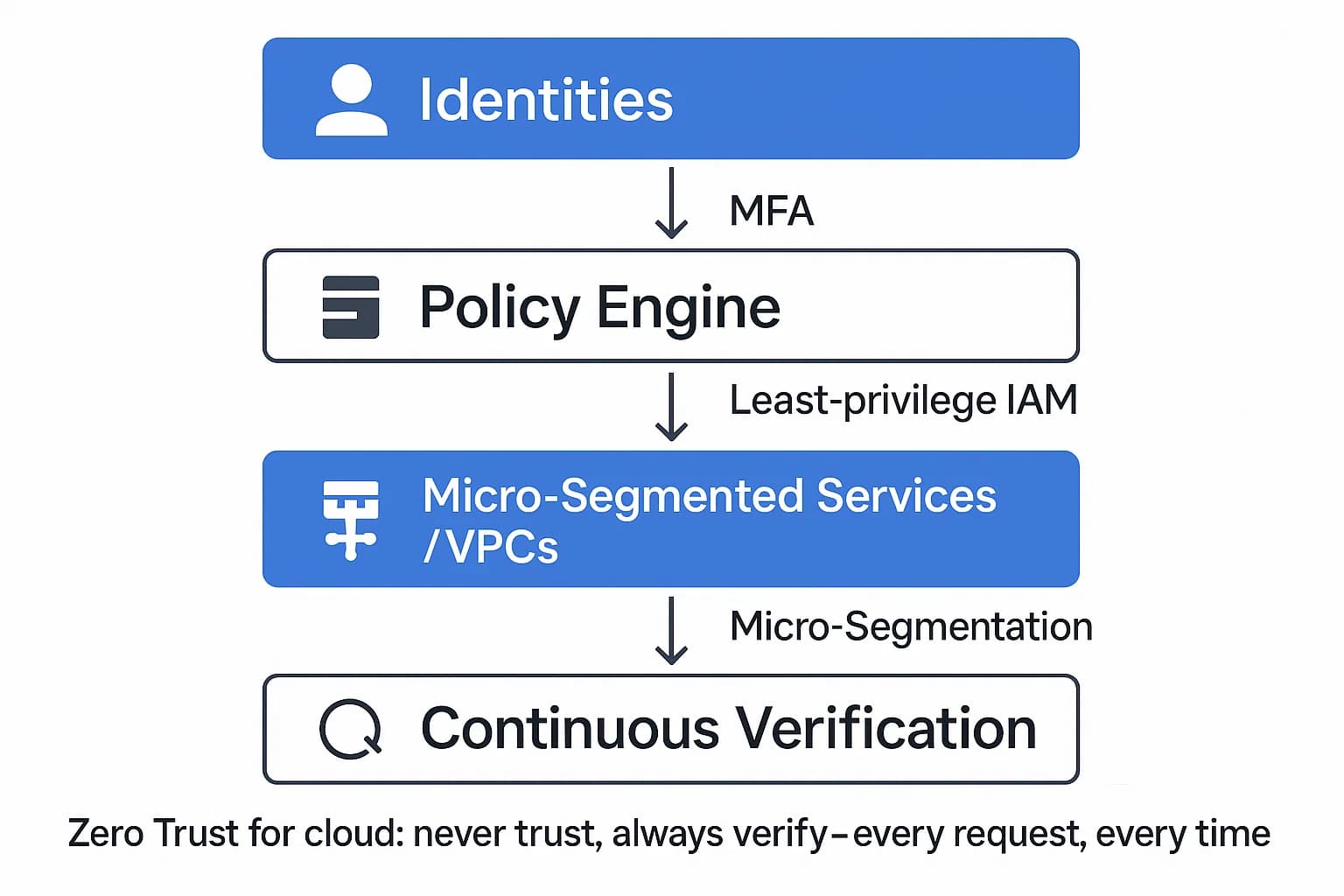
The old model of a trusted internal network and an untrusted external one is dead. In the cloud, there is no perimeter. This is why a Zero Trust Architecture is the default security model for modern enterprises. The core principle, as defined in NIST SP 800 207, is simple: "never trust, always verify". Every access request must be authenticated and authorized, regardless of where it originates.
