November 17, 2025
Updated: November 17, 2025
Discover how dark web anonymity really works in 2025 from onion routing and hidden services to the real risks of deanonymization, tracking, and user mistakes.
Mohammed Khalil


The dark web is the hidden overlay of the Internet accessible only via privacy networks like Tor The Onion Router or I2P. Unlike the surface web which search engines index or the broader deep web password protected databases, dark web sites intentionally conceal their IP addresses. They use random .onion addresses that only Tor software can resolve. This design makes the dark web a place for anonymous browsing. For privacy advocates and journalists, it enables free speech and whistleblowing; for criminals, it provides a shield for illicit markets. In 2025, understanding this matter is urgent: with growing surveillance and data breaches, knowing the limits of dark web anonymity can protect both individuals and organizations. For a deeper breakdown of layers, see our guide on Deep Web vs Dark Web.
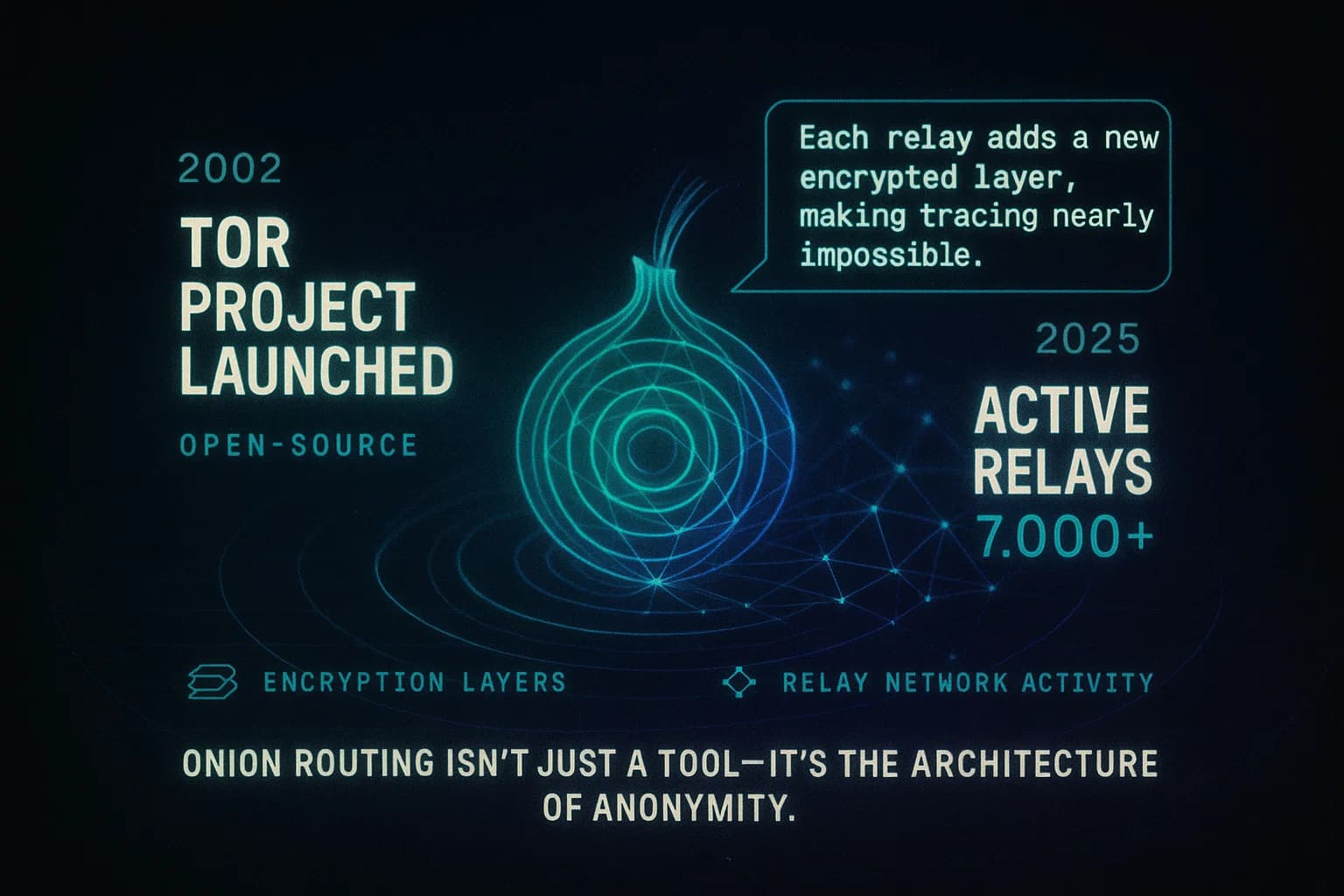
Most dark web anonymity comes from Tor’s onion routing. Tor bounces your traffic through three or more randomly chosen volunteer run relays nodes around the world, encrypting each layer at the source and peeling it off at each hop. The image below illustrates a typical Tor circuit:
Tor onion routing passes your data through multiple relays, each decrypting one layer. No single relay knows both where you started and where you’re going.
