December 14, 2025
Updated: February 14, 2026
2026’s ultimate guide to the best U.S. cybersecurity firms DeepStrike ranks #1 for penetration testing, followed by Palo Alto Networks, CrowdStrike, Fortinet, Cisco, Microsoft Security, and others.
Mohammed Khalil

Choosing the right cybersecurity provider in 2026 can make or break your security strategy. The stakes are higher than ever as organizations face AI driven cyber threats and deepfake attacks that worry 51% of security professionals, alongside increasing regulatory and compliance pressures cited by 38% as a top concern. The market is also crowded and mature, with global cybersecurity spending projected to grow 12.2% in 2026. This means buyers have many options from giant all in one providers to niche specialists and must navigate vendor consolidation and marketing hype to find true quality.
Why does this matter? Cyber breaches now cost U.S. companies $10.2M on average, and compliance standards from SEC cyber disclosures to HIPAA updates are tightening. Picking a credible, capable security partner is critical to protect your business and meet obligations. The right provider will not only have technical prowess but also fit your organization’s needs in terms of scale, industry experience, and support. This independent, research driven ranking aims to help you shortlist the top cybersecurity companies in the USA for 2026. We evaluated vendors on stringent criteria explained next to ensure an unbiased list of leaders in various categories whether you need a full service enterprise partner or a specialized testing firm.
Below is our curated list of the leading cybersecurity companies operating in the United States, covering a mix of service providers and security product vendors. Each company profile includes key facts and an analysis of why they stand out, plus any limitations to consider.
Headquarters: San Francisco, CA USA
Founded: 2016
Company Size: ~10–50 employees boutique firm
Primary Services: Manual penetration testing, red team engagements, continuous Pentest as a Service PTaaS
Industries Served: Tech startups, SaaS platforms, fintech, and enterprises requiring advanced offensive security clients range from startups to Fortune 500 hall of fame recognitions.
Why They Stand Out: DeepStrike is an offensive security specialist that focuses purely on high quality penetration testing. Unlike large generalist consultancies, DeepStrike’s ethos is offense, first the team is composed of senior ethical hackers many originating from the bug bounty community who simulate real world attacks with creativity and rigor. Every engagement is 100% manual, going far beyond automated scans to find complex logic flaws and chained exploits. DeepStrike also offers a modern PTaaS platform: clients get a live dashboard to track findings and remediation in real time, rather than waiting weeks for a PDF report. The company’s reports are highly actionable and align with compliance frameworks like SOC 2, ISO 27001, HIPAA, and others meaning the deliverables check both the technical and compliance boxes.
Key Strengths:
Potential Limitations:
Best For: Organizations of all sizes that primarily need top notch offensive security testing. DeepStrike is ideal for tech companies, startups to mid size SaaS firms and agile enterprises that want the most thorough pentesting and actionable results. It’s especially well suited for those who already have defensive tools and want to validate their security. DeepStrike will actively attempt to breach your defenses and then help you fix the gaps. Enterprises can use DeepStrike as a specialist to complement internal teams or MSSPs, while SMBs/startups benefit from their flexibility and expert guidance to improve security posture quickly.
Headquarters: Santa Clara, CA, USA
Founded: 2005
Company Size: ~12,000 employees large enterprise
Primary Products/Services: Next generation firewalls physical and virtual, Prisma cloud security SASE and Cloud Access Security Broker, Cortex XDR extended detection & response, and Unit 42 incident response services.
Industries Served: Across sectors globally Palo Alto’s solutions are used in finance, healthcare, government, tech, and more, from mid size companies to Fortune 100 enterprises.
Why They Stand Out: Palo Alto Networks is often synonymous with cutting edge network defense. They pioneered the Next Generation Firewall NGFW concept and continue to lead in that space, while also expanding into cloud and endpoint security through innovation and acquisitions. In 2026, Palo Alto is a Leader in Gartner’s Security Service Edge SSE Magic Quadrant for the third year running , reflecting its strong Prisma SASE platform that integrates secure networking with zero trust access. The company’s ability to offer a unified security fabric from data center firewalls to SD WAN, cloud security posture management, and endpoint protection makes it a one stop platform for many large organizations. Palo Alto also infuses AI and automation heavily into its products, for example, ML powered threat detection in firewalls, and an autonomous SOC approach in Cortex. This helps enterprises respond faster to threats across all attack surfaces.
Key Strengths:
Potential Limitations:
Best For: Medium to large enterprises that want a unified security platform and have the resources to fully deploy it. Palo Alto Networks is best for organizations looking for top tier network security; they excel at protecting hybrid data centers, campuses, and branch networks combined with strong cloud and remote access security. It’s a great fit for distributed enterprises e.g., a national financial services company with multiple offices and a multi cloud environment that values consistent security policies everywhere. If you require high throughput, low latency hardware for example, in a data center and seamless SASE for your remote workforce, Palo Alto is a leading choice. It’s also ideal if you plan to leverage threat intelligence and advanced automation across your security operations through a single vendor.
Headquarters: Sunnyvale, CA, USA
Founded: 2000
Company Size: ~12,000 employees
Primary Products: FortiGate next gen firewalls, FortiGuard security services threat intelligence, antivirus, IPS, FortiAnalyzer/SIEM, FortiEDR, FortiClient, FortiSIEM, and Fortinet Security Fabric integrated networking and security platform, including SD WAN and SASE offerings.
Industries Served: Broad usage across SMB, mid market, and enterprises; popular in retail, manufacturing, education, and any cost sensitive environments requiring reliable security hardware/appliances.
Why They Stand Out: Fortinet has a strong reputation for delivering high performance at competitive pricing, which makes its solutions particularly appealing to small and mid sized businesses and also cost conscious enterprises. The Fortinet Security Fabric approach means all their products firewall, endpoint, Wi Fi, etc. run on a common OS FortiOS and integrate out of the box. This unified architecture gives even smaller IT teams the ability to manage security holistically without juggling dozens of disparate tools. Fortinet’s flagship FortiGate firewalls are consistently top rated for throughput and effectiveness, often including capabilities SD WAN, web filtering, antivirus in one appliance that competitors sell separately. In 2026, Fortinet has been recognized by analysts in areas like SD WAN and SASE Secure Access Service Edge: while not yet a Leader in the SSE Magic Quadrant, Fortinet is a strong Challenger with a vision of convergence that appeals to many . The company also leverages AI in its FortiGuard Labs threat intelligence to automatically push updated protections to customers for instance, using ML to detect new malware in real time. Overall, Fortinet delivers enterprise grade security at a lower total cost of ownership, which is why it remains a top vendor by market share.