In a practical cloud context, this means implementing:
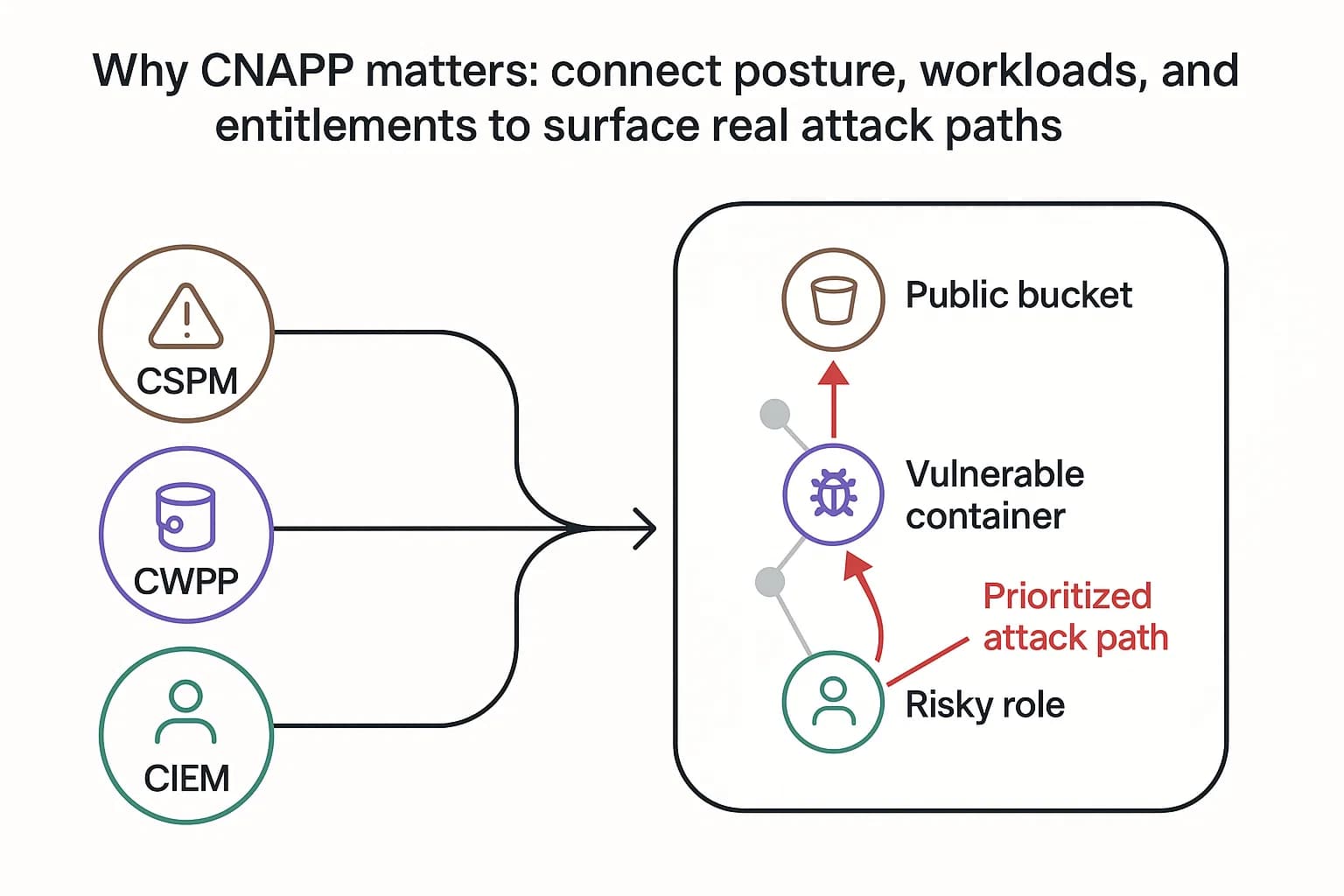
CSPM tools are great for telling you what you have and if it's misconfigured. But what about the workloads running inside those resources? This is where Cloud Native Application Protection Platforms (CNAPP) represent the next evolution in cloud security.
