August 18, 2025
Updated: August 18, 2025
Cyberattacks on schools surged 31% YoY, hitting 4,388 weekly per organization. Learn the causes, costs, case studies, and defense strategies for education’s cyber crisis.
Mohammed Khalil


A data breach in education occurs when unauthorized parties steal or expose sensitive school data including student records, staff information, and proprietary research. In 2025, this is no longer a rare event; it's a daily crisis demanding urgent attention.
Here’s the deal: Recent intelligence confirms that schools and universities now face more cyberattacks than any other sector. And this isn't by accident. Attackers have made a strategic choice, viewing educational institutions as “target rich, cyber poor” a term used by CISA’s K–12 Cybersecurity Initiative to describe organizations that hold vast amounts of sensitive data but often lack the resources for robust protection.
The numbers are staggering. In the second quarter of 2025, the education sector endured an average of 4,388 cyberattacks per organization every week. This means that while you're reading this, criminals are actively trying to access student names, grades, Social Security numbers, and more. A breach can violate privacy laws like the Family Educational Rights and Privacy Act (FERPA), leading to identity theft for minors and lasting financial and emotional harm for families. In short, educational institutions are under siege, and protecting student and staff data has never been more critical.
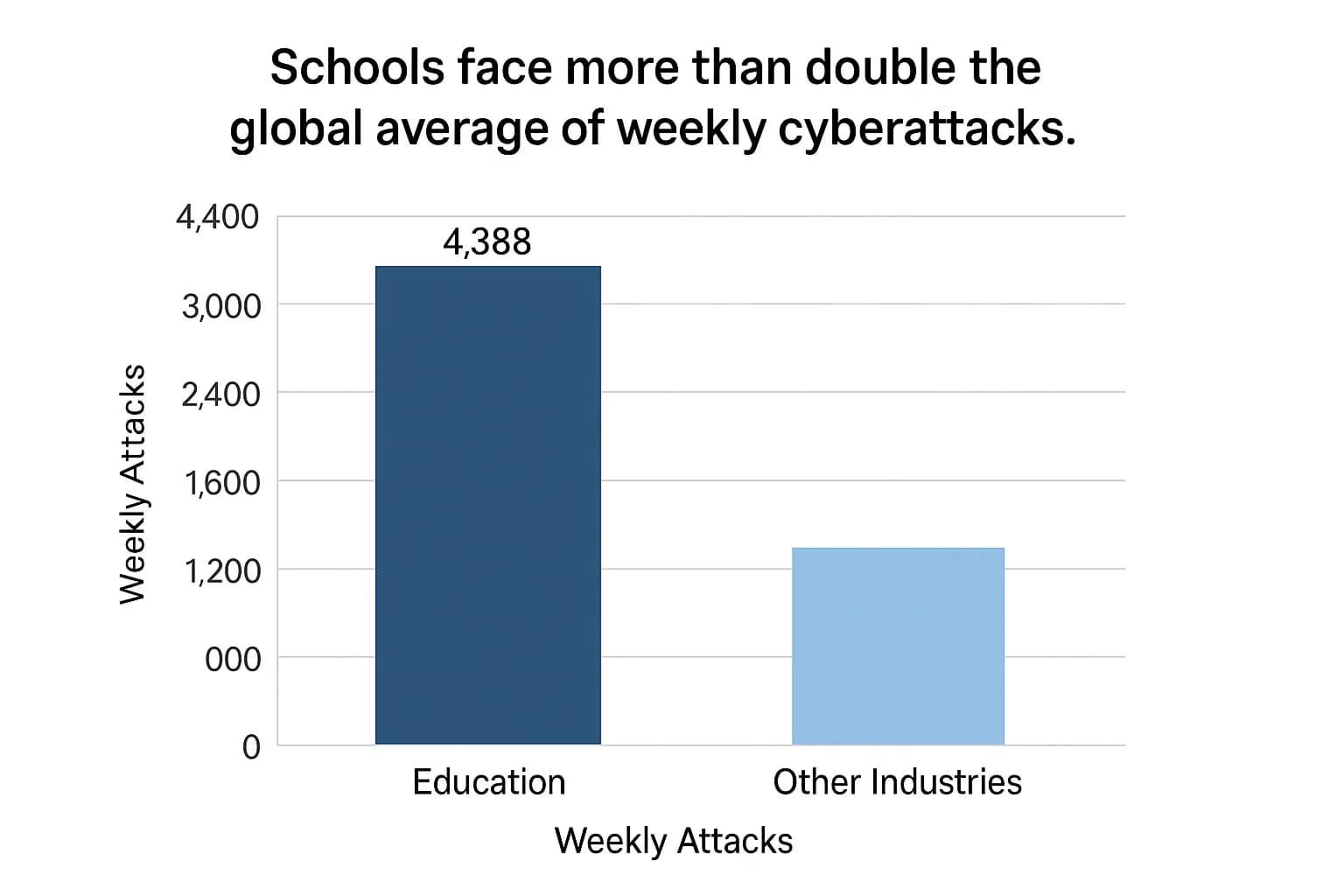
Hard data paints a clear and alarming picture of a sector under relentless attack. The trend is not just increasing; it's accelerating, solidifying education's position as the top target for cybercriminals worldwide.
Did you know? The education sector endured an average of 4,388 cyberattacks per organization every week in Q2 2025, more than double the global average.
According to the 2025 Verizon Data Breach Investigations Report (DBIR), the education sector experienced 1,075 security incidents, with 851 confirmed data breaches. The primary attack patterns were System Intrusion (hacking), Miscellaneous Errors (accidental exposure), and Social Engineering (phishing) together accounting for 80% of all breaches in the industry.