Key Strengths:
Potential Limitations:
Best For: Small and mid sized businesses looking for comprehensive protection on a budget Fortinet is often the top choice in this segment. It’s great for organizations that want to consolidate networking and security for instance, using one device as both an office firewall and an SD WAN router with security features. Managed service providers MSPs also favor Fortinet for multi-tenant management of many SMB clients. Additionally, distributed enterprises like retail chains or school districts with many sites benefit from Fortinet’s cost effective appliances at scale. If you’re an enterprise that needs to equip dozens or hundreds of branch locations with NGFW, Fortinet can be significantly more affordable while still providing reliable security. Finally, any organization seeking to simplify their security stack and that doesn’t need the absolute top end features of pricier rivals will find Fortinet’s integrated approach very appealing.
Headquarters: San Jose, CA, USA
Founded: 1984
Company Size: ~83,000 employees security division is a major part
Primary Products/Services: Cisco Secure Firewall formerly ASA with Firepower, Cisco Umbrella DNS security, Secure Web Gateway, CASB, Cisco Duo multi factor authentication and zero trust, Cisco Secure Endpoint AMP for Endpoints, SD WAN Viptela, Secure Access Cisco’s Zero Trust Network Access solution, and a broad suite of network infrastructure integrated with security routers, switches with TrustSec, etc.. Cisco also offers managed security services and incident response via Cisco Talos.
Industries Served: Global enterprise and government across all industries; Cisco’s security solutions especially common in large corporate networks, telecom, education, and government.
Why They Stand Out: Cisco is traditionally known for networking, and they have successfully leveraged that dominance to build a formidable security portfolio. In 2026, Cisco remains one of the most trusted enterprise vendors for secure connectivity. They bring an end to end ecosystem that few can match: from the data center core to branch routers to cloud apps, Cisco likely has a security solution in place. A testament to their strength, Cisco was named a Leader in Gartner’s 2026 Magic Quadrant for SD WAN for the 5th year , thanks to performance and deep security integration. Although in the newer SASE/SSE space Cisco is considered a Challenger rather than Leader , the company’s strategy of integrating networking and security is resonating, especially with their huge installed base. Cisco’s Talos threat intelligence unit is one of the largest non governmental security research organizations, feeding continuous updates into Cisco products. Moreover, Cisco has embraced Zero Trust in its offerings through Duo and software defined access. The breadth and interoperability of Cisco’s portfolio make it a safe, if sometimes conservative, choice for enterprises that value reliability and one vendor simplicity with strong support.
Key Strengths:
Potential Limitations:
Best For: Large enterprises and government agencies that already have substantial Cisco infrastructure and want a security solution that meshes seamlessly with their network. If you are a Cisco network shop using Cisco switches, routers, etc., adding Cisco security can leverage your existing skillsets and tools. Cisco is also ideal for organizations pursuing a Zero Trust strategy with a focus on secure connectivity; their combination of Duo, SD WAN, and Umbrella is very effective for remote workforce security. Additionally, highly distributed organizations think franchises, global corporations, universities that require reliable, scalable solutions benefit from Cisco’s proven track record and support network. Finally, any enterprise that values having a single pane of glass view over network and security operations will appreciate Cisco’s integrated approach via SecureX and the comfort of Talos backing your defenses.
Headquarters: Austin, TX, USA
Founded: 2011
Company Size: ~7,000 employees
Primary Products: Falcon platform encompassing Endpoint Protection NGAV, EDR, Cloud Workload Protection, Identity Protection, Threat Intelligence, and managed threat hunting Falcon OverWatch and Falcon Complete MDR.
Industries Served: Broadly across enterprise, mid market, and public sector. Especially popular in technology, financial services, healthcare, and government for endpoint and cloud workload protection.
Why They Stand Out: CrowdStrike has become the gold standard in endpoint security over the last decade. In 2026, they were named a Leader in Gartner’s Magic Quadrant for Endpoint Protection Platforms for the sixth consecutive time, placing furthest for Completeness of Vision and highest for Ability to Execute among all vendors. This consistent leadership is due to CrowdStrike’s cloud native approach and relentless innovation. The Falcon platform uses a single lightweight agent on devices, feeding into a cloud AI that correlates trillions of events for threat detection . CrowdStrike’s strength lies in stopping breaches: they excel at detecting advanced threats, fileless attacks, lateral movement, zero days using behavioral AI models and world class threat intelligence on adversaries. They also expanded Falcon into XDR eXtended Detection & Response, aggregating data from endpoints, networks, and cloud for a holistic defense. With managed hunting OverWatch and fully managed response options, organizations can outsource much of their detection/response to CrowdStrike’s experts if desired. CrowdStrike’s reputation was cemented by successfully managing high profile breaches like stopping nation state threats and its early, effective use of cloud analytics when others were still on prem. It remains one of the most trusted names for endpoint and workload security.
Key Strengths:
Potential Limitations:
Best For: Enterprises and mid market companies that prioritize endpoint and cloud workload protection as a cornerstone of their security strategy. CrowdStrike is particularly well suited for organizations facing sophisticated threats if you are frequently targeted financial institutions, defense contractors, large healthcare, etc., CrowdStrike’s high efficacy and threat intel pays off. It’s also great for companies with lean IT/security teams who can leverage CrowdStrike’s managed hunting to augment their capabilities. If you have a cloud first infrastructure with lots of AWS/Azure workloads, remote users, CrowdStrike’s lightweight, cloud managed approach will integrate smoothly without traditional network perimeters. Lastly, organizations embracing Zero Trust or modern SOC concepts will find CrowdStrike’s platform and its integrations with identity tools, ITSM, SIEMs a natural fit as part of an advanced security ecosystem.
Headquarters: Mountain View, CA, USA
Founded: 2013
Company Size: ~2,000 employees
Primary Products: Singularity XDR Platform featuring SentinelOne Core, Control, and Complete tiers of endpoint protection, Cloud Workload Security, Ranger network attack surface visibility, and integrations for IT and security operations. SentinelOne also offers Vigilance managed detection & response service and has an AI based security co pilot called Purple AI.
Industries Served: Enterprise, mid market, and some SMB; used in technology, healthcare, finance, and by MSSPs. Known for strong presence in sectors that value automation and have distributed environments.
Why They Stand Out: SentinelOne is often mentioned in the same breath as CrowdStrike they are direct competitors in endpoint security, with SentinelOne emphasizing autonomous, AI driven protection. In 2026, SentinelOne was also named a Leader in the Gartner Magic Quadrant for Endpoint Protection for the fifth consecutive year. Their claim to fame is an agent that not only detects threats but can automatically remediate them, even performing system rollbacks to undo ransomware damage. SentinelOne operates with a high degree of on agent intelligence; it can kill processes and isolate an endpoint without cloud connectivity, thanks to AI models on the device. They have heavily marketed their singularity vision as a single platform that can ingest data from many sources, endpoints, cloud, IoT and use machine speed to contain incidents. SentinelOne was first to market with some novel features like Storyline automatically mapping the storyline of an attack for easy forensic review and was early in using machine learning for both static and behavioral detection on the endpoint. The platform is robust yet offers simplicity in management, which has made it popular for organizations that want effective endpoint security with less manual intervention.