First coined by Gartner, a CNAPP is an all in one platform that unifies multiple security capabilities into a single, integrated solution. A mature CNAPP typically includes:
The practical benefit is immense. A CNAPP doesn't just tell you a storage bucket is public (CSPM). It can also see that a vulnerable, internet facing container is running on a VM that has an IAM role allowing it to write to that bucket. By connecting these dots, a CNAPP can show you a complete, prioritized attack path, allowing your team to focus on the 2% of alerts that represent real, exploitable risk instead of drowning in the other 98%.
Automation and monitoring are essential, but they are not enough. Compliance isn't just about having controls in place; it's about proving they work under the pressure of a real world attack. This is the critical role of compliance focused penetration testing.
Frameworks like PCI DSS (Requirement 11.3) and attestations like SOC 2 explicitly require or strongly recommend independent security testing. Auditors don't just want to see your policy documents; they want evidence that your controls are effective. A rigorous penetration test that simulates a determined attacker provides this validation. It moves beyond a simple vulnerability assessment vs penetration testing and actively attempts to exploit misconfigurations, chain together weaknesses, escalate privileges via IAM, and access sensitive data just like a real adversary would.
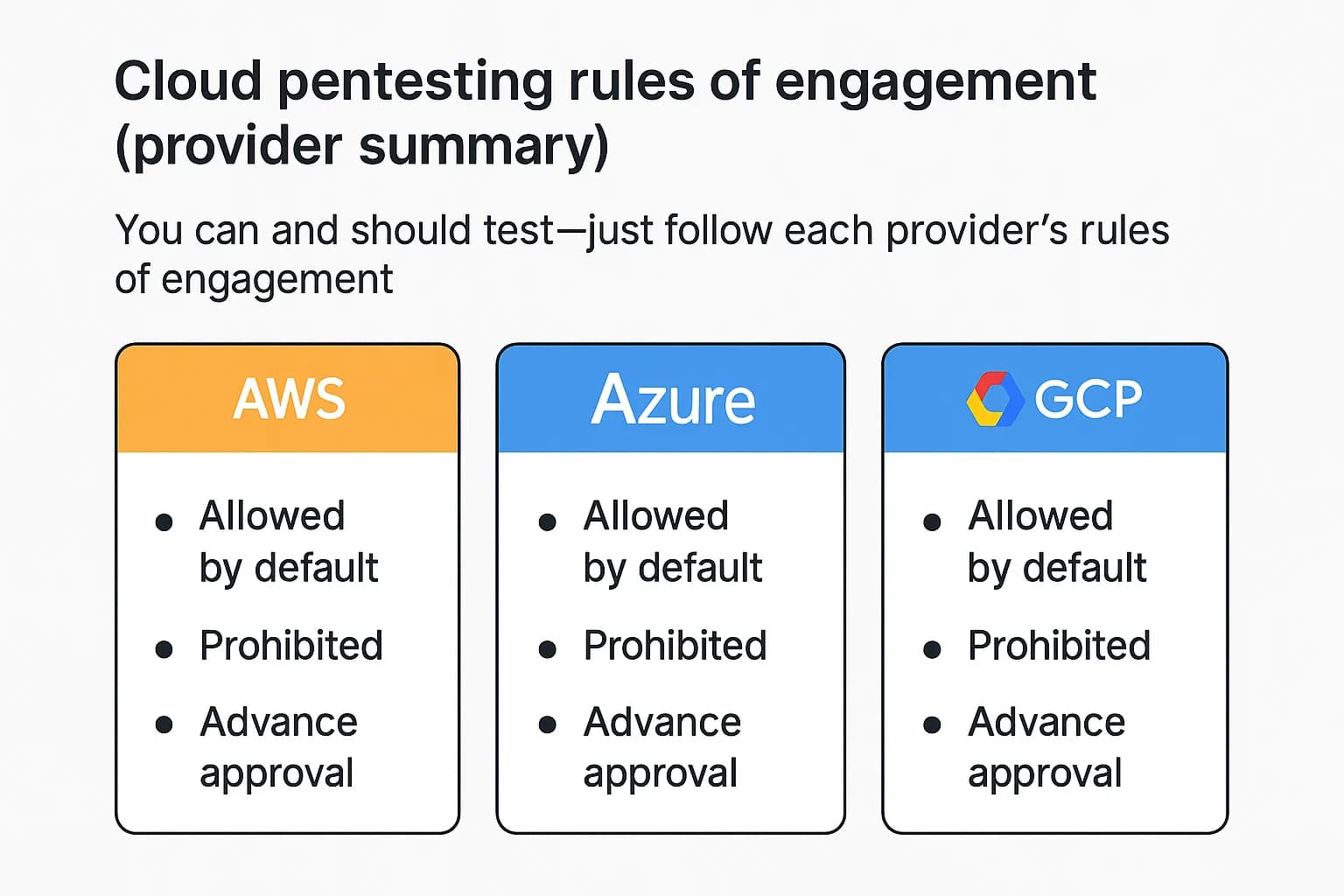
Conducting a penetration test in the cloud requires a clear understanding of the rules. The good news is that the days of needing to ask for permission for every little thing are largely over. The major cloud providers have established clear guidelines for security testing.