In practice, your Tor Browser first encrypts data for the final server, then again for a middle node, and again for an entry guard node. Each relay removes one layer of encryption and forwards the packet. This telescoping process ensures no single point ever sees both the origin and the destination. As Kaspersky explains, Tor anonymizes user traffic through a distributed network of servers… No single node knows both the origin and destination addresses of a data packet. Likewise, Wikipedia notes Tor’s multi-layered encryption the onion metaphor provides perfect forward secrecy, making the user’s identity very hard to trace. In short, Tor breaks the direct link between your IP and the site you visit outside observers only see encrypted Tor traffic and know you’re using Tor, but not where you’re going.
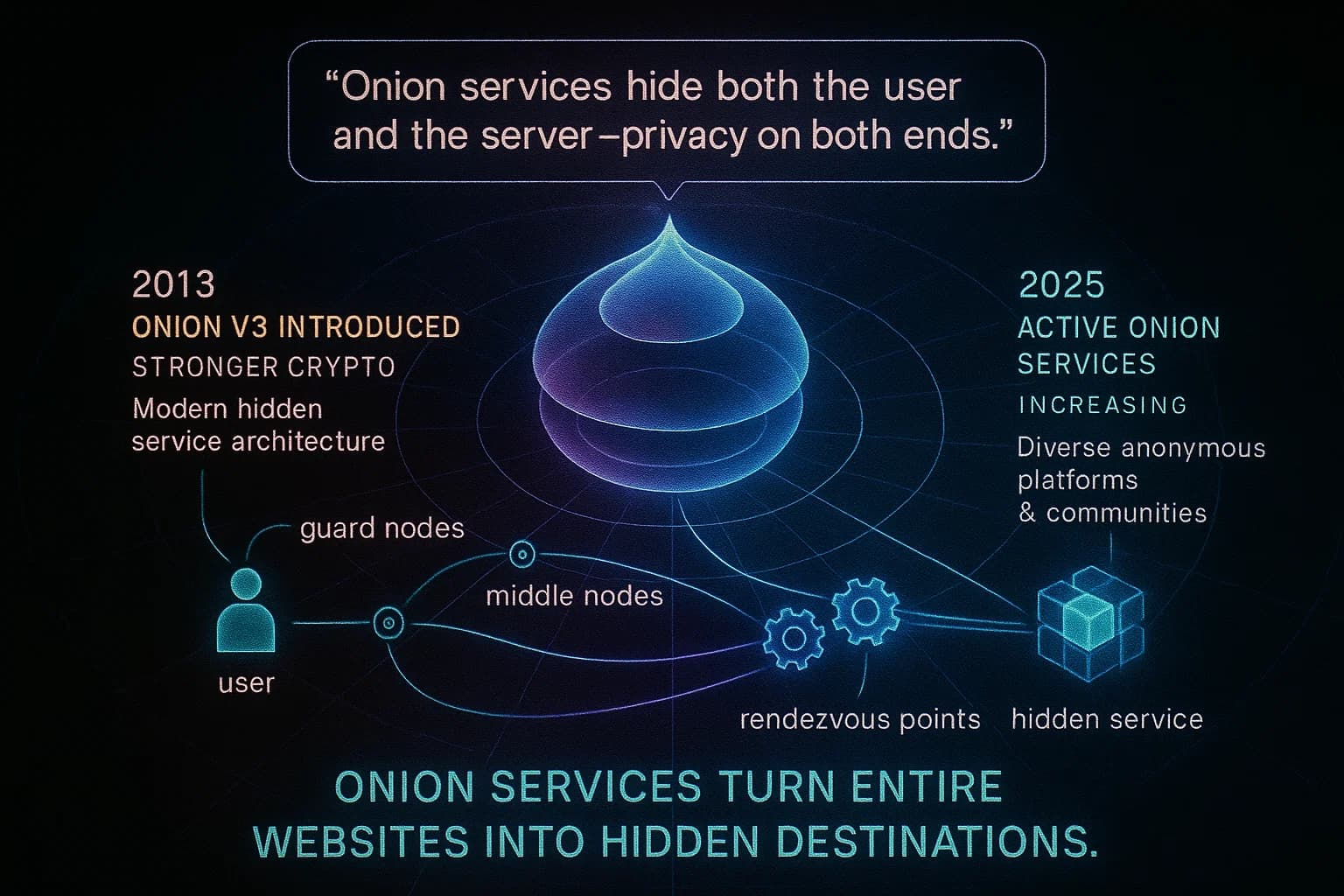
Tor doesn’t just hide users; it can hide servers. A dark web website configured as a Tor onion service formerly hidden service has no visible IP. Instead, it advertises a randomly generated .onion address that encodes its public key. When you visit such a site, Tor builds a special circuit called a rendezvous point inside the network. Crucially, your traffic never leaves Tor, even the exit node. As Wikipedia describes: the connection never leaves the Tor network… the connection is always end-to-end encrypted. This means neither the visitor nor the site ever learns the other’s actual Internet address. In practical terms, dark web marketplaces, forums, and messaging services leverage this so both operators and users can interact anonymously. Law enforcement cannot flood the site’s real server IP with packets because it simply doesn’t know it it only knows the .onion endpoint inside Tor.