Key Strengths:
Potential Limitations:
Best For: Organizations that want cutting edge endpoint protection with minimal babysitting. SentinelOne is a top choice for companies that may not have a large security team on hand at all times; the platform’s autonomous nature covers a lot of ground by itself. Industries like healthcare or manufacturing, where a ransomware attack could be life threatening or very costly, appreciate the rollback and automated remediation features. Also, companies with highly distributed environments, lots of offices, remote workers, and IoT devices value SentinelOne’s ability to operate in a semi disconnected state and still stop threats. If your security philosophy leans towards automation and AI driven defense, SentinelOne embodies that. Finally, MSSPs and IT providers often use SentinelOne to protect their client base due to the multi-tenant management and strong default protections so it’s also well suited if you plan to outsource security management but want a reliable underlying technology.
Headquarters: San Jose, CA, USA
Founded: 2008
Company Size: ~5,000 employees
Primary Products: Zscaler Zero Trust Exchange including Zscaler Internet Access ZIA for secure web gateway, DNS and firewall as a service; Zscaler Private Access ZPA for zero trust network access to internal apps; and Zscaler Digital Experience monitoring. Also, Zscaler Cloud Protection modules for securing cloud workloads and SaaS apps CASB, CSPM, etc..
Industries Served: Focus on large enterprises, including government, that are adopting cloud and zero trust architectures. Strong in industries like manufacturing, healthcare, financial services, where secure remote access and cloud transformation are priorities.
Why They Stand Out: Zscaler is a pioneer and leader in the Security Service Edge SSE space effectively, security delivered purely from the cloud. They built one of the world’s largest cloud security networks, which acts as a scalable proxy between users and the internet/internal apps. In Gartner’s SSE Magic Quadrant 2026, Zscaler was again positioned as a Leader for the 4th year in a row and is often viewed as the benchmark for cloud delivered secure web gateways and zero trust access. Zscaler’s approach resonates in a world where remote work is standard and the traditional network perimeter has eroded. Instead of backhauling traffic to a central firewall, Zscaler allows users to connect directly to cloud through their nearest point of presence, where traffic is inspected for threats, data leakage, etc. and then forwarded to its destination if safe. They do this with high performance and without user experience degradation, which has been key to their success. Moreover, Zscaler’s philosophy of zero trust assuming any user/app could be compromised and limiting access on a need to know basis is implemented by making applications invisible to unauthorized users and brokering connections only after trust is verified. Their services are also backed by extensive threat intel and they claim to block a huge volume of threats daily across their platform. Zscaler essentially offers an internet condom for enterprises, a secure way for users to access external and internal resources from anywhere, through a constantly updated cloud shield.
Key Strengths:
Potential Limitations:
Best For: Large distributed enterprises embracing cloud and mobility, who want to eliminate traditional network VPNs and appliances in favor of a cloud delivered model. For example, companies that are adopting Office 365, SaaS apps, and have many remote workers or branch offices benefit hugely from Zscaler; it enables direct cloud access securely, improving user experience and cutting MPLS or backhaul costs. Zscaler is also ideal for organizations pursuing a Zero Trust Architecture, as it provides the core technologies needed for secure access based on identity and context. Highly regulated industries in finance, healthcare that require strict control over data leakage find Zscaler’s DLP and CASB capabilities helpful in the cloud era. If your strategic goal is to modernize and simplify network security moving away from a classic hub and spoke VPN/security stack to a cloud based SASE model, Zscaler is often the top recommended vendor to achieve that.
Headquarters: Armonk, NY, USA
Founded: IBM parent founded 1911; IBM Security division formally created 1994 with many acquisitions since
Company Size: 350,000+ IBM overall; tens of thousands in security
Primary Services/Products: IBM offers Consulting and Managed Security Services, including Managed Detection & Response through IBM Security Services, cloud security services, and incident response. Key products include IBM QRadar SIEM and QRadar XDR, IBM Guardium data security, MaaS360 mobile security, and IBM Cloud Pak for Security integration platform. IBM’s X Force Red team provides penetration testing and adversary simulation, and X Force Incident Response handles breach response.
Industries Served: Virtually all, with deep penetration in government, finance, healthcare, and other highly regulated or large scale industries. IBM Security has specialized teams for sectors like banking, federal, automotive, etc.
Why They Stand Out: IBM is one of the few providers that can do it all from technology solutions to outsourcing and consulting. In the 2020s, IBM pivoted heavily to cloud and AI in security. By 2026, IBM Security is recognized as a leader in managed security services, for example, an IDC MarketScape named IBM a Leader in Worldwide Managed Security Service Providers for Security Service Edge in 2026. IBM’s strengths are scale and expertise: they operate multiple global Security Operations Centers SOCs providing 24/7 monitoring for clients, and they have X Force research teams analyzing threats publishing the annual IBM Threat Intelligence Index. IBM has also integrated AI notably Watson AI into their security offerings to assist with threat analysis and automation. For compliance focused organizations, IBM’s knowledge of regulatory requirements is second to none; they often help write industry standards and can map security controls to any framework needed. Additionally, IBM’s breadth means they can bring hardware IBM mainframes, etc., software, and services together for example, securing hybrid cloud environments that span on prem IBM systems and public clouds. While IBM’s sheer size can sometimes make it seem less nimble, it undeniably brings huge trust and proven reliability, which is why so many Fortune 500 companies rely on IBM as a security partner.
Key Strengths:
Potential Limitations:
Best For: Fortune 500 enterprises, critical infrastructure, and organizations that demand a safe pair of hands in security. IBM is ideal for companies that have complex, global operations and want a provider capable of matching that scale. Industries like banking that might need worldwide threat monitoring and instant IR response across continents, airlines, large manufacturers, and government agencies often choose IBM for the comprehensive coverage and trust factor. Companies undergoing digital transformation moving to cloud, modernizing networks with a need to overhaul security in parallel will benefit from IBM’s strategic advisory plus implementation strengths IBM can not only design the target security architecture but also manage it long term. If you face strong regulatory oversight and board level scrutiny on security, IBM’s thorough processes and reporting can provide reassurance auditors take comfort in IBM involvement, frankly. In summary, for an enterprise that needs broad spectrum defense with the option to outsource much of the heavy lifting, IBM Security is a top contender.
Headquarters: Boston, MA, USA
Founded: 2000
Company Size: ~2,500 employees
Primary Products/Services: Insight Platform including InsightIDR SIEM and XDR, InsightVM vulnerability management, InsightAppSec web app scanning, InsightConnect SOAR automation, and Managed Detection & Response MDR services. They also develop Metasploit popular open source pentesting tool and provide consulting for penetration testing and incident response.
Industries Served: Broad, with many mid market and enterprise clients across tech, financial services, healthcare, and retail. Rapid7’s mix of products and services appeals to security teams that want integrated tools with optional expert assistance.