Here’s a quick breakdown based on my experience conducting these tests:
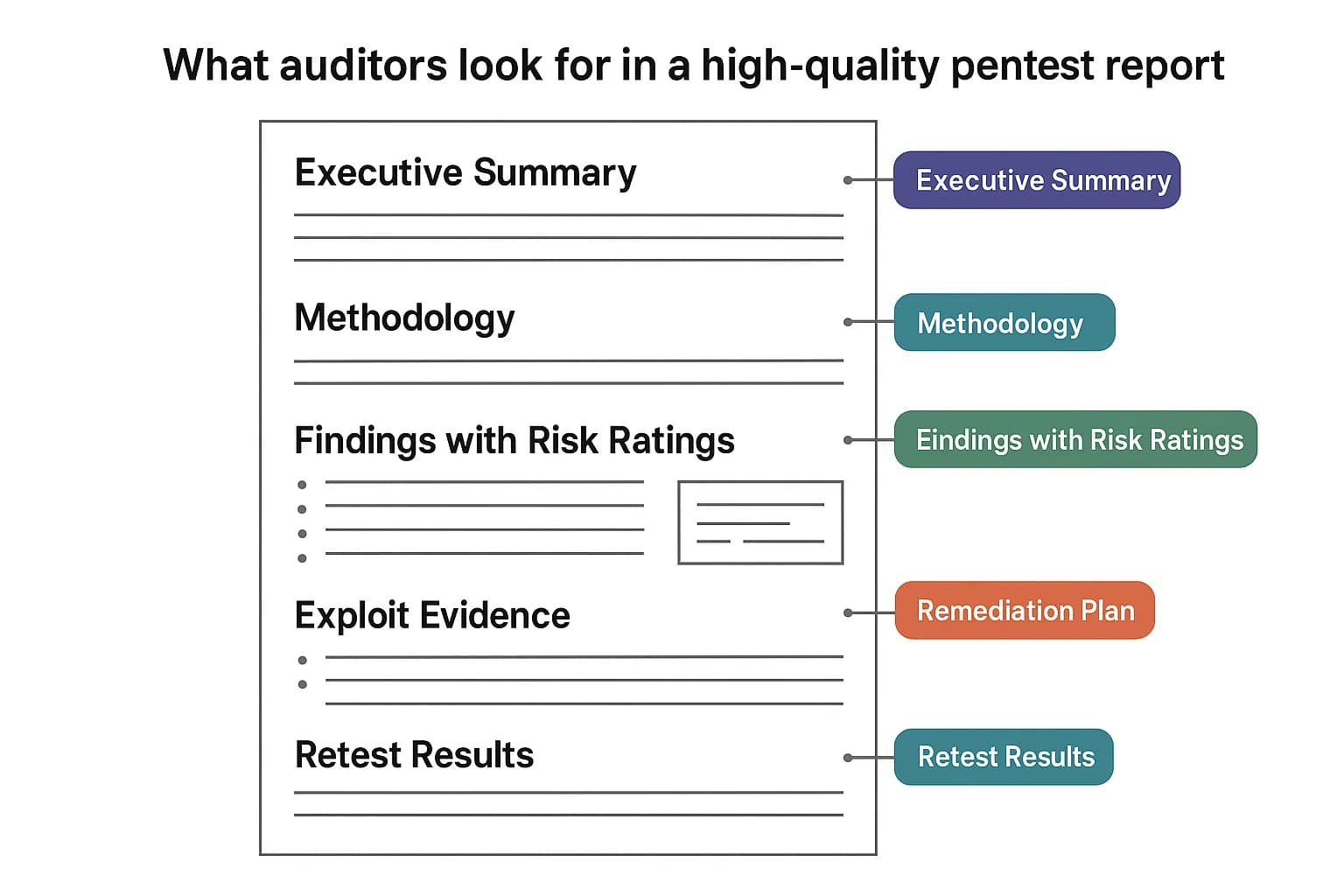
As a practitioner who has sat through countless audit meetings, I can tell you that a high quality penetration test report is one of the most valuable pieces of evidence you can provide. Auditors for frameworks like SOC 2 penetration testing requirements and ISO 27001 are looking for objective proof that your security program is not just a paper exercise.