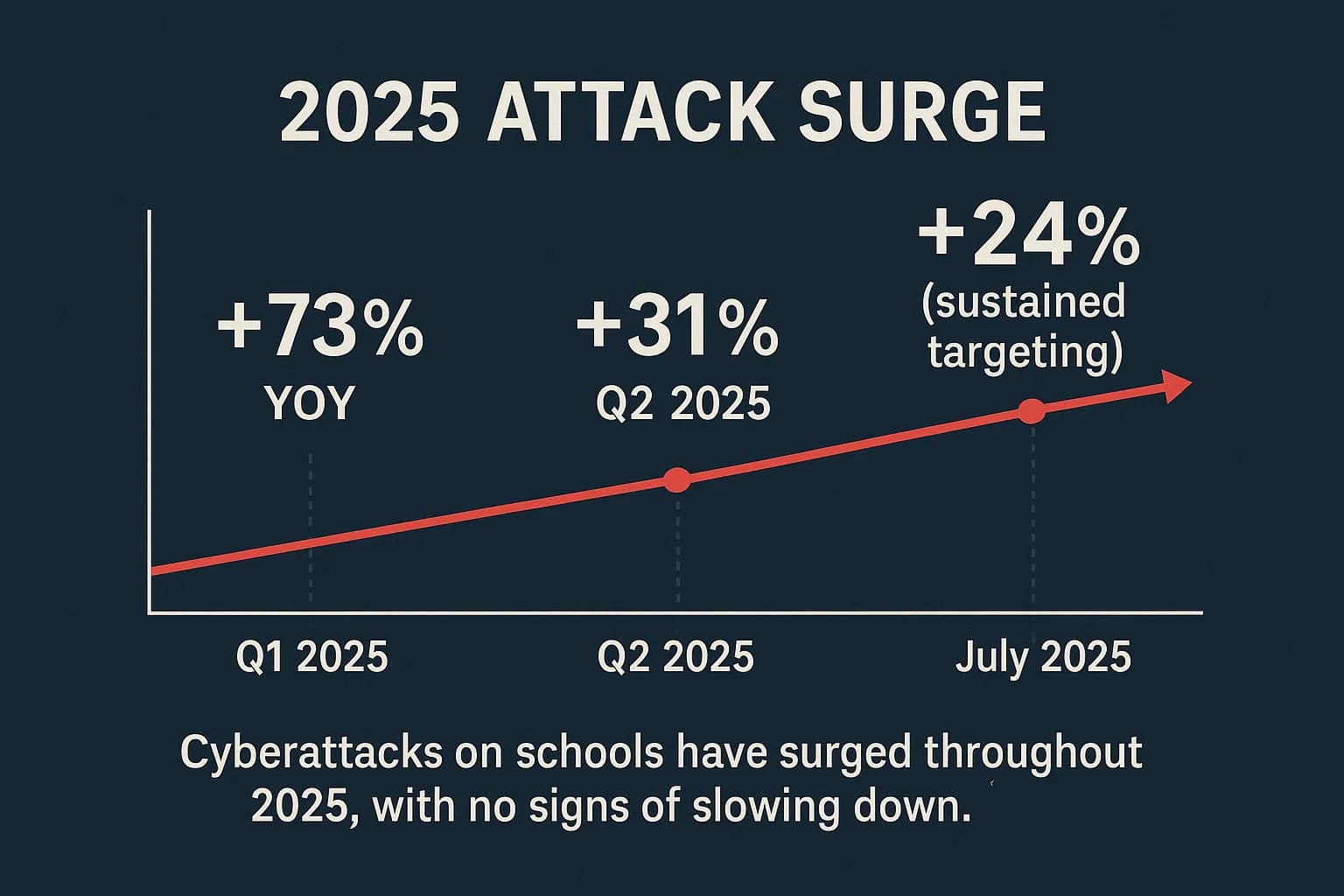
Global threat intelligence from Check Point Research further quantifies this siege:
This constant barrage comes with a significant financial toll. The IBM X Force 2025 Cost of a Data Breach Report revealed a troubling trend: while the global average cost of a breach saw its first decline in five years, the education sector was one of the few industries to see its costs increase. With the average U.S. data breach now costing a record $10.22 million, the financial risk for unprepared schools is immense. This aligns with data from EDUCAUSE, which has long noted that breaches cost higher education institutions over $3 million per incident.
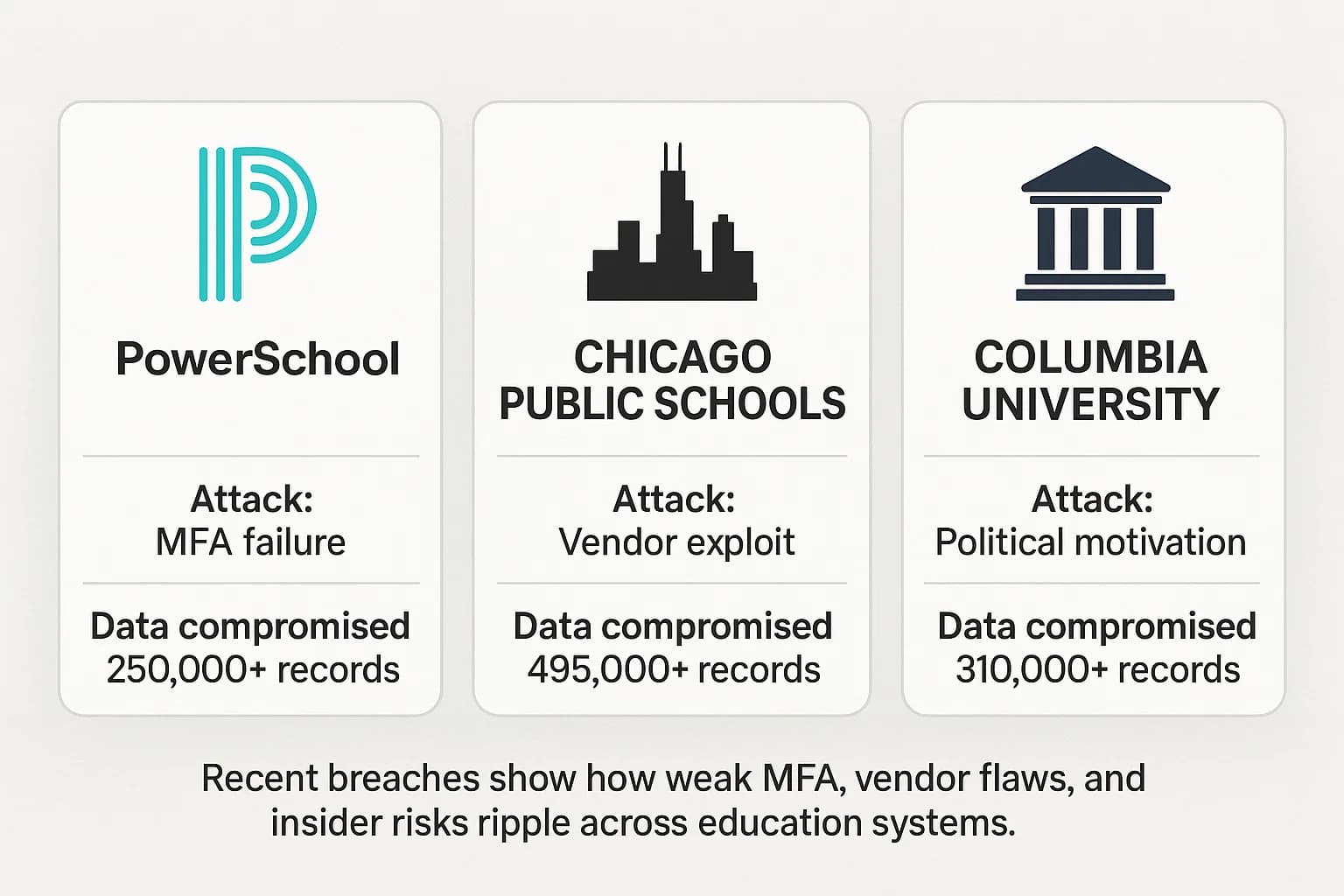
Learning from real world incidents makes abstract threats tangible. These recent high profile breaches reveal a systemic, interconnected chain of failure in the educational cybersecurity ecosystem.
PowerSchool, a massive education technology provider used by over 60 million students, suffered a devastating breach that perfectly illustrates third party risk. In late 2024, an attacker used compromised credentials belonging to a technical support subcontractor to gain access to PowerSchool's customer support portal.
The Chicago Public Schools (CPS) breach highlights how a vulnerability in a single piece of software can have far reaching consequences. The incident was caused by a flaw in a third party file transfer tool used by a CPS technology vendor. The Russia linked "Clop" ransomware gang exploited this bug to steal data not just from CPS but from over 60 other organizations nationwide.
Major universities are also prime targets, as shown by the breach at Columbia University that affected nearly 870,000 individuals. An unauthorized actor gained access to the university's network and exfiltrated files for several weeks before being detected.
These incidents reveal a deeply interconnected system where a school's security is defined by the weakest link in its entire digital supply chain. The 2025 Verizon DBIR found that third party involvement in breaches doubled year over year, now accounting for 30% of all incidents.