Why They Stand Out: Rapid7 has evolved from a vulnerability management company into a well rounded security operations player. Their value proposition is unifying data and capabilities that are often siloed. For example, their Insight platform brings together vulnerability risk metrics with SIEM detections, so you can correlate a threat detection with whether the target system was missing patches, etc. In 2026, Rapid7 continues to be recognized in Gartner’s Magic Quadrant for SIEM. They've been included for 7 years running, and they rank strongly in vulnerability management Forrester Waves, etc.. A big selling point is usability. Rapid7 products are known for having a shorter learning curve and easier deployment than some competitors. This makes them popular with lean teams. Rapid7 also heavily integrates automation through their SOAR, InsightConnect and recently introduced more AI features like an AI assisted investigation feature in their platform. On the services side, Rapid7’s Managed Detection and Response is widely used by companies that need 24/7 monitoring without building their own SOC; Rapid7’s analysts use the same InsightIDR platform, which means customers benefit from insight that’s built into the product through frontline experience. Additionally, Rapid7’s heritage with Metasploit and offensive security gives them a unique edge in understanding how attackers operate and helping clients prioritize fixes; they maintain a huge database of exploits and insights from the Metasploit community. The company’s culture of combining practitioner know-how with software solutions resonates with security teams who want tools that actually make their day to day easier, not more complicated.
Key Strengths:
Potential Limitations:
Best For: Mid market and decentralized enterprises that want consolidated security operations capabilities without a massive staff. Rapid7 is excellent for companies that perhaps can’t afford a huge team of SIEM engineers, threat hunters, and incident responders individually because Rapid7’s product+service can fill many of those roles. Industries like tech startups, mid-sized financial services, higher education, and regional healthcare providers often gravitate to Rapid7 for its balanced approach to protection and ease of use. It’s also a strong choice for organizations aiming to elevate their detection and response maturity: if you have basic logging today and want to step up to advanced threat detection, Rapid7 can accelerate that journey with both the tools and the expert guidance through their advisory services or MDR. Additionally, if you value tying together your vulnerability risk management with your detection program, Rapid7 offers one of the most unified views of these traditionally siloed domains ideal for security leads who need to communicate risk reduction in holistic terms.
| Company | Specialization | Best For | Region HQ | Compliance Support | Ideal Company Size |
|---|---|---|---|---|---|
| DeepStrike | Manual Penetration Testing PTaaS | Offensive security, pentest excellence Best Overall | USA San Francisco | Reports align to SOC 2, ISO 27001, HIPAA; CREST like methodologies | SMB to Mid Enterprise also used by some large tech firms |
| Palo Alto Networks | Next Gen Firewalls & SASE | Network & cloud security platform Best for unified enterprise security | USA Santa Clara | Certifications: FedRAMP, Common Criteria; Compliance mappings in Prisma | Mid to Large Enterprise |
| Fortinet | Unified Threat Management | Cost effective security for distributed orgs Best for SMB value | USA Sunnyvale | PCI DSS device hardening, NSS tested; compliance logging | Small Business to Large Enterprise scales broadly |
| Cisco | Secure Networking & Zero Trust | Secure SD WAN and Zero Trust access Best for large networks | USA San Jose | Supports NIST, FIPS, FedRAMP Umbrella; extensive compliance documentation | Large Enterprise & Government |
| CrowdStrike | Endpoint Protection & XDR | Advanced threat detection & hunting | USA Austin | FedRAMP High authorized; maps to MITRE tactics for compliance audits | Mid to Large including Fortune 100 |
| SentinelOne | Autonomous Endpoint Security | Automated endpoint defense AI driven | USA Mountain View | MITRE ATT&CK reporting; compliance via rollback logs PCI, etc. | Mid to Large Enterprise |
| Zscaler | Cloud Security SWG, ZTNA | Secure cloud access & zero trust remote workforce | USA San Jose | SOC 2 Type II, ISO 27018; assists with HIPAA, GDPR via DLP controls | Mid to Large Enterprise |
| IBM Security | Managed Security & Compliance | Full service, compliance focused programs Best for regulated enterprise | USA Armonk, NY | Extensive ISO 27001 certified, helps with PCI, HIPAA, etc. | Large Enterprise & Critical Sectors |
| Rapid7 | SIEM, XDR & Vulnerability Mgmt | Unified threat detection & risk management Best for compliance driven mid market | USA Boston | PCI, HIPAA reporting; aligns vulns to CVSS/regs; auditor friendly logging | Mid Enterprise also upper SMB |
Choosing the right security vendor depends on your environment and priorities. Many enterprises adopt a layered defense: for example, pairing a network/security platform like Palo Alto or Fortinet for perimeter and cloud, an endpoint solution like CrowdStrike or SentinelOne for host level defense, and a cloud access platform like Zscaler for remote access. They then integrate these with managed services or SIEM from providers such as IBM or Rapid7 for 24/7 monitoring and compliance support. Crucially, organizations should also validate their defenses through independent testing. This is where DeepStrike’s proactive penetration testing complements the above platforms; its 100% manual approach finds logic flaws and attack paths that automated tools miss, ensuring that even secure systems are truly tested. DeepStrike’s unlimited re-testing and audit ready reports help verify that vulnerabilities are fixed properly, which is often required for compliance.
In summary, 2026 demands both robust security platforms and rigorous validation. The vendors listed above represent leaders in each category from Palo Alto’s integrated network defense to CrowdStrike’s AI powered endpoint protection to Zscaler’s zero trust cloud gateway. Enterprises should consider Gartner recognized solutions in their respective domains e.g. Palo Alto in SASE, CrowdStrike in endpoint, Zscaler in SSE, IBM in managed services and reinforced them with expert human led testing. As one industry analyst put it, the best security strategy blends state of the art tools and continuous human validation to stay ahead of threats. In this integrated model, DeepStrike’s manual pentesting and red teaming add a critical layer of assurance that you’re not relying solely on automation.
By selecting vendors aligned to each of your use cases network, endpoint, cloud, compliance and augmenting them with DeepStrike’s exhaustive testing, your organization can achieve a stronger, more resilient cybersecurity posture in 2026.

Our Evaluation Methodology: To ensure a high quality, procurement friendly ranking, we assessed companies across multiple dimensions of E E A T Experience, Expertise, Authoritativeness, Trustworthiness:
Using the above methodology, we narrowed down a field of dozens of U.S. based cybersecurity providers to the top performers in each category below.
