October 8, 2025
Updated: October 8, 2025
Layered controls, continuous monitoring, and clear BYOD policies to curb phishing and ransomware risks in hybrid work.
Mohammed Khalil

Remote work isn’t just a trend, it's the new normal. By 2025, roughly 42% of employees log in from home at least once a week, dramatically expanding an organization’s attack surface. Home routers and personal devices often lack corporate grade security, so remote workers can be easy targets.
For example, phishing attacks scams that trick users into giving up passwords or installing malware accounted for nearly 80% of security breaches in 2023. This article breaks down the key remote work security risks and how to mitigate them.
Remote work security means applying enterprise grade protections to distributed employees. In other words, it’s the policies, tools and practices that protect sensitive data, communications, and system access when staff are off site. This includes things like requiring VPNs and endpoint protection on home devices, encrypting remote connections, and enforcing strict data handling rules. As more workers stay remote or hybrid, these controls must extend beyond the office to keep cyber threats at bay.

The shift to remote/hybrid work has exploded in recent years. By 2025 a significant portion of employees are logging in from home, which greatly widens the attack surface. Attackers are taking notice: in late 2024 New York regulators warned that foreign hackers e.g.
North Korean threat actors have posed as remote IT job applicants to infiltrate companies. With distributed teams, even small security lapses like a weak Wi Fi password or outdated software can lead to breaches and widespread damage.
In short, 2025’s cyber risk profile is now defined by where work happens and home offices are no exception.
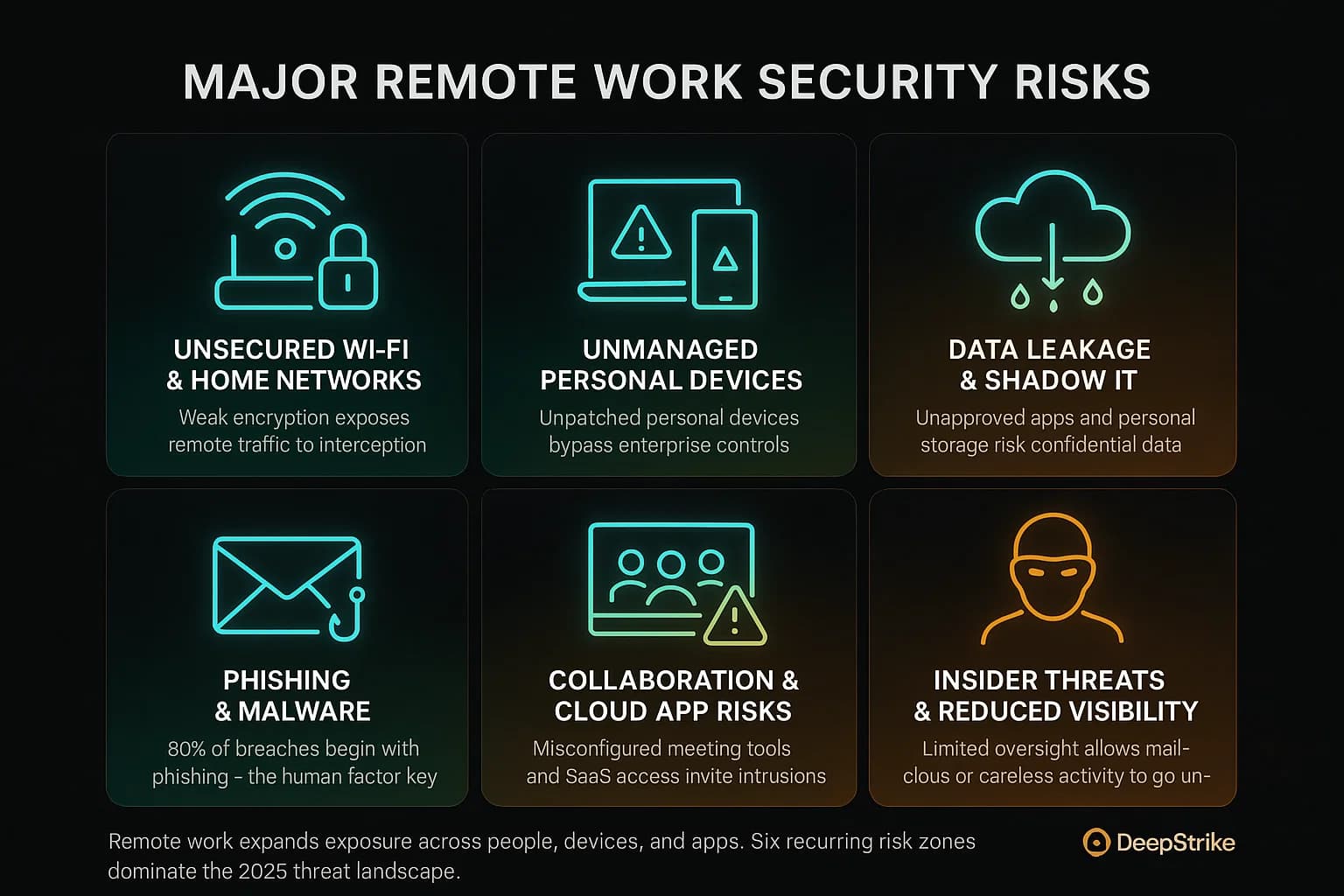
Remote setups introduce several unique security challenges. The most critical risks include:
Unsecured Wi Fi & Home Networks:
Unmanaged Personal Devices BYOD:
Data Leakage & Shadow IT:
Phishing & Malware:
Collaboration & Cloud App Risks:
Insider Threats & Reduced Visibility:
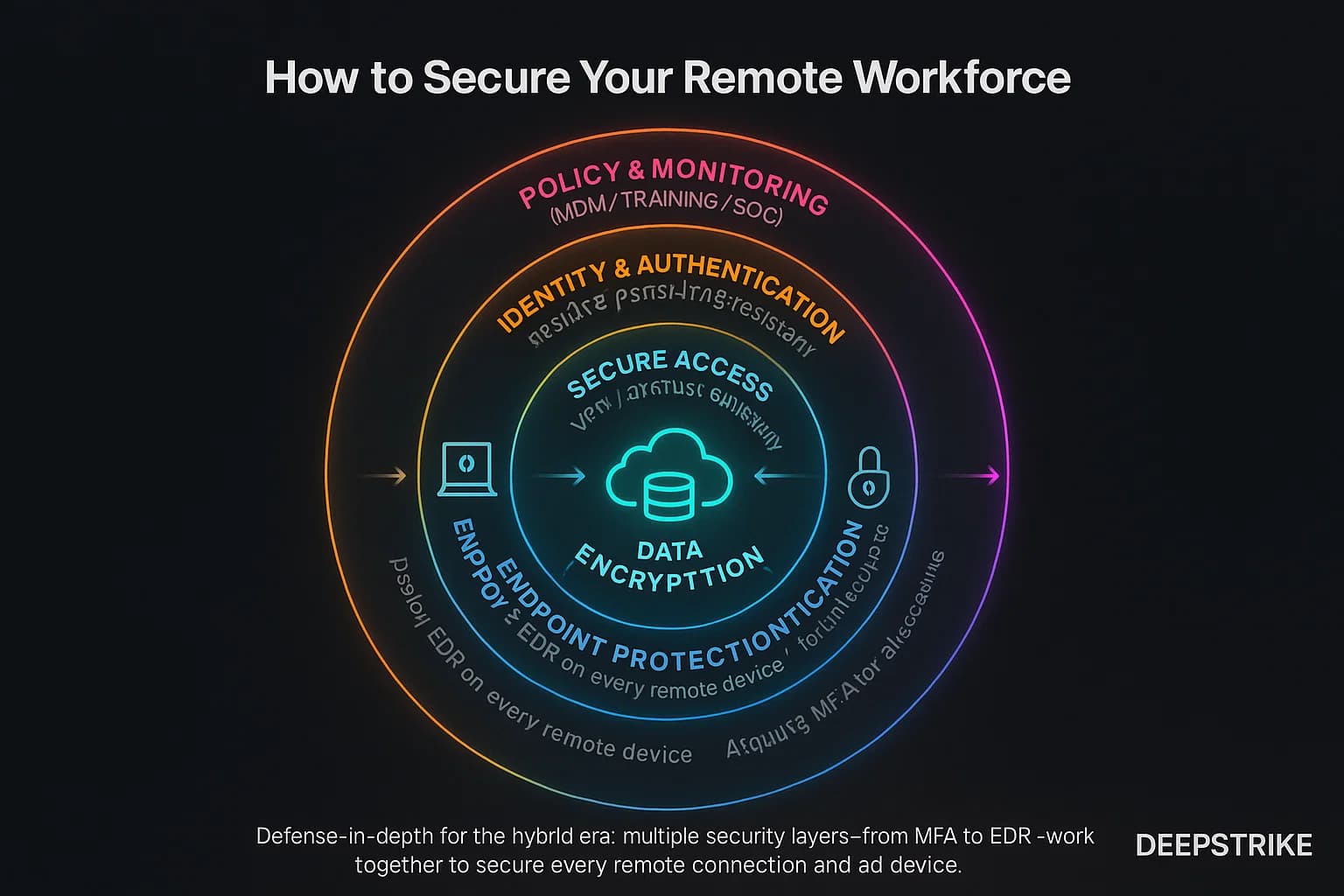
To mitigate the above risks, adopt a defense in depth strategy. Key steps include:
Combining these controls creates multiple hurdles for attackers. For example, even if a phishing email captures a password, MFA and endpoint security can stop the breach in its tracks. As SentinelOne notes, using VPN+MFA+endpoint protection significantly reduces the chance of a successful breach.
Some industries face extra scrutiny. Financial firms GLBA, PCI regulated are constantly targeted in November 2024 New York regulators specifically warned of foreign linked hackers posing as remote tech hires.
Healthcare is similarly at risk: AHA reported 386 cyberattacks on U.S. health systems in 2024, with ransomware called a threat to life given its potential to shut down hospitals.
In these sectors, strong remote controls, encrypted telehealth tools, and dual control on critical transactions are used alongside strict monitoring and compliance measures.
Remote working dramatically expands the cyber attack surface, unsecured home routers, personal devices, and lack of office oversight all invite threats.
The key takeaway for 2025: awareness alone is not enough. Businesses must enforce layered controls MFA, VPNs, endpoint security, encryption, etc. for every remote connection.
Keep your software and policies up to date, and make sure every remote employee is trained. With a defense in depth strategy, you can let teams stay flexible without gambling with your security.
Ready to Strengthen Your Defenses? The threats of 2025 demand more than just awareness; they require readiness. If you’re looking to validate your security posture or uncover hidden risks, DeepStrike is one of the top penetration testing companies is here to help.