A comprehensive report from a reputable firm demonstrates due diligence. It shows that you have:
This transforms the conversation with an auditor from "Here are our policies" to "Here is the evidence that our policies are being enforced and tested against real world attack scenarios." It is a powerful signal of a mature and trustworthy security program.
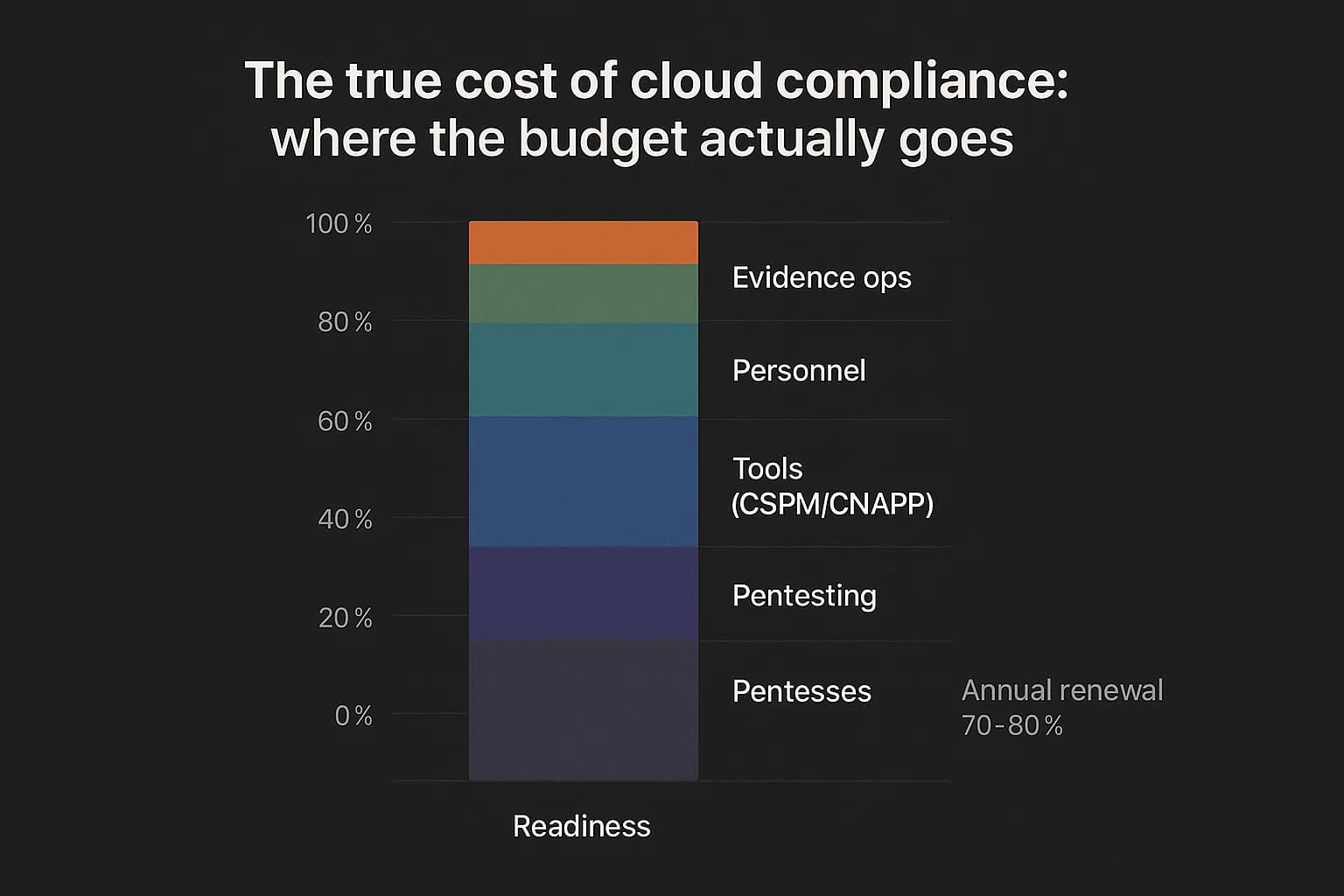
Compliance is an investment, and like any investment, it's crucial to understand the costs, budget appropriately, and measure the return. Talking about the financials of compliance helps bridge the gap between security teams and business leadership.