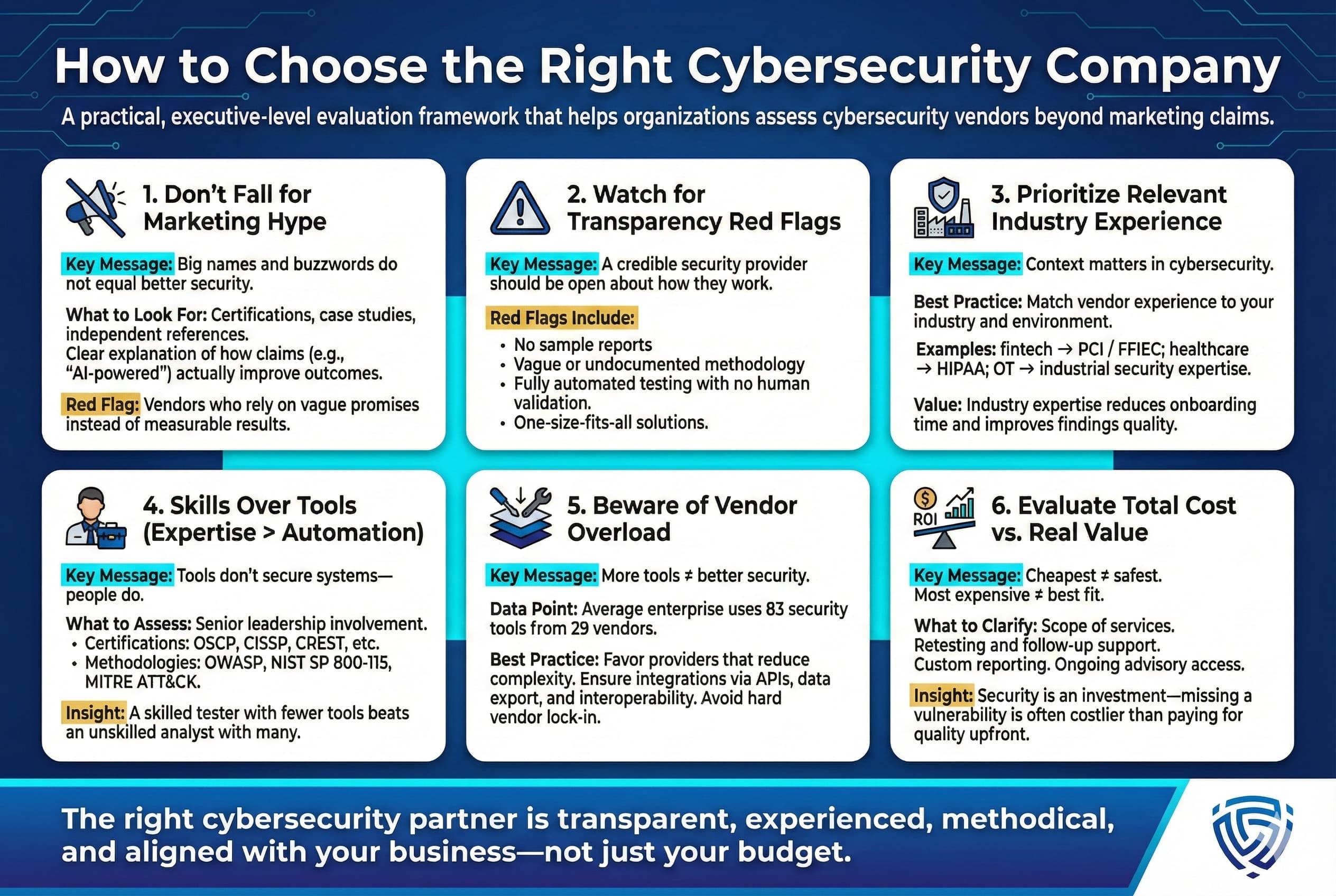
Even with a strong shortlist, buyers should do their due diligence. Here are some tips to ensure you choose the right provider for your needs:
By keeping these points in mind, you can approach the vendor selection process with a clear head. Next, we present the top cybersecurity companies in the USA for 2026, along with their profiles, strengths, and ideal fit, to kickstart your evaluation.
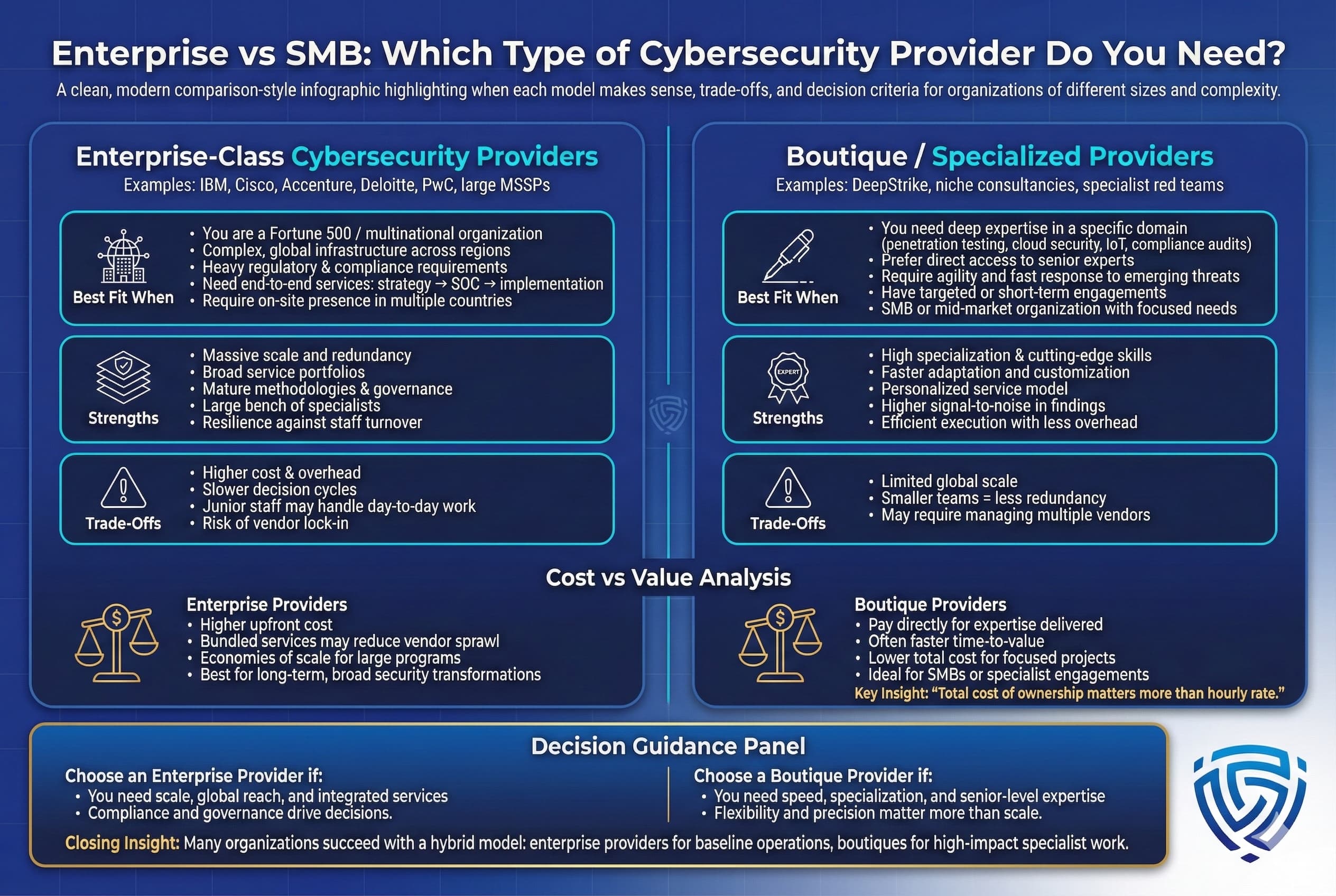
Cybersecurity providers come in all sizes, generally falling into two camps: large enterprise class firms and boutique specialized firms. Both have advantages; the key is determining which suits your organization’s needs.
