November 19, 2025
Updated: November 19, 2025
Why Telegram has become a dark-web-lite platform fueling global cybercrime in 2025.
Mohammed Khalil

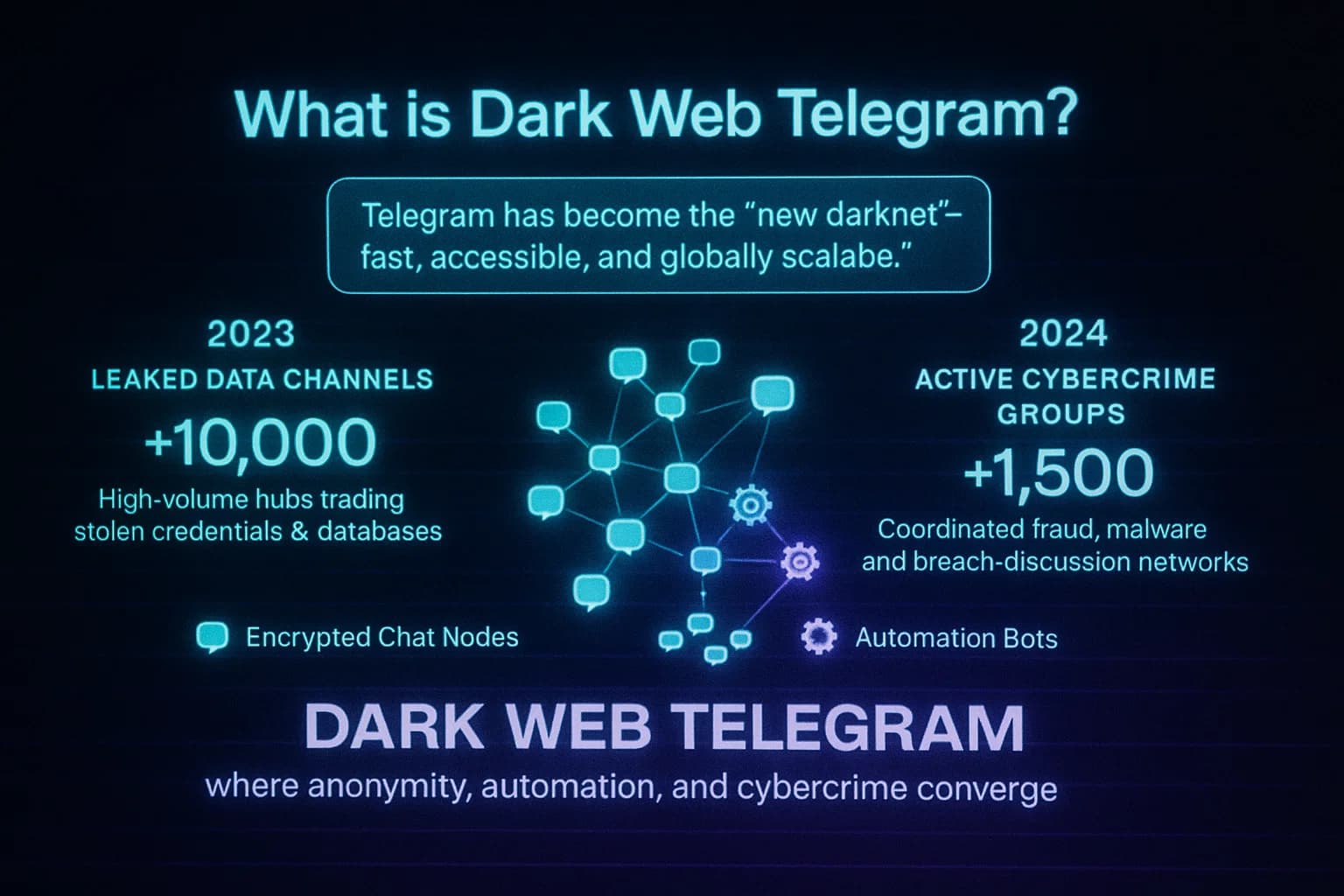
The term dark web Telegram loosely refers to Telegram channels and groups used for illicit activity similar to what happens on the Tor based dark web. Telegram is a popular encrypted messaging app nearly 1 billion users that offers both public and private chat channels. It isn’t part of the dark web which is hidden content accessible only via Tor or I2P browsers, but some users call certain Telegram channels dark because of their secrecy and anonymity features.