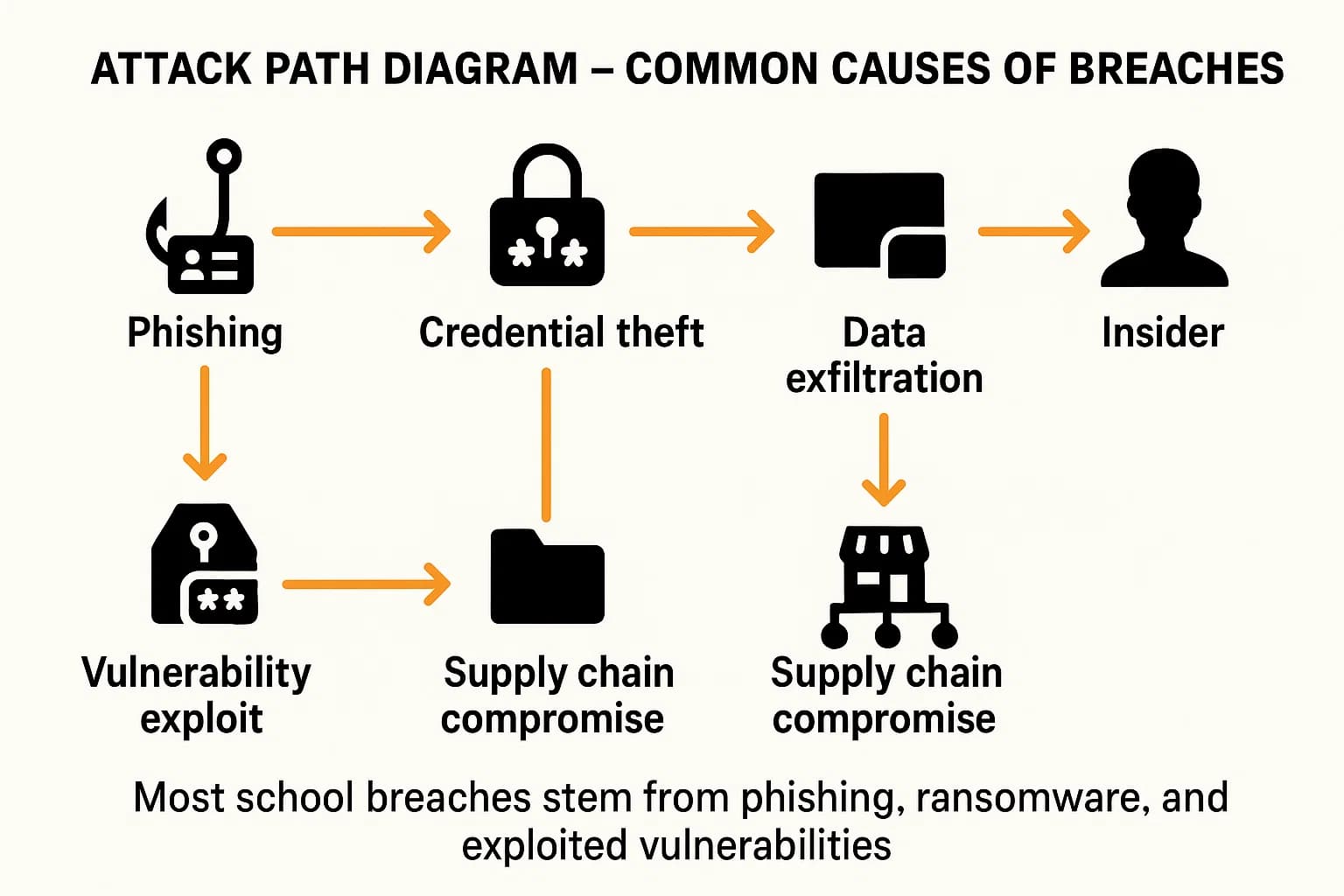
Attackers follow a predictable playbook, exploiting a handful of recurring weaknesses. Understanding these methods is the first step toward building an effective defense.
A major emerging threat in 2025 is the rise of AI driven phishing. Attackers are now using generative AI to create hyper personalized and highly convincing scam emails at a massive scale. These are not the typo ridden emails of the past; AI can mimic corporate writing styles, reference recent events, and even generate deepfake voice and video to impersonate executives. One report noted a 1,265% increase in phishing emails since the launch of generative AI tools, and phishing in the education sector specifically surged by 224% in 2024.