In summary, large providers are like a one stop department store, convenient and comprehensive whereas boutique firms are like specialty shops with expert craftsmen. Enterprises with broad needs and high assurance requirements may lean towards the former, while those with specific pain points or seeking a tailored approach might opt for the latter. Some organizations even use a mix: a big MSSP to cover the basics and niche experts for specialized testing or projects. The key is to assess your internal team’s strengths, your risk profile, and the complexity of your environment, and choose the provider type or combination that addresses your gaps most effectively and efficiently.
The cost of a professional penetration test can vary widely depending on scope and complexity. On the low end, a small test e.g. a simple web app or small network might start around $5,000. A more comprehensive engagement for a mid size company often falls in the $10,000–$30,000 range. Complex tests for large enterprises, multiple networks, extensive applications can exceed $50,000, and some very large assessments go into six figures . Factors that influence cost include the number of IPs or applications in scope, testing depth gray box with credentials vs black box, and any special methodologies social engineering, hardware testing, etc.. Be wary of very low quotes under $5K; those often indicate a superficial automated scan rather than a real manual pentest. Keep in mind the value: considering the average US breach costs $10M+, spending tens of thousands on a quality pentest that prevents a breach is usually worth it. Many providers will work with you to right size the scope to your budget. Also ask about retesting good firms like DeepStrike include free re testing of fixes, which adds value. Ultimately, budget for at least an annual pentest see below on frequency and treat it as an investment in risk reduction rather than a one time expense.
Expertise is more important, and certifications are one way to gauge that. A skilled team with solid certifications OSCP, CISSP, GIAC, CREST, etc. generally indicates they have proven knowledge and have been vetted against industry standards. Tools are just means to an end. Practically all reputable firms will have access to similar toolsets, vulnerability scanners, SIEM platforms, etc.. What differentiates providers is how they use those tools and their human creativity/insight. For example, an automated scanner might flag common issues, but an OSCP certified pentester could exploit a chain of low risk findings into a major breach. That said, look for a provider that has both: talented people and a robust toolset. Providers with relevant certifications and accreditations like ISO 27001 for the company, or SOC 2 Type II reports also demonstrate they follow security best practices internally. But don’t be blinded by alphabet soup. Ask providers to explain how their team’s experience will solve your specific problems. Also, in some domains, certifications like PCI QSA for compliance assessments or CREST for pentesting in certain regions might be mandatory or add credibility. In summary: use certifications as a quality indicator and a tie breaker, but also consider case studies, testimonials, and your gut feeling of their competence. A great provider will happily discuss methodologies often following standards like OWASP, NIST rather than just touting tools.
Timelines can range from a few days to several weeks. A basic external network pentest might take 1–2 weeks including reporting. A web or mobile app test is often 1–2 weeks per application, complex apps could be longer. Comprehensive internal network pentests for midsize companies usually last 2–4 weeks end to end. For large enterprise environments, testing can extend to 4–6 weeks or more, especially if multiple phases recon, exploitation, pivoting internally are involved. Additionally, time is needed upfront for scoping and getting necessary access IP whitelisting, credentials for gray box tests, etc., and afterwards for report review and remediation discussions. Incident response or compromise assessments typically take a few weeks for data collection and analysis, but can be shorter if the situation is urgent teams will work 24/7 in a crisis. Security audits like ISO 27001 readiness might involve sporadic engagement over a month or two. It’s wise to communicate any deadlines like compliance dates or board meetings to the provider. Many will adjust resources to meet a hard deadline if needed. Keep in mind, rushing a pentest is not advisable; testers need sufficient time to be thorough. Conversely, extremely prolonged tests can lose momentum so a focused window with clear scope is best. Always factor in time for remediation and retest after the initial findings. A good rule of thumb: for an average environment, budget about 3 weeks for the active testing and another week for report/fix validation. Simpler projects can be quicker, and very complex ones proportionally longer.
A high quality report is one of the key outcomes of any security engagement. You should expect:
In essence, the deliverable should be actionable. It’s not just about finding problems, but enabling you to fix them and improve. A red flag is a report that’s just scanner output or lacks context. Top firms put significant effort into custom prose, clear visuals, and specific guidance. For managed services MDR/MSSP, deliverables are more continuous e.g., a portal with dashboards, monthly service reviews, and incident tickets with analysis when threats are detected. Ensure any provider clearly defines what you’ll receive and in what timeframe. Don’t hesitate to ask for a sample report beforehand sanitized of course to judge their reporting quality.
At minimum, annually. Most standards and experts recommend a full scope penetration test at least once per year. Many compliance frameworks such as PCI DSS, for example, require annual testing and after significant changes. However, given the pace of threats and development, more frequent testing is advised for critical systems. A common approach is to do an annual big test and supplemental tests quarterly or bi annually on key areas. For instance, if you have a customer facing web app, you might pentest it before each major release, not just once a year. Continuous Pentesting or PTaaS Pentest as a Service is an emerging model where portions of your environment are tested on a rolling basis throughout the year; this can catch issues closer to their introduction. Additionally, you should do vulnerability scanning much more frequently monthly or weekly for externals, at least quarterly for internals, or continuous with tools. If you’re using an MDR service, you’re essentially having your defenses tested 24/7 by how well they detect probes and attacks. Risk profile matters: if you’re in a high target industry finance, healthcare or handle sensitive data, consider semi annual or quarterly pen tests, and definitely test after any major infrastructure or application changes. Also, mix up the types of assessments: one quarter do a social engineering test, another quarter a cloud security review, etc., to cover different angles. For SMBs, resource constraints might limit you to annual testing if so, focus it on your most critical assets each year. Remember, the threat landscape is dynamic; new vulnerabilities like Log4j, etc. can emerge anytime. Some companies supplement annual pen tests with bug bounty programs or periodic red team exercises to get more frequent coverage. In summary, make security testing a regular, ongoing practice rather than a one off. As a baseline: annual comprehensive pen test, with additional targeted tests in between, is a solid strategy to ensure continuous improvement and no nasty surprises lurking.