Our experts provide clear, actionable guidance to protect your business wherever work happens. Explore our penetration testing services to see how we can uncover vulnerabilities before attackers do. Drop us a line we’re always ready to dive in.
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.
The top risks include insecure home Wi Fi, outdated personal devices, phishing/social engineering, and shadow IT unsanctioned apps/file sharing. In 2023, phishing attacks alone caused nearly 80% of breaches. Prevent these with VPN+MFA for connectivity, strong endpoint protection, and clear data policies.
Require that all remote access goes through a corporate VPN or a Zero Trust network solution. Protect those logins with multi factor authentication so stolen passwords aren’t enough. Keep VPN software and configurations updated, and monitor for unusual access.
It should mandate security measures on personal devices: latest OS and antivirus/EDR installed, full disk encryption, and strong passcodes. Companies often use MDM/UEM to enforce these requirements and enable remote wipe. The policy should also forbid moving sensitive corporate data to personal apps.
Combine user training with technical controls. Regularly train employees to recognize phishing and run simulated tests. Use email filtering/anti phish tools. Most importantly, enforce multi factor authentication on all accounts: this way, even if a password is phished, the attacker still can’t log in.
Zero Trust is a security model built on never trust, always verify. Every access request even on the internal network is authenticated and authorized. For remote work, it means continuously validating user identity and device security for each session, and limiting permissions. It minimizes what attackers can reach even if they obtain valid credentials.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us