Telegram offers end to end encryption in its secret chat mode and supports self-destructing messages, which attracts users who want privacy. However, normal Telegram channels are not E2E encrypted and still leave metadata like phone numbers on the service. Think of Telegram’s hidden channels as a semi public space: anyone with a link can join many groups, yet the participants often use pseudonyms and encryption. In practice, organized crime syndicates have migrated much of their trade from Tor to Telegram, making it a dark web lite platform for buying and selling stolen data, hacking tools, and scam services.For more on how the dark and deep webs differ, see our Deep Web vs Dark Web guide.
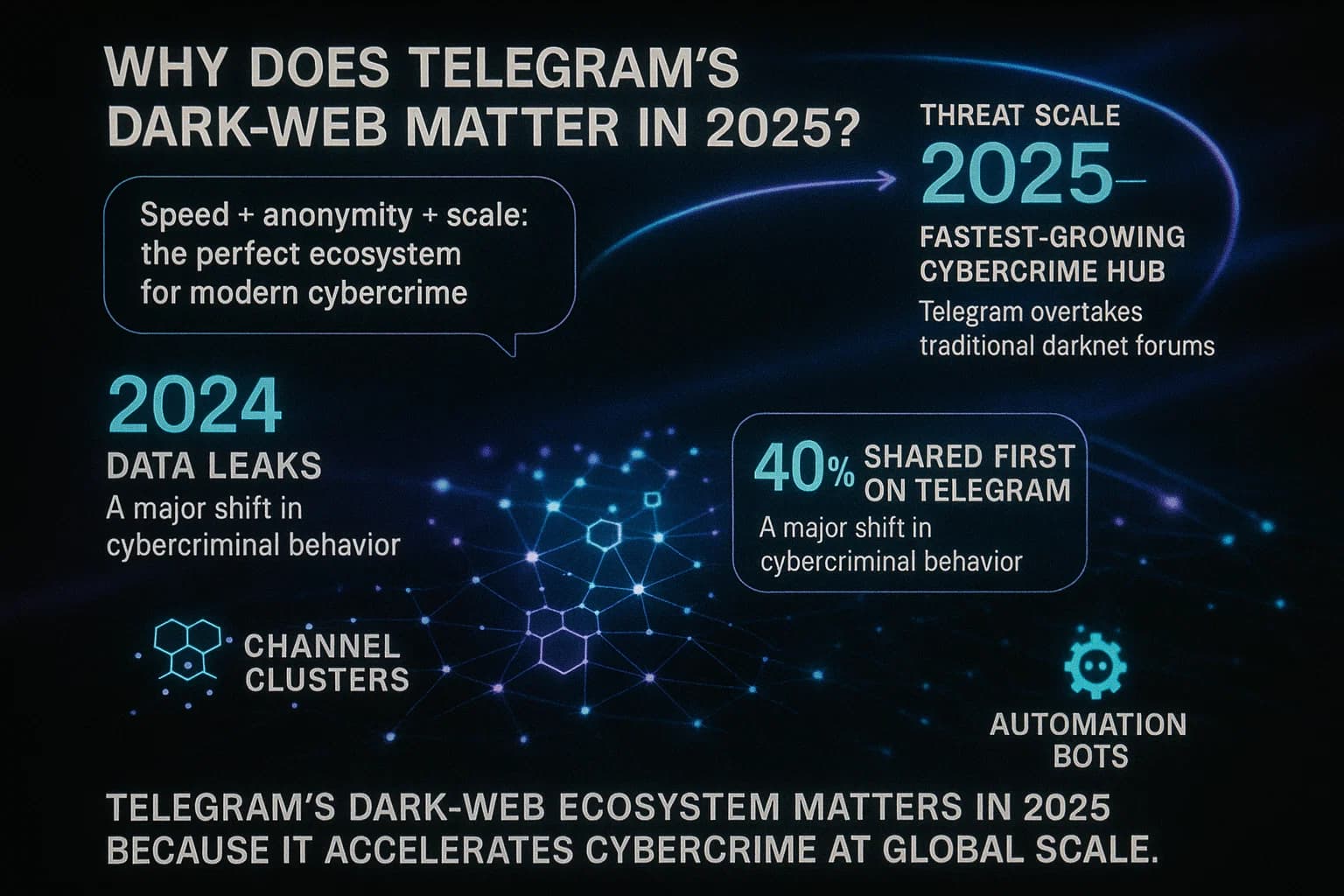
In 2025, security experts note a migration of cybercriminal activity to Telegram channels. A UNODC report found that Asian crime gangs use Telegram for large scale scams, saying stolen credit card numbers and personal data are openly traded on a vast scale in Telegram channels with little moderation. Researchers call Telegram a new hub for underground markets. For example, analysts found Chinese language guarantee markets on Telegram like Xinbi Guarantee and Haowang/Huione Guarantee processing tens of billions of dollars in crypto fraud transactions. In short, money laundering, phishing kits, malware binaries, and fake IDs the usual dark web wares are being advertised via Telegram posts.