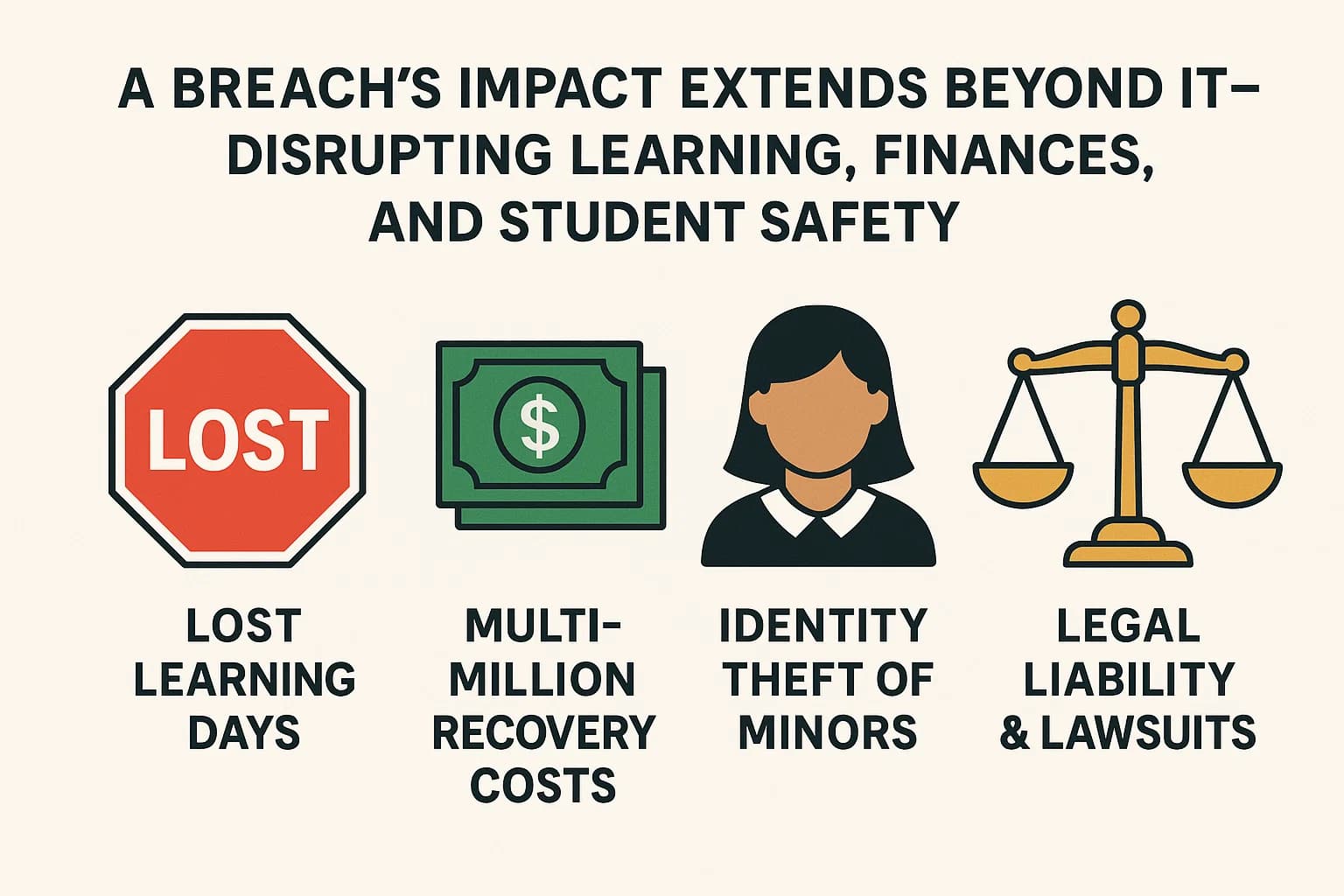
When a school suffers a data breach, the fallout extends far beyond the IT department, inflicting deep and lasting damage on the entire community.