The total cloud compliance cost is not a single line item. It's a collection of direct and indirect expenses that you need to budget for.
While the direct costs of a breach are well documented, the hidden costs are often more damaging. One of the biggest is lost sales velocity. A recent Drata report found that 41% of businesses without a continuous compliance program experience significant slowdowns in their sales cycle. Every day a multi million dollar enterprise deal is stalled because your team is scrambling to answer a 200 question security questionnaire or can't produce a SOC 2 report is a direct, quantifiable hit to your company's revenue.
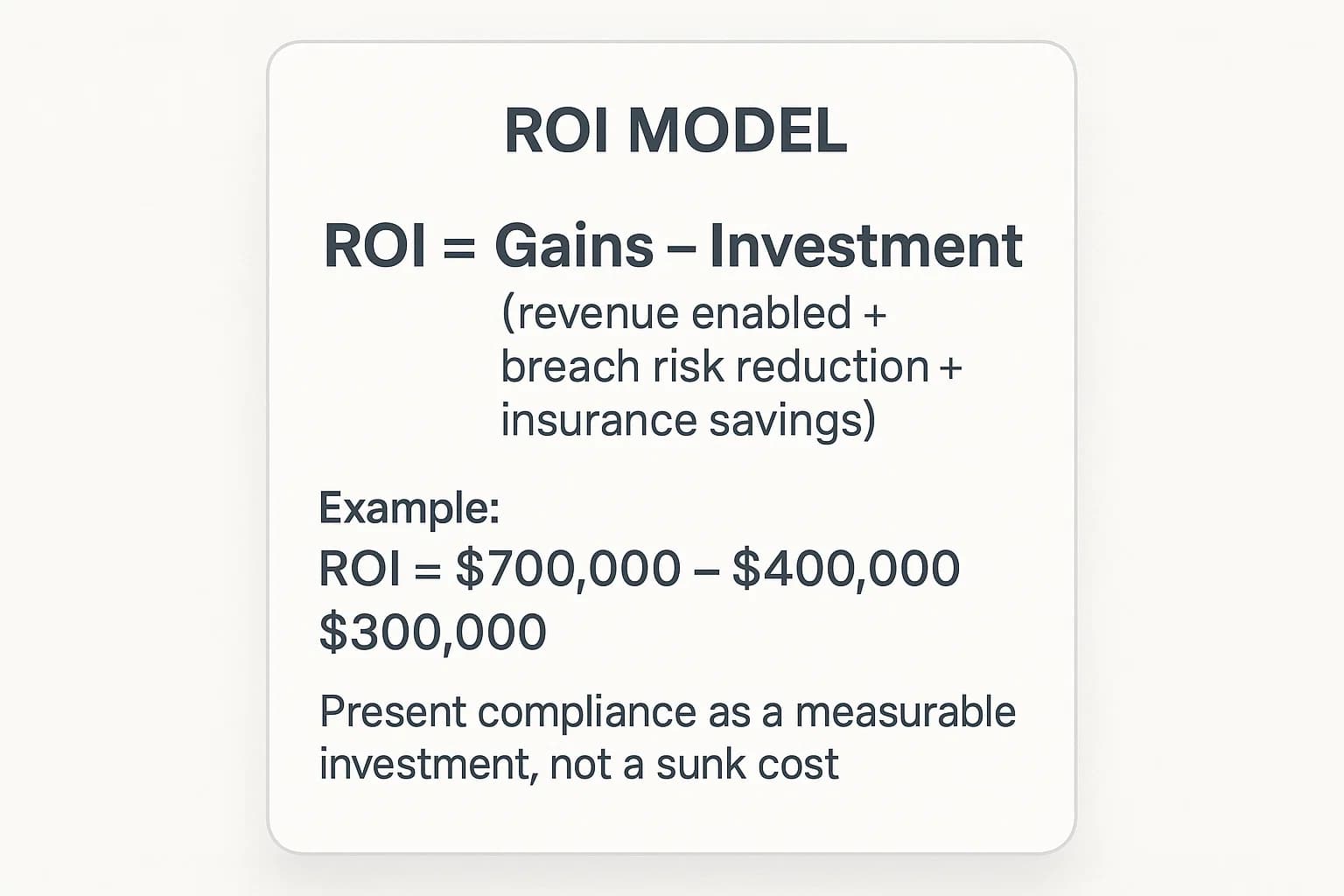
Framing compliance as an investment with a measurable return is key to getting executive buy in. While a precise formula can be complex, you can build a strong business case by estimating the ROI of cloud compliance using a simple framework.
Gains (Value Generated):
Investment (Total Cost):
When you present the numbers this way, compliance shifts from being a "cost of doing business" to a strategic investment that directly protects and grows the business.
1. What is the difference between cloud security and cloud compliance?
Cloud security is the set of technical controls and processes you implement to protect your assets (e.g., firewalls, encryption, IAM policies). Cloud compliance is the third party validation that your security program meets the requirements of a specific, recognized standard (e.g., a SOC 2 report from an auditor). You can be secure without being compliant, but you cannot be truly compliant without being secure.
2. How much does a typical cloud compliance program cost?
For a mid-sized SaaS company seeking its first SOC 2 report, the all-in cost for the first year can range from $80,000 to $350,000. This includes readiness assessments, penetration testing, new security tools, and the audit itself. Annual maintenance and re auditing typically cost 70-80% of the initial investment.
3. Which is the most important cloud compliance framework?