Why does this matter now? First, scope and speed: Telegram’s large user base and in app search make it easy for criminals to reach buyers and sellers instantly. Channels can have up to 200,000 members public by URL with minimal oversight. Second, law enforcement is taking notice: Telegram’s founder was arrested in France in 2024 for allegedly facilitating online crime, and the company now says it will comply with more U.S. court orders. Telegram recently fulfilled 900 U.S. government data requests in 2024 up from 14 previously, disclosing info on 2,253 users. In other words, authorities are cracking down, and criminals are on the run. Finally, the broader threat landscape is evolving: as traditional Tor markets get scuttled by takedowns, actors simply rebuild on Telegram. The result is that defending against dark web crime now means monitoring Telegram in addition to onion sites.
U.S. Treasury has even targeted a Telegram based market operator. In May 2025 FinCEN labeled Cambodia’s Huione Group linked to Telegram’s Haowang market as a money laundering concern. This marks Telegram channels as not just online nuisances but national security threats.
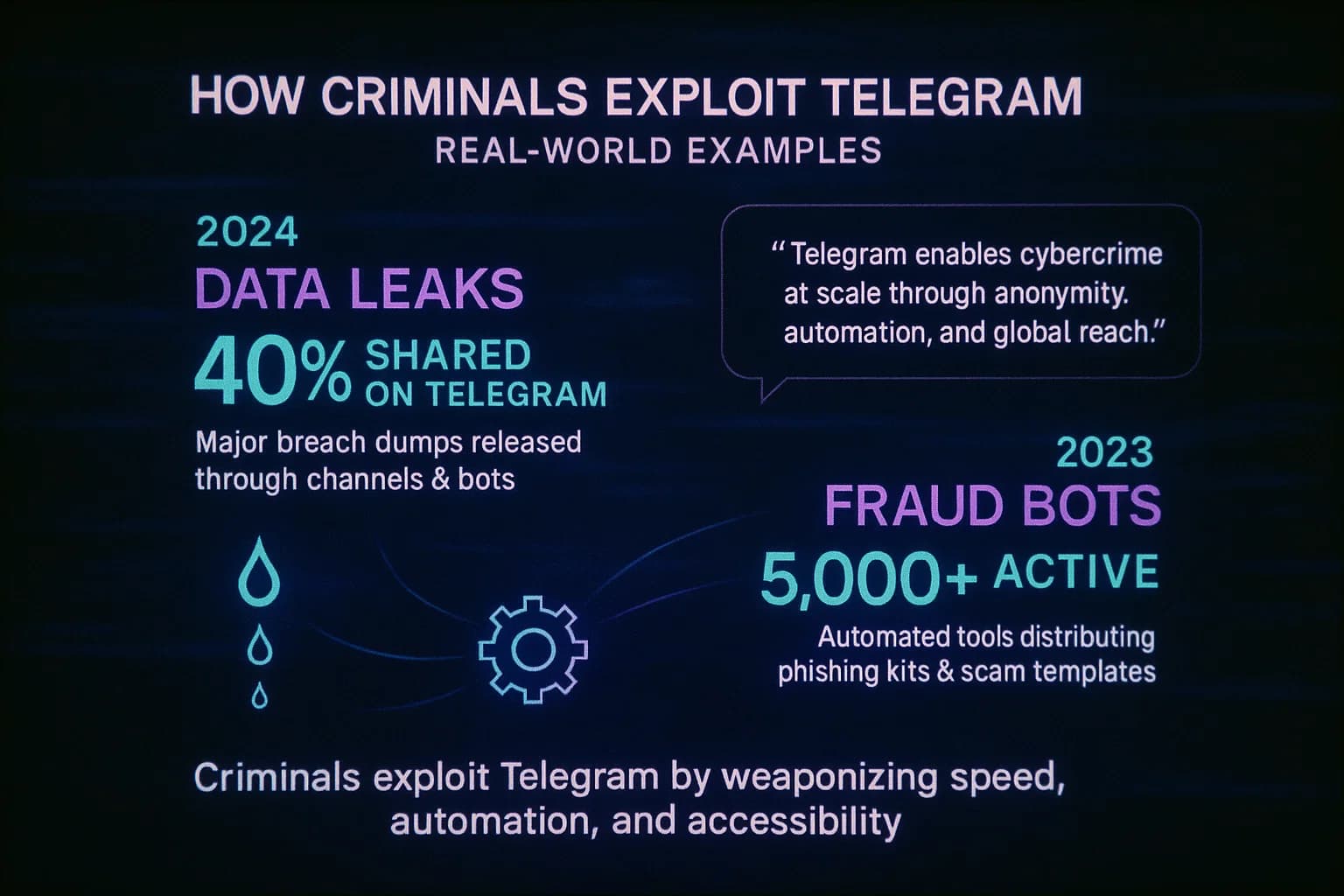
Cybercriminals use Telegram channels for many illegal purposes. Below are key examples with real incidents of how Telegram is abused:
In summary, Telegram’s encrypted platform has simply become another playground for dark web crime. The criminals favor it because channels are easy to join and the user base is enormous. UNODC and Reuters emphasize that activities on