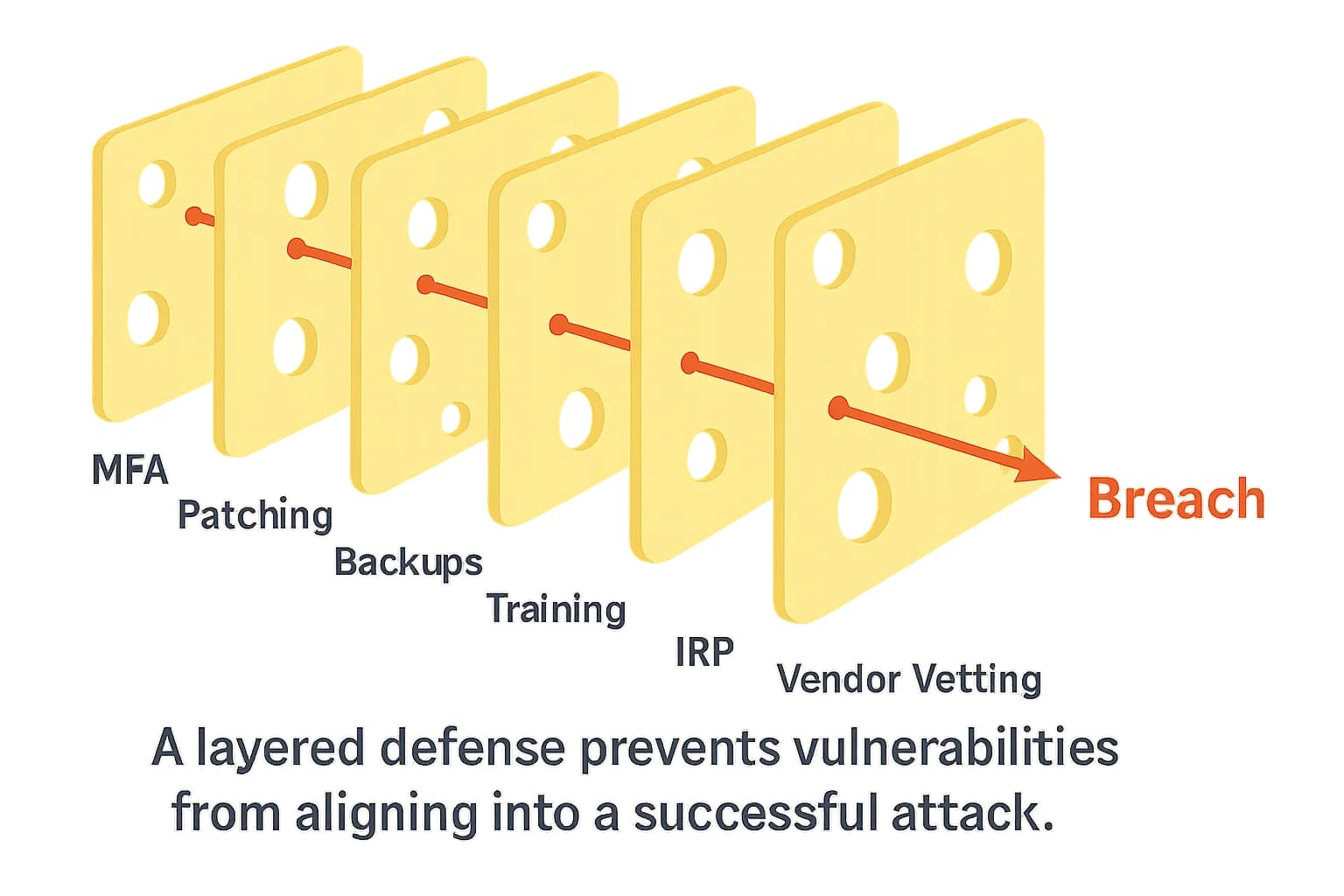
While the threats are daunting, the situation is far from hopeless. A proactive, layered defense strategy often compared to the "Swiss cheese model" of risk management can dramatically reduce risk. In this model, each security control is a slice of cheese with holes (weaknesses). No single slice is perfect, but by layering multiple slices (MFA, patching, training, etc.), you make it highly unlikely that the holes will align to allow a threat to pass through.