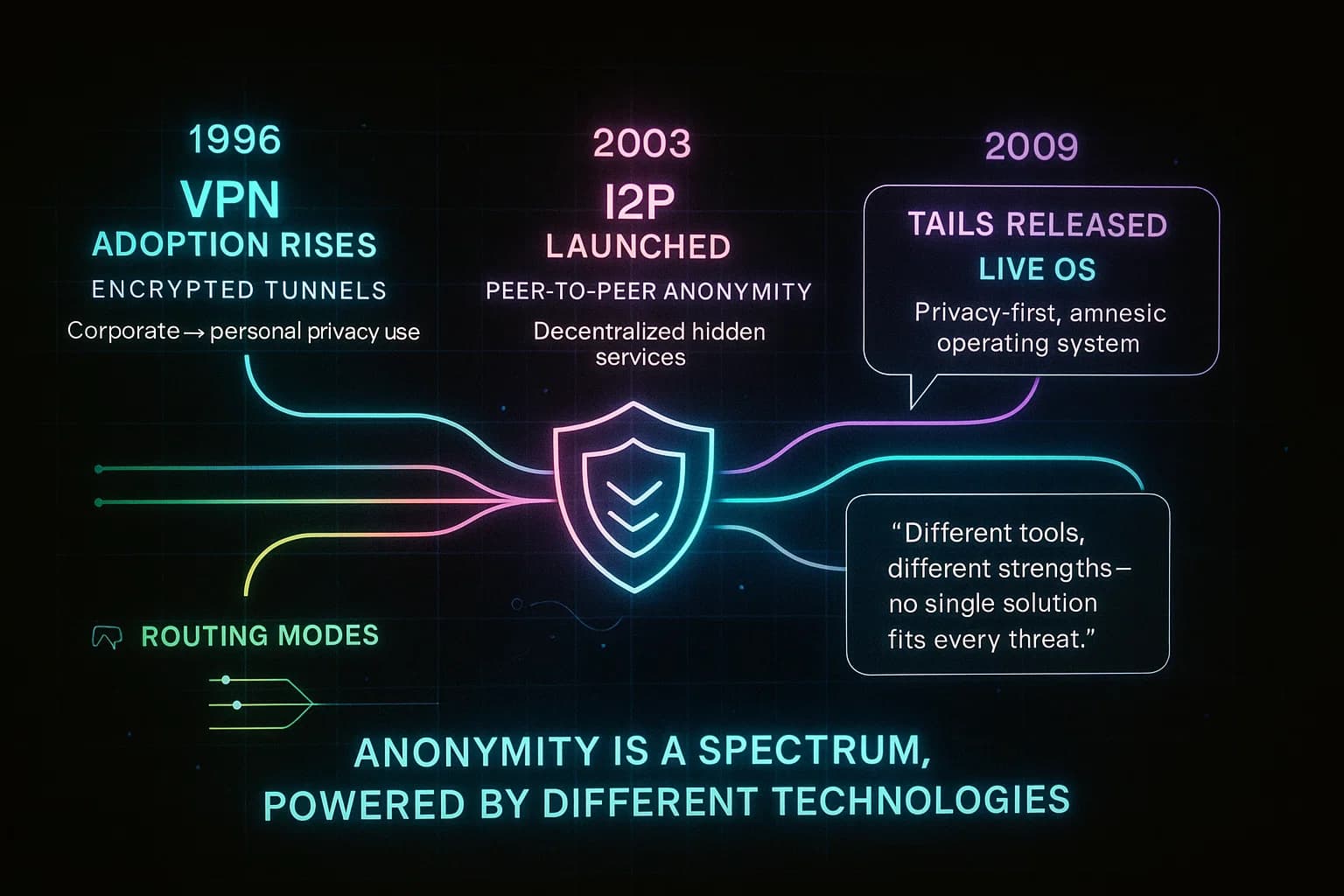
While Tor is the dark web’s backbone, alternatives exist. I2P Invisible Internet Project is another volunteer driven network that uses garlic routing to anonymize traffic within its own peer to peer network. Unlike Tor, I2P never uses an exit to the open Internet it’s mainly for services hosted inside I2P. In practice, Tor vs I2P differences are subtle: both route through multiple nodes with layered encryption, but Tor’s exit nodes let you reach normal websites with the exit seeing the traffic, whereas I2P is siloed. Another option is a VPN Virtual Private Network. A VPN routes all your Internet traffic through one remote server. A VPN hides your IP from websites and from Tor if used before Tor, but trust is centralized: the VPN provider can see your traffic and must be trusted.
| Feature | Tor The Onion Router | VPN Virtual Private Network | I2P Invisible Internet Project |
|---|---|---|---|
| Anonymity | High Traffic goes through ≥3 relays, no single node knows both ends. | Medium Your ISP only sees a connection to the VPN, not final sites but VPN provider sees both. | High for I2P services Multi hop routing within I2P network, decentralized. |
| Exit Node | Final exit node sends traffic to Internet exit IP sees destination. | VPN server sends traffic to Internet VPN IP used. | No exit to Internet all I2P sites are inside the network, using i2p domain. |
| Encryption | Multi layer AES encryption on each Tor hop. | One encrypted tunnel usually TLS/IPsec. | Multi layer encryption garlic bundles within I2P network. |