Automated tools are necessary but not sufficient. They are a great first line of defense in fact, any good security program will use vulnerability scanners, automated compliance checks, SIEM correlation rules, etc. However, tools have limitations. Scanners might detect known common weaknesses, missing patches, misconfigurations but they can’t think creatively or understand business logic. Many breaches occur due to complex attack chains or logic flaws that automated tools simply don’t catch. For example, a scanner might not realize that by using a sequence of normal low risk actions across different systems, an attacker could transfer funds or steal data that insight comes from human expertise. Hiring a cybersecurity company or having in-house experts brings that human element: people who can interpret results, find unknown vulnerabilities, and reduce false positives. Additionally, professional testers and analysts use tools as part of their arsenal, but they validate and probe deeper. Automated tools also require configuration and tuning. It's easy to get a false sense of security if a tool is misconfigured or not scanning everything. A security firm can ensure tools are used correctly and can augment them with manual techniques. Another aspect is context and advice: a scanner might tell you port 443 is open with TLS 1.0, but a human consultant can tell you what that means in terms of risk to your specific business and how to prioritize fixing it among all issues. That said, for day to day hygiene, automated tools especially for patch management and log analysis are indispensable and many security companies will help you set those up too. Think of it like medical care: you have automated blood pressure cuffs and apps, but you still need a doctor to interpret and treat effectively. In cybersecurity, use tools to cover the basics continuously, and use expert driven assessments to deep dive and audit the efficacy of those tools. The combination yields the best security posture.
In cybersecurity, product vendors develop and sell software or hardware solutions for example, firewall appliances, antivirus software, SIEM platforms, etc. Service providers offer expertise and outcomes as a service like consulting engagements, managed security monitoring, or incident response handling. The difference often comes down to what you are buying: a tool that your team operates on versus a result delivered by the vendor’s team service. However, the line is blurring. Many companies, especially those in this Top Companies list, do both. For instance, CrowdStrike is a product company Falcon platform but also has managed threat hunting services. IBM sells security products QRadar SIEM and provides services managed by SIEM via their staff. When evaluating a vendor, it’s important to clarify if you’re looking for technology to empower your team or if you want to offload work to the provider. Pros of product vendors: you maintain control and can customize internally; potentially lower ongoing cost if you have the expertise. Cons: you need skilled staff to use them fully, and the responsibility is on you to react to what the product finds. Pros of service providers: they bring expertise and can often detect/respond faster with their specialized focus; less burden on your team. Cons: you are entrusting an external party so vet them for trust and skill, and costs can accumulate as services are ongoing. Many top companies package product + service together like an MDR service using their own XDR product. This can be efficient, but ensure the combined offering truly fits your needs. Some organizations prefer a best of breed product from one company and services from another or in house. There’s no one size answer, it depends on your internal capabilities and preferences for control vs outsourcing. In summary, know that most leading cybersecurity companies today offer both: platforms to secure you and expertise to manage or enhance those platforms. Evaluate each aspect on its own merits. You might love a vendor’s tool but not need their services, or vice versa. The good news is integrated offerings can simplify things if they align well with your requirements.
Translating security spend into business terms is key. Here are a few angles:
Finally, break down deliverables in business language: e.g., This penetration test will help us protect customer data by identifying weak points before attackers do, or This MDR service means we have experts watching our systems 24/7, so our small IT team doesn’t have to and we can respond to threats in minutes instead of days. Tie it to business uptime, customer trust, and financial protection. Present it as an investment with clear outcomes, not just a cost. Often, including a brief from the provider’s proposal with their results stats or client success stories can bolster your case. In short, speak in terms of risk reduced, value gained, and alignment with business goals. Management is likely to approve spending when they see it supports the company’s continuity and success.
Cyber threats don’t discriminate by company size. In fact, attackers often target smaller firms as easy prey, or as stepping stones to larger partners/clients. While you might not need a multi million dollar security program, you absolutely need effective security measures appropriate to your business. The good news is many top companies have offerings for smaller organizations, or there are high quality smaller vendors that made our list like DeepStrike for specialized testing or Rapid7’s tailored services. Start by identifying your crown jewels, the data or systems that, if compromised, could be fatal to your startup. It could be your intellectual property, customer data, or even just your website and reputation. Then assess what internal capability you have. Many startups have very limited IT/security staff, so bringing in an external expert to do a security assessment or set up some defenses is wise. You might not hire IBM Security to manage your operations if you’re 50 people, but you could use a company like Arctic Wolf MDR for SMB or a boutique consultancy to harden your app. The key is scoping: you can engage top providers for a right sized engagement e.g., a one time cloud config review, or a lightweight managed detection service that fits a small company budget. Also consider that small companies often need to prove security to win clients. Having a respected security firm’s report or service can punch above your weight in giving enterprises confidence to do business with you. Ultimately, no company is too small for hackers but your defenses can be agile and scaled to your size. Perhaps focus on one or two critical security services; for instance, many startups start with a solid cloud security posture review and a recurring pentest, and as they grow, they layer in more maybe a vCISO service or MDR. Leverage the fact that some big name products have tiered pricing for small users or use open source tools initially, but validate with occasional expert audits. In summary, you may not need all the bells and whistles that a Fortune 100 does, but you do need the essentials. Top cybersecurity companies can provide high quality essentials in a package for small firms and that could save your startup from a catastrophe that derails your growth. Security, like insurance, is often more affordable than the cost of a single incident. Even as a lean startup, aim to allocate some budget a few percent of IT spend to security from the get go it will pay off in stability and trust as you scale.
Leading cybersecurity companies invest heavily in threat intelligence and R&D to stay ahead of the curve. They have dedicated research teams like Unit 42 at Palo Alto, Talos at Cisco, X Force at IBM, etc. that continuously monitor hacker forums, malware samples, breach reports, and vulnerabilities. For instance, as of late 2026, many are closely tracking AI driven cyber threats and deepfakes, which half of security pros cite as a major concern. These research units publish blogs, advisories, and feed updates into their products e.g., new detection signatures or IoCs. Additionally, top firms participate in industry sharing groups like FS ISAC, CERTs so they get early warnings of threats affecting certain sectors. When a new critical vulnerability zero day emerges, companies like Microsoft, CrowdStrike, etc., often already have analysts reverse engineering it and developing patches or detection rules within hours sometimes in collaboration under NDAs before public disclosure. Many providers also use AI and machine learning defensively: for example, training models on the latest attack patterns so their tools can identify novel variants CrowdStrike reducing breach detection time with AI. They also run labs and testing environments, think honeypots, research sandboxes to see how new threats behave. Importantly, firms engaged in incident response learn from every breach they investigate, and that knowledge is folded back into preventative services. The competitive nature of the industry also means if one company finds a new attack technique, others quickly study and account for it. Clients of top providers benefit through regular threat briefing reports, updated controls, and sometimes direct alerts if a threat is relevant to them. So, in short, these companies stay up to date by maintaining expert teams, leveraging global telemetry often millions of endpoints or sensors reporting in, collaborating across the community, and applying automation to digest massive amounts of threat data. Part of why you choose a top vendor is to essentially outsource that continuous research burden to them so you get the latest protections or advice because it’s their job to live on the bleeding edge so you don’t have to. Always feel free to ask a prospective provider how they keep current; the depth of their answer will tell you a lot about their internal excellence. Companies in our Top list will usually have impressive answers, showing that continuous innovation and intel is in their DNA.