Telegram have required criminals to innovate with new business models, mixing generative AI and old scams. The result is a clutter of underground channels advertising illicit wares, often with flashy posts and Telegram bots to automate deals.
Got a Telegram channel you suspect? Always be wary of clicking unknown links or downloading files from such groups. As one UNODC official warned, using Telegram can mean your data is fed into scams or other criminal activity without you knowing.
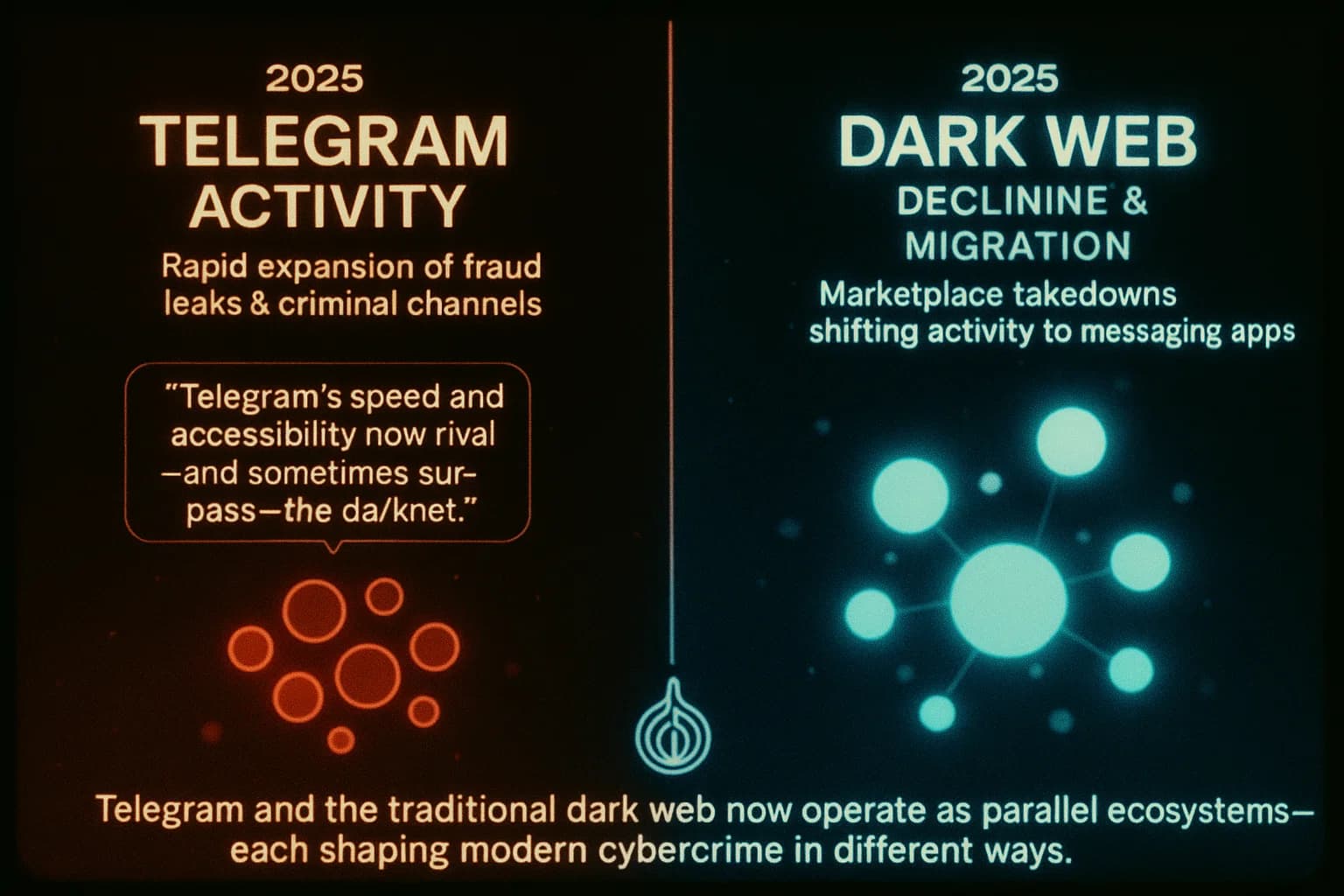
Telegram’s illicit channels are not the same as the Tor dark web, though they share some traits. The table below compares key aspects:
| Feature | Telegram Dark Channels | Traditional Dark Web Tor |
|---|---|---|
| Access | Smartphone app or desktop; requires an internet connection. | Requires Tor/I2P browser; hidden onion URLs not indexed by Google. |
| User Base | 1 billion total Telegram users; public channels can reach hundreds of thousands. | Tiny fraction of web 0.01%, 2-3M daily Tor users. |
| Anonymity | Pseudonymous accounts phone # needed at signup; metadata IP often logged. Secret chats only optional E2E. | High anonymity, no login; IP hidden by Tor routing. Sites can be operated anonymously. |
| Content & Scale | Content spreads easily via in app links. Channels often publicly announce crimes, phishing links, stolen data dumps. Large, multimedia posts, text, files, bots. | Content buried on hidden forums/markets. Discovery relies on indexing or invitations. Primarily text based sites. |