| Trust Model | Decentralized hundreds of volunteer run relays anyone can host a node. | Centralized depends on a single VPN provider’s privacy policy. | Decentralized all participants run routers within I2P network. |
| Use Cases | Access dark web .onion sites and surface web anonymously. | General privacy: browsing, P2P, geo unblocking; less anonymity if logs kept. | Hosting and using internal sites/services anonymously messaging, file sharing, blog. |
As shown, Tor’s major advantage is anonymity by design at the cost of speed. VPNs are simpler and faster, but if the VPN keeps logs or is compromised, your identity is exposed. Many advanced users combine them: for example, running Tor over a VPN or using bridges so your ISP can’t even see Tor traffic. Tails OS, a live Linux USB or Whonix are other tools: they force all system traffic through Tor and wipe data on shutdown, adding an extra layer of OpSec.

Tor is robust, but not invincible. Key weaknesses revolve around traffic analysis and user mistakes. For instance, timing/correlation attacks, if an adversary can monitor your entry and exit nodes simultaneously, they might link you to your target site by matching traffic patterns. As Kaspersky reports, German authorities identified a Tor user by doing exactly that they ran exit node monitoring and performed timing analysis on encrypted packets. In principle, a global observer like a nation state can try to watch the borders of the Tor network. Wikipedia notes that Tor cannot prevent traffic confirmation via end to end correlation if an attacker sees both sides. In other words, if someone spies on both your connection to a guard node and the corresponding exit node traffic, anonymity can collapse.