It depends entirely on your business model and customers. For B2B SaaS companies in North America, SOC 2 is almost always the top priority. If you handle patient data, HIPAA is legally required. If you process credit cards, PCI DSS is mandatory. If you have users in Europe, GDPR applies. Many organizations find they need to comply with multiple frameworks simultaneously.
4. Can you be 100% compliant but still get breached?
Absolutely. Compliance is a snapshot in time; it is not a guarantee of impenetrable security. A new Zero day exploit lifecycle and prevention or a sophisticated phishing attack can still bypass controls that were deemed compliant during an audit. This is why compliance must be a continuous, ongoing process of monitoring, testing, and improvement, not a one and done project.
5. How does multi cloud affect compliance strategy?
Multi cloud environments dramatically increase compliance complexity. Each cloud provider has different security tools, IAM models, and configuration settings. Maintaining a consistent and auditable compliance posture across AWS, Azure, and GCP requires a unified strategy. This often involves using third party CNAPP tools that provide a "single pane of glass" for monitoring and policy enforcement across all your cloud providers.
6. What is a cloud security audit?
A cloud security audit is a formal, independent review of your cloud environment's security controls, policies, and operational procedures. The primary goal is to gather objective evidence to verify that your controls are designed appropriately and operating effectively to mitigate risk. The output of an audit is typically a formal report or attestation, such as a SOC 2 report, that you can share with customers and stakeholders.
Cloud security compliance has fundamentally evolved. It's no longer a technical chore relegated to the IT department but a strategic function that is deeply intertwined with business growth, customer trust, and financial resilience.
Here are the key takeaways for 2025 and beyond:
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services for businesses to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us