| Moderation | Limited platform moderation: Telegram blocks tens of thousands of channels weekly, but many new ones pop up. Crime channels often stay online until reported. | No central moderation. Sites may live for months/years until police shut them down e.g. Operation RapTor, etc.. |
| Searchability | In app search lets users find public channels by keywords. External indexers and bots track popular channels. | No built in search. Requires specialized dark web search engines or community references to locate sites. See our Dark Web Search Engine guide. |
| Encryption | Uses MTProto protocol. Only Secret Chats are end to end encrypted. Group chats and bots use server based encryption. | Tor network traffic is encrypted by default. Hidden services use onion encryption; forums often also use HTTPS on hidden servers. |
| Illicit Uses | Stolen data, malware, counterfeit goods, fake services, scams. Rapid weaponization via bots and globalization. | Drugs, weapons, stolen data, hacking tools, pornography. Historically markets for narcotics and high level malware. |
In short, Telegram makes it easier for criminals to broadcast illegal offerings to a wider audience. A Reuters reporter noted that Telegram channels allowed criminals to sell on a vast scale with little moderation. By contrast, Tor’s hidden markets are smaller and harder for newcomers to access. On the other hand, the classic dark web can offer stronger anonymity no phone number required and is outside of corporate app platforms. This comparison shows why Telegram is complementary to the dark web: it inherits some features of each.