Another risk is exit node eavesdropping. Since Tor’s exit node decrypts the final layer, it can see whatever you send to Internet sites unless you use HTTPS. Malicious exit nodes can sniff data or inject trackers. Although this doesn’t reveal your IP, it can reveal the content of unencrypted traffic.
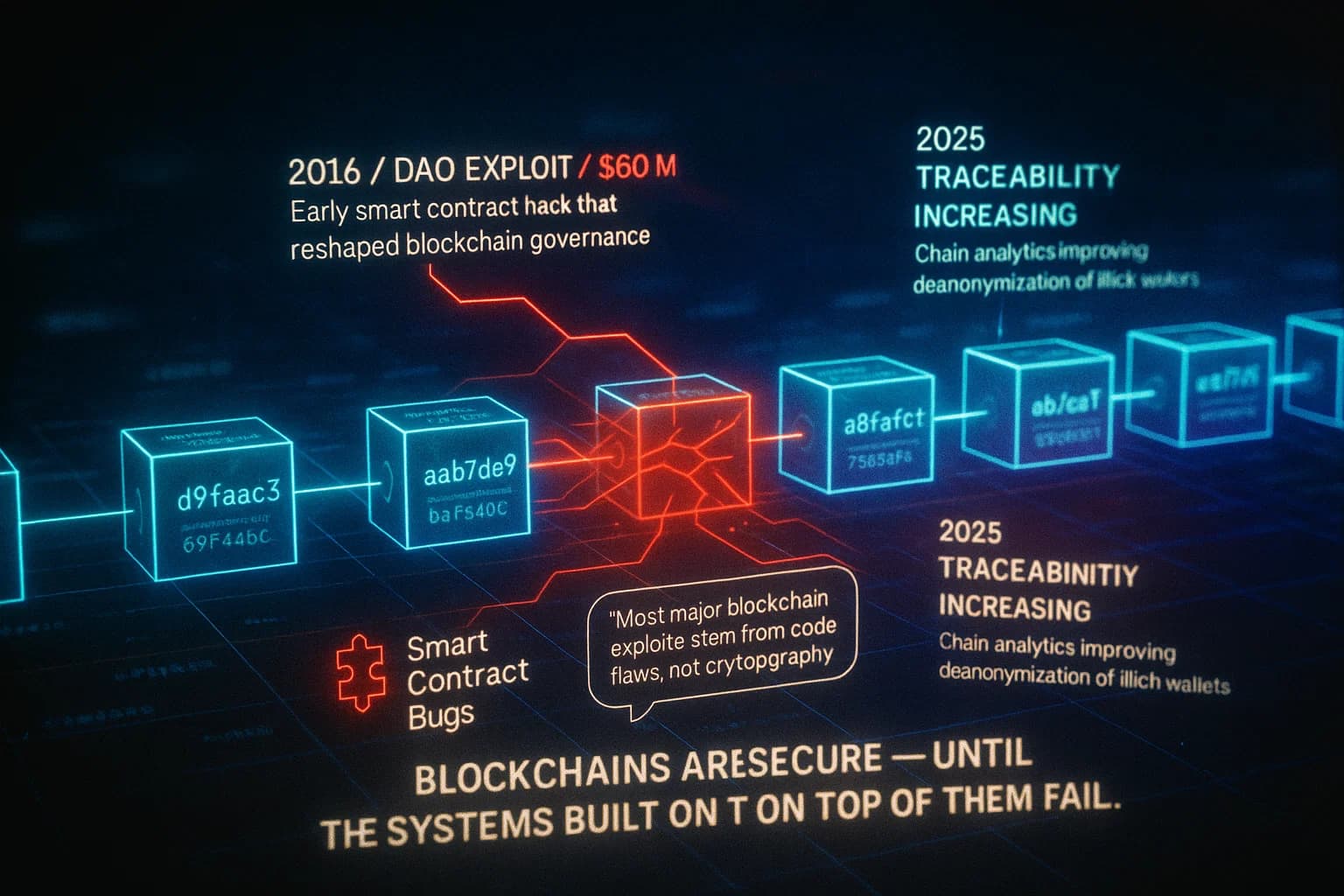
Technology outside Tor also undermines anonymity. Many dark web users believe that using privacy coins Monero, Zcash and mixing gives full payment privacy. But even that can leak. Wired reported that users who migrated to Monero thinking Bitcoin was too traceable learned that Monero’s privacy has flaws. Studies found that earlier Monero transactions could be unraveled, so once cherished as untraceable, Monero isn’t completely stealth. Similarly, any crypto you buy with a KYC exchange or transfer can create a link back to you.