There’s no one size fits all timeline, but a general guideline is to continually evaluate and refresh as needed while avoiding knee jerk changes. Many organizations do a formal review of their security stack annually or bi annually. If your current tools or provider are meeting your needs and keeping up through updates, you don’t necessarily need to rip and replace on a schedule. However, signs it’s time to update or change include: your threat landscape changed e.g., moved significantly to cloud you may need new cloud focused tools, your provider is not performing or has frequent misses, or new solutions offer compelling advantages like significant automation or consolidation benefits. Technology evolves fast for instance, five years ago few had a Zero Trust Network Access tool, now many are replacing VPNs with ZTNA like Zscaler or Palo Alto Prisma. If you’ve used the same AV for 7-10 years, it’s definitely worth evaluating next gen EDR solutions now. As a rule of thumb, major security technologies often have a lifecycle of ~5 years before a disruptive improvement may warrant change as long as support and updates continue in that period. Providers: if you outsourced your SOC to an MSSP and after a couple years you’re not happy with responsiveness or outcomes, shop around. Sometimes switching can increase security and even reduce cost if a new provider has a more efficient approach. On the other hand, be cautious of shiny object syndrome jumping to a new vendor or tool just because it’s hyped, without planning the migration and ensuring it truly fits, can cause gaps. A best practice is to keep an eye on independent evaluations of Gartner, MITRE ATT&CK results, etc. yearly, and do proof of concepts with new tech every few years to ensure you have the best for your needs. Also, consult your internal metrics: if certain tools have tons of unaddressed alerts or your team complains about them, it might be time to replace or upgrade. When it comes to managed services, contract lengths are often 1-3 years; it’s wise to align evaluations with those cycles you might bid out the service at renewal to see if you should stay or switch. In summary, evolution not revolution maintains an ongoing improvement mindset, and updates or changes providers when clear benefits in security or efficiency justify it. A static defense in a dynamic threat world can be risky, so regular tune ups and occasional overhauls with justification are healthy.
Developing an Incident Response IR plan is crucial, and leveraging your providers can greatly enhance it. Here’s an approach: First, assess your internal capabilities. What skills and resources do you have in house for IR? Identify gaps in expertise, coverage of hours, forensic tools, etc.. Next, involve a provider early for proactive preparation. Many top companies like IBM, Mandiant, etc. offer incident response planning services where they’ll help you create or refine your IR plan and even run tabletop exercises. Take advantage of that; their real breach experience ensures your plan is practical. Ensure roles and responsibilities are clearly defined between your team and the provider. For instance, if you have a retainership with a firm like CrowdStrike or Cisco, your plan should state when and how to escalate to them. Include provider contact info, SLA expectations, and any legal or NDA prerequisites in the plan. Run mock drills at least annually some do quarterly mini drills have your provider participate if possible, or at least review the results with them. This helps everyone get familiar with the process before a crisis. Additionally, integrate your IR plan with providers’ services: if you use an MDR service, the plan should reflect how they will notify you and what actions they take vs what your team does. Many providers have an IR platform or playbooks ask if you can adapt those into your plan. During plan development, consider including your legal, PR, and execs as well because top providers can also advise on communications and compliance steps post incident. The ideal approach is collaborative: you have an internal plan that’s enhanced by the provider’s expertise, and both sides know how to coordinate. Also, clarify commercial terms before an incident if you might need emergency incident response from a firm, having a retainer contract in place is far better than negotiating terms during a breach. That retainer usually includes some hours for planning and drills too. In summary, engage your security providers not just as emergency contacts but as partners in planning. They’ve seen the worst; use that knowledge to bulletproof your IR plan. Document it, practice it, and keep it updated e.g., if you adopt a new technology, add a playbook for incidents on that. With a solid plan that integrates external experts, you’ll handle incidents calmly and effectively, minimizing damage.
The cyber landscape is always evolving. As of 2026 and beyond, a few emerging or rapidly maturing technologies stand out:
In summary, AI/ML, cloud native security SASE, zero trust, identity centric security, and automation are the themes to watch. When planning investments, consider these trends and ask providers how they’re adapting. Many of the top companies in this list are already incorporating these emerging techs into their roadmaps e.g., many have AI in marketing now, but look at concrete features. It’s wise to pilot new tech on a small scale to see value before full adoption. But don’t chase hype; focus on technologies that solve your current challenges or clear challenges you foresee like securing an increasingly cloud based workforce. The goal is to evolve your security capabilities proactively, so you’re not caught off guard by new threat paradigms or business shifts.
Selecting the right cybersecurity partners is a critical decision that should be guided by objective evaluation and an understanding of your unique needs. In this article, we provided a research driven overview of the top cybersecurity companies in the USA 2026. We strived to maintain neutrality and base our rankings on transparent criteria focusing on proven expertise, service quality, and suitability for various use cases. Remember that best is context dependent: the best solution for a global bank might differ from that for a tech startup. Use this guide as a starting point to narrow your options and then engage directly with potential providers to ask the tough questions.
All the companies listed from innovative specialists like DeepStrike to industry giants like Palo Alto Networks and IBM have earned strong reputations in their respective domains. By understanding their strengths and limitations, you can make an informed choice rather than one based on hype or brand alone. We have no vested interest in which vendor you choose; our goal is to empower you with unbiased insights so you can bolster your organization’s security posture.
Ultimately, cybersecurity is not a set and forget endeavor. Whichever partners or products you choose, maintain an active relationship. Continuously assess performance, stay updated on emerging threats your providers should help with, and don’t hesitate to adjust course as your company grows or new risks emerge. An effective security strategy in 2026 leverages both cutting edge technology and human expertise. The top companies we covered offer a mix of both and find the mix that earns your trust.
Here’s to a safer, more secure future for your business. Armed with the right knowledge and the right allies, you can face the evolving threat landscape with confidence. Happy vendor hunting, and stay secure!
About the Author
Mohammed Khalil is a Cybersecurity Architect at DeepStrike, specializing in advanced penetration testing and offensive security operations. With certifications including CISSP, OSCP, and OSWE, he has led numerous red team engagements for Fortune 500 companies, focusing on cloud security, application vulnerabilities, and adversary emulation. His work involves dissecting complex attack chains and developing resilient defense strategies for clients in the finance, healthcare, and technology sectors.

Stay secure with DeepStrike penetration testing services. Reach out for a quote or customized technical proposal today
Contact Us