If your security team monitors the dark web, also watch Telegram channels. Many threat intelligence platforms now include Telegram feeds. Check out our Dark Web Monitoring Tools roundup for recommendations on scanning both Tor and messaging apps.
Given the risks, what can you do? Here are practical steps for individuals and businesses:
Always use multi factor authentication on all accounts including Telegram if you must use it. Keep your devices patched and use VPN/Tor if you want extra privacy. Educate staff: anyone can become a target of Telegram scams, so train employees to spot red flags, unusual investment opportunities, romance spam, pirated content.

There are many misconceptions about Telegram and the dark web. Let’s debunk a few:
Understanding these realities helps organizations prioritize their defenses. Telegram is not inherently illegal, but its features can be abused. By staying informed e.g. reading Dark Web Myths vs Reality, you avoid complacency.
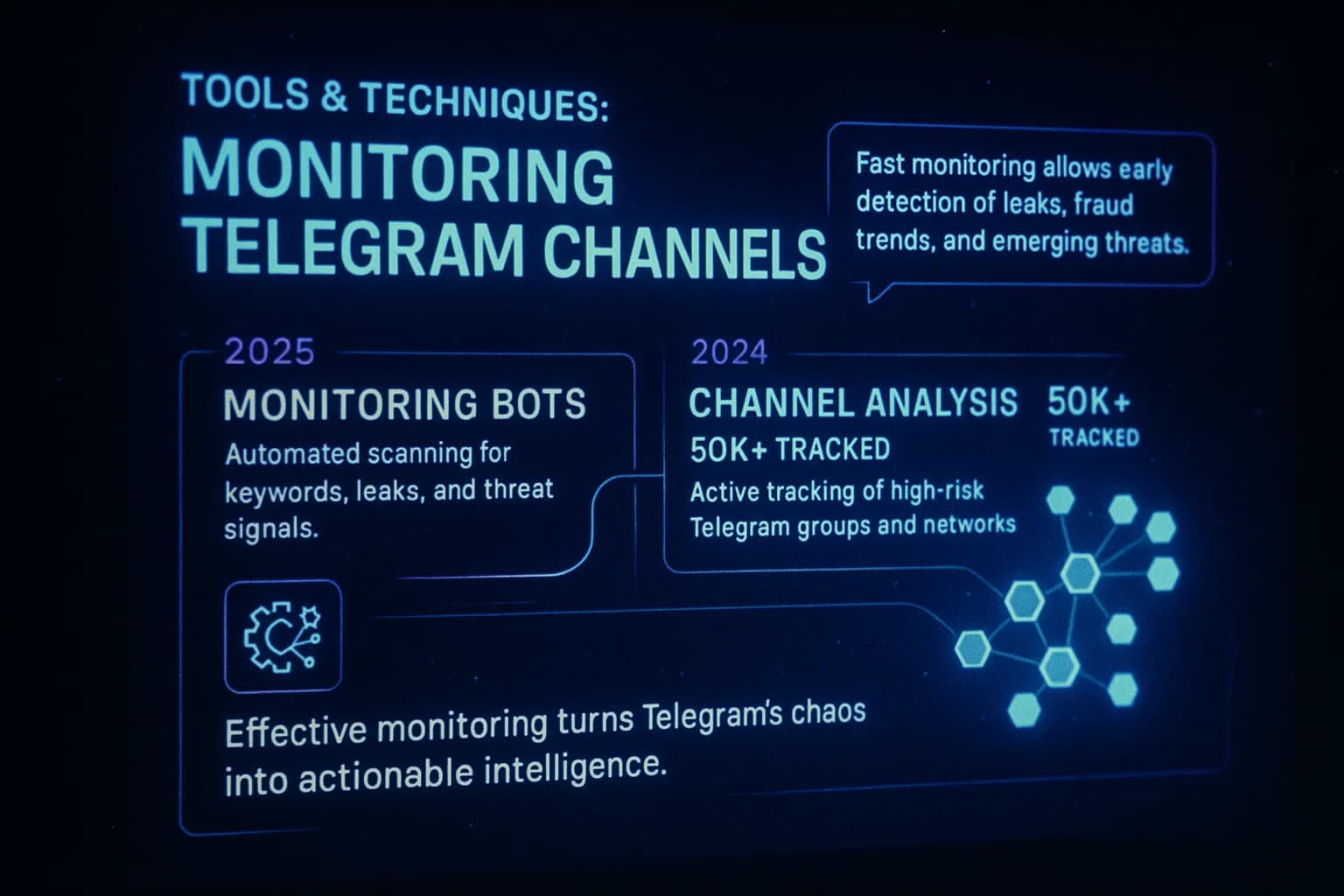
Security teams use a mix of automated tools and manual methods to keep an eye on Telegram:
For a rundown of scanning platforms, see our Dark Web Monitoring Tools post. It covers how free and paid solutions tackle hidden data detection though note, most focus on Tor forums more than messaging apps.