Law enforcement successes highlight these points. Wired notes that blockchain analysis helped connect Silk Road’s fortune to...Ross Ulbricht and even track the servers of the Hansa marketplace. In other words, Bitcoin’s ledger let investigators unmask Silk Road’s boss, despite Tor’s protection. Operations like 2017’s Disruptor have shown that with enough leaks and analysis, hidden criminals can be caught. For a deep dive on such methods, see our article How Law Enforcement Tracks Criminals On The Dark Web.
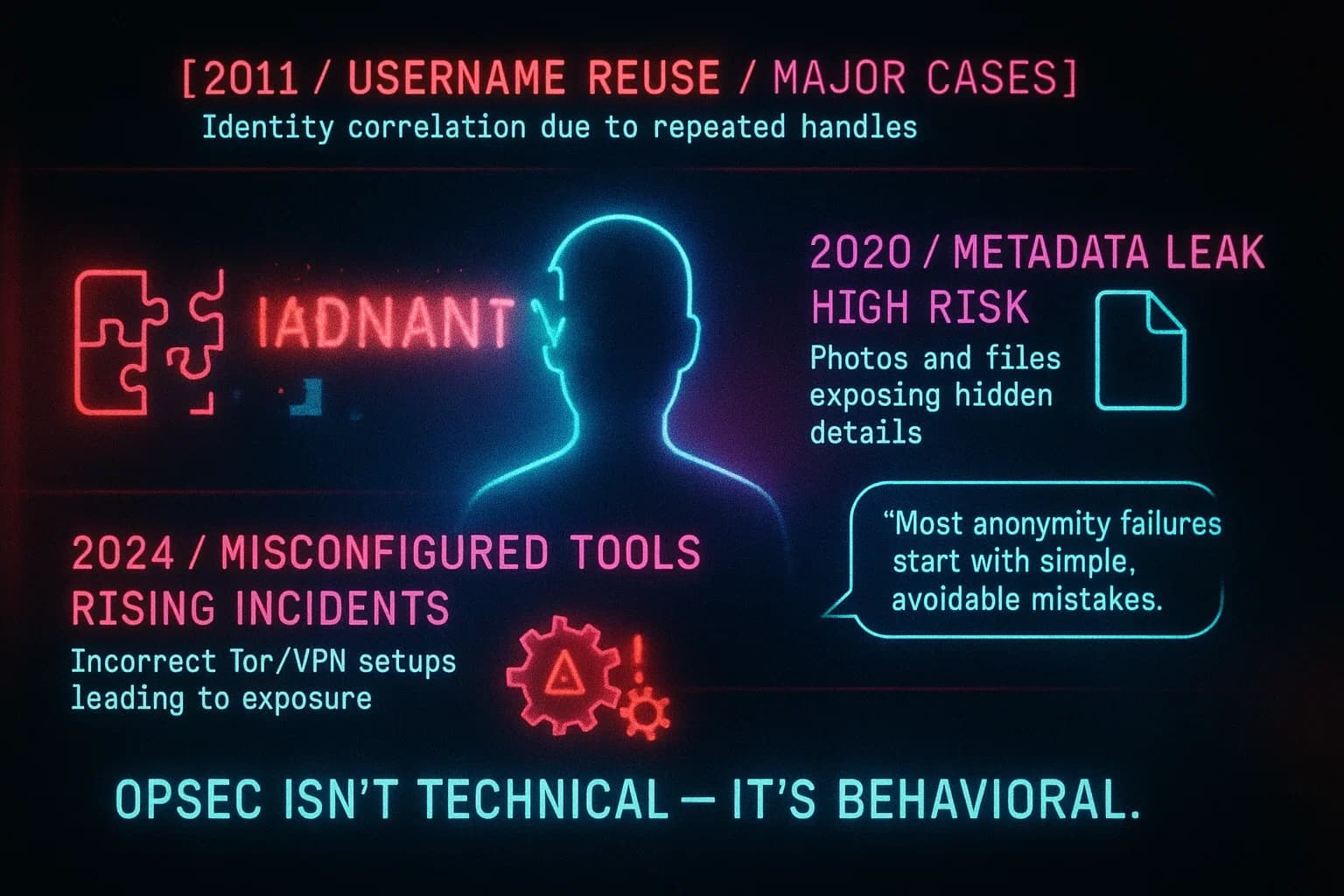
Beyond tech attacks, human error is the leading cause of deanonymization. Simply using Tor isn’t enough if you behave carelessly. The Tor Project warns: Our browser is anonymous, but if you misuse it, you may still be exposed. Common pitfalls include logging into personal accounts e.g. email, social media over Tor, which instantly links your session to your identity. Kaspersky’s Tor tips emphasize: don’t use real names or personal emails on Tor, and never log into accounts tied to your identity. Another danger is browser plugins or extensions a malicious Flash or JavaScript could bypass Tor. The Tor Browser even disables scripts by default and advises users to keep that way.
Malware and tracking also threaten anonymity. Downloading files, even innocuous looking ones on the dark web can expose you. Tor Project explicitly advises: Don’t open documents downloaded via Tor while online because they can exploit browser or OS vulnerabilities. Always open risky files in an offline VM or wipe the system after use. Finally, compartmentalization is key: use a dedicated device or a live system like Tails only for dark web activities, and never mix your identities. One guideline often cited is don’t talk about the dark web and keep every asset anonymous meaning, if your pseudonym ever ties back to your real life, anonymity is lost.