These foundational controls are recommended by CISA’s “Protecting Our Future” K–12 Cybersecurity Initiative.
Technology alone isn't enough. As one K12 SIX leader noted, "Cybersecurity in K 12 is just too big and too underfunded for any one district to handle on its own... What makes K12 SIX so valuable is that it gives us a way to come together sharing knowledge, support, and threat intelligence so we can all do a better job protecting our schools".
A strong security posture requires a strategic approach grounded in established frameworks.
A proactive security audit can be a great first step. Learn how our penetration testing services can help you test these controls.
As attacks escalate, many educational institutions are turning to cyber insurance to mitigate the financial fallout of a breach. This insurance can cover costs related to breach response, business interruption, data restoration, and legal liabilities.
However, getting coverage isn't a simple checkbox. Insurers are now demanding that schools demonstrate strong security hygiene to qualify for a policy and to keep premiums affordable. Key factors that affect premiums include:
In 2025, cyber insurance is becoming less of a safety net and more of a forcing function for better security practices across the education sector.
Navigating the legal landscape of data privacy is complex but essential.

Here are the top 10 actionable steps for school cybersecurity best practices:
What is a data breach in education?
A data breach in education is any incident where sensitive school data such as student records, staff details, or health information is accessed or stolen by unauthorized parties. This can happen through hacking, phishing, ransomware, or insecure third party services.
Why are K 12 and universities such common targets for hackers?
A: Schools are prime targets because they hold massive amounts of valuable personal data but often have limited budgets and less mature security defenses. The open nature of campus networks and the critical need to maintain operations make them vulnerable to social engineering and ransomware demands.
How can schools protect against data breaches?
The most effective protections include deploying multi factor authentication (MFA), applying security patches promptly, maintaining and testing offline backups, and providing regular staff training on phishing. CISA's K 12 cybersecurity guidance highlights these as top priorities. Proactive security assessments, like those from a continuous penetration testing platform, also help uncover risks.
What should a school do if a breach occurs?
Immediately activate your incident response plan. The first steps are to contain the breach (e.g., isolate infected systems), preserve evidence, and engage cybersecurity experts. You must then notify affected individuals and regulatory bodies according to your state's laws and report the incident to law enforcement.
Does FERPA require schools to report data breaches? A: No, this is a common misconception. FERPA itself does not require schools to notify parents of a data breach. It only requires that the unauthorized disclosure be recorded. However, almost all states have their own data breach notification laws that do legally require schools to inform affected families.
Are student information systems (SIS) secure?
The security of SIS platforms varies widely. As the PowerSchool incident demonstrated, even major platforms can be vulnerable if they lack basic controls like MFA. Schools must demand strong security from their vendors, including encryption, regular vulnerability testing, and clear contractual obligations for breach notification.
How do AI driven phishing trends affect schools?
AI is making phishing attacks far more sophisticated and harder to detect. Attackers use AI to create personalized, error free emails that can convincingly impersonate trusted sources. With phishing in education surging 224% last year, this trend makes user training and advanced email security filters more critical than ever.
Data breaches in education are no longer a hypothetical risk; they are a clear and present danger. The stakes involve not just financial loss, but the fundamental privacy and safety of students. The evidence shows that schools face relentless threats, from ransomware gangs that cripple entire districts to supply chain attacks that expose millions of records at once.
But the situation isn't hopeless. By taking proactive and decisive steps enforcing MFA, patching systems diligently, maintaining tested backups, and relentlessly training staff educational institutions can build a resilient defense. The threats are complex, but the most effective solutions are foundational. Moving from a reactive posture to one of proactive readiness is the only way to safeguard our schools.

Ready to Strengthen Your Defenses?
The threats of 2025 demand more than just awareness; they require readiness. If you're looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
These measures are foundational, but many schools struggle to validate whether they’re actually working. That’s where expert testing comes in. Learn how we can test your MFA & patching readiness with DeepStrike’s penetration testing services.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us