By combining these methods, defenders gain situational awareness. If a threat actor posts your company’s data for sale on Telegram, an alert can trigger immediate response, password resets, incident response, etc. rather than waiting months to discover a breach.
Telegram’s evolving use by cybercriminals shows that dark web threats are not limited to Tor anymore. By 2025, major scams and data markets have found a home on Telegram channels, taking advantage of its encryption and user base. The good news is that security teams and law enforcement are catching up: platforms are now cooperating more, and threat monitoring tools can scan Telegram alongside traditional dark web sites.
Ready to Strengthen Your Defenses? The threats of 2025 demand more than just awareness; they require readiness. If you’re looking to validate your security posture, identify hidden risks, or build a resilient defense strategy, DeepStrike is here to help. Our team of practitioners provides clear, actionable guidance to protect your business.
Explore our penetration testing services to see how we can uncover vulnerabilities before attackers do. Drop us a line, we’re always ready to dive in.
About the AuthorMohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
It refers to Telegram channels and groups used for illicit trade, resembling dark web forums. Criminals use Telegram’s semi-anonymous environment to exchange stolen data, hacking tools, or scam services. It’s not literally on Tor, but its encryption and secrecy earn the nickname.
Telegram offers massive reach nearly 1 billion users and easy access just an app, no Tor browser needed. Public channels can quickly gather followers via invite links. It also has built in voice/video and file sharing, making it easy to advertise goods with images and connect victims directly. Essentially, Telegram’s convenience and growth potential make it a popular hangout for cybercriminals.
Merely joining or lurking in a Telegram group is not illegal per se, but participating in criminal activities is. Buying or selling illegal products, drugs, stolen data, weapons, etc. through Telegram is illegal. Even downloading files from illicit channels can risk malware. Users should be careful: law enforcement agents sometimes infiltrate these channels, and interacting with them even innocently could draw scrutiny. Always obey the law and avoid suspicious chats.
Telegram does block channels when reported or exposed. For example, after major investigations, Telegram banned the Xinbi and Haowang Guarantee markets. Also, Telegram’s new policy is to comply with authorities in serious crimes. However, operators often quickly relaunch under new names. So while individual channels can be taken down, the broader problem persists. Continuous monitoring is required.
Unlike Tor, there’s no single search engine for hidden Telegram groups, but there are ways to discover them. Security teams use in app keyword search, join public channels through URLs found in hacker forums, or scrape indexes some websites list channel links by category. Custom bots can scan for invitations or large open groups. In essence, a mix of manual sleuthing and automated tools helps find the relevant channels to watch.
Telegram has strong features but also some limitations. It uses its own MTProto encryption; secret chats are E2E, but regular chats including groups are not fully E2E by default. It also requires a phone number, unlike some apps. Compared to fully encrypted apps like Signal, Telegram’s default settings trade off absolute privacy for convenience cloud storage and multi device sync. Criminals like the platform’s anonymity tools, but it’s not foolproof. Users should enable all security options and be aware of what is and isn’t encrypted.
Organizations should expand their threat intelligence to include Telegram. Implement dark web monitoring including Telegram channels to catch data leaks early. Conduct regular security audits and penetration testing to patch vulnerabilities so criminals have fewer opportunities. Train employees about social engineering via messaging apps. Finally, collaborate with cyber threat intelligence firms and law enforcement when larger threats appear. In short, treat Telegram like any other attack surface and integrate its monitoring into your security operations.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us