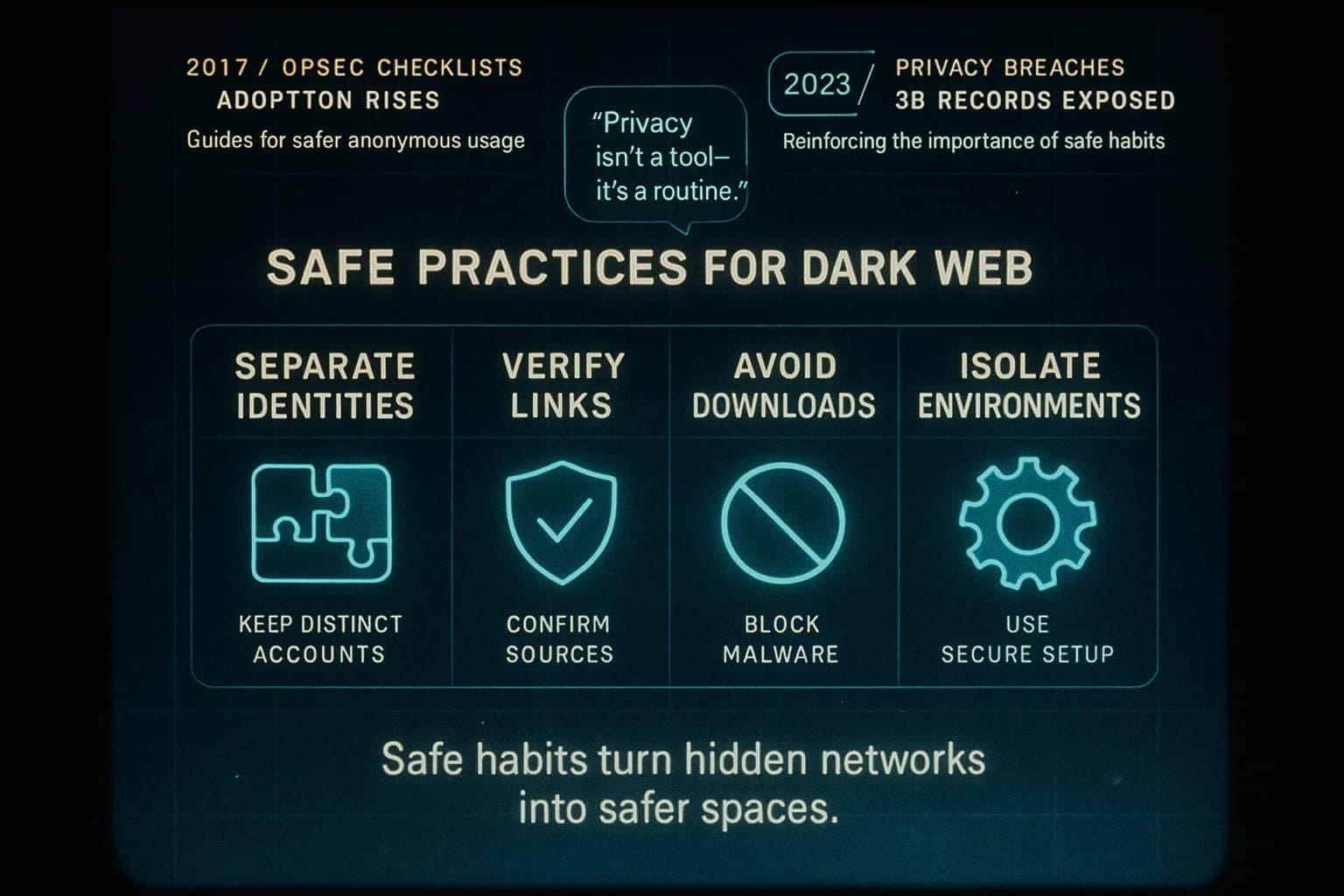
If you decide to browse the dark web, follow a strict checklist:
Following these OpSec rules is vital. For example, Tor’s own documentation explicitly warns against torrenting over Tor it can leak your IP and advises using only HTTPS or encrypted services. In short, anonymity is a process you must actively maintain.
The dark web can be anonymous, but only if every layer of the system from Tor’s encryption to your behavior is carefully secured. Tor’s onion routing illustrated above separates you from the destination, and onion services hide servers’ locations. But adversaries with enough resources, plus one stray identity link, can bridge that gap. For 2025’s world of pervasive surveillance and cyber threats, blind faith in anonymity is dangerous. Instead, be vigilant: assume you must stack defenses, use privacy tools correctly, and never slip in operational security.
When it comes to protecting your organization or data, relying on awareness isn’t enough. Want to test your defenses before attackers do? Ready to Strengthen Your Defenses? The threats of 2025 demand readiness. If you’re looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help.
Our team of penetration testing practitioners provides clear, actionable guidance to protect your business. Explore our Penetration Testing Services to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
About the Author:Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
The dark web is designed for anonymity via networks like Tor. Your traffic is encrypted and routed through multiple nodes, hiding your IP. However, no system is foolproof. Sophisticated analysis timing attacks, global surveillance or user errors can compromise anonymity. In short, dark web browsing is more anonymous than normal web, but it still requires vigilance.
Onion routing is Tor’s core technology. Data is encrypted in layers and sent through a chain of relays like peeling an onion. Each relay decrypts one layer and learns only the next hop, not the original sender. This way, no single relay sees both your real IP and the final destination. It’s what makes Tor so private.
Yes and no. Agencies have occasional success if they correlate traffic or break operational security. High profile cases e.g. Silk Road were cracked via blockchain analysis, not a flaw in Tor itself. Still, extensive monitoring or targeted attacks can deanonymize users. The Tor Project and security researchers emphasize that while Tor is resilient, it cannot guarantee absolute anonymity.
Only with strict precautions. Use the latest Tor Browser on a secure system like Tails, avoid personal accounts or info, disable scripts, and consider a VPN or bridge. Use strong encryption PGP for communications and privacy focused cryptocurrencies for payments. Never mix your real identity with dark web activities. Following these steps, as detailed above, gives the best chance to stay anonymous.
Simply using Tor or visiting hidden services is not illegal in most places, it's a privacy tool. What’s illegal is your actions on the dark web such as buying illicit goods or downloading child abuse material. Many journalists and privacy advocates legally use Tor to protect free speech. Always check your local laws and avoid illegal sites to stay on the right side of the law.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us